Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×miniOrange provides ready to use Single Sign-On solution using MariaDB. This solution ensures that you are ready to roll out secure access to any of your application using MariaDB Credentials within minutes.
Various User Stores i.e. CRM/HRM/CMS/LMS where users are stored, do not support Single Sign-On or any other authentication protocol inherently.Here miniOrange MariaDB SSO solution comes into the picture and provides different SSO services to these type of applications.
miniOrange offers free help through a consultation call with our System Engineers to configure SSO for different apps using Azure AD as IDP in your environment with 30-day free trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you in no time.
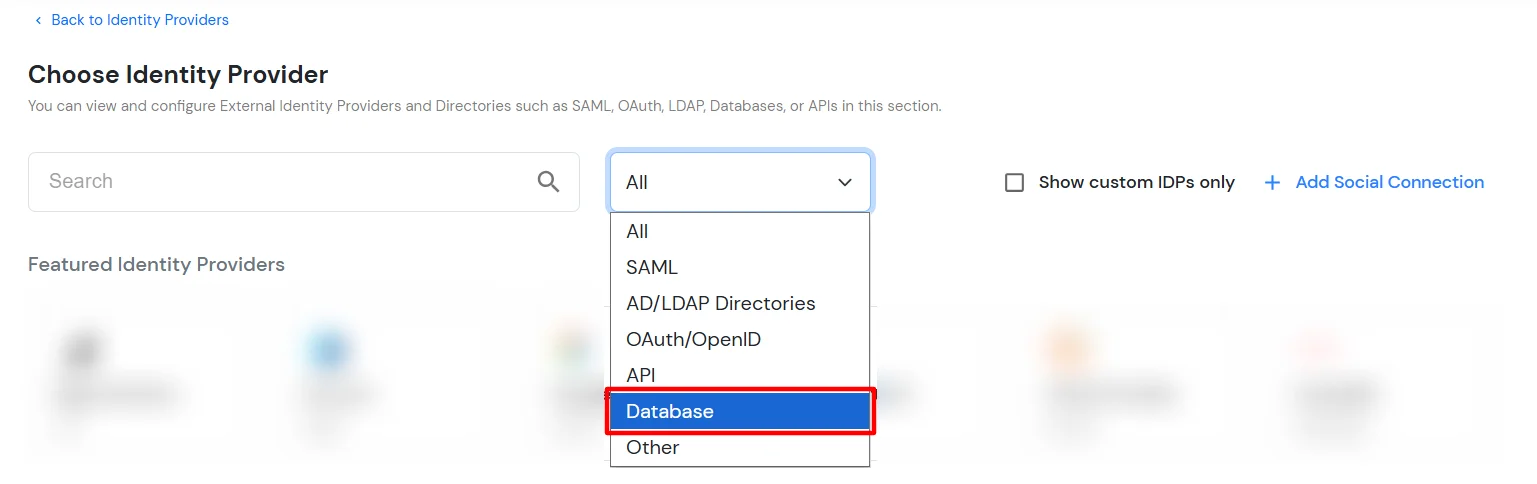
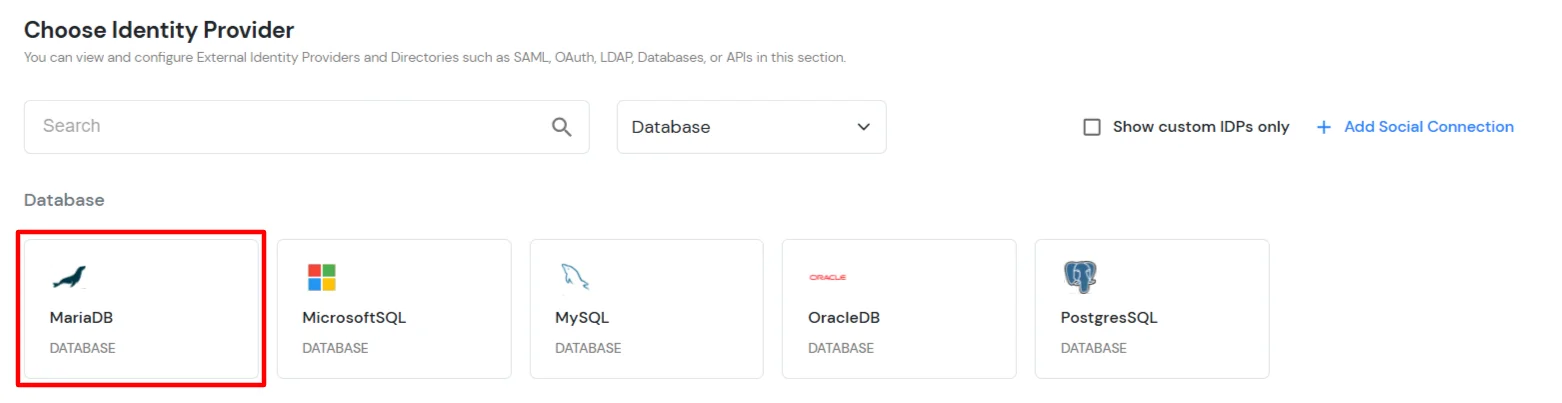
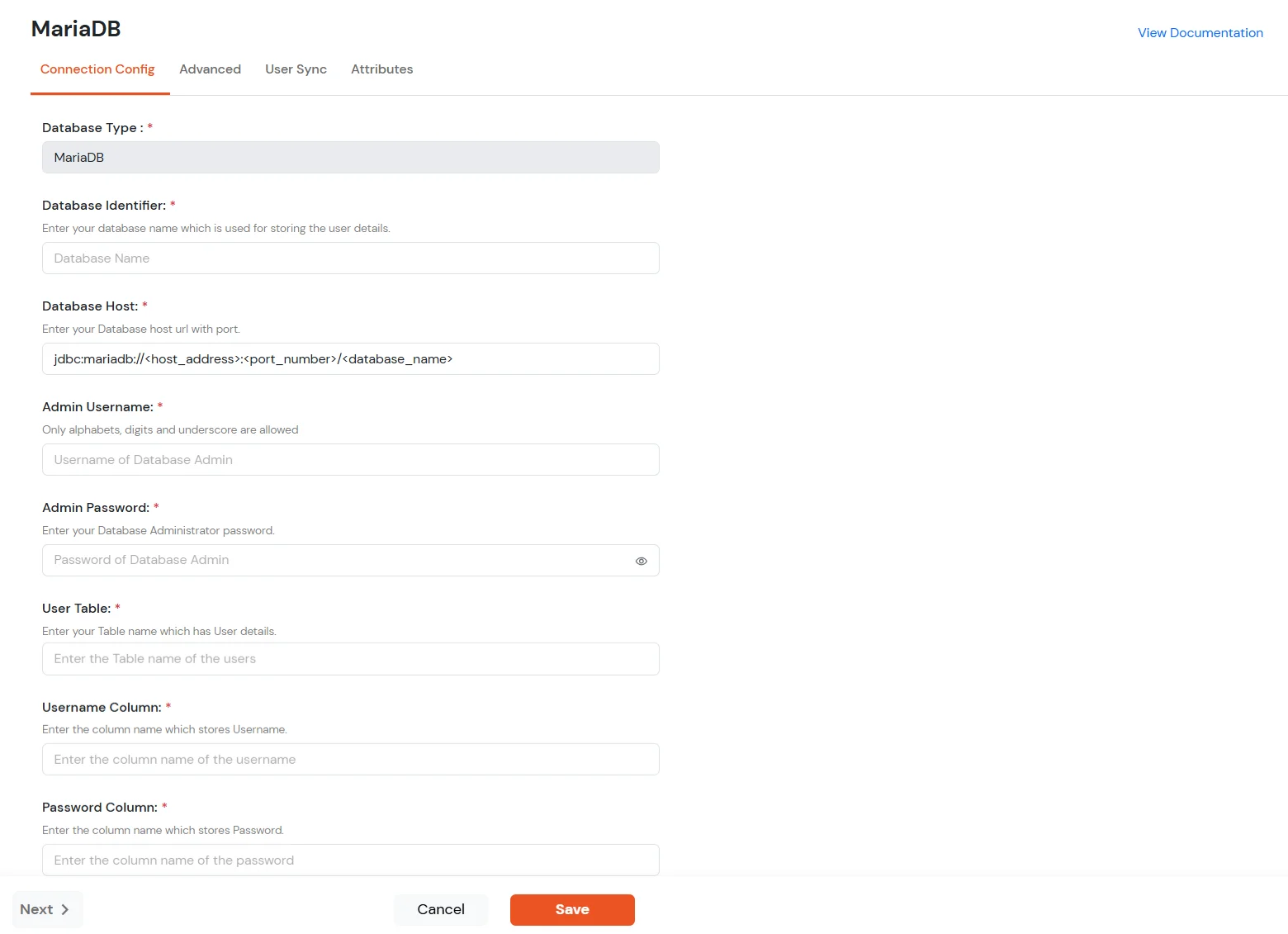
| Field | Description | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| Database Identifier | Enter the Database Identifier—the name of the database you are adding. It can be any name relevant to the User-store. | ||||||||
| Database Host | The following table shows the default values and syntax for the fields on the configuration page.
