Need Help? We are right here!
Search Results:
×65%
50%
40%
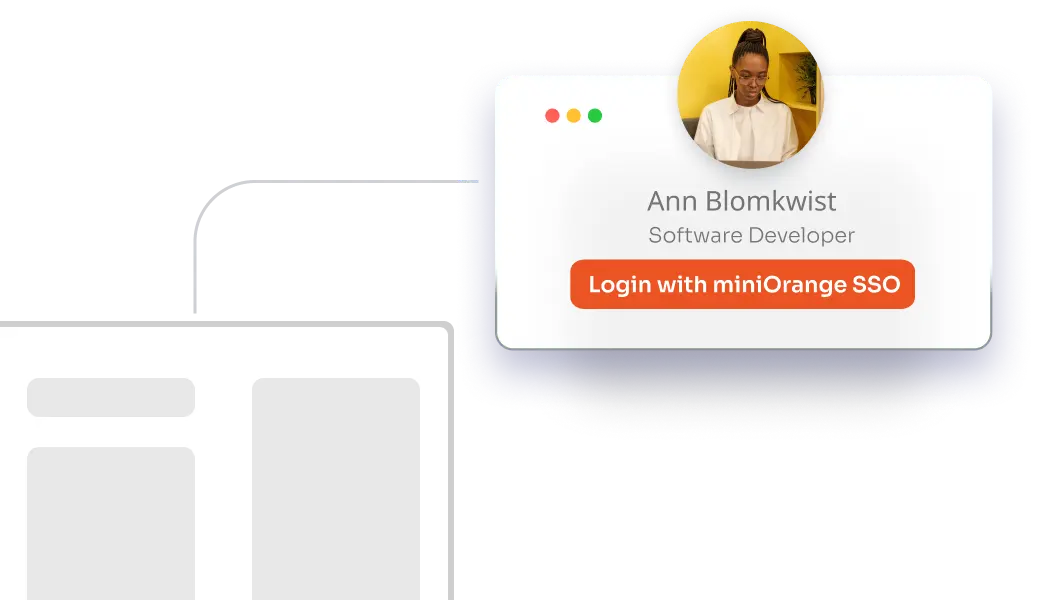
Effortless access to telecom systems with secure authentication using SAML, OAuth 2.0, and OpenID Connect.
Read more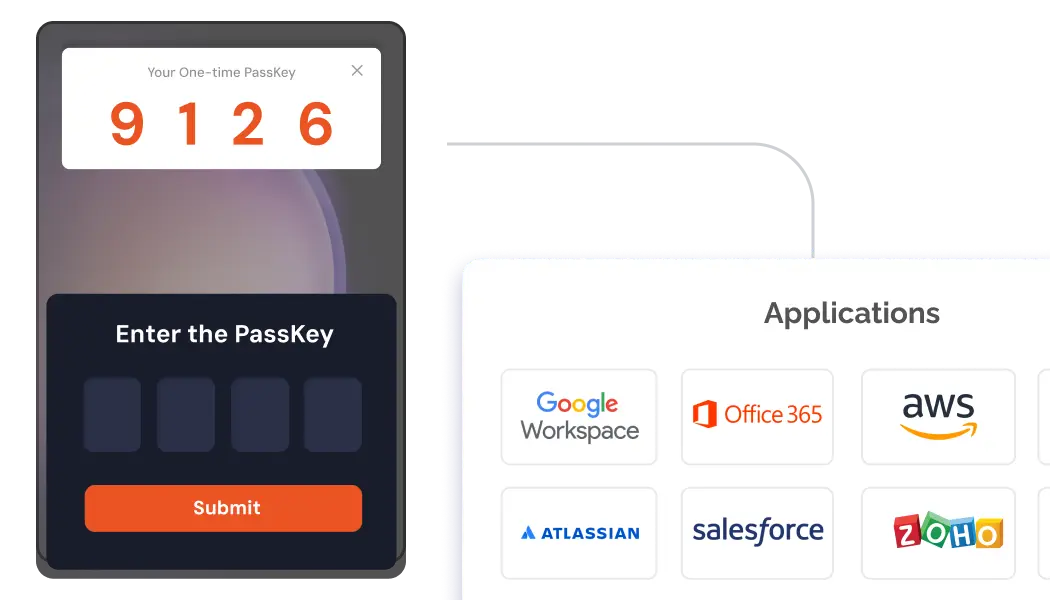
Enhance telecom security with 15+ methods like hardware tokens, biometrics, and more to prevent security breaches.
