Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
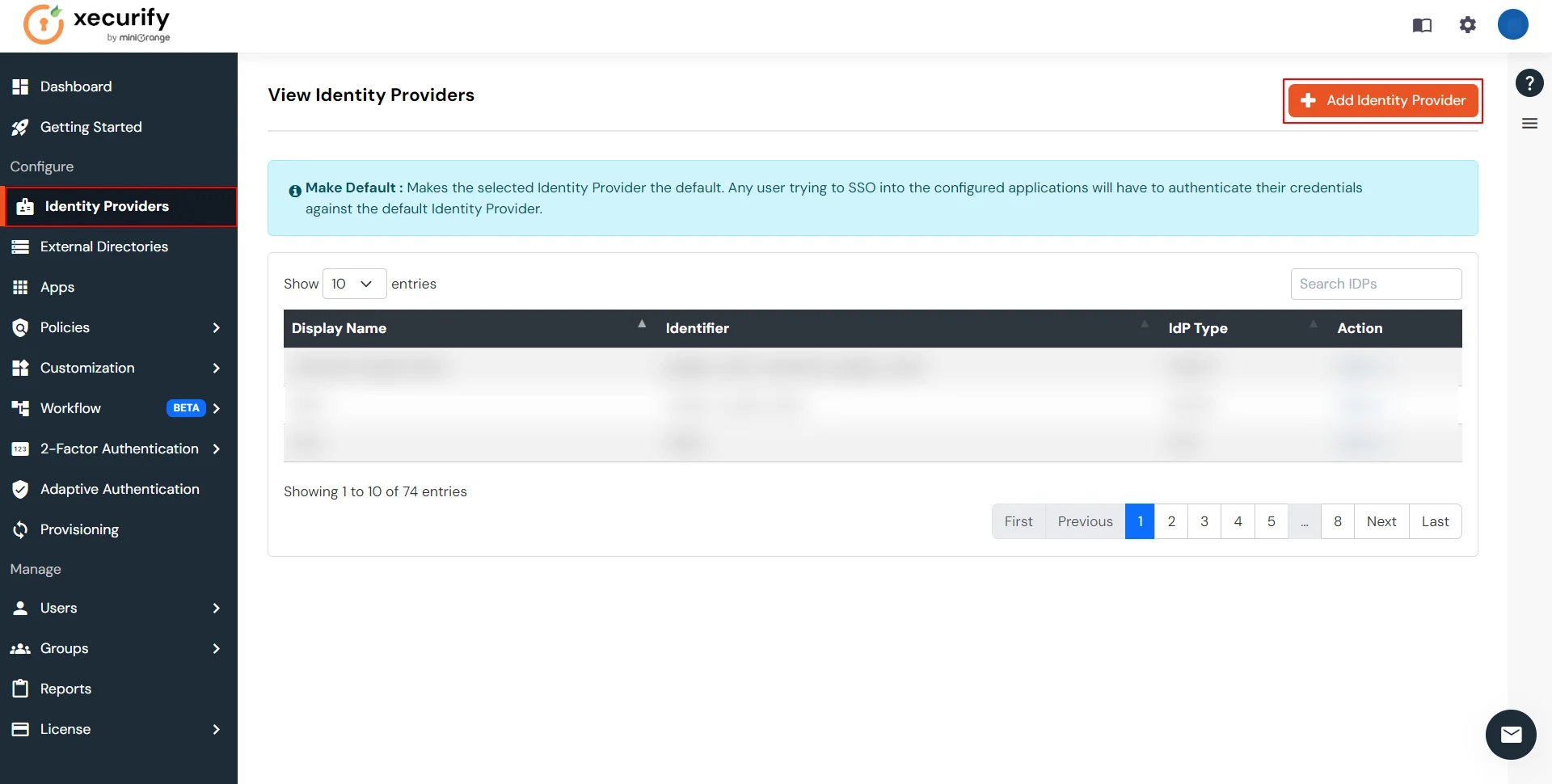
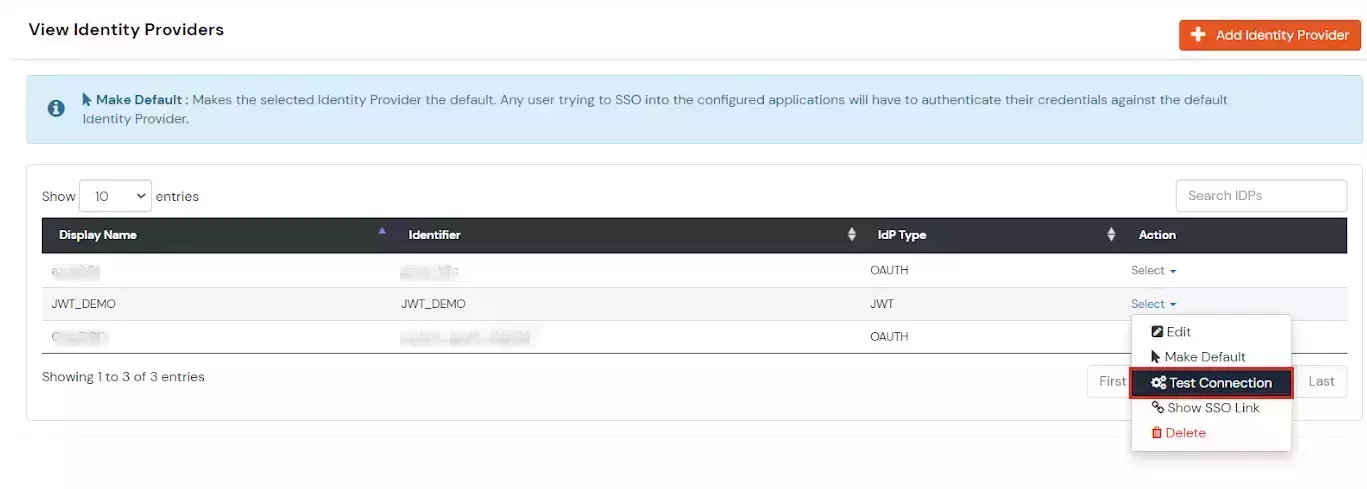
×miniOrange supports Single Sign-On for secure login for users and admins. miniOrange supports several different protocols for your applications, such as SAML, WS-FED, OAuth, OIDC, JWT, RADIUS, etc. Using Single Sign-on, users can use one set of credentials to login to multiple applications. This improves security, as it reduces avenues for phishing attacks, and also improves access to your application.