|
||||||||
| Admin Username | For localhost, the Admin Username is typically 'root'. For a remote host, contact your administrator. | ||||||||
| Admin Password | Enter the Admin Password that corresponds to the Admin Username. | ||||||||
| User Table | The User Table is the database table where users are stored for authentication. For example, in WordPress the User Table is wp_users. | ||||||||
| Username column | The Username column is the column that stores the usernames used for authentication. For example, in WordPress the Username Column is user_login. | ||||||||
| Password column | The Password column is the column that stores the users' passwords. For example, in WordPress the Password Column is user_pass. |
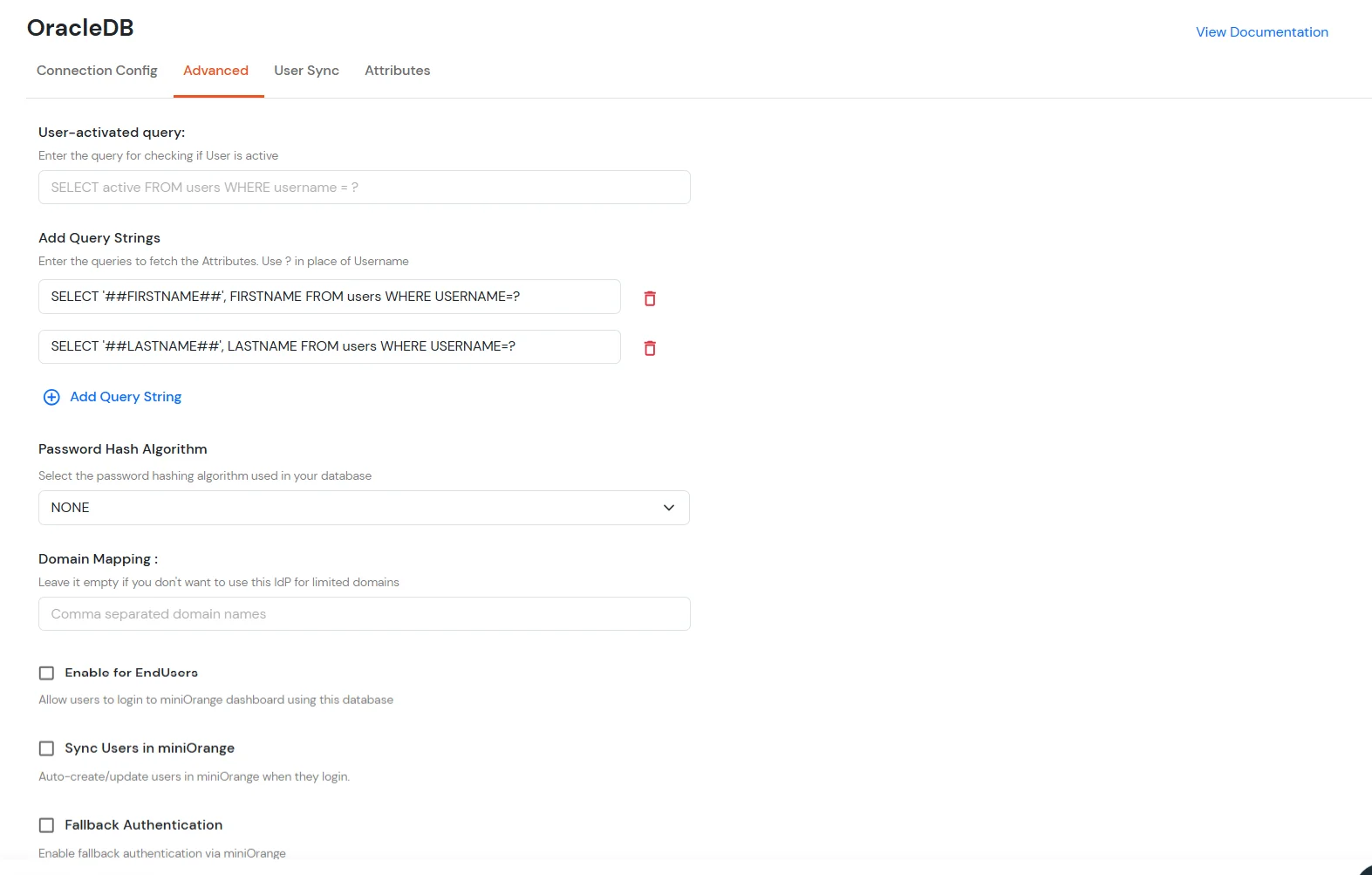
| User-activated query | In which you can enter the query for checking if the User is Active or not. Example: |
| Add Query Strings | Add the query strings for the columns you want to import from the database. This can be useful for attribute mapping: Example: |
| Password Hash Algorithm | The Hashing type which is used for MariaDB is, PHPASS. |
| Domain Mapping | Enter comma-separated domain names to restrict this IdP to specific domains. To allow all domains, leave it empty. |
| Enable for EndUsers | Enable this option, if you want your endusers to log in to their corresponding End-User Dashboard using IDP Credentials. |
| Sync Users in miniOrange | Users will be created/updated in miniOrange when logging into the End User dashboard. Only applies when 'Enable for End Users' is enabled. |
| Fallback Authentication | If you enable this option, then the users present in an external database will be authenticated directly through the miniOrange IdP, without being created in the miniOrange IdP. It is helpful in case when the database from where the authentication is being performed contains some private or sensitive information about users. |
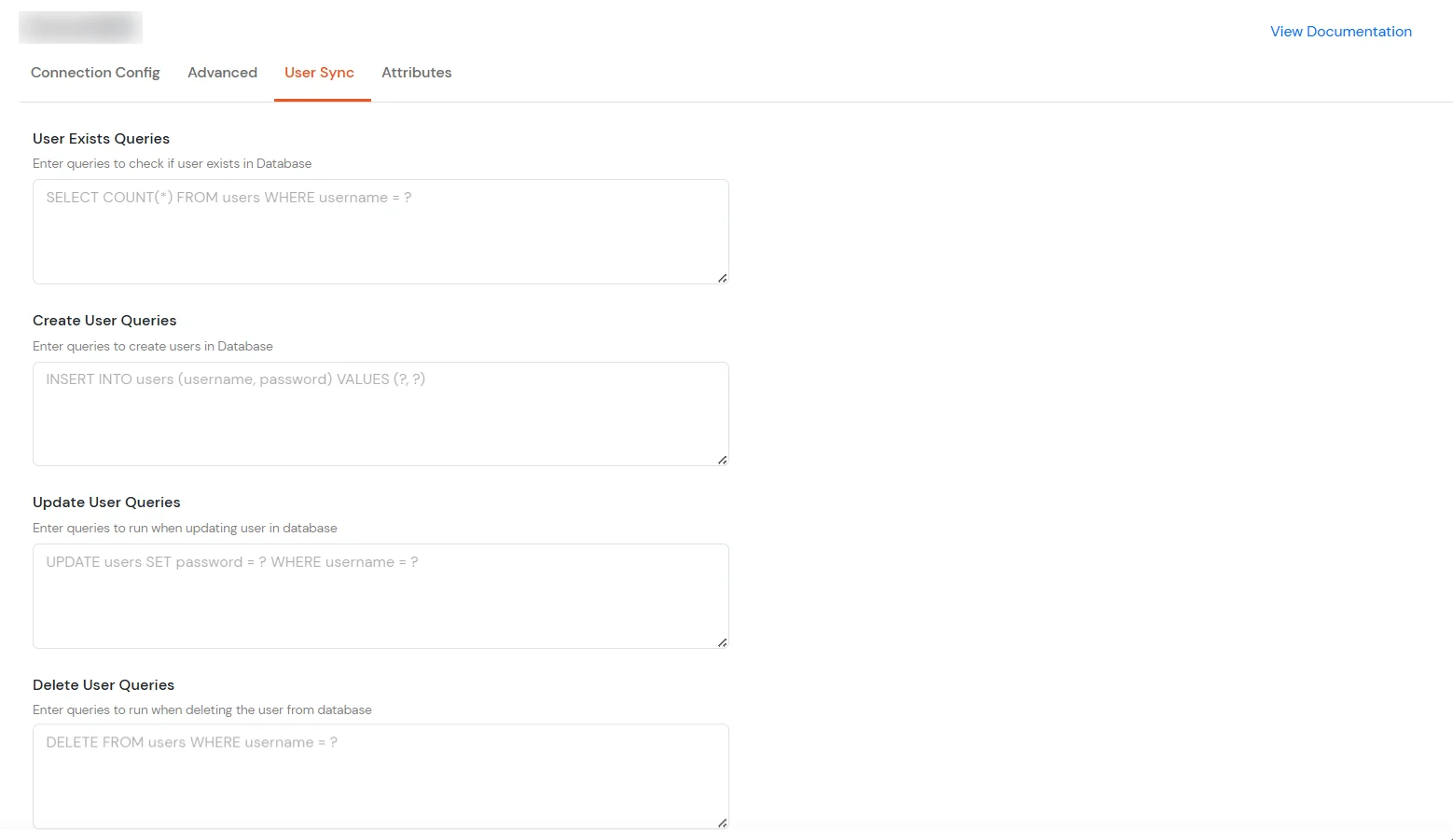
| User Exists Queries | Enter the SQL query to check if a user exists in the database. Example: |
| Create User Queries | Enter the SQL query to create a new user in the database. Example: |
| Update User Queries | Enter the SQL query to update user information in the database. Example: |
| Delete User Queries | Enter the SQL query to delete a user from the database. Example: |
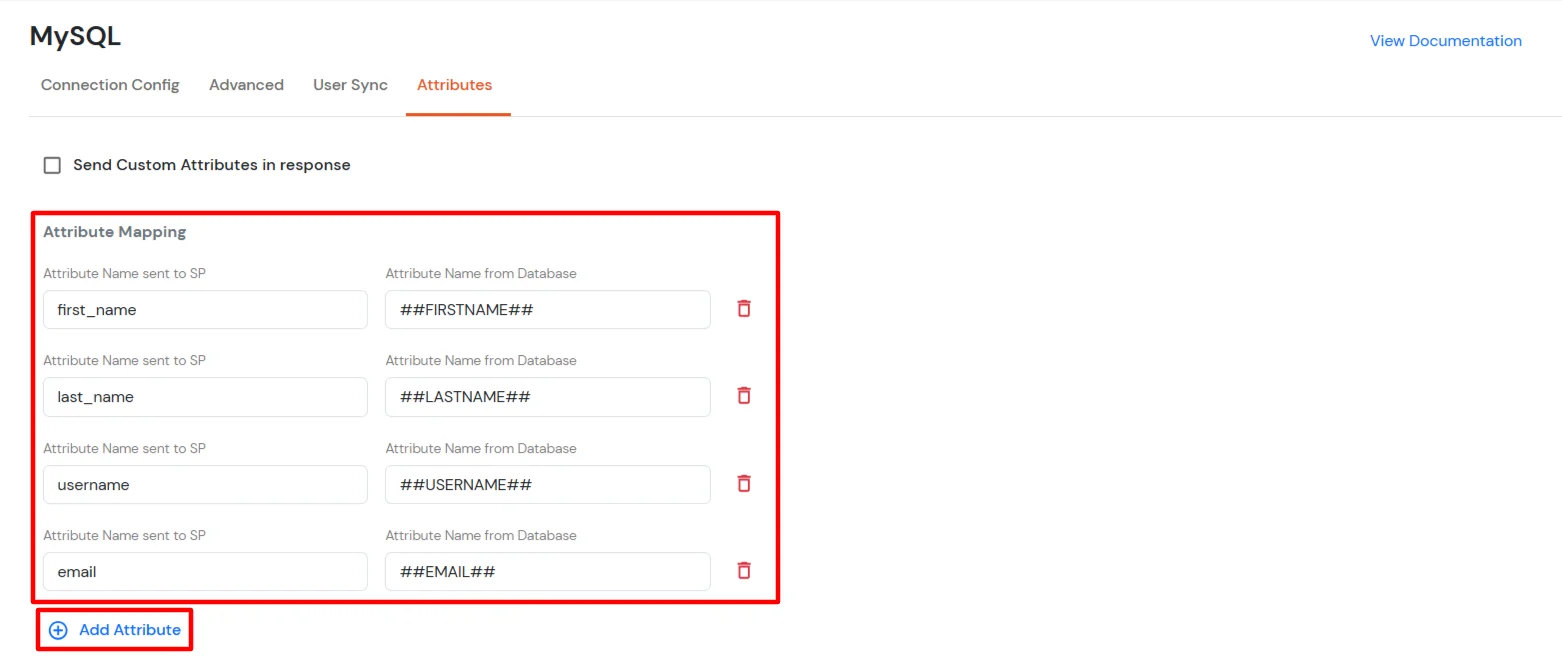
Note: Add a query string for each attribute you want to fetch from the database.
