Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×The miniOrange identity provider (IdP) is a service that stores and verifies user identity. IdPs are typically cloud-hosted services, and they often work with single sign-on (SSO) providers to authenticate users. The purpose of this guide is to get you up and run as quickly as possible so that you can play with and test-drive various features that miniOrange has. It is a standalone application with default database and packaged tomcat and does not cover any complex deployment options. We support both Windows and Linux OS for installation.
This short tutorial walks you through starting up the server in standalone mode, setting up the initial admin account, and logging into the miniOrange admin dashboard.
miniOrange On-Premise server has the following system requirements. This section lists recommended versions and requirements.
| Operating System (Linux preferred) |
Any operating system that runs minimum Java 8 |
| CPU Core | 4 Core |
| RAM | 16GB and above |
| Storage | 32GB or above |
| JAVA Environment | jdk1.8.0_381 and above |
| Server Access Policies | Port 80 - HTTP Port 1812 & 1813 - Radius UDP (optional) Port 3389 - RDP (Windows Server) - For Login Port 22 - SSH (Linux Server) - For login |
| Database | Find the list of all supported versions here. |
| Server Ports | Ensure the following ports are available on the server for installing the required services: 6379 - Redis 5672 - RabbitMq |
You can download miniOrange On-Premise server from here
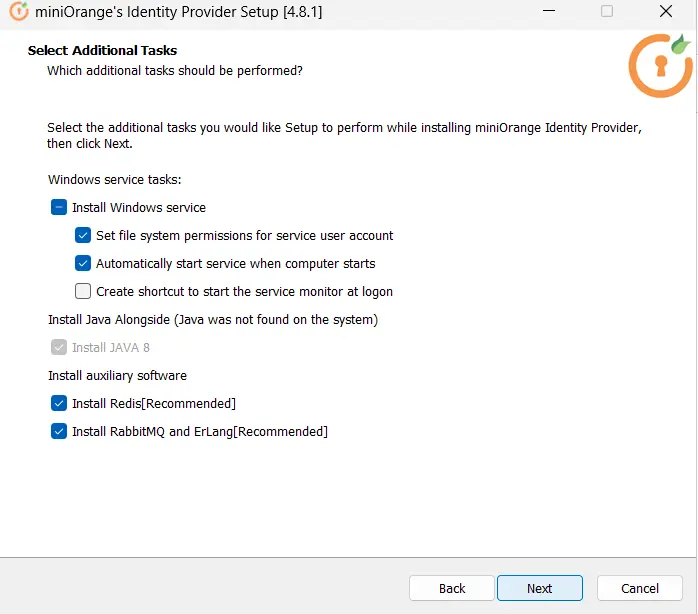
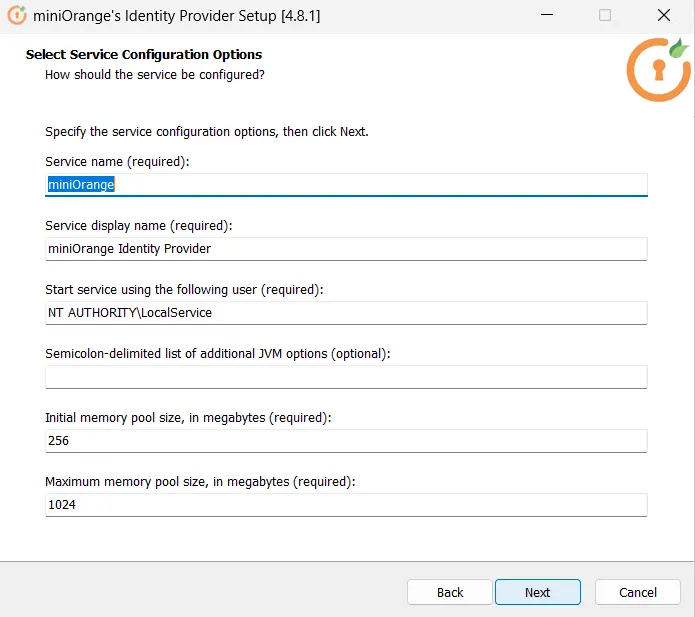
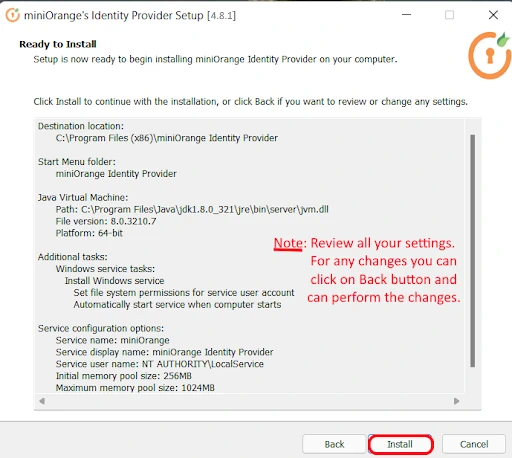
Follow the steps to deploy miniOrange On-Premise server on your operating system:
You can verify the integrity of the installer using the SHA256 checksum. To verify the checksum, please follow the below steps:
CertUtil -hashfile mo-idp-server-4.13.0-installer.exe SHA256
In case of no internet connectivity. You can choose and download the offline installer from here.
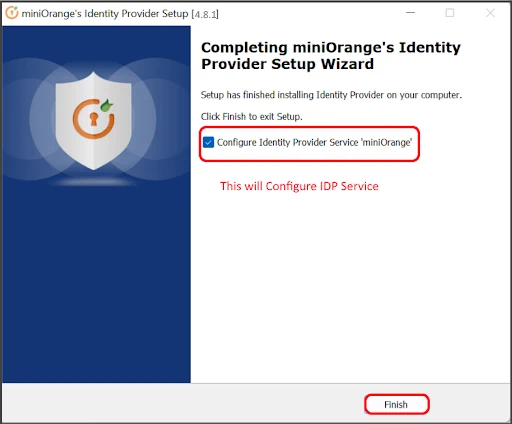
If you already have a database setup which is not in the list below, you can contact us to add support for that database.
ALTER DATABASE YourDatabaseName
SET ALLOW_SNAPSHOT_ISOLATION ON;You can refer this link to know more about how miniOrange can enhance performance and data consistency by enabling Snapshot Isolation.
