Need Help? We are right here!
Search Results:
×Mac filtering, also known as MAC-based restriction or MAC address-based restriction, is a network security method that controls access to a network by filtering devices based on their unique Media Access Control (MAC) addresses. Each network-connected device, such as computers, smartphones, or routers, has a distinct MAC address as a hardware identifier.
Mac filtering allows administrators to list approved or disallowed MAC addresses. Devices with MAC addresses on the approved list are granted access to the network, while those on the disallowed list are blocked. This approach adds an additional layer of security by permitting only authorized devices to connect, helping to prevent unauthorized access and enhance network protection.
Our Risk Engine verifies the MAC address of each device during the login. It identifies devices based on their MAC addresses before allowing network access.
MAC restriction maintains a whitelist for authorized devices and a blacklist for unauthorized ones based on the MAC addresses of these devices.
It serves as a gatekeeper for your environment, by permitting access for whitelisted devices.
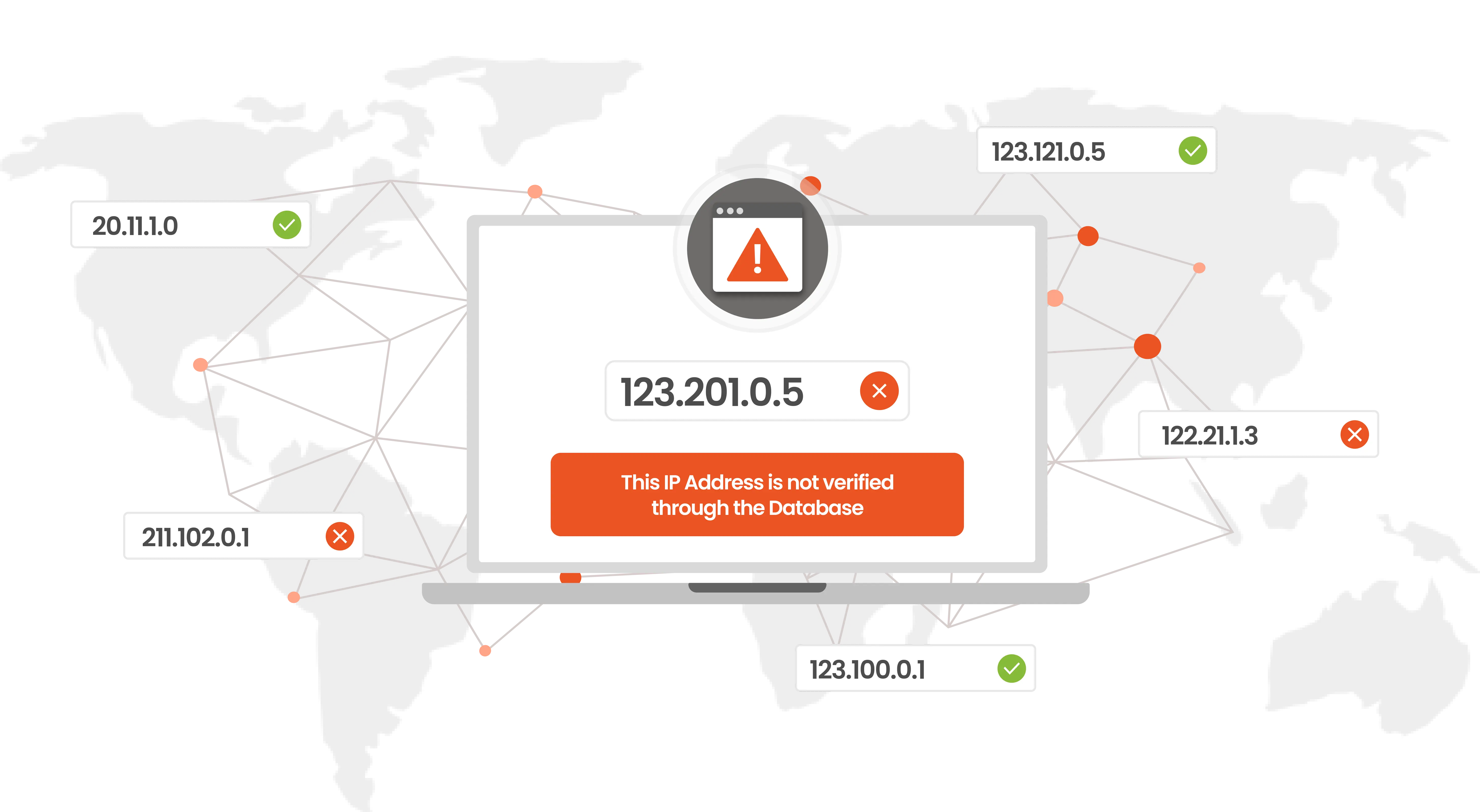
In Mac's IP-based restriction, the admin manages a list of approved or blocked IP addresses. When a user tries to log in, their IP address is checked against the predefined list of IP addresses.
