Single Sign-On (SSO) for Apps Using Ping Federate as IDP | PingFederate SSO Login
Enable SSO login for your app, miniOrange offers a pre-built solution that simplifies the integration of Ping Federate as IDP and acts as a broker between Ping Federate and other applications acting as SP. With this setup, user authentication is handled by Ping Federate, and miniOrange facilitates communication for a seamless implementation process.
Follow the Step-by-Step Guide given below for Ping Federate Single Sign-On (SSO)
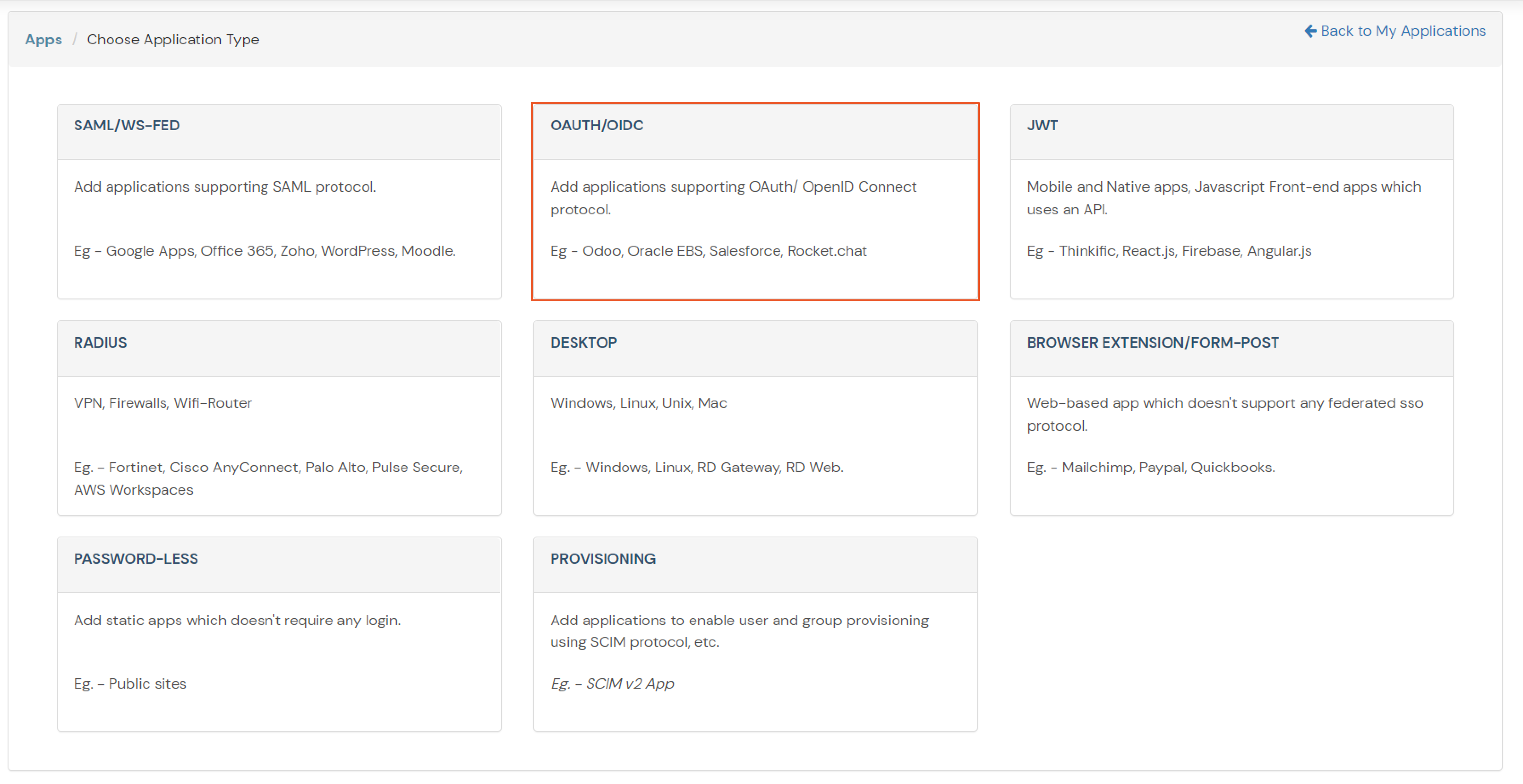
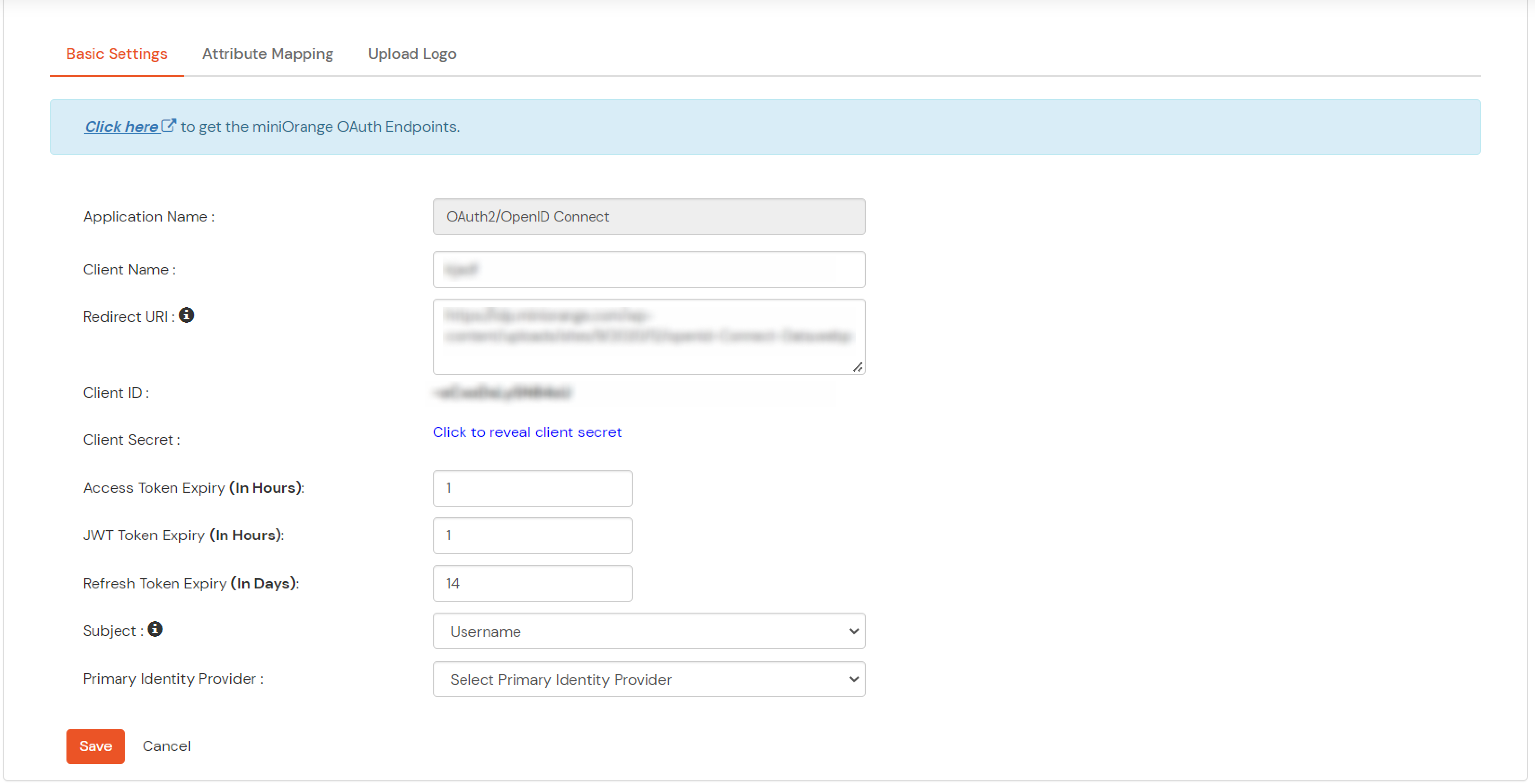