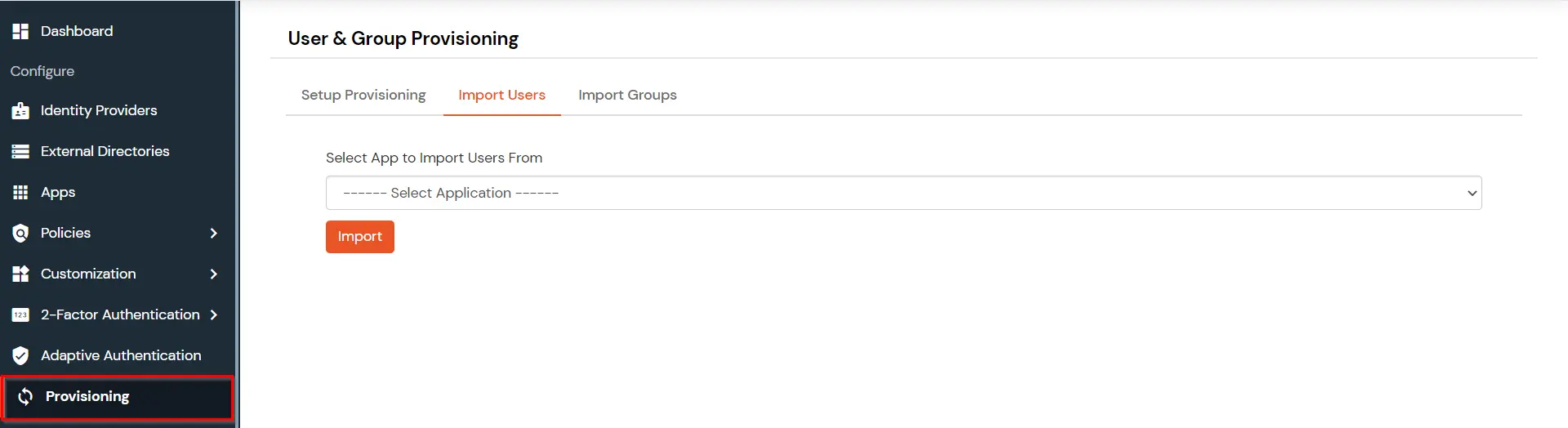
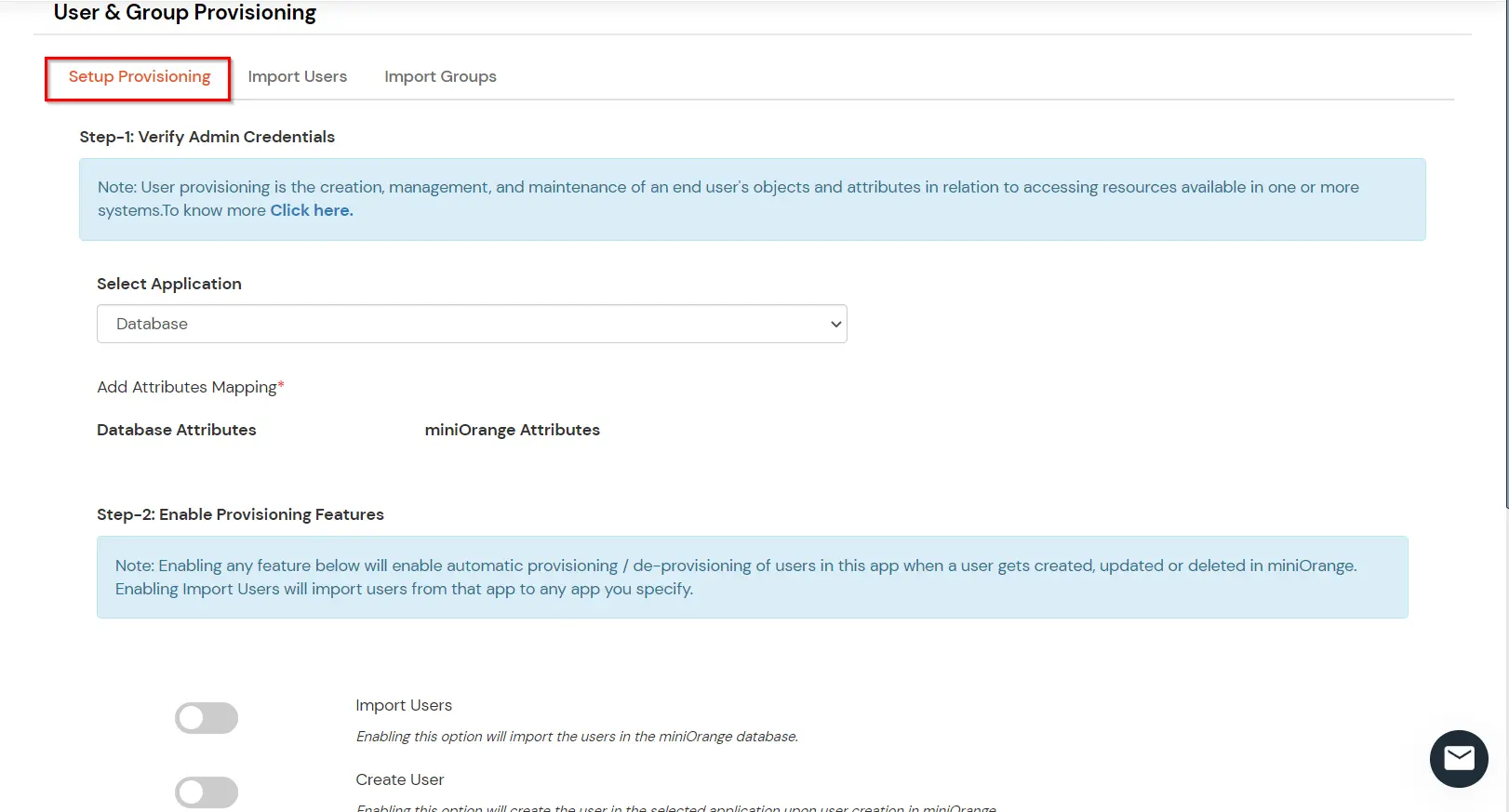
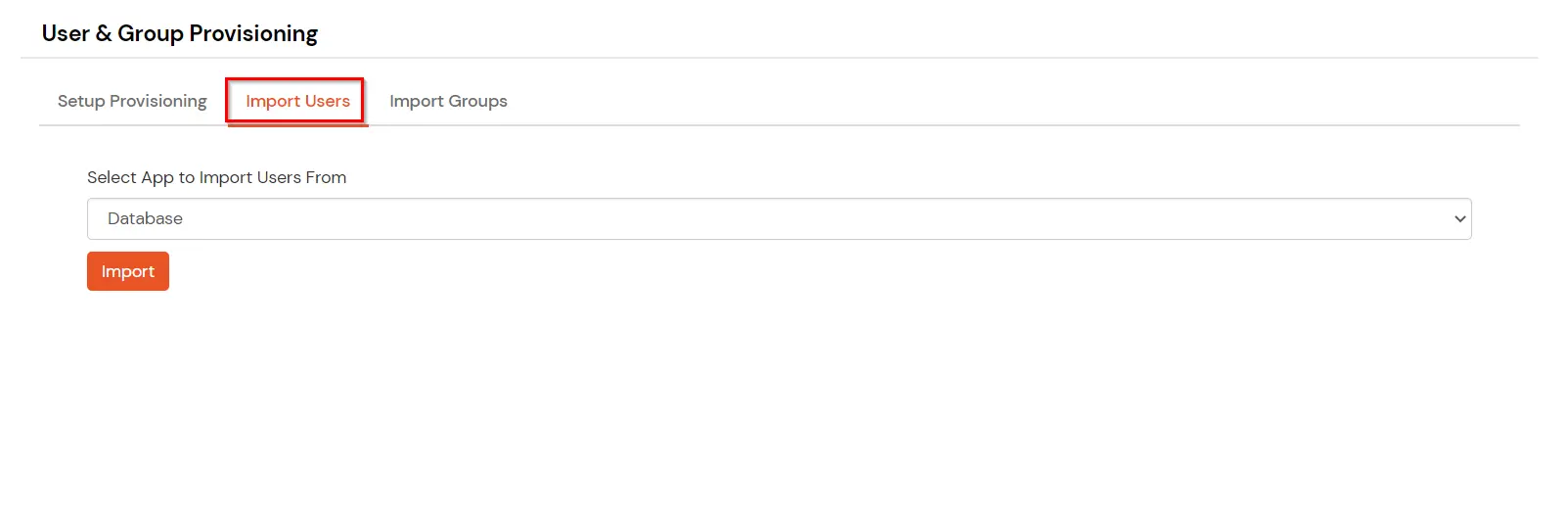
If you have already configured your application in miniOrange you can skip the following steps.
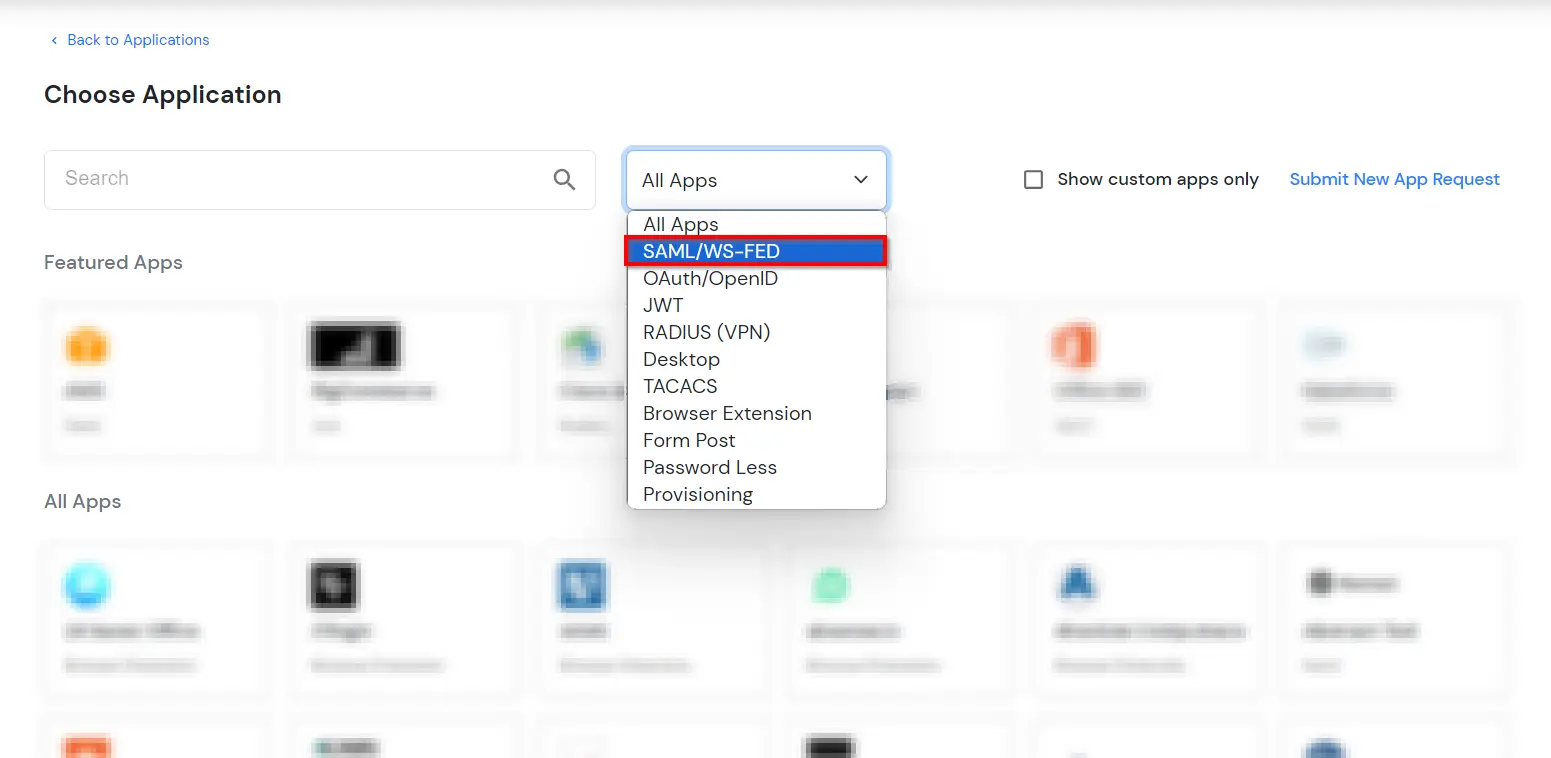
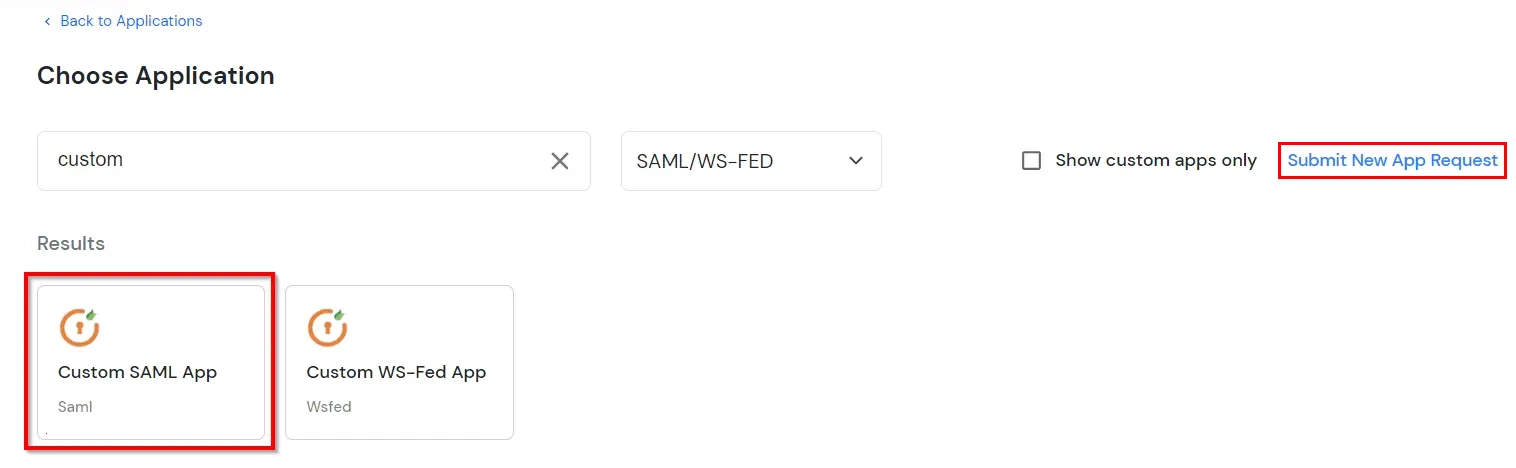
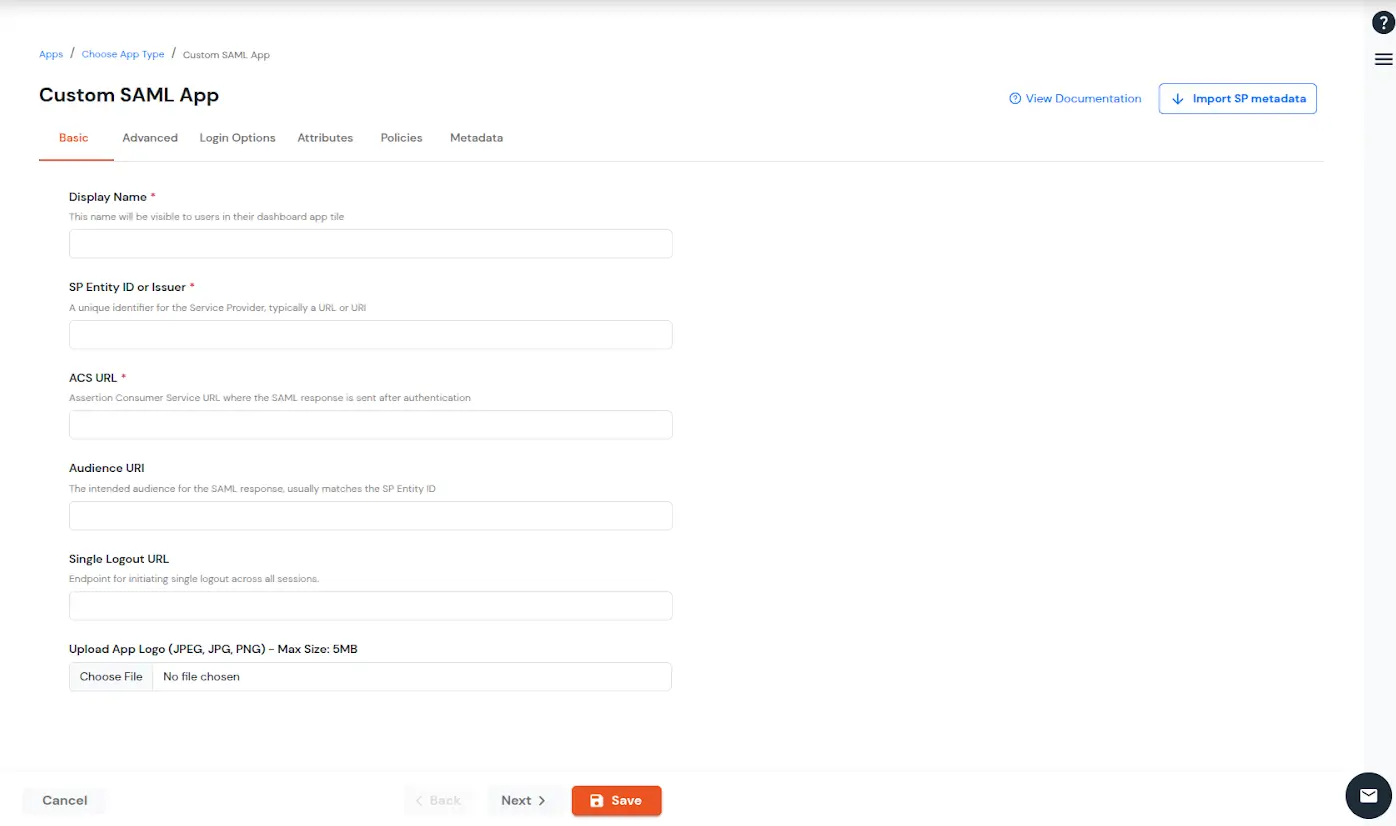
| Display Name (required) | Enter the Display name for your app as per your preference. |
| SP Entity ID or Issuer (required) | Is used to identify your app against the SAML request received from SP. The SP Entity ID or Issuer can be in either URL or in String format. |
| ACS URL or Assertion Consumer Service URL (required) | Defines where the SAML Assertion should be sent after authentication. Make sure the ACS URL is in the format: https://www.domain-name.com/a/[domain_name]/acs |
| Audience URL | As the name suggests, specifies the valid audience for SAML Assertion. It is usually the same as SP Entity ID. If Audience URL is not specified separately by SP, leave it blank. |
| Single Logout URL | The URL where you want the logout request to be consumed and where your users should be redirected after single logout from the applications. |
