Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×miniOrange's ServiceNow Single Sign-On (SSO) solution enables seamless access to your ServiceNow application using a single set of credentials, simplifying the login process across multiple applications. With ServiceNow SSO integration by miniOrange, you can leverage federated identity and connect all your applications, including ServiceNow CRM, using a unified set of credentials. In addition to SSO, miniOrange provides robust IAM features for ServiceNow, empowering organizations to secure access to their ServiceNow instance and efficiently manage user access. Benefit from enhanced security, streamlined user management, and a seamless login experience by implementing miniOrange's ServiceNow SSO solutions and best practices.
With miniOrange ServiceNow SSO, you can:
miniOrange offers free help through a consultation call with our System Engineers to Install or Setup ServiceNow SSO solution in your environment with 30-day free trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you in no time.
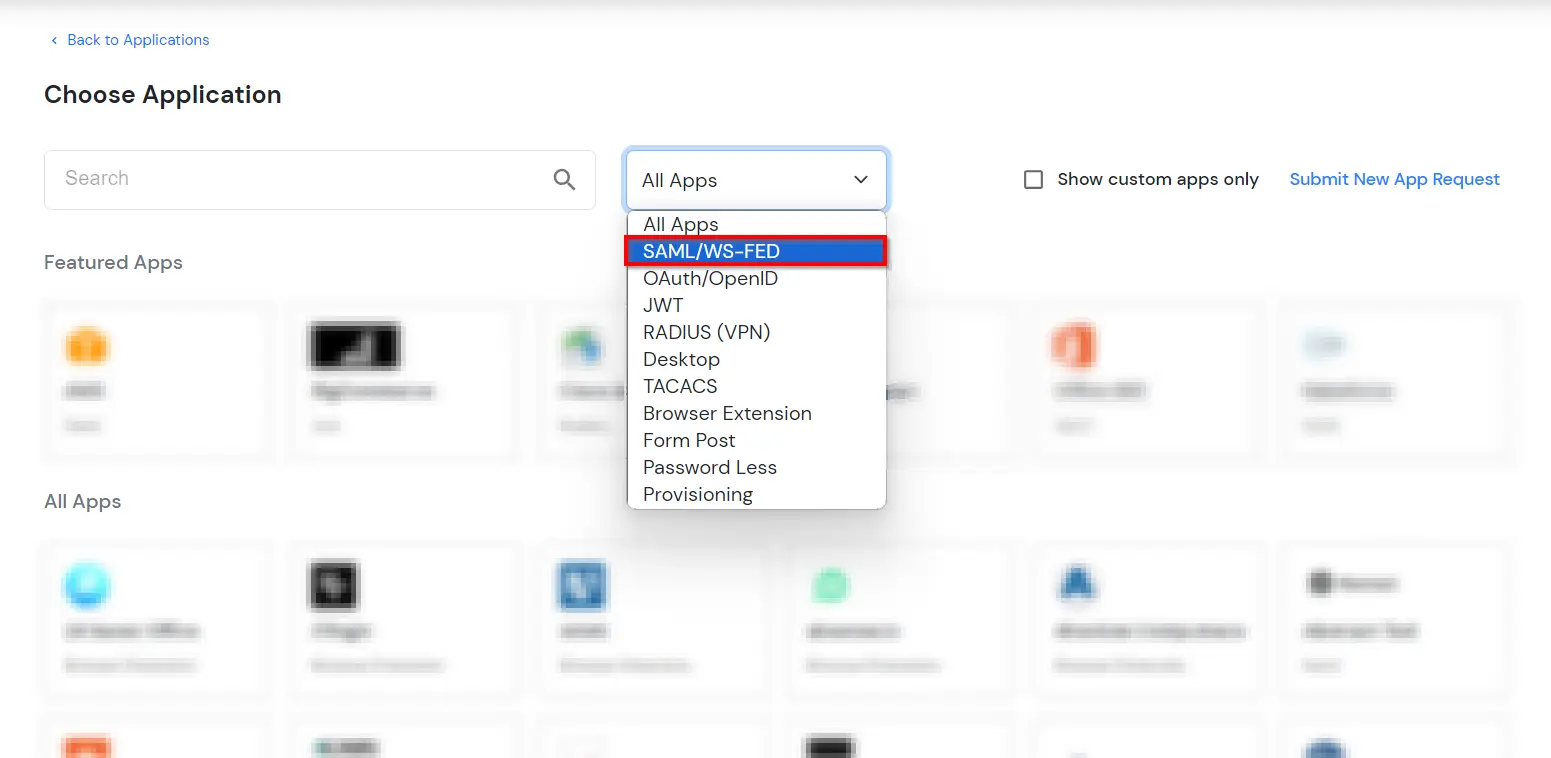
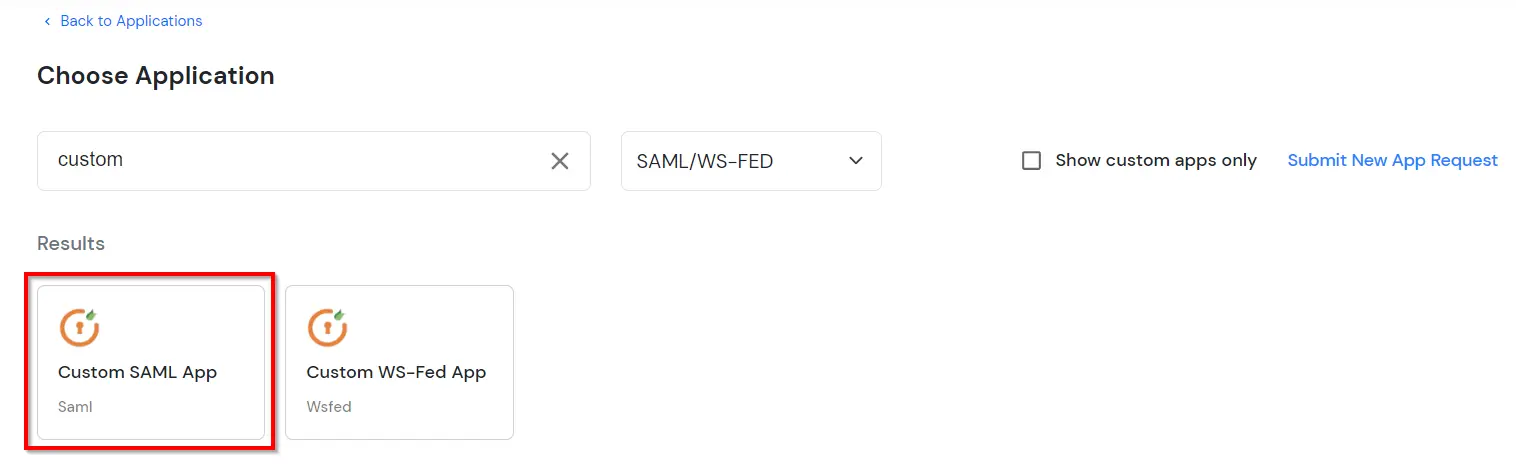
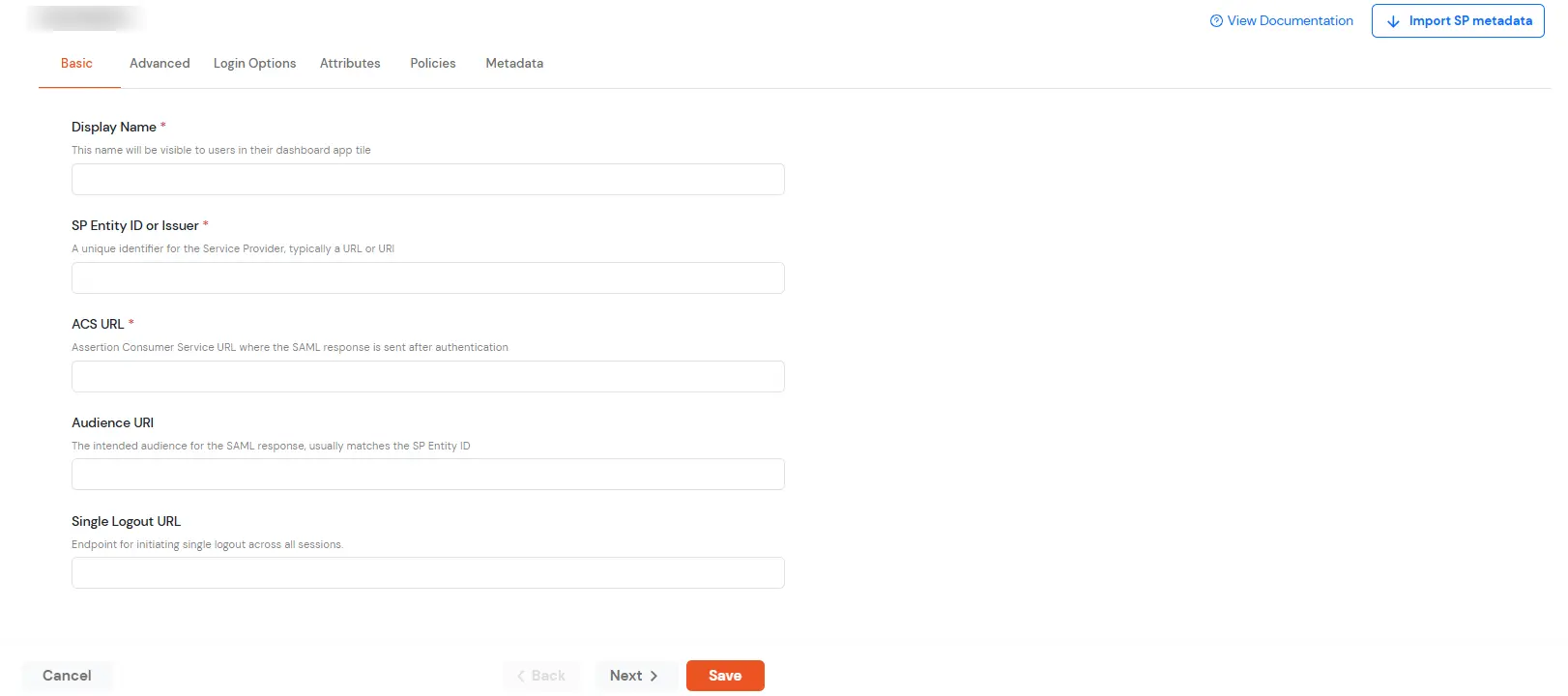
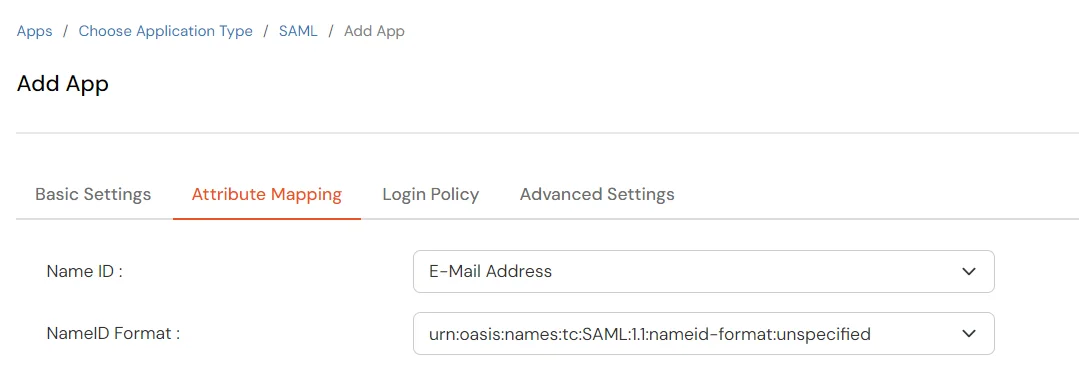
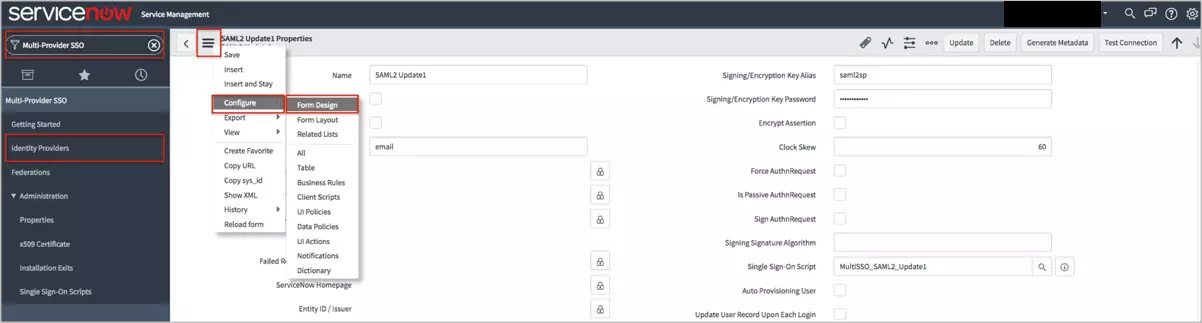
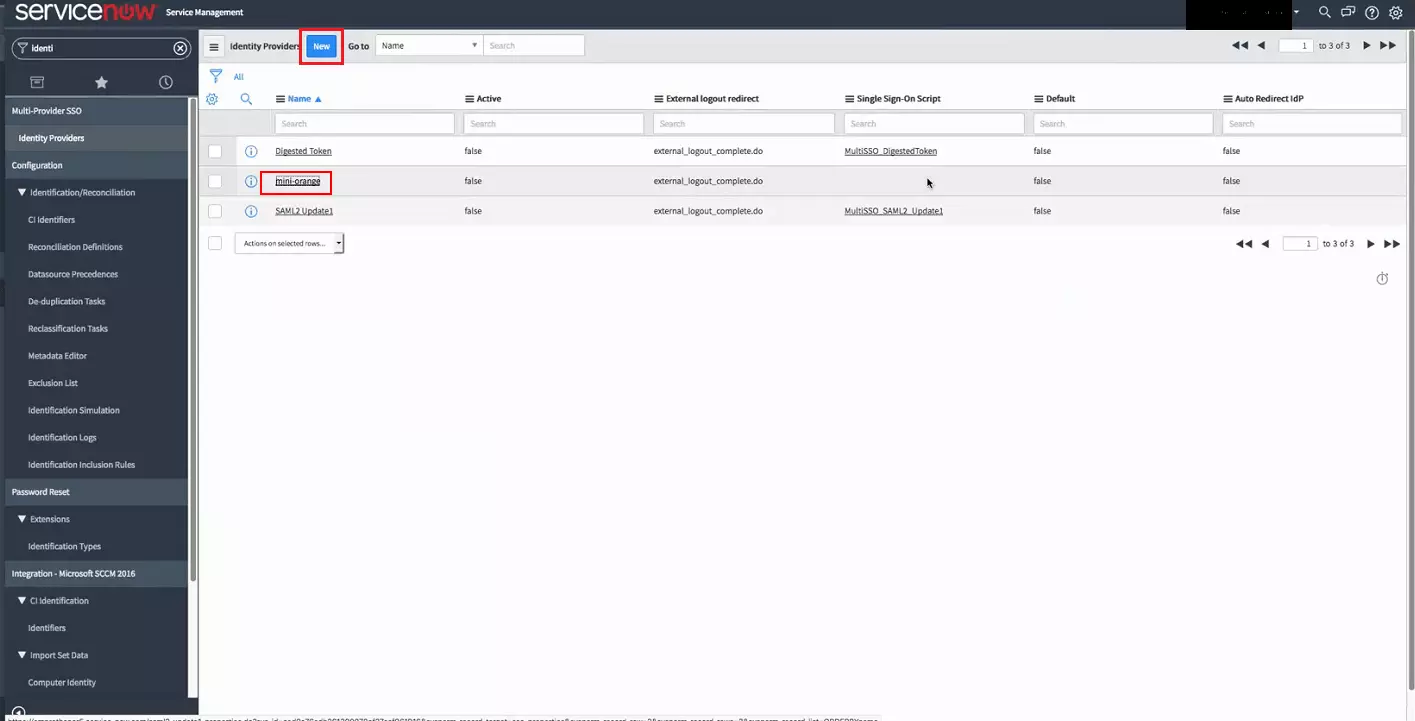
