Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
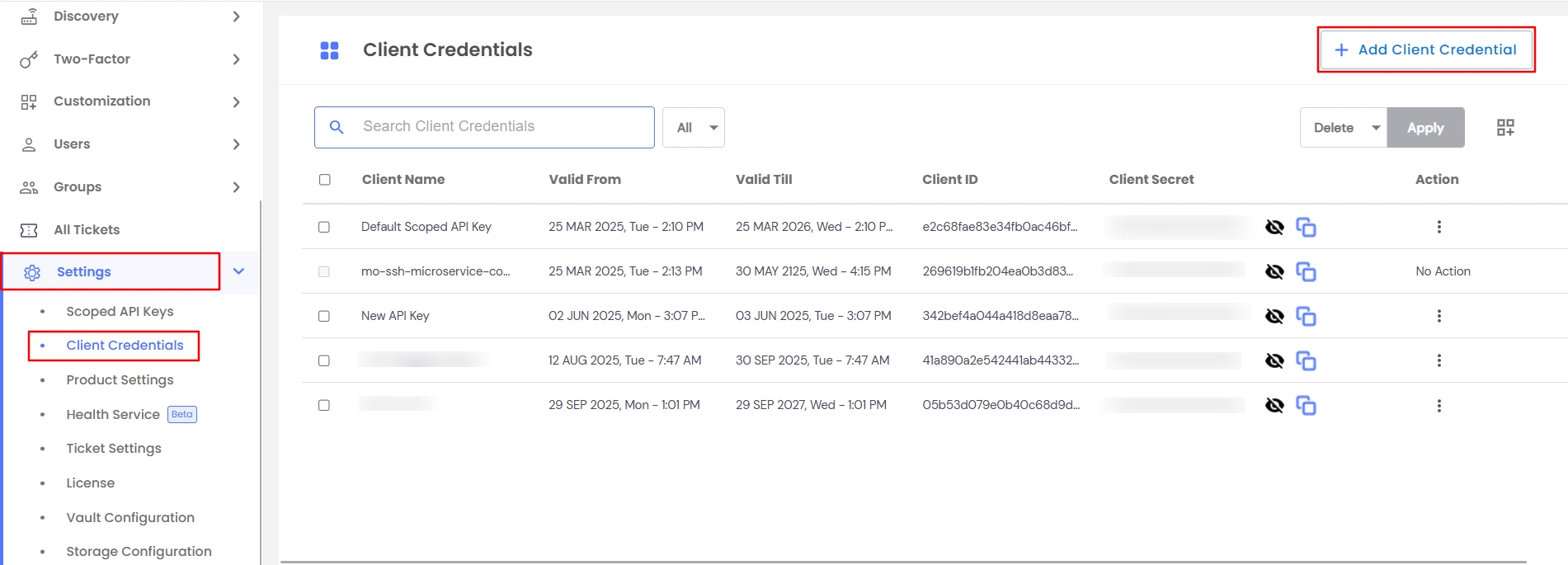
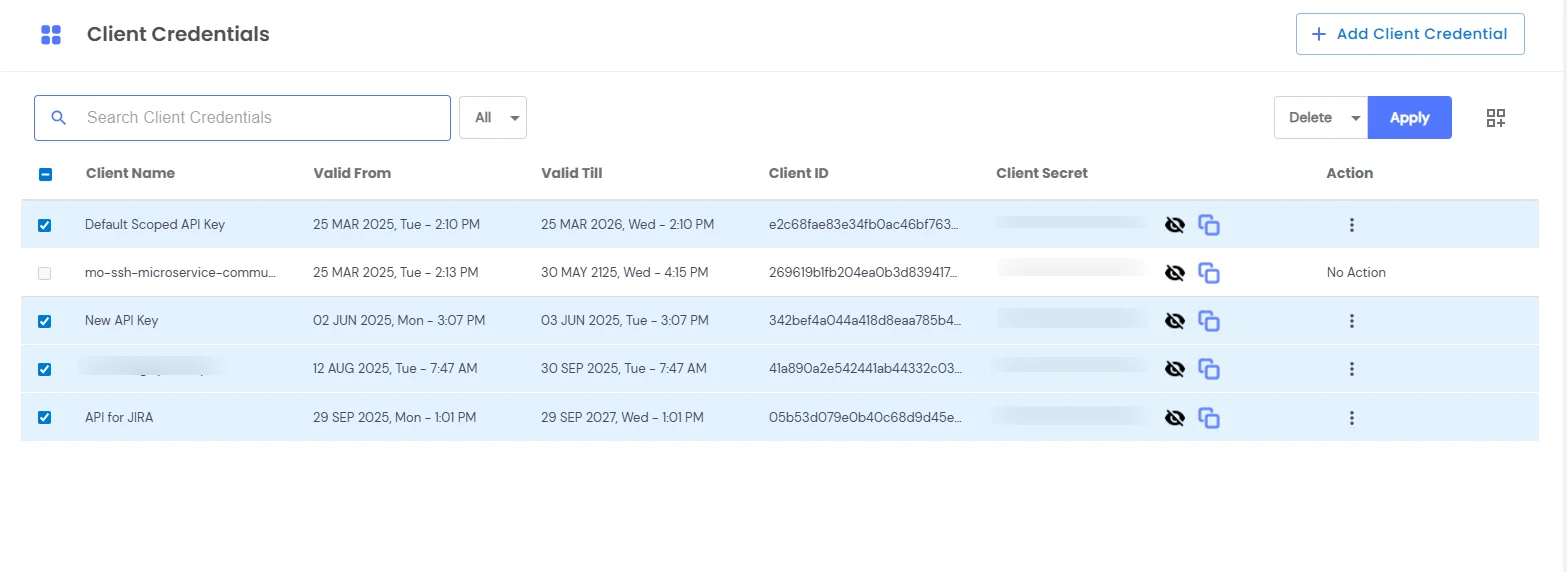
×The miniOrange PAM solution provides two default client credentials - Default Client Credential and mo-ssh-microservice-communication-key.
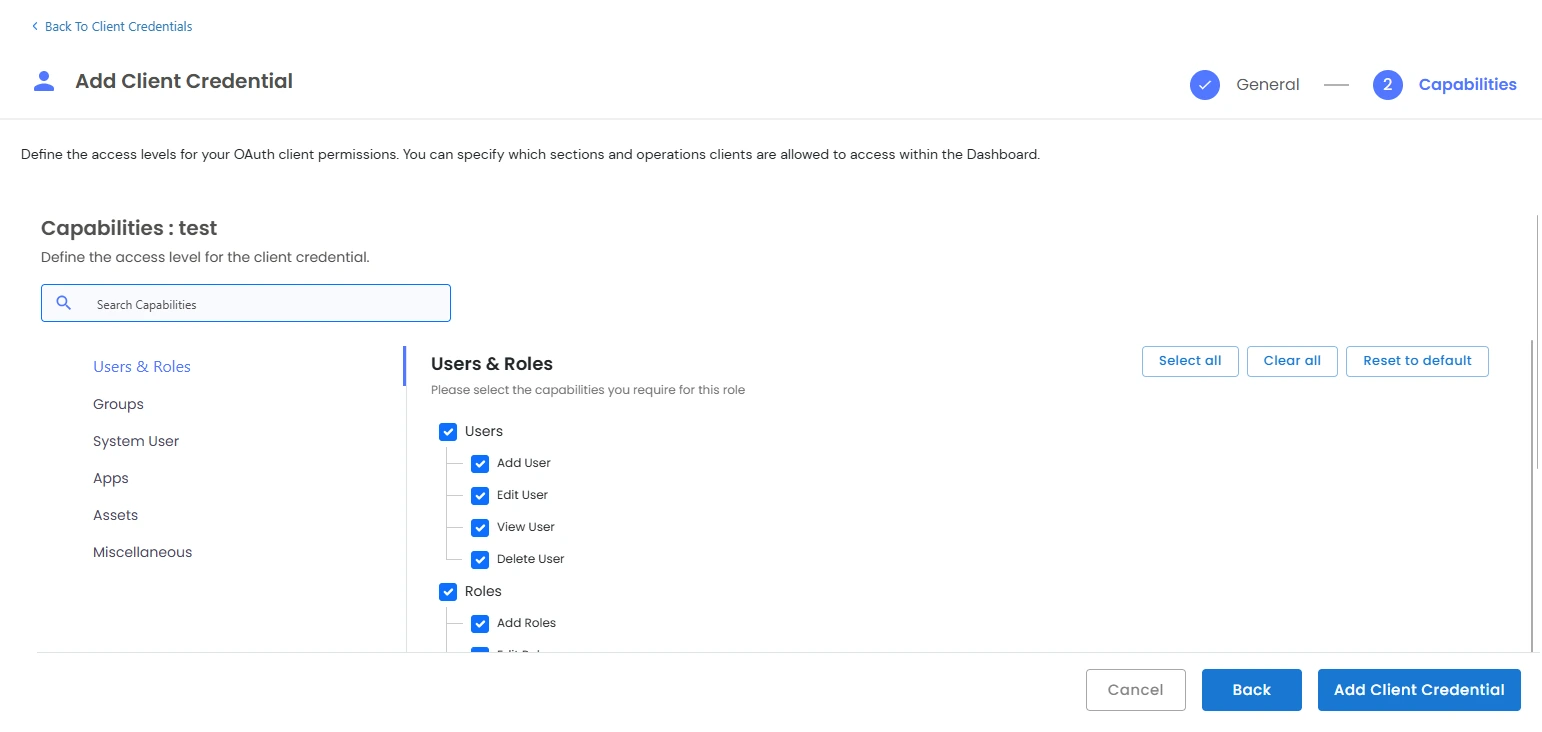
We also provide the feature to create custom client credentials