Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
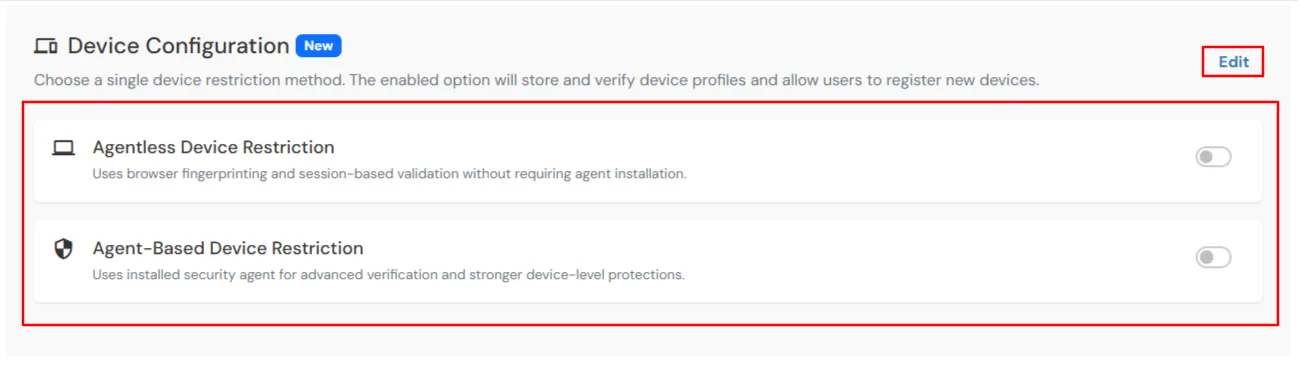
×Adaptive Authentication with Advanced Device Configuration empowers administrators to precisely control the number of devices a user can register while introducing a next-generation Device Security Agent that delivers stronger device identity, real-time risk scoring, and enhanced protection against spoofing and unauthorized access.
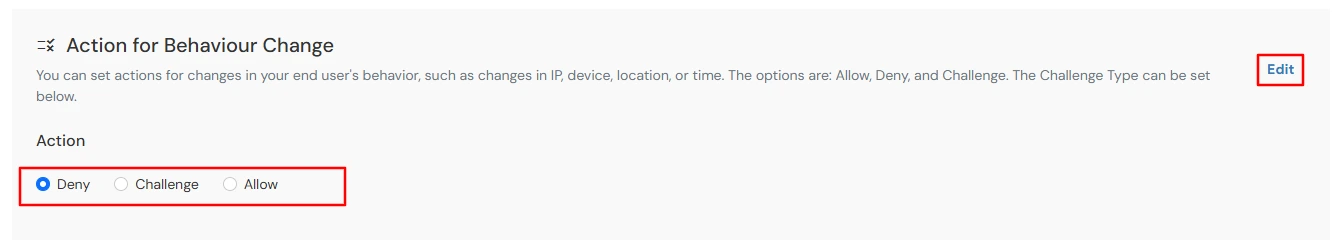
Authentication decisions are driven by continuous device risk evaluation, enabling intelligent enforcement actions such as Allow, Challenge, or Deny based on device trust and behavioral signals.
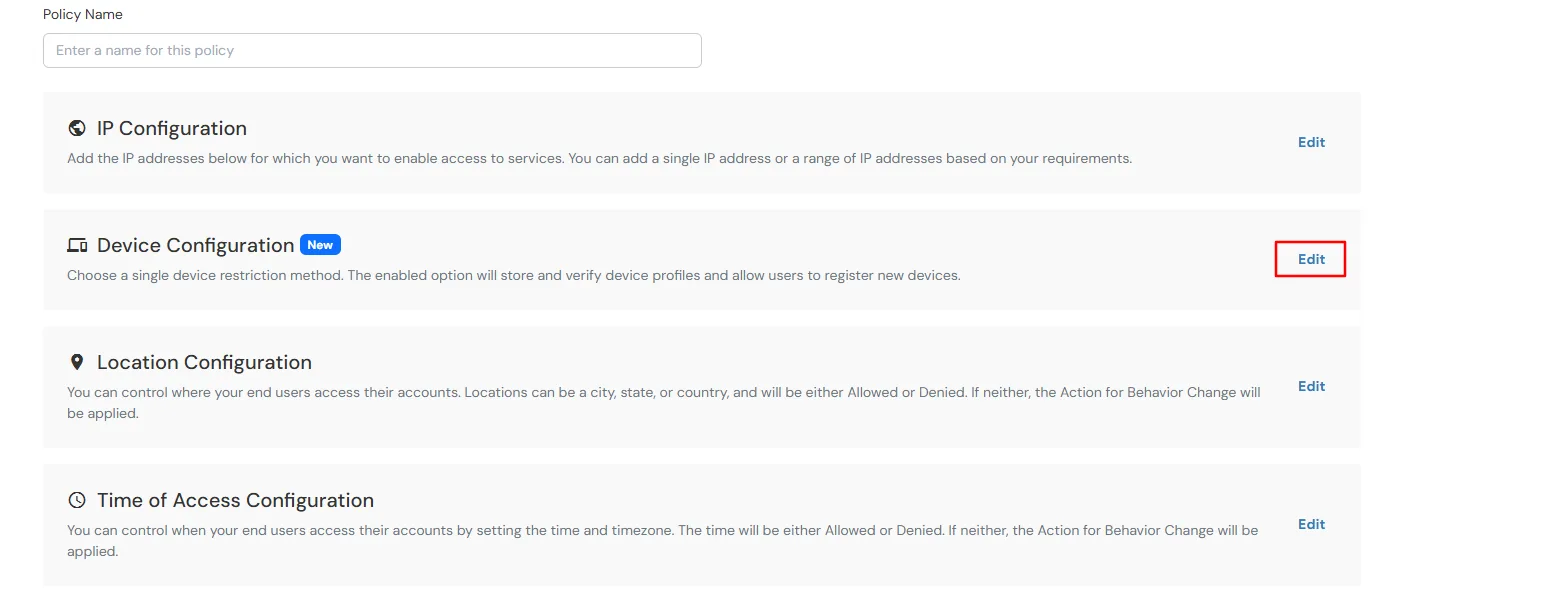
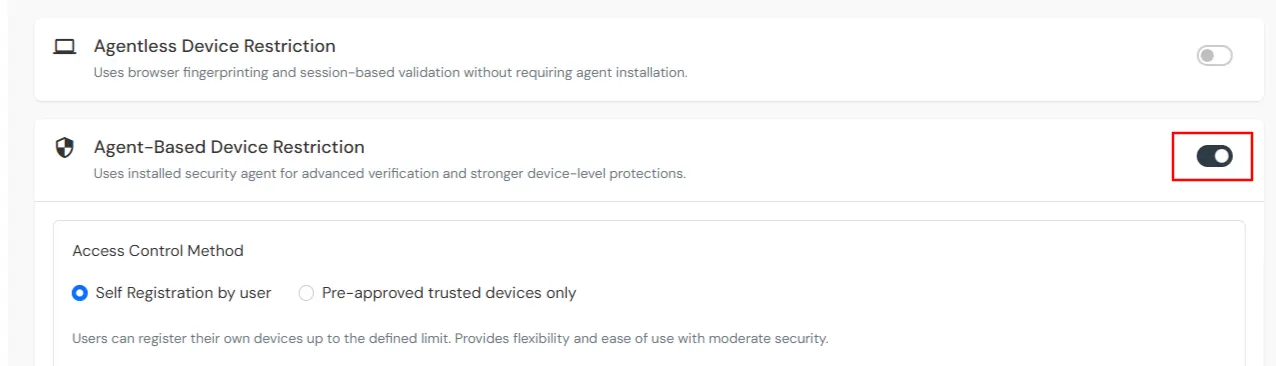
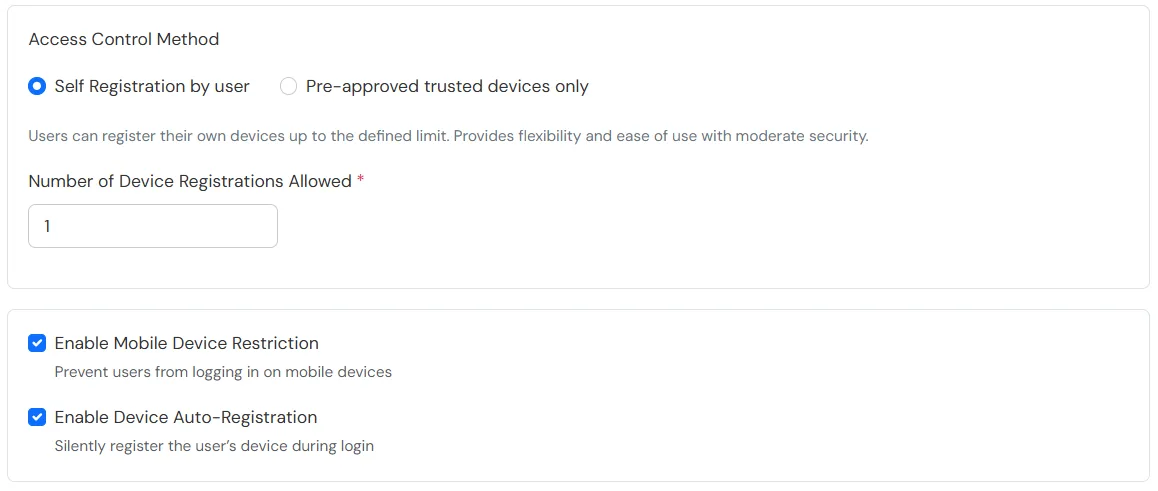
Device Configuration supports the following modes:
miniOrange offers free POC and help through a consultation call with our System Engineers to Setup Multi-Factor Authentication for Device Restriction in your environment with 30-day trial.
For this, you need to just send us an email at idpsupport@xecurify.com to get free POC and we'll help you setting up our solution in no time.