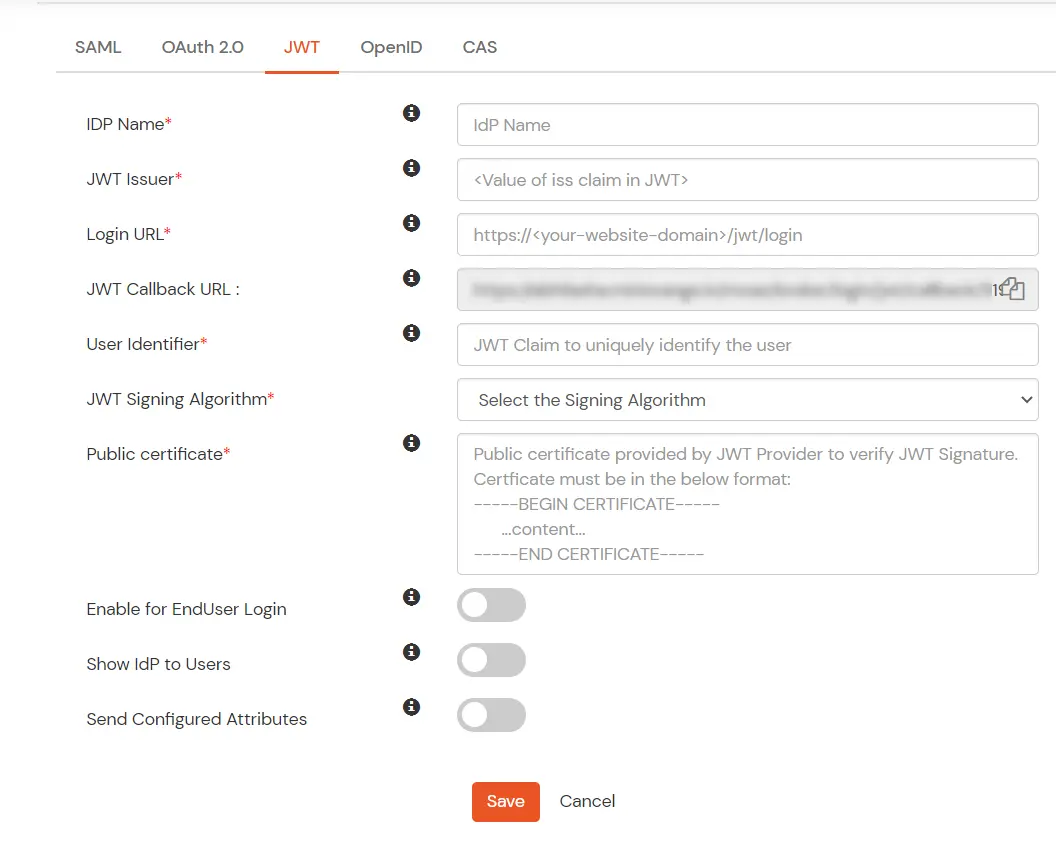
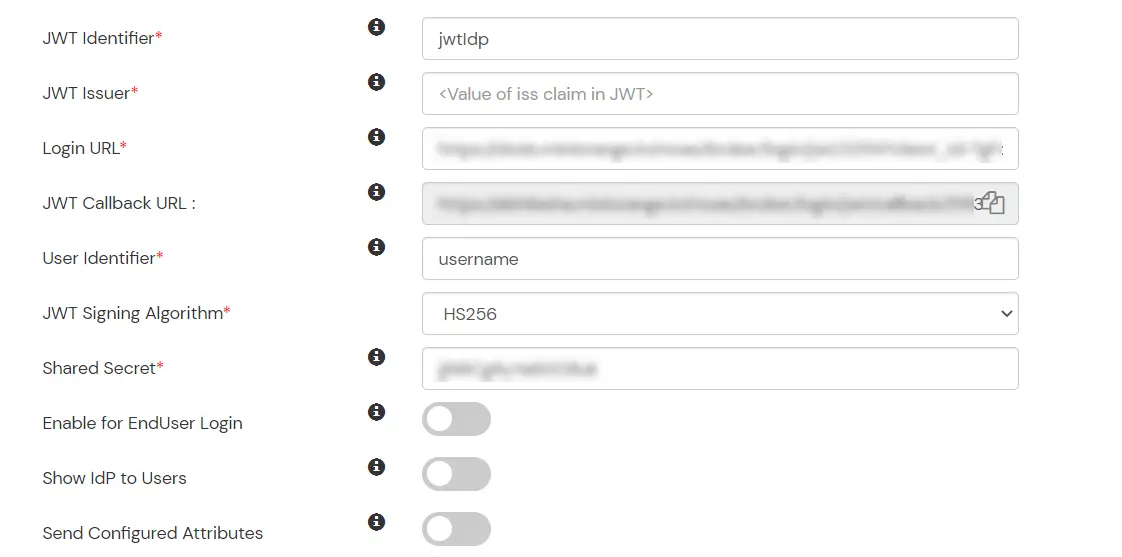
miniOrange provides Single Sign-on for Mobile applications and JavaScript framework based applications through JSON Web Token [so, JWT apps]. This solution allows you to setup Single Sign-On(SSO) into your applications which do not support SAML 2.0 standard. You can allow your users to Single Sign-On into your application by verifying Identity with your existing SAML 2.0 compliant Identity Provider. This is done using JSON Web Token (JWT) tokens and it can be easily integrated with your application built in any framework or language. You can add JWT app to enable SSO in any mobile/client-side apps which do not support any standard protocols and built on platforms like React.js, Firebase, Cordova, Angular.js, etc. You can also add Password-Less app links to user portal from here.
miniOrange offers free help through a consultation call with our System Engineers to Install or Setup JWT SSO solution in your environment with 30-day free trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you in no time.