Need Help? We are right here!
Search Results:
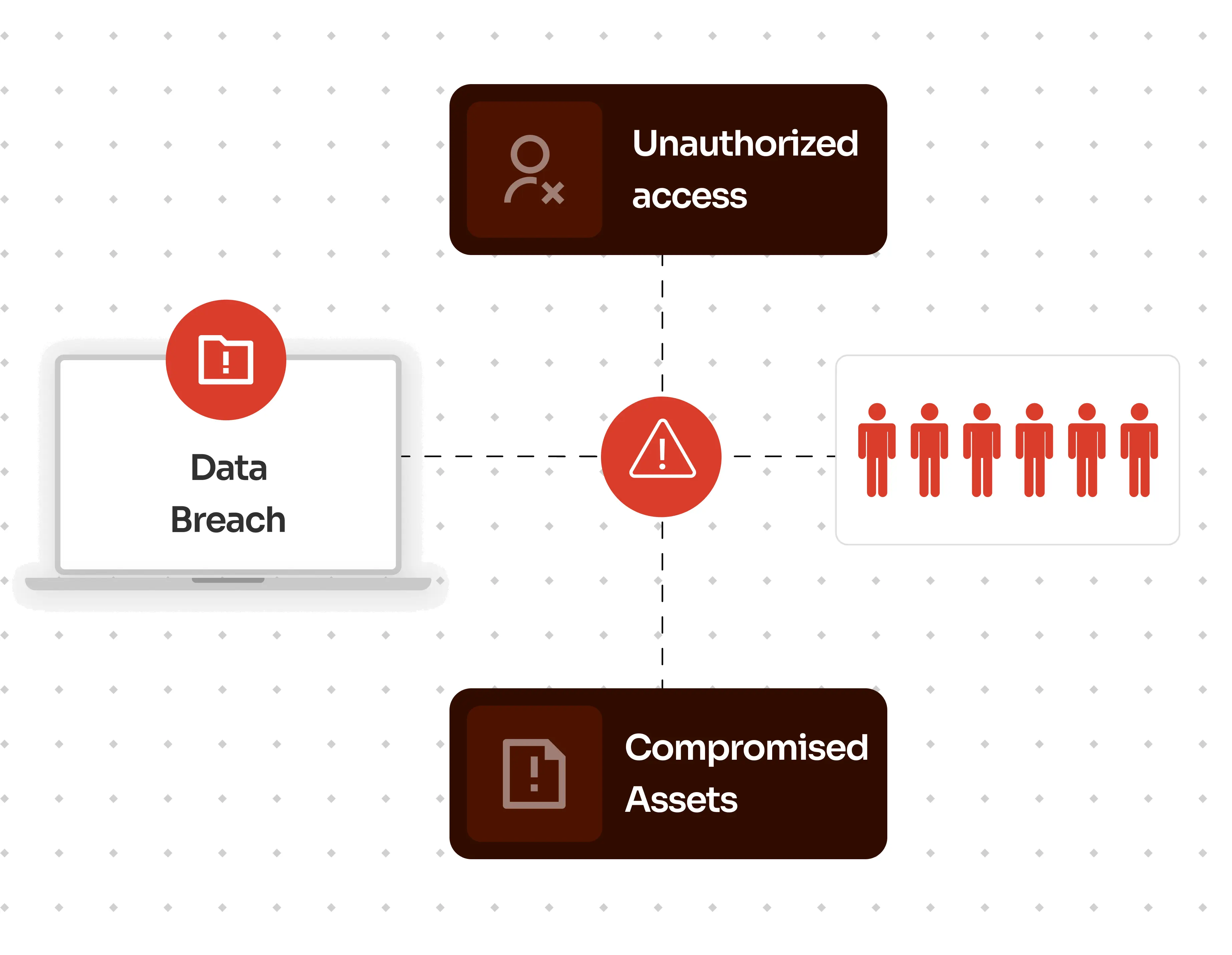
×In a world where mobile devices have become an integral part of our work lives, securing access to critical resources is of utmost importance. However, the convenience of mobile connectivity also brings forth security concerns. Unauthorized access, data breaches, and compromised assets are potential risks that must be mitigated. Users can swiftly access business-sensitive data, like emails and attachments, that they can download on their smartphones and risk leaking it online.