1. Configure Ping Federate as OAuth 2.0 Provider in miniOrange.
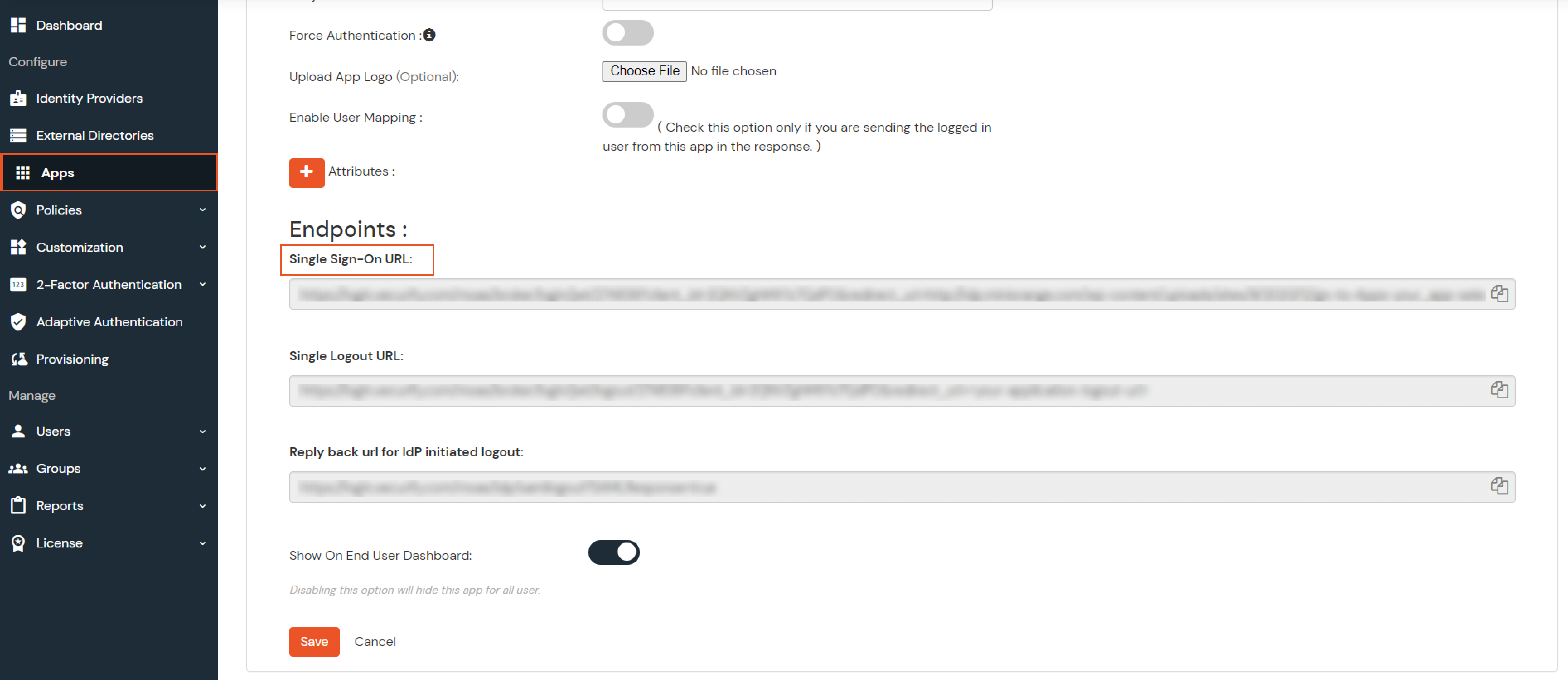
- Go to miniOrange Admin Console.
- From the left navigation bar select Identity Provider. Select Oauth
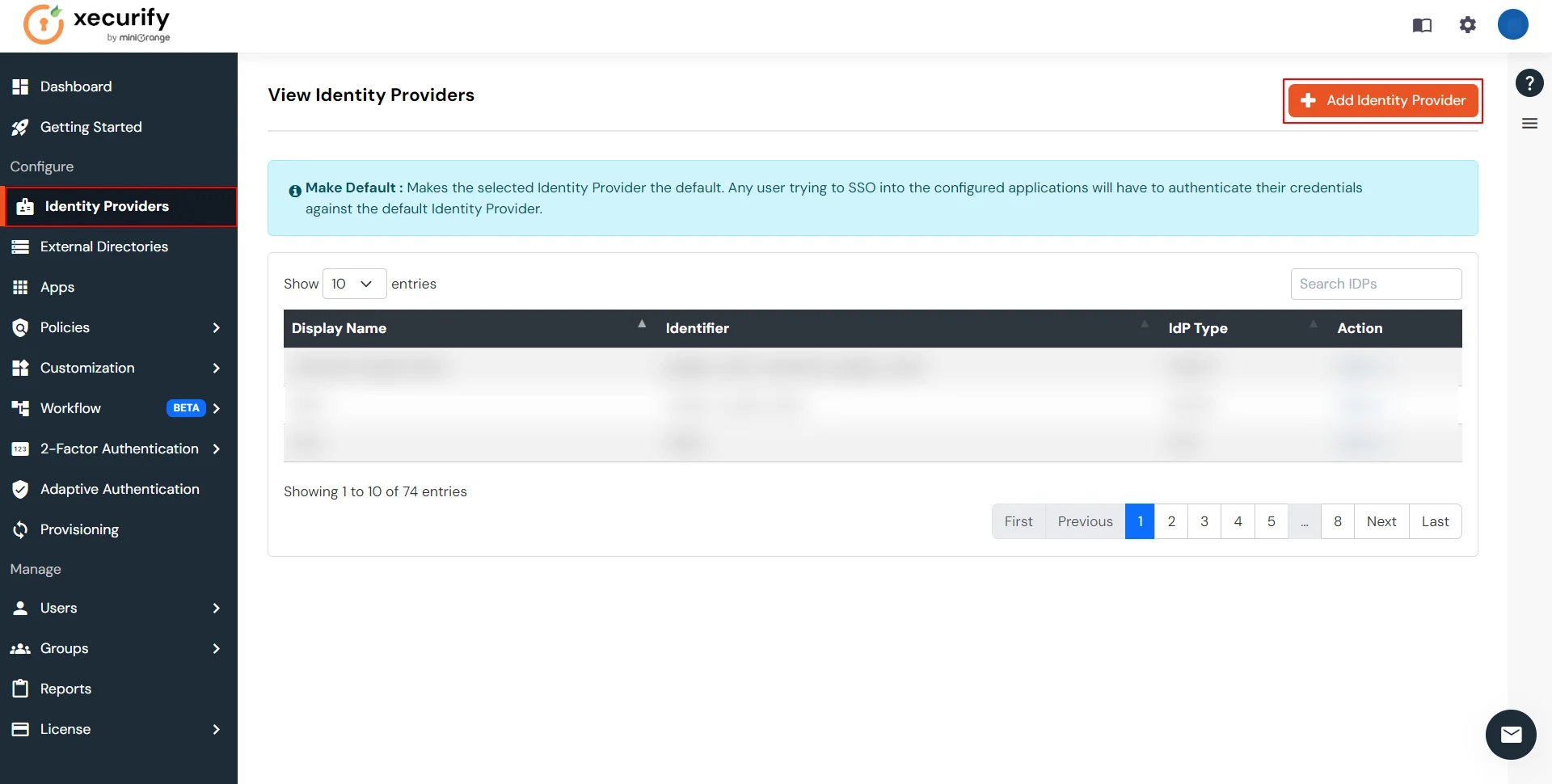
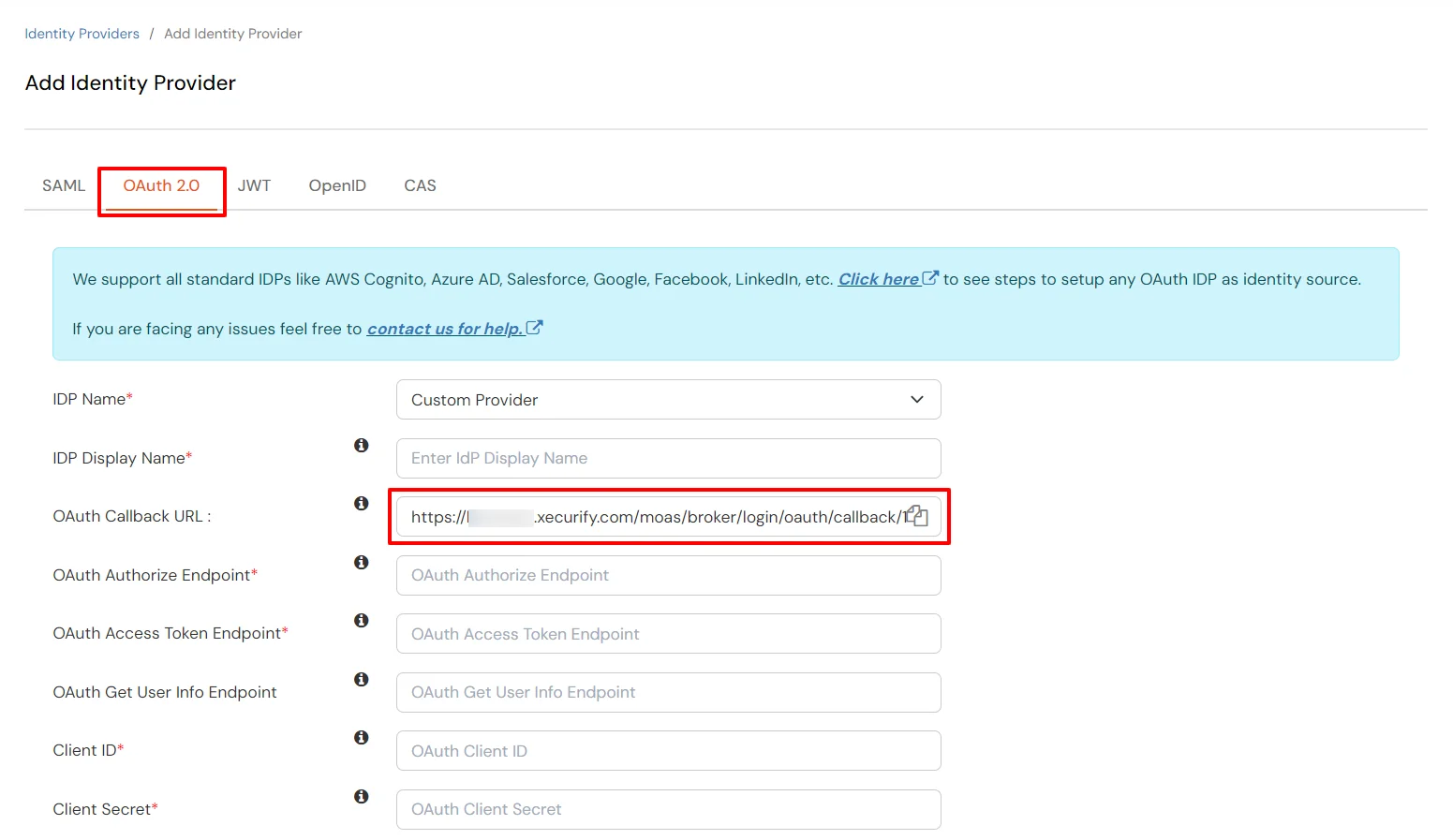
- Enter the following values.
| IdP Name |
Custom Provider |
| IdP Display Name |
Choose appropriate Name |
| OAuth Authorize Endpoint |
https://{your-base-url}/as/authorization.oauth2 |
OAuth Access Token Endpoint |
https://{your-base-url}/as/token.oauth2 |
OAuth Get User Info Endpoint (optional) |
