Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×The Threat Detection feature in miniOrange Privileged Access Management (PAM) is designed to enhance security by identifying, analyzing, and blocking potential threats in real-time. The feature leverages advanced algorithms, including User Behavior Analytics (UBA), to continuously monitor privileged activities, detect anomalies, and take immediate actions such as blocking suspicious activities, sending alerts to administrators, and generating detailed reports.
This document provides a comprehensive overview of the Threat Detection feature in miniOrange PAM, including its core functionality, architecture, algorithms, and the configuration steps for administrators. Additionally, the document includes diagrams to help better understand the technical flow and structure of the feature.
User Behavior Analytics (UBA) is the cornerstone of the Threat Detection feature. It monitors the activity of privileged users and compares it against established baselines of normal behavior. Any deviation from this baseline triggers the detection of potential threats. UBA relies on machine learning algorithms to build dynamic models of user behavior, allowing the system to adapt to changing user patterns over time.
Anomalies are detected by analyzing a wide variety of parameters, such as:
When such anomalies are detected, miniOrange PAM uses real-time monitoring to trigger alerts, blocking actions, or even session termination if necessary.
miniOrange PAM employs a variety of algorithms for detecting threats:
Once a potential threat is detected, the system performs immediate actions:
miniOrange PAM allows administrators to configure threshold limits for specific user activities. For example, if a user attempts to log in more than five times within an hour with incorrect credentials, the system may flag this as a brute force attack.
The architecture of the Threat Detection feature in miniOrange PAM involves multiple components that work together to continuously monitor and respond to potential threats.
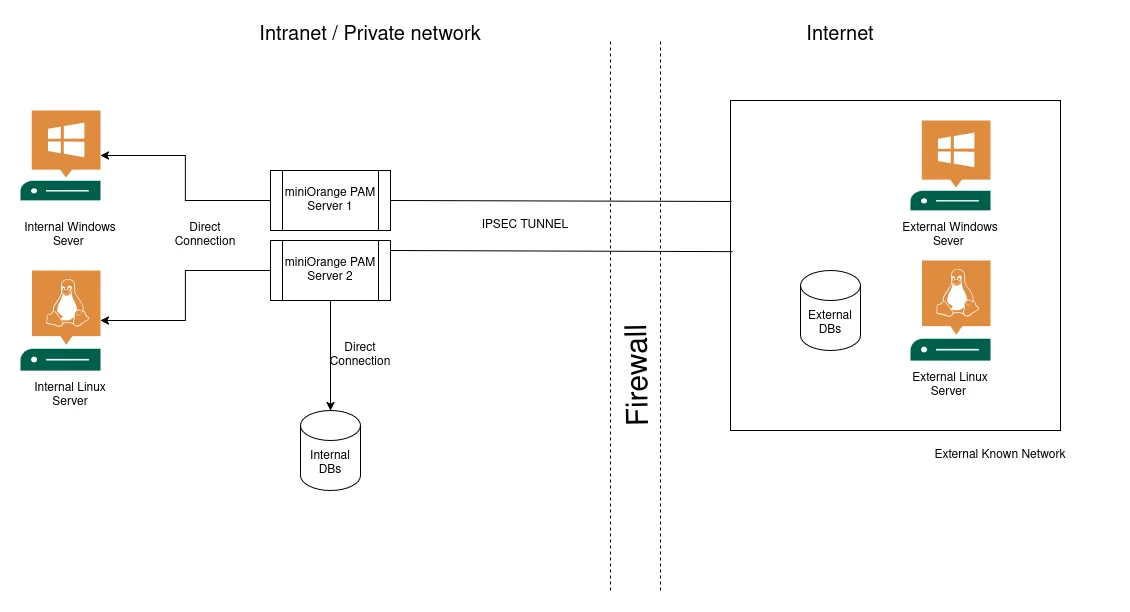
The User Activity Monitoring module captures all actions performed by privileged users, including logins, command executions, and resource accesses. It then sends this data to the Threat Detection Engine for further analysis.
This module stores activity logs for each user and their interactions with the system. The logs are analyzed by the Threat Detection Engine to detect any unusual activities.
The TDE is the central component that combines User Behavior Analytics (UBA), machine learning algorithms, and correlation techniques to detect potential threats. It compares the ongoing user activities against predefined baselines and generates threat alerts when suspicious activities are identified.
The Threat Response Module executes predefined actions when a threat is detected. These actions include:
Once a threat is detected, the Admin Notification System sends alerts to the administrator's preferred channels (email, SMS, or in-app notifications) with relevant details about the threat, enabling the administrator to take further action if necessary.
Administrators can configure the Threat Detection feature through the miniOrange PAM Admin Console. The following configurations are available:
Administrators can set up behavior baselines for each privileged user or group. These baselines will define what is considered "normal" activity, allowing the system to detect deviations effectively.
Threshold limits for various activities (e.g., failed login attempts, resource access attempts) can be customized to fit organizational policies. Once these thresholds are exceeded, the system will automatically trigger alerts and responses.
Administrators can configure actions such as:
The Threat Detection feature in miniOrange PAM provides a comprehensive solution for identifying and mitigating risks associated with privileged user activities. By leveraging advanced algorithms and User Behavior Analytics, the system can automatically detect and respond to potential threats in real-time, ensuring the highest level of security for privileged accounts.
This document has outlined the core components, architecture, and workflow of the Threat Detection feature, providing administrators with a clear understanding of how it works and how to configure it for their organization's needs.
For further support, contact pamsupport@xecurify.com or refer to the miniOrange PAM user guide for detailed instructions on configuring and using the Threat Detection feature.