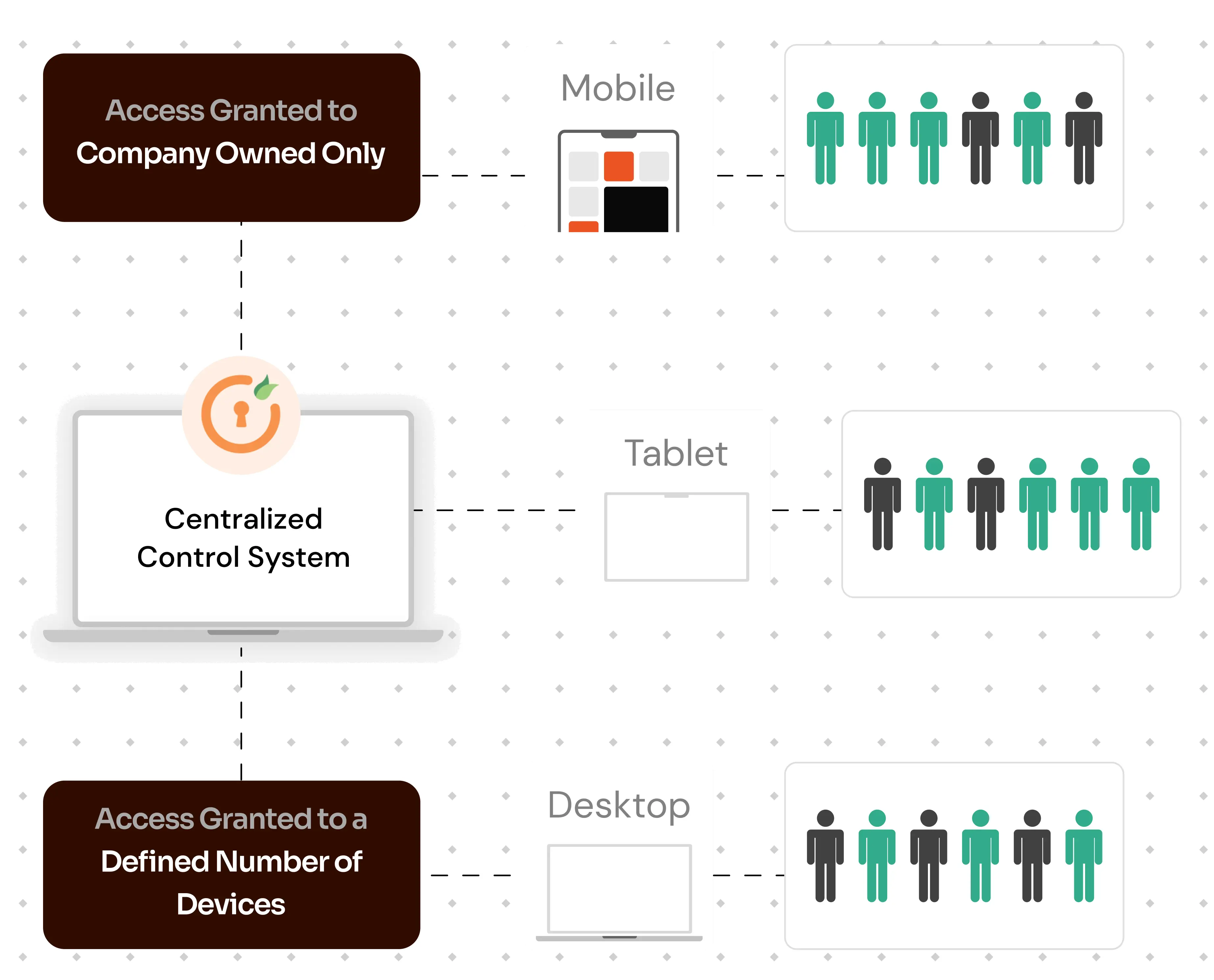
Under the principle of COBO (Company Owned/Business Only), this restriction system typically emphasizes granting access only to corporate devices, ensuring heightened security. By designating certain devices as "trusted", this method not only curtails user access to those specific devices but also potentially restricts access on personal devices, thereby adding an intensified layer of security against unauthorized access.
per user per month
*Please contact us to get volume discounts for higher user tiers.
Manage all your organization’s devices from a single centralized dashboard, making it easy to monitor, update, and troubleshoot remotely.
Seamlessly integrate employee-owned devices, offering secure access to business resources while separating personal user data and maintaining privacy.
Control which apps can be installed or accessed on company devices, reducing the risk of unauthorized data access and data breaches.
Track lost or stolen devices in real-time, helping recover assets and safeguarding critical business data.
Instantly erase or lock data on compromised devices to prevent unauthorized access and protect sensitive business data.