| Upload App Logo | Upload a logo for your application. |
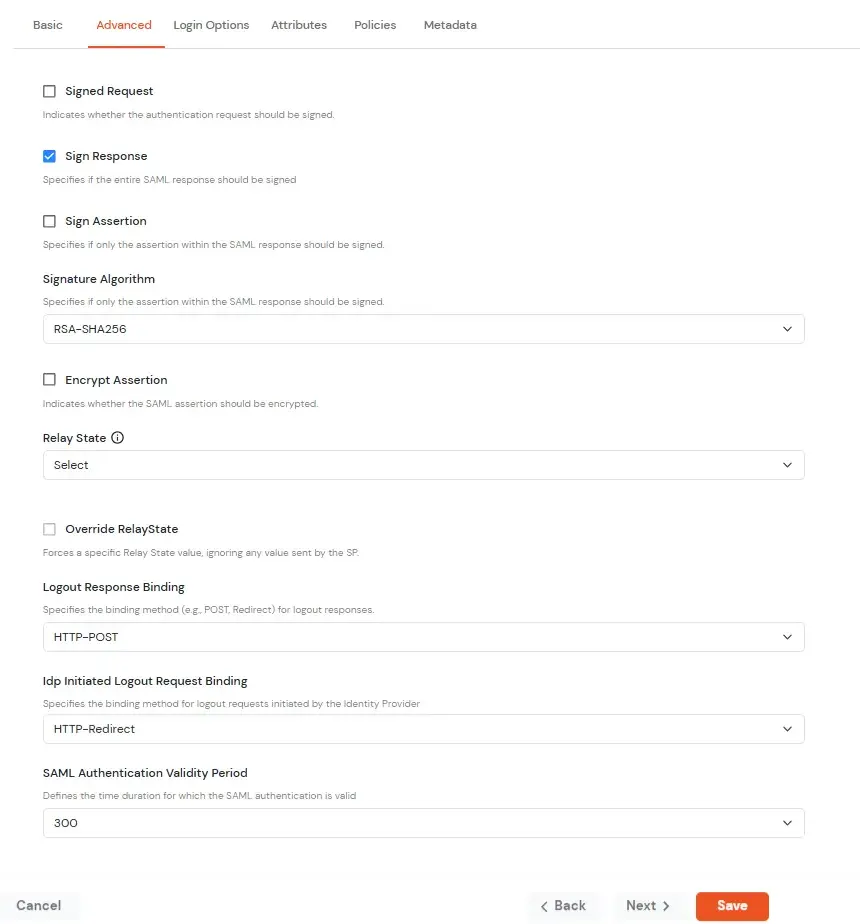
| Signed Request | Enable this to sign the saml request sent by SP. Provide the X509 certificate or upload the certificate. |
| Sign Response | Enable this if you want the entire SAML response to be signed. |
| Sign Assertion | Enable this if you want only the assertion within the SAML response should be signed. |
| Signature Algorithm | Select the algorithm that will be used to sign the SAML request/response. |
| Encrypt Assertion | Select this if you want to encrypt the assertion in SAML response and provide the algorithm and certificate for encryption. |
| Relay State | Enter the URL where you want the user to redirect after sign in to the application. |
| Override Relay state | Enable this to override the default relay state of the SP. |
| Logout Response Binding | A Logout Response is sent in reply to a Logout Request from SP. It could be sent by an Identity Provider or Service Provider. |
| IdP initiated Logout Request Binding: | A Logout Response is sent in reply to a Logout Request from the IdP dashboard. It could be sent by an Identity Provider or Service Provider.