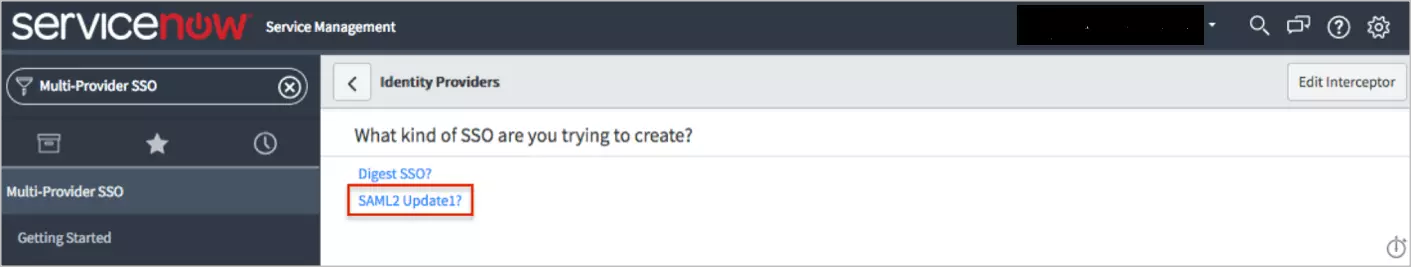
miniOrange ServiceNow SAML integration supports the following features:
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.

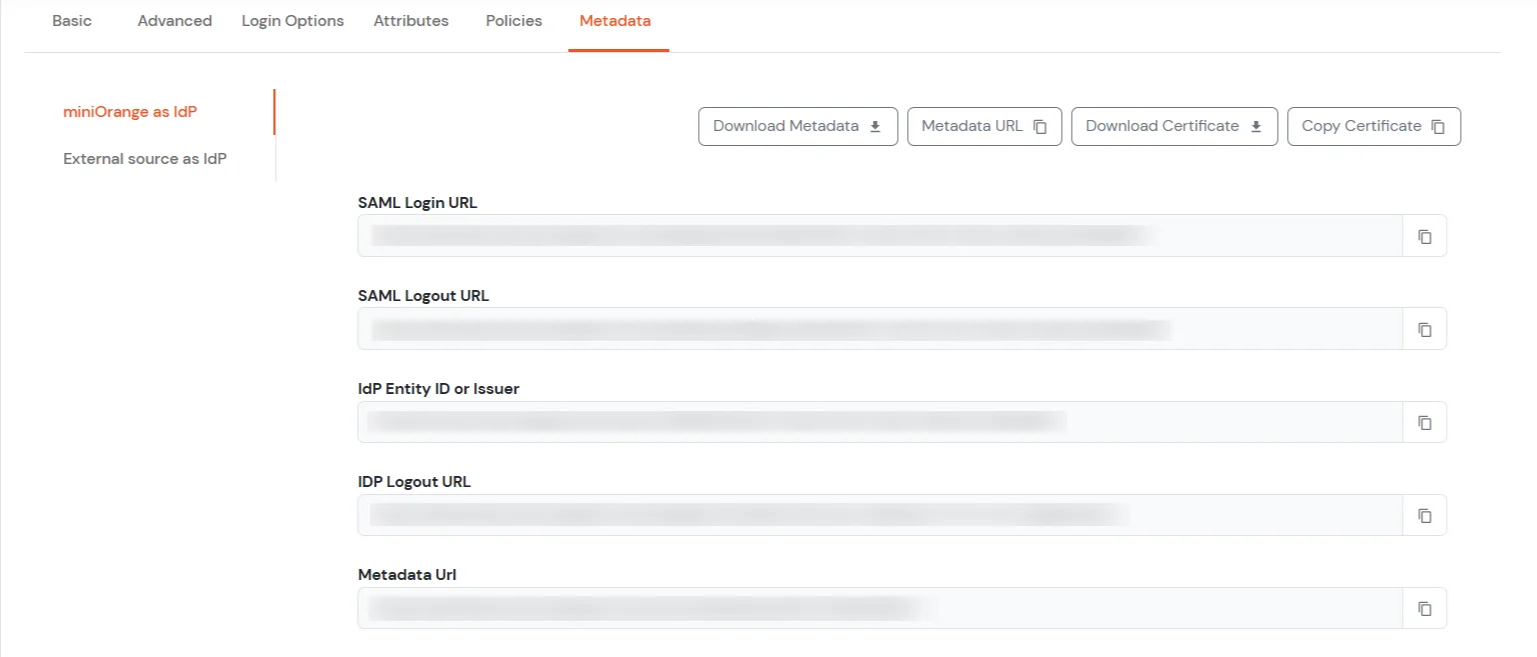
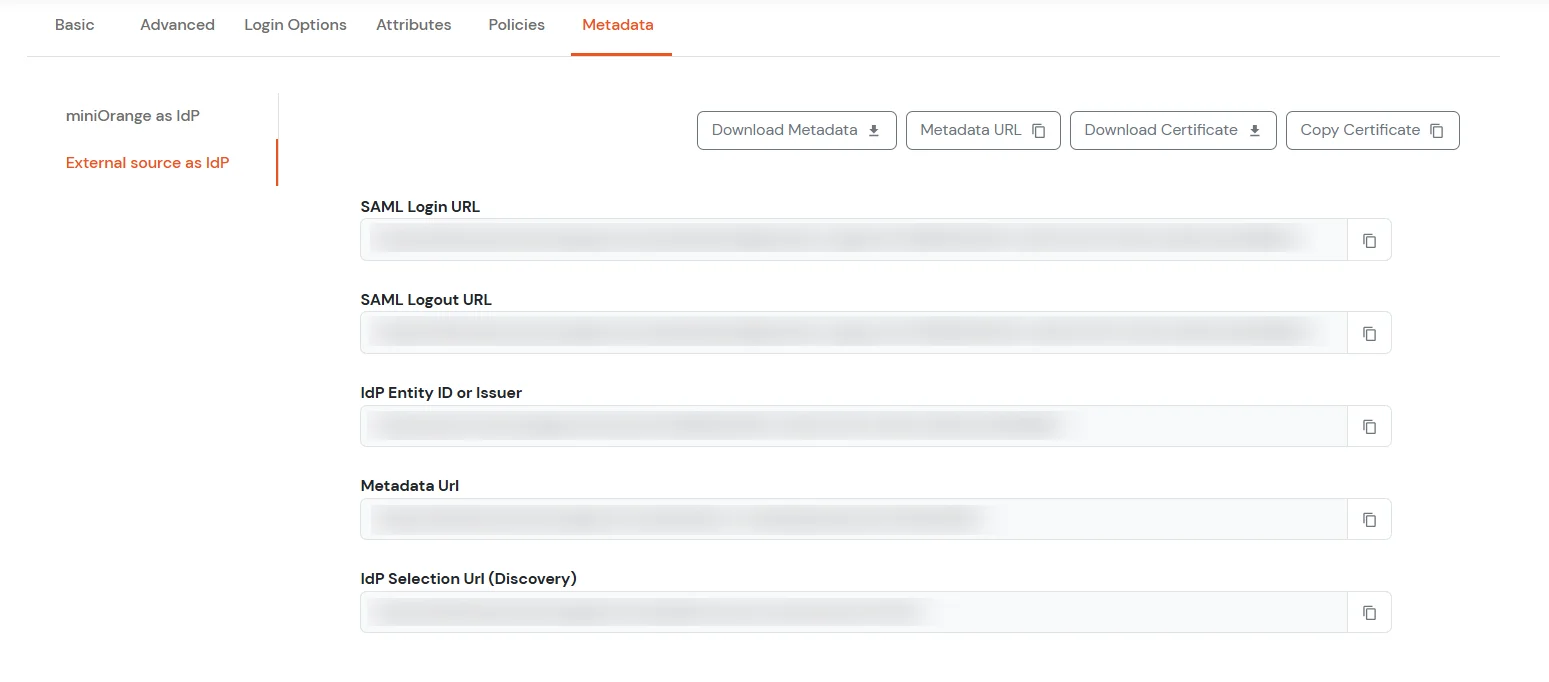
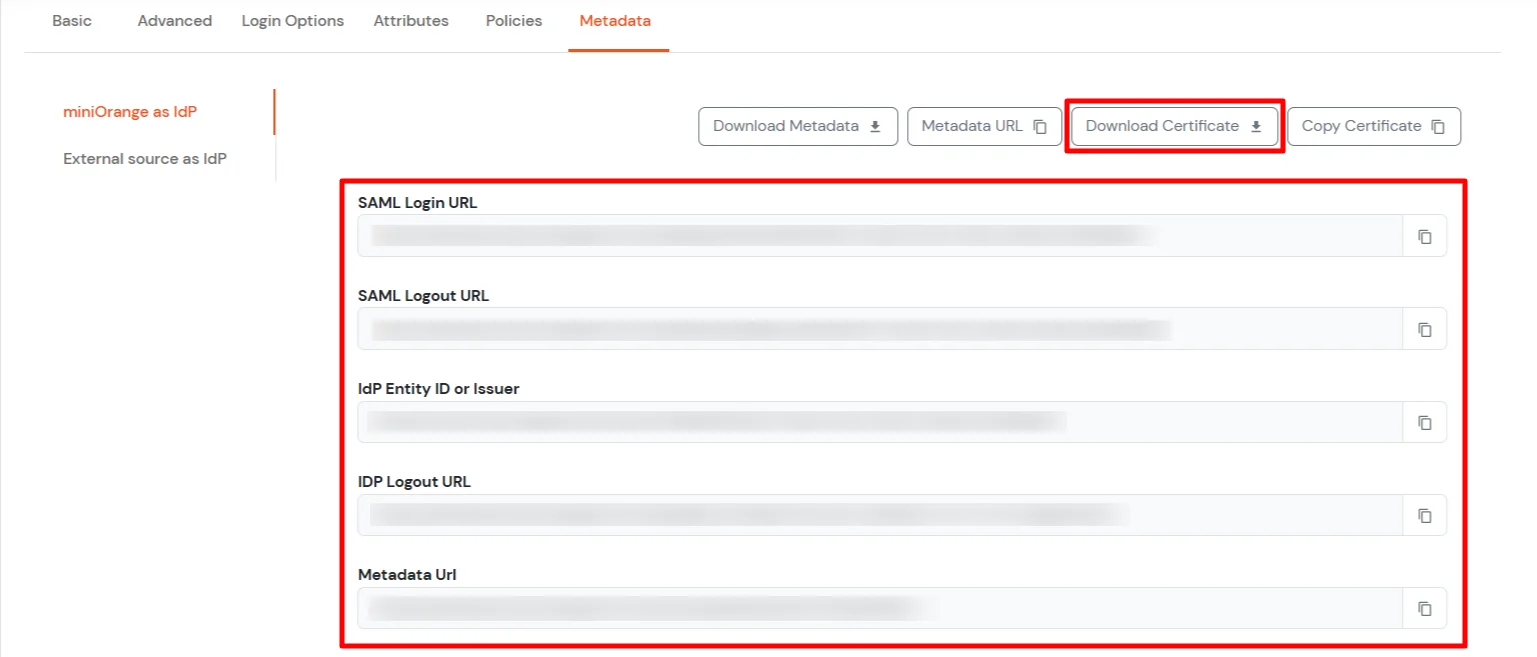
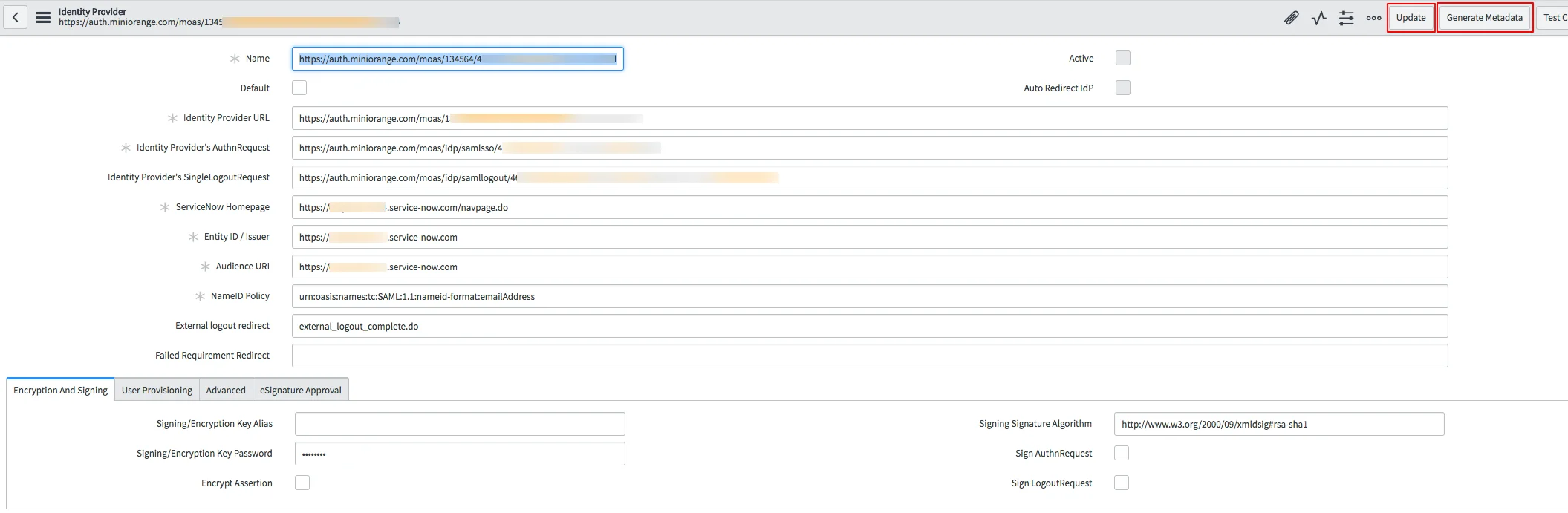