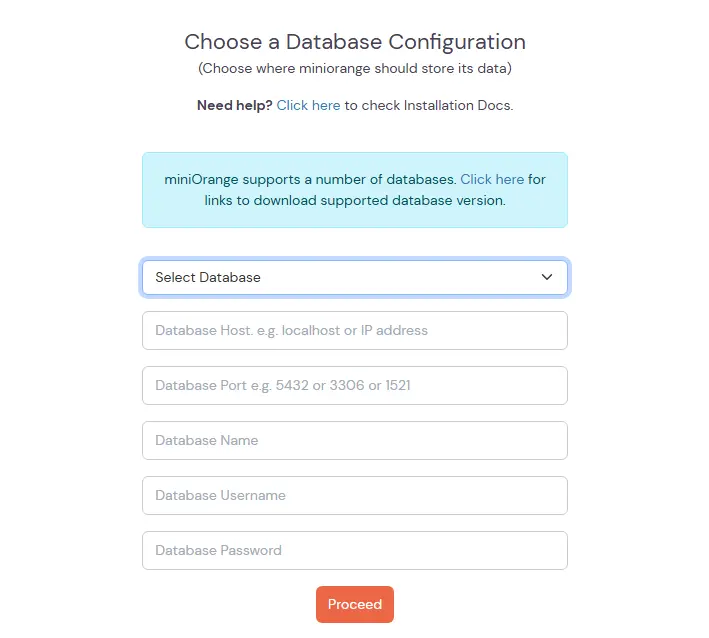
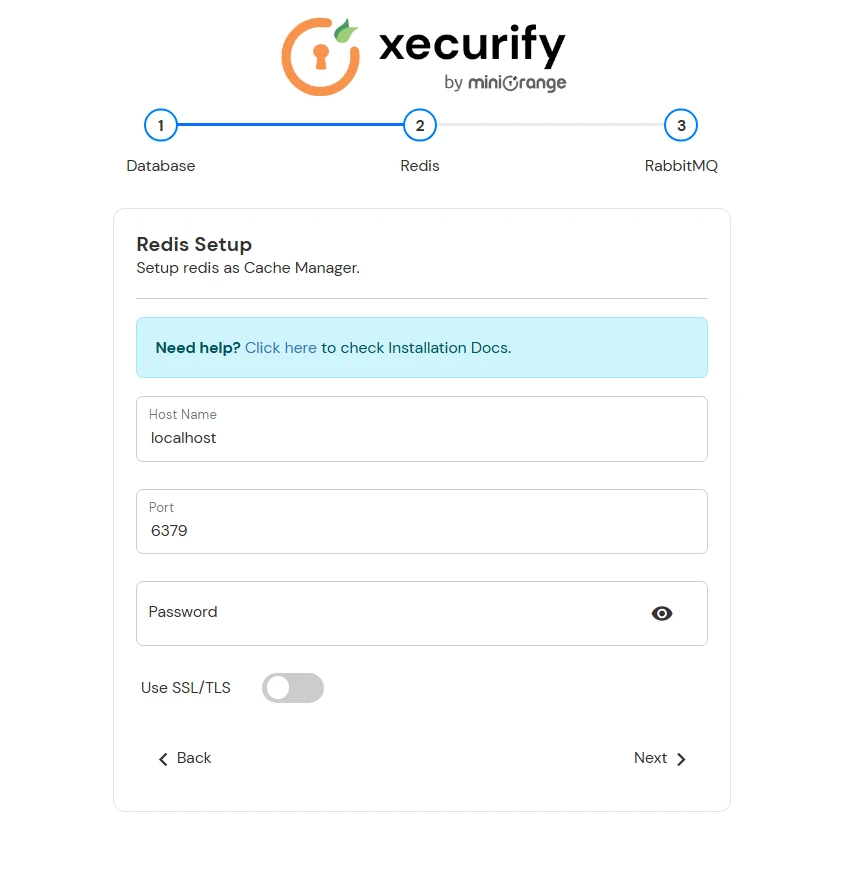
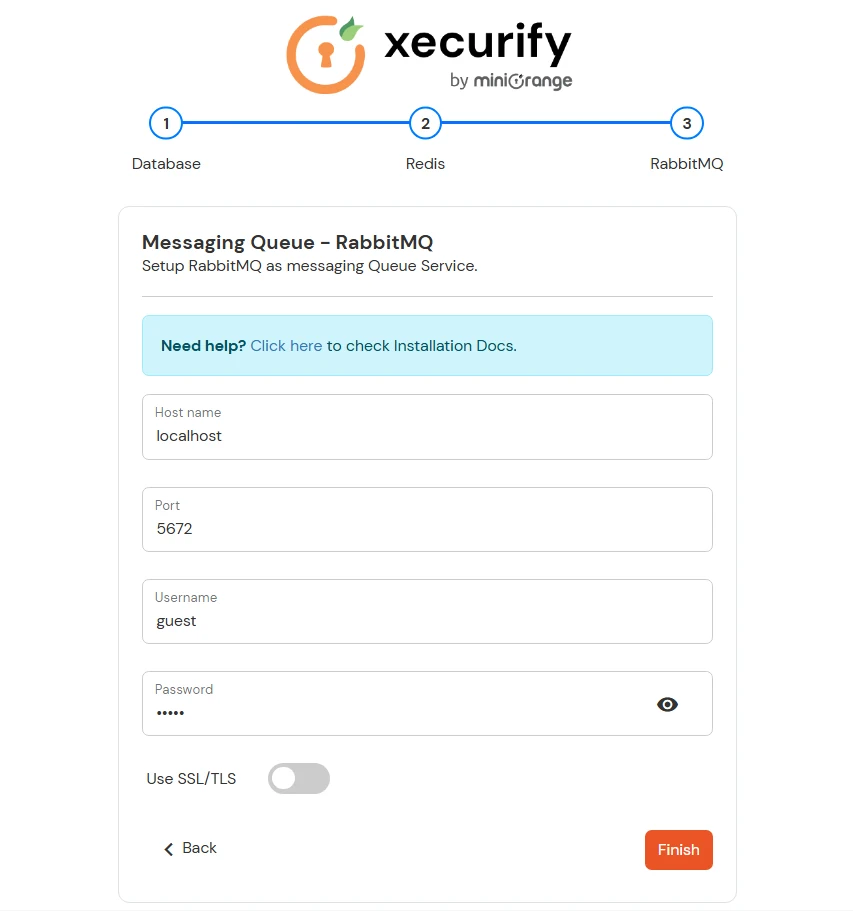
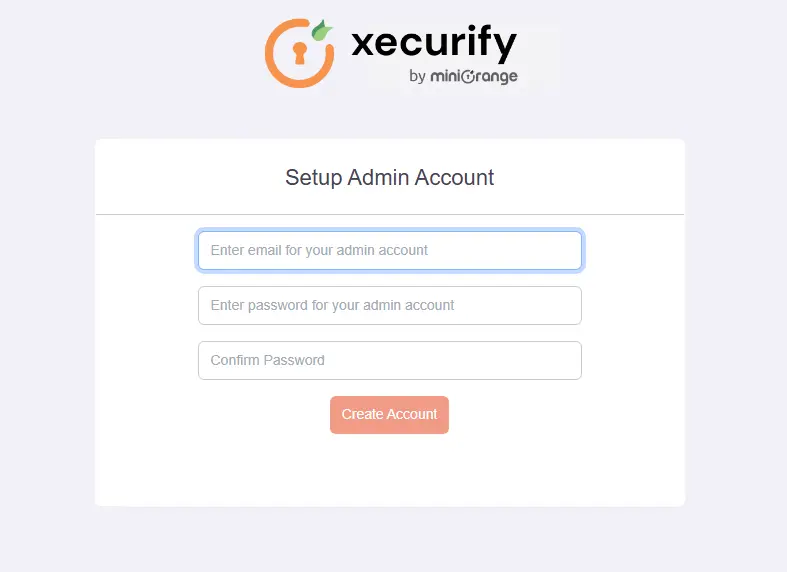
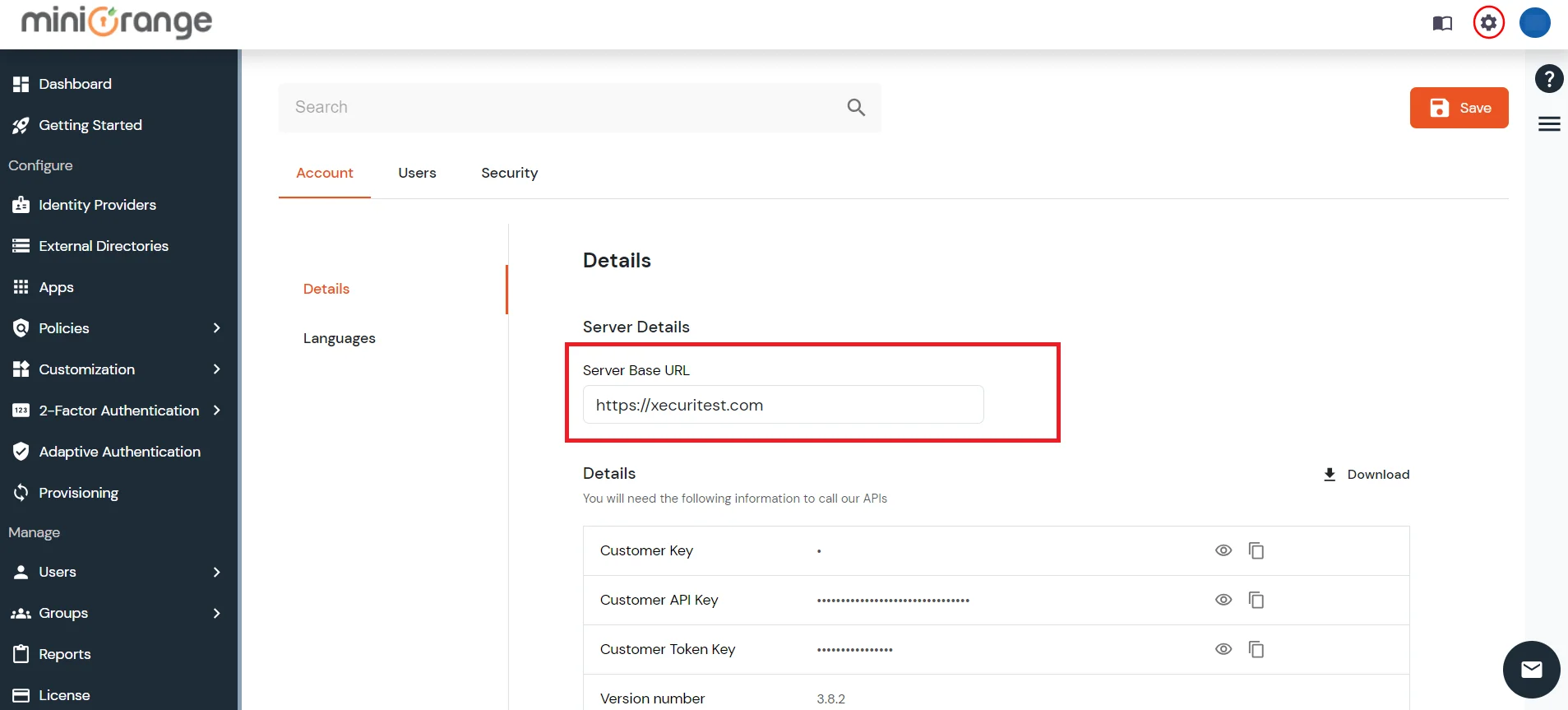
Modify the Server Base URL:
Workflows require secure communication over HTTPS.
[Note: The location of the cacerts file depends on your JDK installation.]
keytool -import ^
-alias miniorange-wildcard ^
-file "C:\Program Files\miniOrange Identity Provider\services\certs\self-signed.crt" ^
-keystore "C:\Program Files\OpenLogic\jdk-8.0.442.06-hotspot\jre\lib\security\cacerts" ^
-storepass changeit
C:\Program Files\Eclipse Adoptium\jdk-17\lib\security\cacerts
C:\Program Files\Java\jdk1.8.0_341\jre\lib\security\cacerts
To enable workflow execution, you must register the Workflow module with the Scheduler service. Follow the steps based on your operating system.
\services\windows\scheduler-mq-register.batcd "C:\Program Files\miniOrange Identity Provider\services\windows"scheduler-mq-register.bata. Database Setup:
sudo -u postgres psqlcreate database <databasename>;b. Install RabbitMQ using the relevant guide:
c. To verify the RabbitMQ installation, use the following command:
systemctl status rabbitmq-server.servicechmod +x *.shsudo sh mo-installer.shsudo systemctl start mo-idp-miniorange.service| Database Type | PostgreSQL/ MySQL/ MSSQL |
| Database Host | localhost |
| Database Username, Password, and Database Name | as set during installation |
./start-services.sh
When prompted, enter start.If you want to start/stop any service manually, you can start them in the following order:
Workflows require secure communication over HTTPS.
[Note: The location of the cacerts file depends on your JDK installation.]
sudo keytool -import \
-alias miniorange-wildcard \
-file /home/abhishek/Downloads/certificates/domain.crt \
-keystore /usr/lib/jvm/java-8-openjdk/jre/lib/security/cacerts \