https://{your-base-url}/idp/userinfo.oauth2 |
| Client ID |
From step 2 |
| Client secret |
From step 2 |
| Scope |
auto |
2. Configure miniOrange as Service Provider (SP) in Ping Federate
- Login to your Ping Federate User Admin dashboard.
- Click on the OAuth Server in the left navigation menu.
- Under Clients, click on Create New.
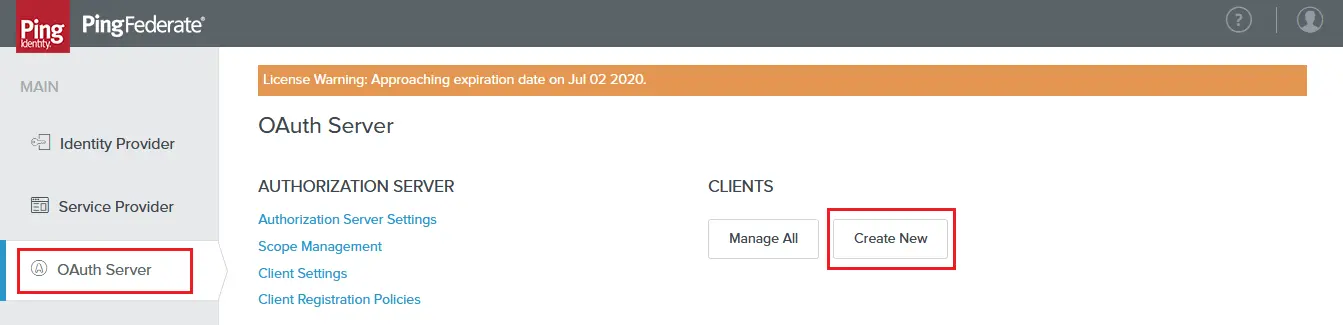
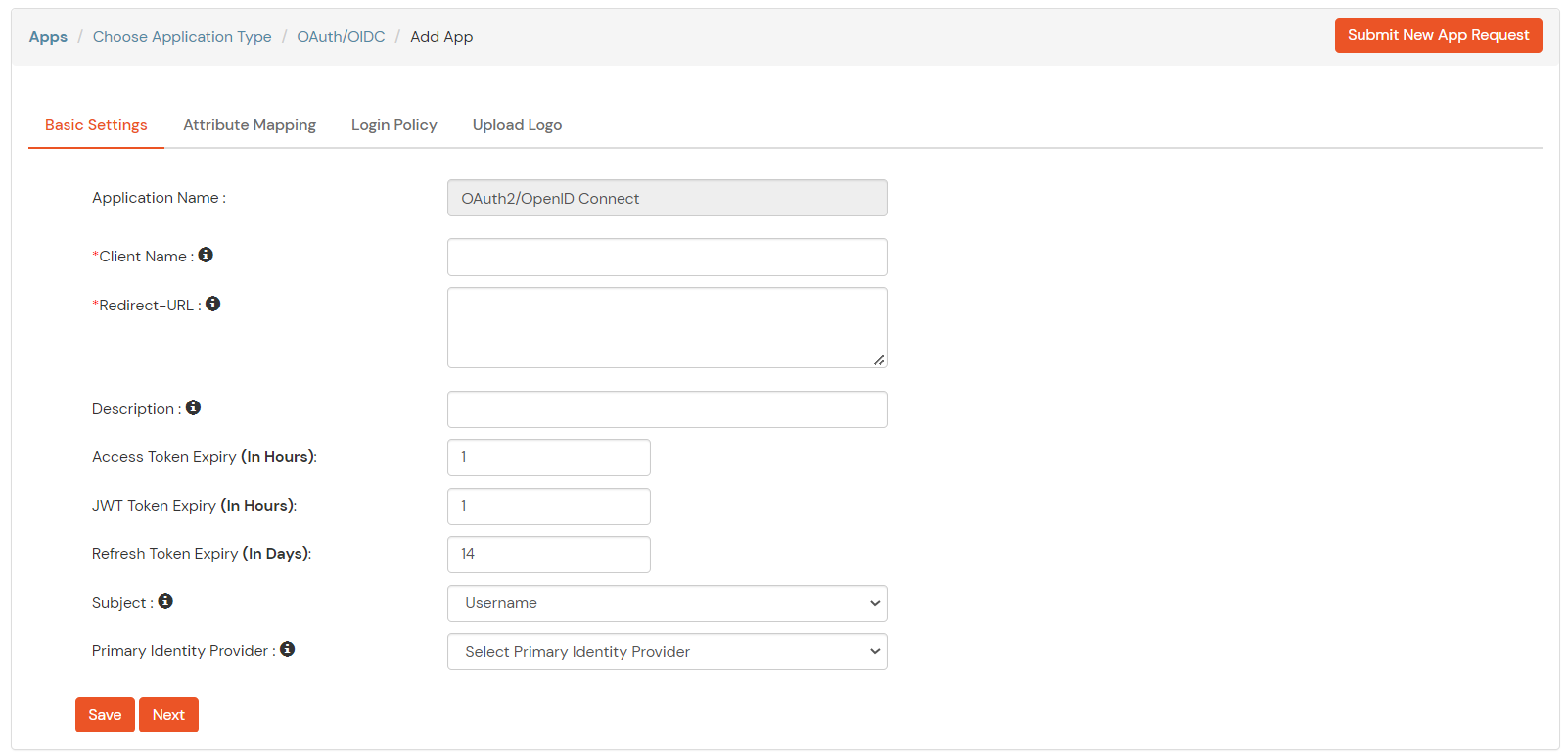
- Enter the Client ID, Name and Description. Select Client Secret in Client Authentication and click on Generate Secret. Take a note of your Client ID & Client Secret.