-----BEGIN CERTIFICATE-----
[your X509Certificate value]
-----END CERTIFICATE-----
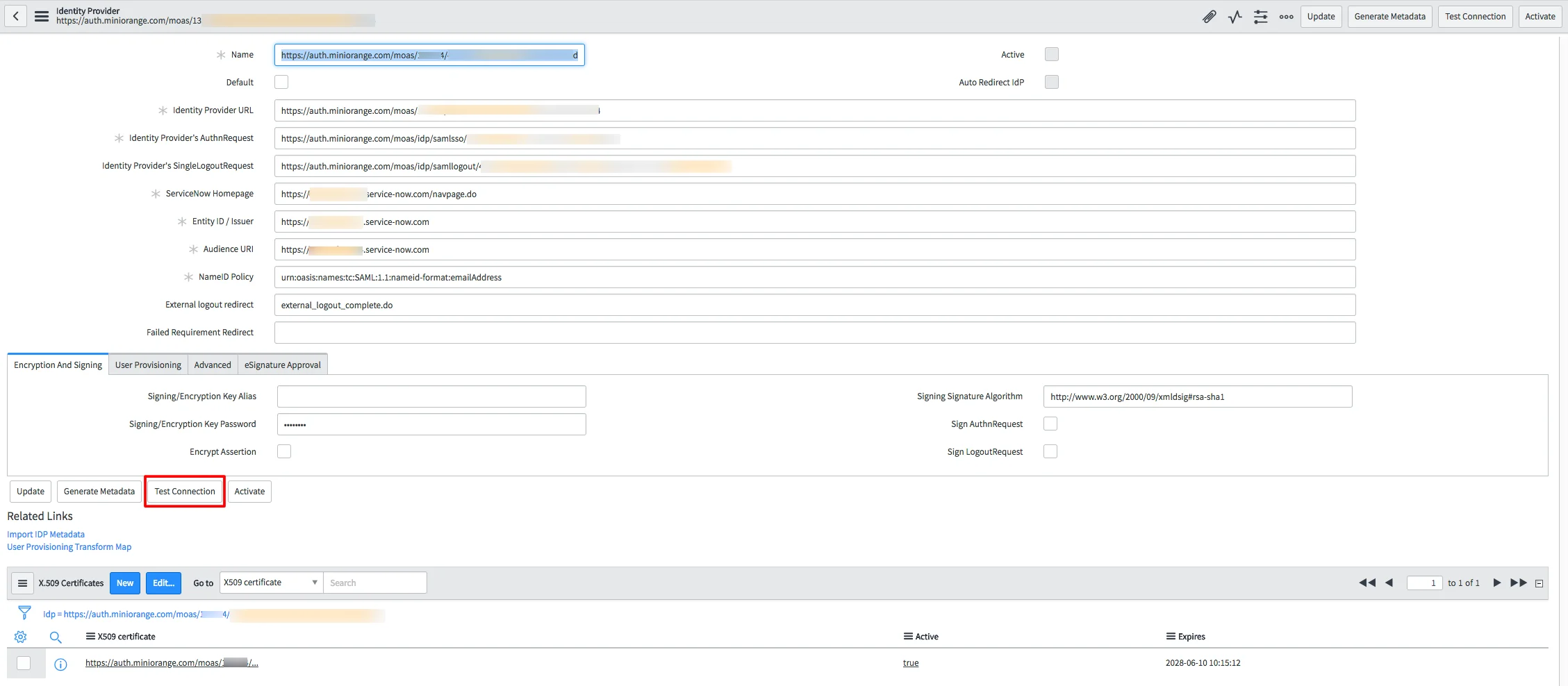

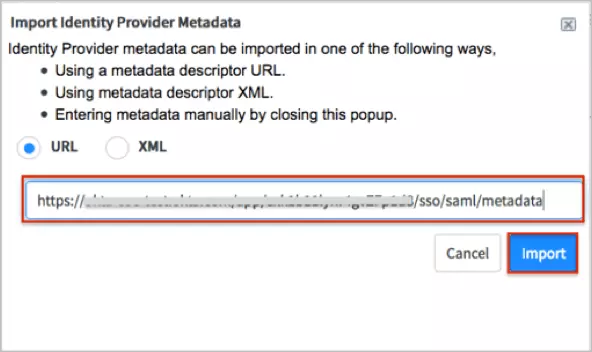
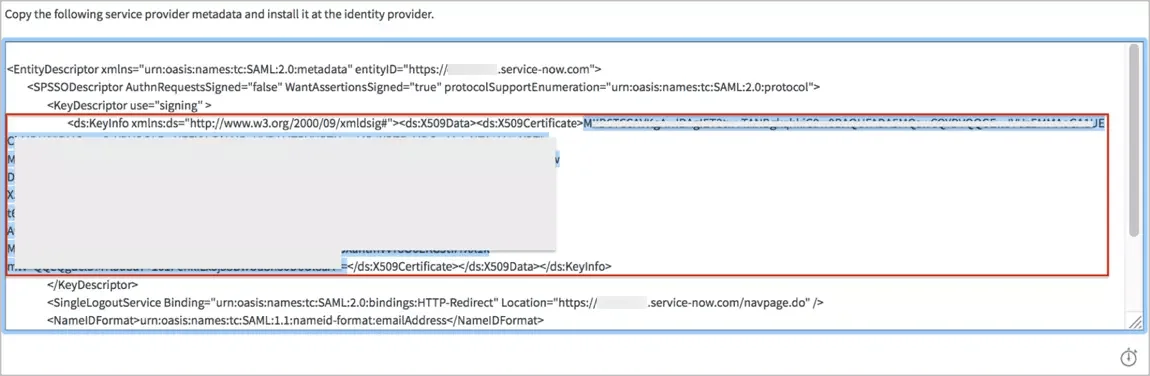
Note : It may requires removing Identity Provider's SingleLogoutRequest field value on IdP record for a successful Test Connection like below:
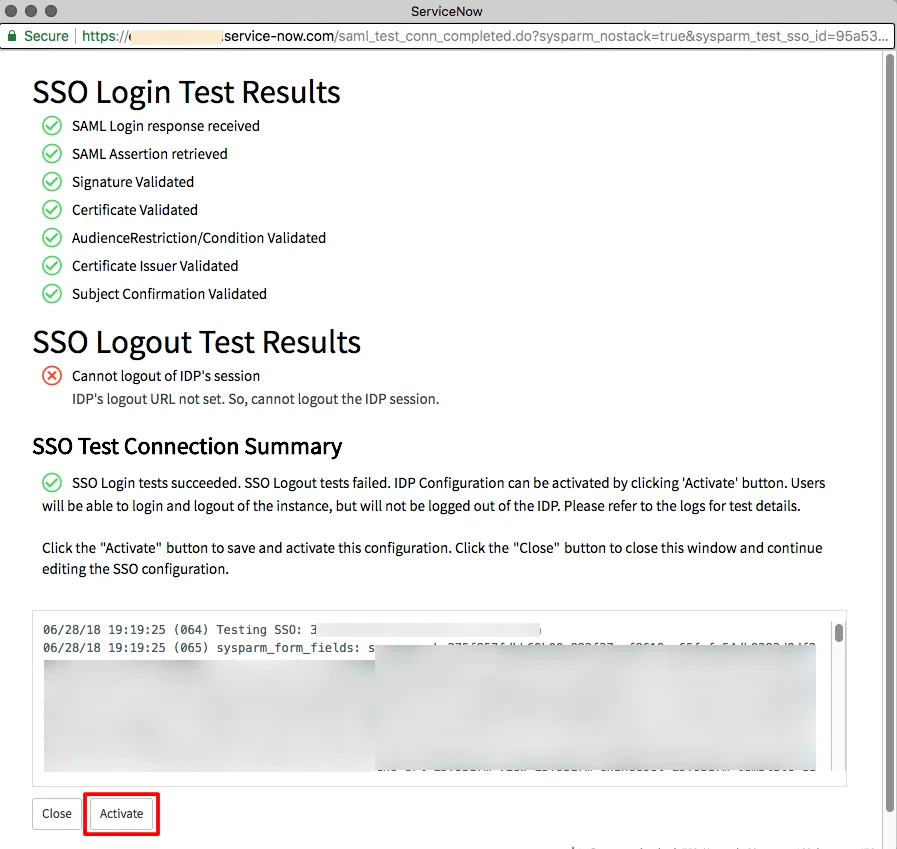
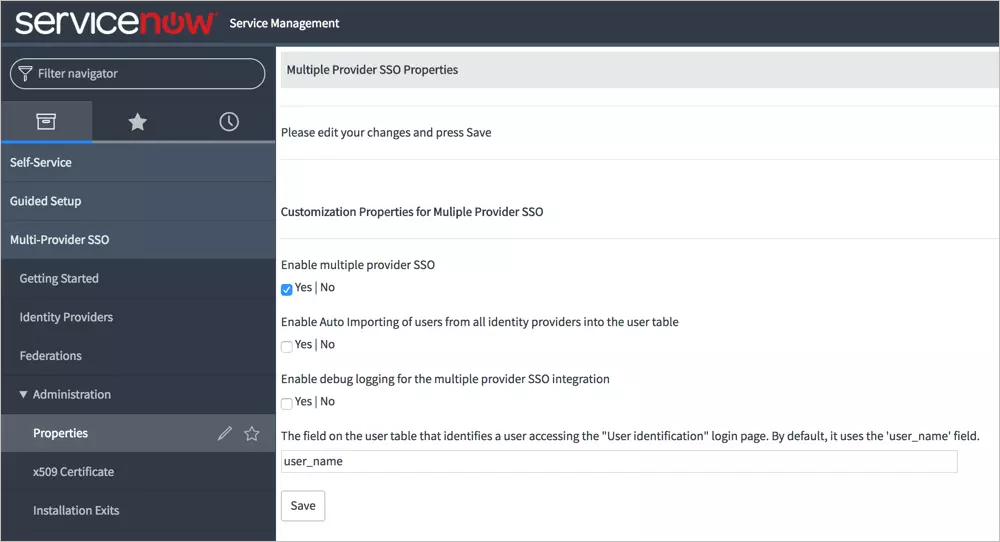
Test SSO login to your ServiceNow account with miniOrange IdP:



Contact us or email us at idpsupport@xecurify.com and we'll help you setting it up in no time.
miniOrange offers a 30-day free trial along with consultation and setup assistance from their system engineers. They provide detailed configuration guides and metadata to help successfully integrate ServiceNow SSO with your identity provider.
The solution supports a broad range, including Active Directory, ADFS, OpenLDAP, Microsoft Entra ID, Okta, AWS, and more.