|
| SAML Authentication Validity Period | The time for which the authentication should be considered valid and the user should be able to perform SSO. After that, the user will have to sign in again. |
| Enable Shared Identity | This feature lets you control whether a specific application can be accessed by shared user or not. |
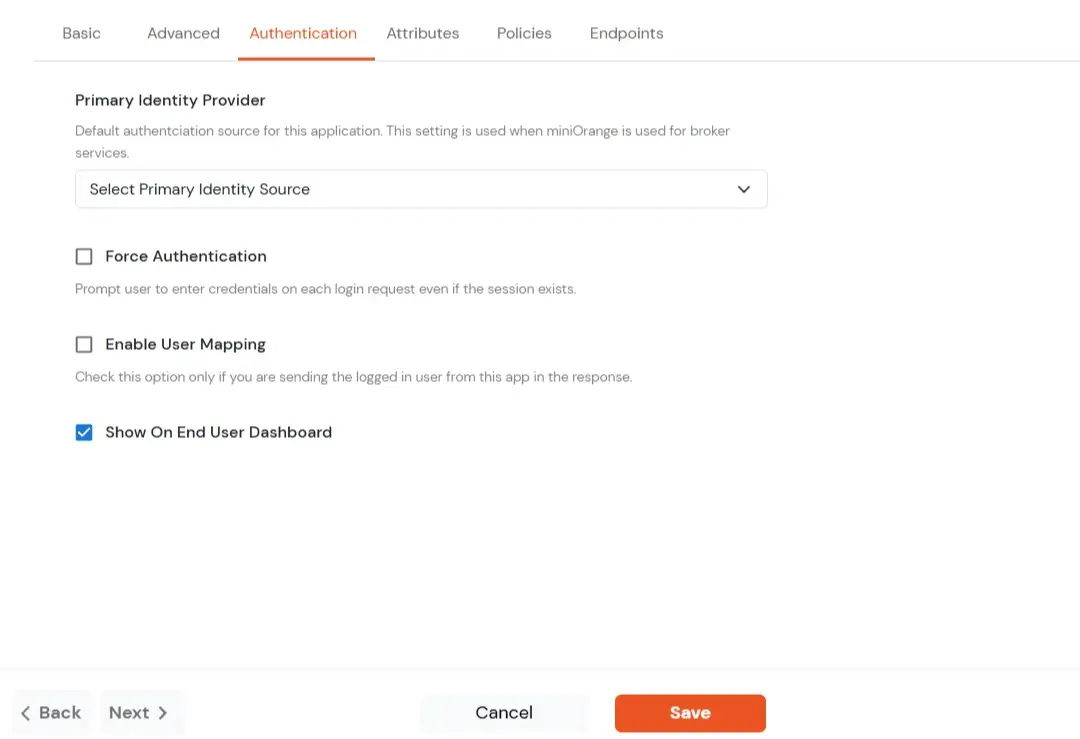
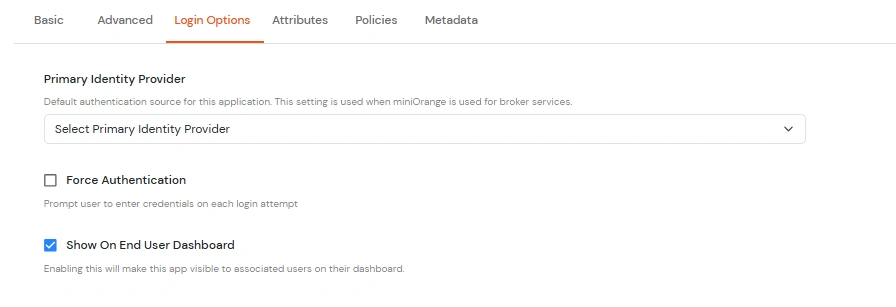
| Primary Identity Provider | Select the identity source from where you want the authentication to happen. You will see the list of all configured sources. |
| Force Authentication | Enable this to enforce authentication on each request to access the application. |
| Show On End User Dashboard | Disable this if you do not want the app to be visible for all users on end user dashboard. |
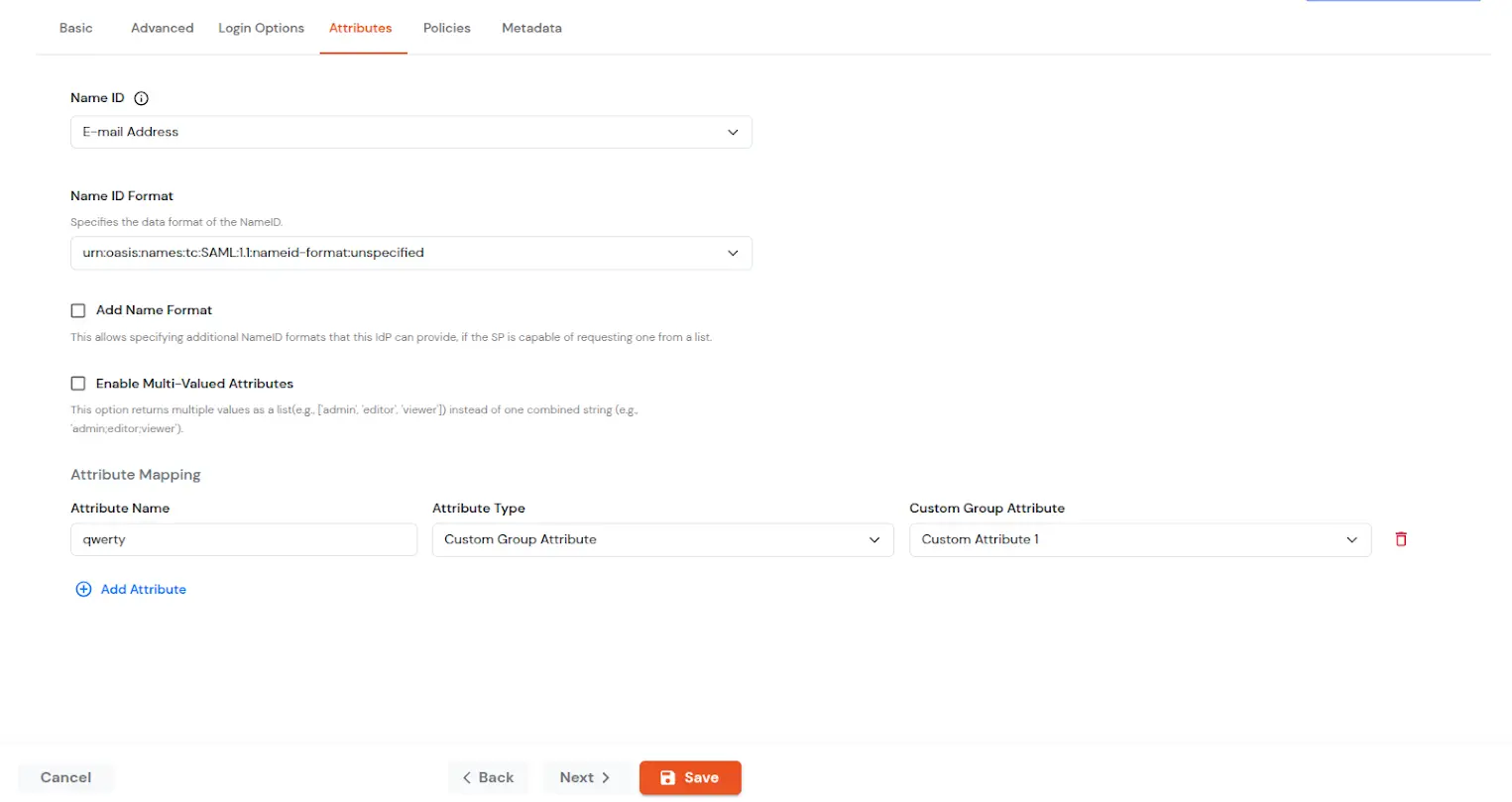
| NameID | NameID is the unique identifier for the authenticated user included in the SAML assertion. It allows the Service Provider to recognize and map the user to an account. Generally, NameID is a username or Email Address. |
| NameID Format | Defines what type of identifier is used in the NameID (e.g., email, persistent, transient) so the SP can correctly map the user. If the SP does not request a specific format, the IdP can leave it unspecified and use a default. |
| Add Name Format | Name Format defines how attribute names are represented in a SAML assertion (e.g., as simple strings or URIs). It helps the SP correctly interpret attribute naming and ensures consistency between IdP and SP. |
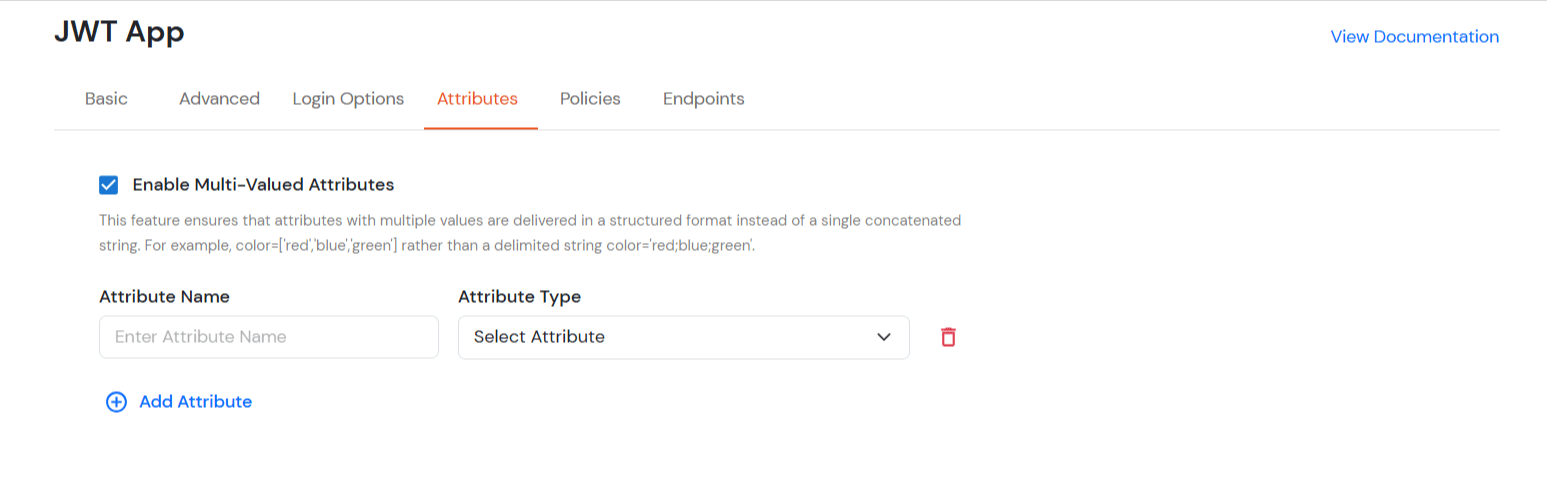
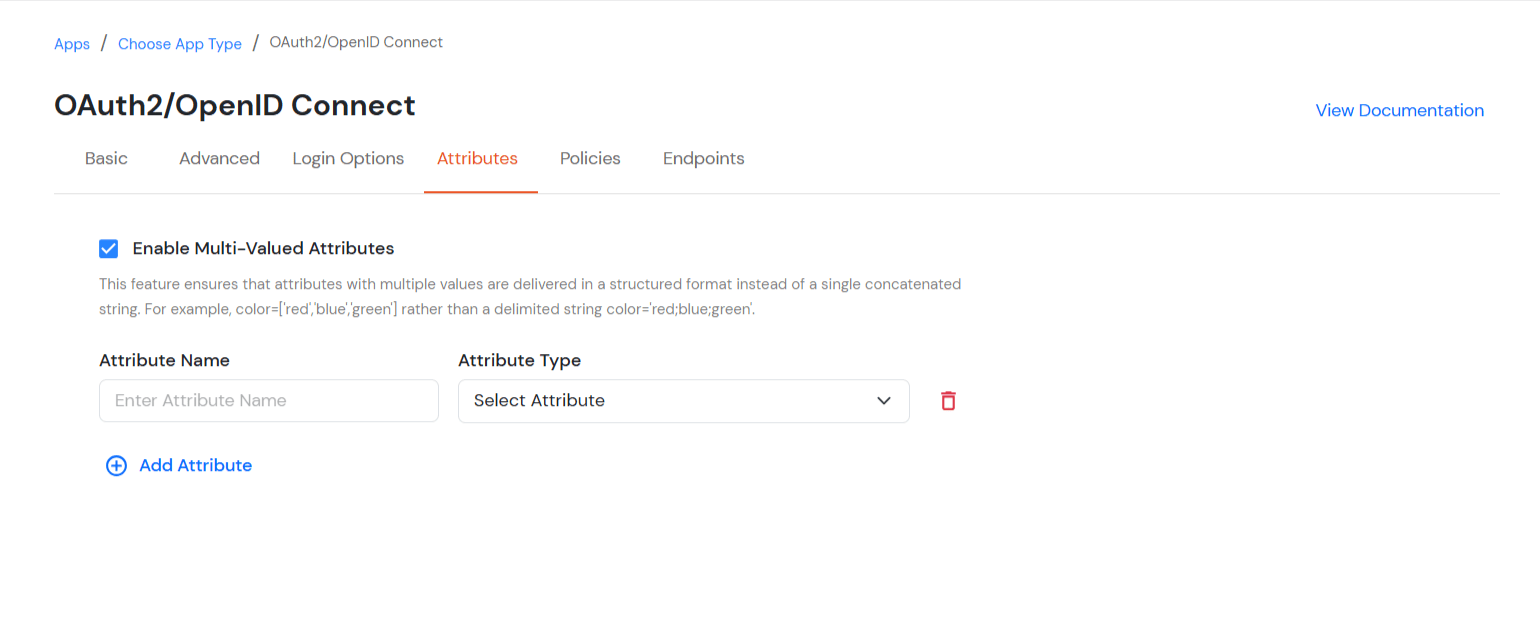
| Enable Multi-Valued Attributes | Enabled:Commas (,) and semicolons (;) are treated as separators, so the attribute is split into a clean list. Example: roles = ['admin', 'editor', 'viewer']. Disabled:Commas and semicolons are not treated as separators, so the attribute stays as one combined string. Example: roles = "admin;editor;viewer". |