-storepass changeit/usr/lib/jvm/java-8-openjdk-amd64/jre/lib/security/cacerts
/usr/lib/jvm/java-11-openjdk/lib/security/cacerts
/opt/jdk/jre/lib/security/cacerts
To enable workflow execution, you must register the Workflow module with the Scheduler service. Follow the steps based on your operating system.
/services/linux/scheduler-mq-register.shcd /opt/mo-idp-server/services/linux/sudo ./scheduler-mq-register.shEnsure you have OpenSSL installed on your system:
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout nginx-selfsigned.key -out nginx-selfsigned.crt
-subj "/C=US/ST=State/L=City/O=Company/OU=Org/CN=example.com"| Flag | Description |
|---|---|
| -x509 | Generates a self-signed certificate |
| -nodes | No password for the private key |
| -days 365 | Certificate valid for 1 year |
| -keyout | Path to save the private key |
| -out | Path to save the certificate |
| -subj | Set certificate details without prompts |
/C=US/ST=State/L=City/O=Company/OU=Org/CN=example.com| Field | Meaning | Example |
|---|---|---|
| C | Country code (2 letters) | US, IN, DE |
| ST | State/Province | California, Karnataka |
| L | City | San Francisco, Bangalore |
| O | Organization | Acme Corp |
| OU | Department | IT, Engineering |
| CN | Domain name | example.com |
1. Locate nginx.conf
/etc/nginx/nginx.confC:\nginx\conf\nginx.conf2. Edit the Server Block
server {
listen 443 ssl;
server_name example.com; # Replace with your domain
ssl_certificate /path/to/nginx-selfsigned.crt;
ssl_certificate_key /path/to/nginx-selfsigned.key;
location / {
# Your application settings
}
}3. Restart Nginx
sudo nginx -t # Test configuration
sudo systemctl restart nginx
nginx -s reload
⚠ Note: Self-signed certificates will show a browser warning because they are not issued by a trusted Certificate Authority (CA). Use only for local development or internal testing.