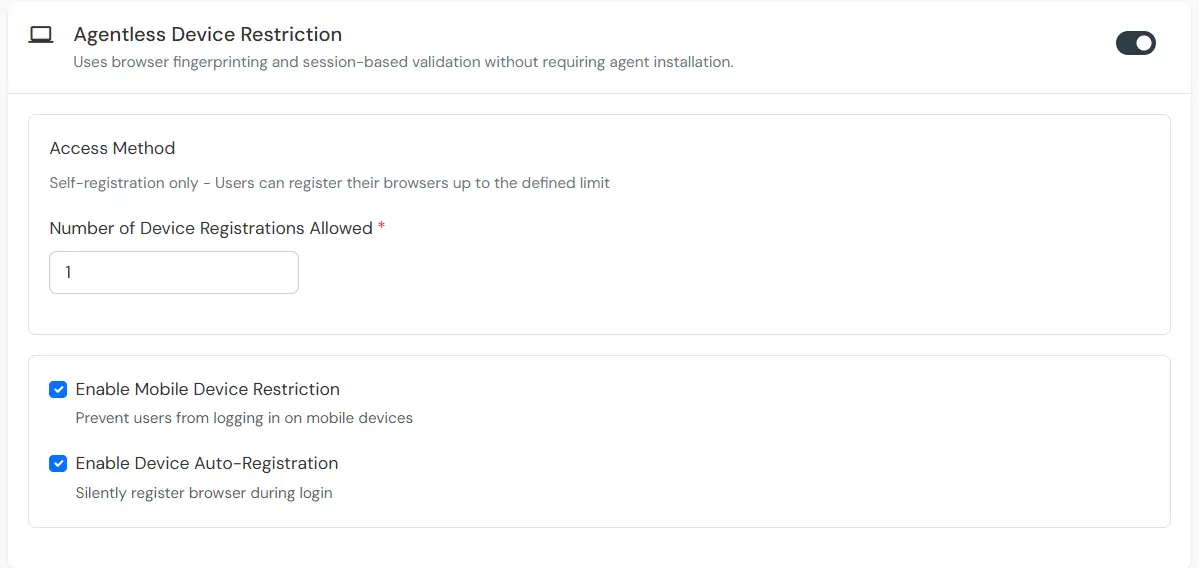
| Attribute | Description |
|---|---|
| Allow | Allow user to authenticate without challenge and registration. |
| Challenge | Allow user authentication with a challenge, e.g., when the device limit is exceeded. |
| Deny | Deny user authentication, e.g., when the device limit is exceeded. |
| Attribute | Description |
|---|---|
| User second Factor |
The User needs to authenticate using the second factor he has opted or assigned for such as
|
| KBA (Knowledge-based authentication) | The System will ask user for 2 of 3 questions he has configured in his Self Service Console. Only after right answer to the questions user is allowed to proceed further. |
| OTP over Alternate Email | User will receive a OTP on the alternate email he has configured threw Self Service Console. Once user provides the correct OTP he is allowed to proceed further. |
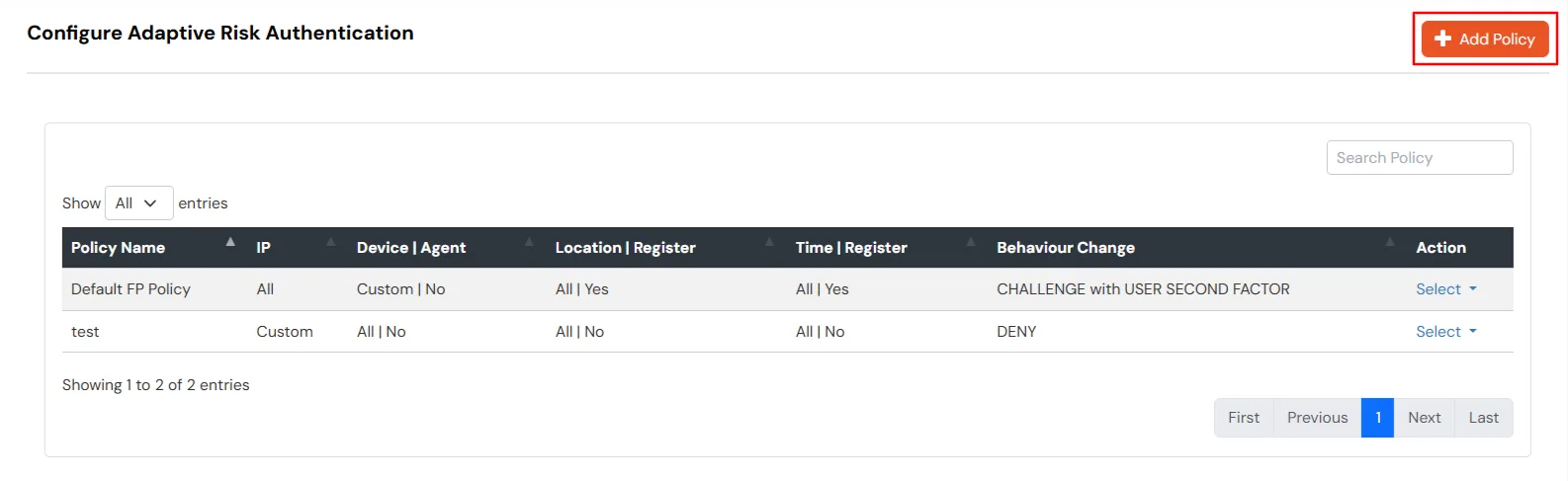
The policy will take effect only after it is associated with a specific application login flow.
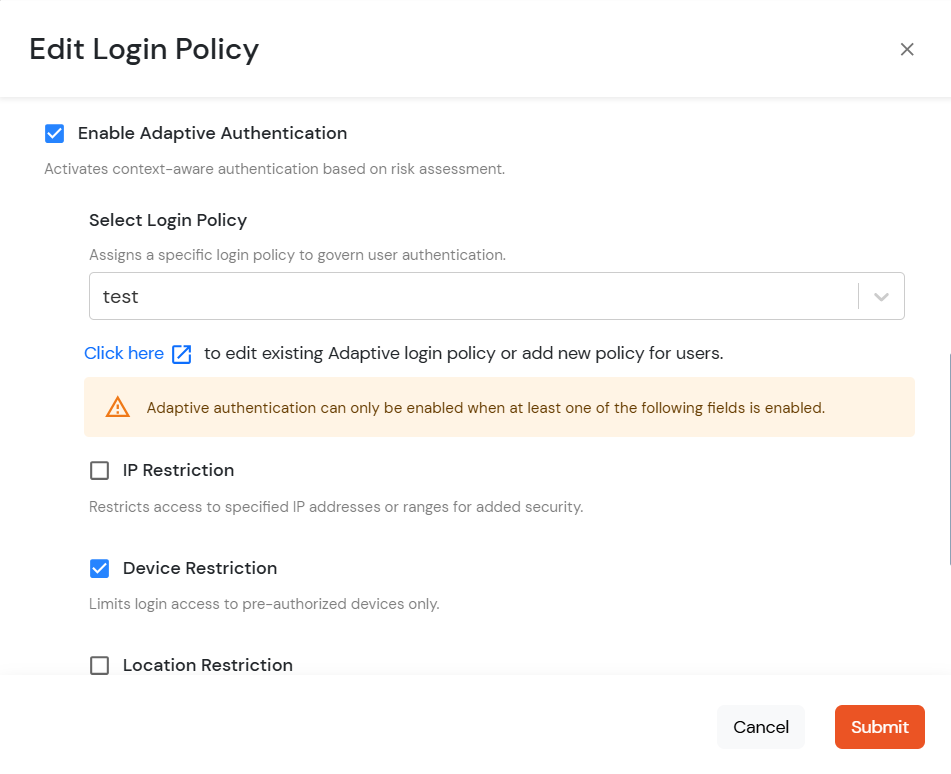
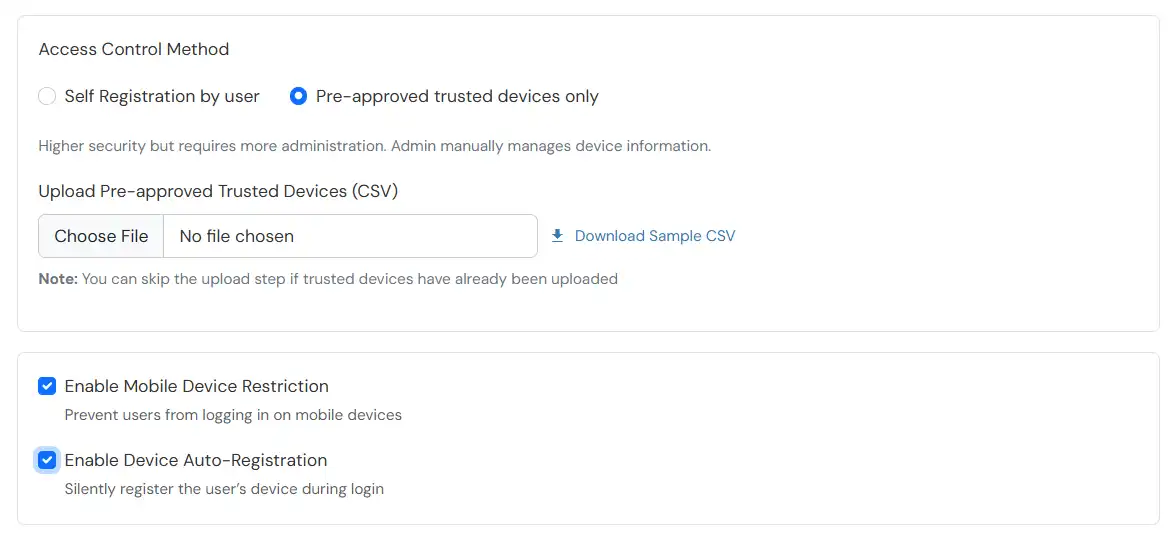
Applies when a user is registering a device for the first time.
https://<domain_name>.xecurify.com/moas/login
Note:
If Auto-Registration is enabled and Action for Behaviour Change is set to Deny or Challenge, the device is registered automatically after successful challenge.