| Attribute Mapping | You can Add Attributes to be sent in SAML Assertion to SP. The attributes include user’s profile attributes such as first name, last name, full name, username, email, custom profile attributes, and user groups, etc. |
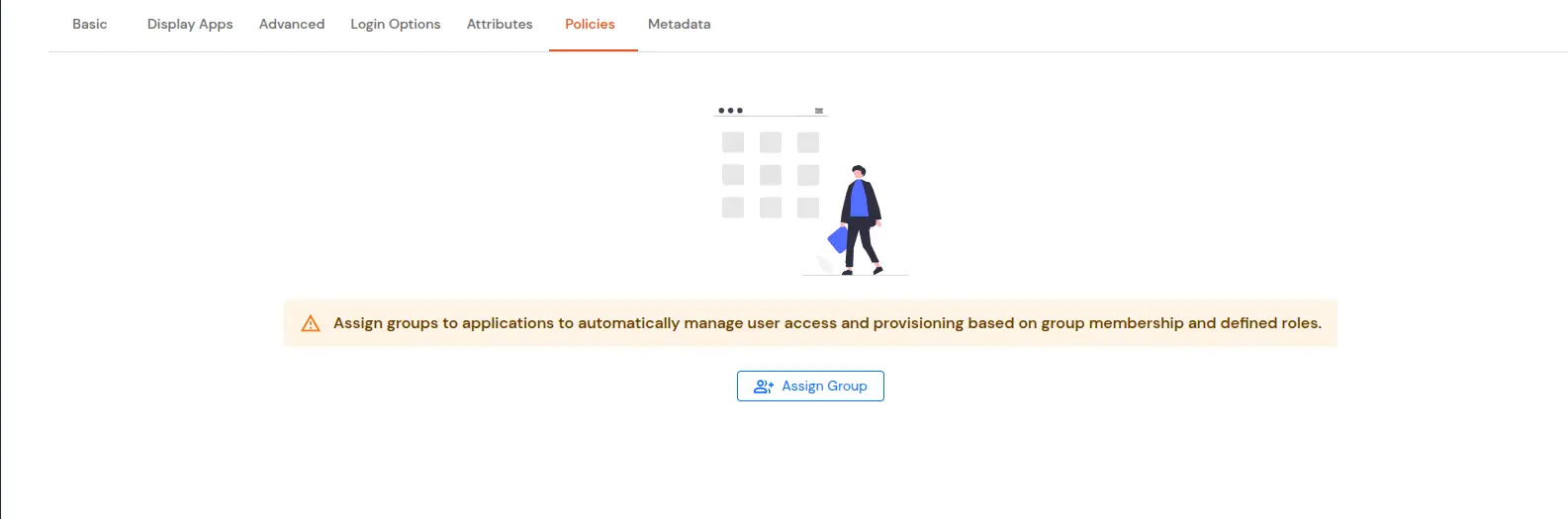
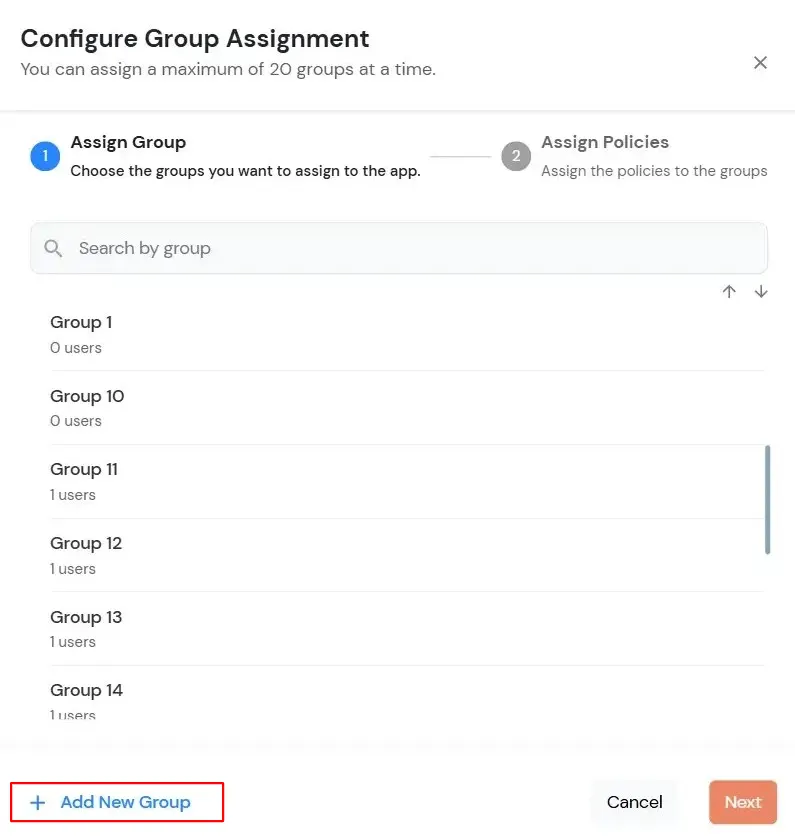
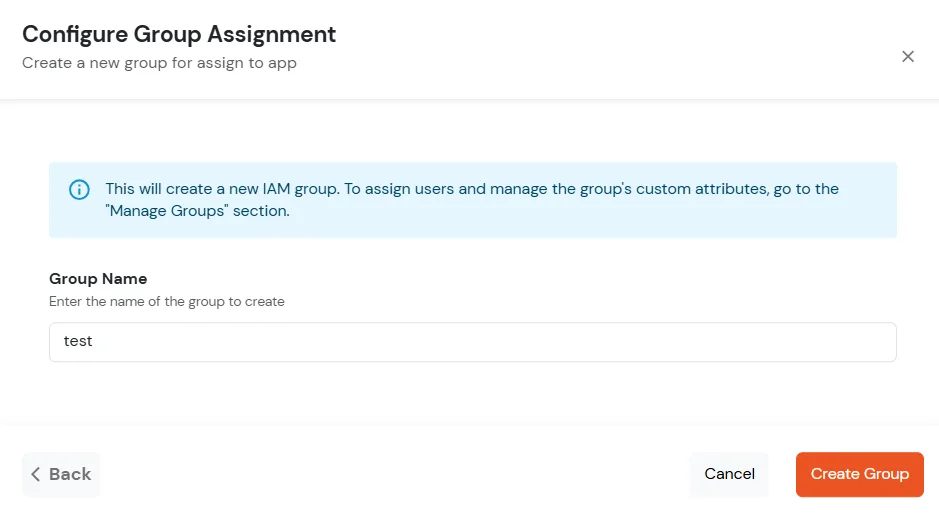
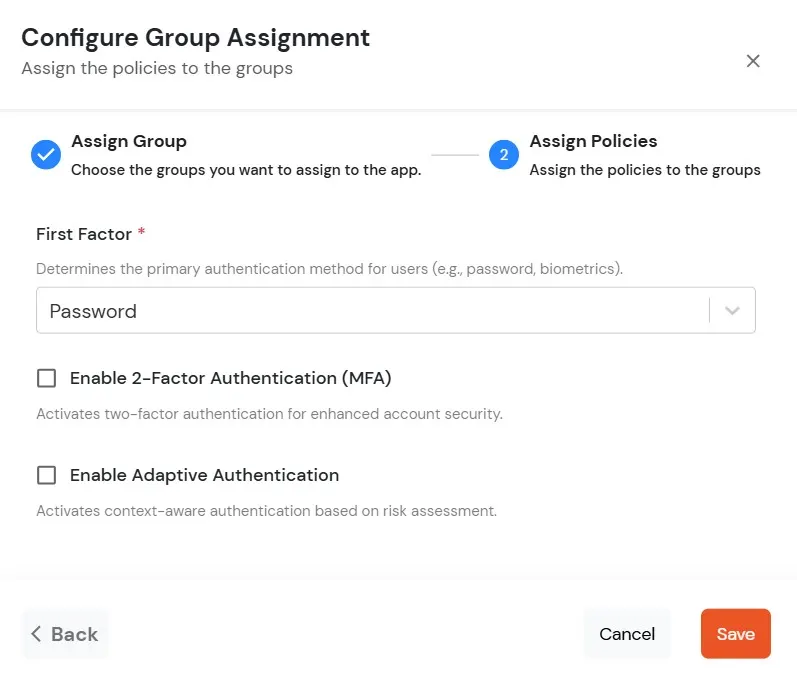
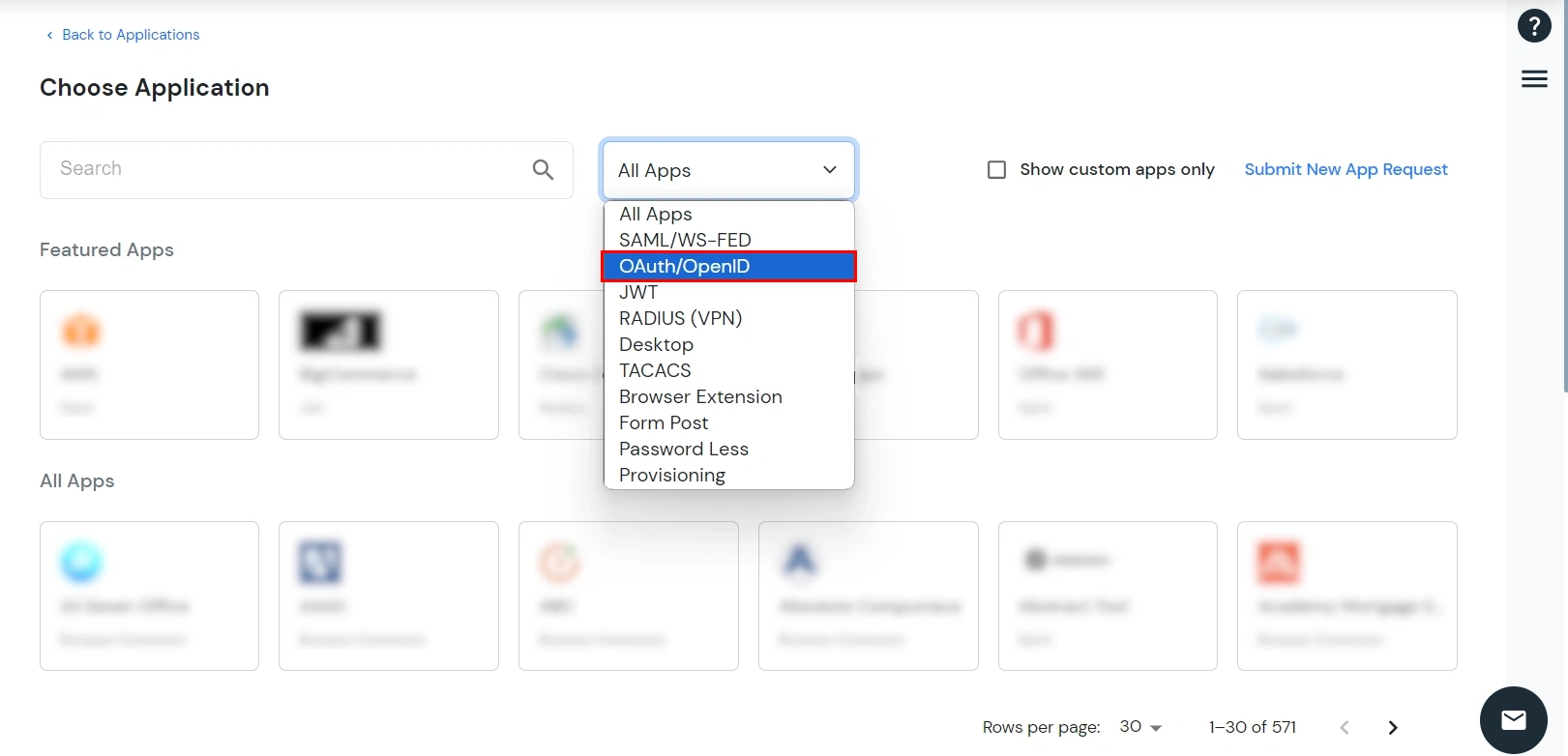
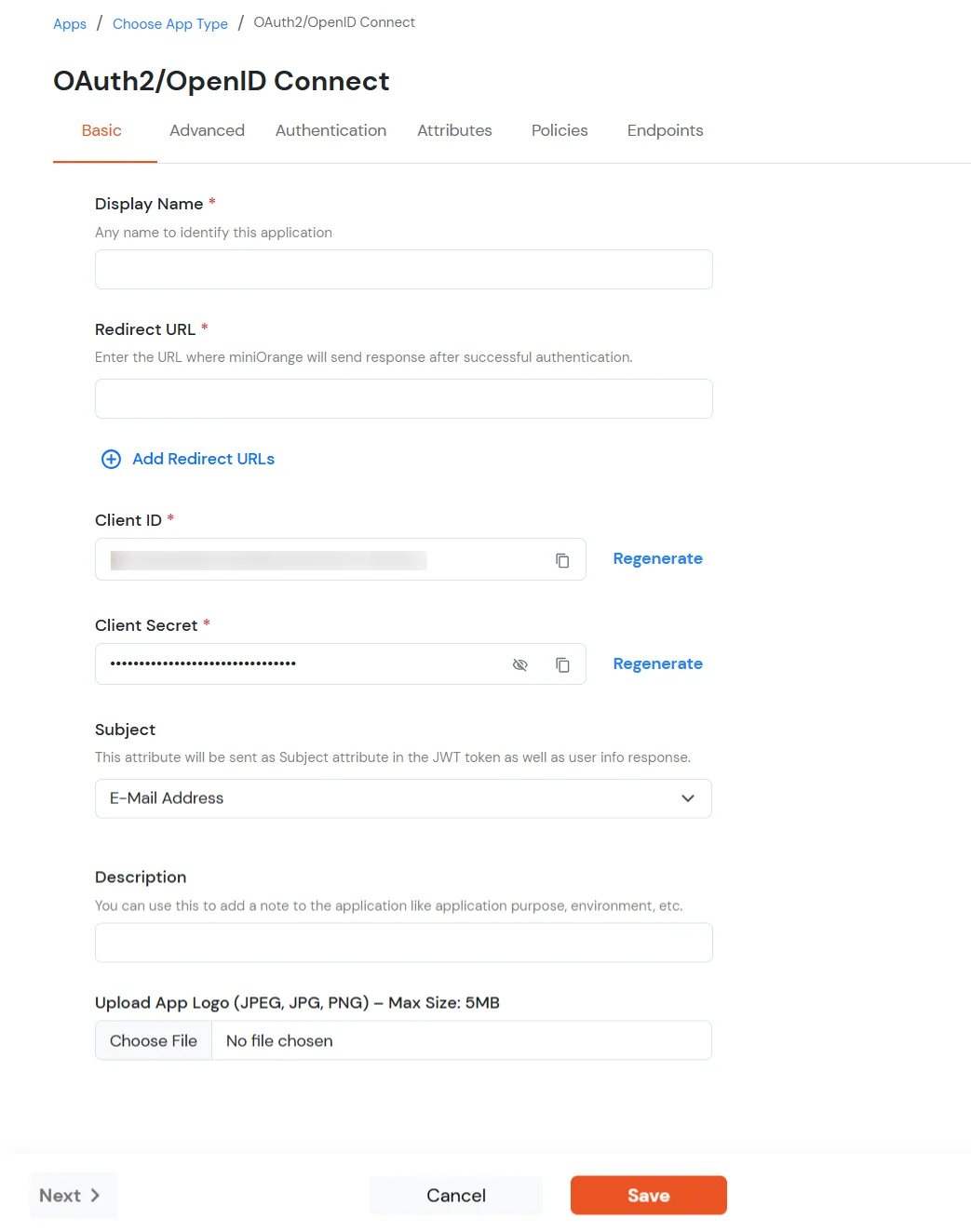
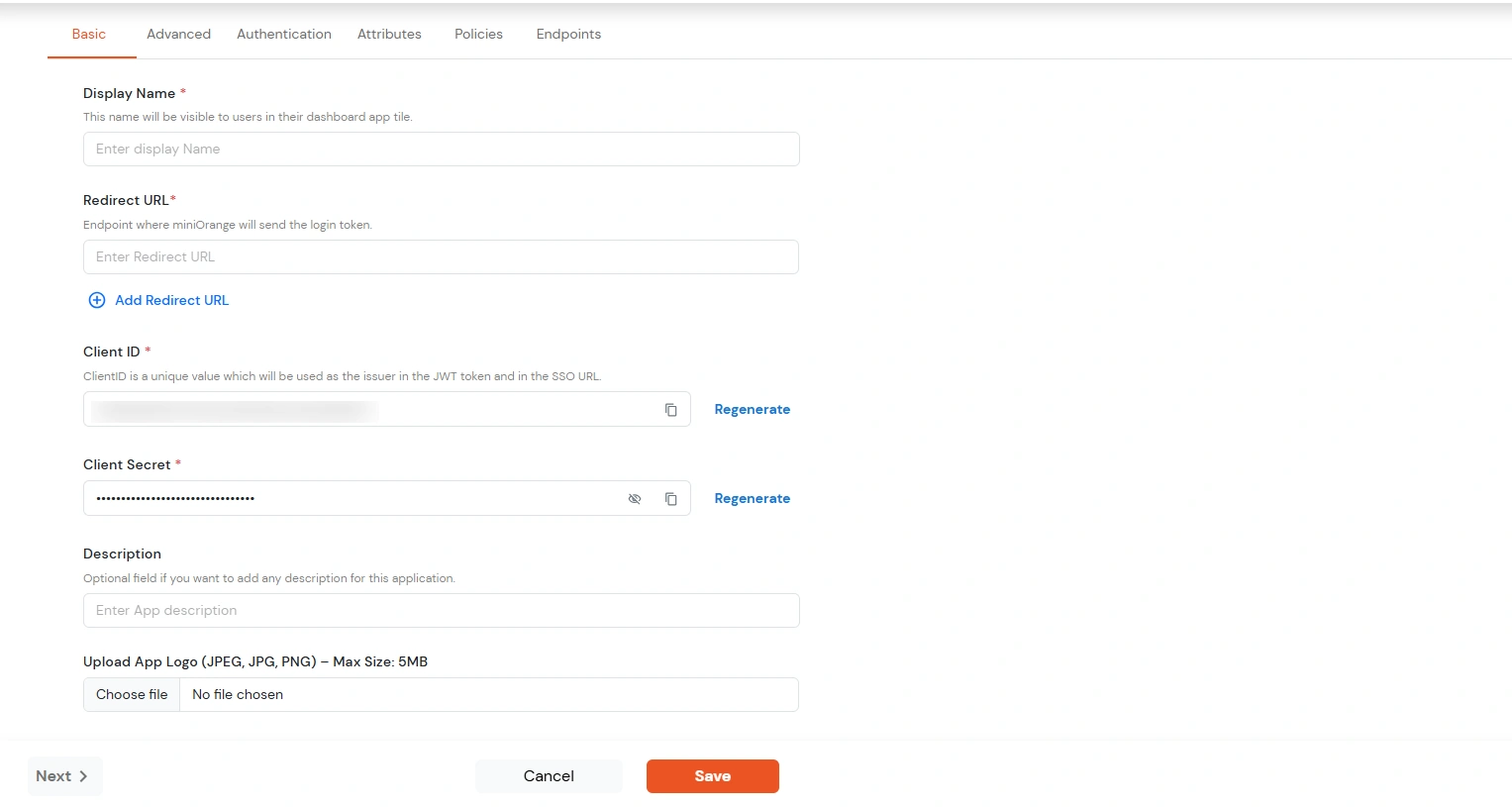
| Display Name | Enter the Display Name (i.e., the name for this application). |
| Redirect URL | Enter the Redirect URL. Make sure it follows this format: https://<mycompany.domain-name.com> |
| Client ID | Auto-generated. Click the copy icon to use it in your application. |
| Client Secret | Client Secret is hidden by default. Click the eye icon to reveal it and use the clipboard icon to copy it. |
| Subject (Optional) | Select an attribute from the dropdown list. |
| Description (Optional) | Add a description if required. |
| Upload App Logo (Optional) | Upload an app logo (Optional). The app will be shown in the end-user dashboard with the logo that you configure here. |



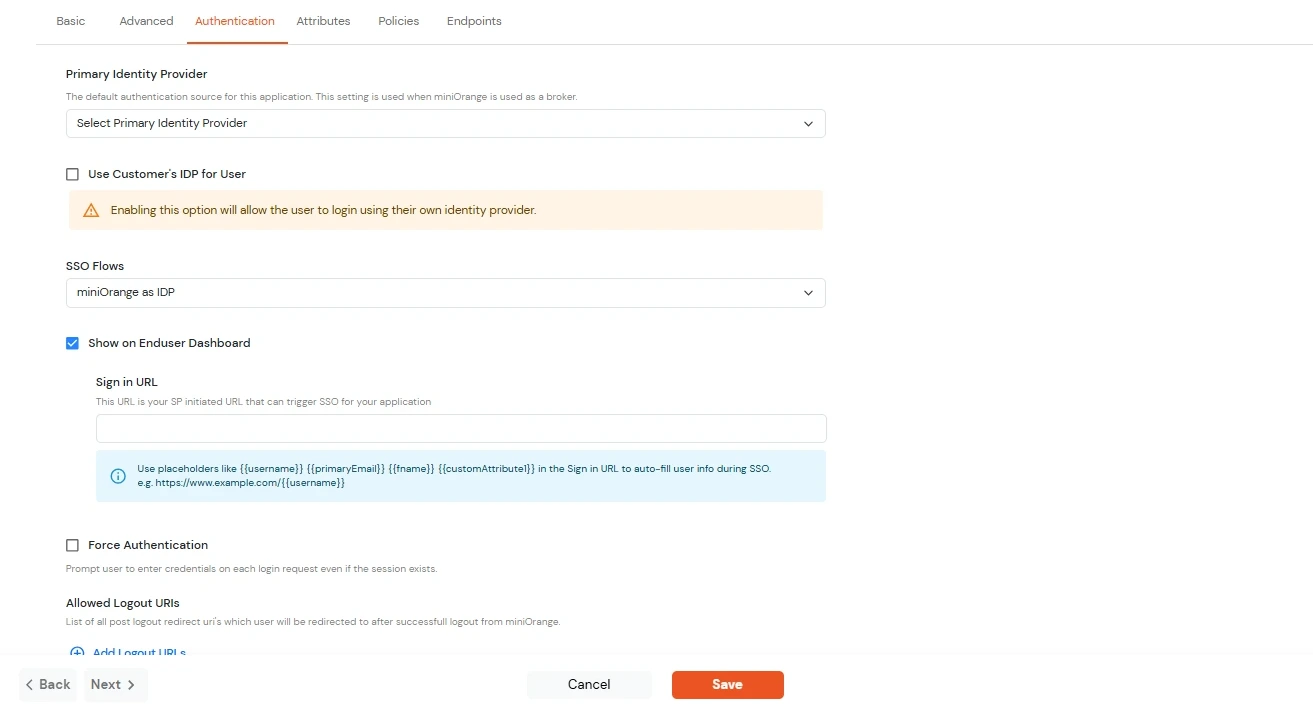
| Primary Identity Provider | Select the default ID source from the dropdown for the application. If not selected, users will see the default login screen and can choose their own IDP. [Choose miniOrange in this case.] |
| SSO FLows | Select the desired SSO flow from the dropdown, such as miniOrange as IDP, miniOrange as Broker, or miniOrange as Broker with Discovery Flow. |
| Show on Enduser Dashboard | Enable this option if you want to show this app in the end-user dashboard. |
| Force Authentication | If you enable this option, users will have to log in every time, even if their session already exists. |