with selected scopes. Admin or Additional admin who has the capability to add client credential and edit scopes. After logging in, you will be able to see a dropdown menu named Settings in the left sidebar.
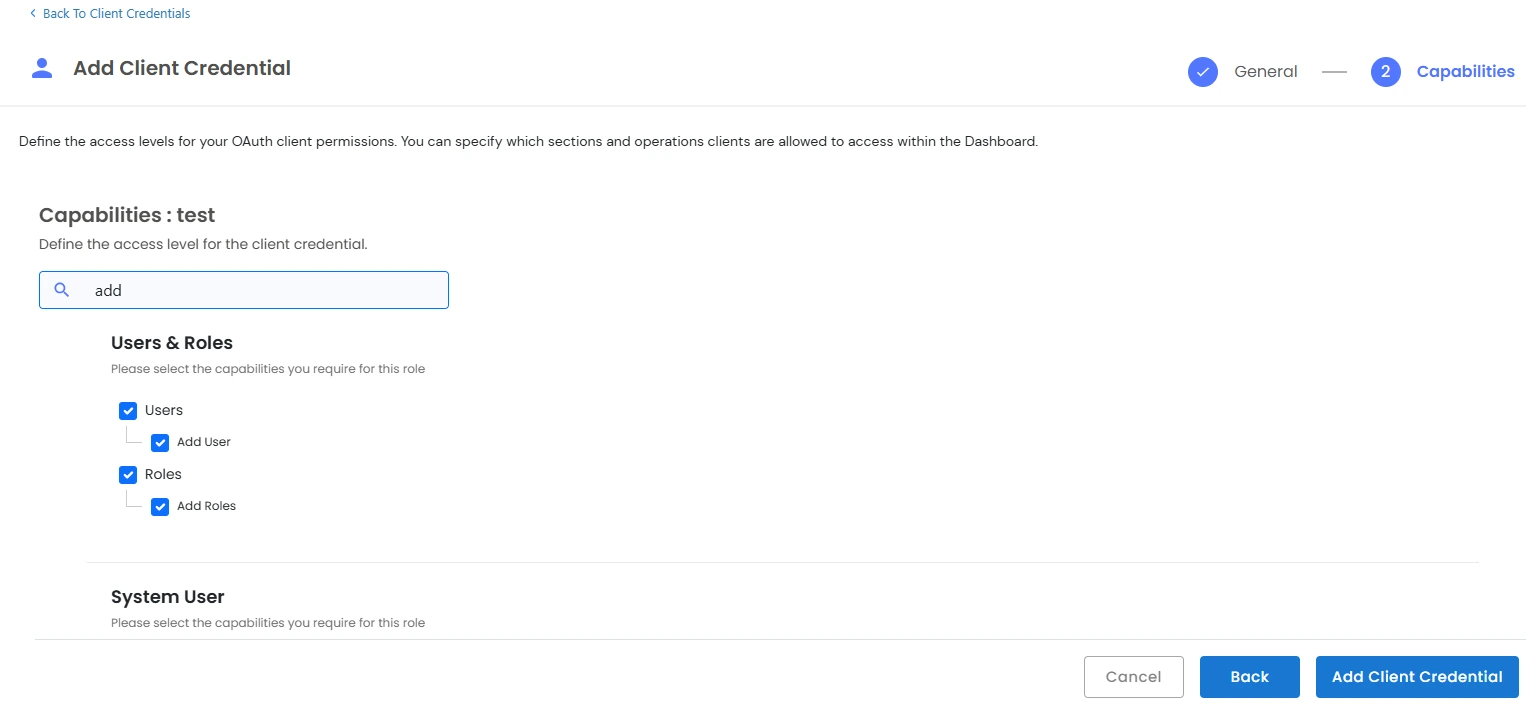
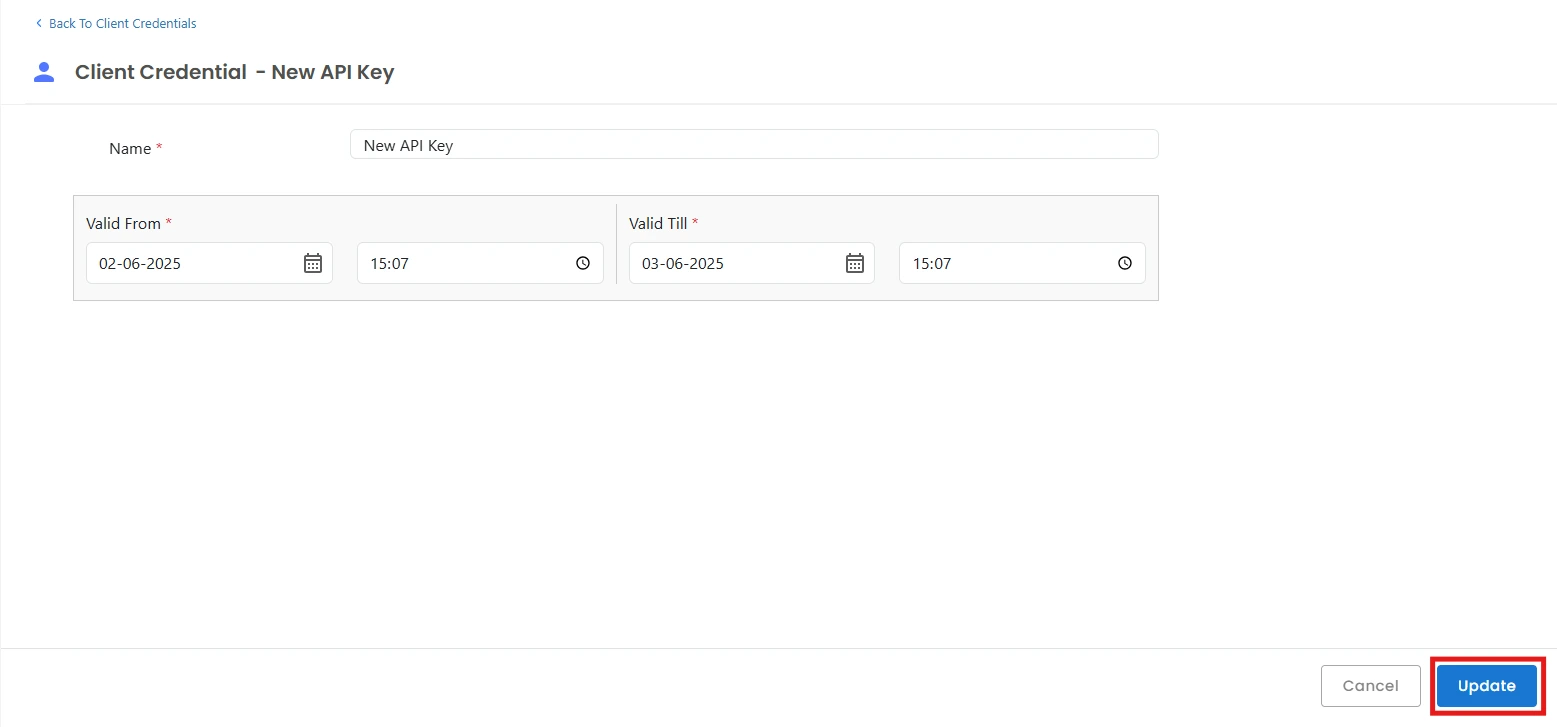
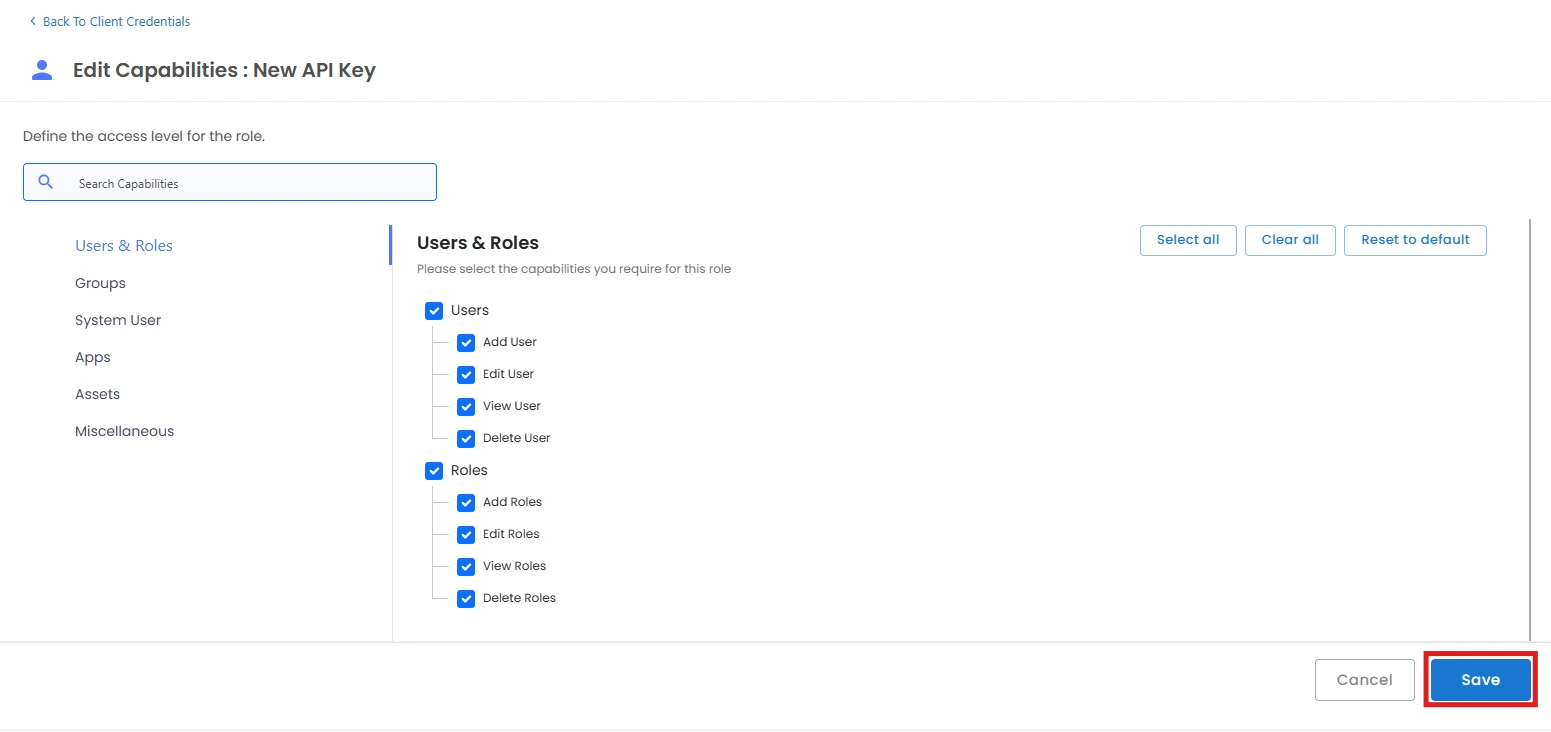
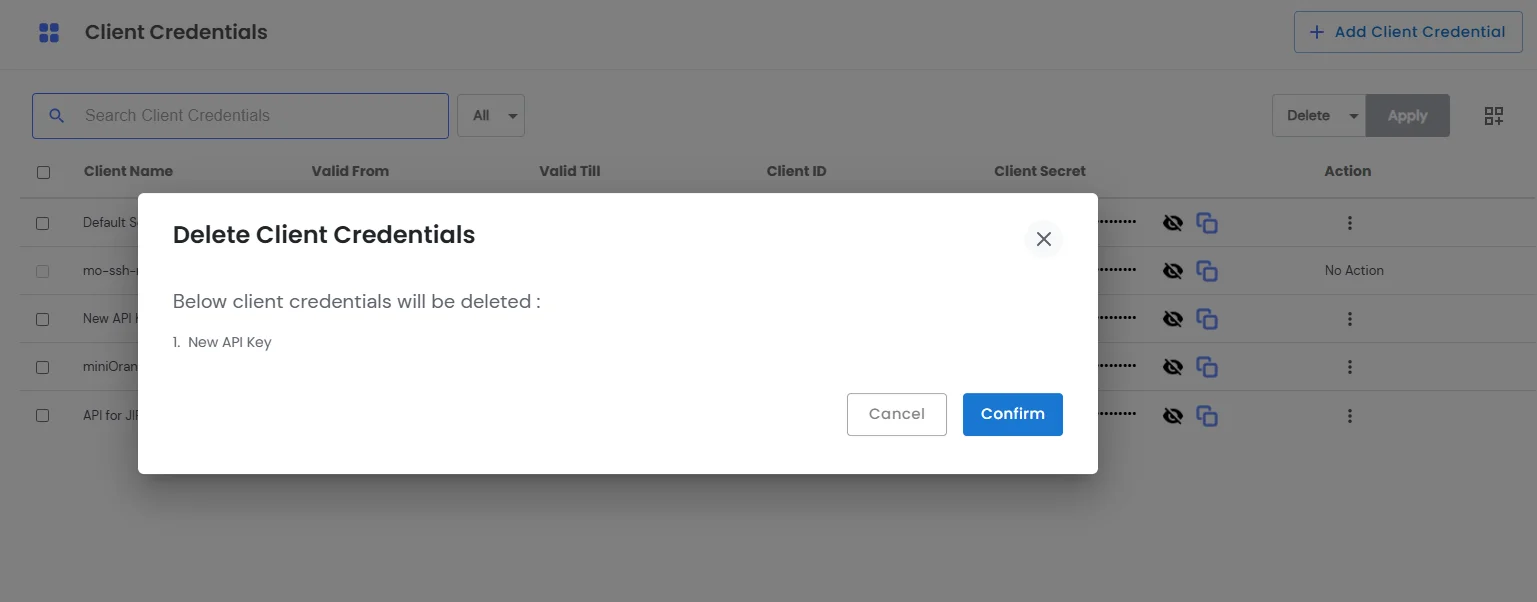
