Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×Remote Desktop Gateway (RD Gateway) Multi Factor authentication (2FA/MFA) configuration adds additional 2FA security for secure access to your Remote Desktop, RDWeb, RemoteApp Access logons on top of Microsoft Entra ID logins. It also blocks connections to your Remote desktop protocol (RDP) servers if users have not passed Multi-factor/two-factor authentication where connection requests are proxied through a Remote Desktop Gateway (RD Gateway). Because RD (Remote Desktop) Gateway gives public network users access to critical resources located within companies, it only makes sense to add layers of access security to RD Gateway access via multi-factor authentication (2FA/MFA) on top of Microsoft Entra ID logins.
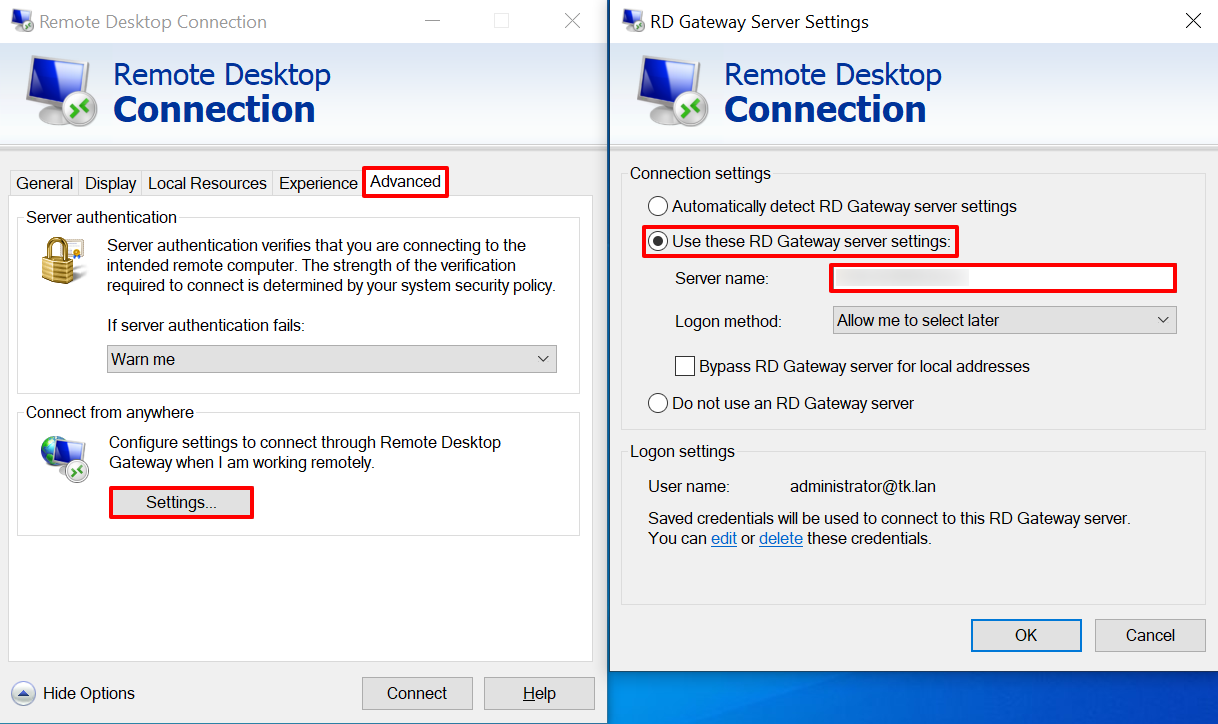
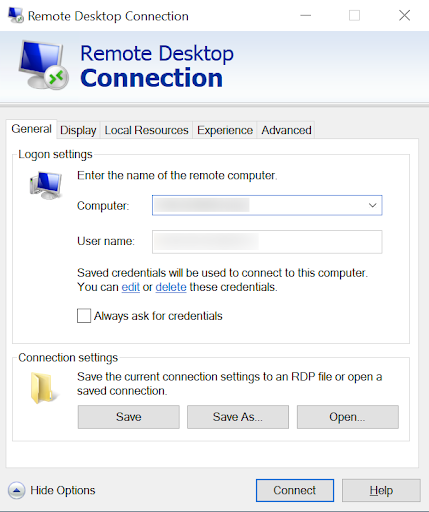
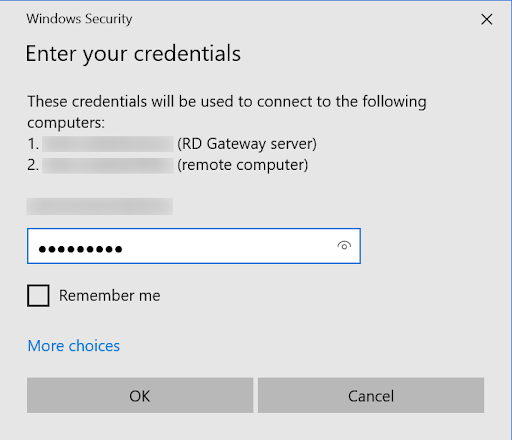
Using the miniOrange RD (Remote Desktop) gateway MFA solution with Microsoft Entra ID logins, you can configure 15+ MFA methods like Push Notification through miniOrange authenticator, and out of band methods like SMS and Email link to secure access for users. Once you have configured the miniOrange MFA solution for the Remote Desktop (RD) gateway, you will have to enter your computer name/username or address and the username along with the password. This can be your Microsoft Entra ID login credentials. Based on your 2FA method, you will receive a notification or SMS/Email link. Once you click on the link, you will be logged in. You can also provide secure access to your Windows and Linux machines with Microsoft Entra ID login using our Windows MFA Solution. Checkout the additional resources (at the bottom of this page) for more details.
A user can try to connect to RDS (Remote Desktop Services) via 2 ways:
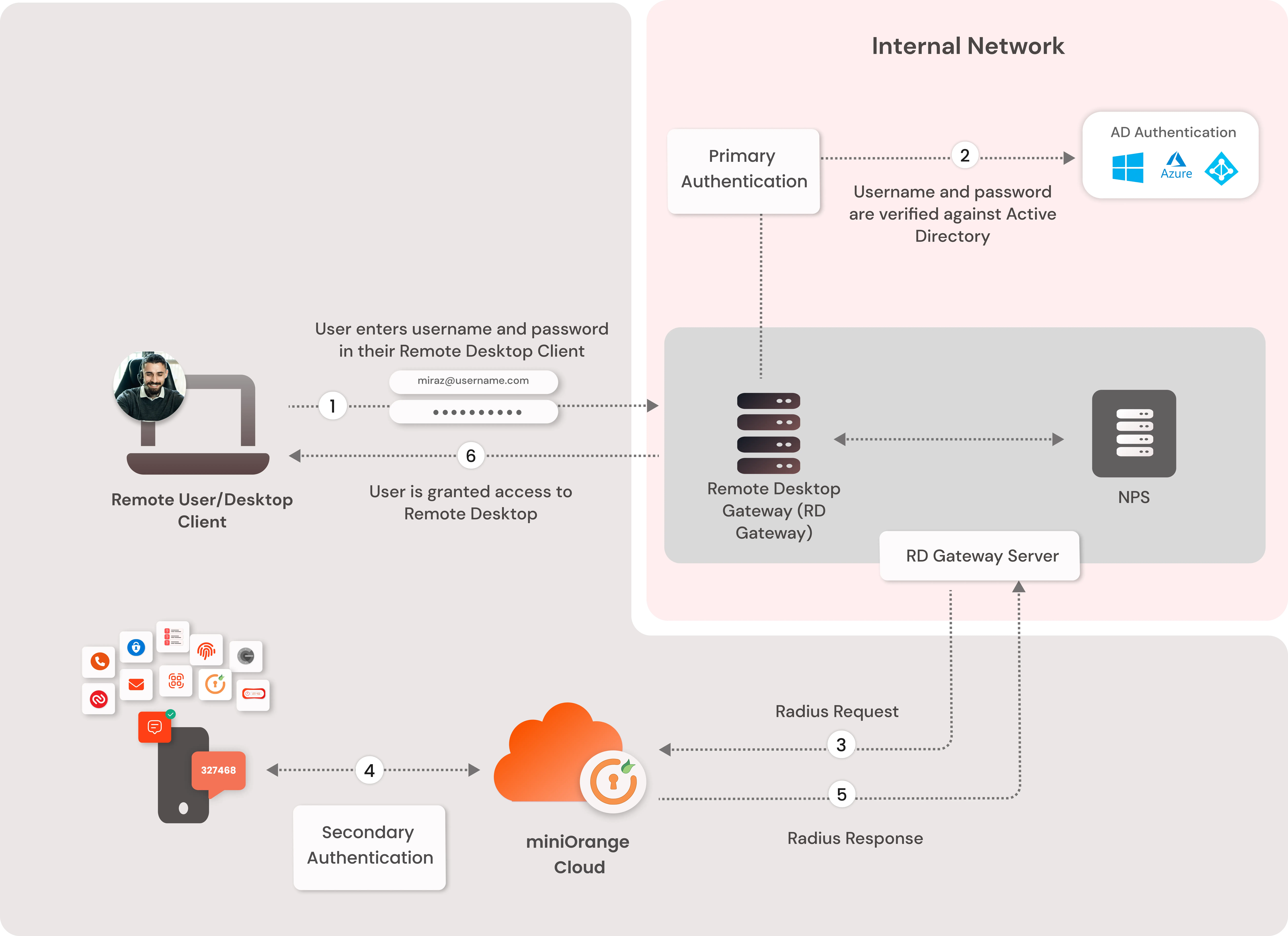
miniOrange Credential Providers can be installed on Microsoft Windows client and server operating systems to add Multi/two factor Authentication to Remote Desktop. In this way you can get secure access to our 2FA/MFA solution for Remote Desktop (RD) Gateway.
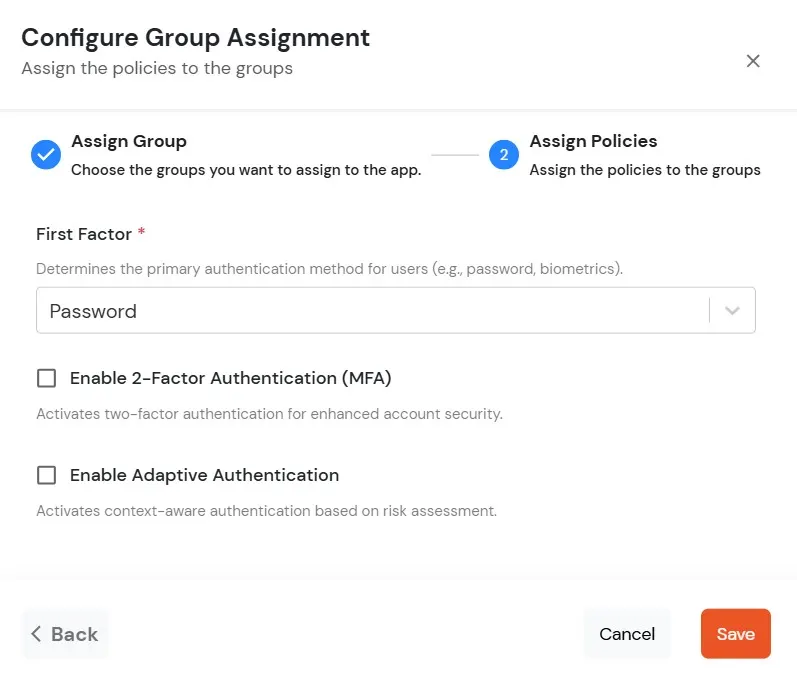
miniOrange supports following Authentication Methods for Multi-Factor Authentication (2FA/MFA):
| Authentication Type | Method | Supported |
|---|---|---|
| miniOrange Authenticator | miniOrange Push Notification | |
| SMS | SMS with Link | |
| Email with Link |
miniOrange offers free help through a consultation call with our System Engineers to Install or Setup secure access using Two-Factor Authentication for Remote Desktop (RD) Gateway with Microsoft Entra ID login solution in your environment with 30 days trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you setting it up in no time.
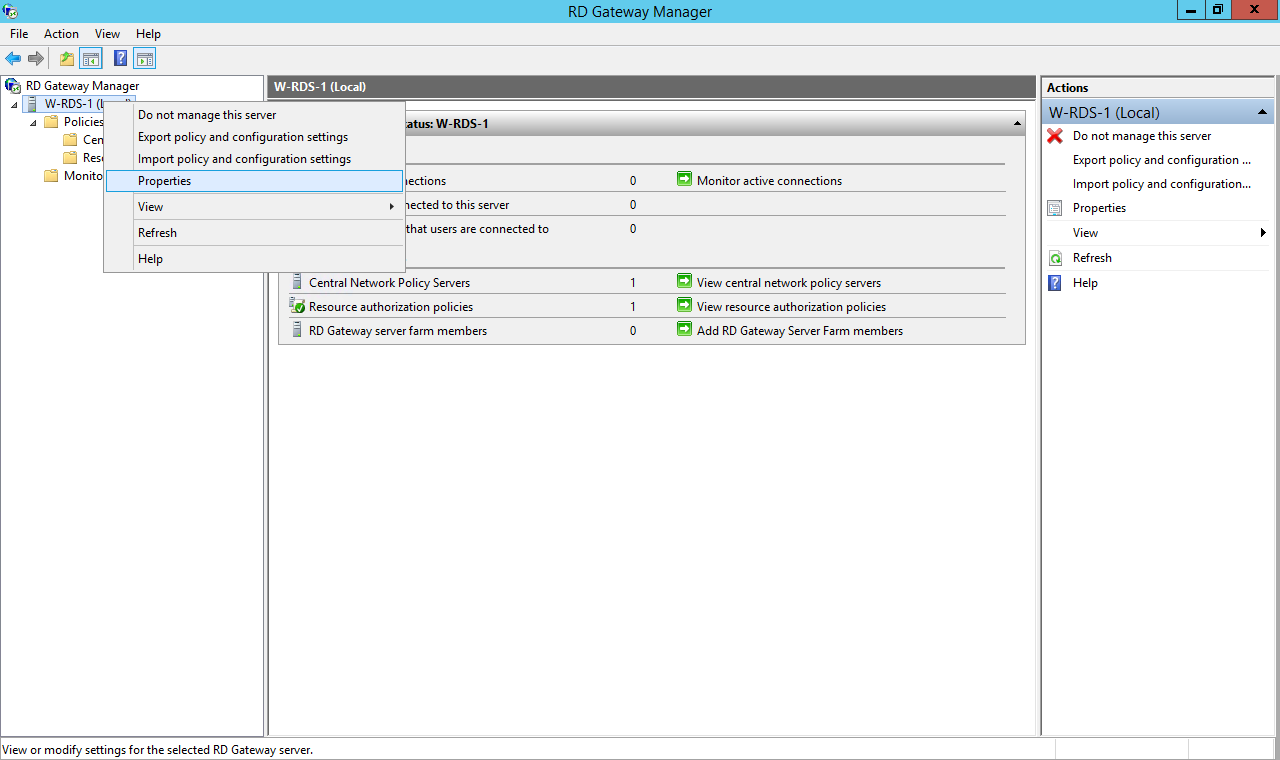
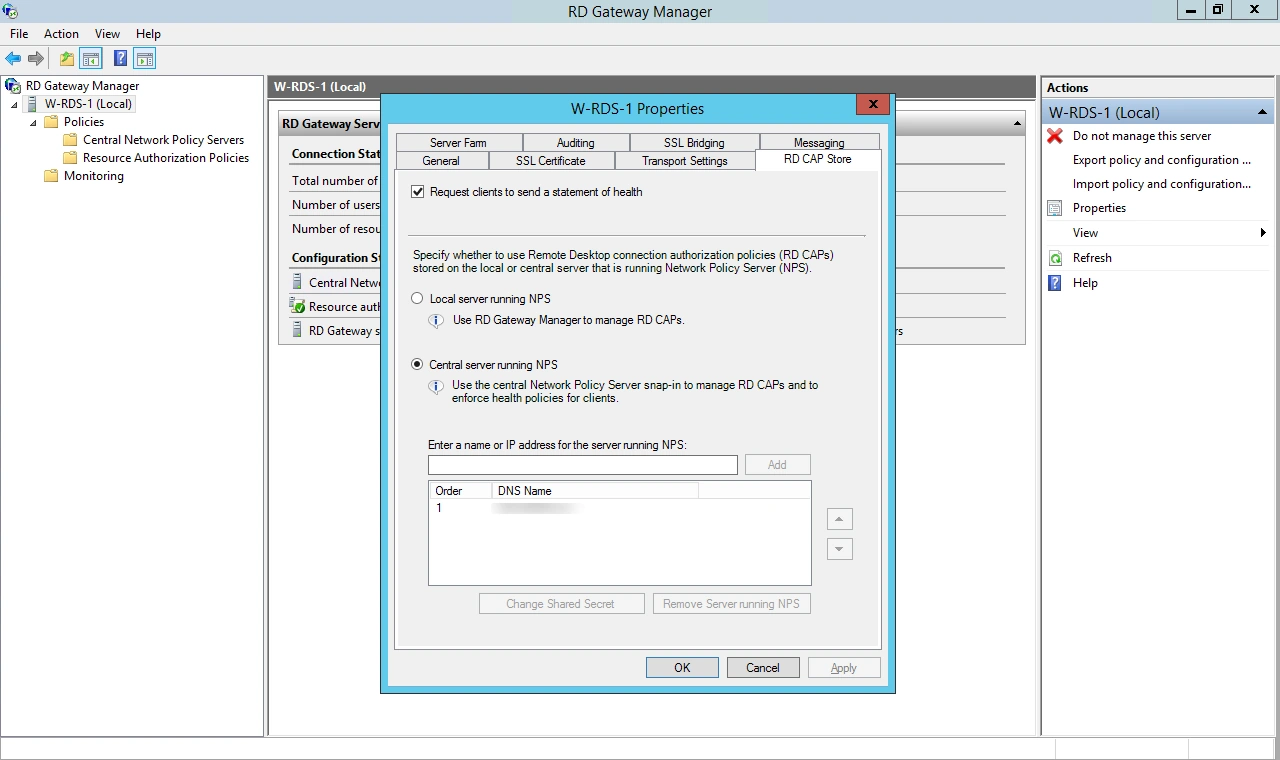
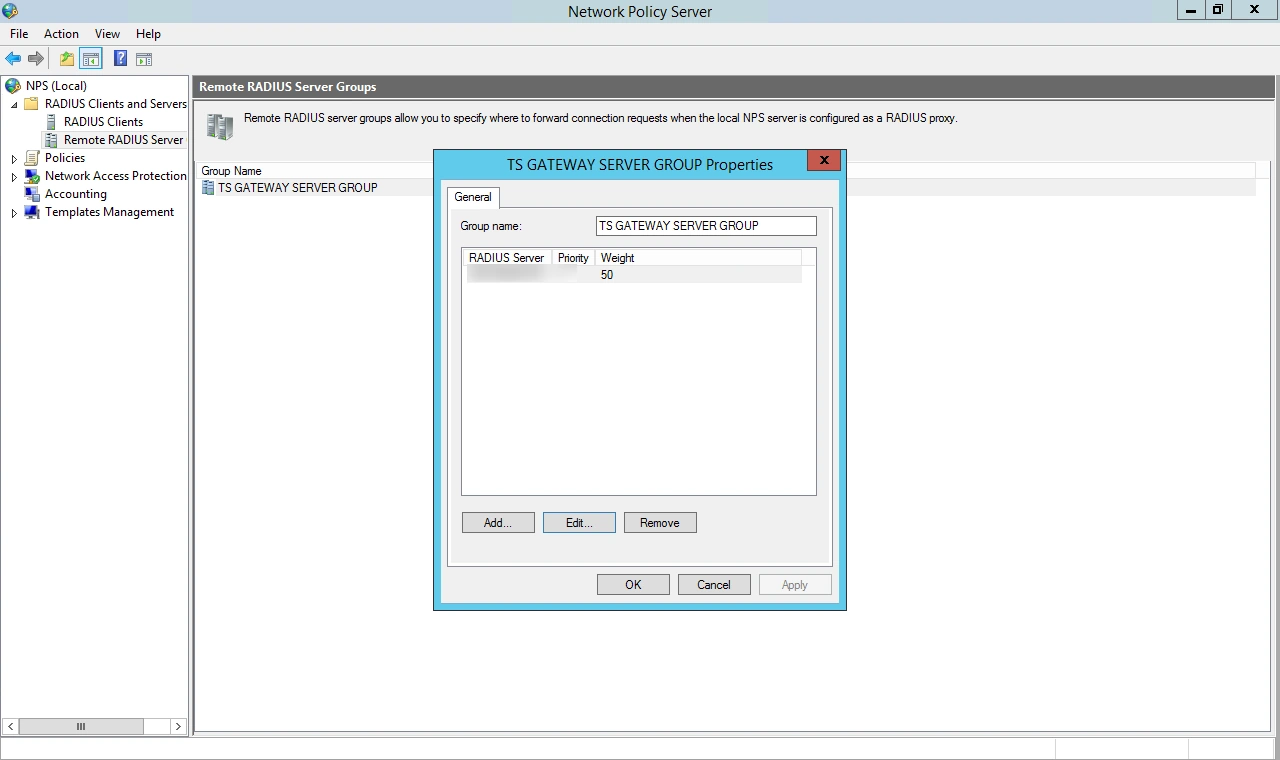
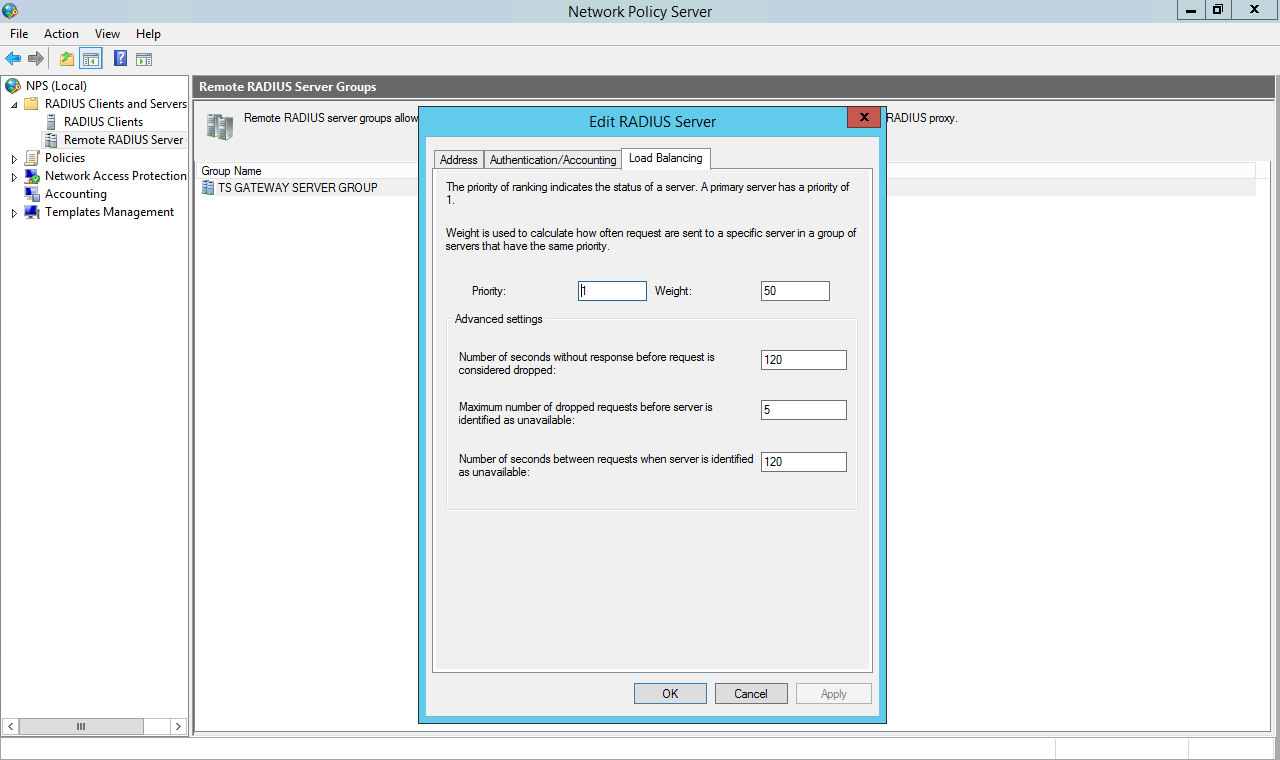
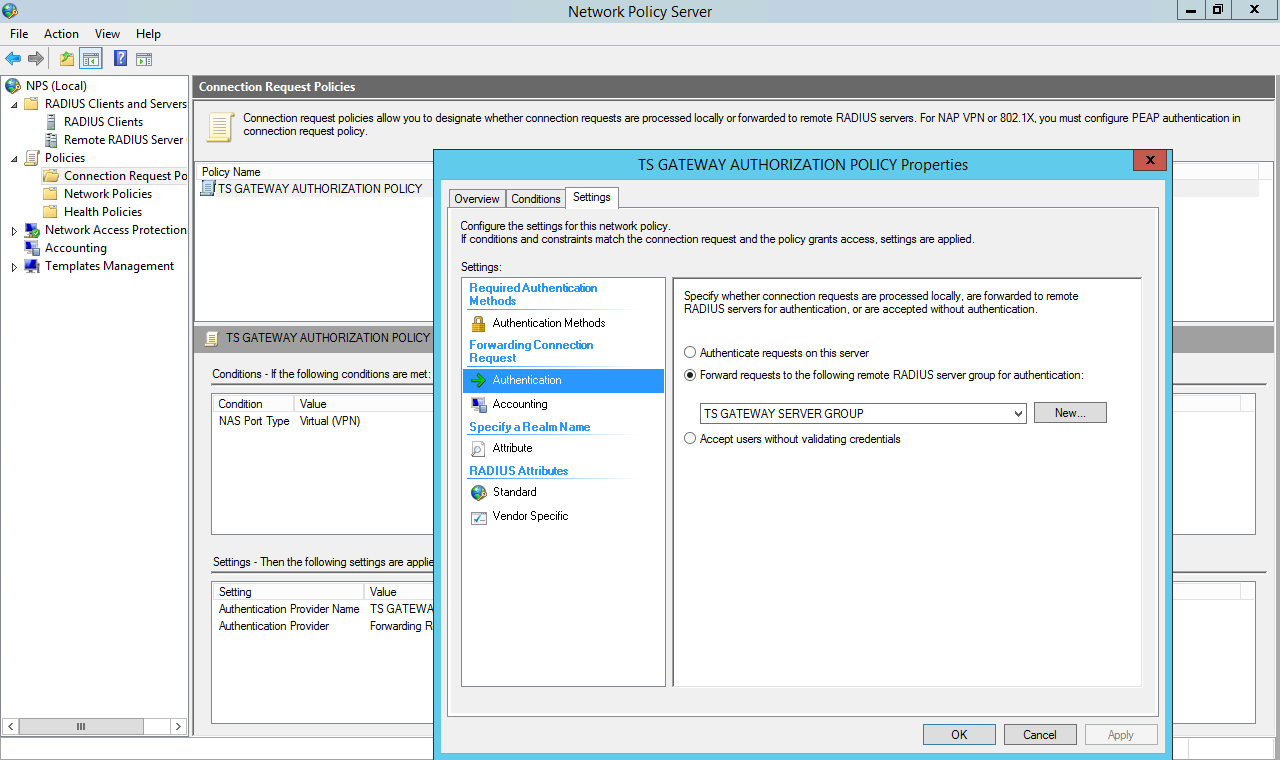
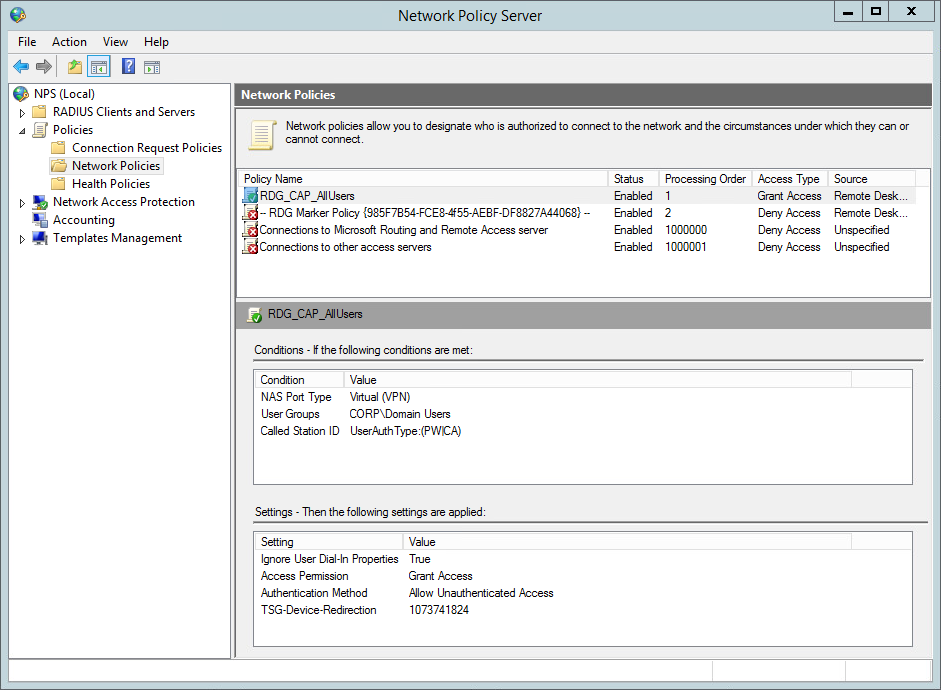
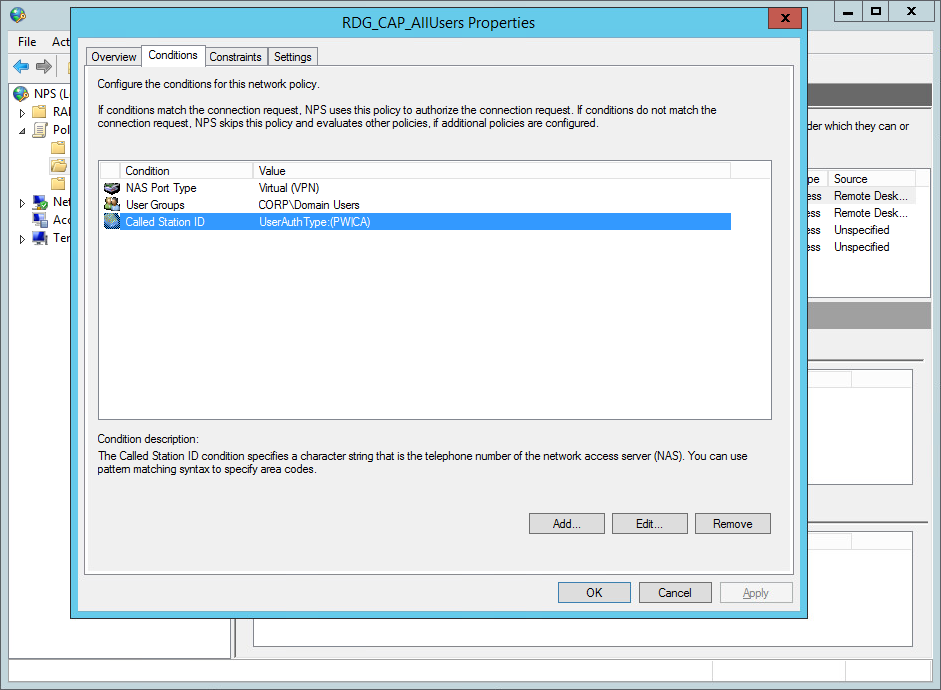

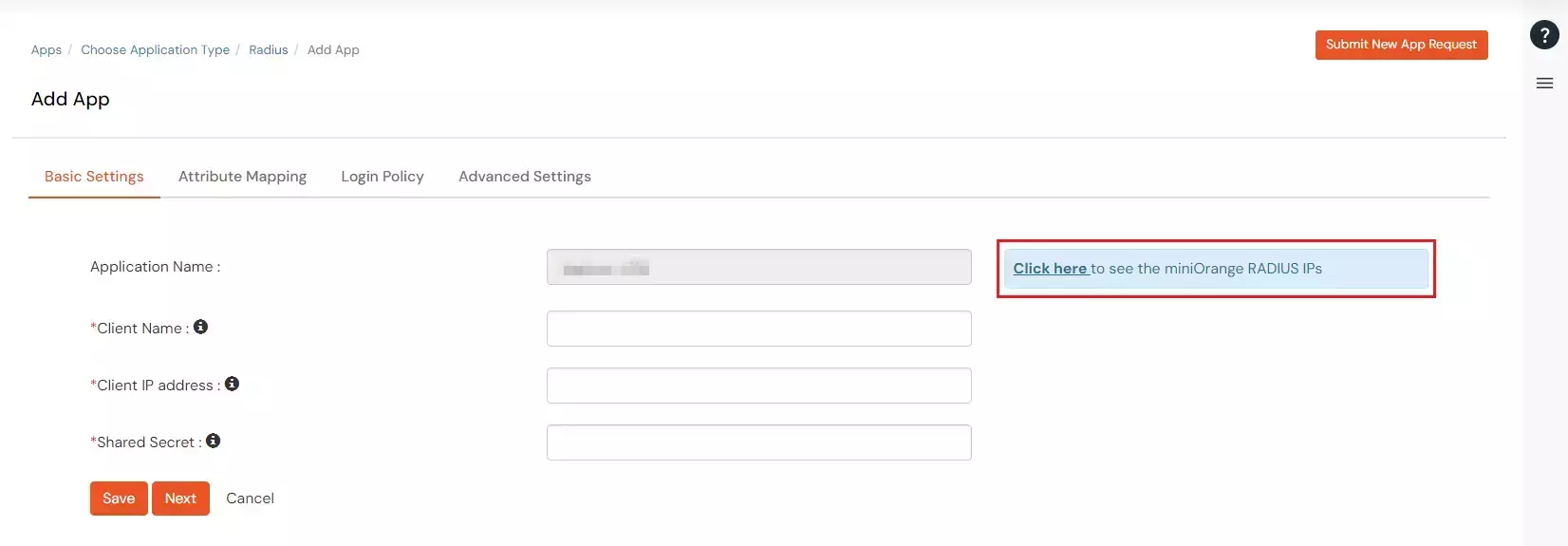
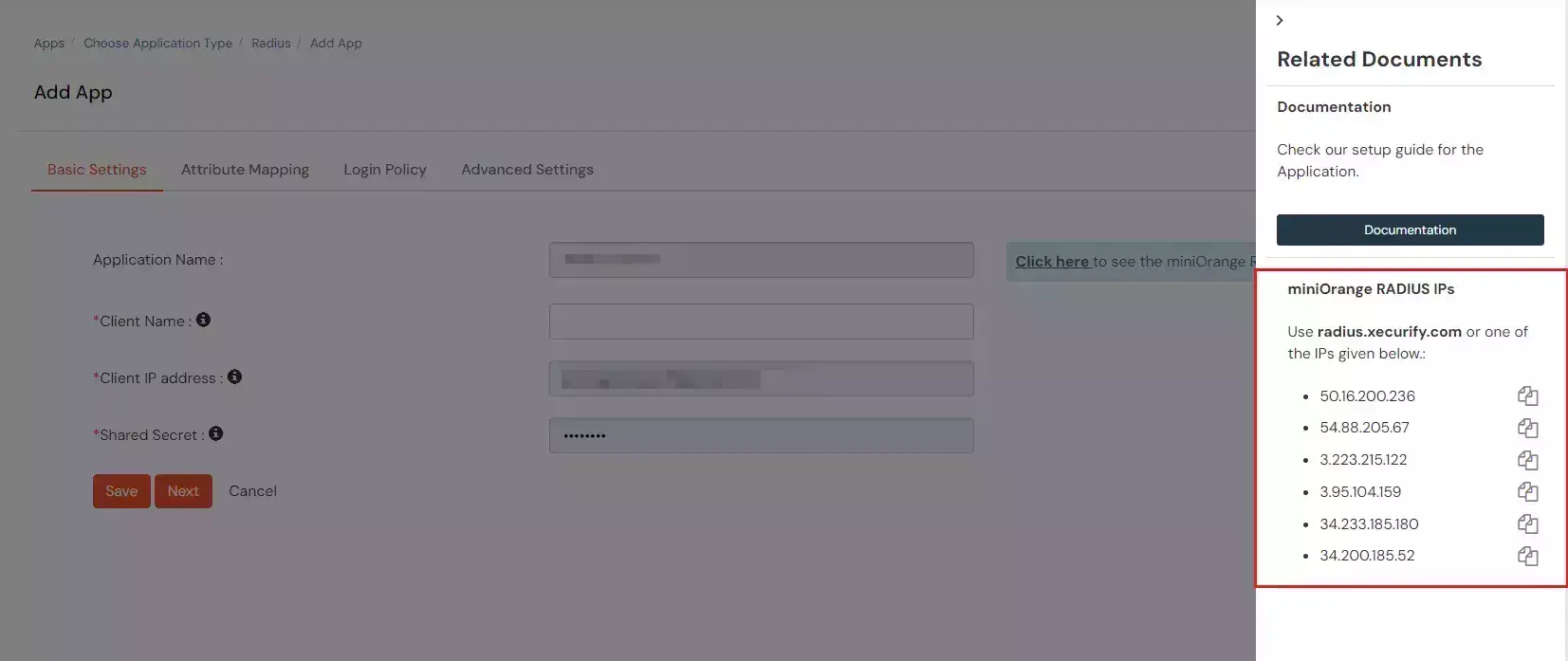
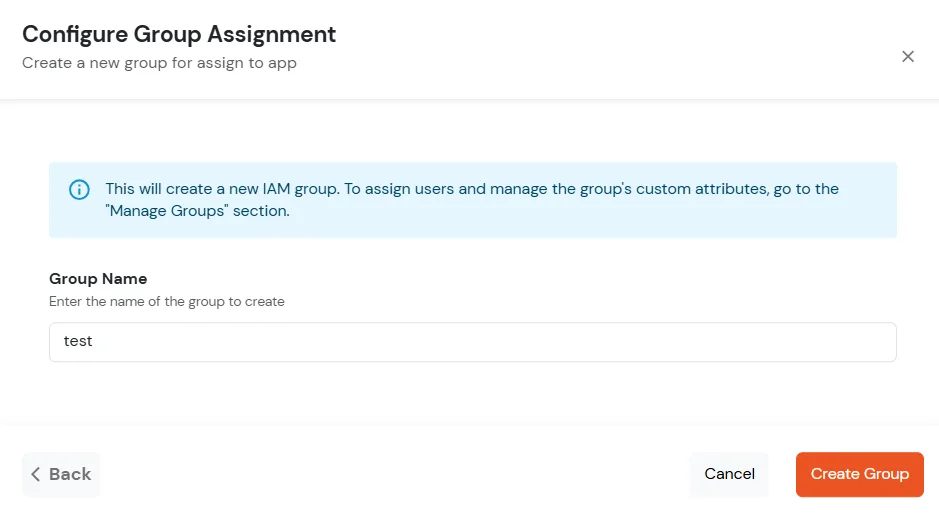
| Display Name: | Any name for your reference. |
| Client IP: | IP address of VPN server which will send Radius authentication request. |
| Shared Secret: | Security key. For Eg. "sharedsecret" (Keep this with you, you will need to configure same on VPN Server). |
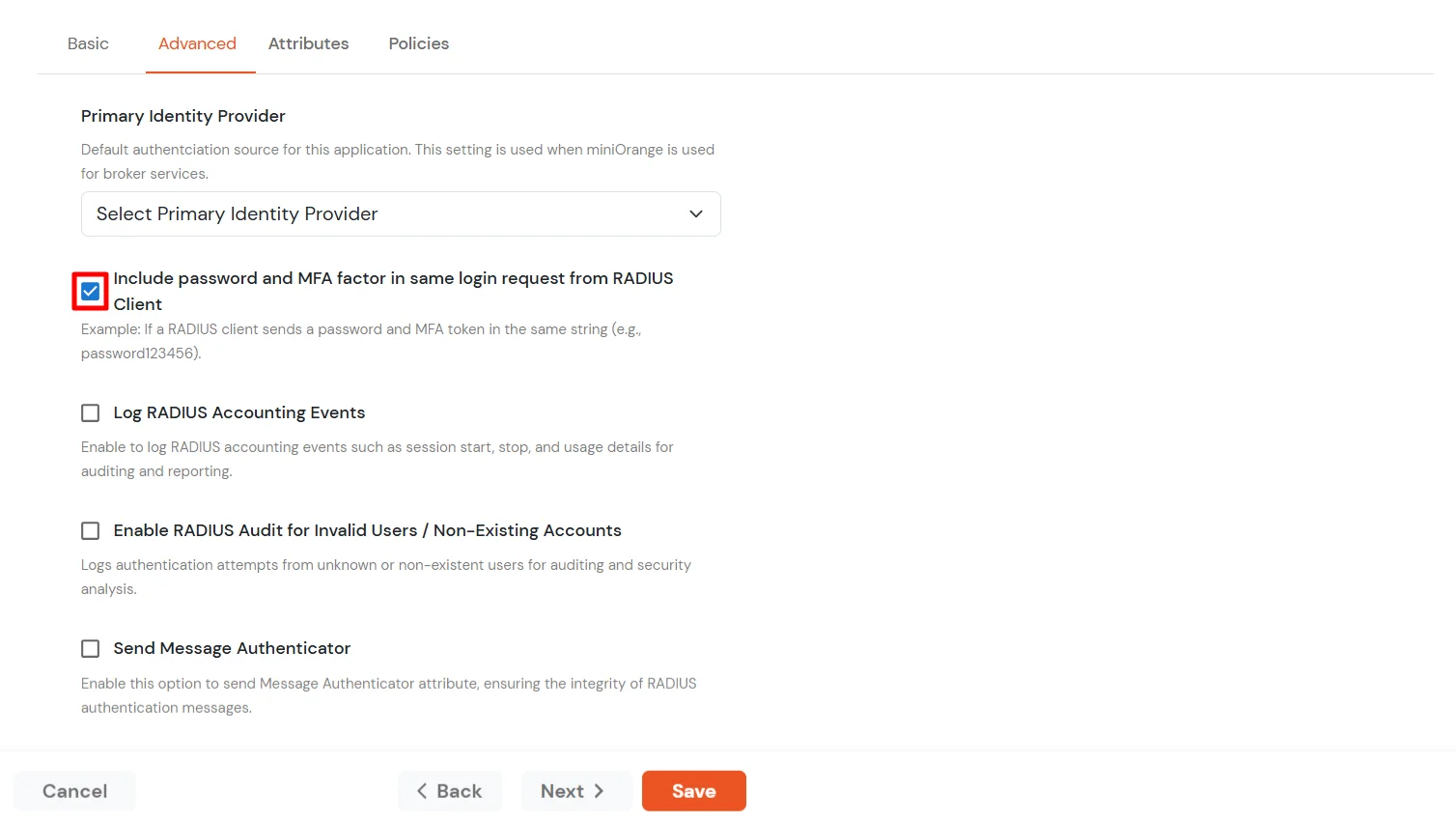
| Include Password & OTP in same Request | Keep this option Disabled |
| Send Groups in Response | Enable this to send user groups as Vendor-Specific Group Attributes. |
3.1: Configure Branding from miniOrange Admin Dashboard.
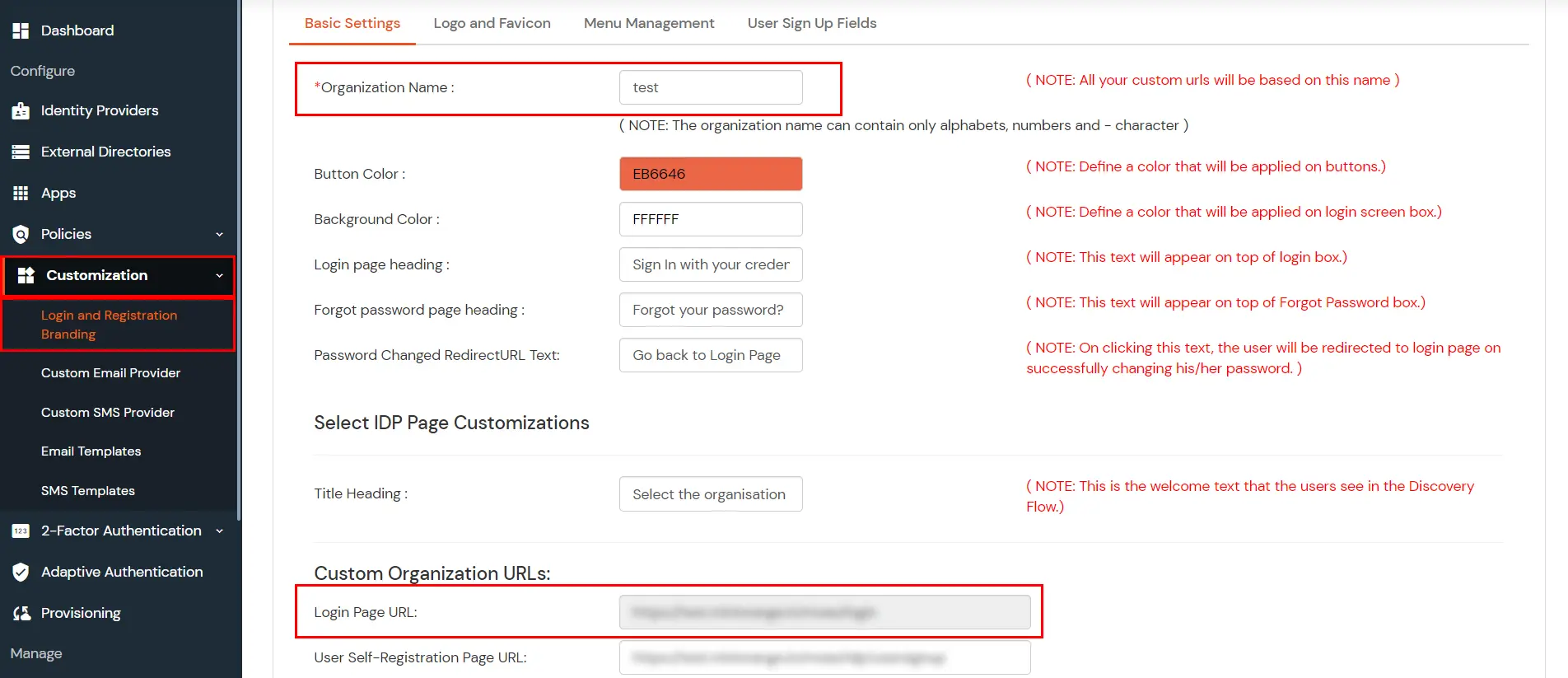
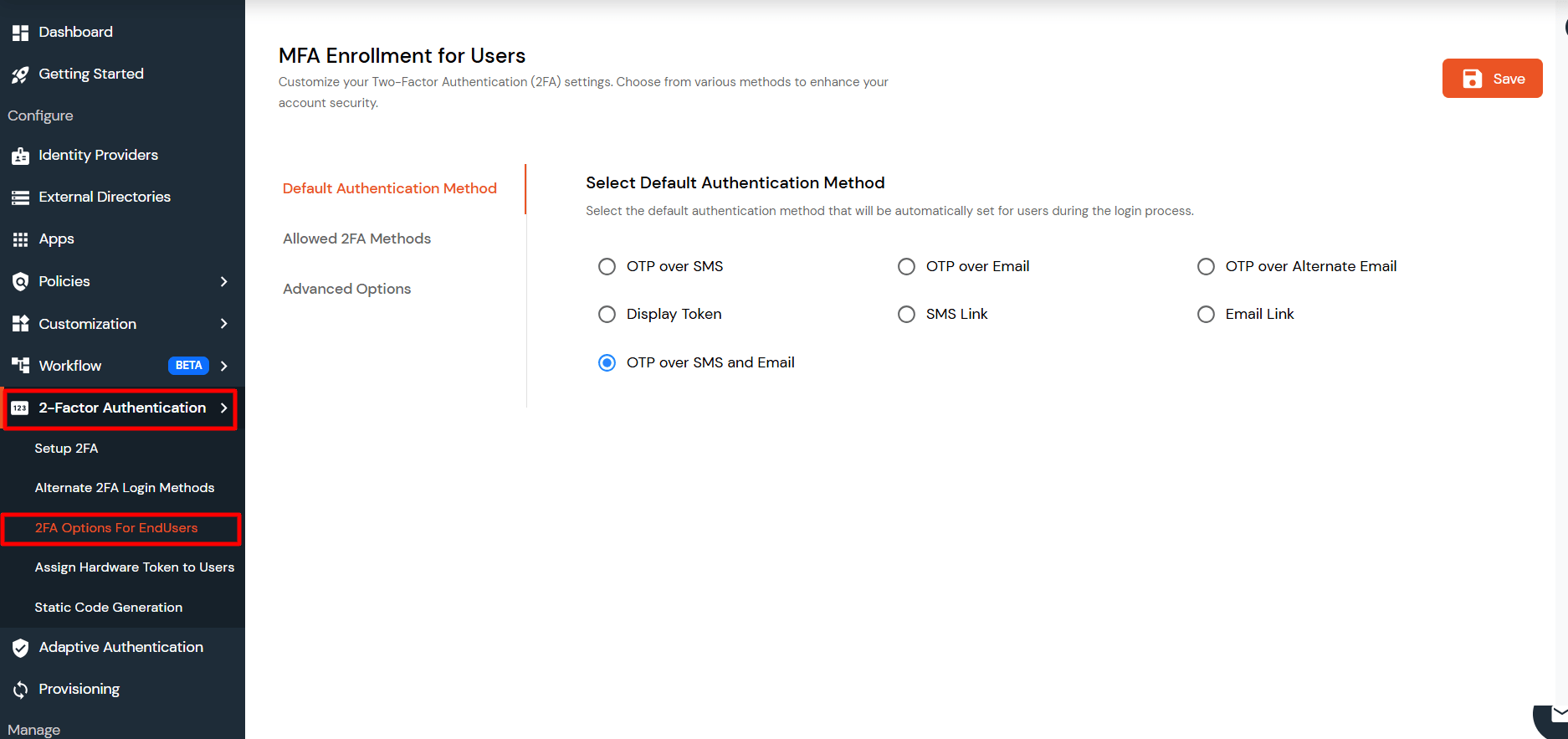
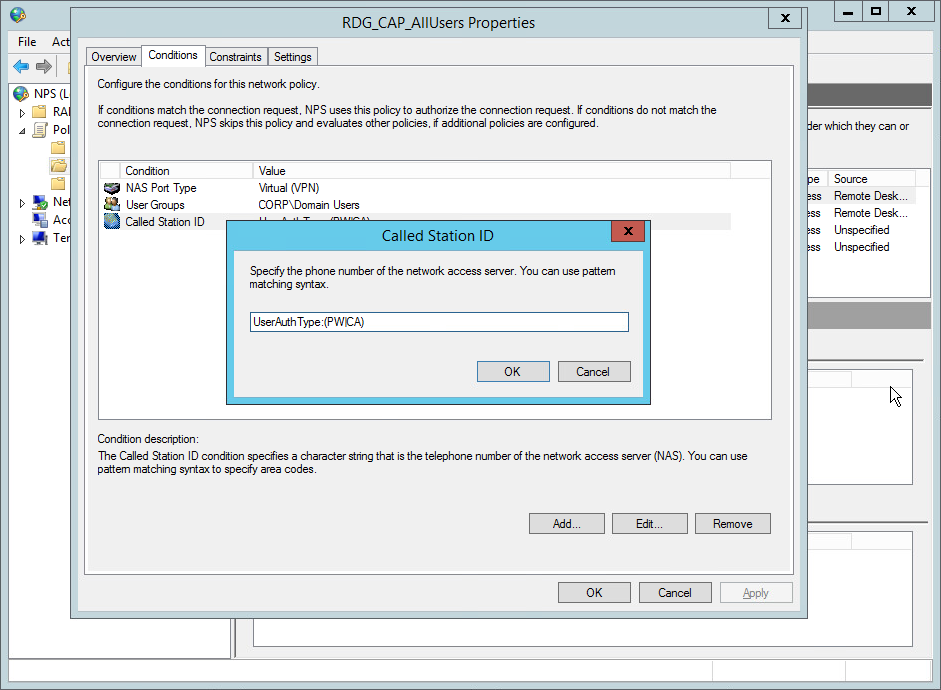
Note: We only support Out of Band methods for MFA over Remote Desktop (RD) Gateway.
Eg. SMS Link, Email Link etc.
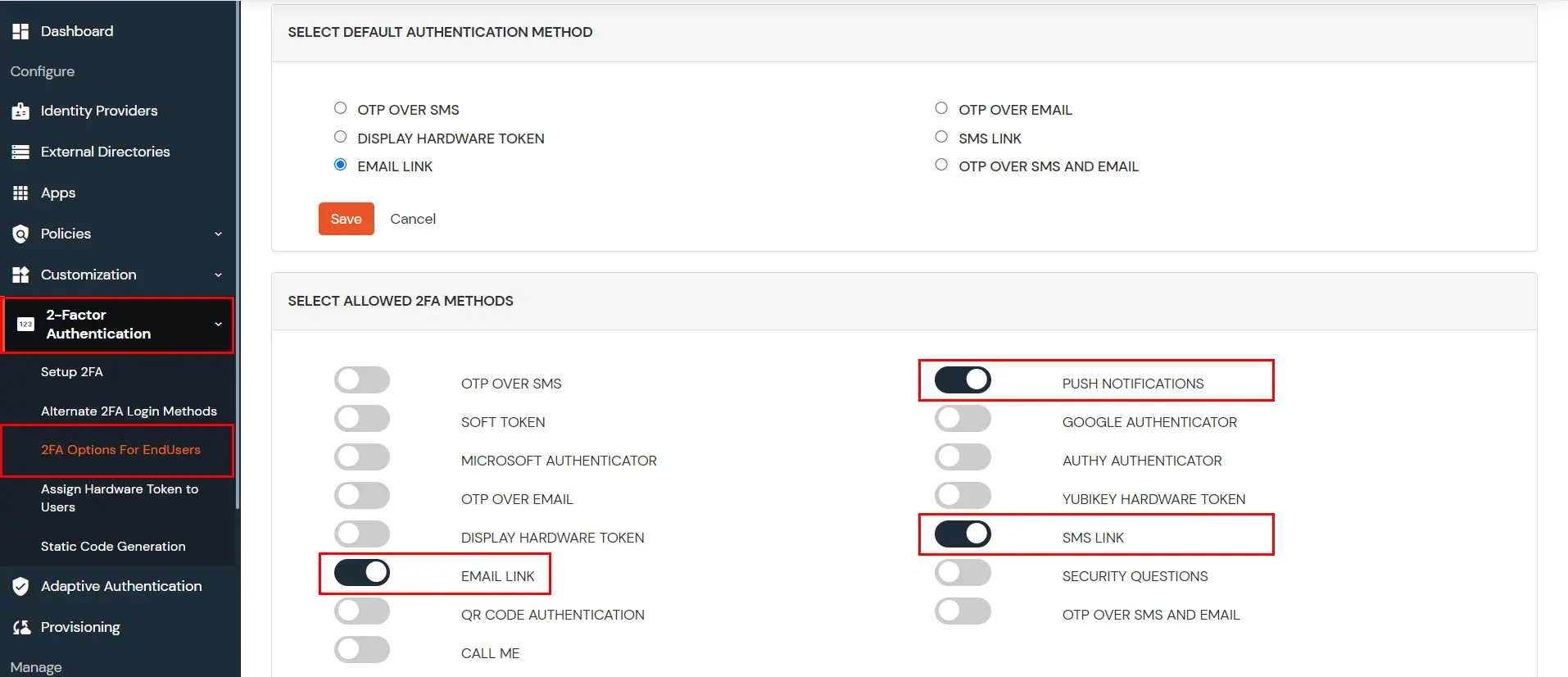
3.2: Configure 2FA for Users of Remote Desktop (RD) Gateway.
This error is usually caused by a time mismatch between the miniOrange server and your mobile device (or a mismatch between your machine time and mobile device time in the case of Offline Authentication for Windows/Linux/Mac).
Security tokens generated by Authenticator apps are "Time-based" (TOTP). They are valid only for a specific 30–60 second window. If the system time on your phone running the Authenticator or your machine(in case of offline authentication) is fast or slow by even 2 minutes, the code will be considered expired by the server/machine.