| Allowed Logout URIs | Click the Allowed Logout URIs link to add a list of post-logout redirect URIs. Users will be redirected to one of these URIs after a successful logout from miniOrange. |
| Single Logout Enabled | Enable this option to send logout requests to other applications when logging out from this app. |
| Sign in URL | You can include user attributes in the sign-in URL using placeholders like {{username}}, {{primaryEmail}}, {{customAttribute1}}, etc. These placeholders will be dynamically replaced with the actual user values during the IdP-initiated SSO flow. You can generate url using following attributes: username, primaryEmail, alternateEmail, fname, lname, primaryPhone and customAttribute1. The url could be like this https://<sso-url>>?username={{username}}
https://<sso-url>>?username={{username}}&email={{primaryEmail}}https://<sso-url>>/{{customAttribute1}}/{{customAttribute2}}/?username={{username}} |
https://<your-company-name>.xecurify.com/moas/idp/openidsso ]https://<your-company-name>.xecurify.com/moas/rest/oauth/token ]| iss | https URI that indicates the issuer |
| sub | identifier of the user at the issuer |
| aud | client_id of the requesting client |
| nonce | the nonce parameter value received from the client |
| exp | expiration time of this token |
| iat | time when this token was issued |
| auth_time | time the authentication happened |
| at_hash | the first half of a hash of the access token |
https://<your-domain>.xecurify.com/moas/api/oauth/getuserinfo ] Required in case of OAuth Onlyhttps://<your-domain>.xecurify.com/moas/idp/oidc/logout?post_logout_redirect_uri ] :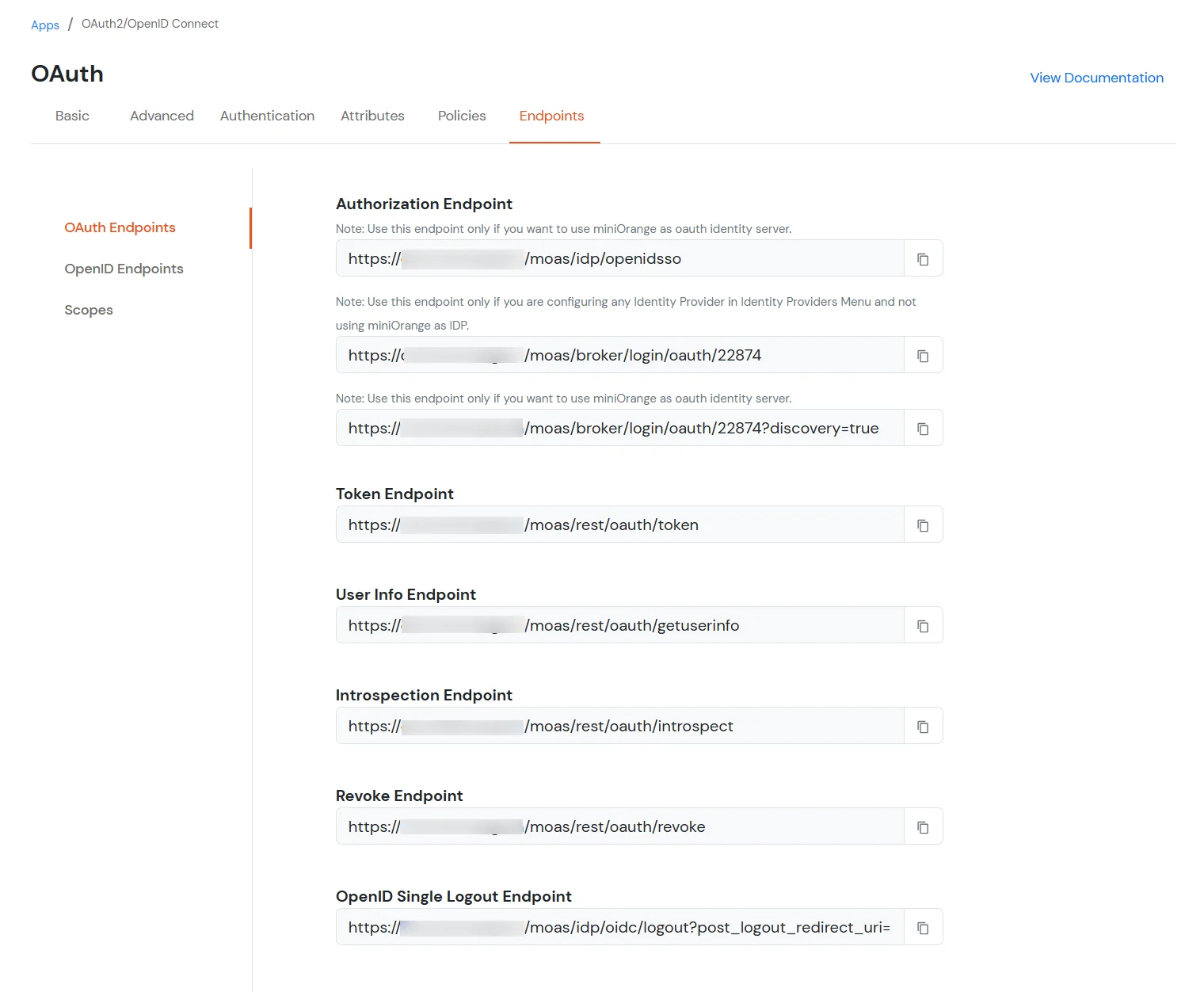
| Display Name | Enter the Display Name (i.e. the name for this application) |
| Redirect URL | Enter the Redirect URL (i.e. the endpoint where you want to send/post your JWT token). You can add multiple redirect URLs by separating them with a ‘;’.E.g. abc.com;xyz.com |