Read more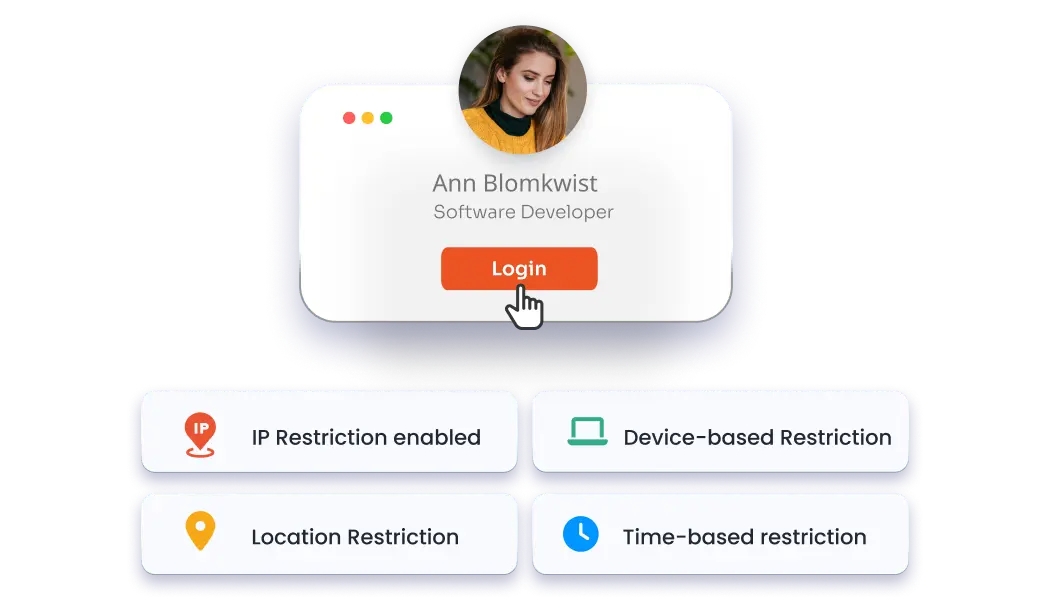
Dynamically adjust security requirements based on user behavior, device trust, and network location for intelligent risk-based access control.
Read more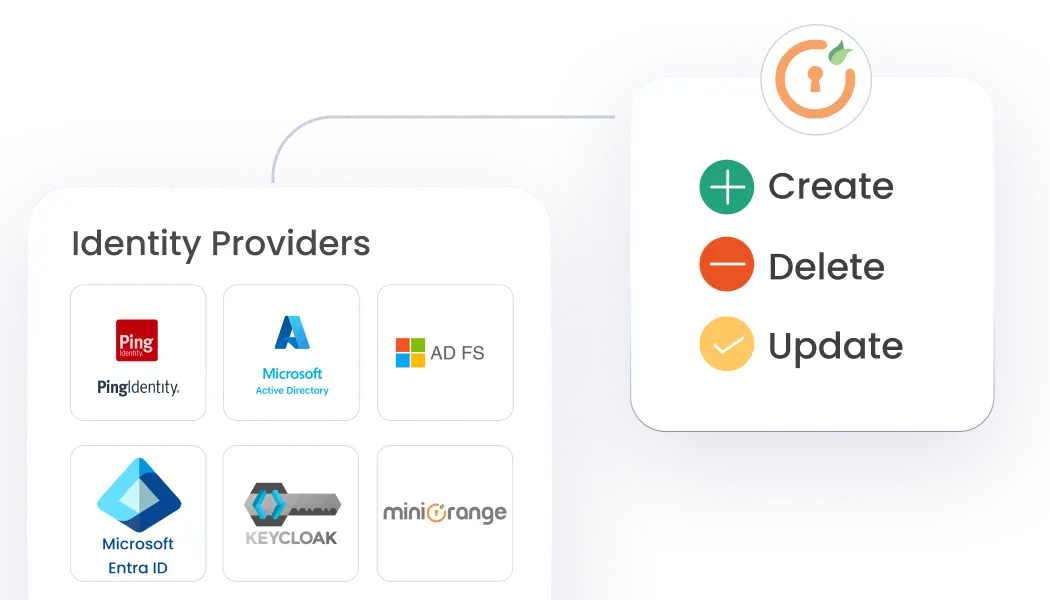
Automate user management (Joiner, Mover, and Leaver), access reviews, and role-based controls for efficient network operations.
Read more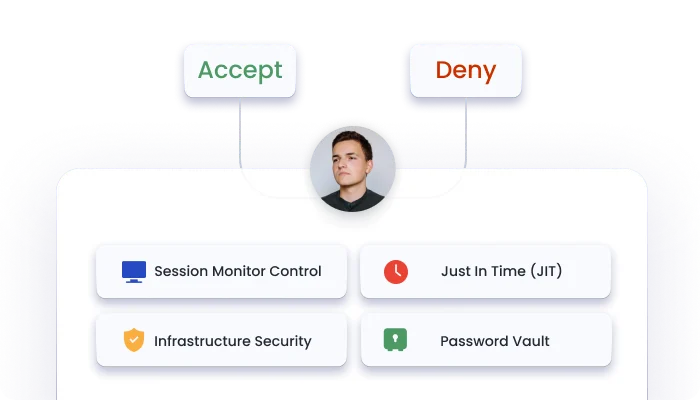
Control network engineer access with session monitor and control, just-in-time access, and 5G infrastructure protection.
Read more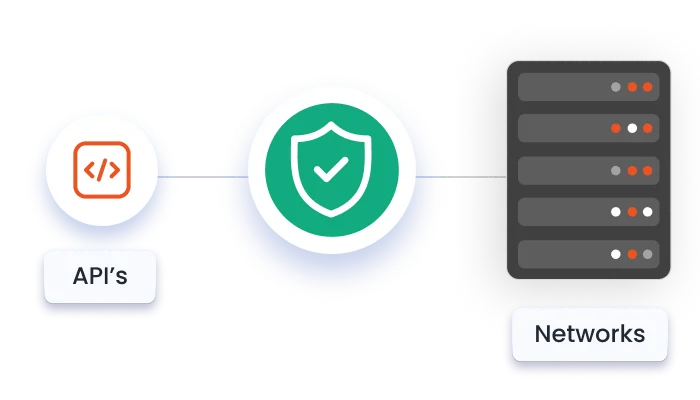
Safeguard core networks, manage BSS/OSS access, and secure telecom APIs against cyber risks.
Read more
Monitor real-time threats, analyze user behavior, and correlate security incidents for proactive defense.
Read moreWe have 6000+ pre-built integrations focusing on applications, devices, and endpoints. These include:
Explore miniOrange app Integration Catalog







Block malicious traffic through identity verification, preventing network amplification attacks with authenticated access controls.
Implement zero-trust architecture with integrated threat hunting and automated security orchestration for complete protection.
Secure network slicing through IAM controls while managing access to diverse endpoints and their authentication.
Automate regulatory compliance with detailed audit trails, access reviews, and comprehensive compliance reporting systems.
Safeguard network operations with privileged access management, real-time session monitoring, and emergency procedures.










I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
Launch miniOrange IAM directly on major cloud platforms with guaranteed uptime and automatic scaling for peak traffic.

Keep all authentication data within your own data centers for maximum control over sensitive telecommunications and customer information.
Combine cloud flexibility with on-premise security, perfect for telecom operators managing both legacy systems and modern applications.
Modern cybercriminals deploy AI-powered phishing campaigns and zero-day exploits specifically designed to target telecom protocols. Supply chain compromises through compromised network equipment firmware create persistent backdoors.
Telecommunications providers must navigate multi-jurisdictional compliance requirements, from GDPR to state-level privacy laws. The cybersecurity mandates require constant adaptation of security frameworks while maintaining operational efficiency.
Critical telecommunications infrastructure often relies on decades-old authentication systems and unpatched network elements. These legacy components use insecure protocols and lack encryption capabilities, creating vulnerable entry points.
Managing security across extensive vendor ecosystems, roaming partners, and cloud providers creates potential attack surfaces. Inadequate contractor access controls and security standards can expose teleco networks to breaches.
Our identity-centric security approach eliminates credential-based breaches and prevents lateral movement across telecommunications infrastructure, protecting critical assets from advanced persistent threats.
Automated identity governance and policy enforcement reduce manual security tasks by 85%, freeing IT teams to focus on strategic initiatives rather than routine access management.
Consolidating multiple security tools into a unified IAM platform eliminates redundant licensing costs and reduces operational complexity, reducing the total cost of cybersecurity ownership.
Superior reliability ensures 99.99% network uptime through robust authentication services that protect revenue-generating telecommunications services from cyber disruptions that could impact customer satisfaction.
