Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×Secure your Outlook Web Access (OWA) and on-premises Exchange with an easy and reliable Single Sign-On (SSO) product from miniOrange. With this, your users only need to remember one set of login details to access OWA and other applications, making their experience smoother and more secure.
OWA single sign-on works with your existing Identity Providers (IDPs), like Microsoft Azure AD, ADFS, Okta, and others. This guide will help you set up OWA SSO step-by-step, so you can simplify access, reduce the hassle of multiple passwords, and make logging in faster for everyone.
You start by trying to log in directly to your OWA and on-premise Exchange account. Your login request is then securely redirected to your Identity Provider (like Microsoft Entra) for verification. Once you successfully authenticate there, you’ll be logged into your OWA account without needing to enter your credentials again.
Here, you first log in to your Identity Provider (such as Microsoft Entra) using your credentials. After that, you can easily access your OWA and other connected apps from your Identity Provider dashboard without having to log in again for each service.
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.

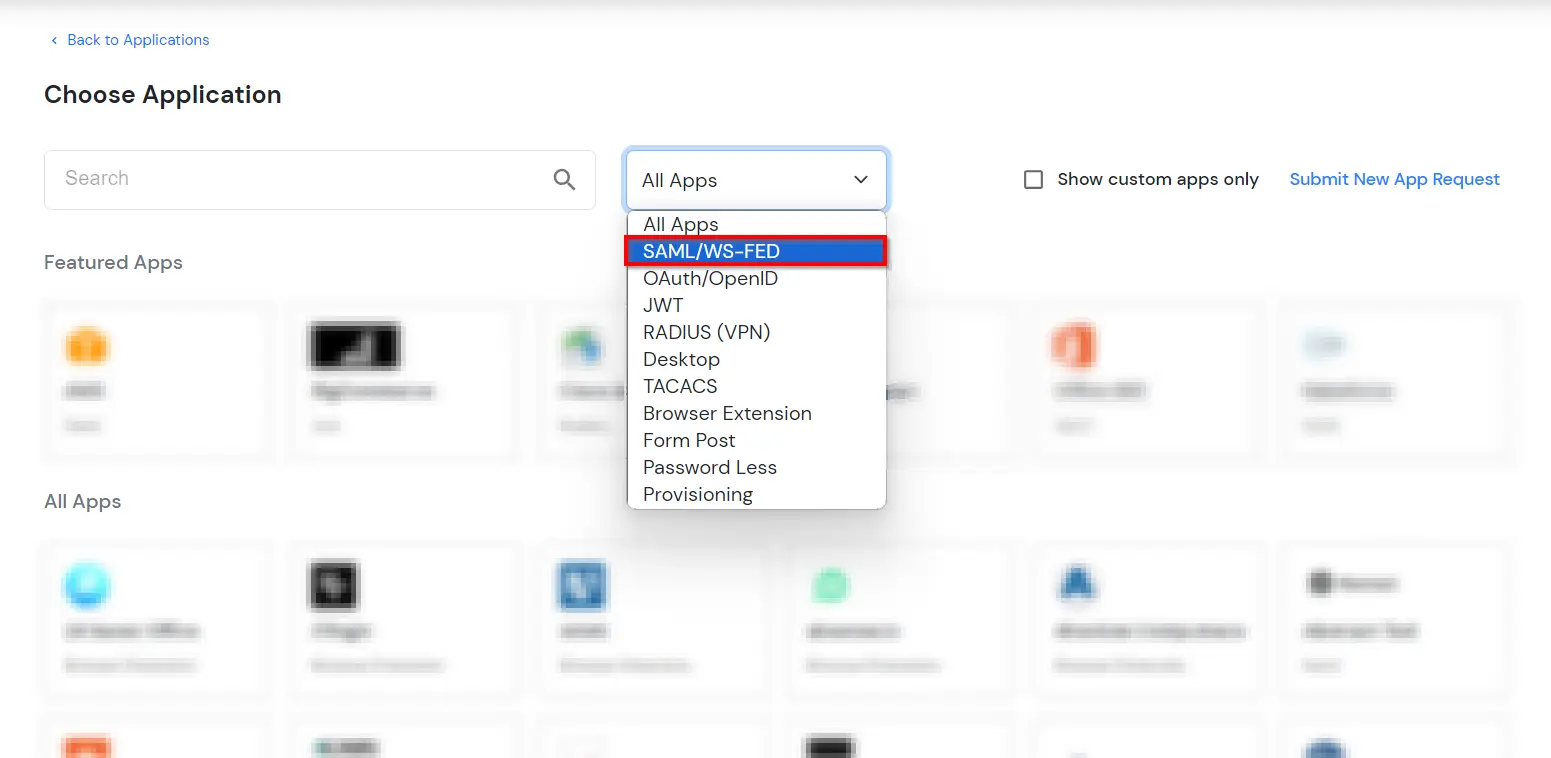
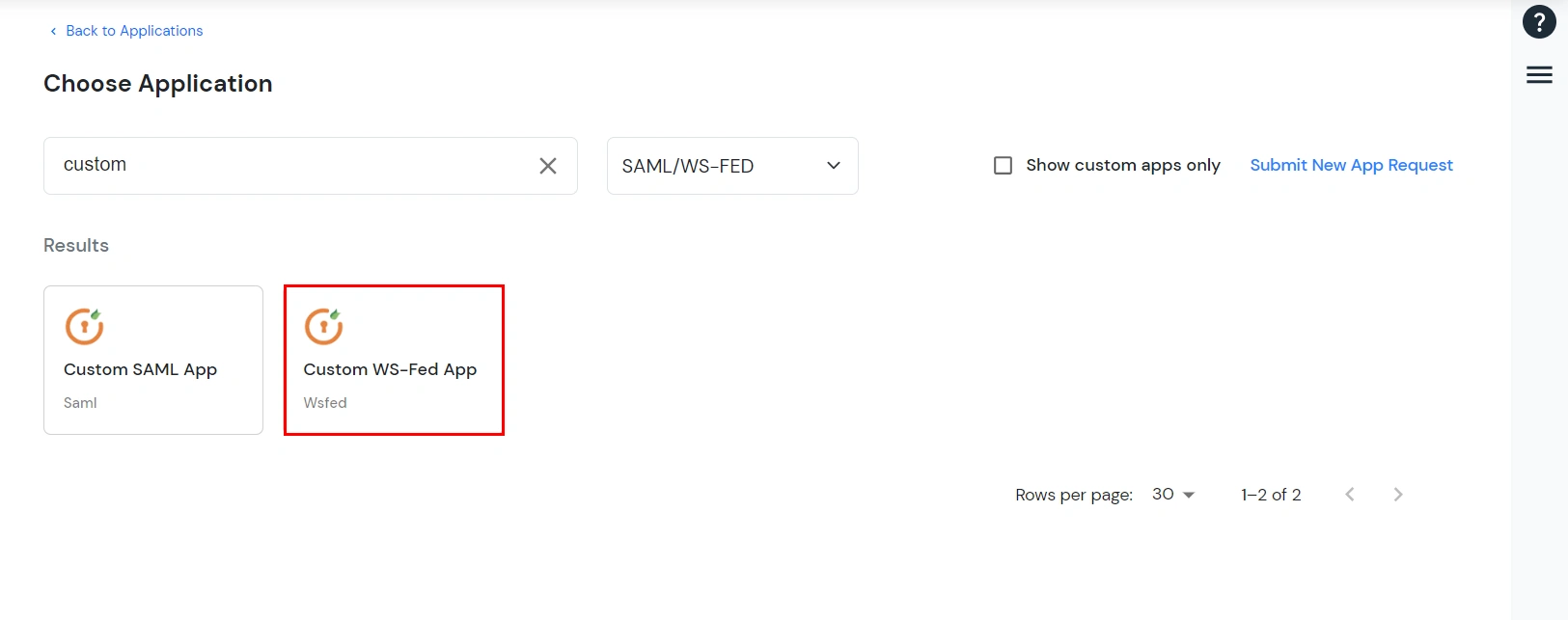
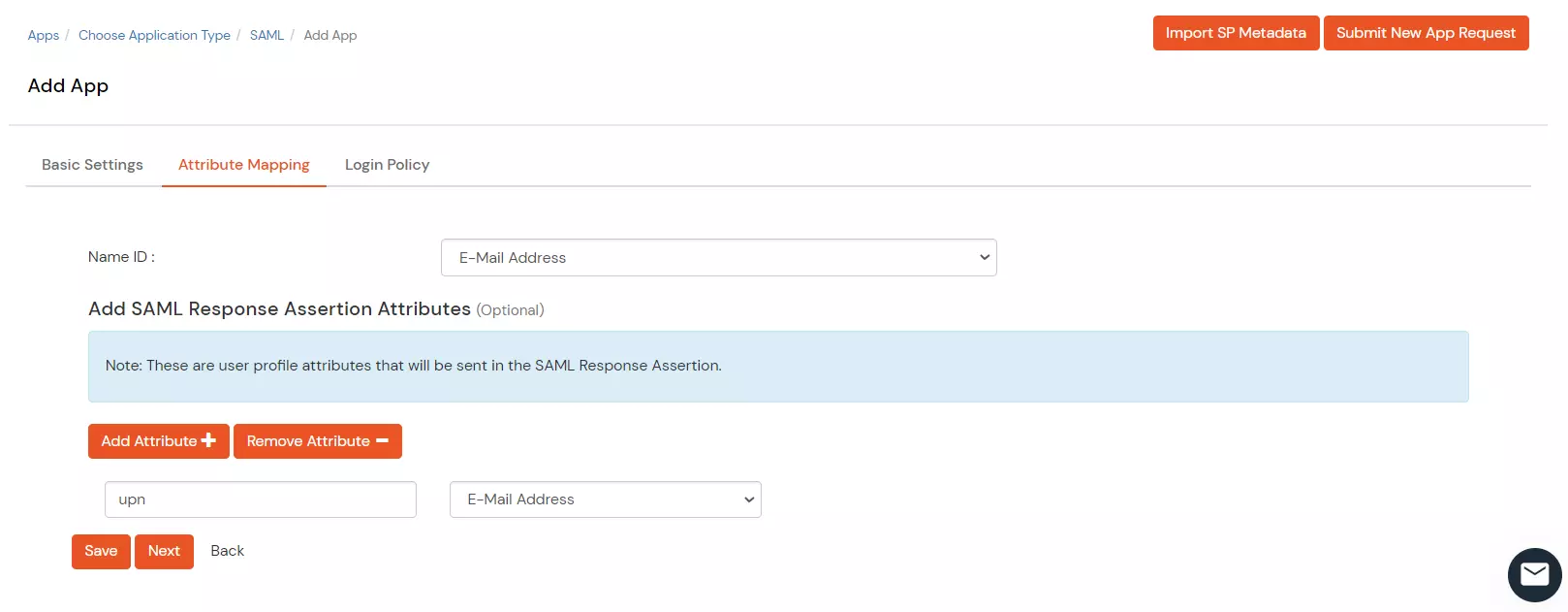
Outlook Web Access OWAhttps://{owa-url} (e.g., https://mail.example.com/owa)https://{owa-url} (e.g., https://mail.example.com/owa)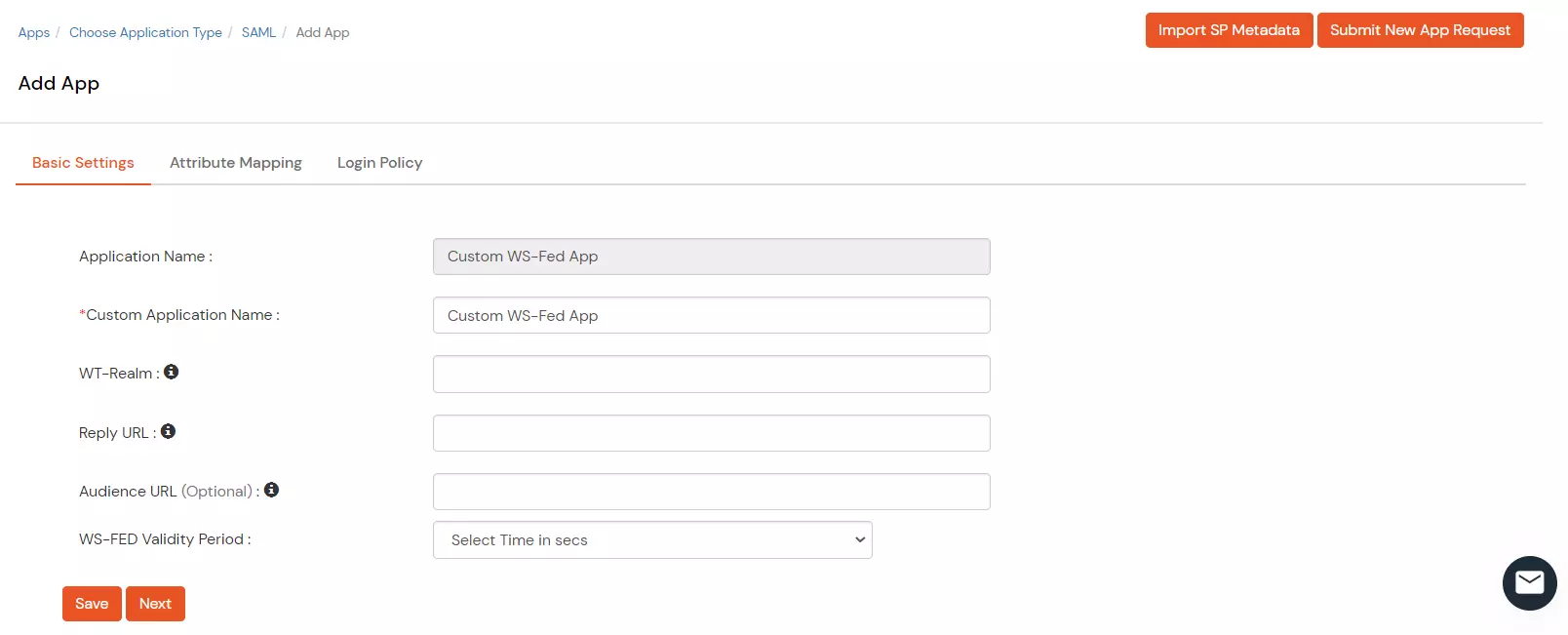
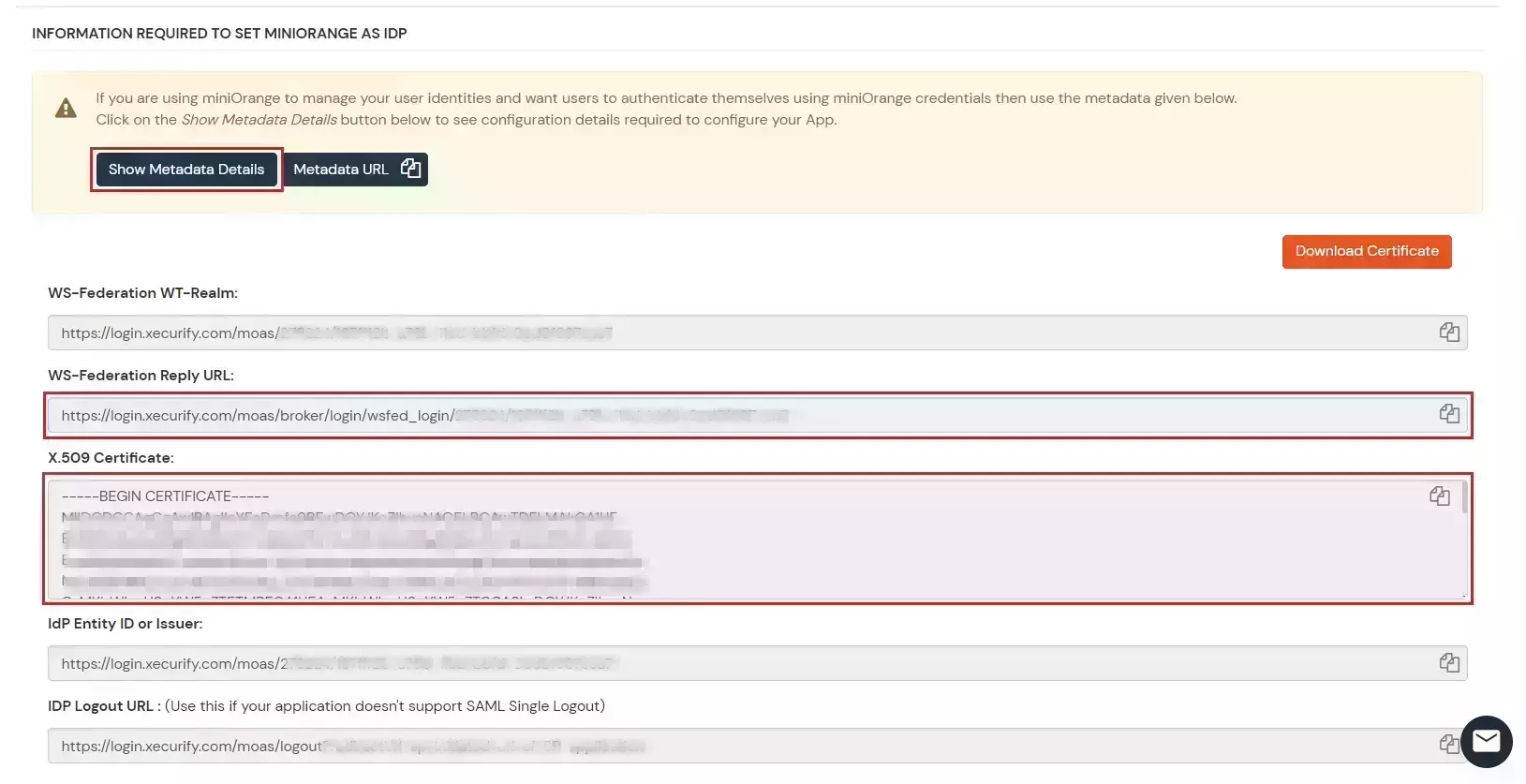
$uris=@("https://##Base URL##/owa/","https://##Base URL##/ecp/","https://##Base URL##/owa","https://##Base URL##/ecp")Note: Make sure the certificate thumb print is in uppercase.
Set-OrganizationConfig -AdfsIssuer "##miniOrange URL##" -AdfsAudienceUris $uris -AdfsSignCertificateThumbprint ##Cert Thumbprint##