| Client ID | The Client ID is shown in the field below. Click the clipboard icon to copy it. |
| Client Secret | Client Secret is hidden by default. Click the eye icon to reveal it and use the clipboard icon to copy it. This is used in the HS256 signature algorithm for generating the signature. |
| Description (Optional) | Add a description if required. |
| Upload App Logo (Optional) | Upload an app logo (Optional). The app will be shown in the end-user dashboard with the logo that you configure here. |





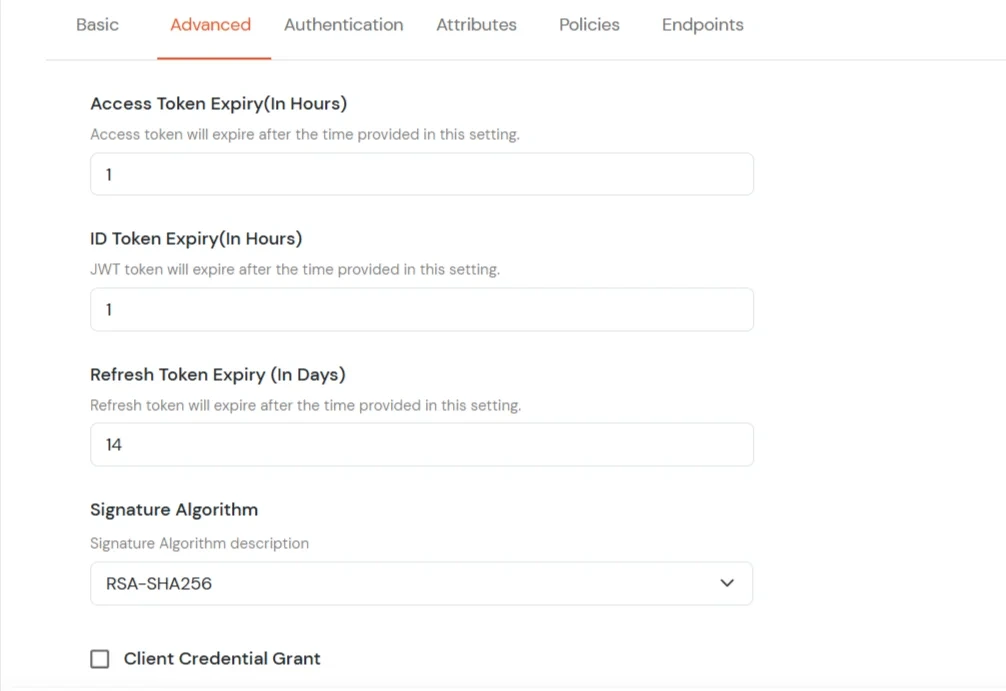
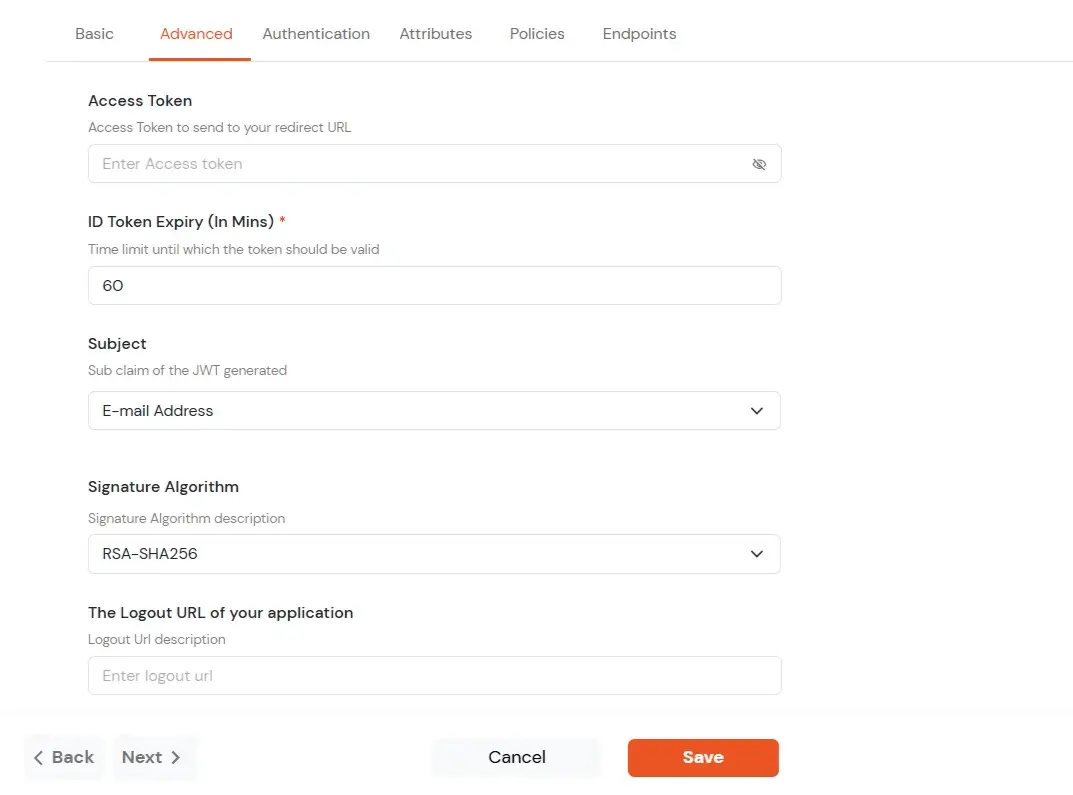
| Access Token | Enter the access token that will be sent to your redirect URL after a user logs in. This token helps your app know the user is allowed to access certain features. |
| ID Token Expiry (In Mins) | Set how long (in minutes) the ID token will be valid. After this time, the user will need to log in again to get a new token. |
| Subject | Choose what information, like the user’s email address, will be used to identify them in the token. This helps your app know which user is logged in. |
| Signature Algorithm | Select your signature algorithm from the dropdown. |
| The Logout URL of your application | Enter the web address where users should be sent after they log out. |
| Enable Shared Identity | This feature lets you control whether a specific application can be accessed by shared user or not. |
| Primary Identity Provider | Select the default ID source from the dropdown for the application. If not selected, users will see the default login screen and can choose their own IDP. [Choose miniOrange in this case.] |
| Force Authentication | If you enable this option, users will have to log in every time, even if their session already exists. |
| Enable User Mapping | Enable this option, if you want the app to show which user is signed in when it responds. |
| Show On End User Dashboard | Enable this option if you want to show this app in the end-user dashboard. |