Ensure all devices meet regulatory standards by enforcing compliance policies automatically, supporting audits, and risk management.
Manage user permissions and access levels, ensuring only authorized personnel can access sensitive applications and data on mobile devices.
Push software updates and security patches remotely, keeping devices secure and up-to-date without user intervention.
Protects sensitive information with encryption, secure access controls, and remote wipe capabilities, reducing the risk of data breaches.
Enables employees to access work resources securely from any device, supporting remote work and improving efficiency.
Centralized management allows IT teams to monitor, update, and troubleshoot devices remotely, saving time and resources.
Ensures devices adhere to regulatory standards and company policies, minimizing compliance risks and supporting audit readiness.
Reduces hardware costs by offering BYOD Support (Bring Your Own Device) policies and extends device usability through proper device management.
Provides real-time insights and full control over device usage, helping prevent unauthorized access and ensuring all devices are secure.
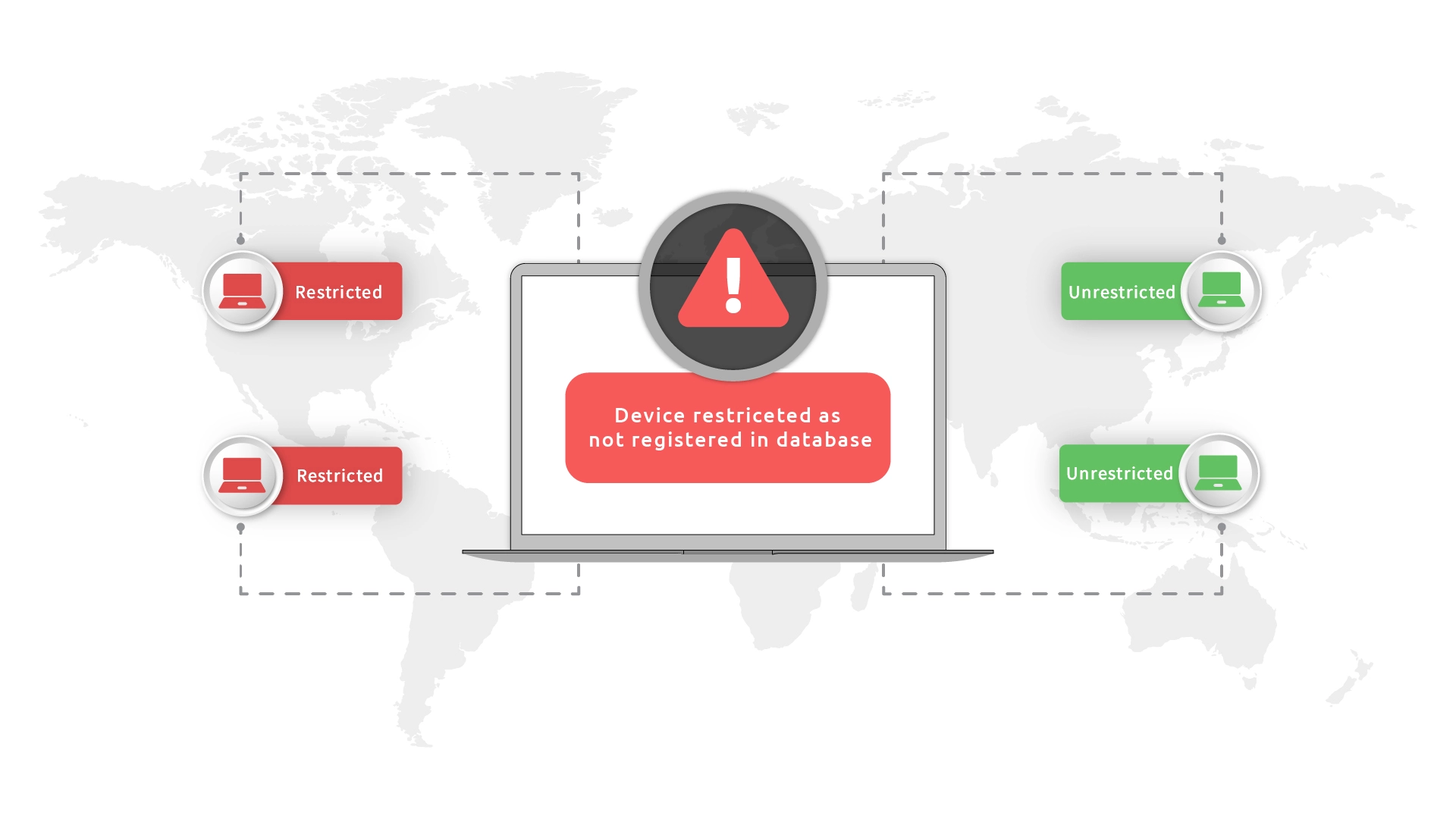
Enable a robust device-based policy which limits login process, ensuring exclusive access to your most valuable information.