Token-based Authentication
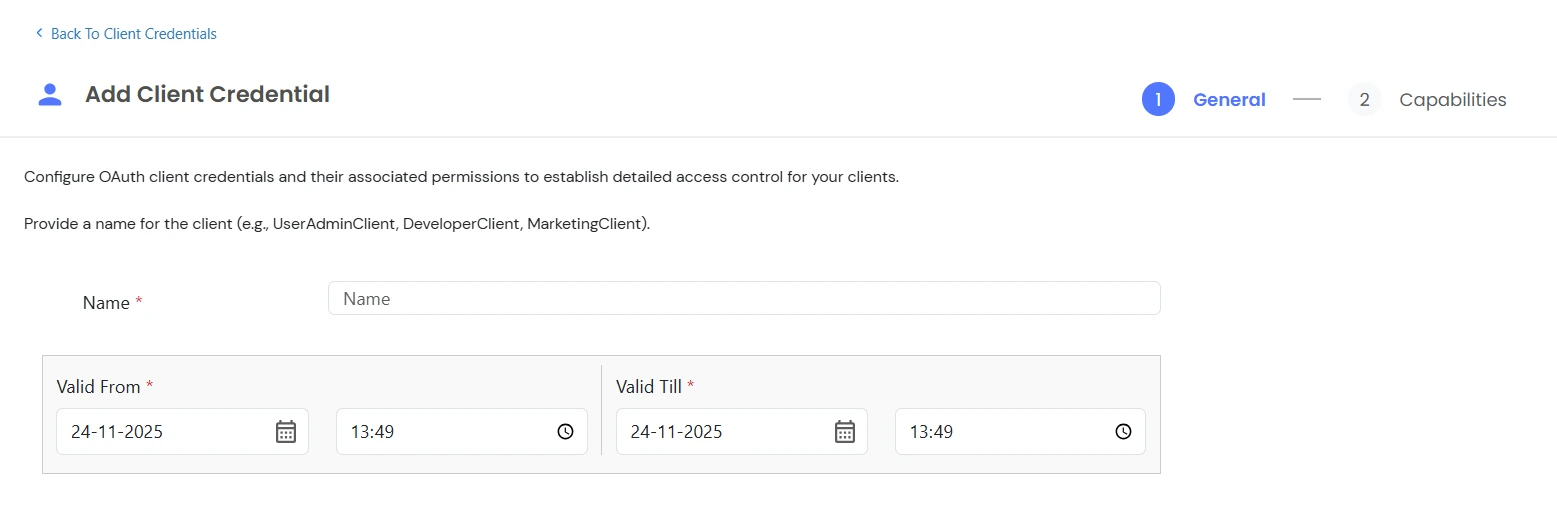
Before you can use the OAuth Client Credentials, you need to have them created by a PAM administrator. If you’re the administrator, follow the Creating OAuth Client Credentials section below.
You’ll need: - client_id: A unique identifier for your application - client_secret: A secret key for authentication - customer_id: Your PAM Customer ID (e.g., “10001”).
This is your first API call - you exchange your client credentials for an access token.
https://{base_url}//pam/apps/autheticate/oauth/token-generation/
{
"grant_type": "client_credentials",
"client_id": "your_client_id",
"client_secret": "your_client_secret",
"customer": "10001"
}
{
"access_token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJjdXN0b21lcl9pZCI6IjEwMDAxIiwiaWF0IjoiMjAyNC0wMS0xNVQxMDozMDowMFoiLCJleHAiOiIyMDI0LTAxLTE1VDExOjMwOjAwWiIsImNsaWVudF9pZCI6MSwic2NvcGVzIjp7Li4ufSwiY2xpZW50X25hbWUiOiJNeSBBcHBsaWNhdGlvbiIsImdyYW50X3R5cGUiOiJjbGllbnRfY3JlZGVudGlhbHMifQ.signature",
"token_type": "Bearer",
"expires_in_minutes": 60
}
Important: Save the access_token - you’ll use this for all subsequent API calls.
For all subsequent requests, you’ll use the Bearer token from Step 2.
https://{base_url}/pam/apps/users/user/(or any other PAM API endpoint)
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9... (your actual token)
GET https://{base_url}/pam/apps/users/user/
Headers:
Authorize: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9...
POST https://{base_url}/pam/apps/users/user/
Headers:
Authorize: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9...
Content-Type: application/json
Body:
{
"username": "newuser",
"email": "user@example.com",
"first_name": "John",
"last_name": "Doe"
}
Tokens expire after 60 minutes. When you get an authentication error:
The following PAM APIs support OAuth Client Credential authentication: