Need Help? We are right here!
Search Results:
×95%
80%
99%
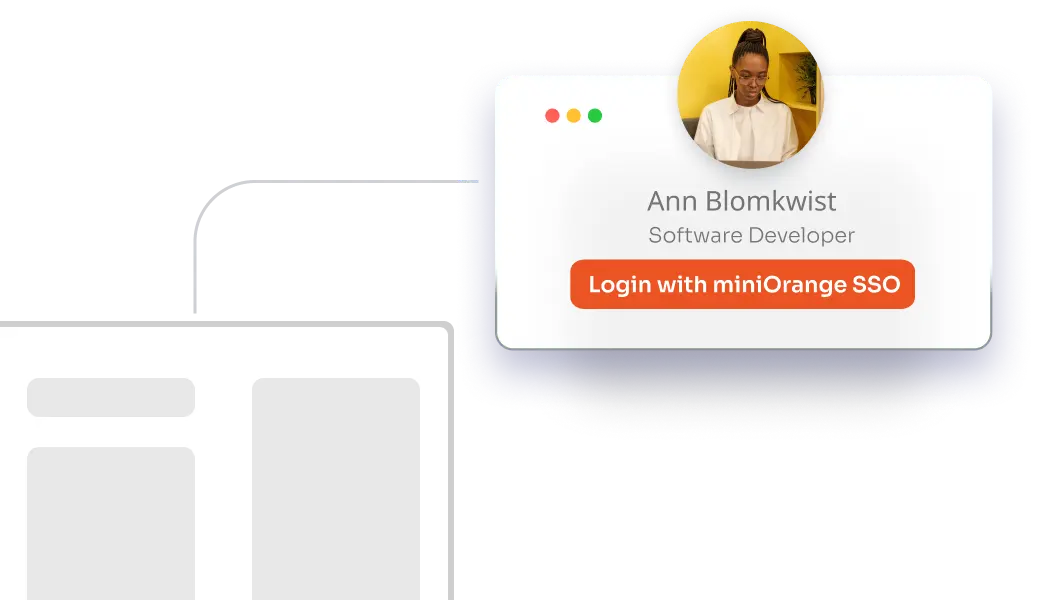
miniOrange enables seamless access to all applications using one credential set. Supports SAML, OAuth 2.0, OpenID Connect, and WS-Federation for secure, unified authentication.
Read more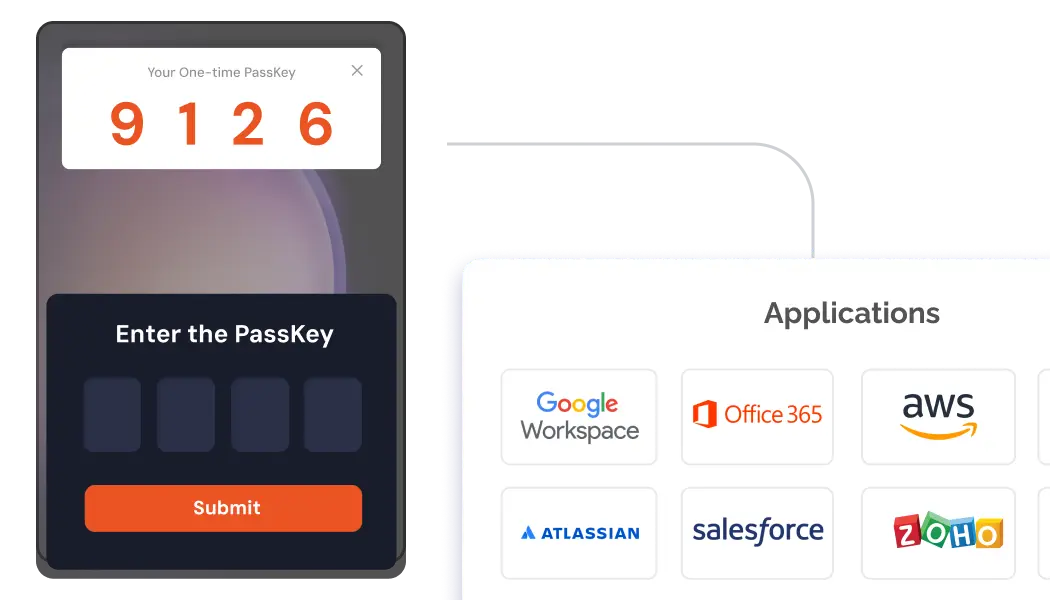
Strengthen security with 15+ MFA methods. Choose from push notifications, OTPs, biometrics, QR codes, and tokens to protect systems, even when passwords are compromised or leaked.
Read more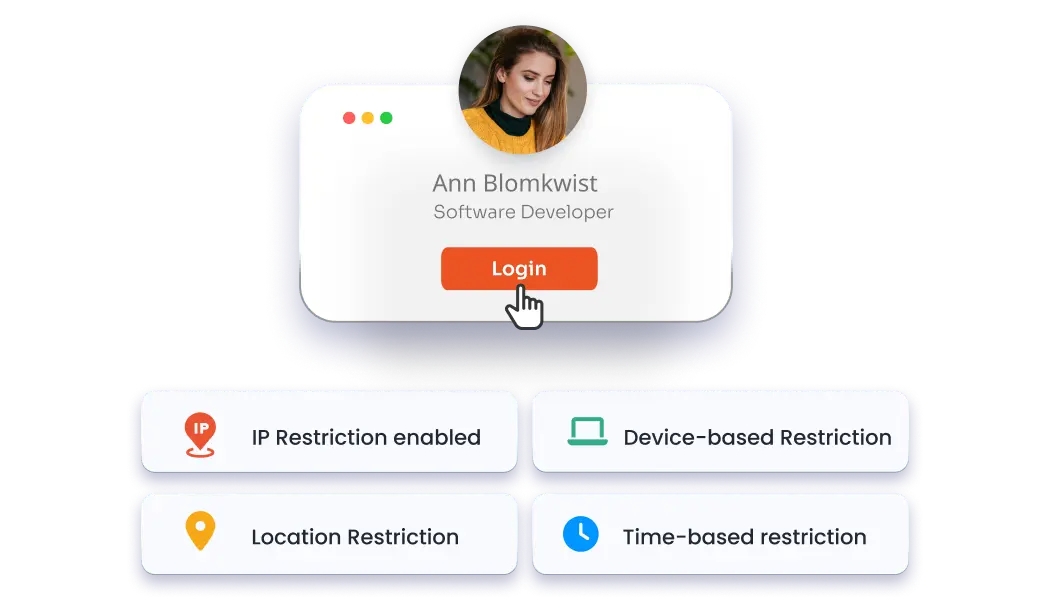
The Adaptive MFA uses real-time risk analysis, device, location, IP, and behavior to adjust authentication dynamically, ensuring secure access without compromising user convenience or experience.
Read more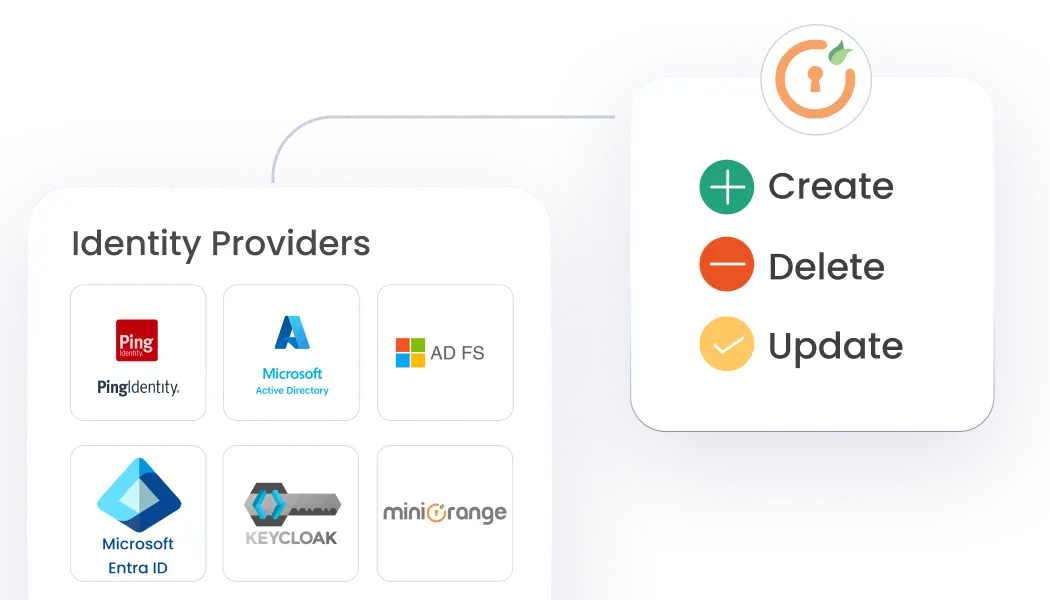
Automate user provisioning, updates, and deprovisioning. miniOrange ensures accurate access rights with onboarding workflows, role-based controls, and instant revocation when employees leave or change roles.
Read more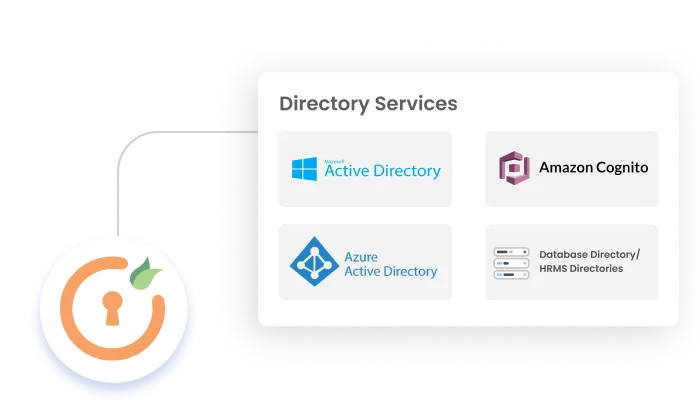
miniOrange centralizes identity management. Integrate existing directories or use our cloud directory. Supports complex structures, flexible attributes, group management, and delegated admin for tailored control.
Read more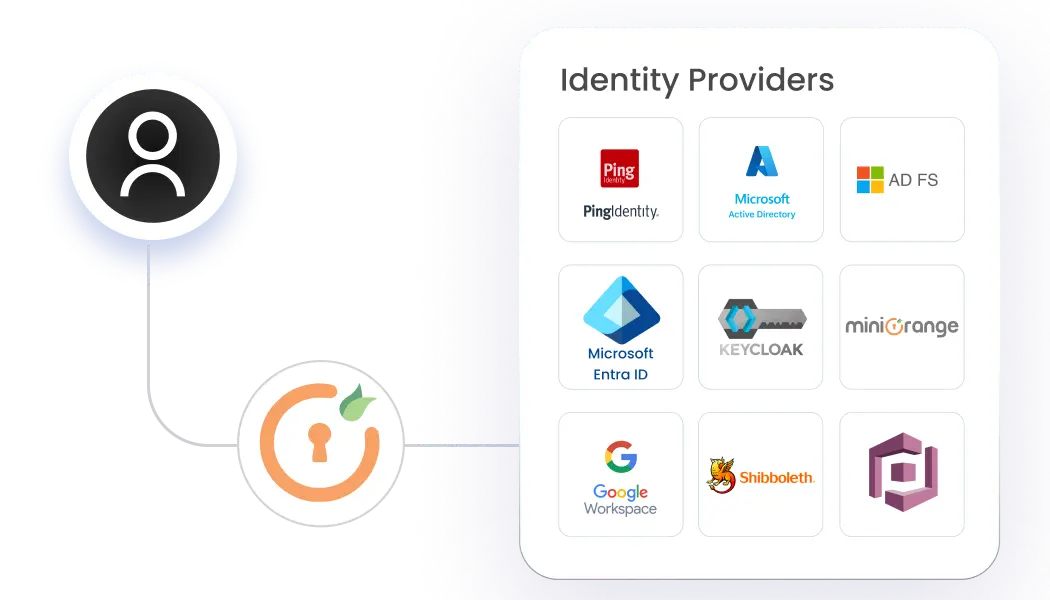
Enable secure B2B collaboration with miniOrange. Establish trust across partners and vendors using major protocols. Integrate diverse identity providers while maintaining centralized authentication policies.
Read moreWe have 6000+ pre-built integrations focusing on applications, devices, and endpoints. These include:
Explore miniOrange app Integration Catalog







Securing code repositories and customer data is paramount. IAM solutions provide controlled access to development environments, production systems, and SaaS applications, ensuring only authorized personnel can make changes or access sensitive information. This helps protect intellectual property and maintain the integrity of their services.
Managing access to vast infrastructure and numerous client environments demands robust IAM. These solutions ensure clear separation between tenants, control administrative privileges, and offer secure access for customers, maintaining the security and reliability of cloud services.
These firms often manage IT for other organizations, requiring secure access to diverse and sensitive systems. IAM solutions enable them to control consultant access, enforce the principle of least privilege across client environments, and maintain compliance with various security policies.
Handling massive amounts of subscriber data and critical network infrastructure necessitates strong IAM. These solutions secure customer accounts, control access to network elements, and manage user identities across various services, ensuring both data privacy and network stability.
Securing interconnected devices and industrial control systems is vital to prevent disruptions and ensure safety. IAM solutions manage the identities of numerous devices and users, controlling access to sensitive operational technology and preventing unauthorized interference.
Protecting proprietary AI models and the sensitive data used for training is crucial. IAM solutions control access to these valuable assets, ensuring that only authorized individuals can use or modify them, safeguarding intellectual property, and preventing misuse.











I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
miniOrange transparently integrates with your existing on-premise infrastructure, including legacy applications, Active Directory, LDAP, and enterprise systems.

Deploy robust identity security across your cloud ecosystem with pre-built integrations for hundreds of SaaS applications and major cloud providers.
Our unified identity management can tie on-premise and cloud environments, enabling seamless identity synchronization and consistent authentication experiences.
Technology companies often experience fast growth and scaling challenges that strain identity systems. Managing user onboarding during hiring surges, handling mergers and acquisitions, and accommodating project-based contractors all require flexible IAM solutions that can scale instantly without compromising security.
Tech companies typically use diverse toolsets spanning cloud services, development platforms, internal tools, and legacy systems. This creates a fragmented access landscape where each application may have its own authentication method, increasing security risks and administrative overhead when not properly integrated.
Engineering teams need secure access to sensitive systems like code repositories, CI/CD pipelines, cloud infrastructure, and production environments. Balancing developer productivity with proper security controls requires specialized IAM approaches that understand developer workflows while maintaining proper segregation of duties.
Technology workforces are increasingly distributed across multiple locations and time zones, often working remotely. This distribution complicates identity verification and requires location-aware authentication policies that don't impede legitimate work activities while preventing unauthorized access.
Managing access to infrastructure components like cloud resources, containers, databases, and server environments requires fine-grained permissions and just-in-time access protocols. Traditional IAM solutions often struggle with ephemeral resources, automated processes, and service account management.
Tech companies must navigate complex regulatory environments, such as SOC 2, ISO 27001, GDPR, and industry-specific standards. To meet these compliance requirements, IAM systems must provide comprehensive activity logs, access certifications, and separation of duties enforcement.
For compliance-conscious organizations, miniOrange offers built-in compliance controls that simplify adherence to SOC2, ISO 27001, GDPR, and comprehensive audit trails, providing detailed logging for security investigations.
miniOrange supports all standard protocols like SAML, OAuth, & OIDC while also offering pre-built connectors for custom apps, enabling tech companies to create a truly unified identity ecosystem.
miniOrange contributes to tech companies' cost efficiency by significantly reducing the IT overhead associated with routine access-related tasks, freeing up valuable IT staff time and resources.
Our solution stands out in the IAM market, offering multiple implementation models including cloud-hosted SaaS, private cloud deployments, on-premises installations, and hybrid configurations.