- To get the Redirect URL:
- Go to miniOrange Admin Console.
- From the left navigation bar select Identity Provider.

- Copy the Callback URL as Redirect URL required for next step.

- Back in Ping Federate, copy the Redirect/Callback URL and enter it in Redirect URIs field and click on Add. Select the Authorization Code grant type and click on Save.
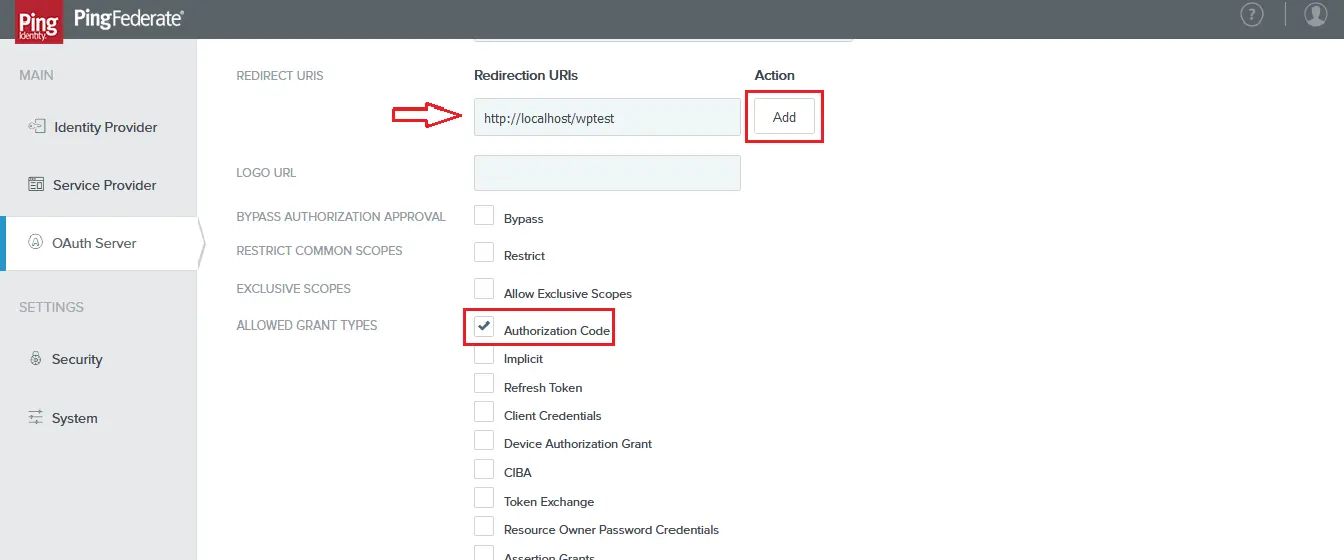
- You have successfully completed your Ping Federate App OAuth configurations.
3. Configure your application in miniOrange
Note:
If you have already configured your application in miniOrange you can skip the following steps.
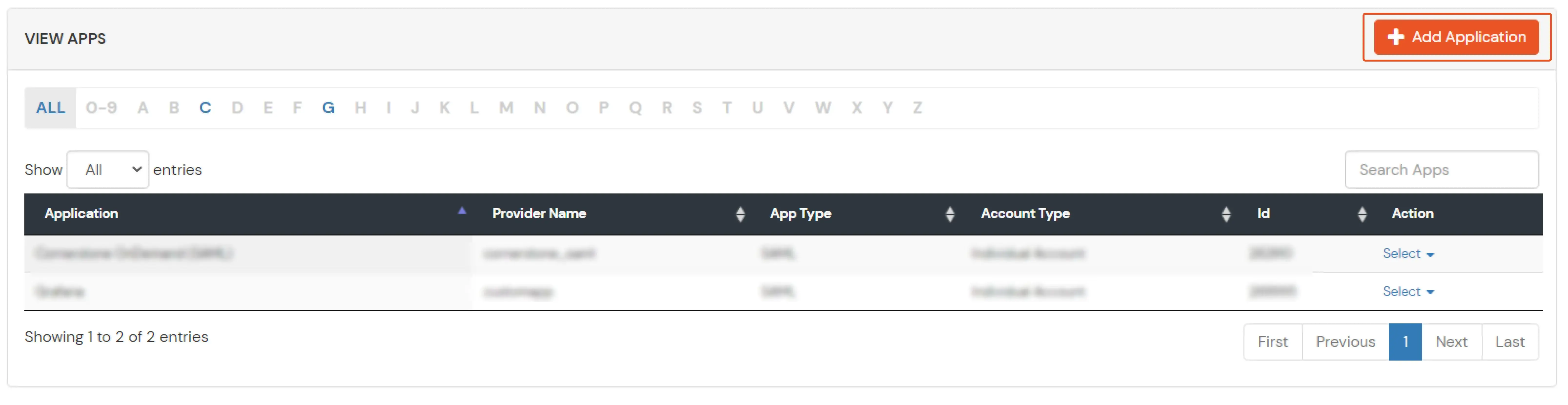
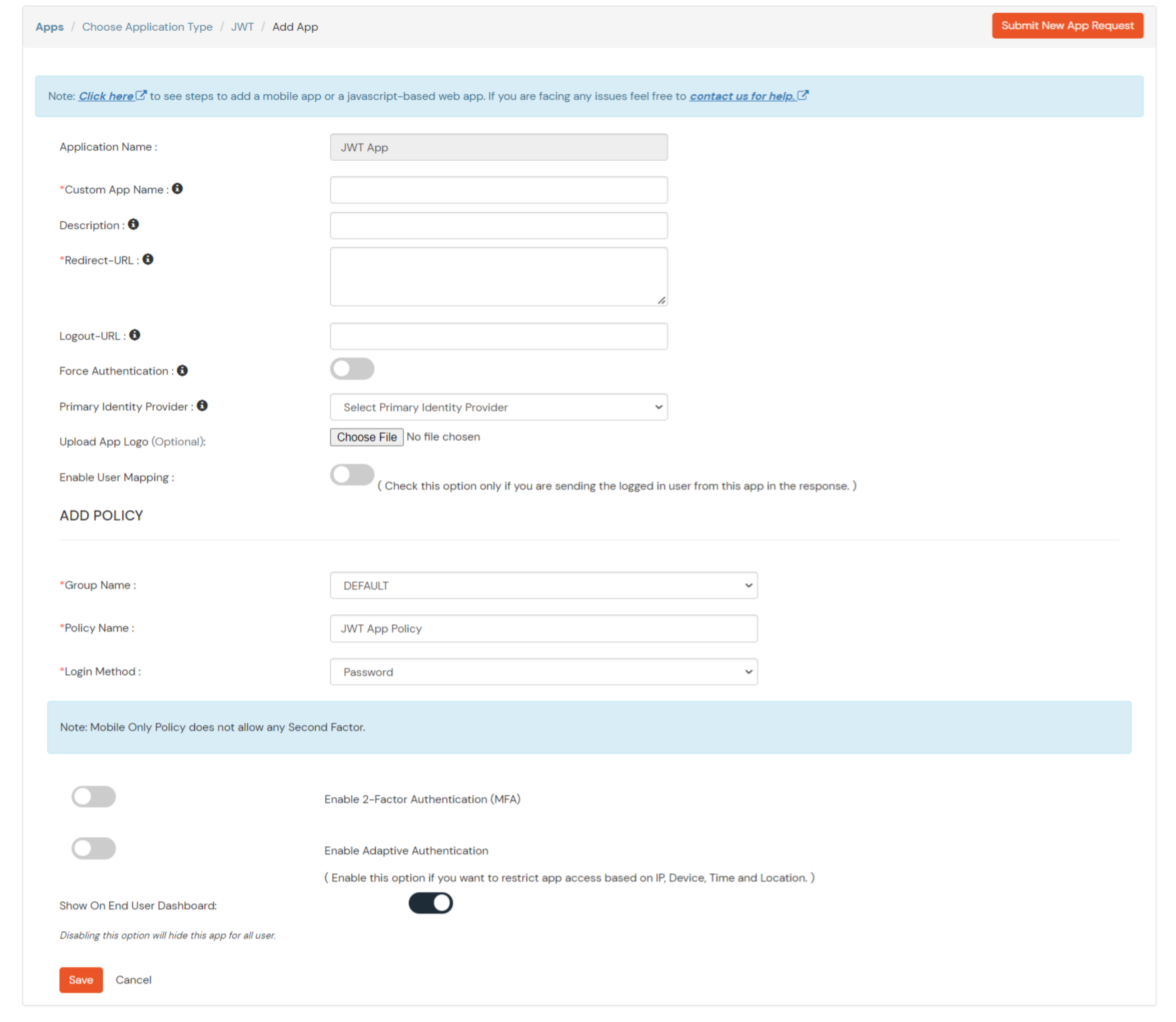
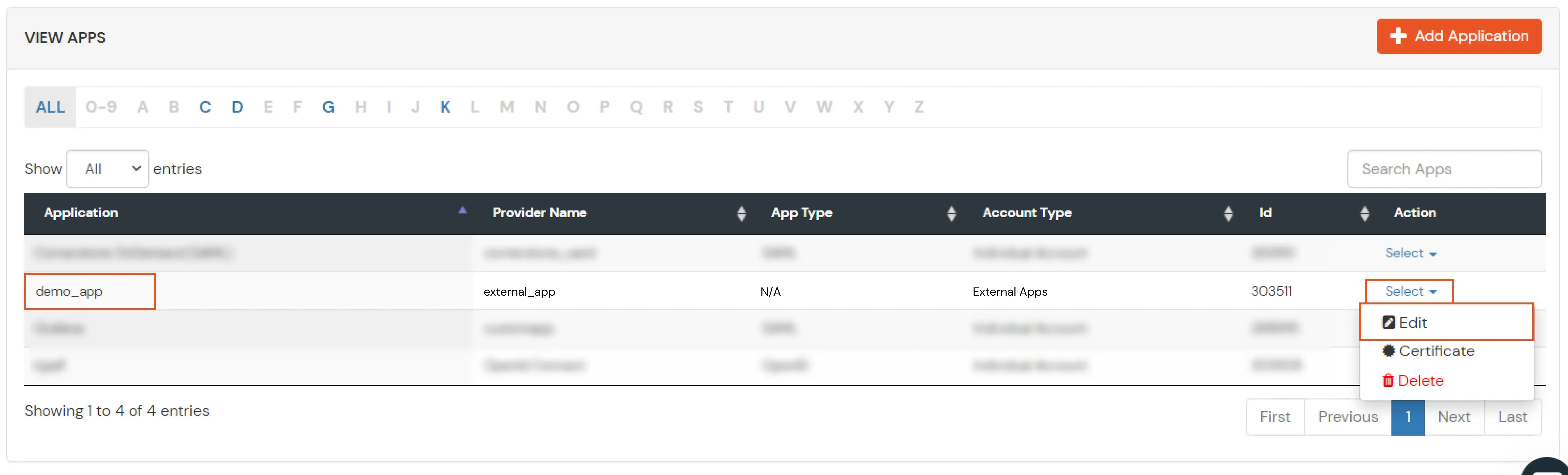
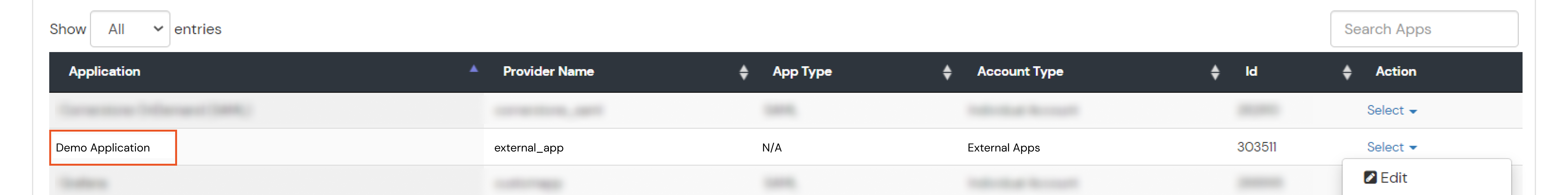
- Click on Create App under SAML.
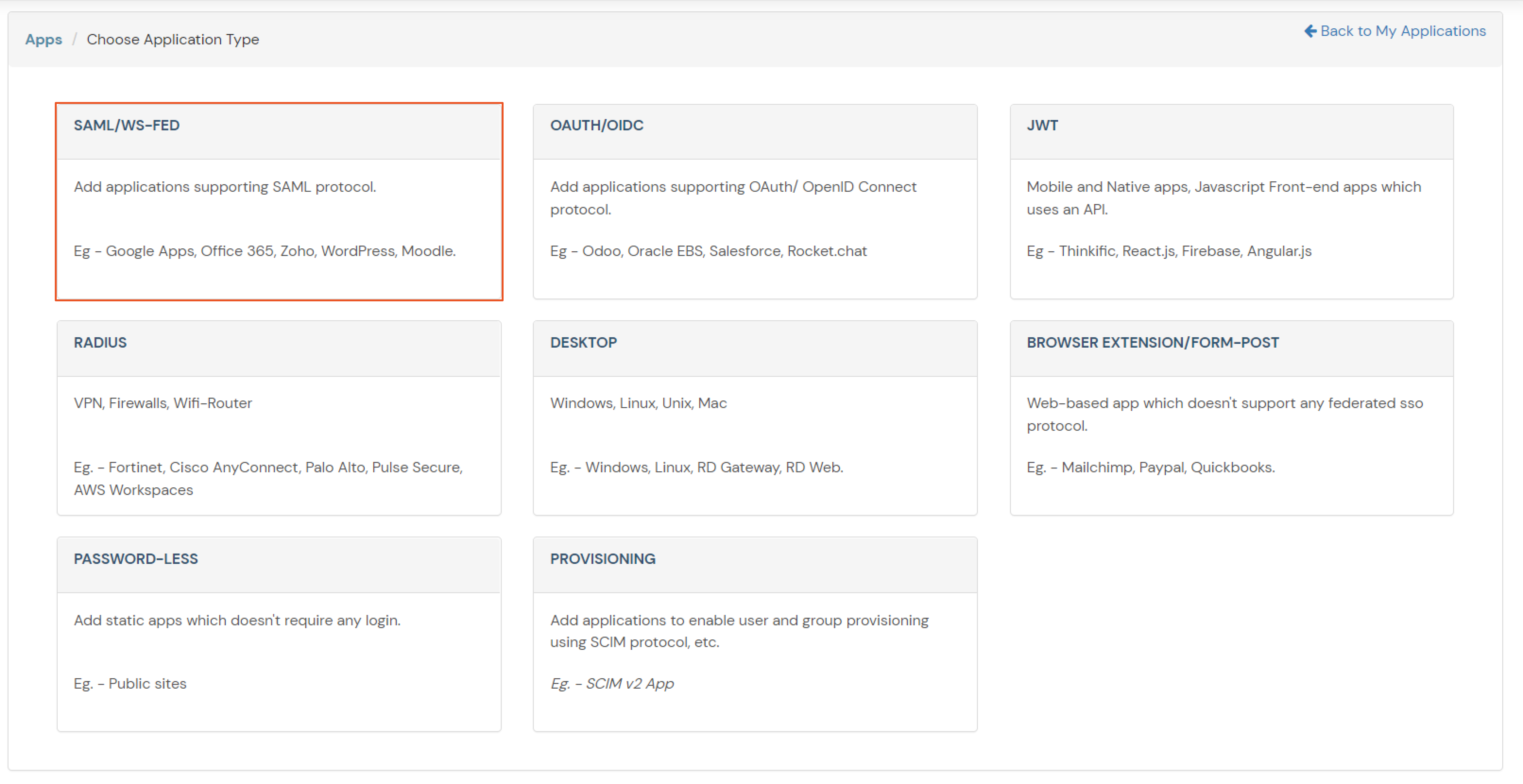
- Search for your Application. In case you do not find your app, search for Custom SAML App.
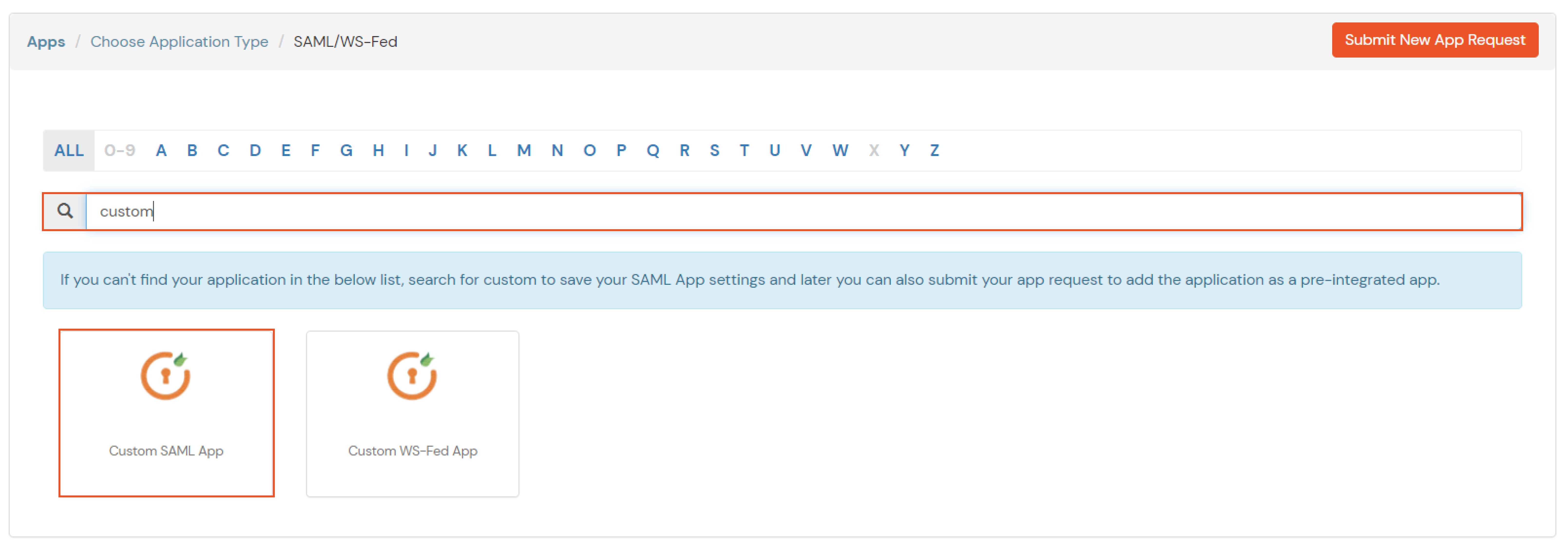
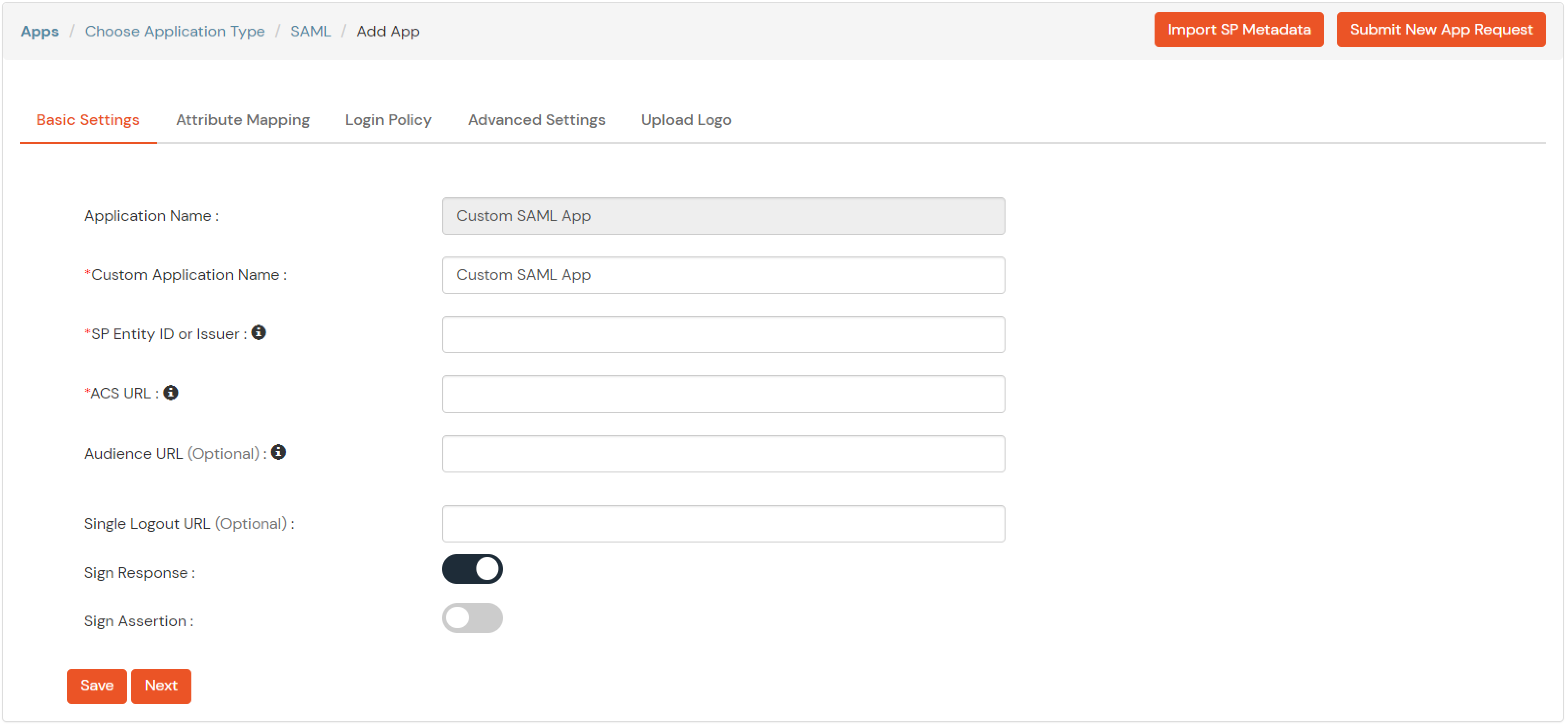
- Get the ACS URL and SP Entity ID from your application.
- Enter the following values OR click on Import SP Metadata:
| Service Provider Name |
Choose appropriate name according to your choice |
| SP Entity ID or Issuer |
Your Application Entity ID |
| ACS URL X.509 Certificate (optional) |
Your Application Assertion Consumer Service URL |
| NameID format |
Select urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress |
| Response Signed |
Unchecked |
| Assertion Signed |
Checked |
| Encrypted Assertion |
Unchecked |
| Group policy |
Default |
| Login Method |
Password |
- Click on Save to configure your application.
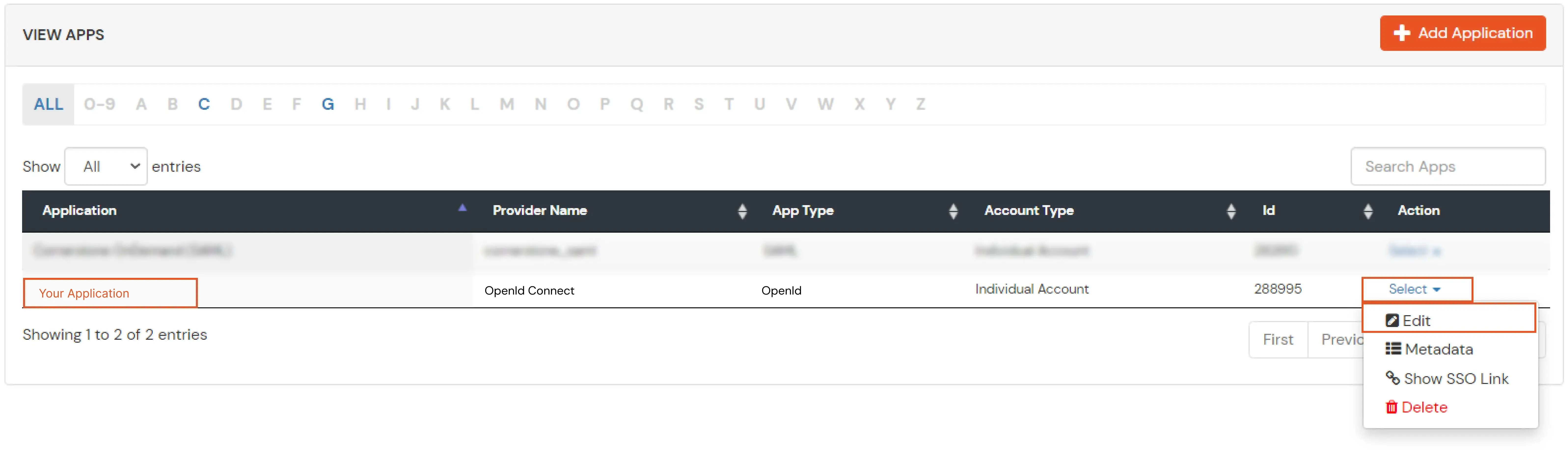
- Now to get the IDP metadata of the app configured, Go to apps >> your_app >> select >> metadata tab.
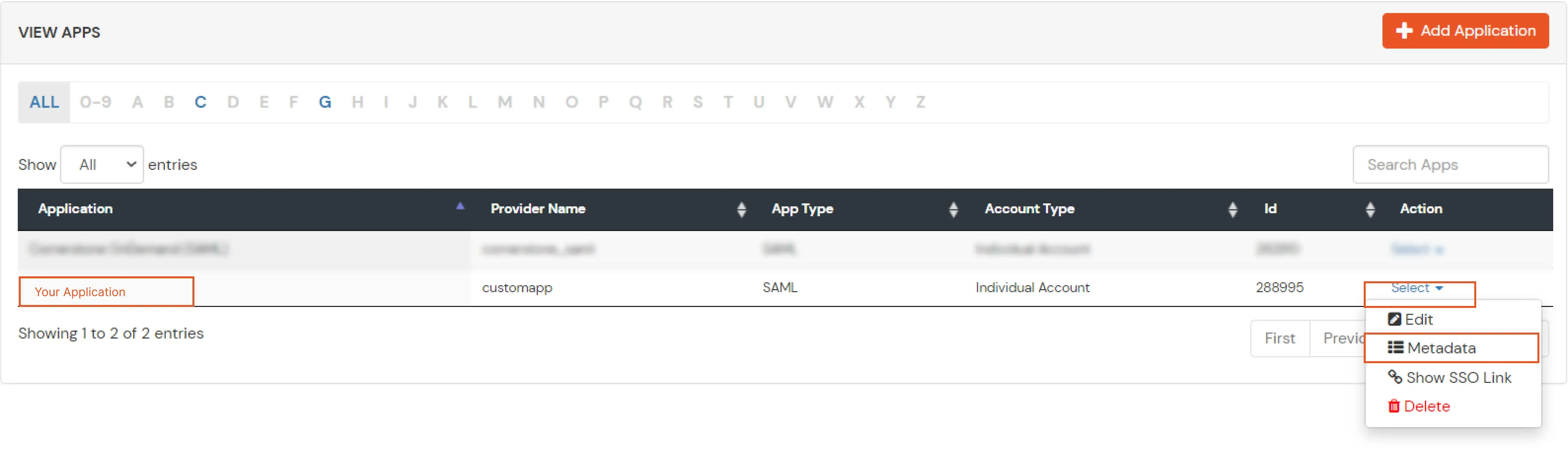
- Click on the Show Metadata details in the Information required to Authenticate via External IDPs section. Download the metadata XML file by clicking on Download Metadata button or copy the Metadata URL link.
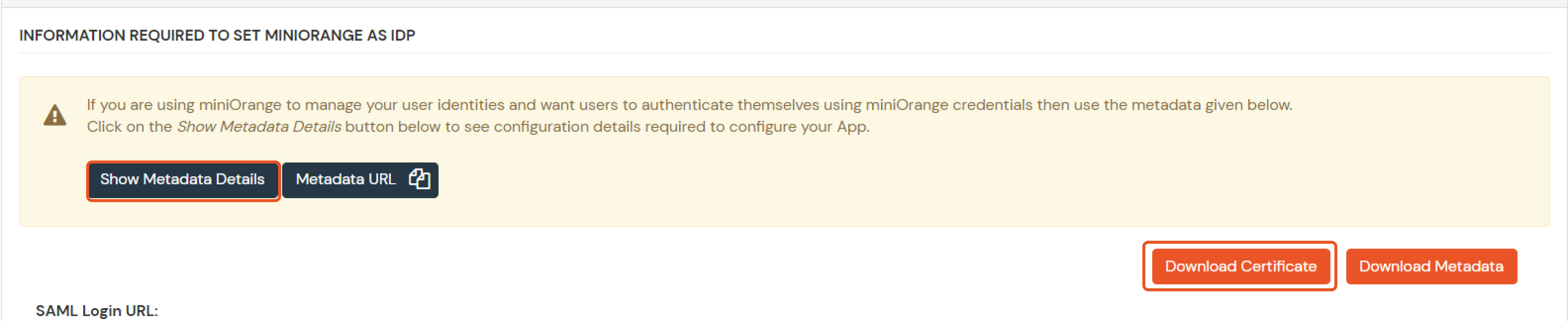
- You need to Upload this metadata in your application.
4. Login using IDP selection page (Optional)
- You can configure multiple IDPs (Identity Providers) and give users the option to select the IDP of their choice to authenticate with.
For Example - It could be multiple AD domains belonging to different departments or multiple okta organizations.
Few usecases where customers configure multiple IDPs -
- Suppose you have a product which many of your clients use and each client has their own unique IDP so you want them to SSO into your product as well using their existing IDP only. miniOrange provides a centralized way to connect with all IDPs in a very easy manner and integrate SSO into your application.
- Suppose you are providing a course to many universities, each having a unique SAML, OAuth protocol supported IDP's like Shibboleth, ADFS, CAS, etc. You can provide Single Sign-On (SSO) into your course application to all these universities by integrating with all of them using a single platform provided by miniOrange.
- This is the endpoint to call from your SAML application -
| For Cloud IDP - |
https://login.xecurify.com/moas/discovery?customerId=<customer_id> |
| For On-Premise IDP - |
https://yourdomain.com/discovery?customerId=<customer_id> |
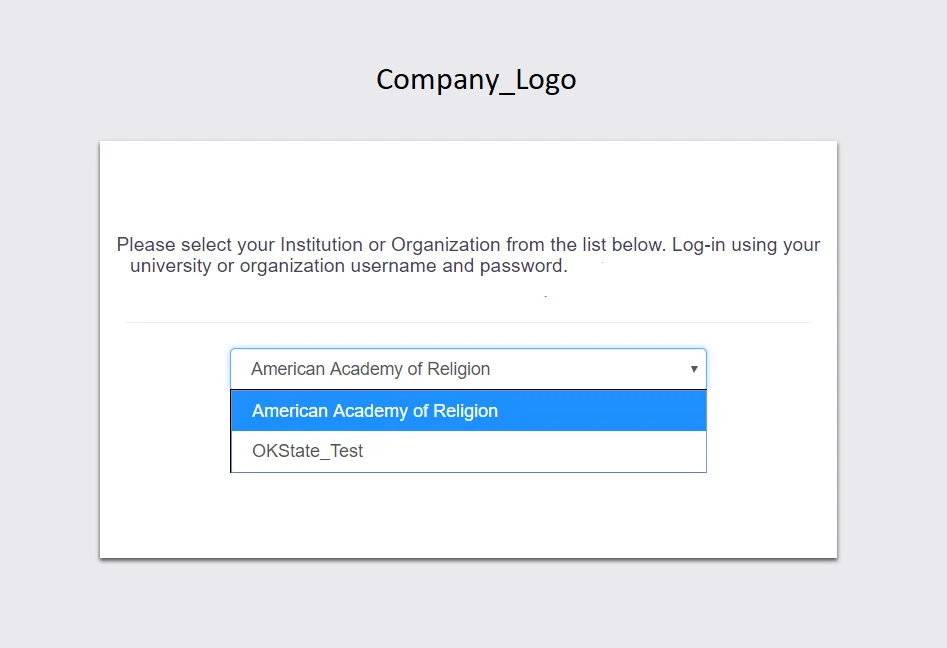
- You should copy the Customer Key from admin console-> Settings -> and replace it with <customer_id> here. Once configured in SP, when you initiate the login from Service Provider, a user will be redirected to IDP Selection Page listing all IDPs configured for that account.
You can see the screenshot below of the IDP Selection Page with a list of IDPs.
Note: To view the IDP in drop-down list, go to Identity Providers tab > against your configured IDP > Select >Edit , here Enable the Show IdP to Users option.
- You also have the option to modify the appearance and design of this page. Login to miniOrange Admin console. Navigate to Customization -> Branding Configuration. See the below screenshot for reference-
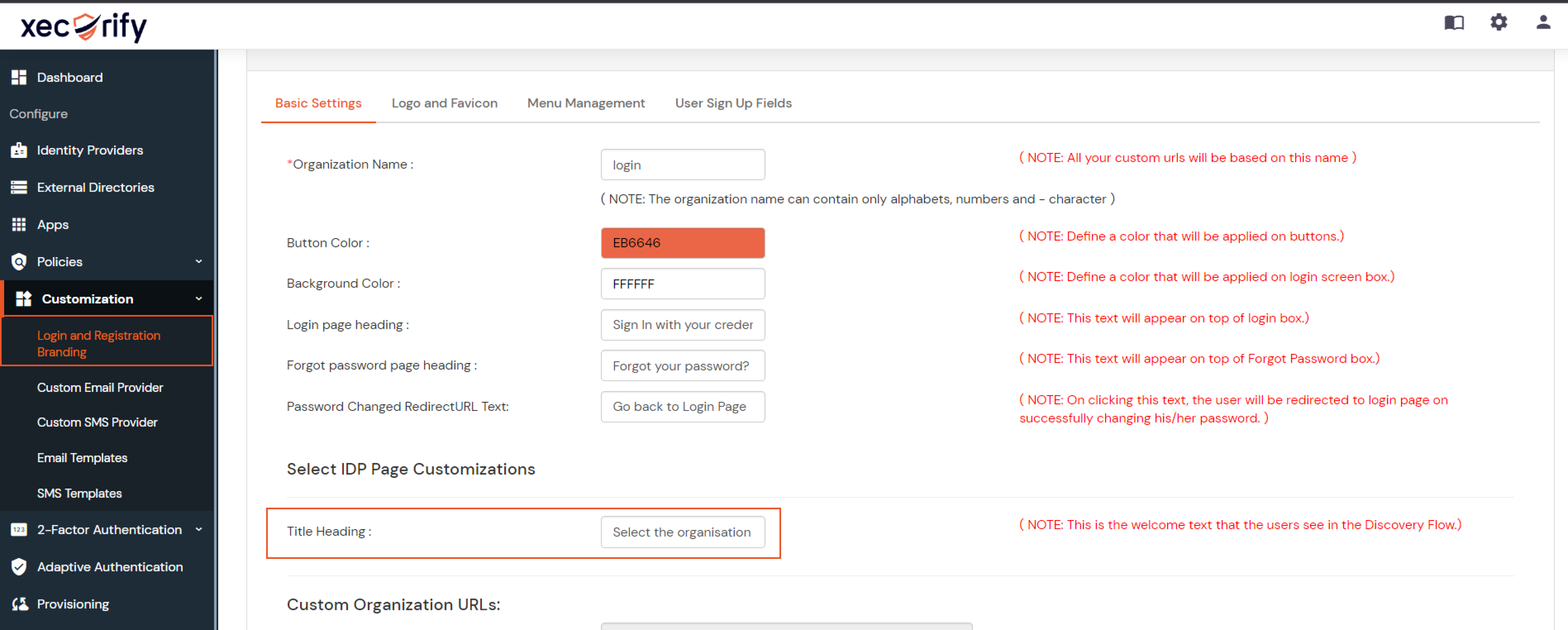
- You can customize the title of this page.
- Change the logo and favicon for this page.
- Change the background and button color for this page from admin UI.
External References