Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
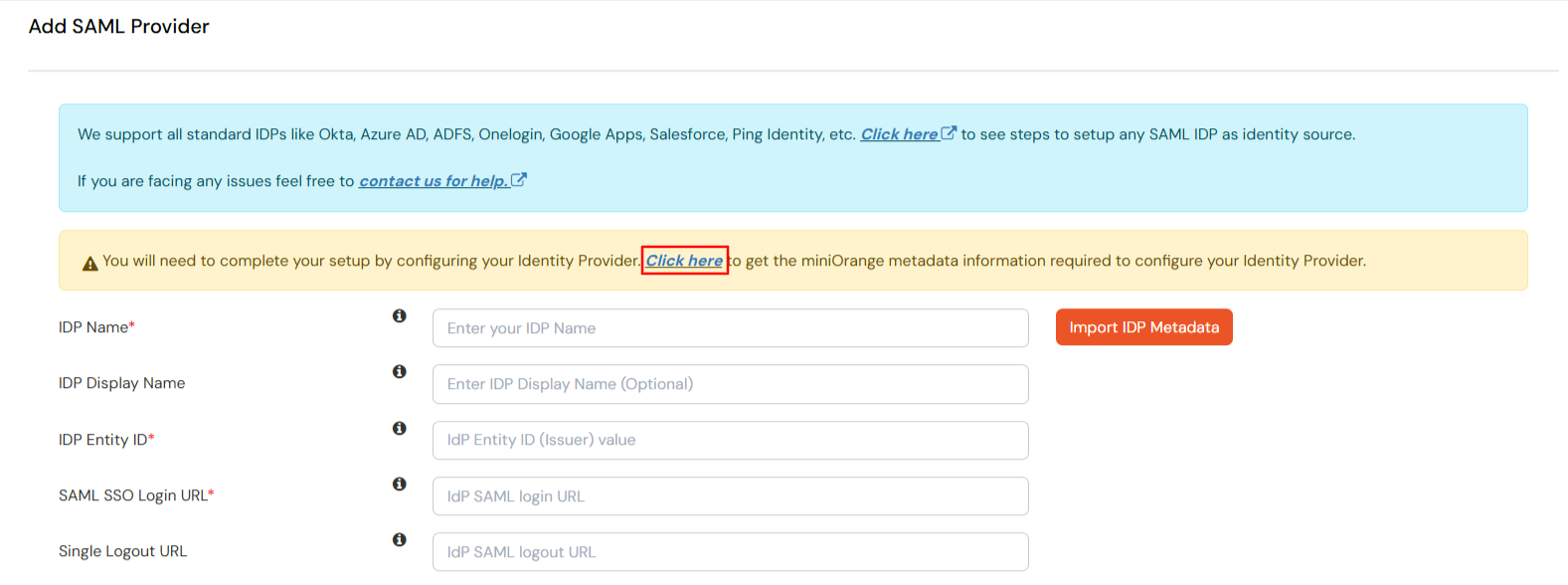
×miniOrange Identity Broker service solution enables cross protocol authentication. You can configure Rippling as an IDP for Single Sign-On (SSO) into your