keytool -genkey -alias onpremssoidp -keyalg RSA -keystore onpremssoidp.jks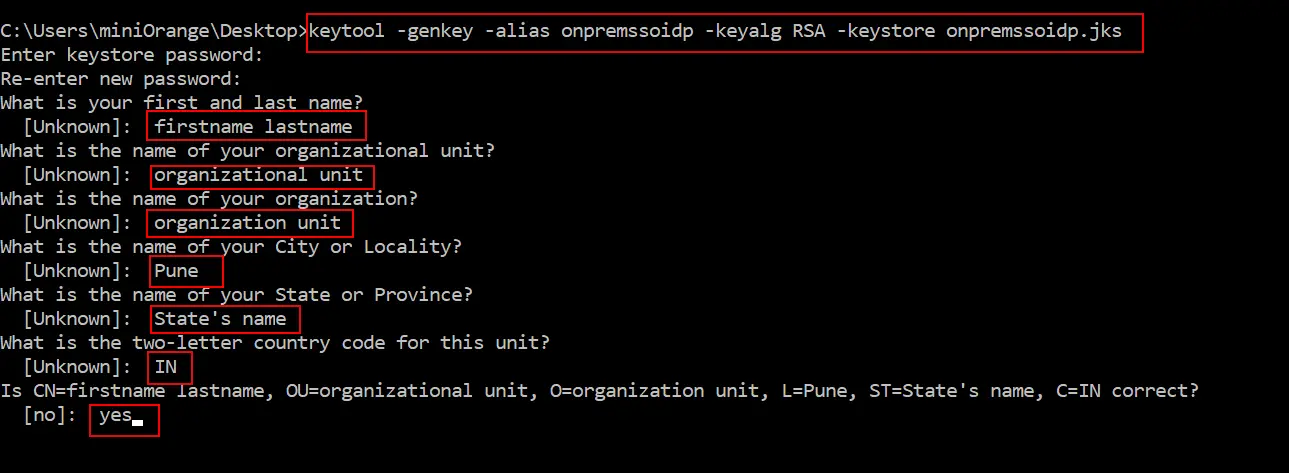
1. Open Tomcat Configuration:
2. Edit server.xml:
<Connector port="443" protocol="HTTP/1.1" SSLEnabled="true" maxThreads="150" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" keystoreFile="<JKS Keystore Path>" ciphers="ALL" keystorePass="<Password while keystore generation>"/>
Note: Make sure the .jks file has appropriate permissions/run command prompt as Administrator.
Using a certificate from Trusted CAs like LetsEncrypt, GoDaddy, Comodo SSL.
certbot certonly --standalone -d.example.com#:/etc/letsencrypt/live/example.com# ls
cert.pem chain.pem fullchain.pem privkey.pem README
<Connector port="443" protocol="org.apache.coyote.http11.Http11NioProtocol"
maxThreads="150" SSLEnabled="true">
<SSLHostConfig>
<Certificate certificateFile="conf/cert.pem"
certificateKeyFile="conf/privkey.pem"
certificateChainFile="conf/chain.pem" />
<SSLHostConfig>
<Connector>
keytool -genkey -alias onpremssoidp -keyalg RSA -keystore onpremssoidp.jks
keytool -delete -alias onpremssoidp -keystore onpremssoidp.jks
openssl pkcs12 -export -in <GoDaddyCertificate>.crt -inkey <PrivateKey>.key