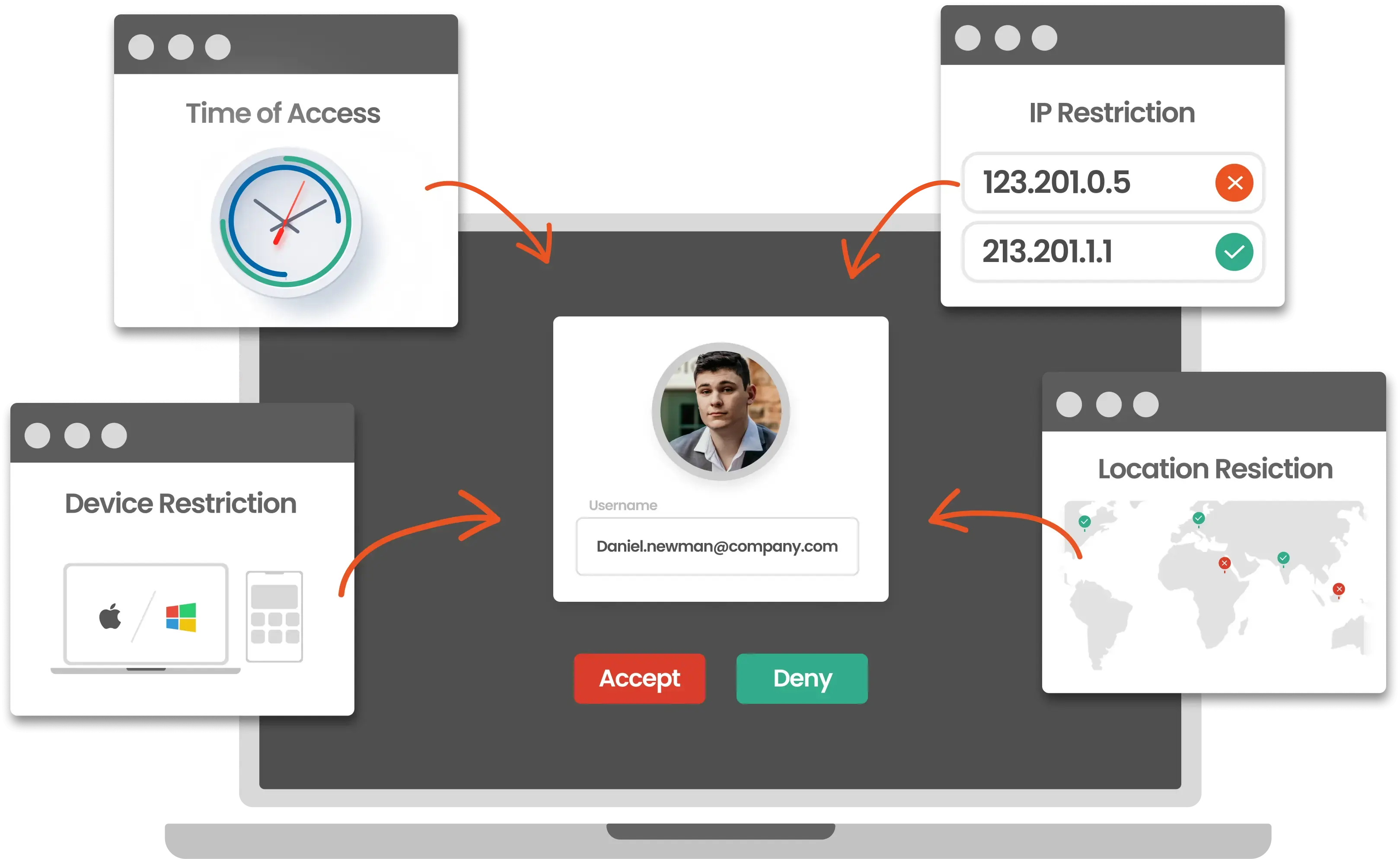
Secure your enterprise systems in high-risk scenarios by enabling admins to set MFA policies for different scenarios and use cases.