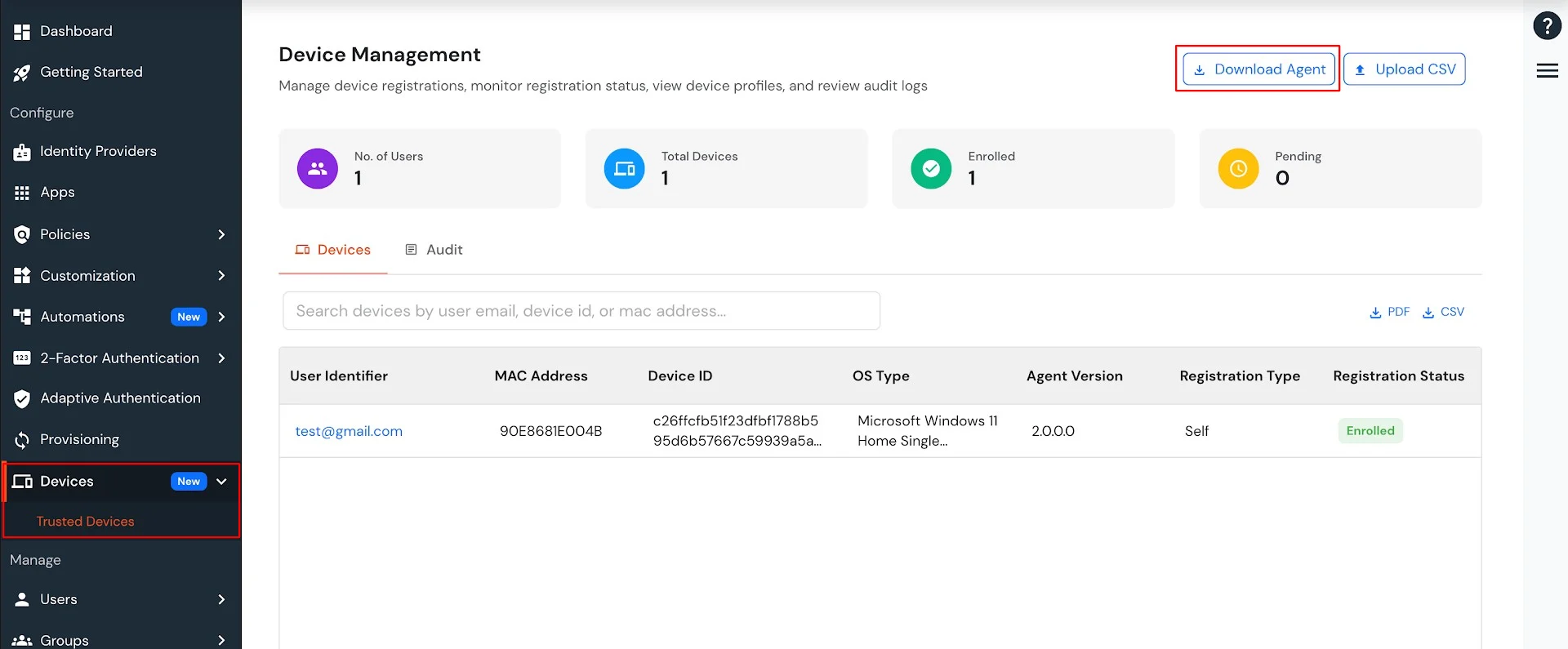
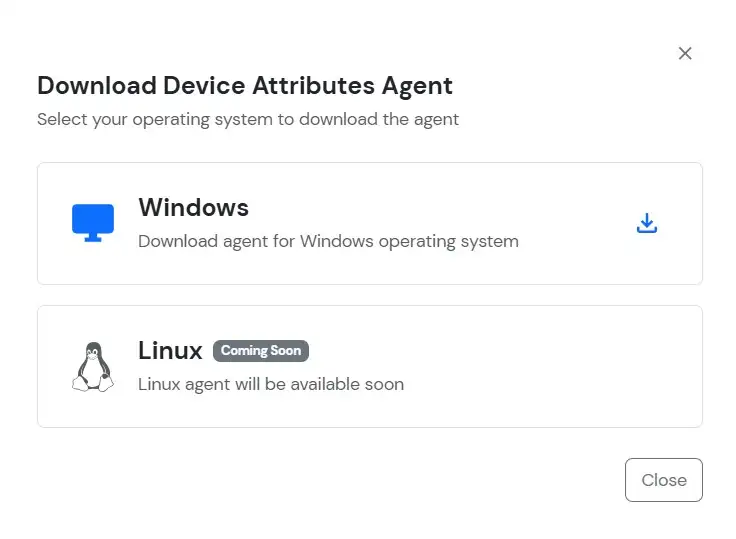
The miniOrange Device Agent must be installed on your device.
Steps to download the Miniorange Agent:
The Risk Engine allows you to evaluate device trustworthiness by analyzing multiple device attributes and calculating a risk score. Based on this score, user access is allowed, challenged, or denied during login and device registration.
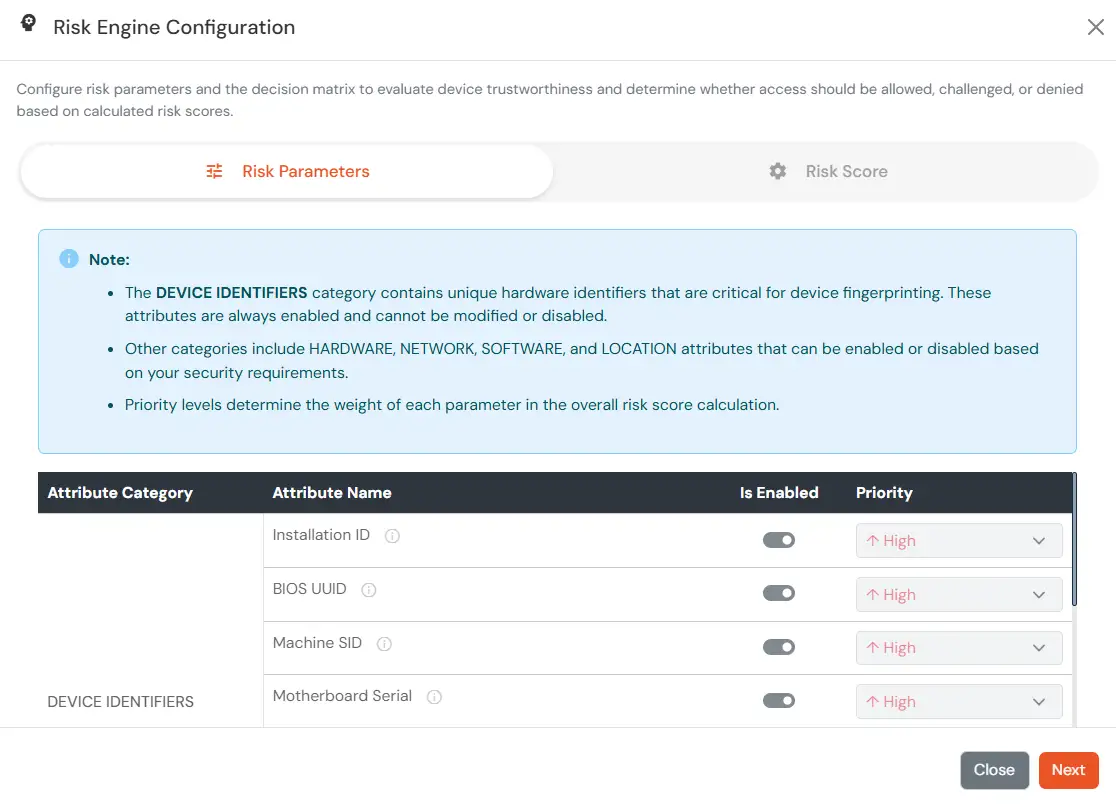
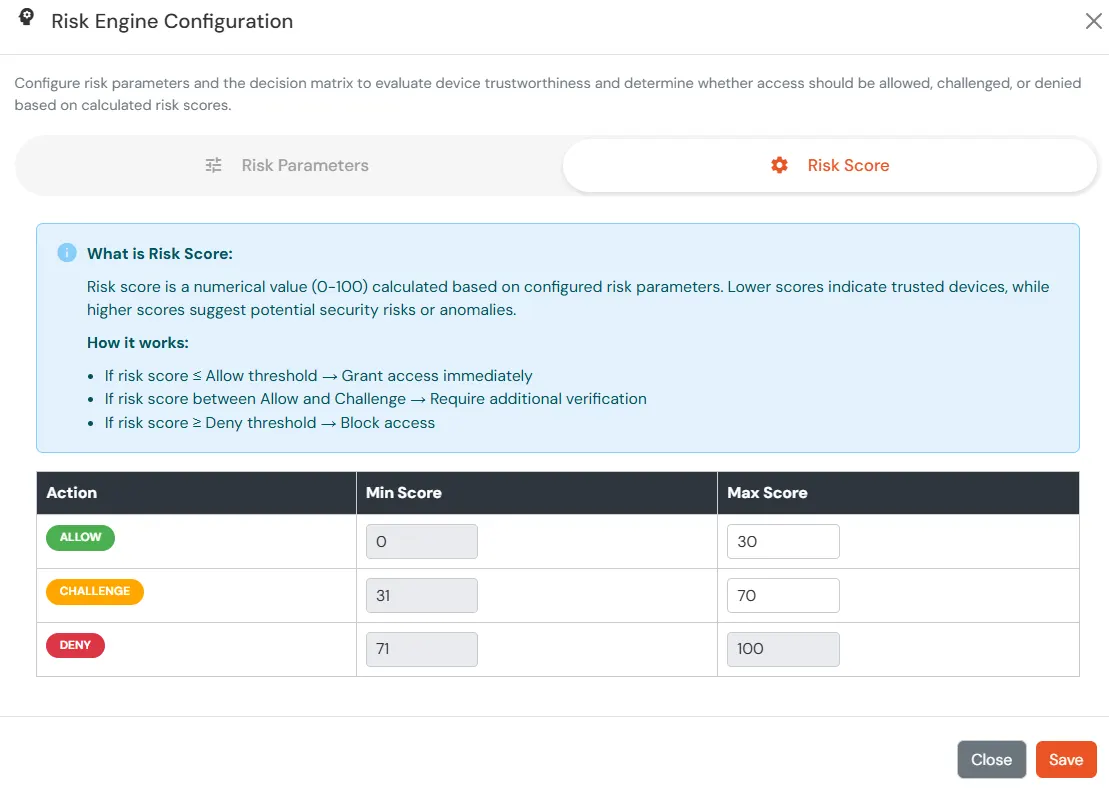

| Attribute | Description |
|---|---|
| Allow | Allow user to authenticate without challenge and registration. |
| Challenge | Allow user authentication with a challenge, e.g., when the device limit is exceeded. |
| Deny | Deny user authentication, e.g., when the device limit is exceeded. |
| Attribute | Description |
|---|---|
| User second Factor | The User needs to authenticate using the second factor he has opted or assigned for such as |