-out <PublicPrivateKeyPair>.p12 -name tomcat -CAfile gd_bundle-g2-g1.crt -caname root
<Connector port="443" protocol="HTTP/1.1" SSLEnabled="true" maxThreads="150" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS" keystoreFile="<JKS Keystore Path>" ciphers="ALL"
keystorePass="<Password while keystore generation>"/>
Creating a New Keystore
keytool -genkey -alias server -keyalg RSA -keysize 2048 -keystore your_site_name.jks
Creating a CSR on Tomcat Servers
keytool -certreq -alias server -file csr.txt -keystore your_site_name.jks
How to Install an SSL Certificate on Your Tomcat Server
keytool -import -alias server -file your_site_name.p7b -keystore your_site_name.jks
Configuring Your SSL/TLS Connector
<Connector port="443" maxHttpHeaderSize="8192" maxThreads="100"
minSpareThreads="25" maxSpareThreads="75"
enableLookups="false" disableUploadTimeout="true"
acceptCount="100" scheme="https" secure="true"
SSLEnabled="true" clientAuth="false"
sslProtocol="TLS" keyAlias="server"
keystoreFile="/home/user_name/your_site_name.jks"
keystorePass="your_keystore_password" />
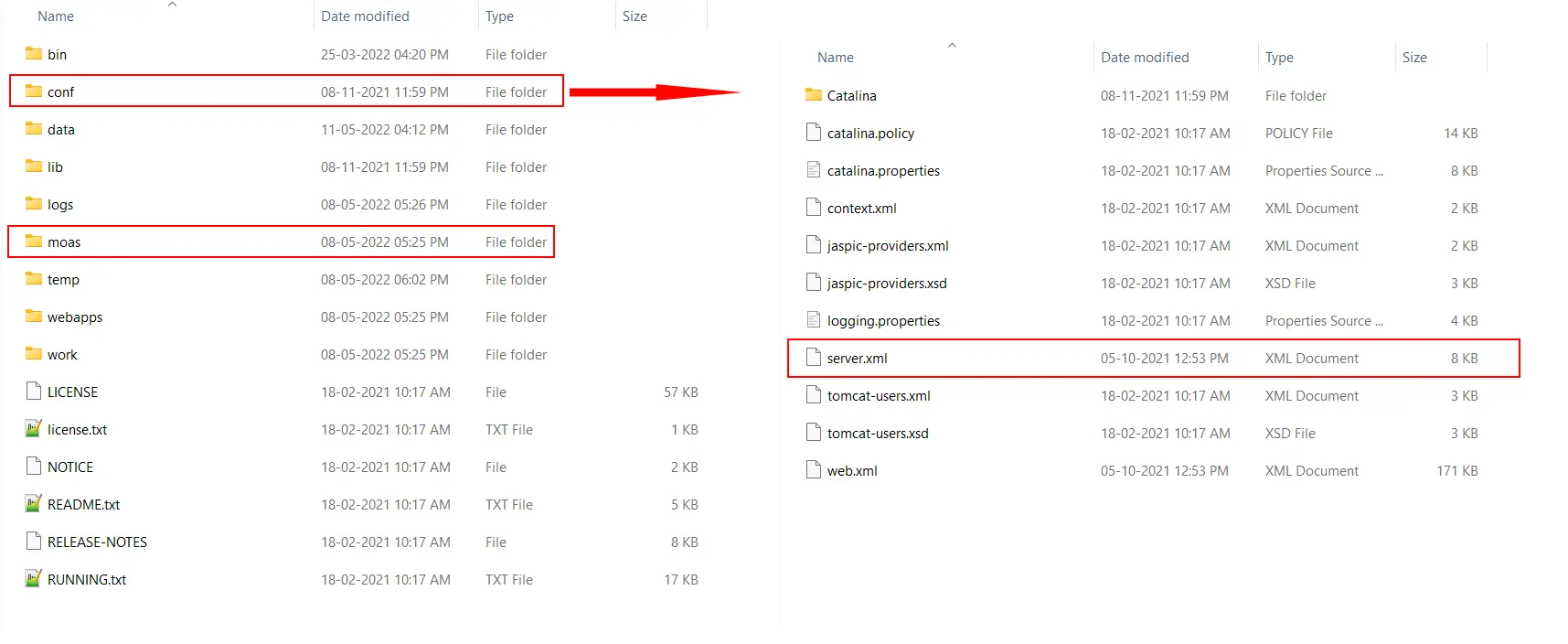
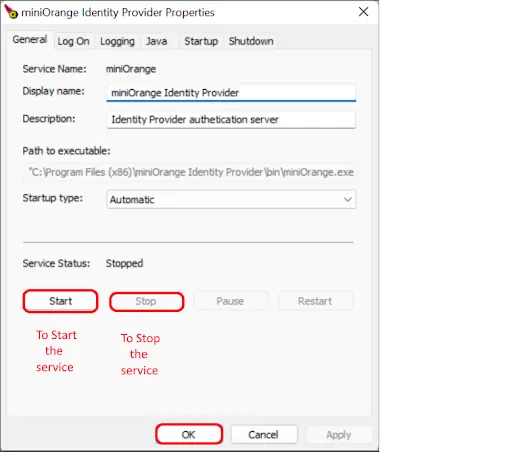
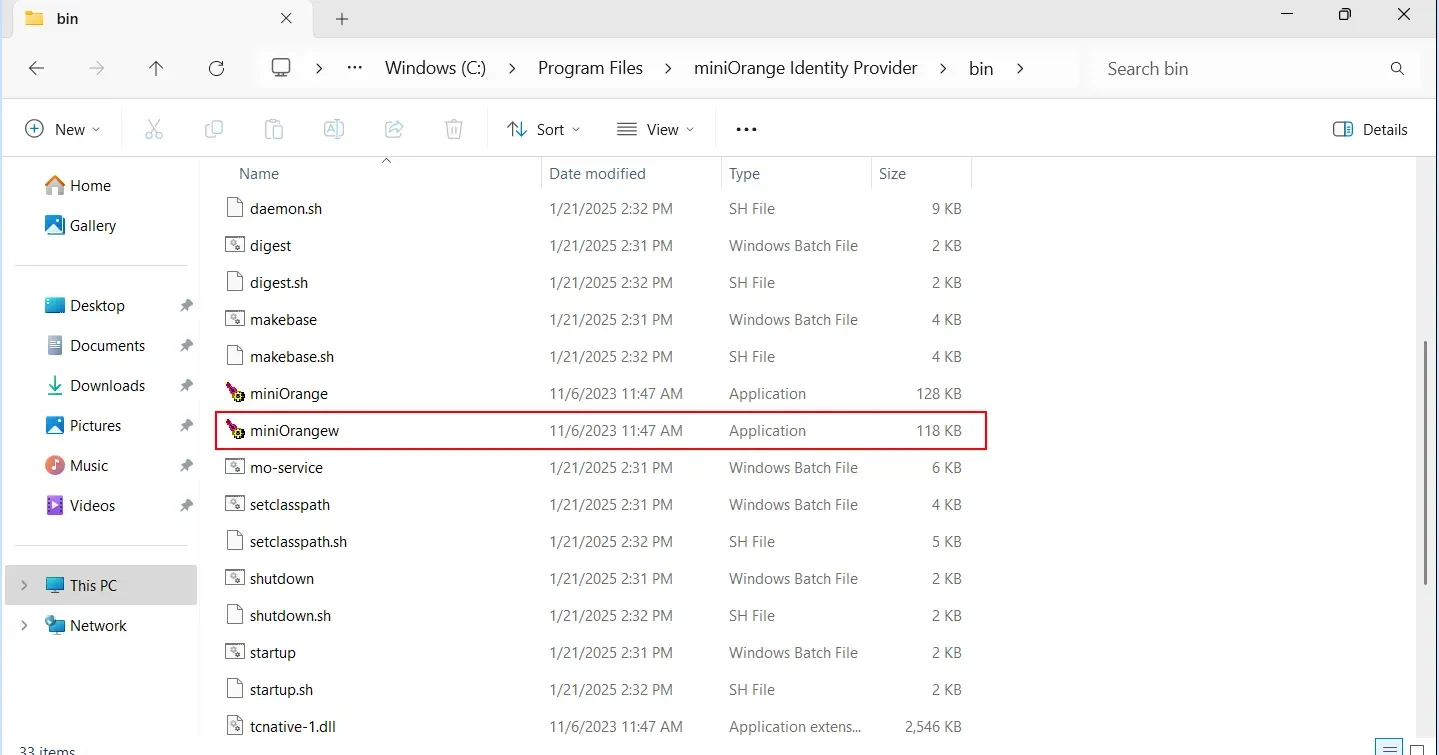