Get-EcpVirtualDirectory | Set-EcpVirtualDirectory -AdfsAuthentication $true
-BasicAuthentication $false -DigestAuthentication $false -FormsAuthentication $false
-WindowsAuthentication $falseGet-OwaVirtualDirectory | Set-OwaVirtualDirectory -AdfsAuthentication $true
-BasicAuthentication $false -DigestAuthentication $false -FormsAuthentication $false
-WindowsAuthentication $false -OAuthAuthentication $false# Restart w3svc and was
net stop was /y
net start w3svc

Get-OwaVirtualDirectory | Set-OwaVirtualDirectory -AdfsAuthentication $false
-BasicAuthentication $false -DigestAuthentication $false -FormsAuthentication $true
-WindowsAuthentication $false -OAuthAuthentication $falseGet-EcpVirtualDirectory | Set-EcpVirtualDirectory -AdfsAuthentication $false
-BasicAuthentication $false -DigestAuthentication $false -FormsAuthentication $true
-WindowsAuthentication $false# Restart w3svc and was
net stop was /y
net start w3svc
Yes, miniOrange can authenticate users from external directories such as Microsoft Active Directory, OpenLDAP, AWS, and more.
The OWA single sign-on supports multiple authentication protocols, including SAML, OAuth, LDAP, and OIDC, to connect with various identity systems.