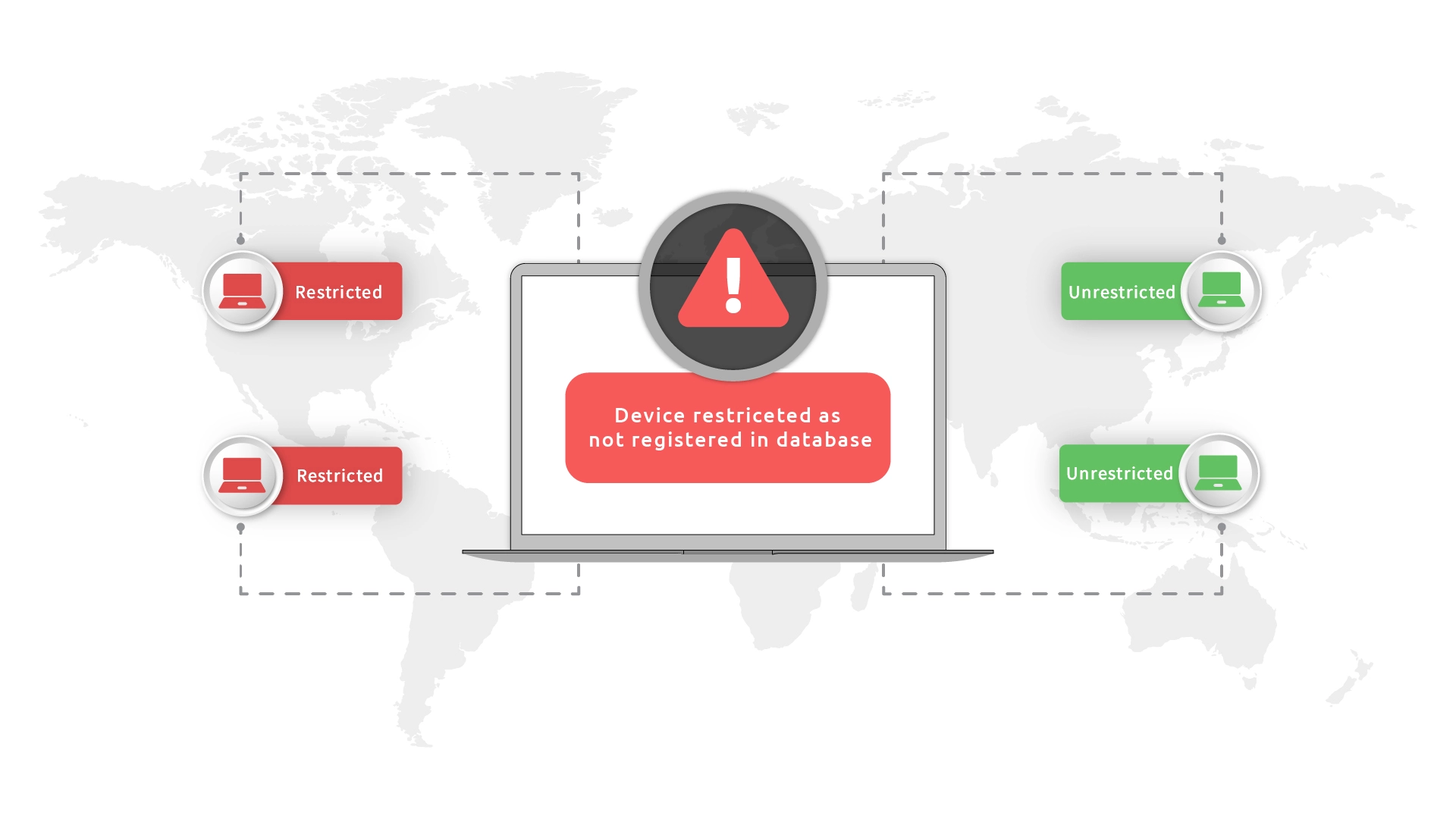
In Mac-based device restrictions, administrators grant end-users the capability to associate a fixed number of trusted devices with their accounts.
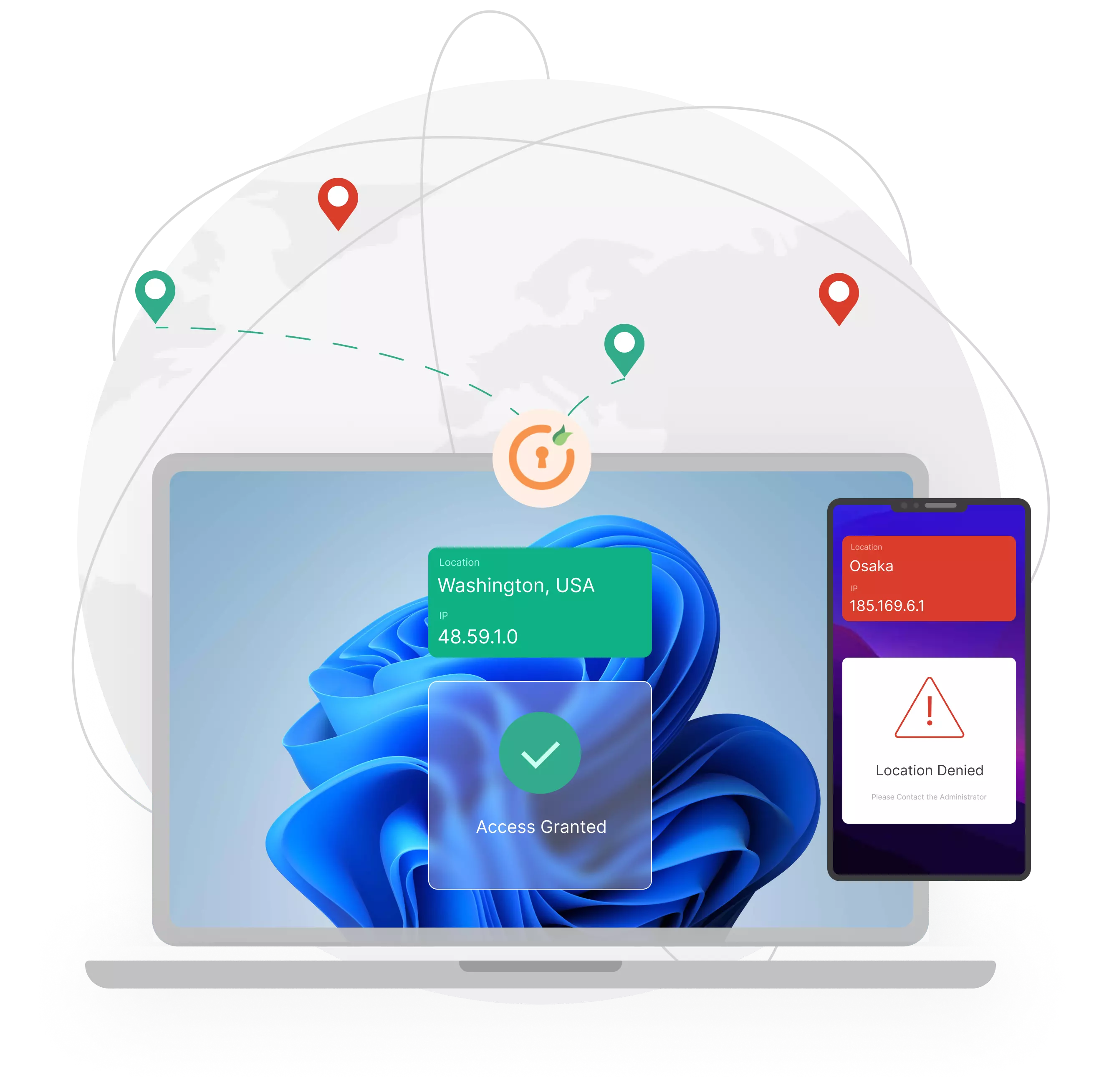
End-users are either granted/denied access based on their geographical location data, like latitude, longitude, and country code, which is verified against the administrator's predefined Location list.







"Nahdi wanted to adopt SSO, and they were using Siebel CRM, but it didn't support any SSO protocols. Changing the entire CRM system and transferring data from one CRM to another is a time-consuming job....."