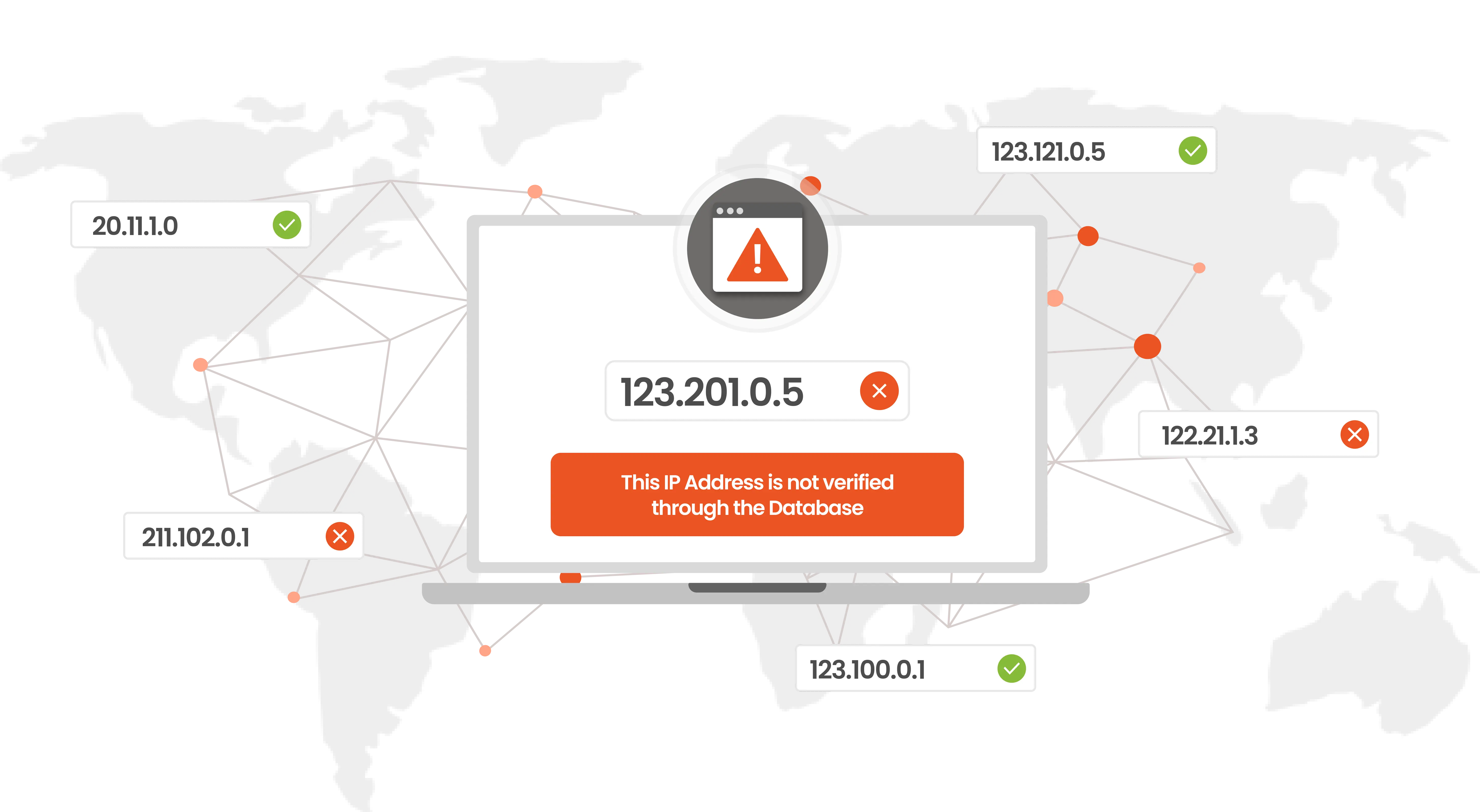
Restrict unwanted user access to crucial business data from unknown IP addresses.
MDM is a security solution that allows organizations to secure, monitor, and manage mobile devices remotely. It’s essential for protecting business data, ensuring compliance, and maintaining control over device usage across the organization.
MDM lets administrators set policies that restrict device access to specific apps, websites, and functions. This control prevents unauthorized activities, reduces security risks, and ensures that devices are used for business purposes only.
Yes, MDM supports BYOD environments by separating personal and work data on employee-owned devices. It allows employees to access work resources securely while keeping personal information private.
With MDM, administrators can remotely lock or wipe lost or stolen devices, protecting sensitive business data from unauthorized access and helping mitigate potential data breaches.
Most MDM solutions are compatible with multiple operating systems, such as iOS and Android, allowing organizations to manage a diverse range of devices within one unified platform.