applications/websites. Here, Rippling will act as an Identity Provider (IDP) and miniOrange will act as a broker.
We offer a pre-built solution for integrating with Rippling, making it easier and quick to implement. Our team can also help you set up Rippling as SAML IDP to login into your applications.
miniOrange offers free help through a consultation call with our System Engineers to configure SSO for different apps using Rippling as IDP in your environment with 30-day free trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you in no time.
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.
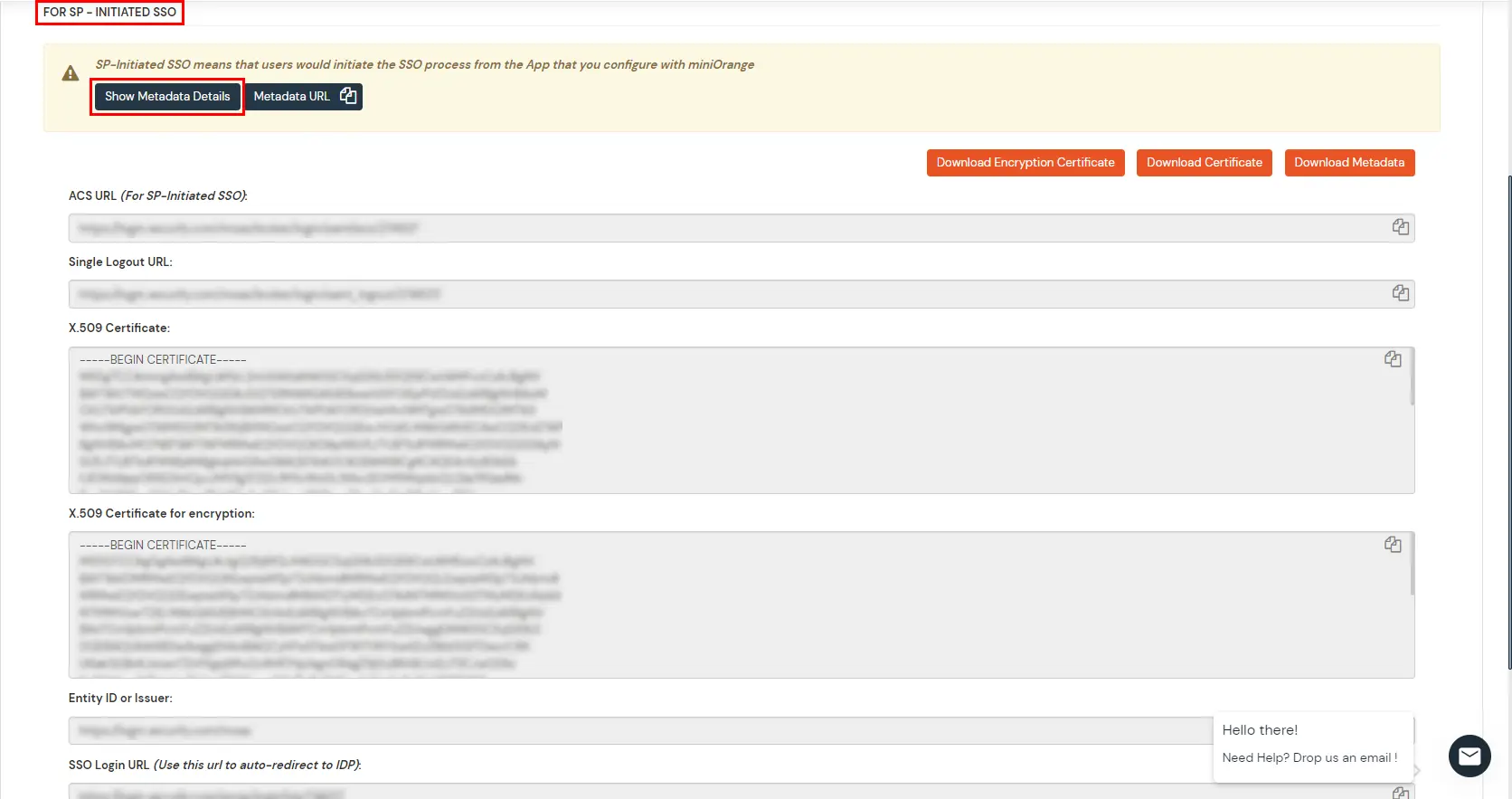
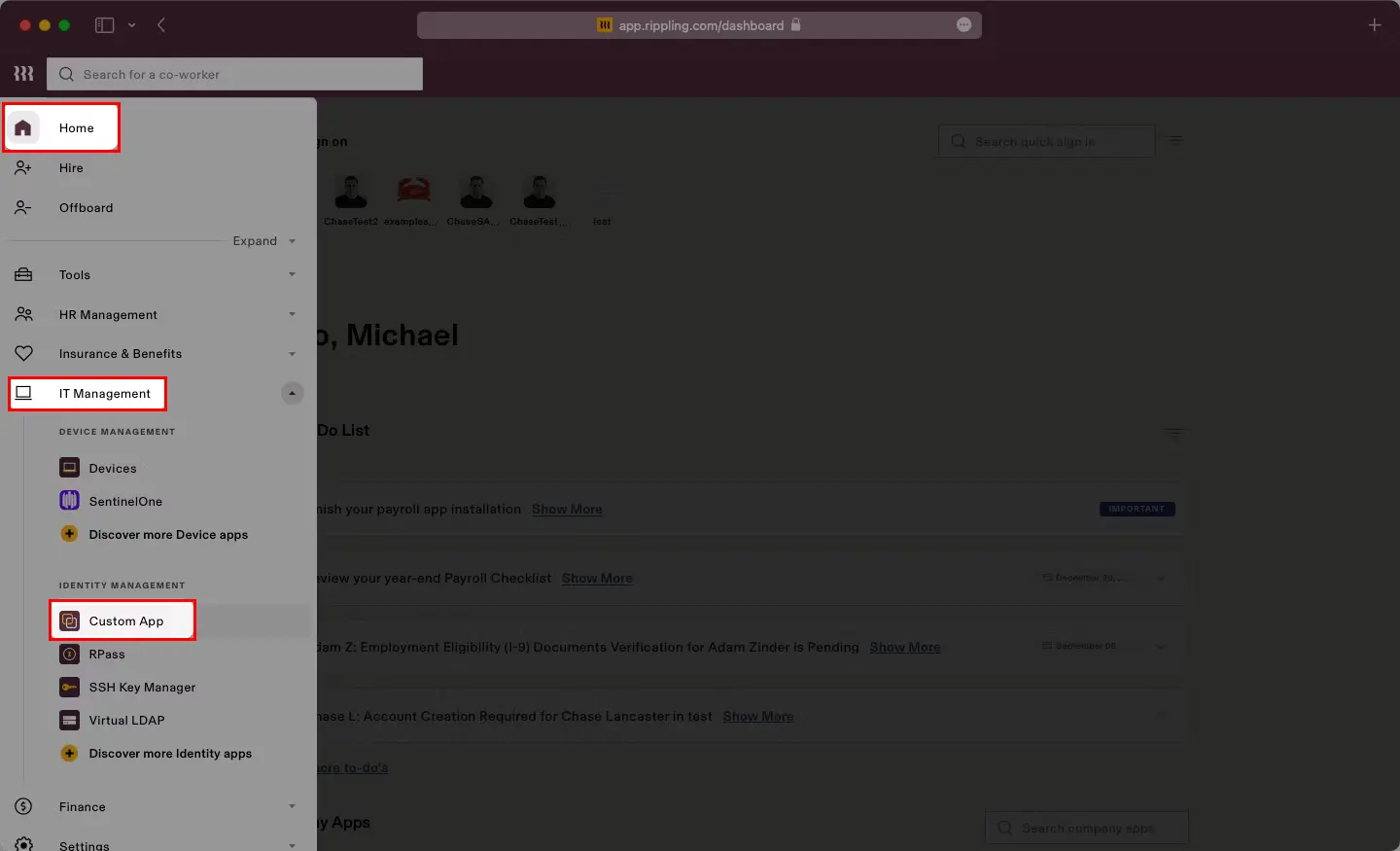
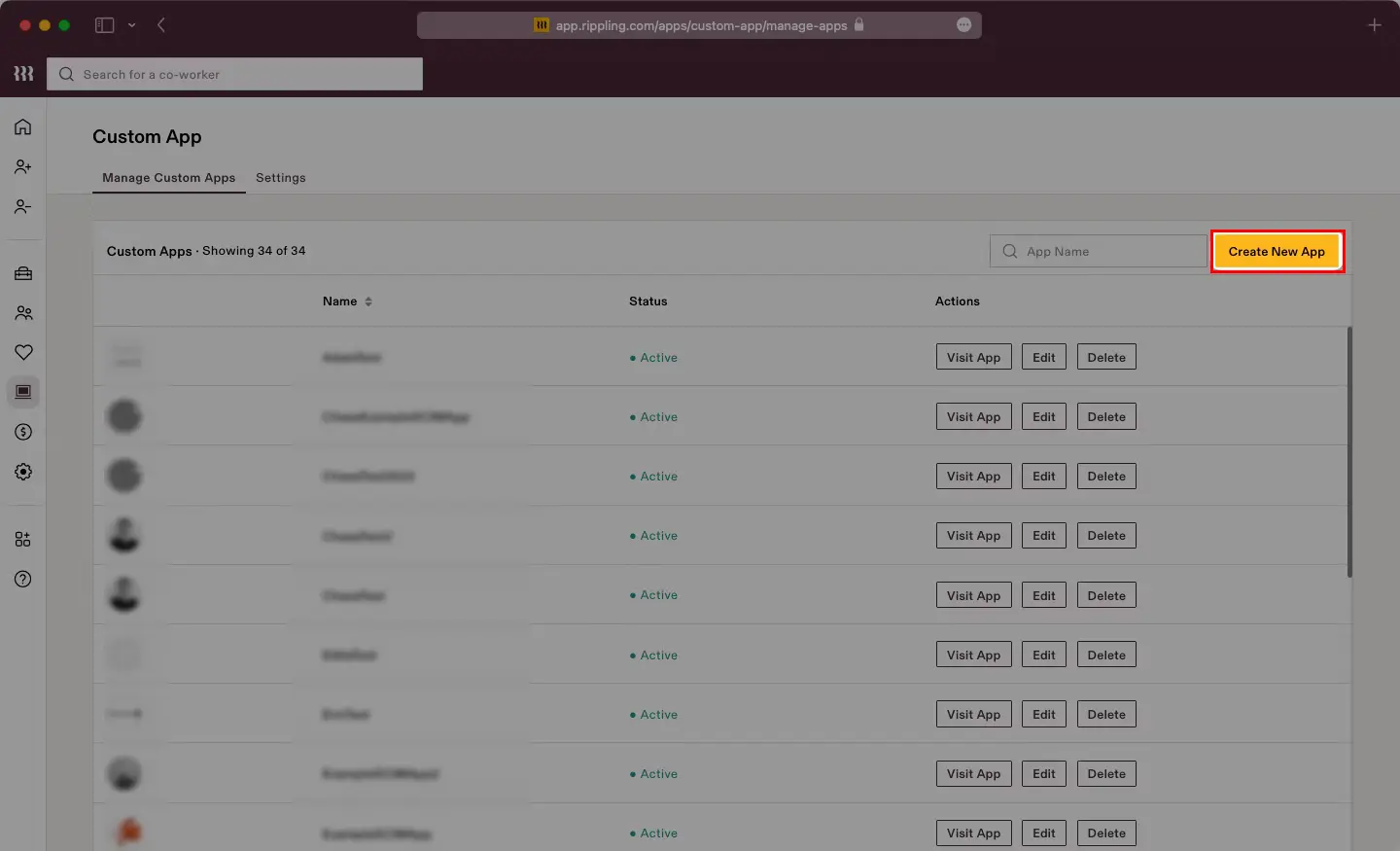
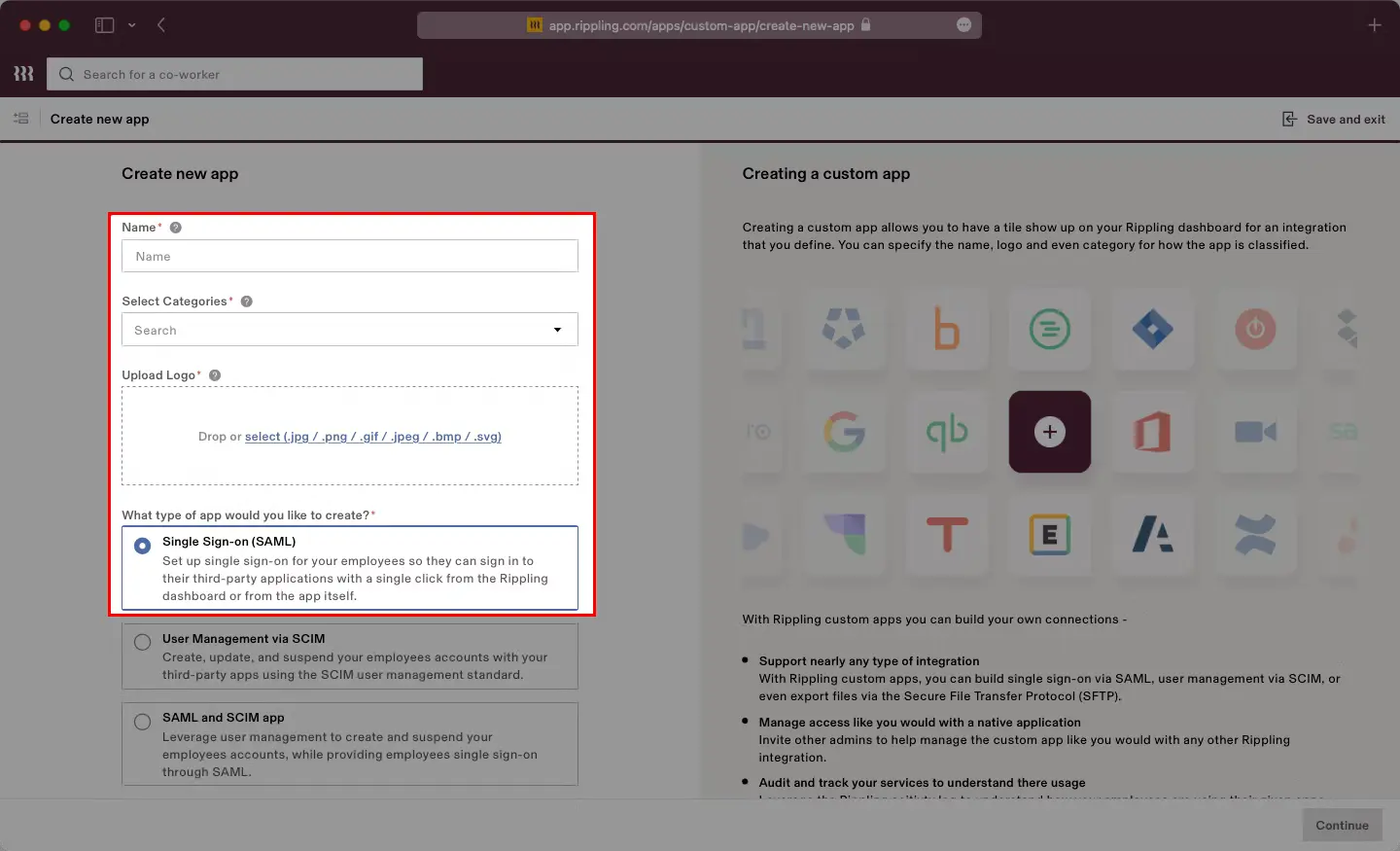
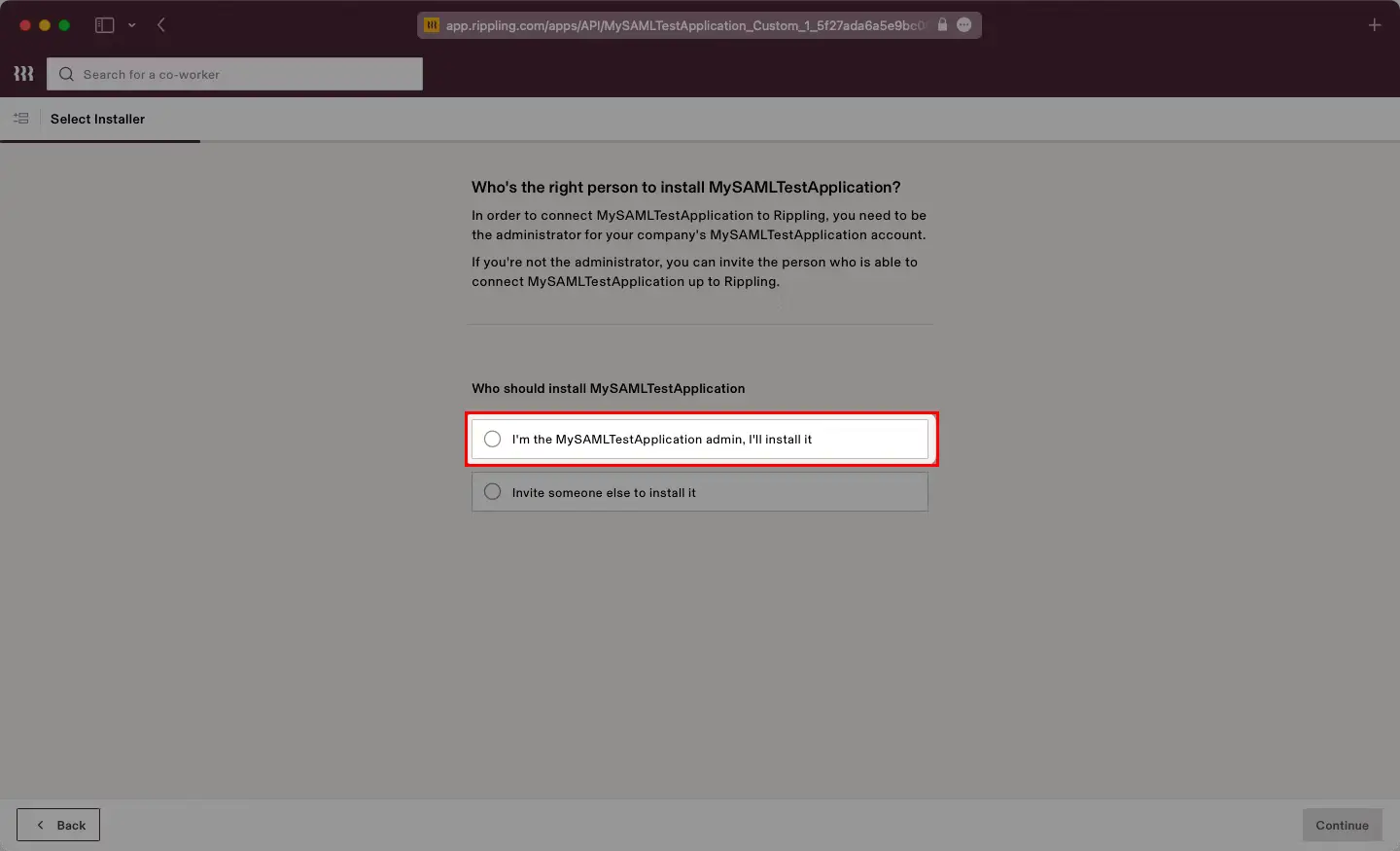