C:\Program Files\miniOrange Identity Provider\bin and open file: miniOrangew.exe-Dspring.profiles.active=redis 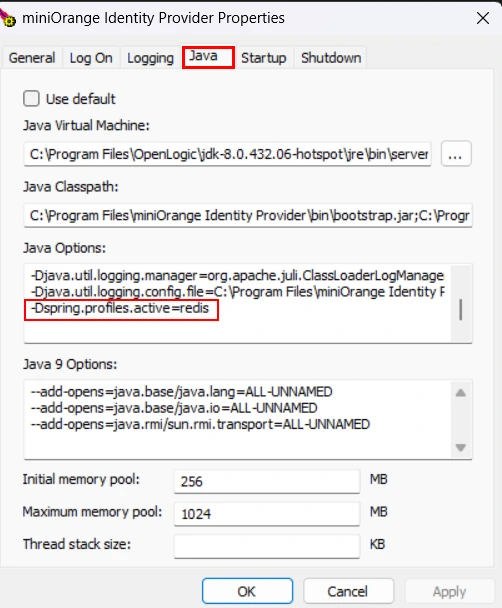
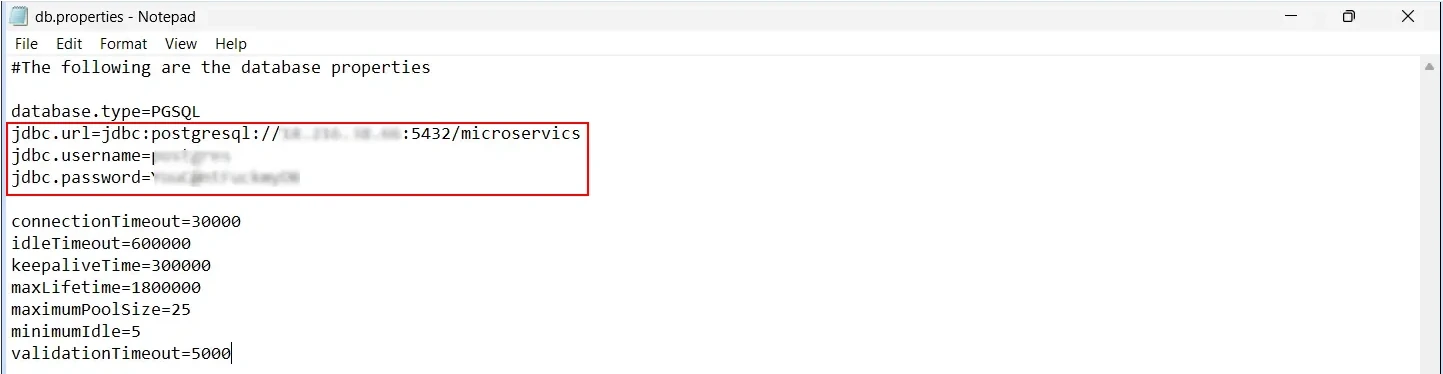
C:\Program Files\miniOrange Identity Provider\moas\WEB-INF\classes\ and open db.properties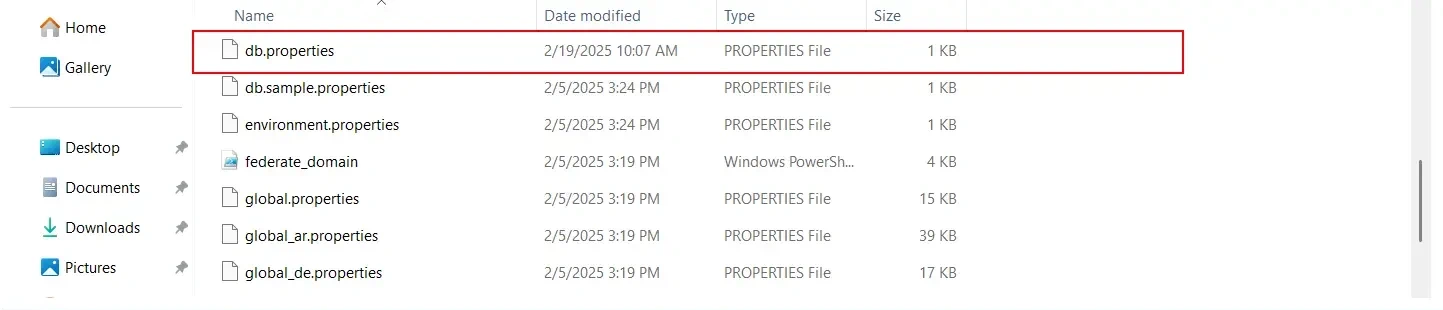
C:\Program Files\miniOrange Identity Provider\services\config and edit the application.properties.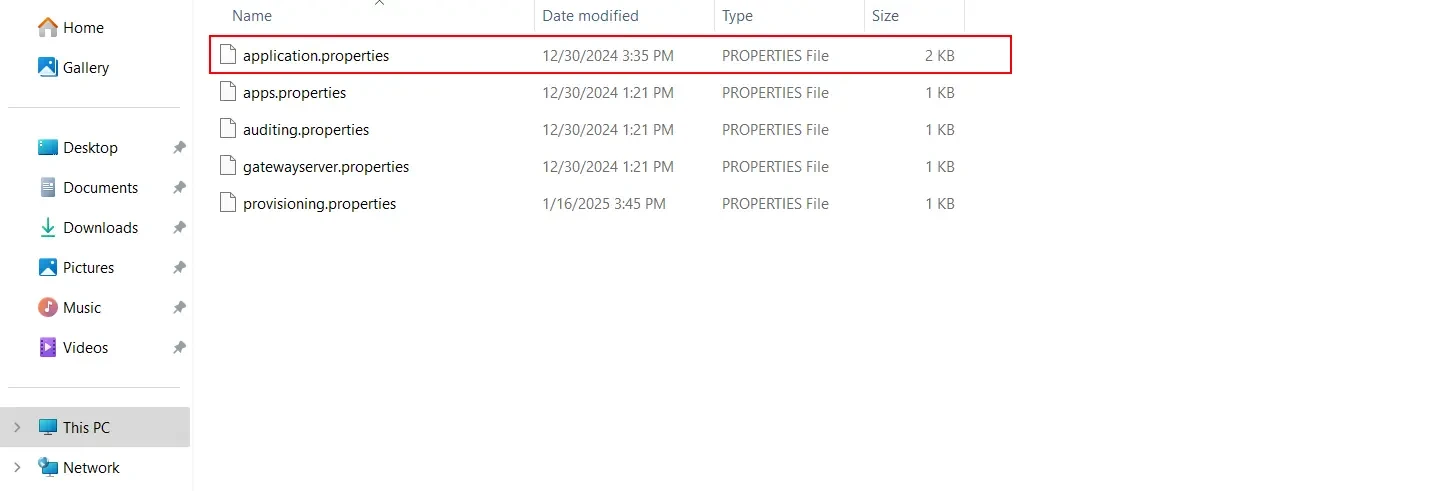
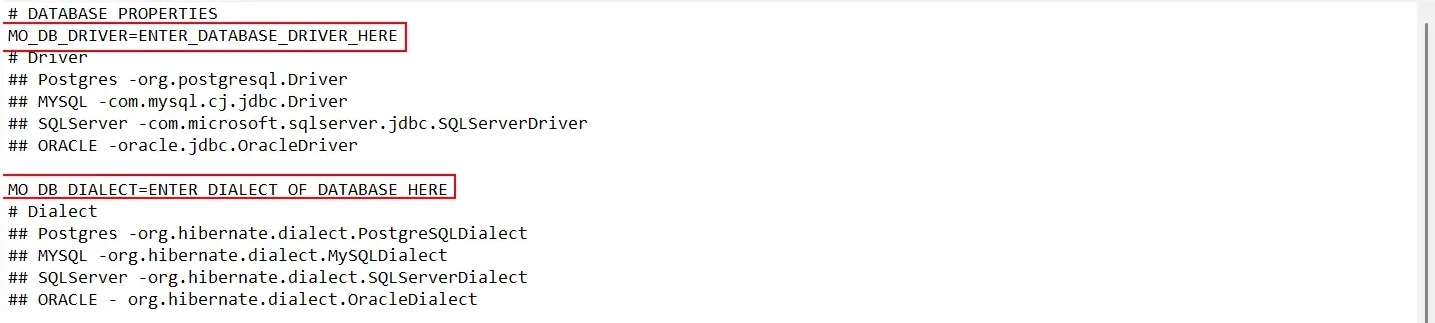
| Database | Example values | |
|---|---|---|
| Driver | Postgres | org.postgresql.Driver |
| MySQL | com.mysql.cj.jdbc.Driver | |
| SQLServer | com.microsoft.sqlserver.jdbc.SQLServerDriver | |
| ORACLE | oracle.jdbc.OracleDriver | |
| Dialect | Postgres | org.hibernate.dialect.PostgreSQLDialect |
| MYSQL | org.hibernate.dialect.MYSQLDialect | |
| SQLServer | org.hibernate.dialect.SQLServerDialect | |
| ORACLE | org.hibernate.dialect.OracleDialect |

| Properties | Property Values (from above step) |
|---|---|
| MO_DB_PRIMARY_URL & MO_DB_REPLICA_URL | jdbc.url |
| MO_DB_PRIMARY_USER & MO_DB_REPLICA_USER | jdbc.username |
| MO_DB_PRIMARY_PASS & MO_DB_REPLICA_PASS | jdbc.password |