| KBA (Knowledge-based authentication) | The System will ask user for 2 of 3 questions he has configured in his Self Service Console. Only after right answer to the questions user is allowed to proceed further. |
| OTP over Alternate Email | User will receive a OTP on the alternate email he has configured threw Self Service Console. Once user provides the correct OTP he is allowed to proceed further. |
The policy will take effect only after it is associated with a specific application login flow.

Applies when a user is registering a device for the first time.
https://<domain_name>.xecurify.com/moas/login

Note:
If Auto-Registration is enabled and Action for Behaviour Change is set to Deny or Challenge, the device is registered automatically after successful challenge.

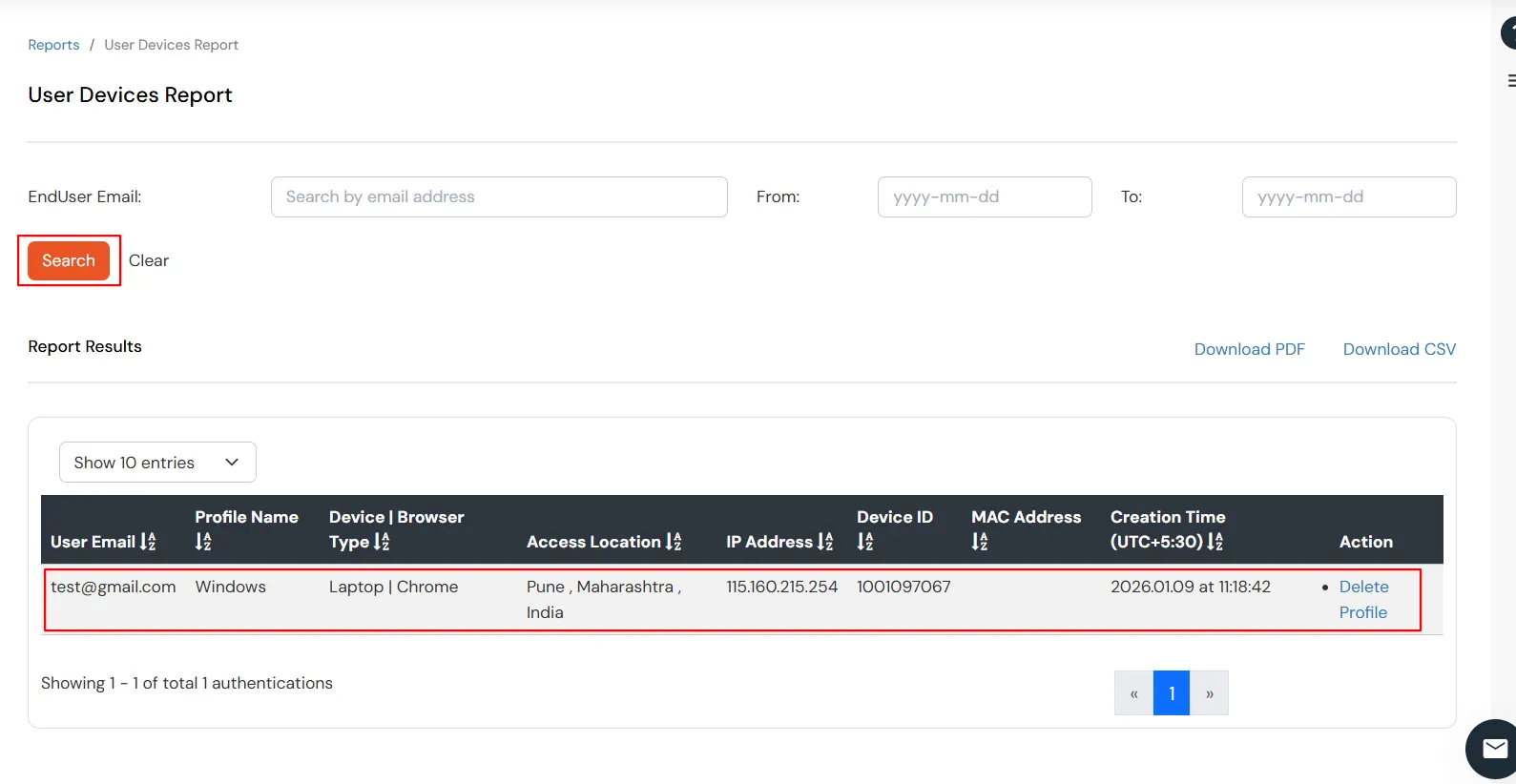
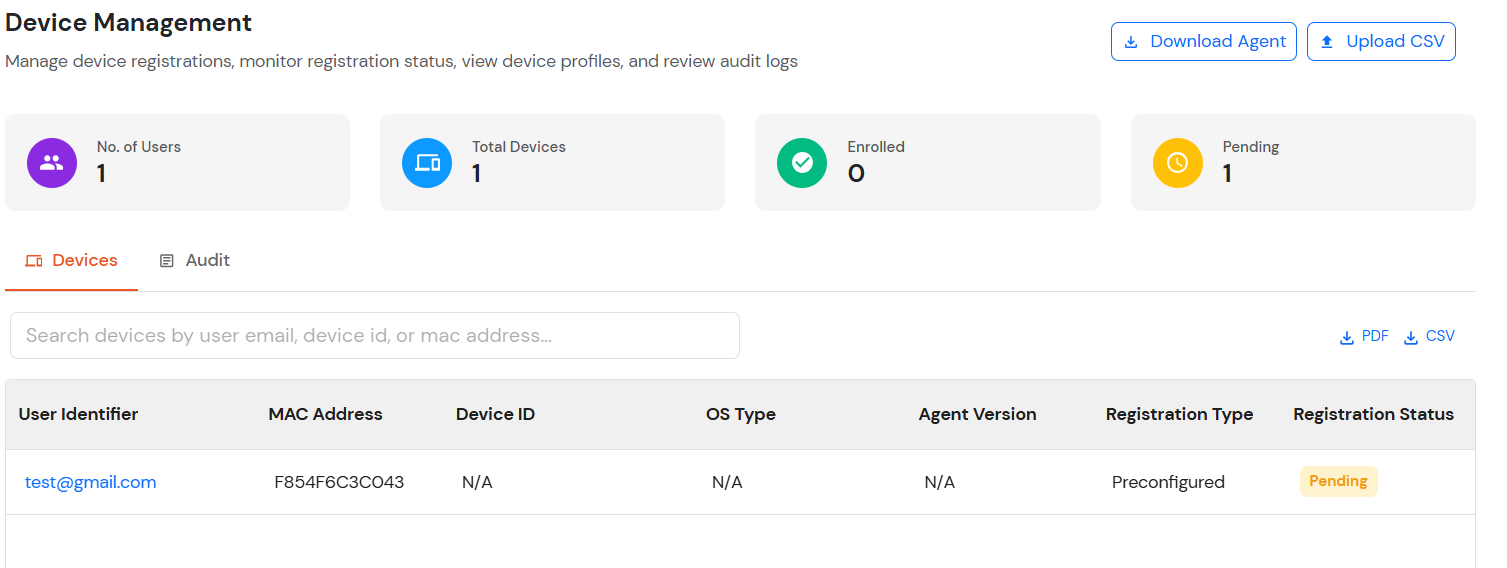
After a user completes the registration flow, their registered devices appear in the Trusted Devices section of the customer admin account.
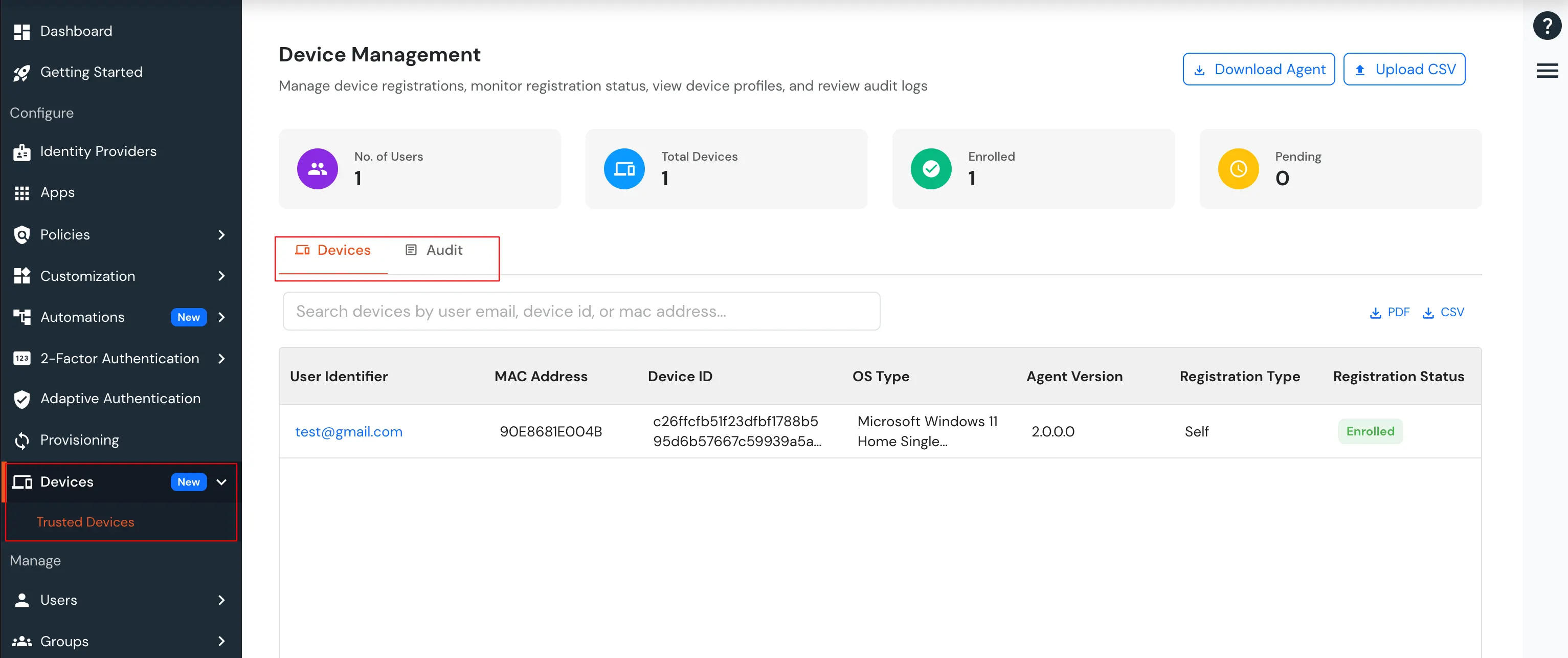
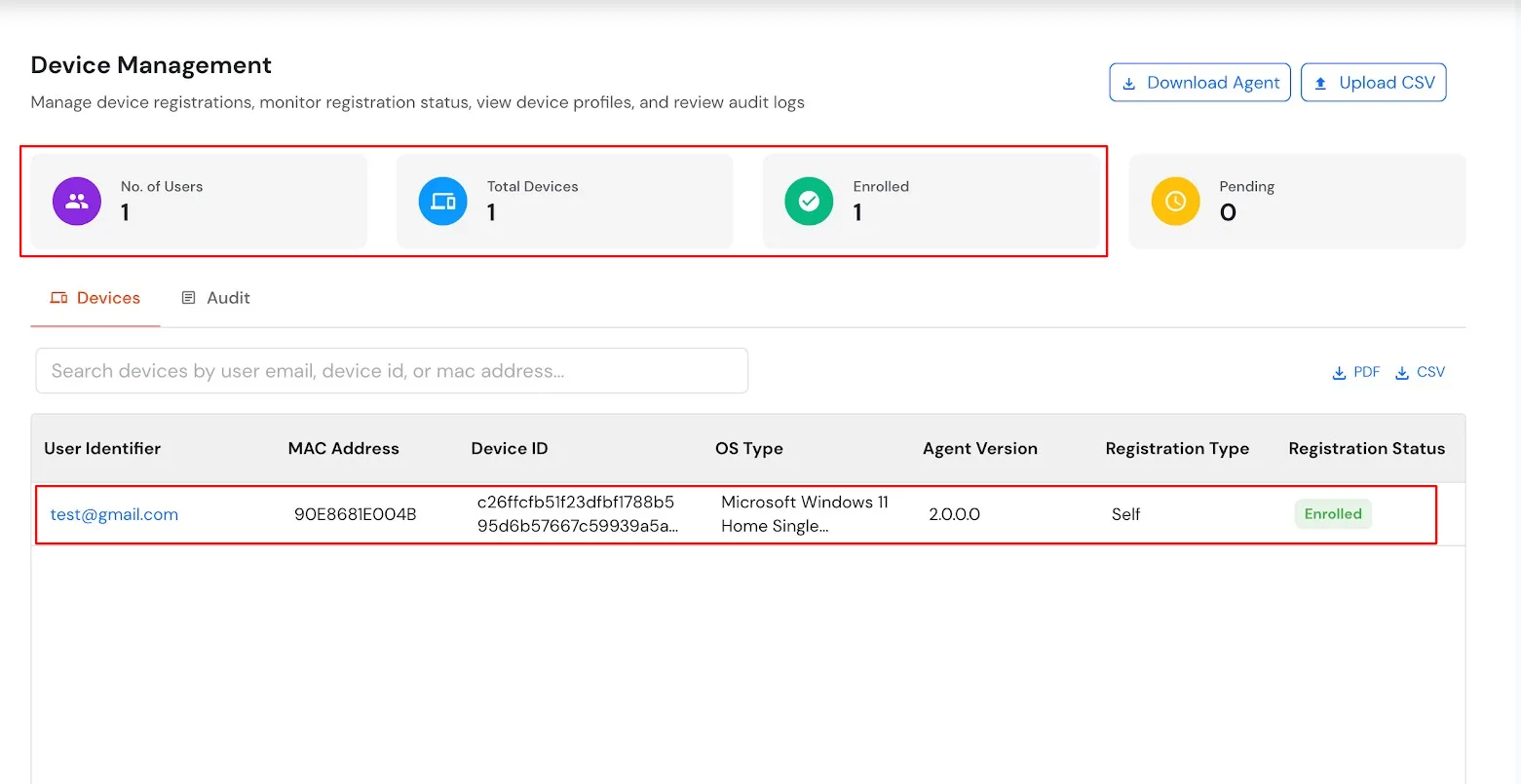
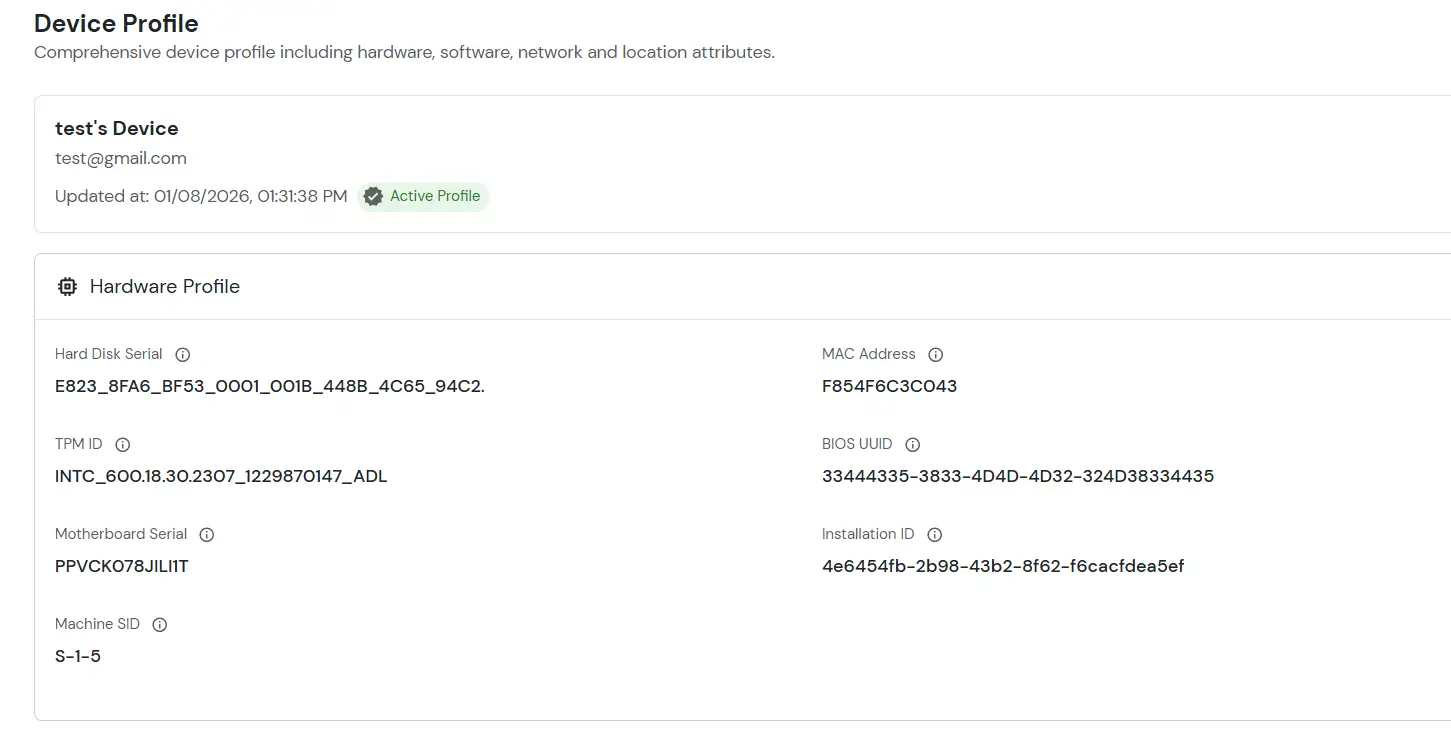
All configured device attributes associated with the selected user are displayed on this page.
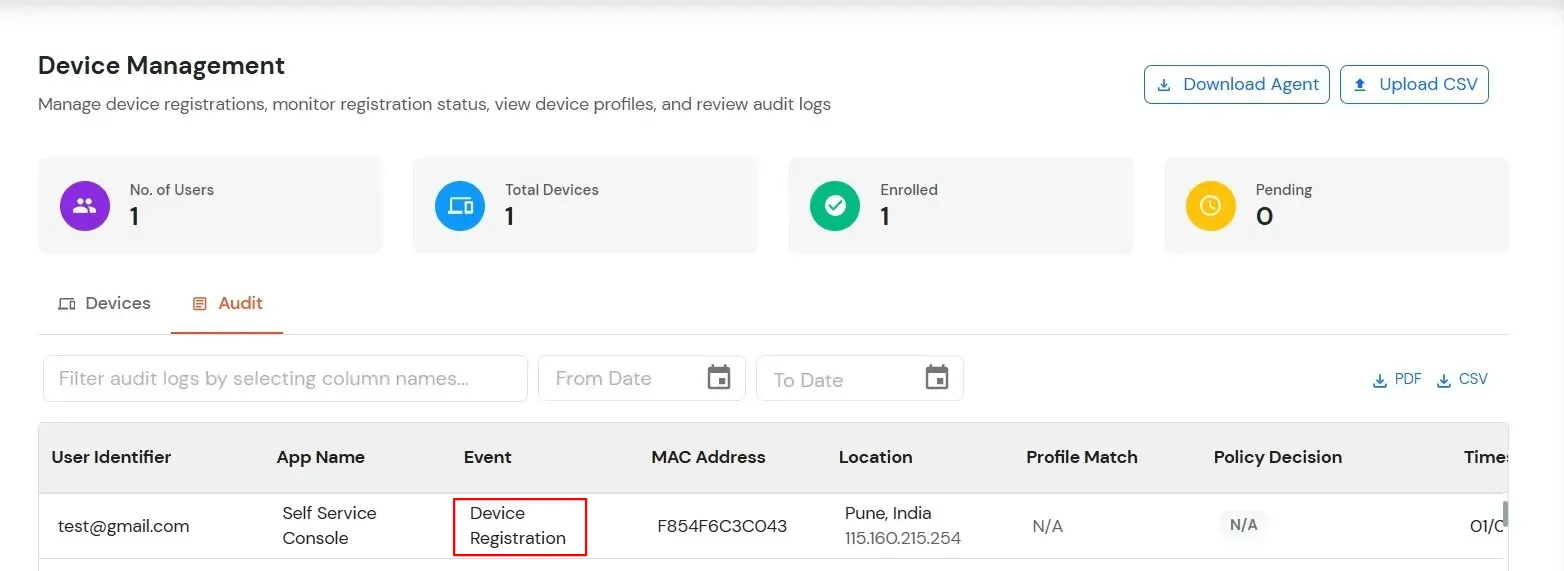
User device audit details are displayed here.
Defines how users are authenticated and what they experience during login.
https://<domain_name>.xecurify.com/moas/login

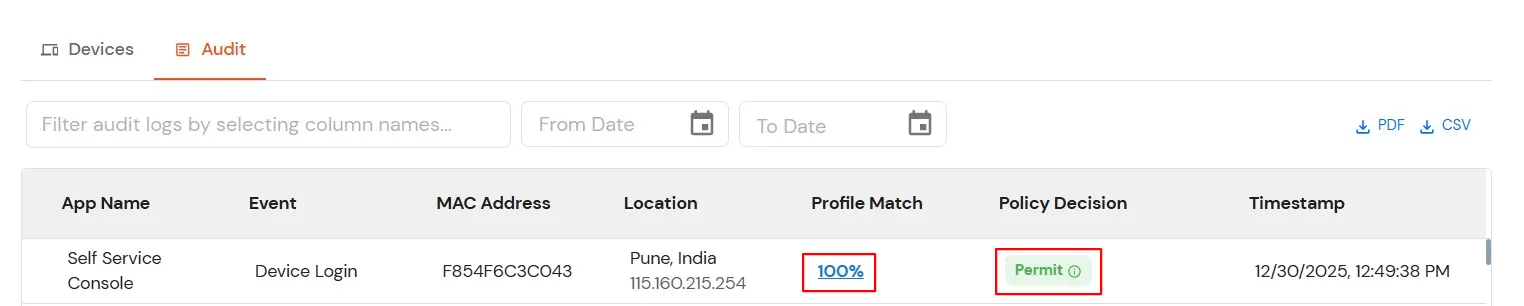
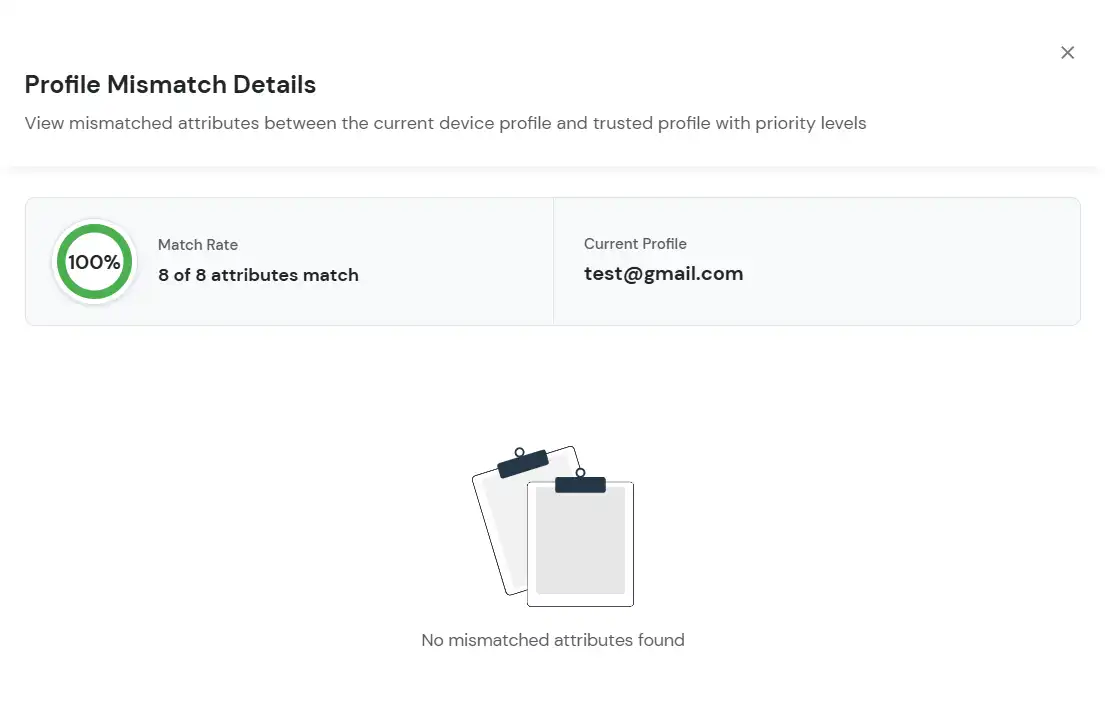
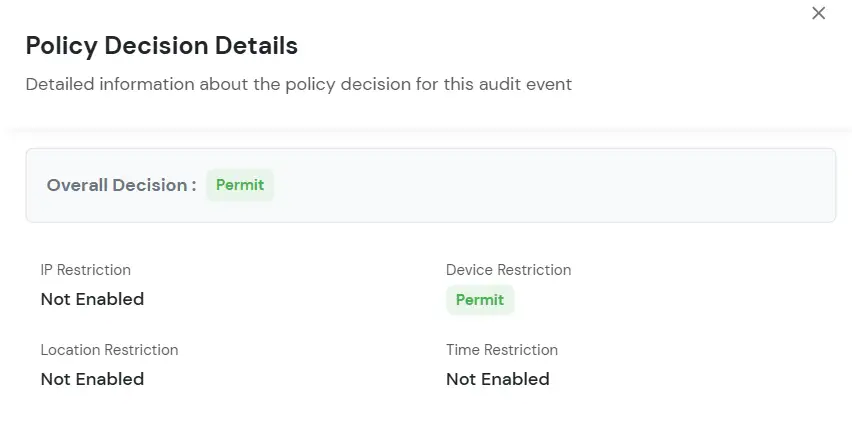
The Risk Engine allows you to evaluate device trustworthiness by analyzing multiple device attributes and calculating a risk score. Based on this score, user access is allowed, challenged, or denied during login and device registration.



The policy will take effect only after it is associated with a specific application login flow.

Applies when a user is registering a device for the first time.
https://<domain_name>.xecurify.com/moas/login

Note:
If Auto-Registration is enabled and Action for Behaviour Change is set to Deny or Challenge, the device is registered automatically after successful challenge.

After a user completes the registration flow, their registered devices appear in the Trusted Devices section of the customer admin account.



Defines how users are authenticated and what they experience during login.
https://<domain_name>.xecurify.com/moas/login