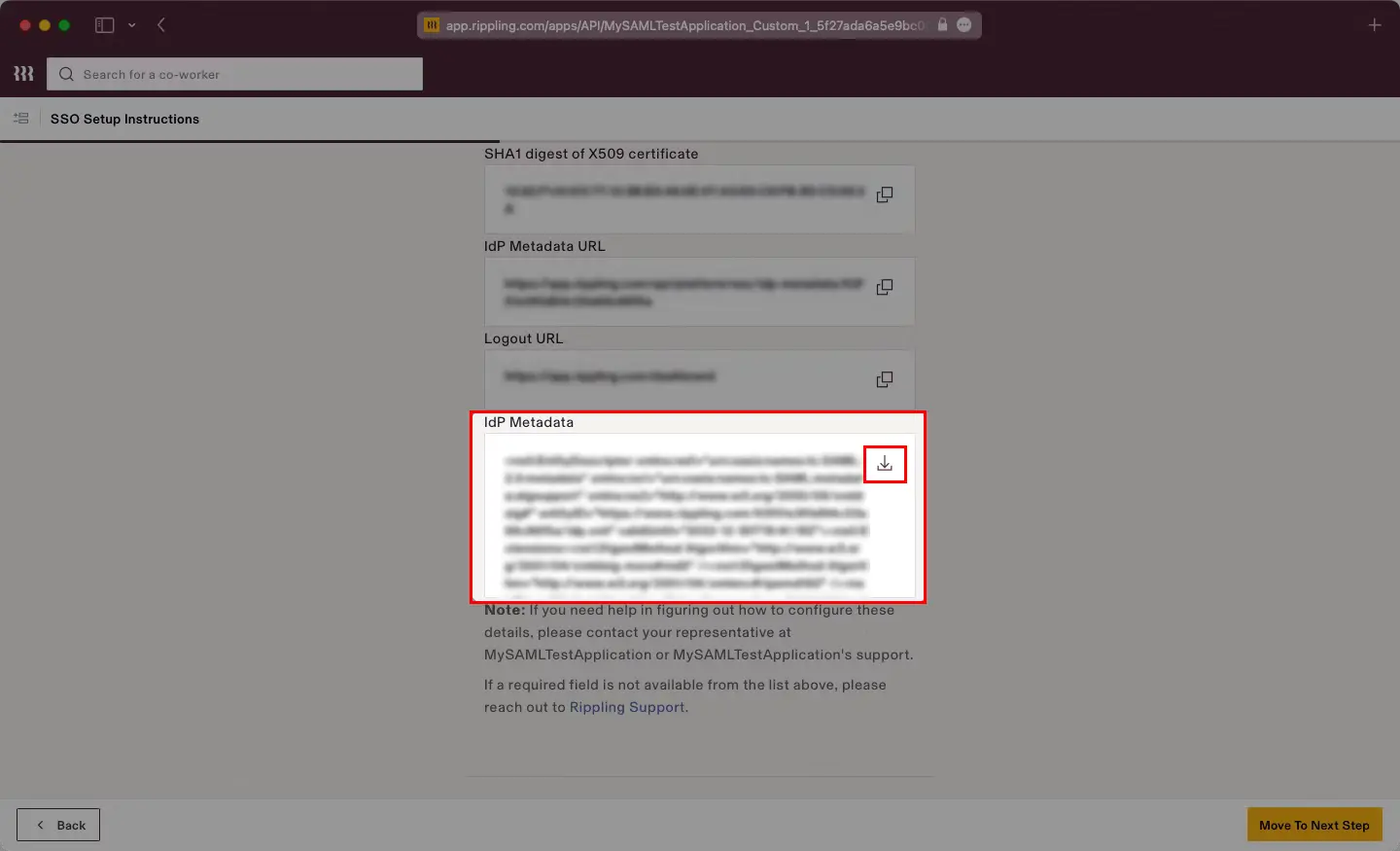
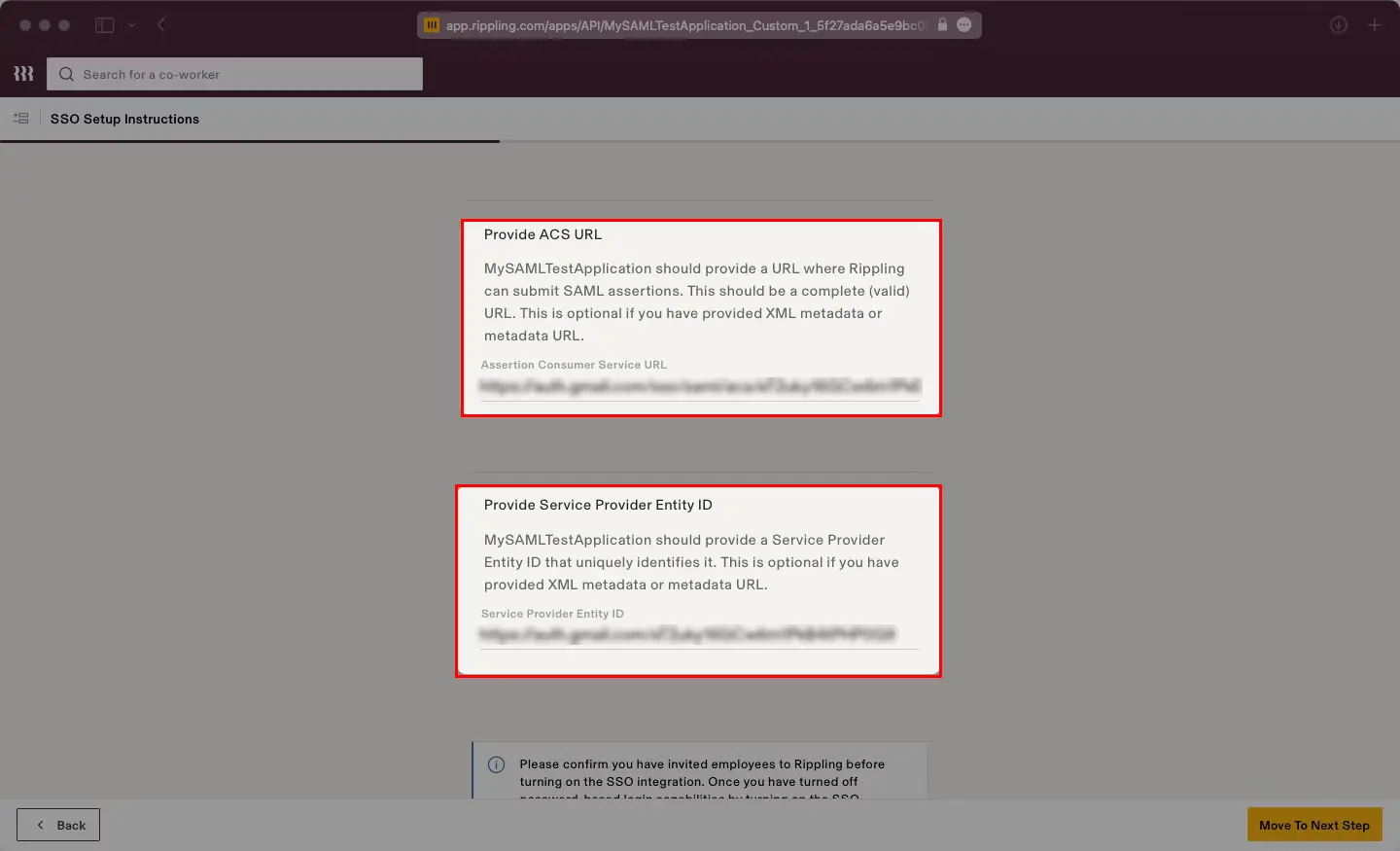
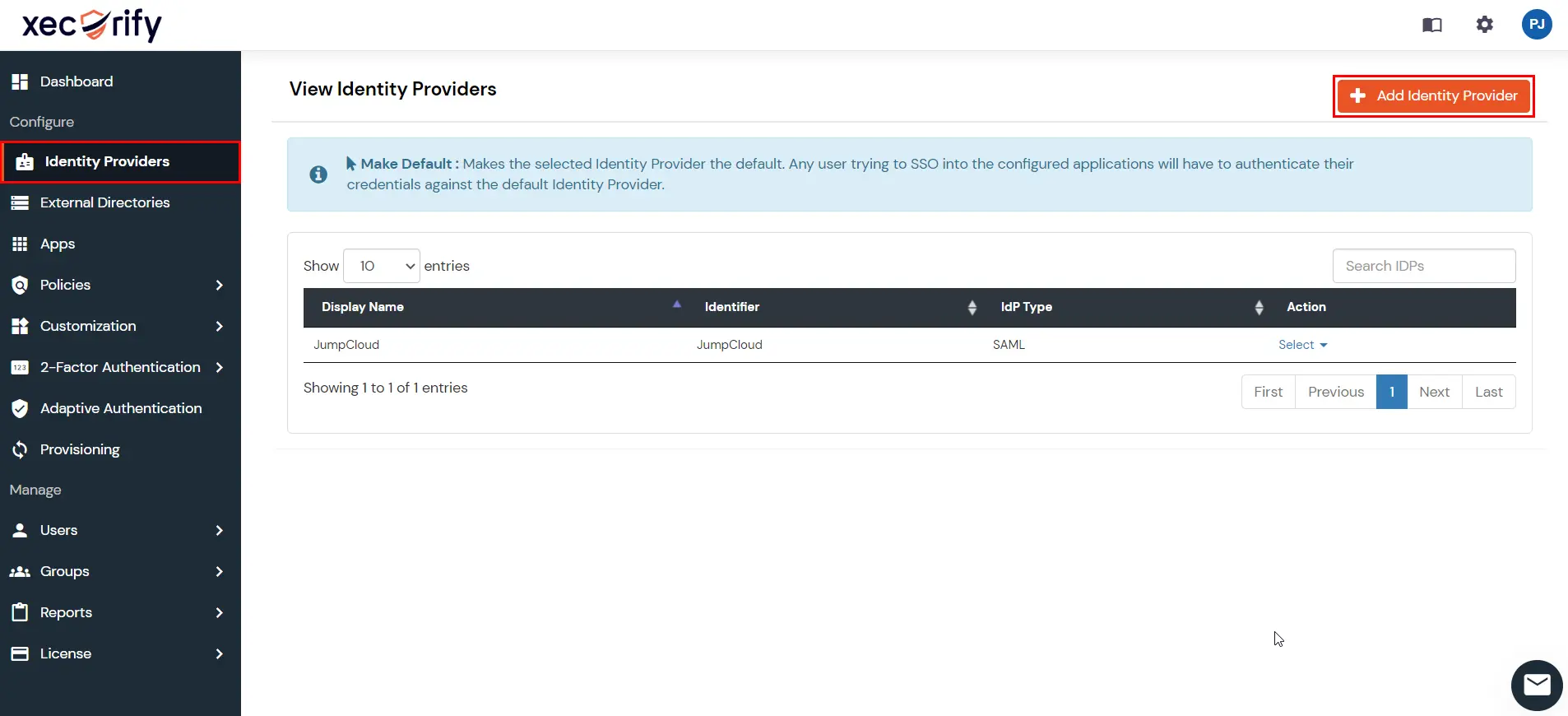
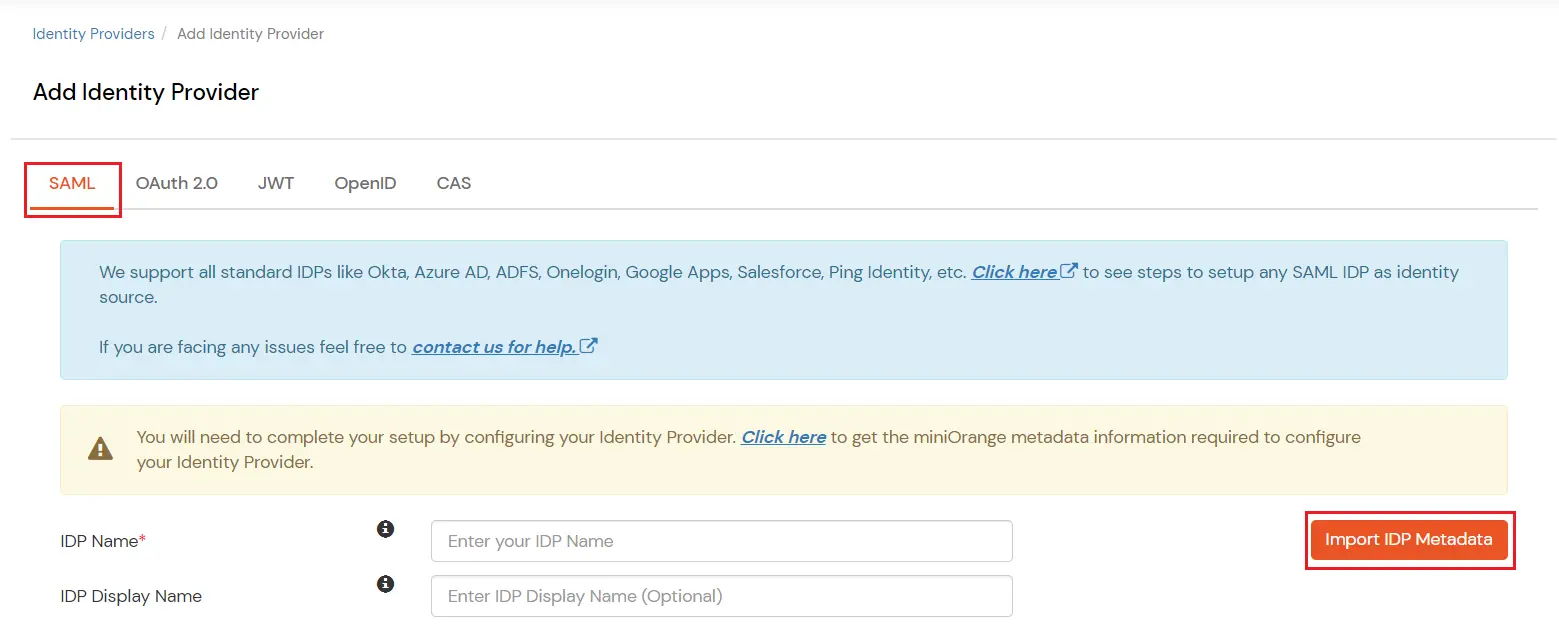
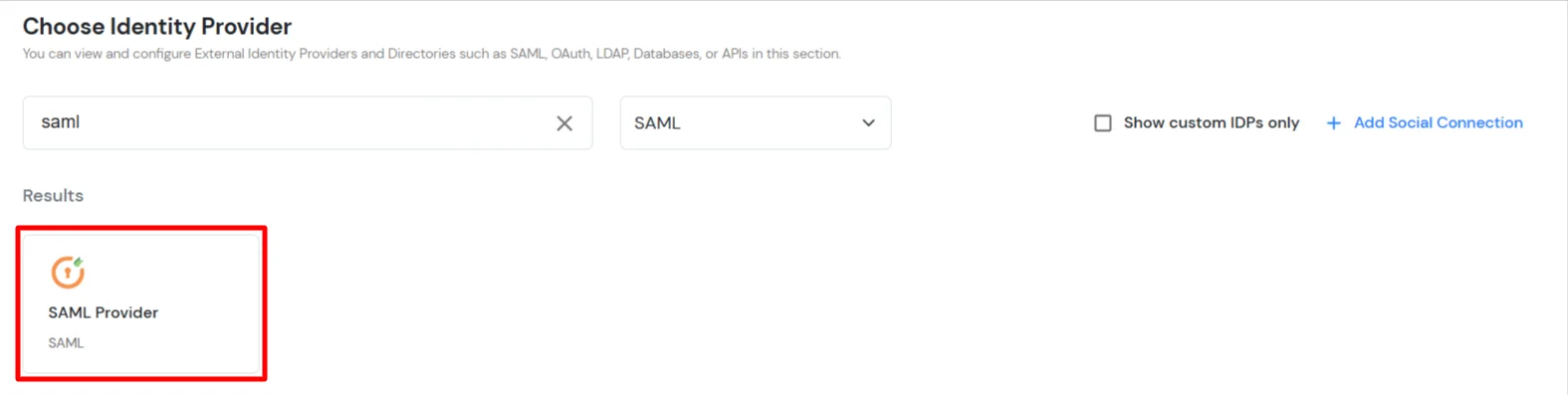
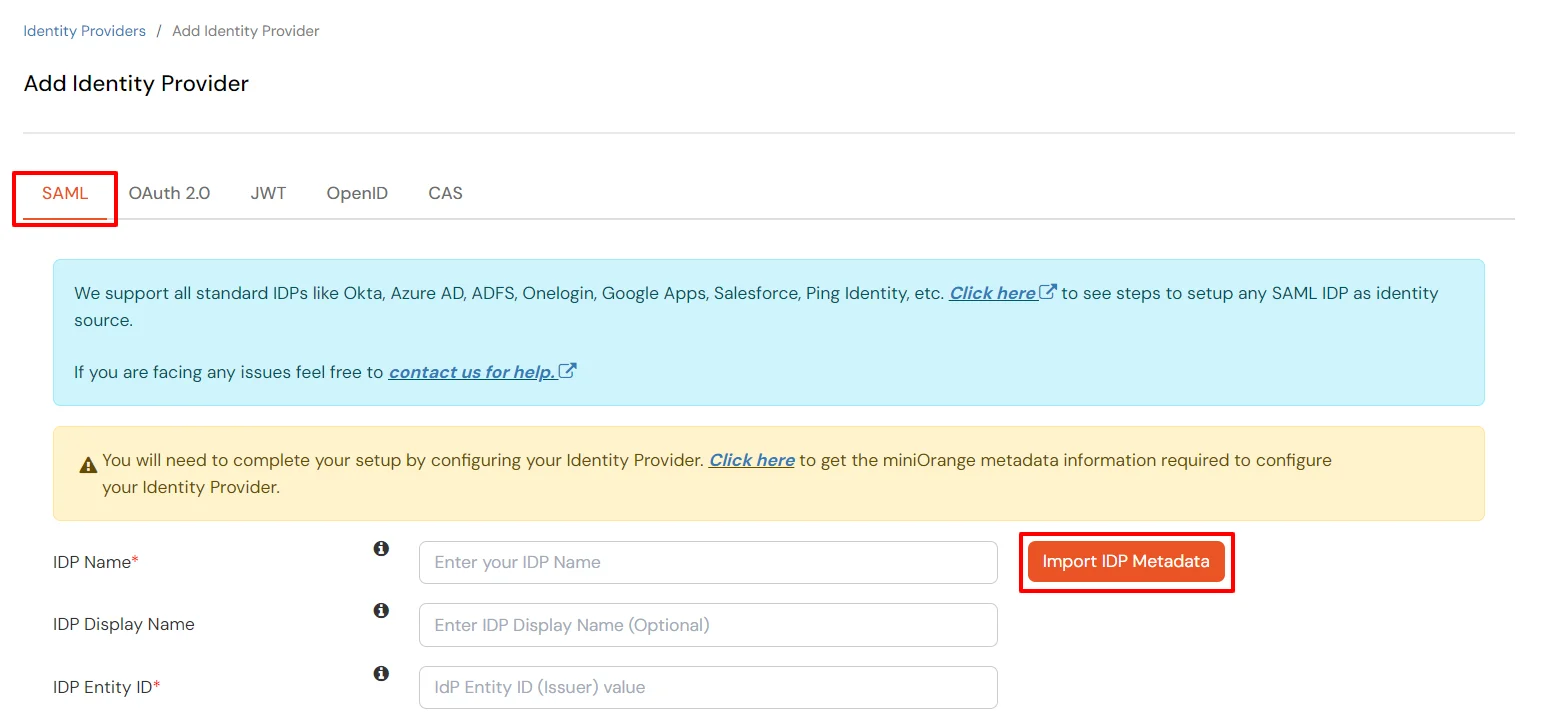
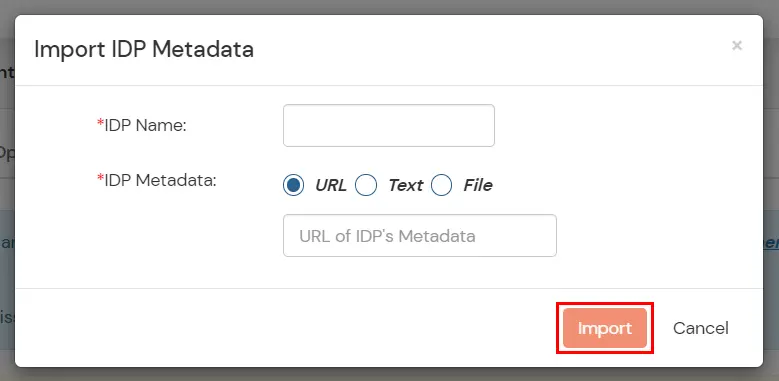
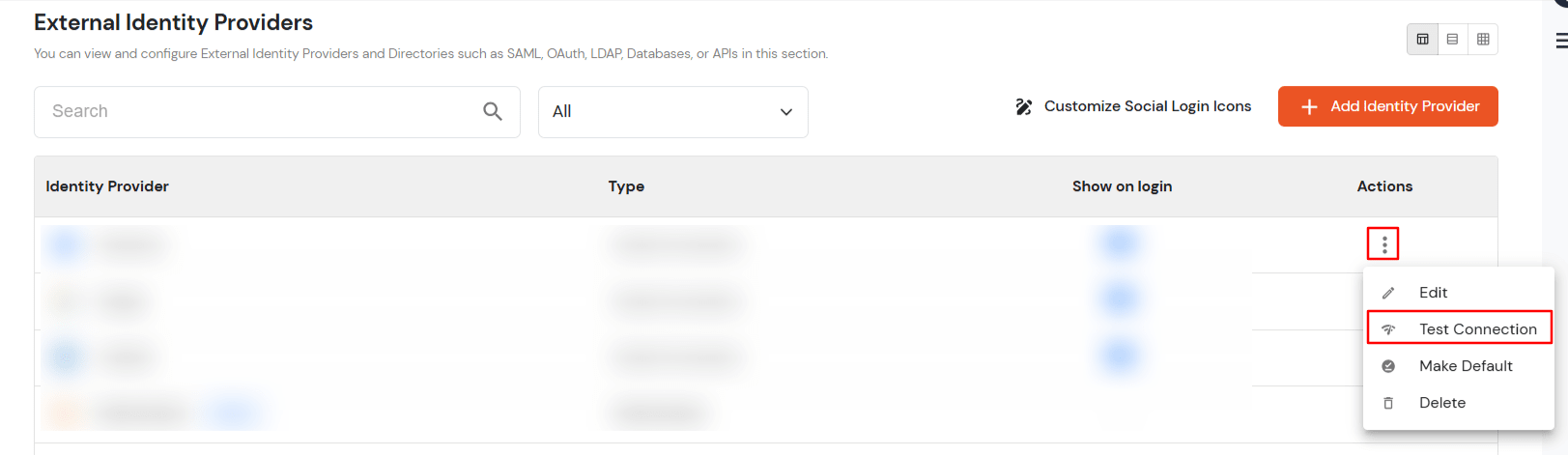
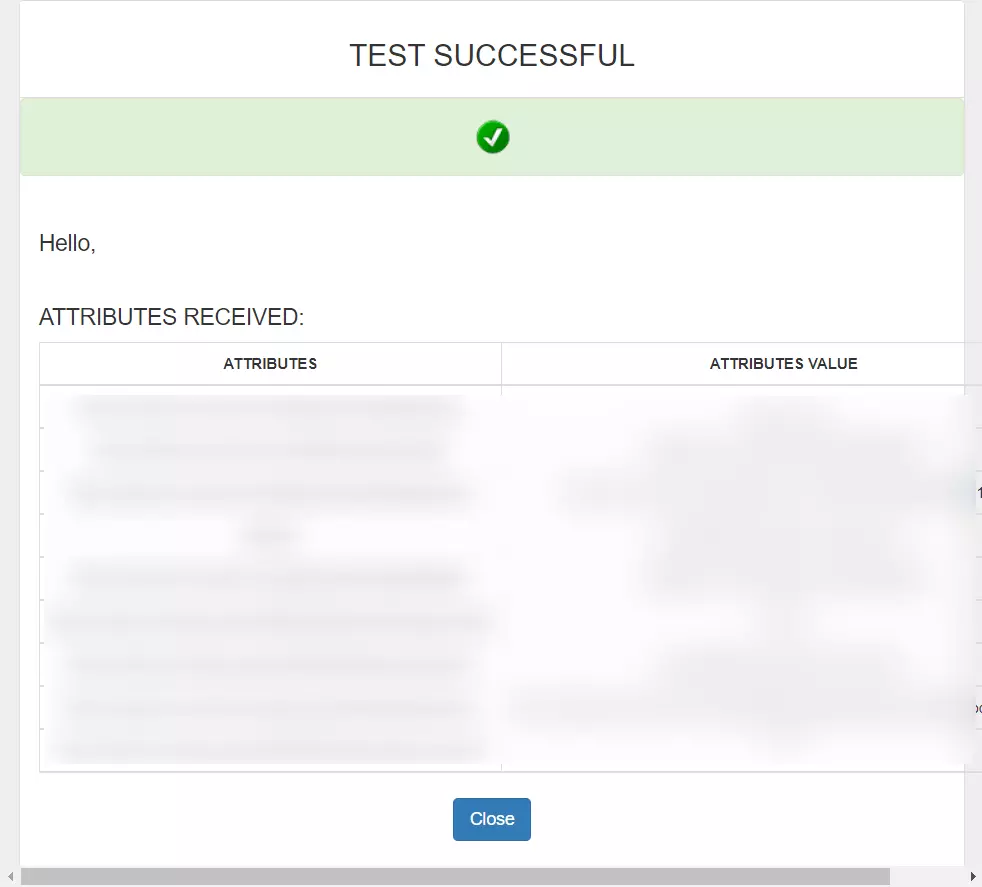
You can follow this guide, if you want to configure SAML/WS-FED, OAuth/OIDC, JWT, Radius etc
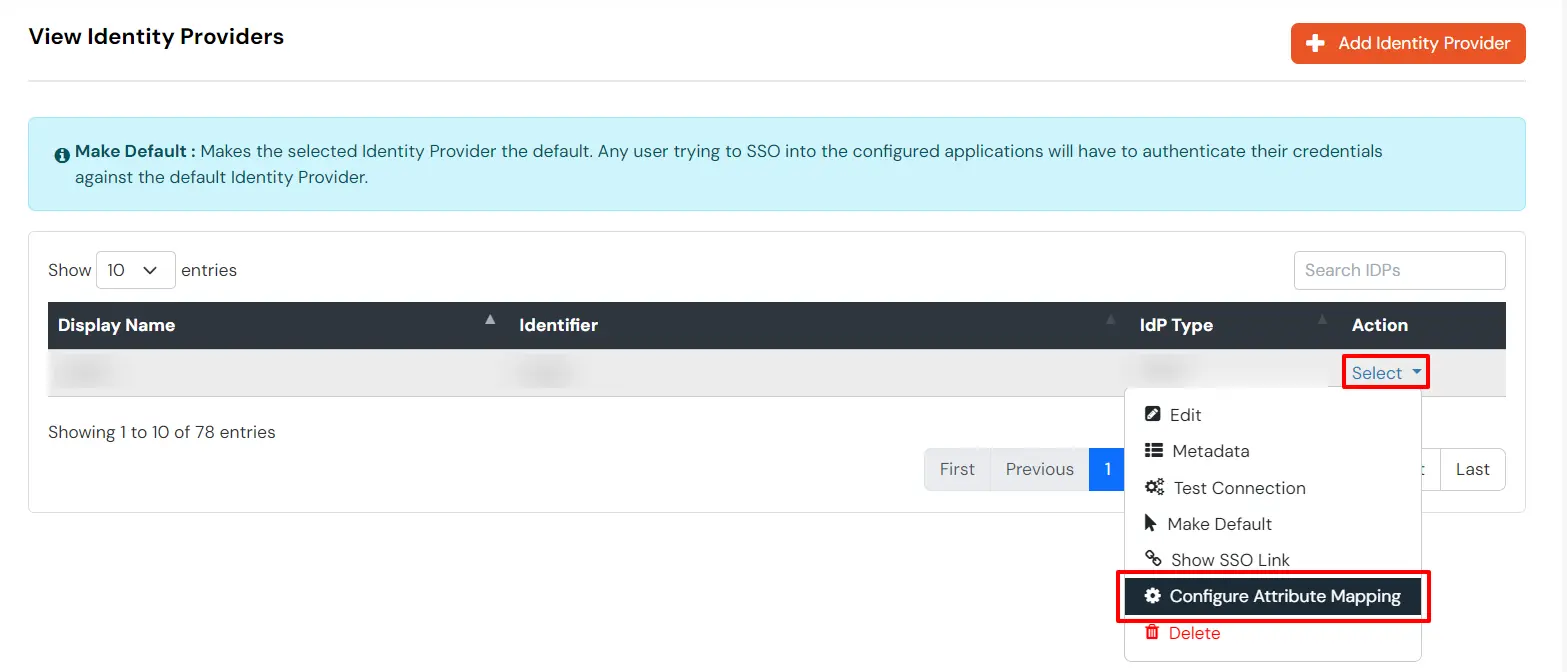
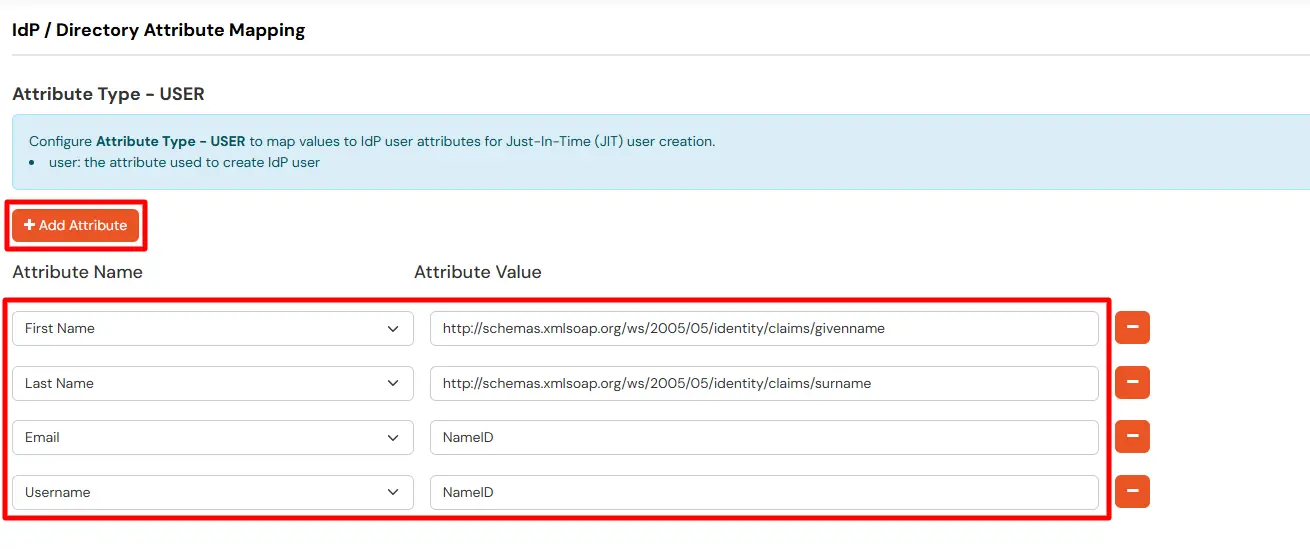
Maps information, such as email and username, during Just-In-Time (JIT) user creation. Email and Username attributes are necessary to create the user profile.
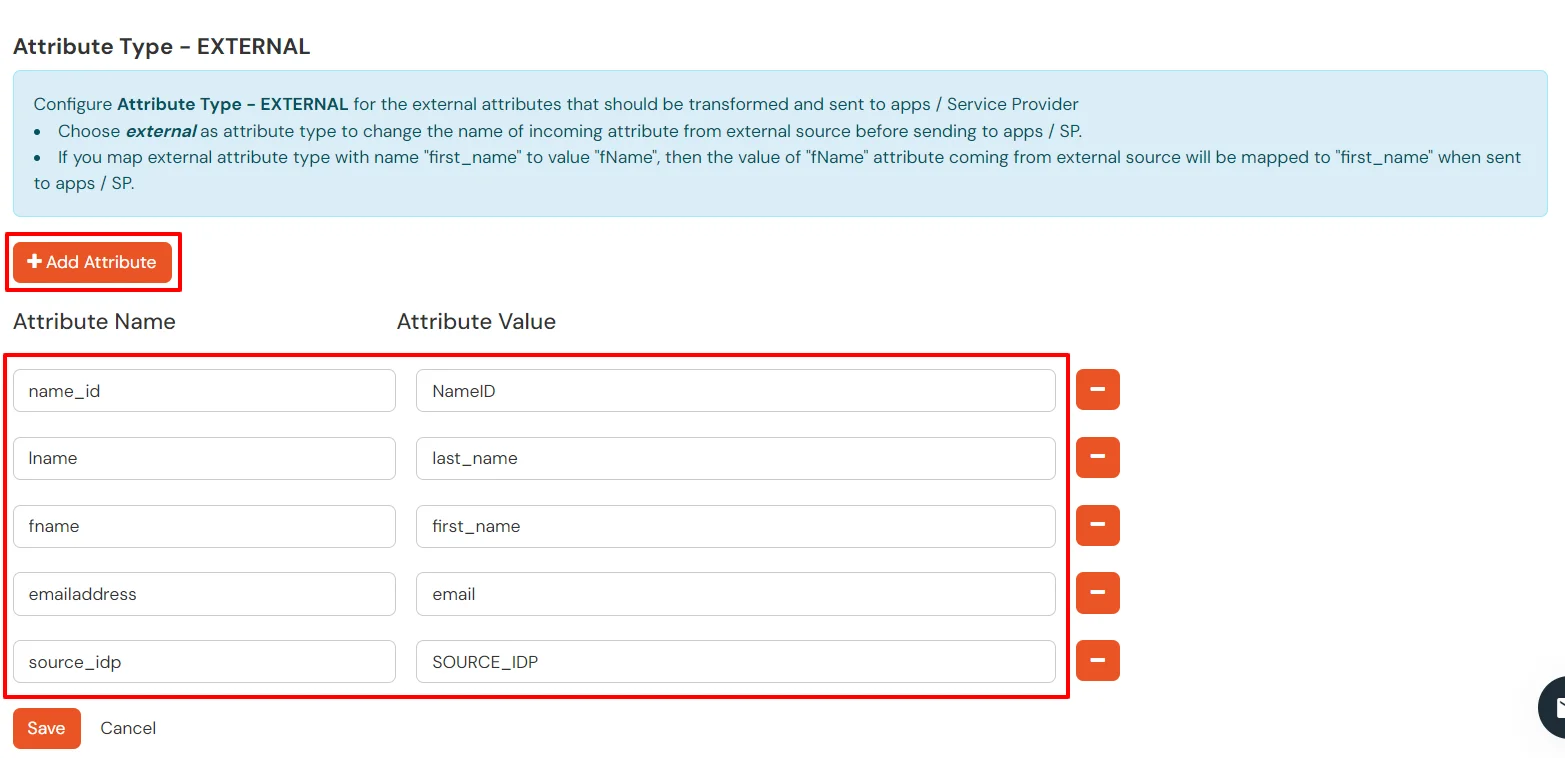
EXTERNAL mappings help alter incoming attribute names before sending them to apps, ensuring that the data is in the correct format.
You can follow this guide, if you want to configure multiple IDPs (Identity Providers) and give users the option to select the IDP of their choice to authenticate with.