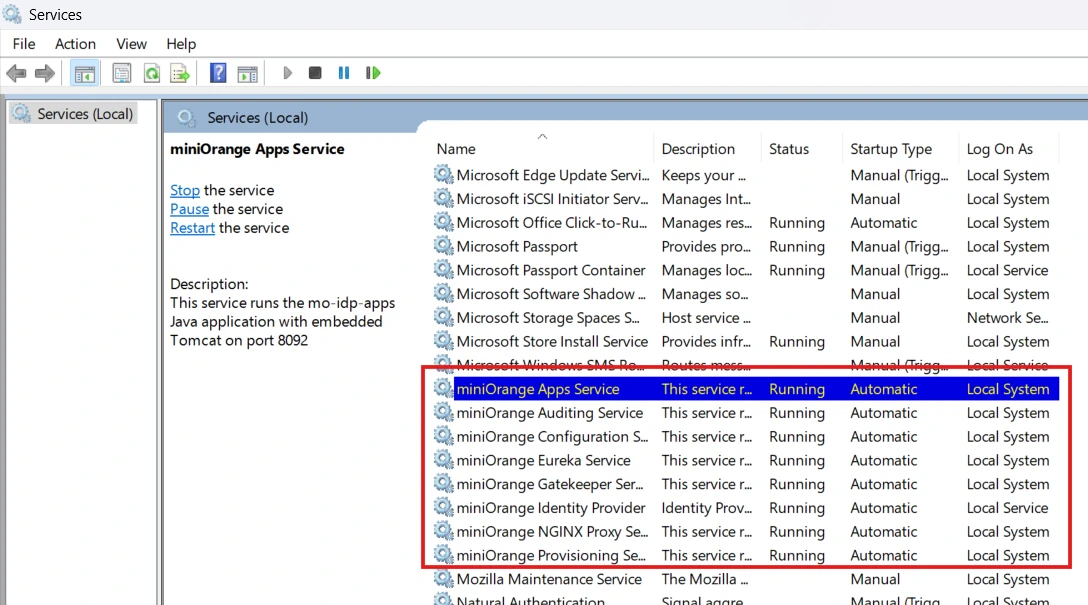
<miniOrange Identity Provider Folder>/services/windows/windows-service.bat start (Wait 10-15 seconds for the services to start.)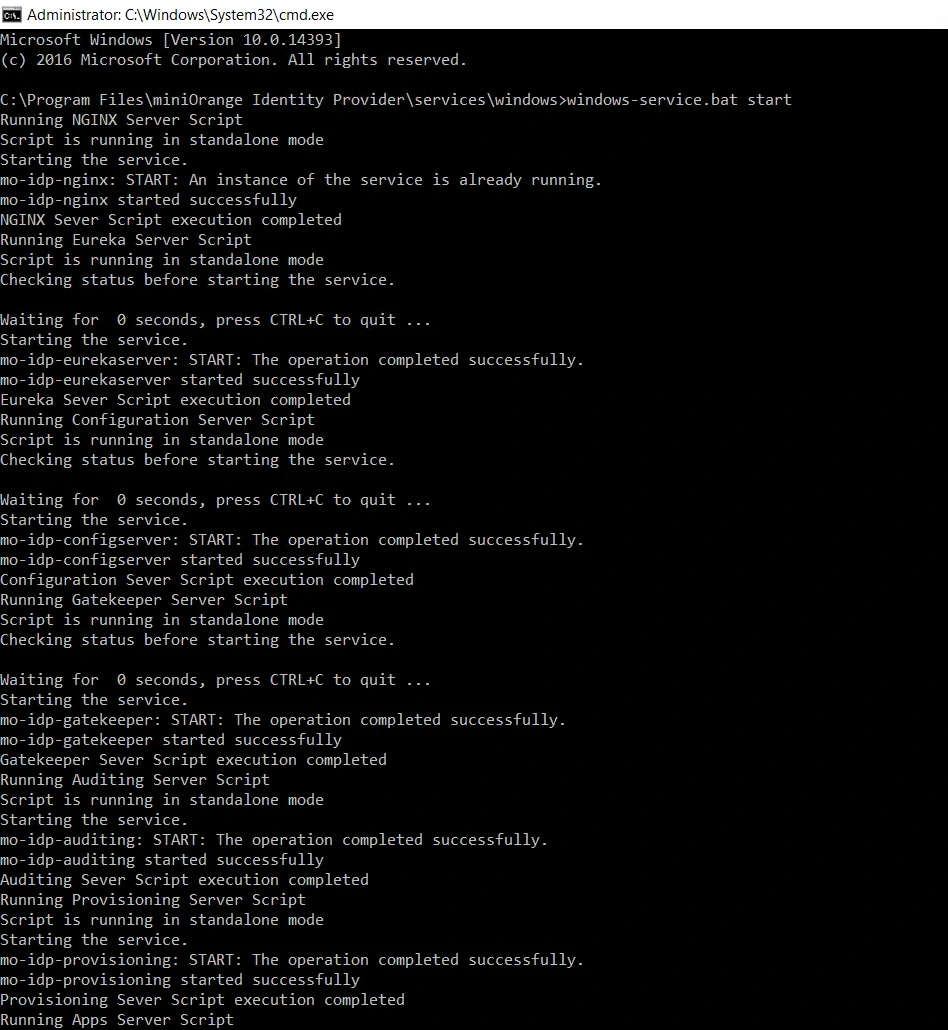
<miniOrange Directory\services\logs>
Follow the below steps to start the microservices:
/moas/WEB-INF/classes/db.properties.

/services/config and edit the application.properties.

| Database | Example values | |
|---|---|---|
| Driver | Postgres | org.postgresql.Driver |
| MySQL | com.mysql.cj.jdbc.Driver | |
| SQLServer | com.microsoft.sqlserver.jdbc.SQLServerDriver | |
| ORACLE | oracle.jdbc.OracleDriver | |
| Dialect | Postgres | org.hibernate.dialect.PostgreSQLDialect |
| MYSQL | org.hibernate.dialect.MYSQLDialect | |
| SQLServer | org.hibernate.dialect.SQLServerDialect | |
| ORACLE | org.hibernate.dialect.OracleDialect |

| Properties | Property Values (from above step) |
|---|---|
| MO_DB_PRIMARY_URL & MO_DB_REPLICA_URL | jdbc.url |
| MO_DB_PRIMARY_USER & MO_DB_REPLICA_USER | jdbc.username |
| MO_DB_PRIMARY_PASS & MO_DB_REPLICA_PASS | jdbc.password |
<miniOrange Identity Provider Folder>/services/windows/windows-service.bat start (Wait 10-15 seconds for the services to start.)
<miniOrange Directory\services\logs>
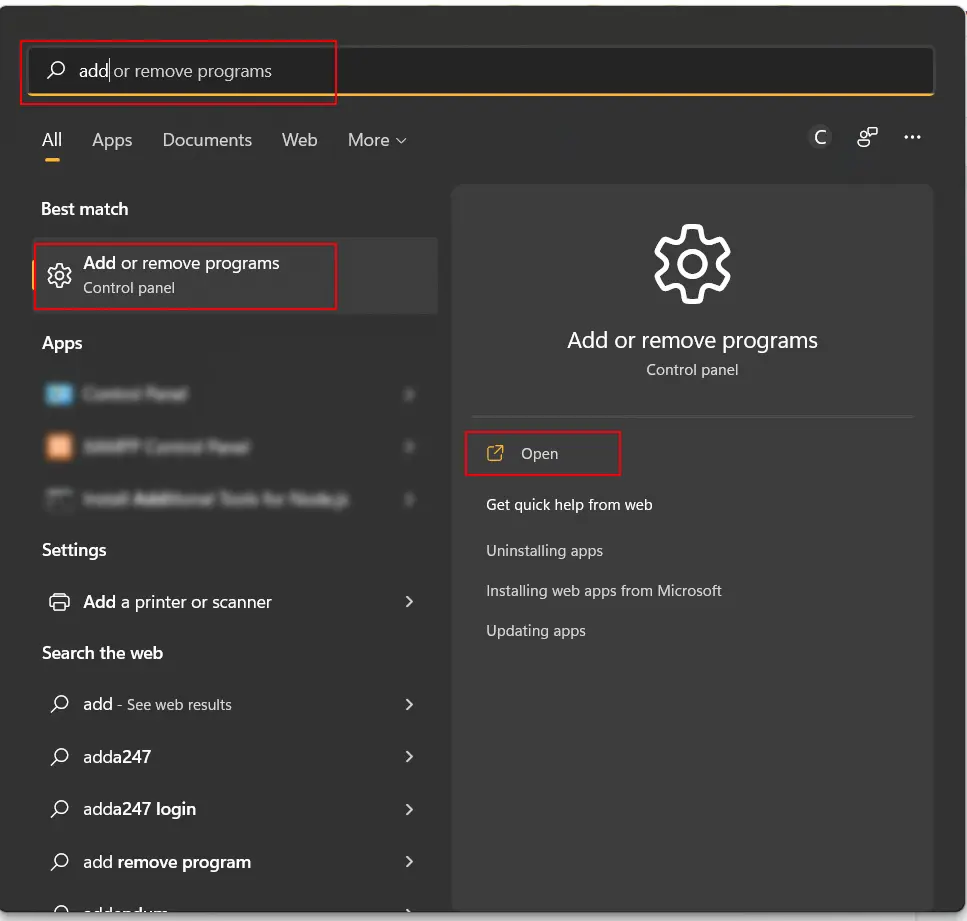
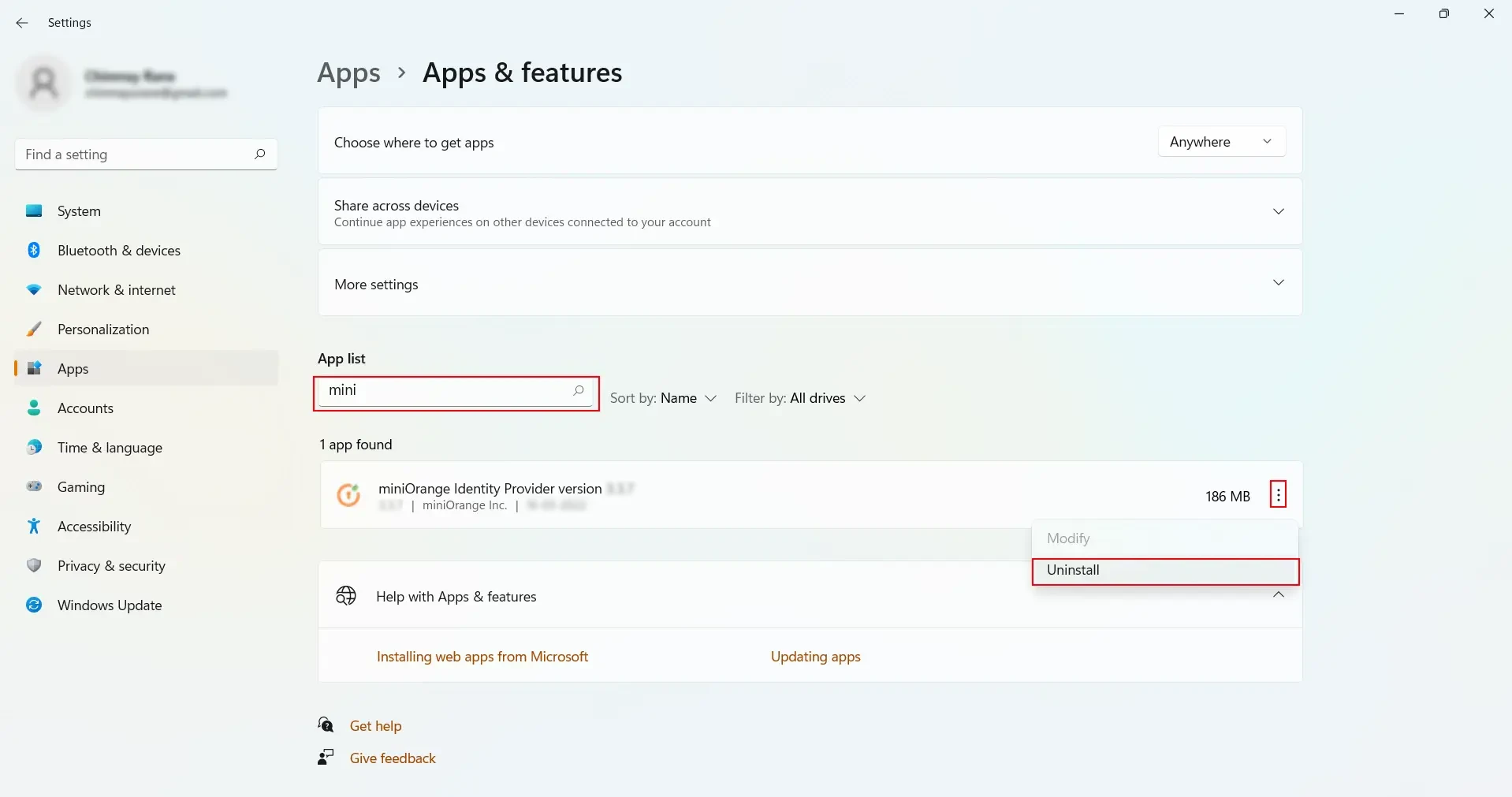
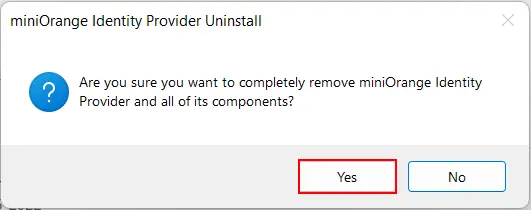
$$\text{HKEY\_LOCAL\_MACHINE} \rightarrow \text{SOFTWARE}$$[
If you encounter the error:"keytool error: java.lang.Exception: Key pair not generated, alias <onpremssoidp> already exists"
This indicates that the keystore file already exists. To resolve this, follow these steps:
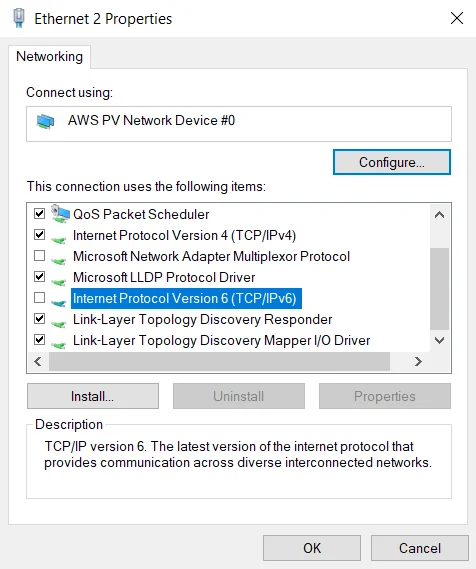
Encounter the error:
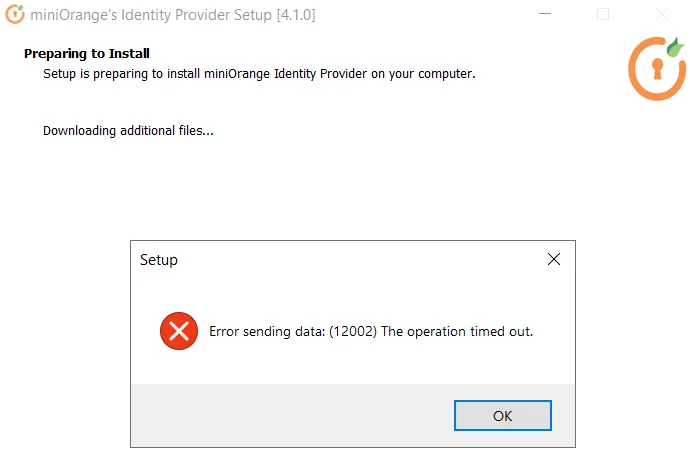
If you get an error similar to the above image, follow these steps.
Disable IPv6 on Windows: