Azure DevOps Single Sign-On SSO
Azure DevOps Single Sign-On (SSO) adds security and convenience when your users sign into applications with miniOrange & are synchronized with their Azure DevOps account to sign into their accounts using those Azure DevOps credentials. The problem arises when users forget their password so they try the hit and test method for logging into their Azure DevOps account. Another irritable pattern is to enter the credentials every time when the users try to log in.
This is where Single Sign-On (SSO) comes into play. SSO will help users to seamlessly login to their account automatically using their AD credentials which means they do not have to enter the credentials again once they have signed in to their machine.
Seamless Azure DevOps SSO solution provided by miniOrange
Azure DevOps SSO integration by miniOrange provides secure access and full control over multiple Web and SaaS applications to enterprise users and clients. Azure DevOps SSO let users to Single Sign-On into Azure DevOps account with one set of login credentials, eliminating user-managed passwords and the risk of phishing. Single Sign-On for Azure DevOps sets up leverages the existing on-premise Active Directory infrastructure and provides seamless integration without the need to manage multiple on-premise and cloud identities.
In addition to SSO for Azure DevOps, users will have one-click access to all their apps and will not be locked out by mistake. Users requirement to secure Azure DevOps also helped us to introduce enhanced Azure DevOps Two-Factor Authentication solution. Azure DevOps 2FA security solution makes it easier for users and organizations to safeguard and prevent themselves from security breaches.
miniOrange and Azure DevOps Single Sign-On (SSO) integration supports the following features:
- SP Initiated Single Sign-On (SSO)
- IdP Initiated Single Sign-On (SSO)
Connect with External Source of Users
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.
Prerequisites
1. Sync On-Premise Active Directory with Microsoft Entra ID
NOTE: If you want to use your On-Premise Active Directory as a user store to Single Sign-On into Azure DevOps then follow the below steps to sync your AD and Microsoft Entra ID.
- Download the Microsoft Entra ID Connect
- Run the Microsoft Entra ID installer on your domain machine and follow the setup.
2. Verify your UPN Domain in Azure Portal
- In the Azure portal navigate to Microsoft Entra ID >> Custom domain names and click on Add custom domain.
- Enter the full domain name in the right pane that pops up and click on Add domain.
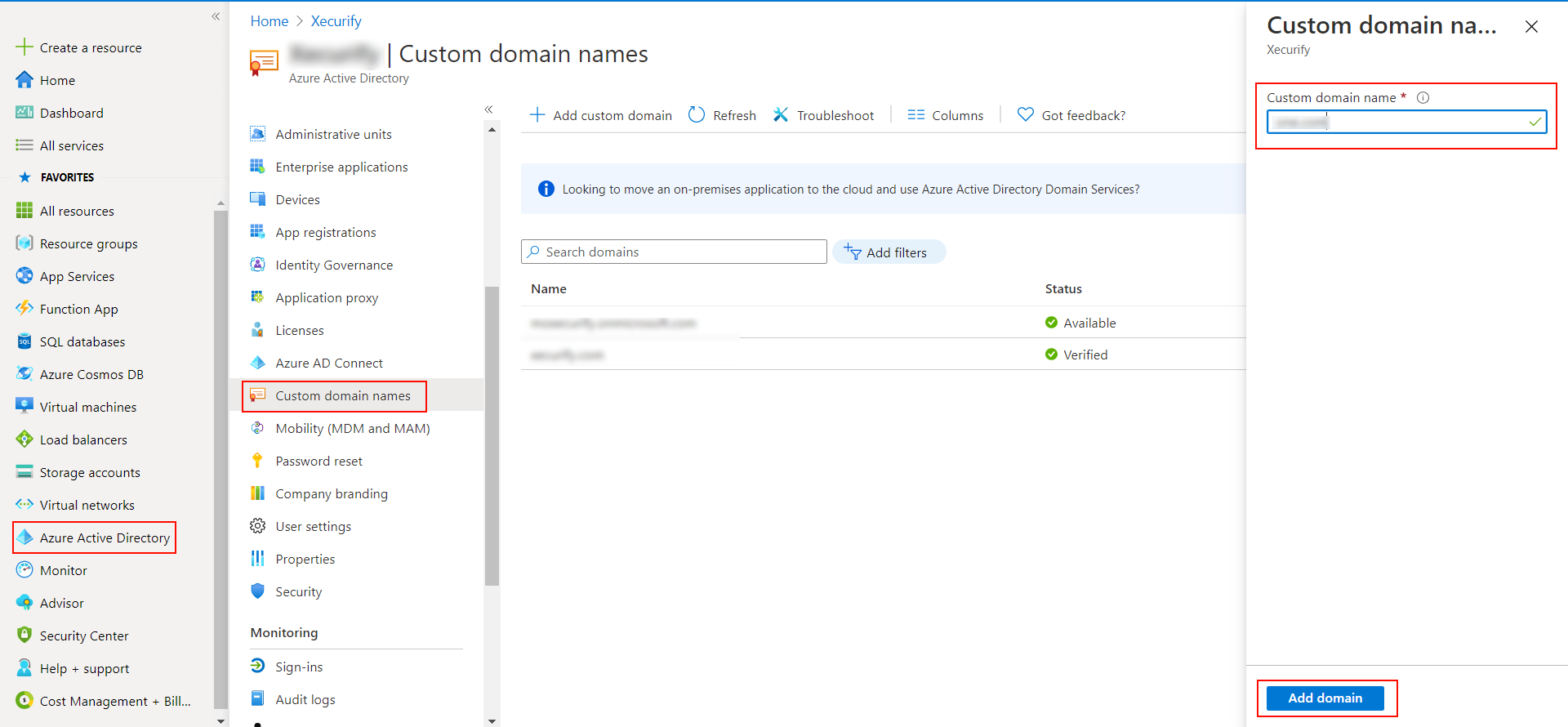
- A new window will open up with TXT/MX records for the domain. You will have to add the resented entry in your domain name registrar.
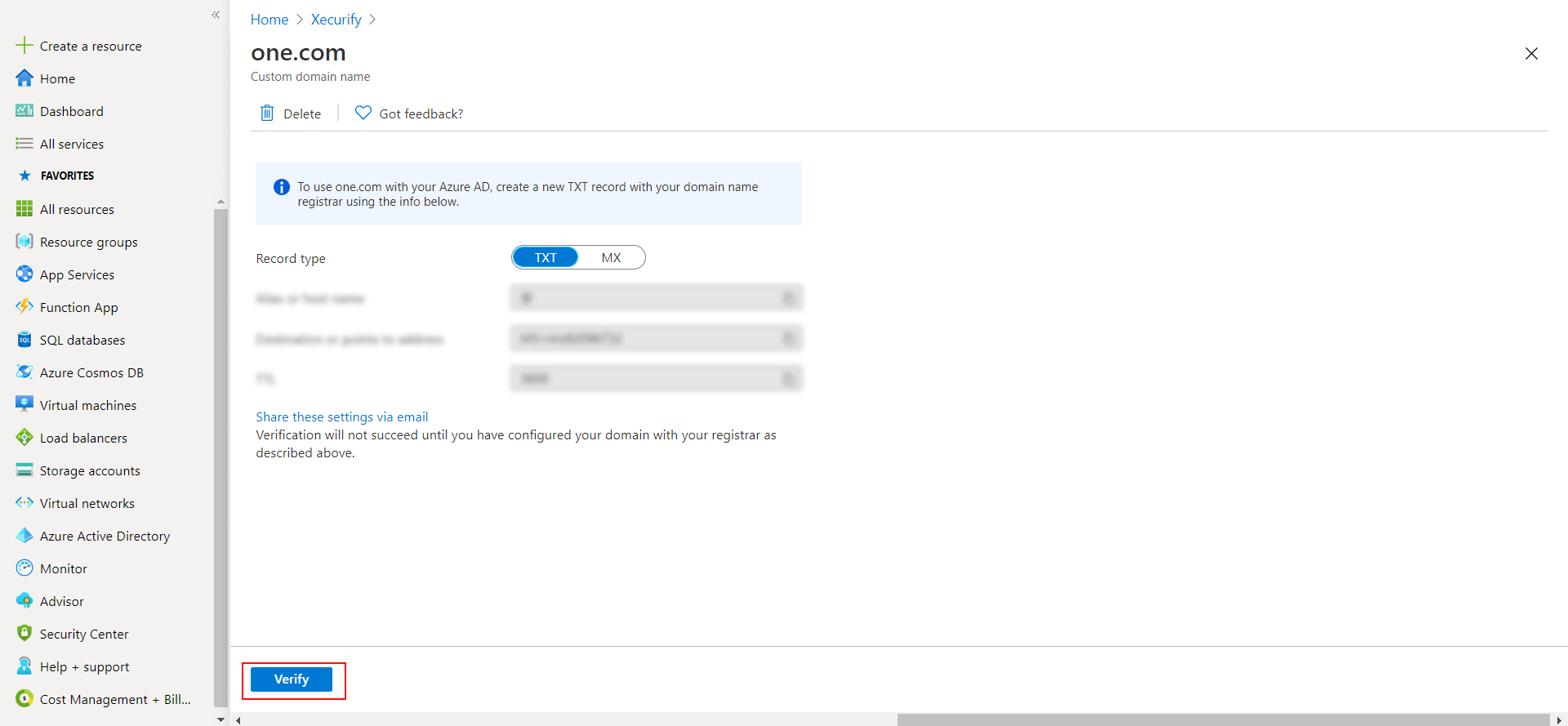
- Click on verify once you have added the entry
Please make sure your organisation branding is already set under Customization >> Login and Registration Branding in the left menu of the dashboard.
Follow the step-by-step guide given below for Azure DevOps Single Sign-On (SSO)
1. Configure Azure DevOps in miniOrange
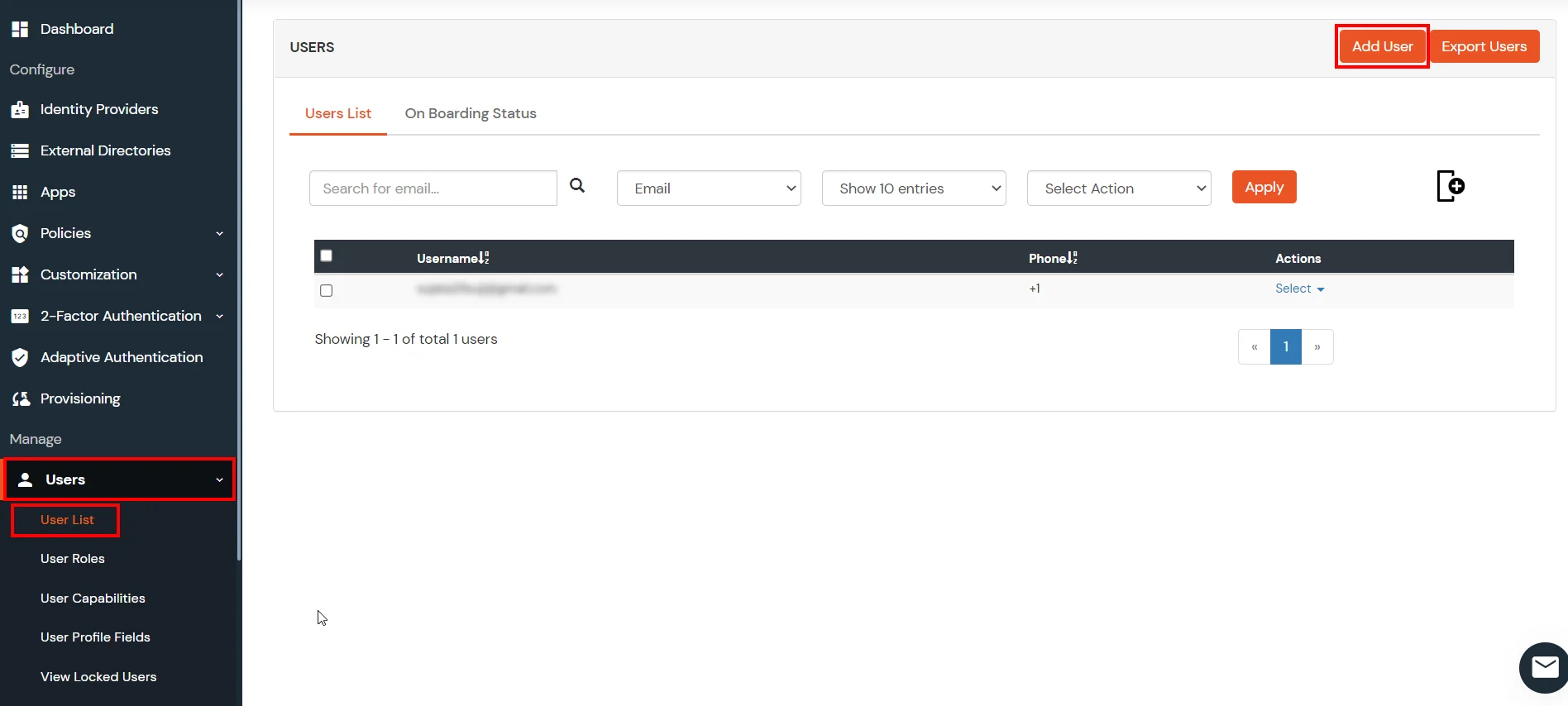
- Login into miniOrange Admin Console.
- Go to Apps and click on Add Application button.

- In Choose Application Type click on Create App button in SAML/WS-FED application type.
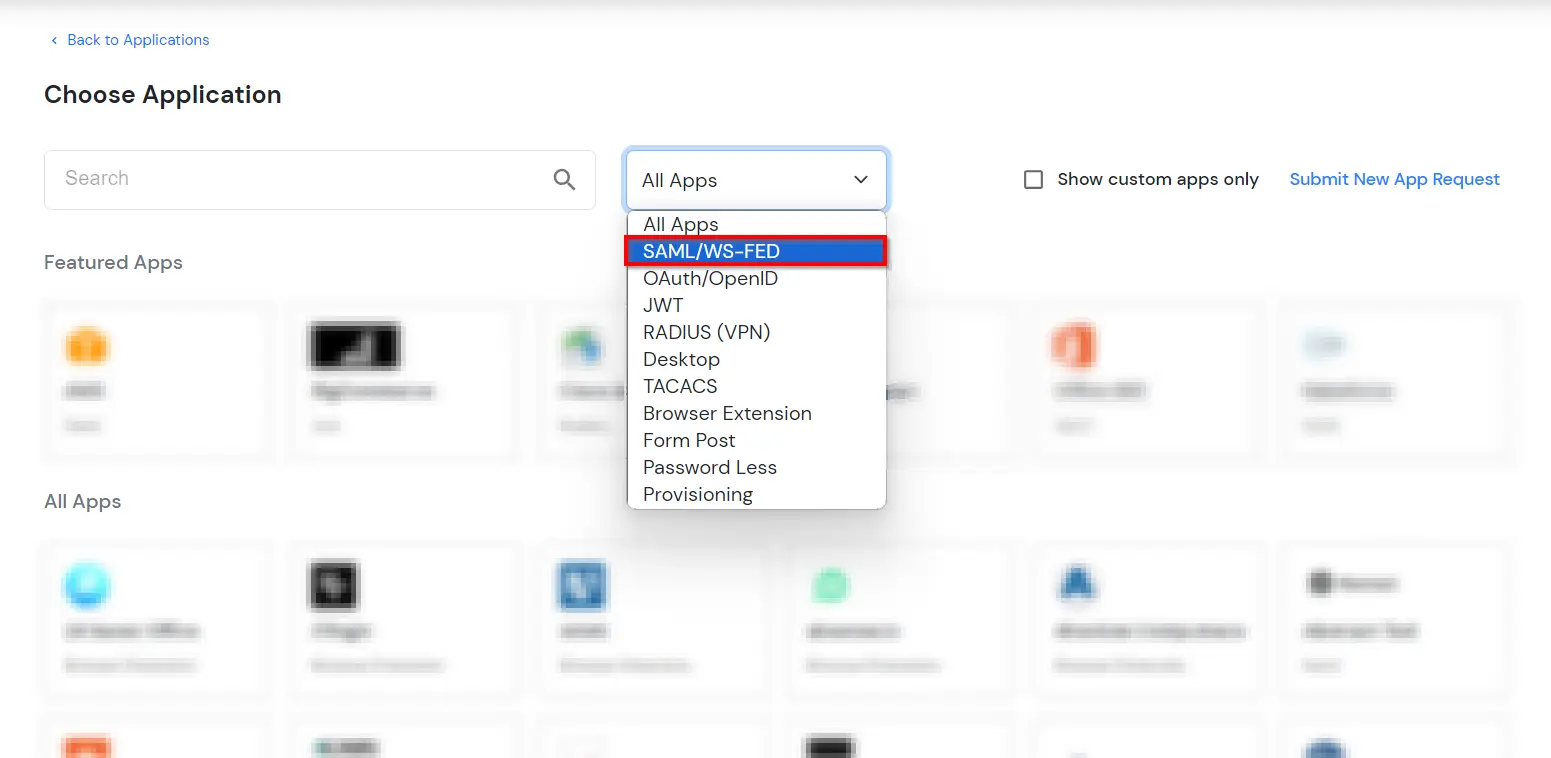
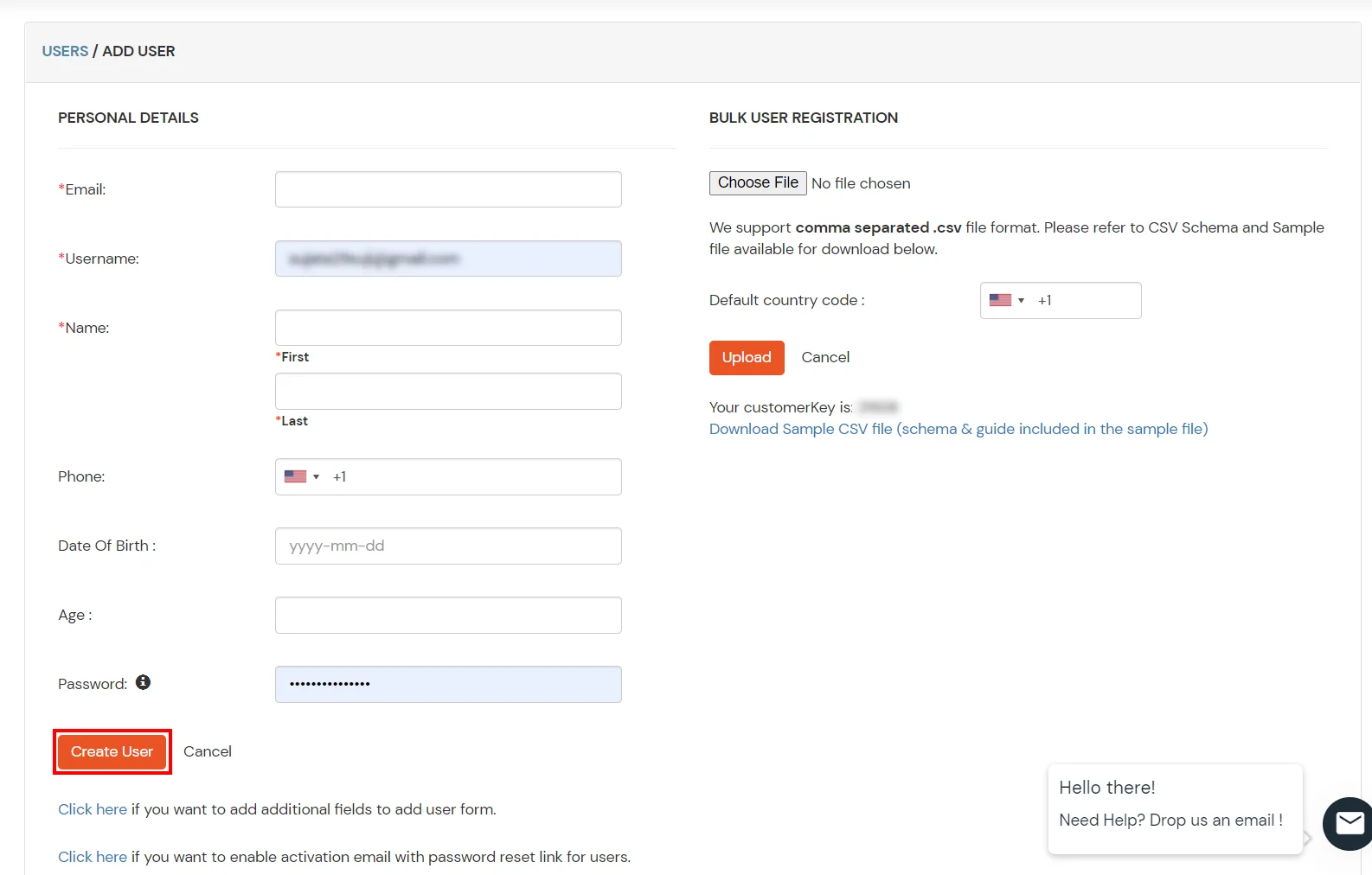
- In the next step, search for Office 365. Click on Office 365 app.

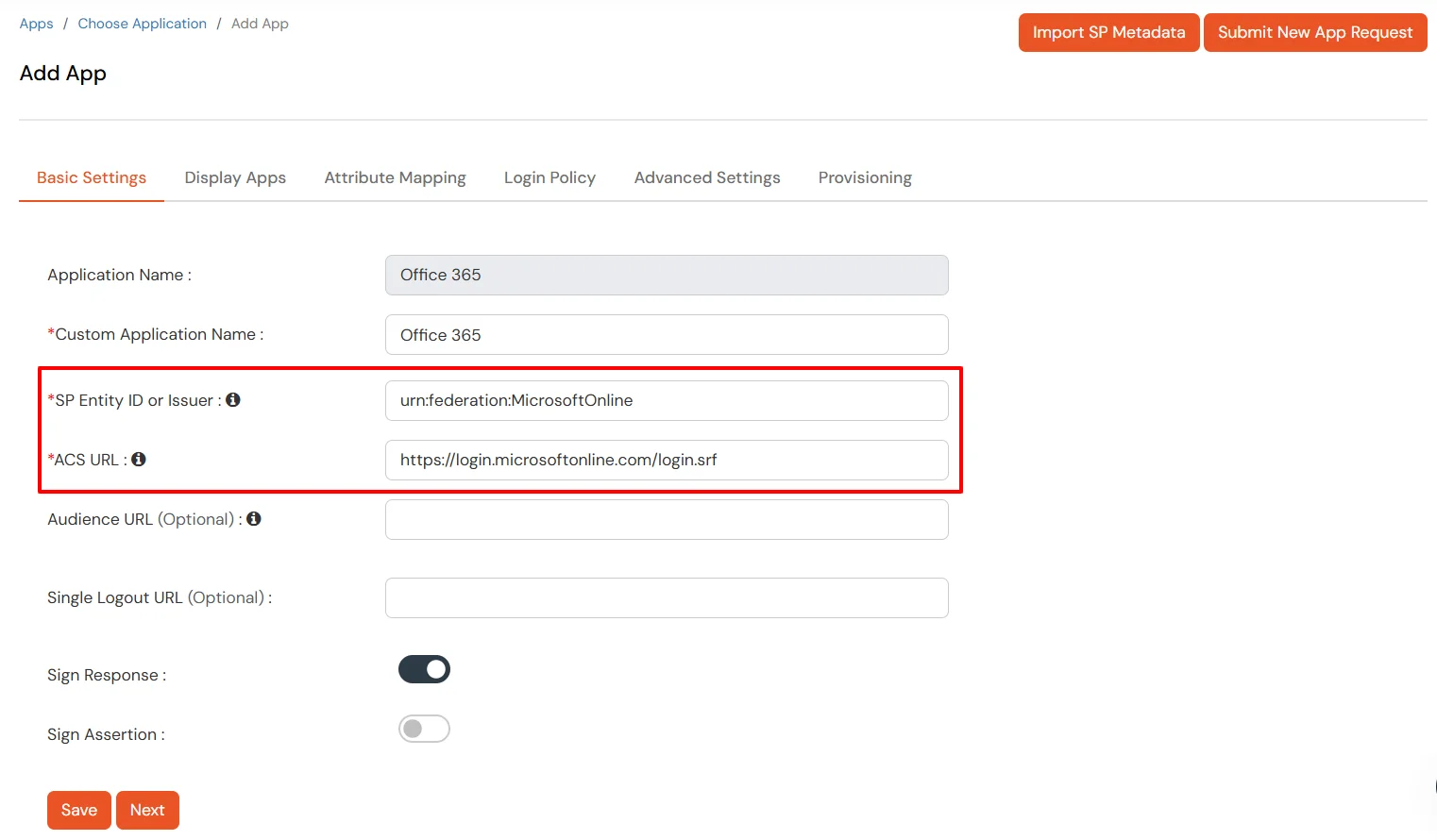
- Make sure the SP Entity ID or Issuer is:
urn:federation:MicrosoftOnline
- Make sure the ACS URL is:
https://login.microsoftonline.com/login.srf
- Click on Next.
-
Configure Name ID based on the User Store you are using:
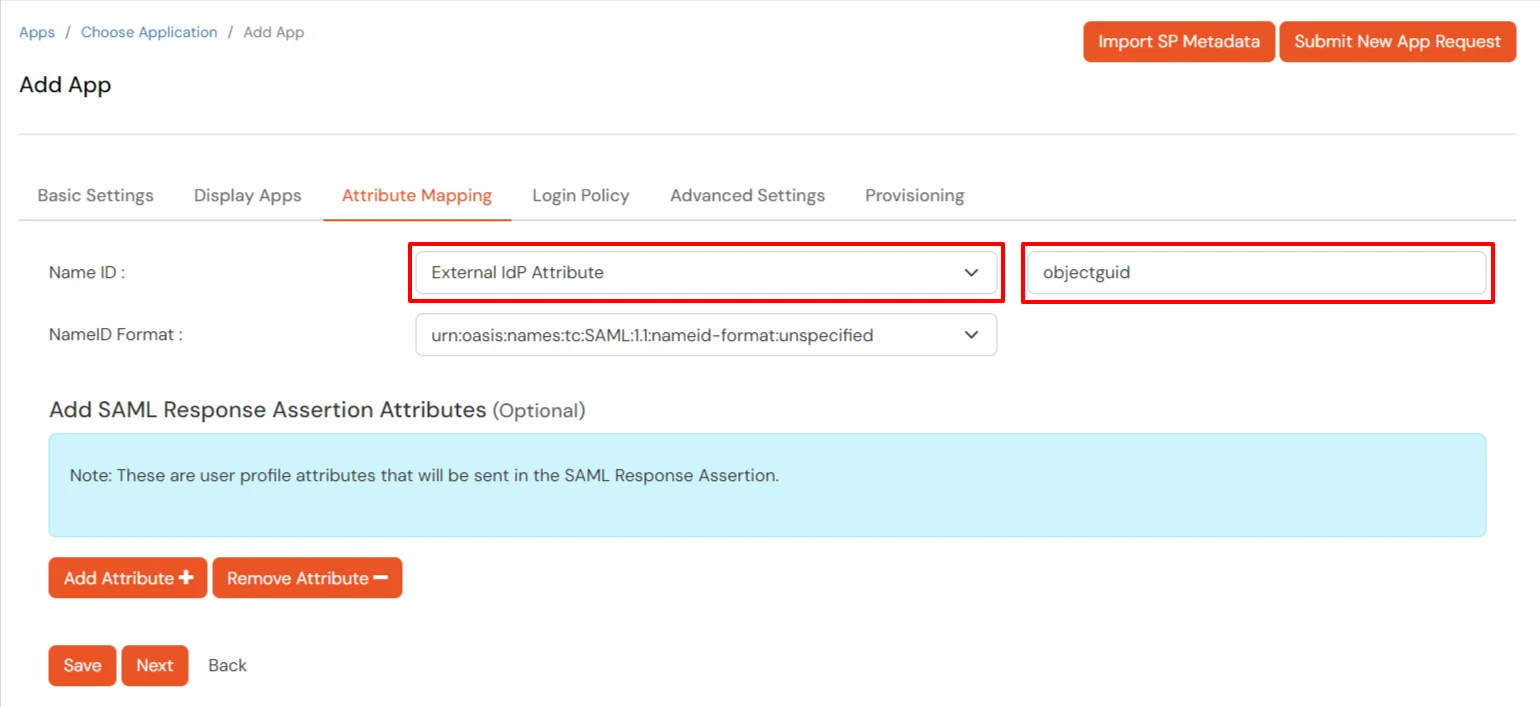
- Using Active Directory / miniOrange brokering service: Select External IDP Attribute from the dropdown and add objectguid in the text-box that appears.
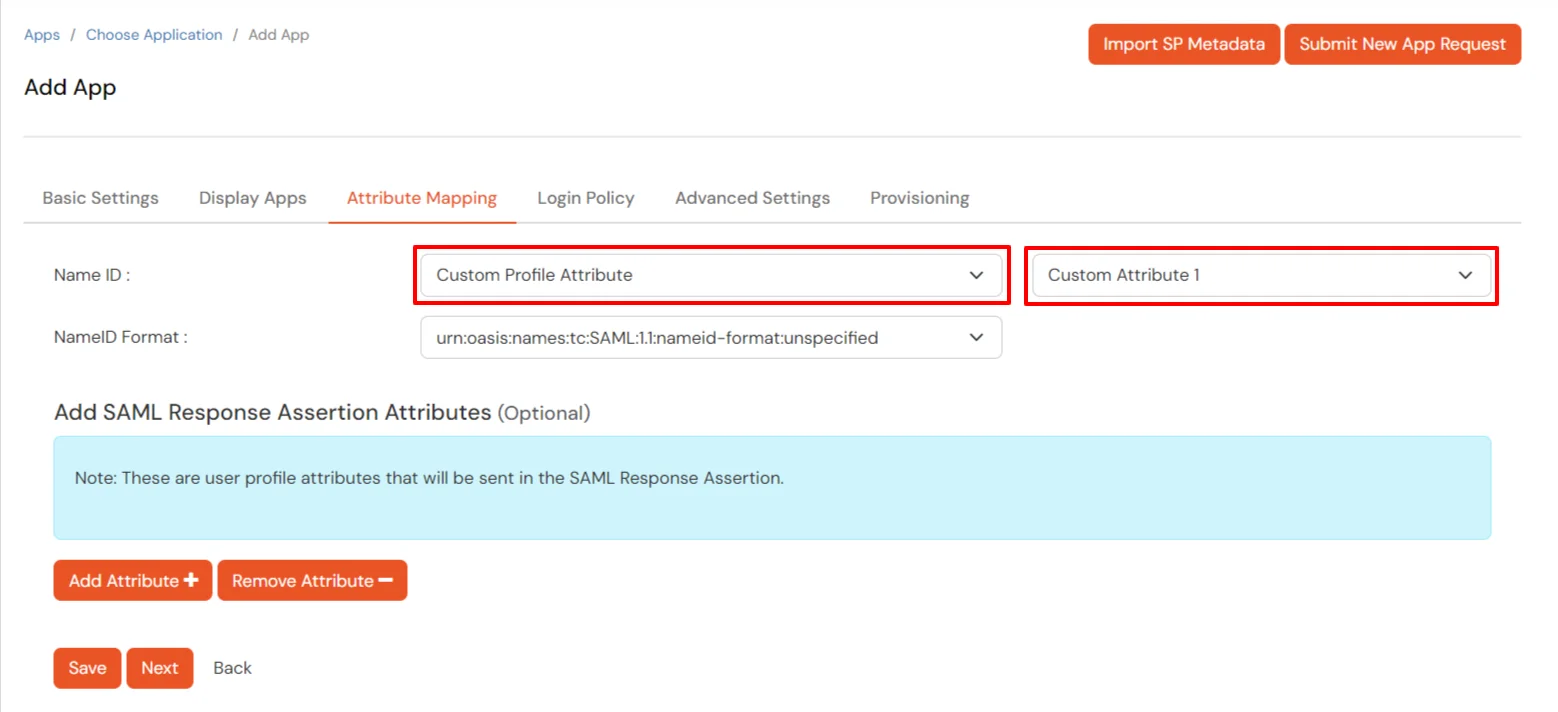
- Using miniOrange as a User Store: Select Custom Profile Attribute and select a Custom Attribute from the drop-down.
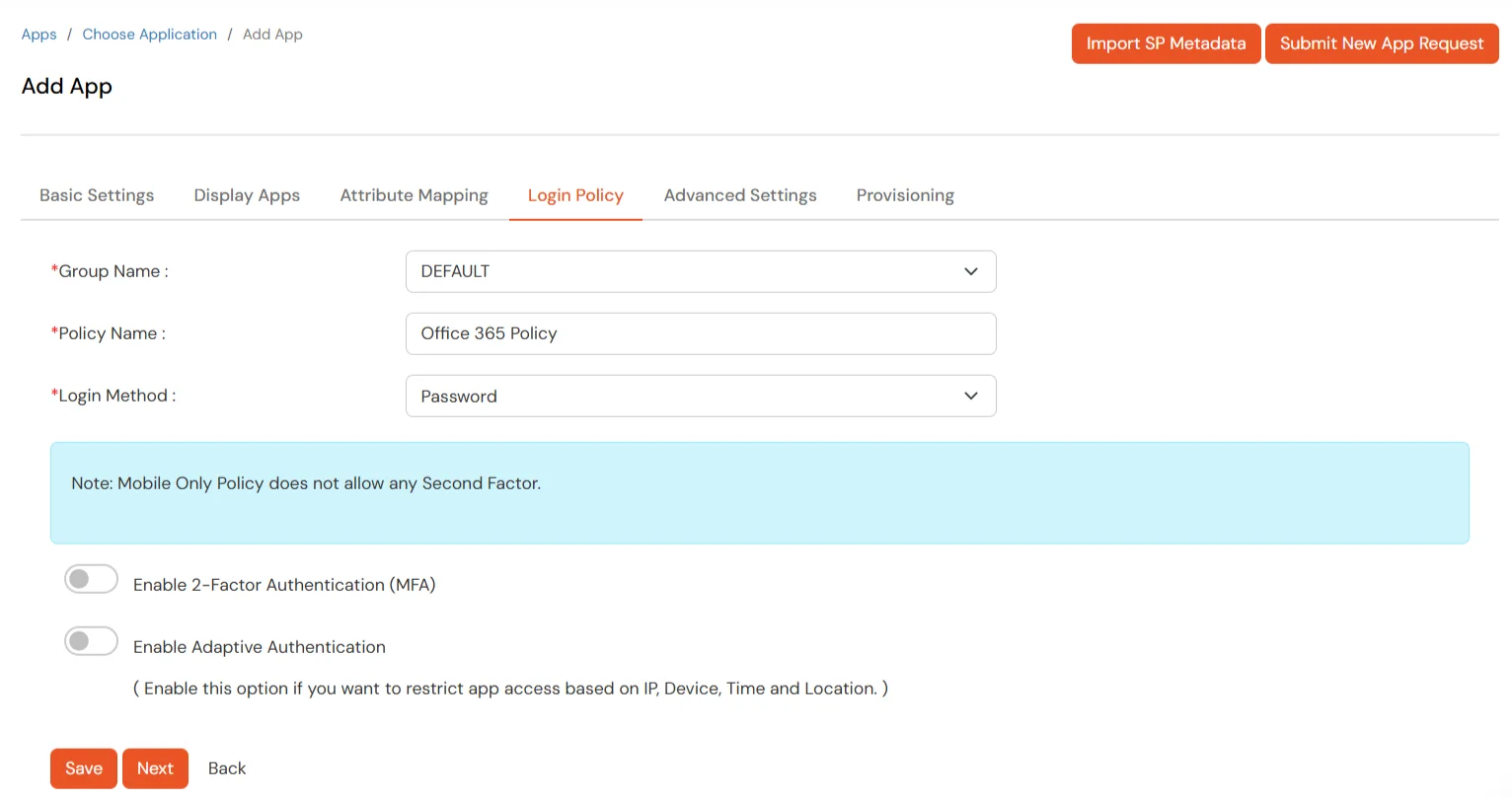
- Set the login policy. You can choose to enable 2FA for login or have users login using a standard username-password.
- Click on Save to configure Office 365.
2. Configure Microsoft Graph Services
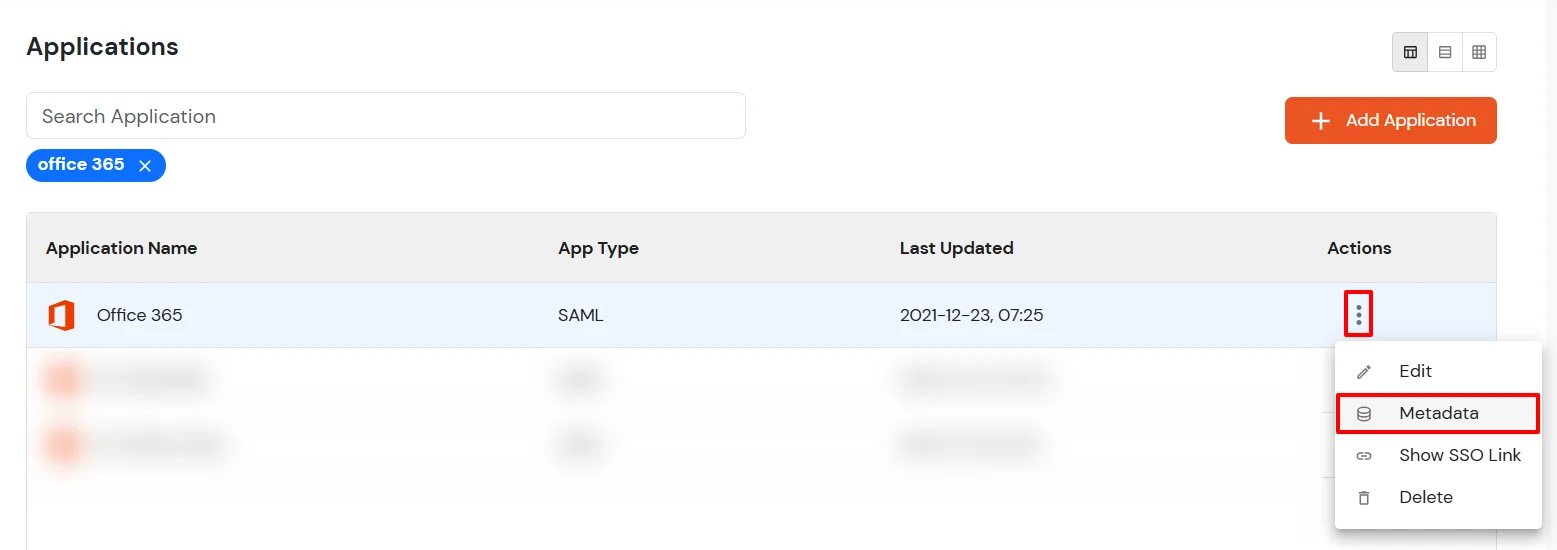
- Click on the icon ' ' and choose Metadata.
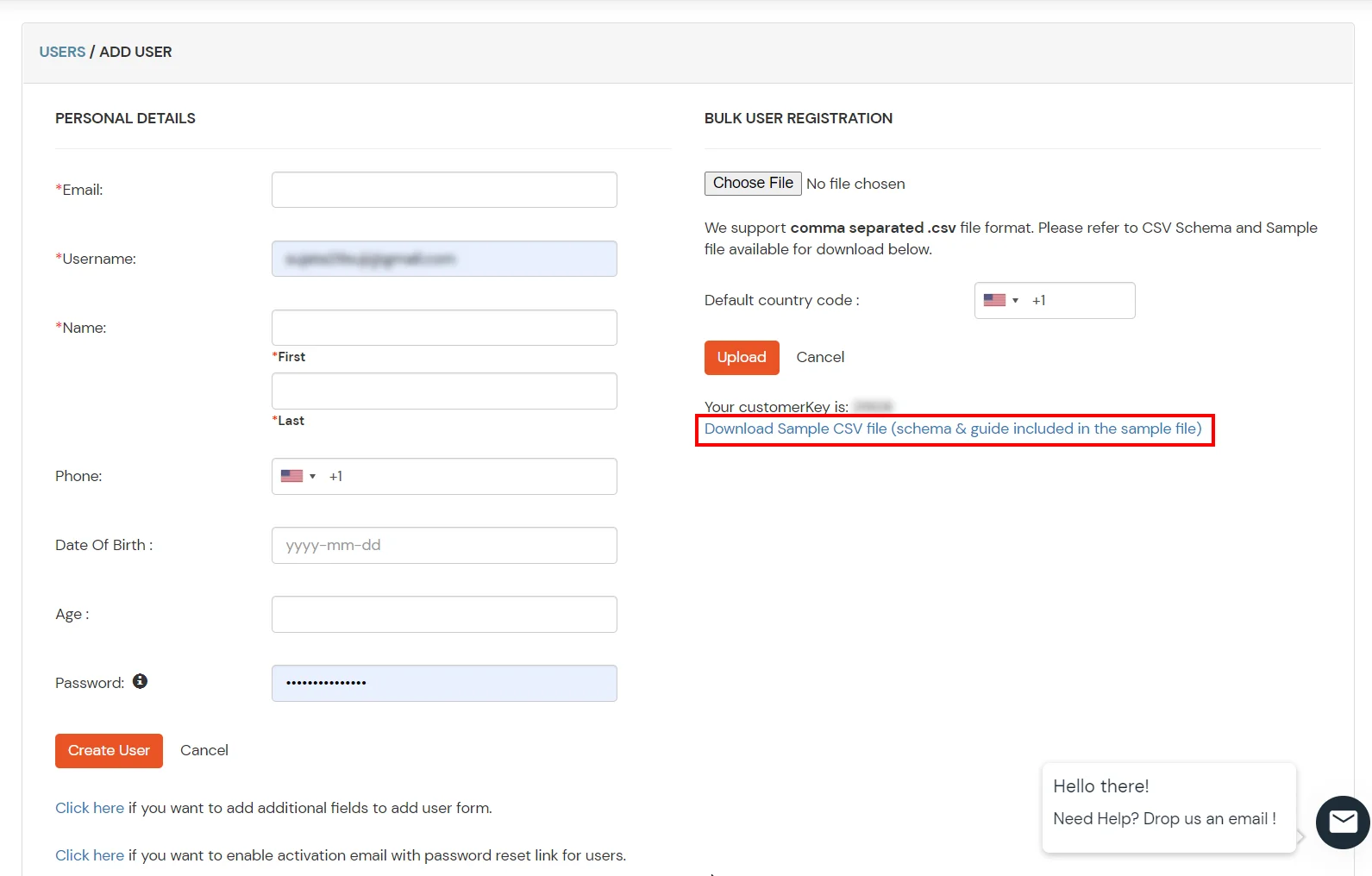
- Click on the Download Federate Domain Script button under "INFORMATION REQUIRED TO AUTHENTICATE VIA EXTERNAL IDPS"
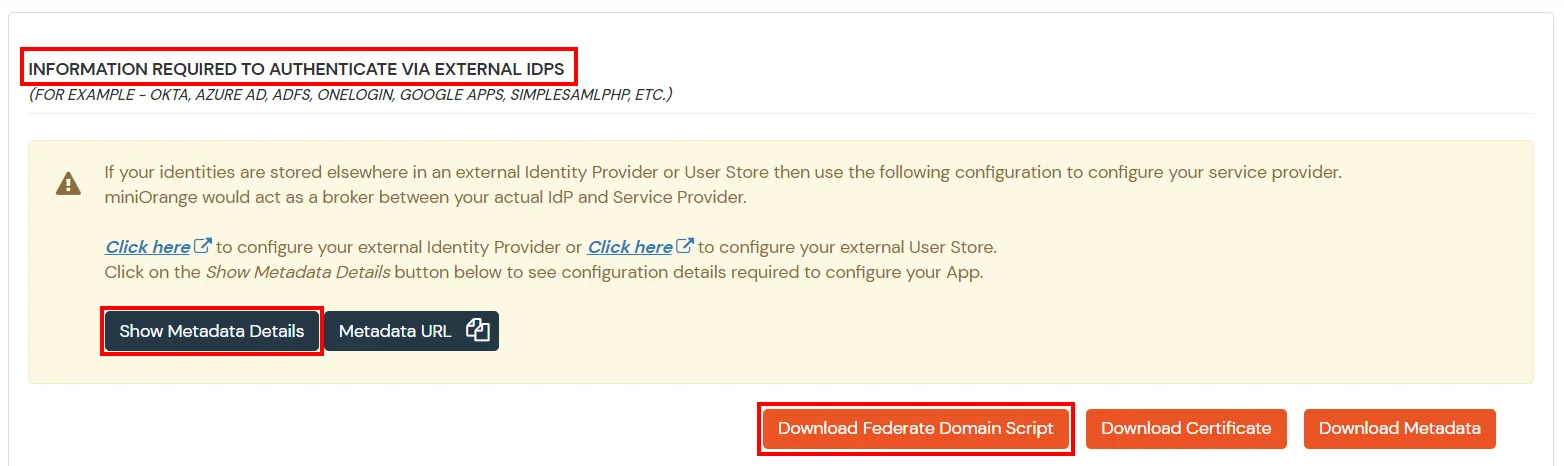
- Enter the domain name that you want to federate and click on Download.
Note: You cannot federate your default "onmicrosoft.com" domain. To federate your Azure DevOps tenant, you must add a custom domain to Azure DevOps.
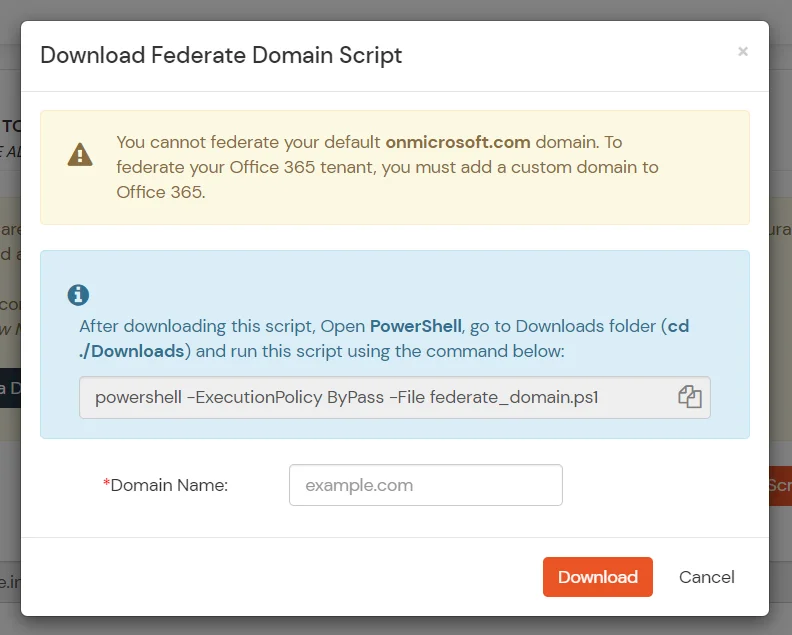
- After downloading the script, Open PowerShell run the federate_domain script using:
cd ./Downloads
powershell -ExecutionPolicy ByPass -File federate_domain.ps1
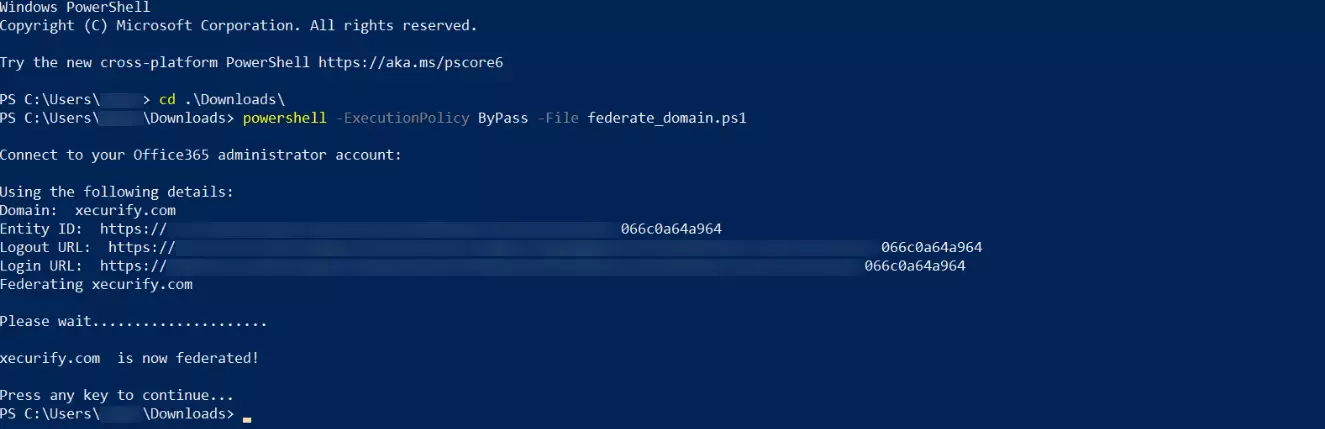
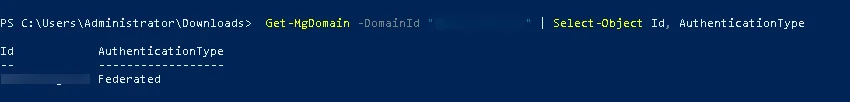
- Your domain is now federated. Use the commands below to check your federation settings:
Get-MgDomain -DomainId "<domain>" | Select-Object Id, AuthenticationType
4. Test SSO Configuration
1. Using SP initiated login :-
- Go to Azure DevOps - Azure DevOps Login and click on sign-in
- You will be redirected to Microsoft Graph portal. Here you have to enter the UPN of the user.(It should contain the domain that is federated with miniOrange)
- Now you will be redirected to miniOrange IdP Sign On Page.
- Enter your login credential and click on Login. You will be automatically logged in to your Azure DevOps account.

2. Using IdP initiated login :-
- Login to your miniOrange Self Service Console as an End User and click on the Azure DevOps icon on your Dashboard.
- Once you click on Azure DevOps you don't need to enter credentials again you will be redirected to Azure DevOps account.

5. Configure Your User Directory (Optional)
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, Microsoft Entra ID, OpenLDAP, Google, AWS Cognito etc), Identity Providers (like Okta, Shibboleth, Ping, OneLogin, KeyCloak), Databases (like MySQL, Maria DB, PostgreSQL) and many more. You can configure your existing directory/user store or add users in miniOrange.
- Click on External Directories >> Add Directory in the left menu of the dashboard.
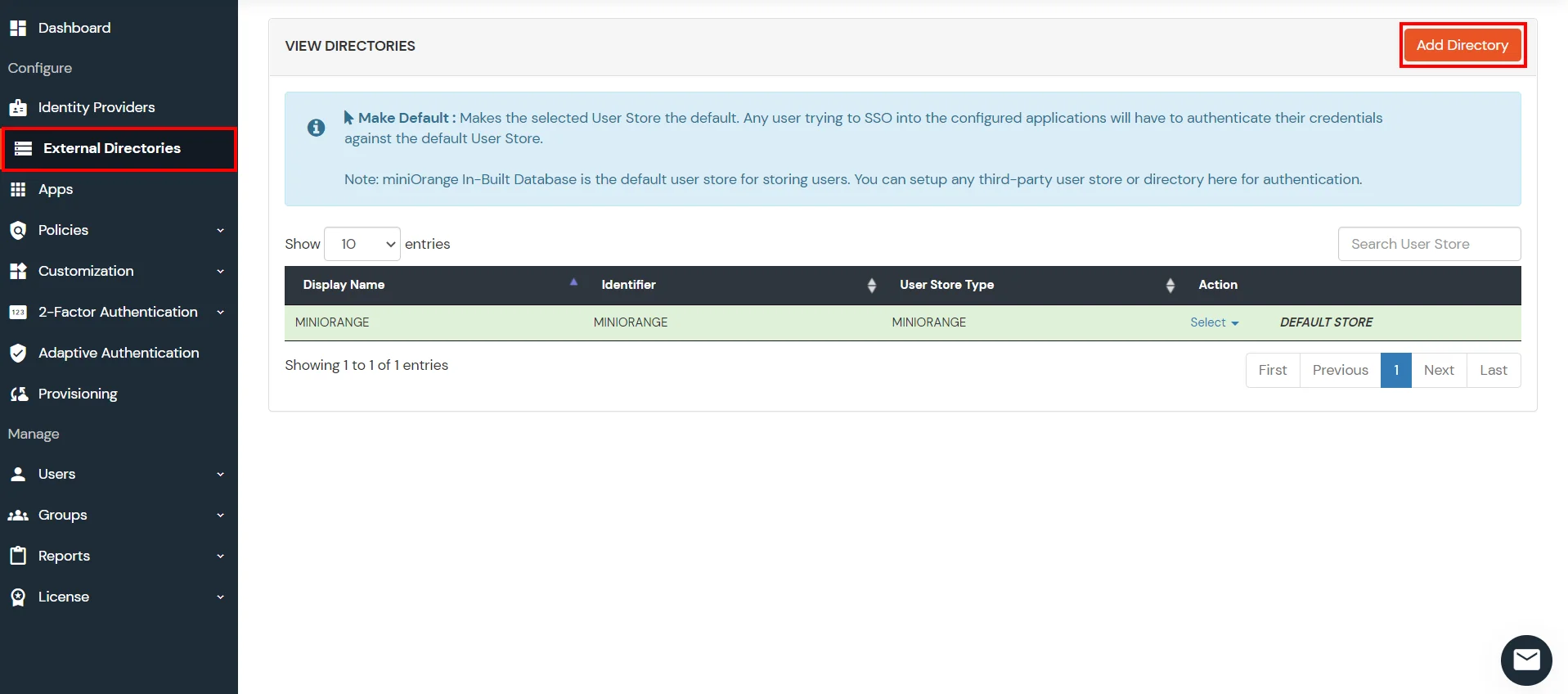
- Select Directory type as AD/LDAP.
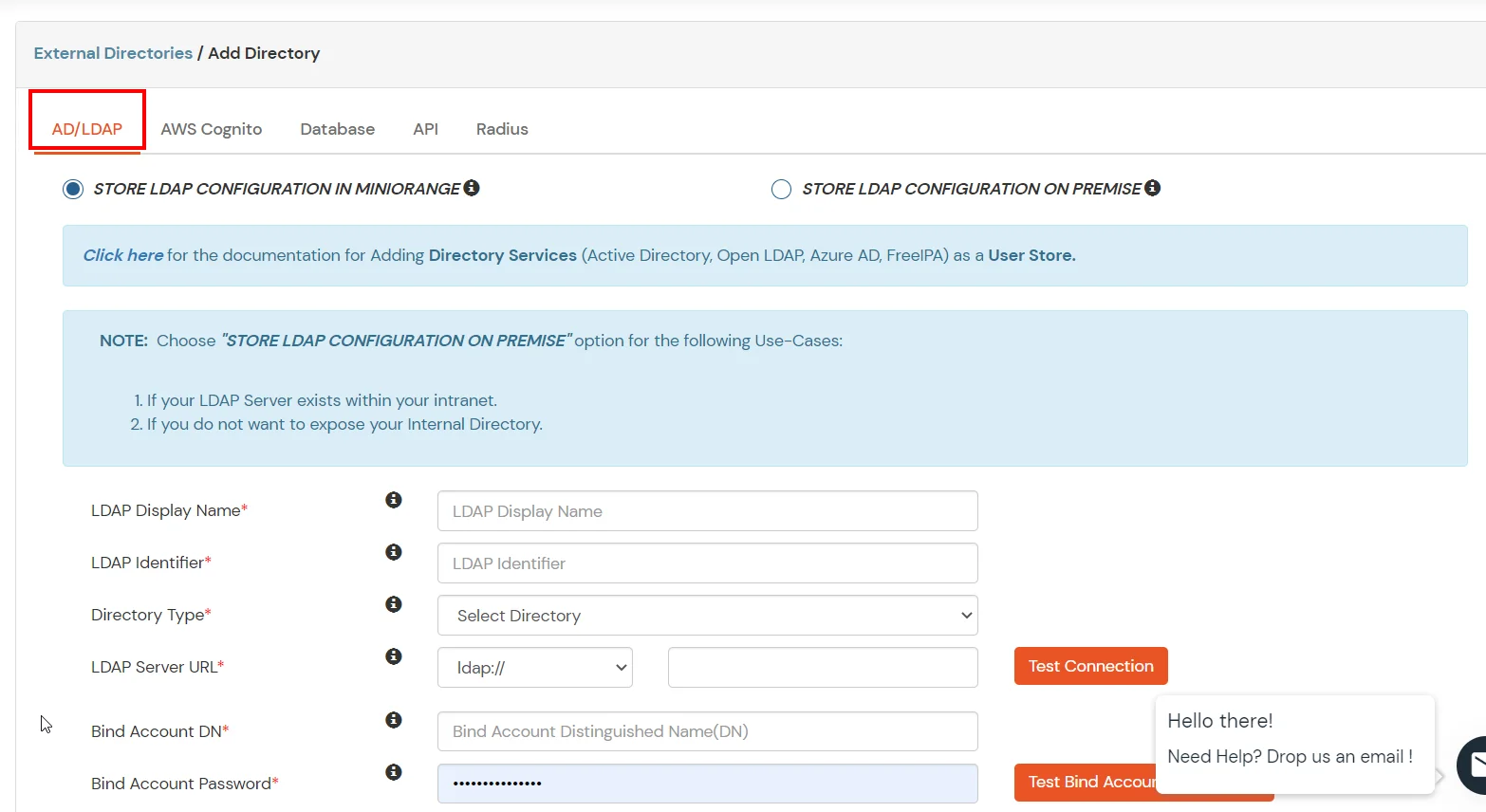
- STORE LDAP CONFIGURATION IN MINIORANGE: Choose this option if you want to keep your configuration in miniOrange. If active directory is behind a firewall, you will need to open the firewall to allow incoming requests to your AD.
- STORE LDAP CONFIGURATION ON PREMISE: Choose this option if you want to keep your configuration in your premise and only allow access to AD inside premises. You will have to download and install miniOrange gateway in your premise.
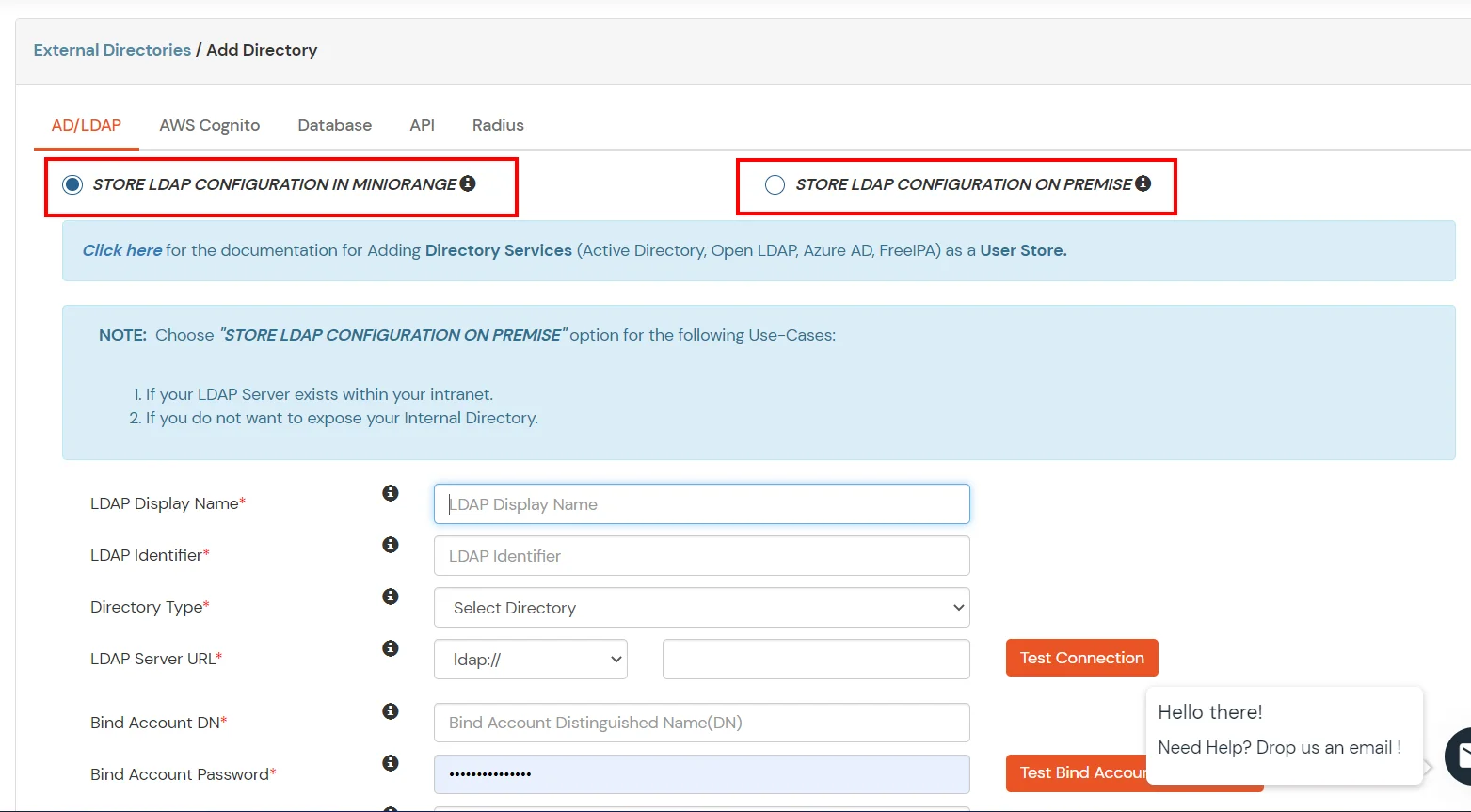
- Enter LDAP Display Name and LDAP Identifier name.
- Select Directory Type as Active Directory.
- Enter the LDAP Server URL or IP Address against LDAP Server URL field.
- Click on Test Connection button to verify if you have made a successful connection with your LDAP server.
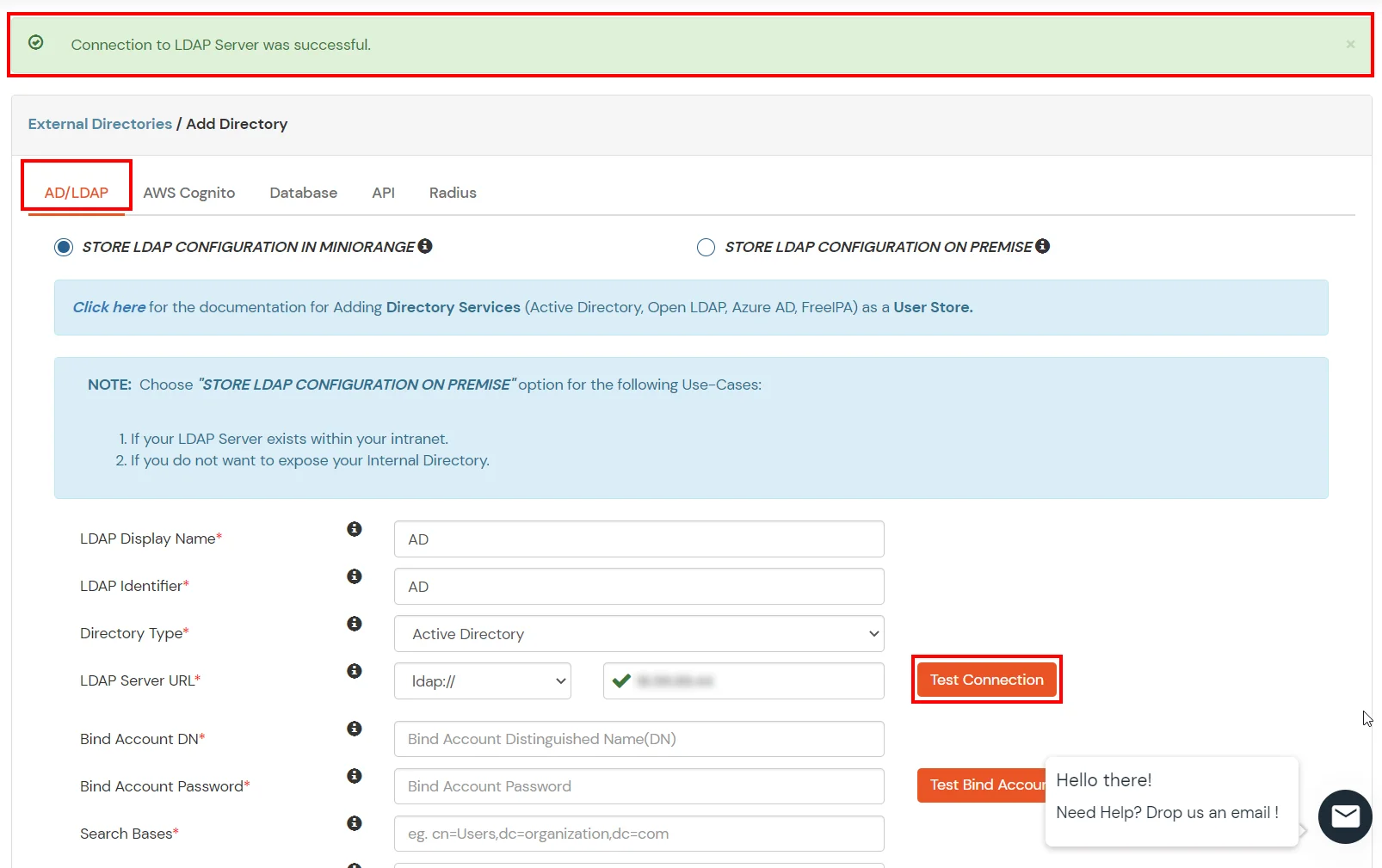
- In Active Directory, go to the properties of user containers/OU's and search for Distinguished Name attribute.
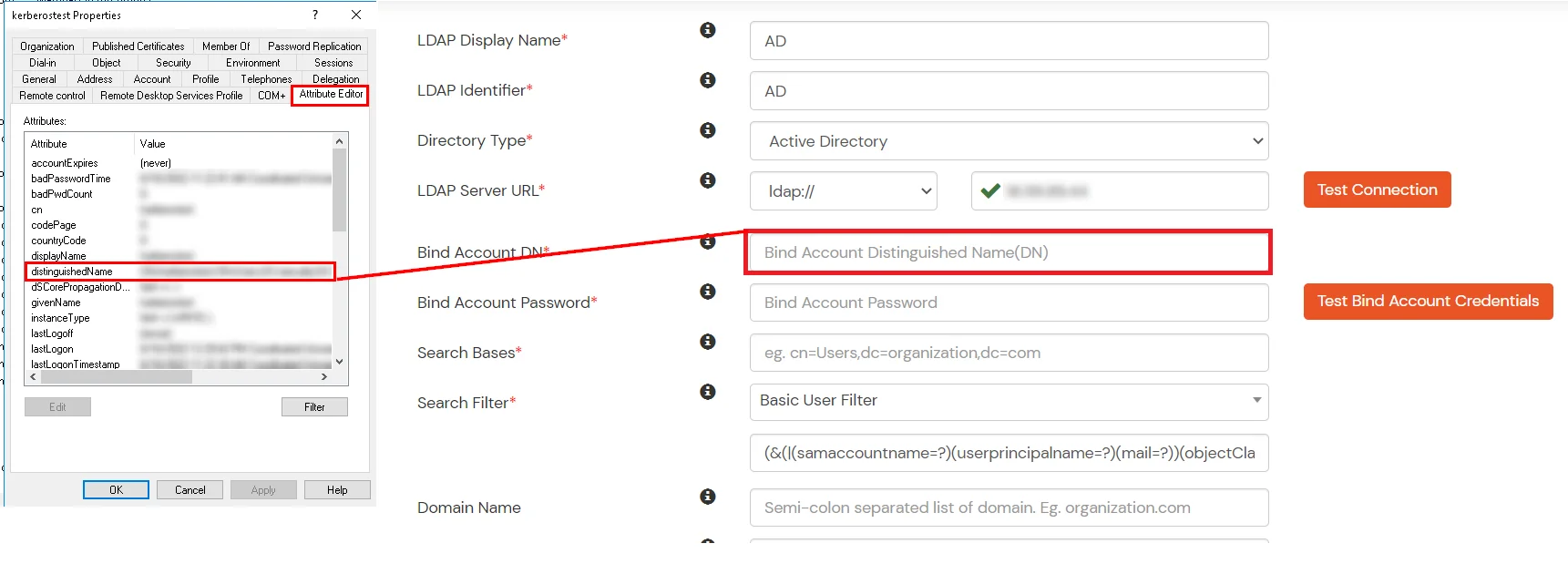
- Enter the valid Bind account Password.
- Click on Test Bind Account Credentials button to verify your LDAP Bind credentials for LDAP connection.
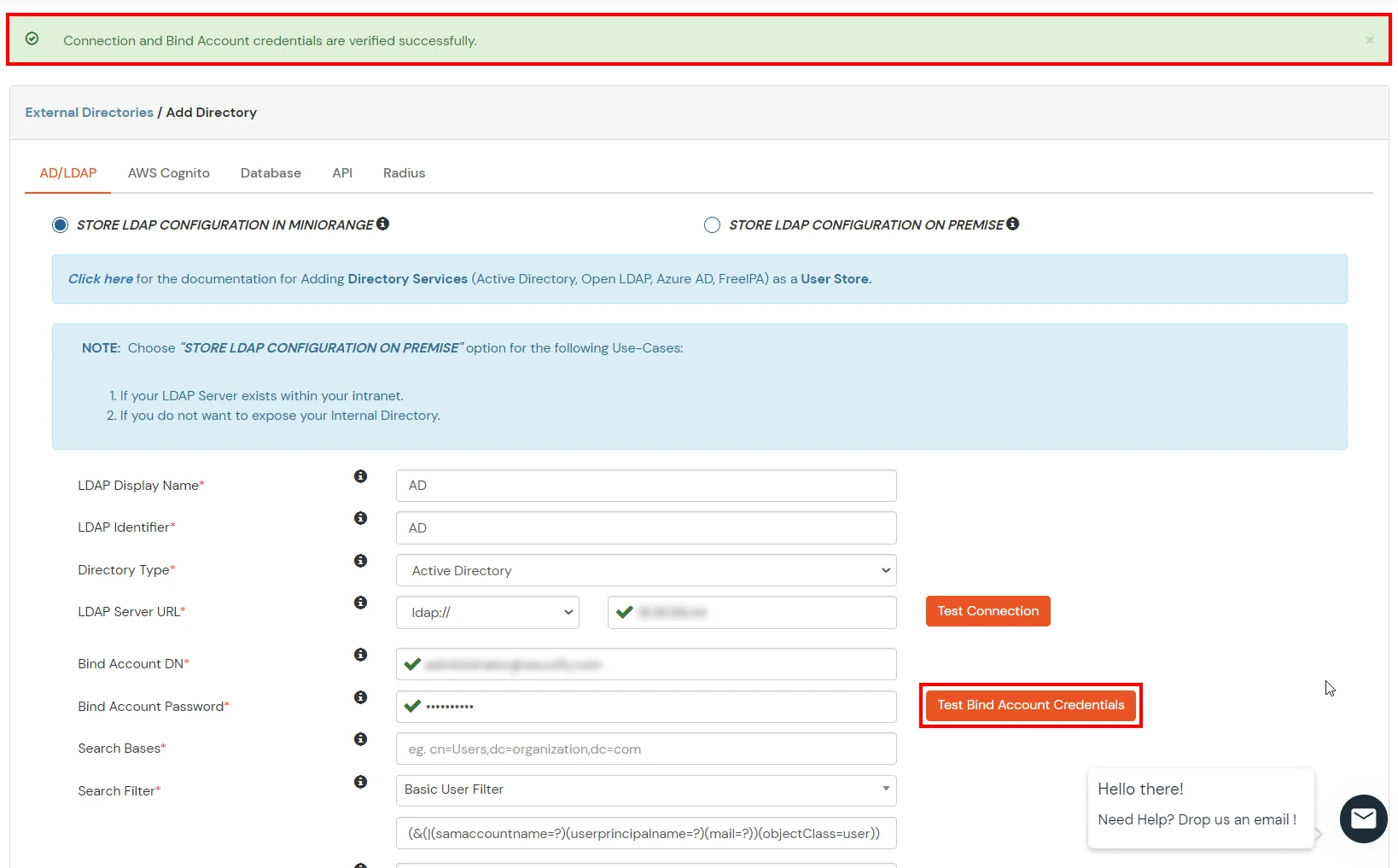
- Search Base is the location in the directory where the search for a user begins. You will get this from the same place you got your Distinguished name.
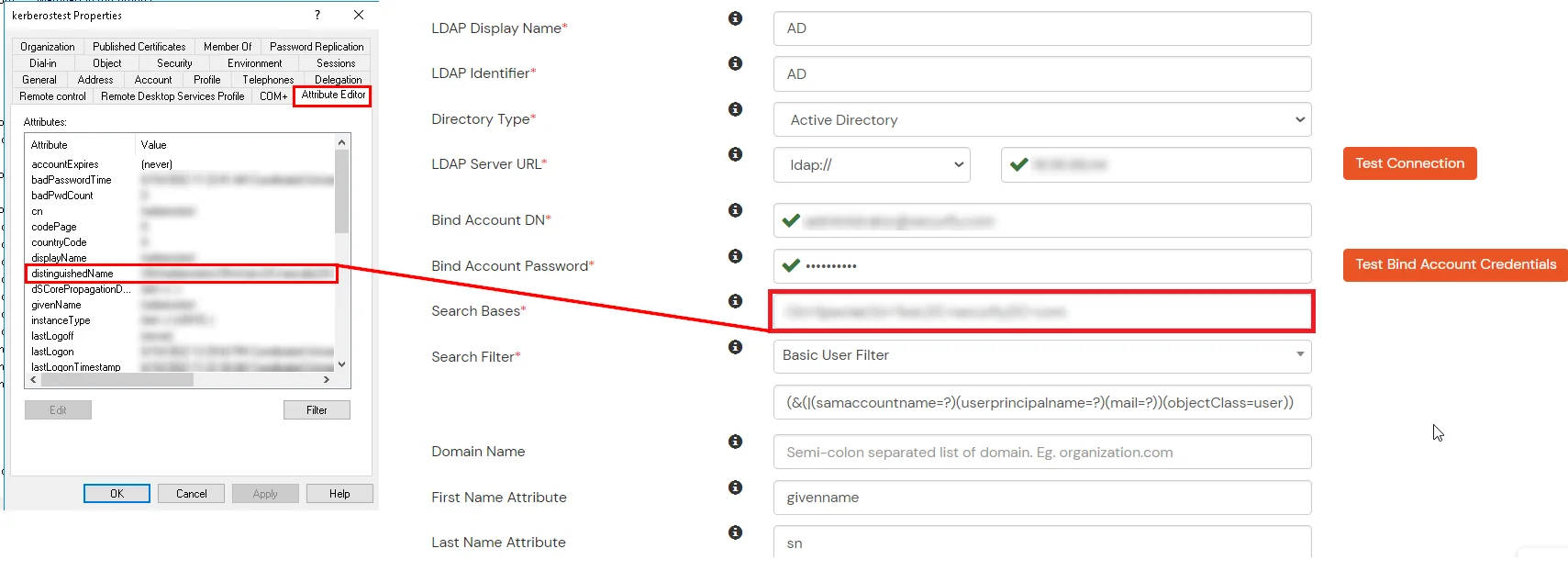
- Select a suitable Search filter from the drop-down menu. If you use User in Single Group Filter or User in Multiple Group Filter, replace the <group-dn> in the search filter with the distinguished name of the group in which your users are present. To use custom Search Filter select "Write your Custom Filter" option and customize it accordingly.
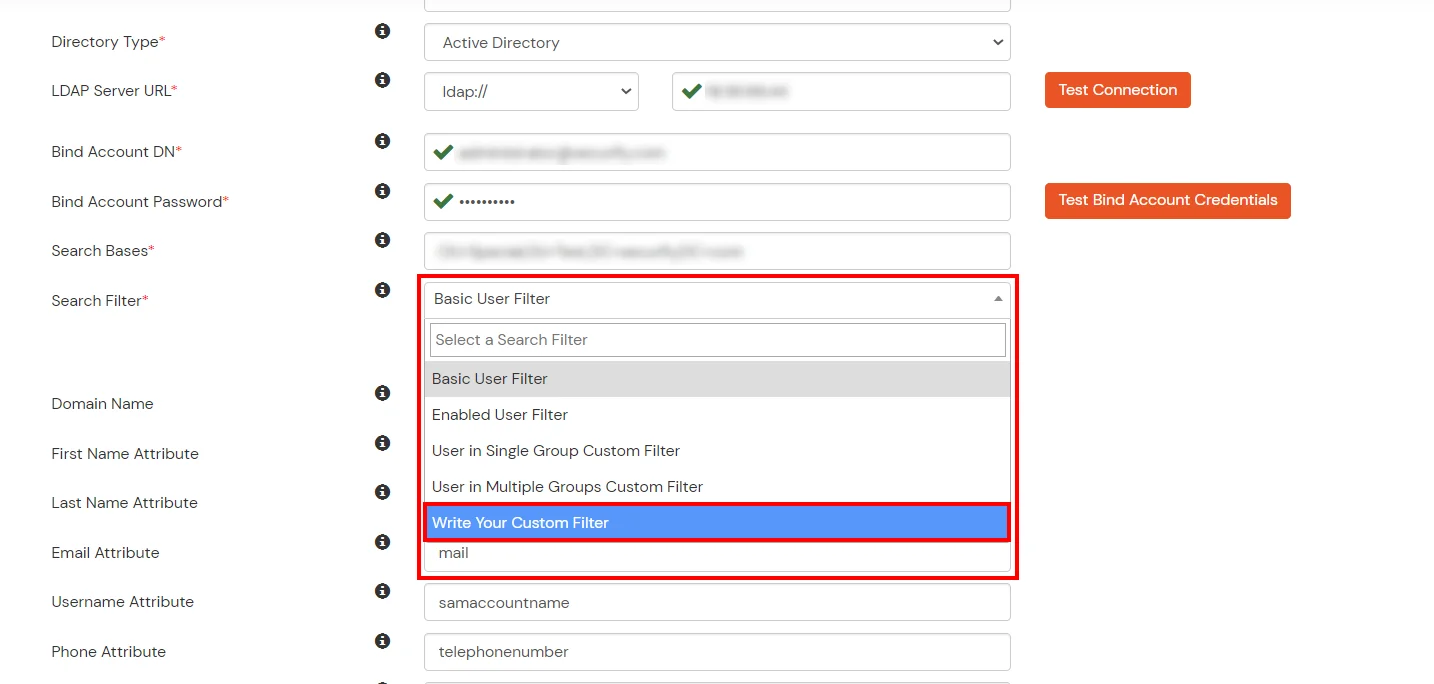
- You can also configure following options while setting up AD. Enable Activate LDAP in order to authenticate users from AD/LDAP. Click on the Save button to add user store.
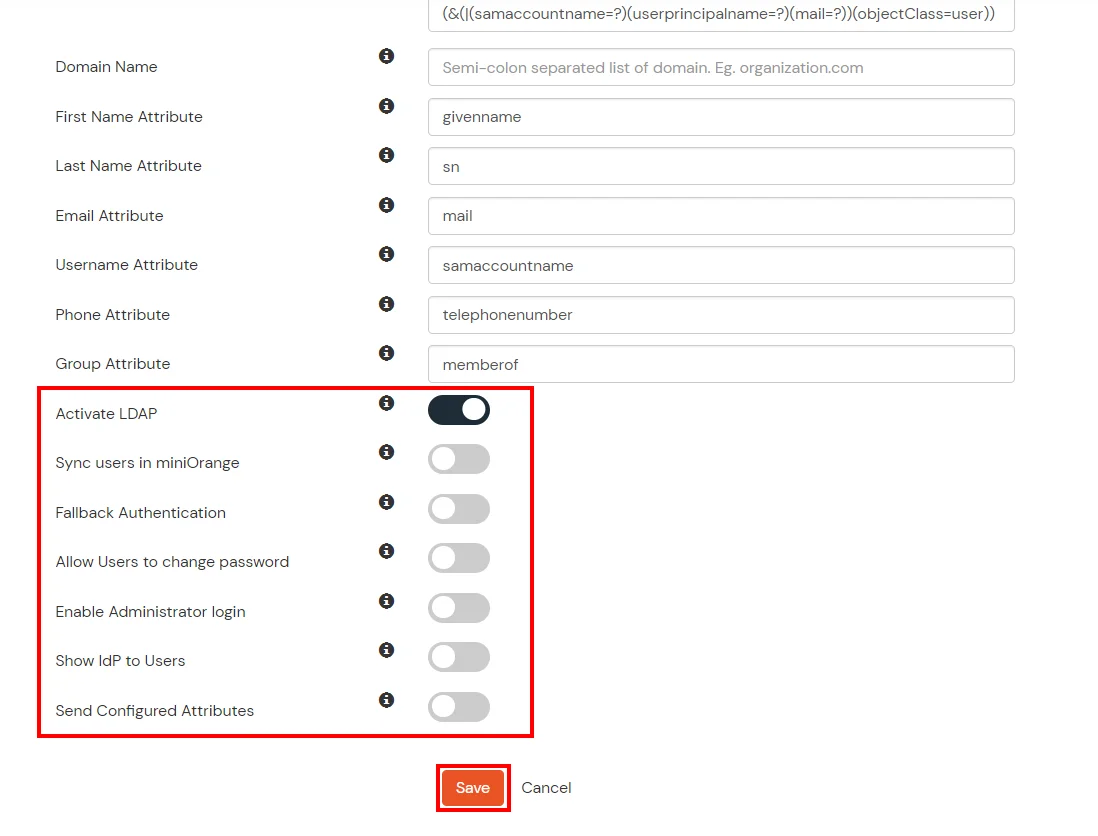
Here's the list of the attributes and what it does when we enable it. You can enable/disable accordingly.
| Attribute |
Description |
| Activate LDAP |
All user authentications will be done with LDAP credentials if you Activate it |
| Sync users in miniOrange |
Users will be created in miniOrange after authentication with LDAP |
| Fallback Authentication |
If LDAP credentials fail then user will be authenticated through miniOrange |
| Allow users to change password |
This allows your users to change their password. It updates the new credentials in your LDAP server |
| Enable administrator login |
On enabling this, your miniOrange Administrator login authenticates using your LDAP server |
| Show IdP to users |
If you enable this option, this IdP will be visible to users |
| Send Configured Attributes |
If you enable this option, then only the attributes configured below will be sent in attributes at the time of login |
- Click on Save. After this, it will show you the list of User stores. Click on Test Connection to check whether you have enter valid details. For that, it will ask for username and password.
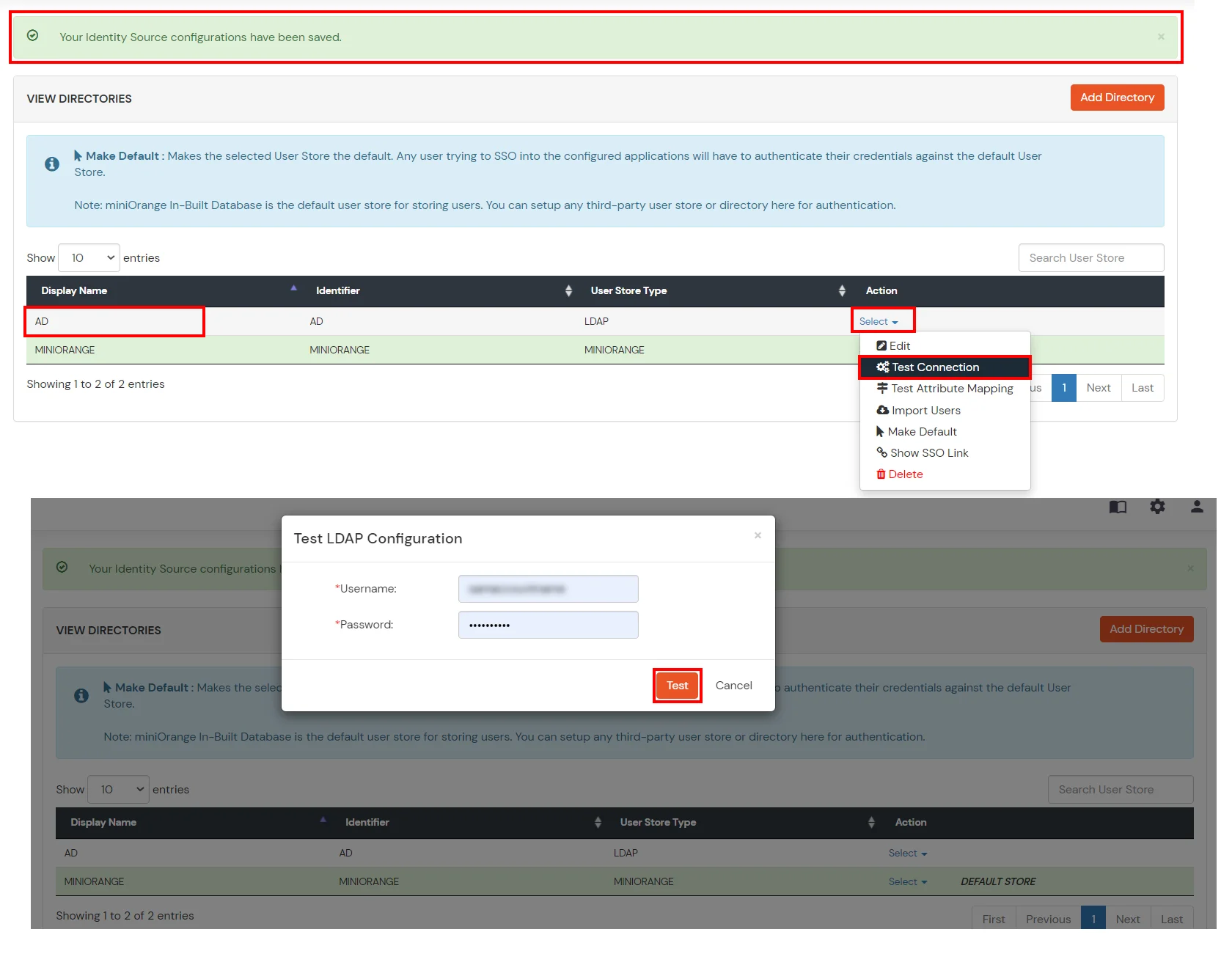
- On Successful connection with LDAP Server, a success message is shown.
- Click on Test Attribute Mapping.
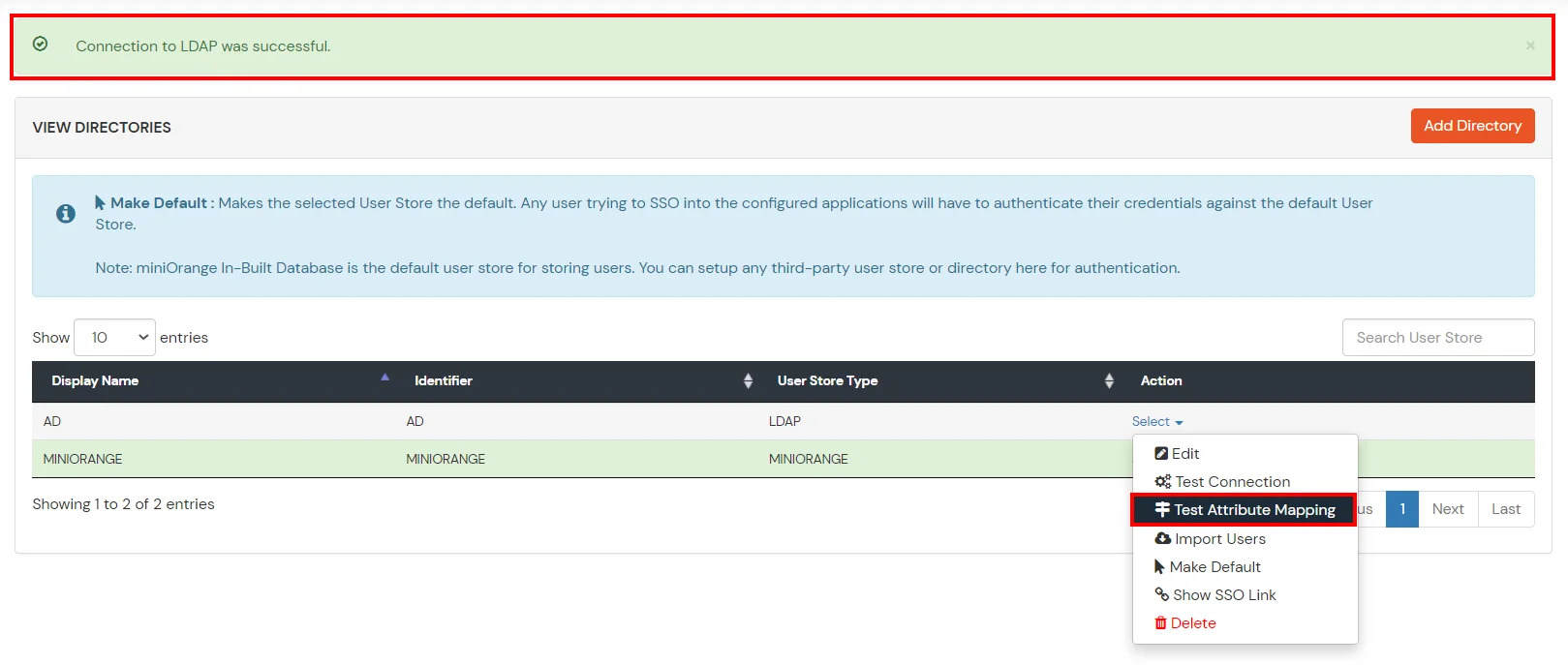
- Enter a valid Username. Then, click on Test. Mapped Attributes corresponding to the user are fetched.
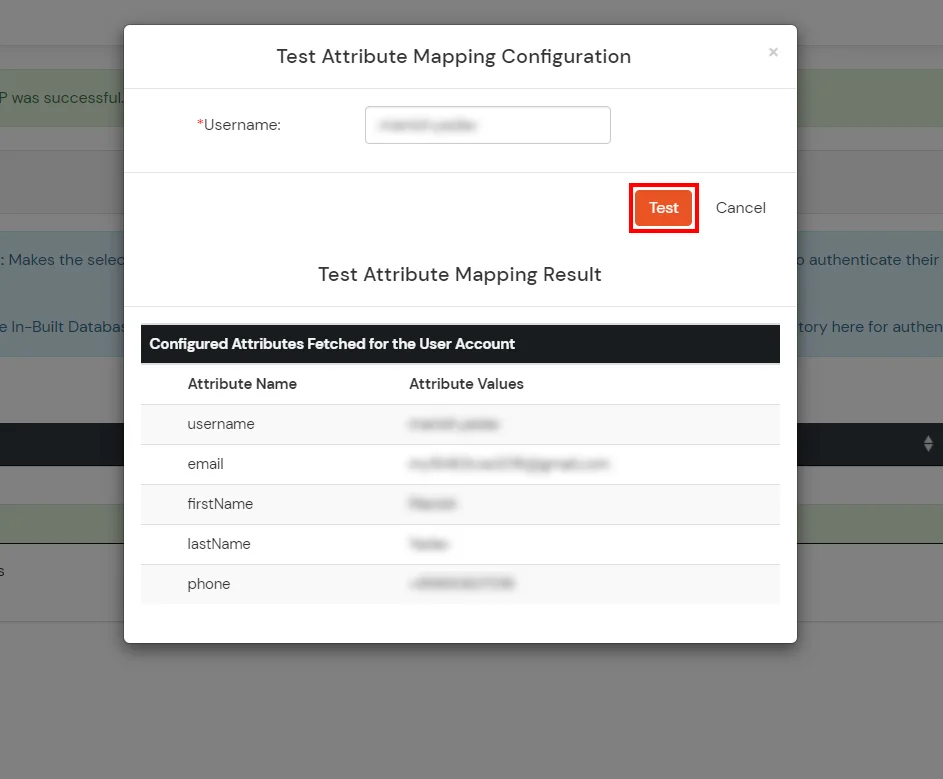
- After successful Attribute Mapping Configuration, go back to the ldap configuration and enable Activate LDAP in order to authenticate users from AD/LDAP.
Refer our guide to setup LDAPS on windows server.
User Import and Provisioning from AD
- Go to Settings >> Product Settings in the Customer Admin Account.
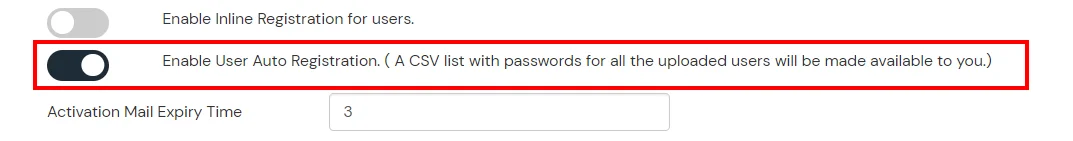
- Enable the "Enable User Auto Registration" option and click Save.
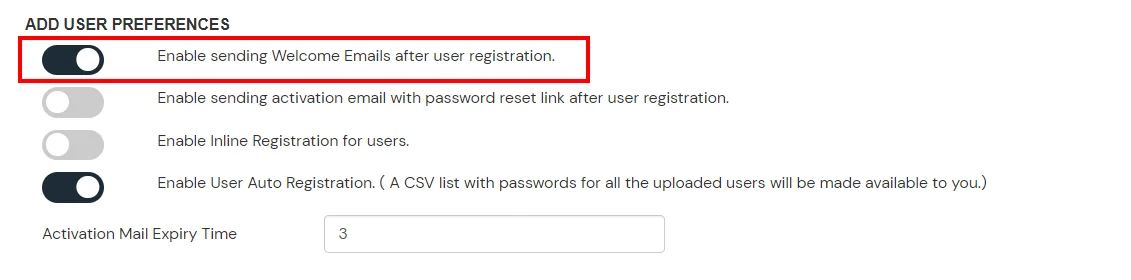
- (Optional) To send a welcome email to all the end users that will be imported, enable the "Enable sending Welcome Emails after user registration" option and click Save.
- From the Left-Side menu of the dashboard select Provisioning.
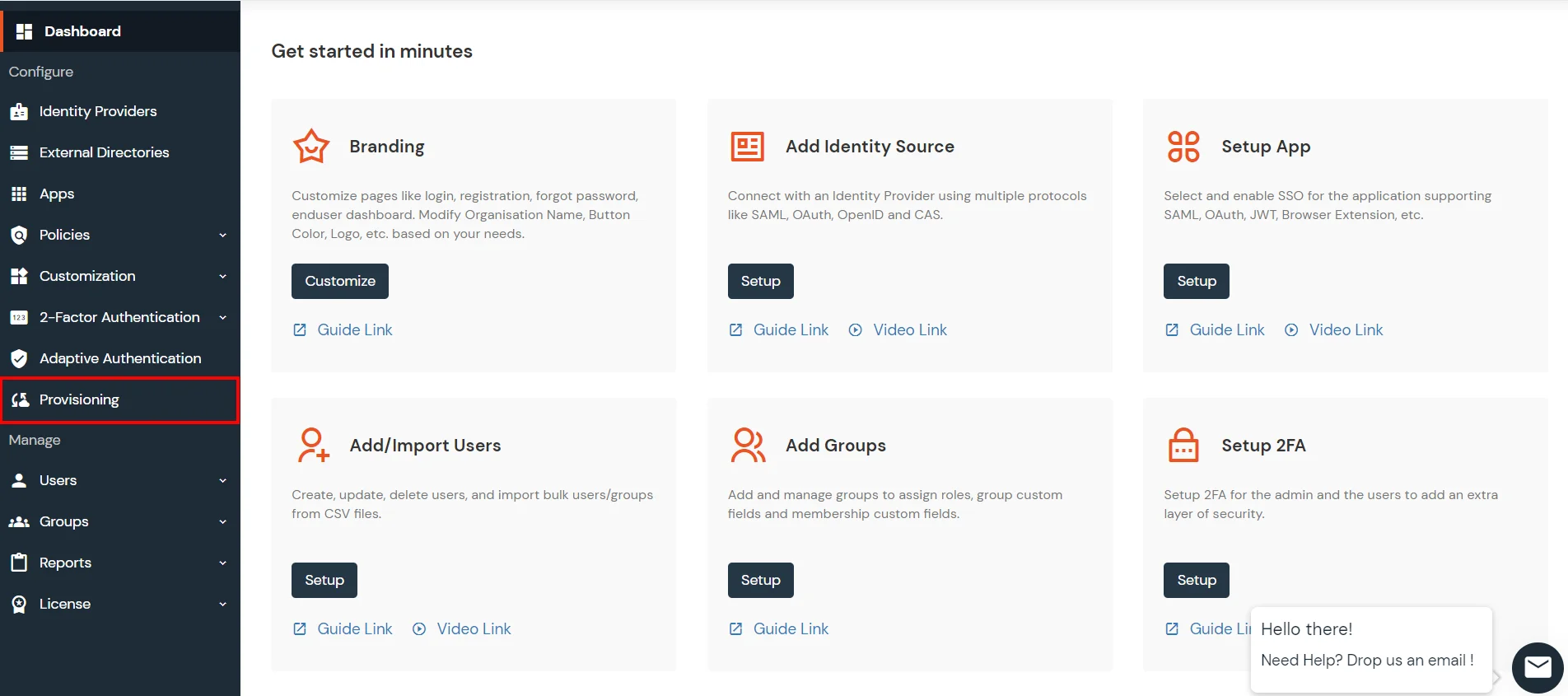
- In Setup Provisioning tab select Active Directory in the Select Application drop-down.
- Toggle the Import Users tab, click on Save button.
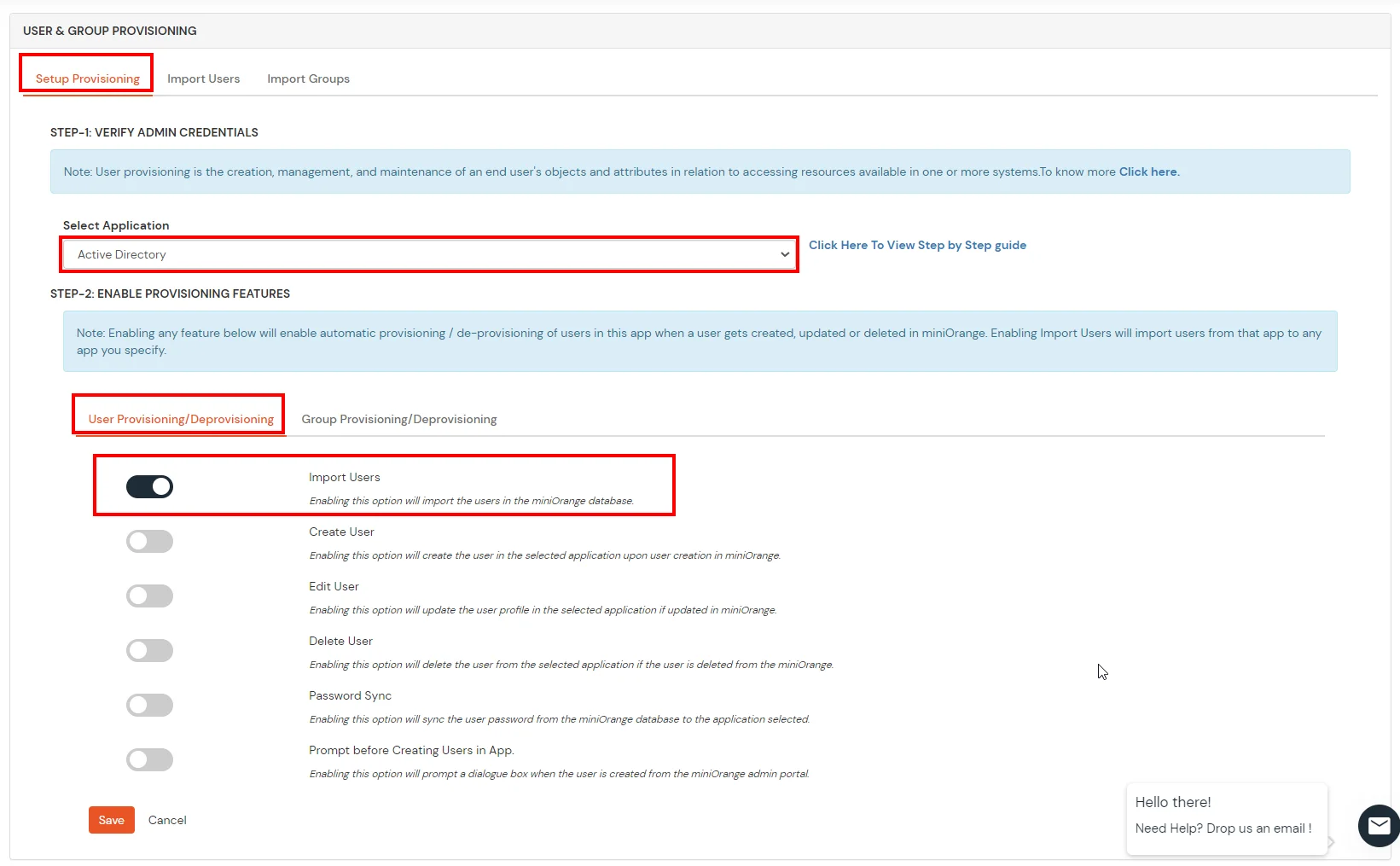
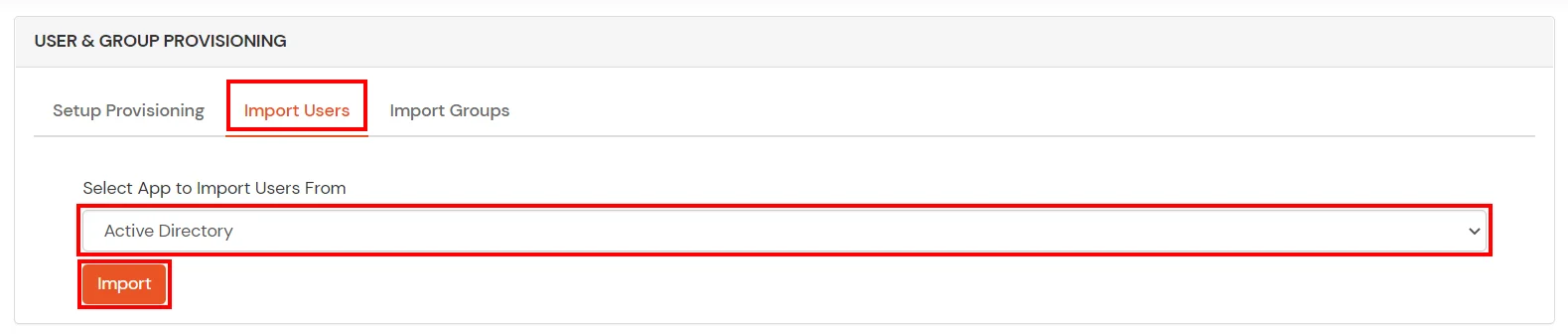
- On the same section, switch to Import Users section.
- Select Active Directory from the dropdown and click on the Import Users tab, to import all the users from Active Directory to miniOrange.
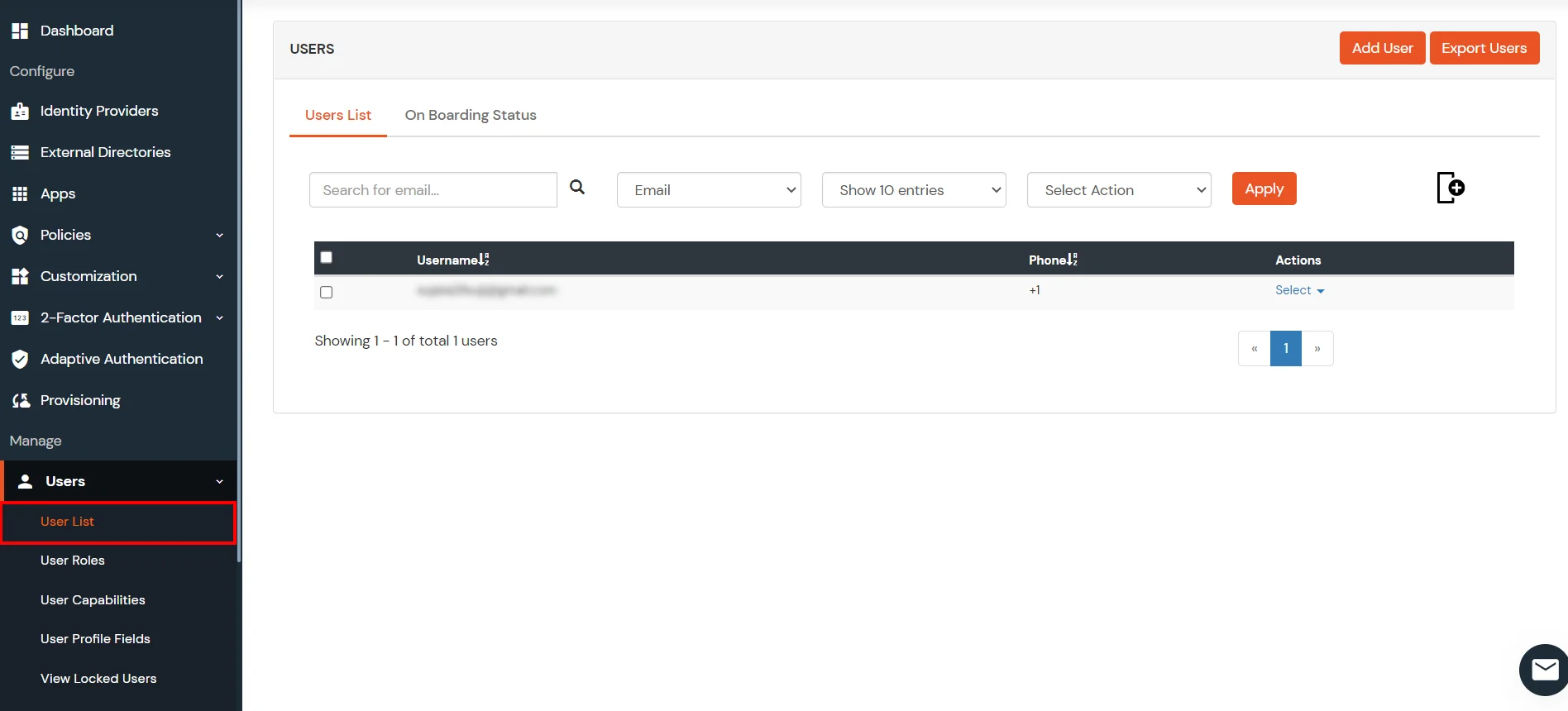
- You can view all the Users you have imports by selecting Users >> User List from Left Panel.
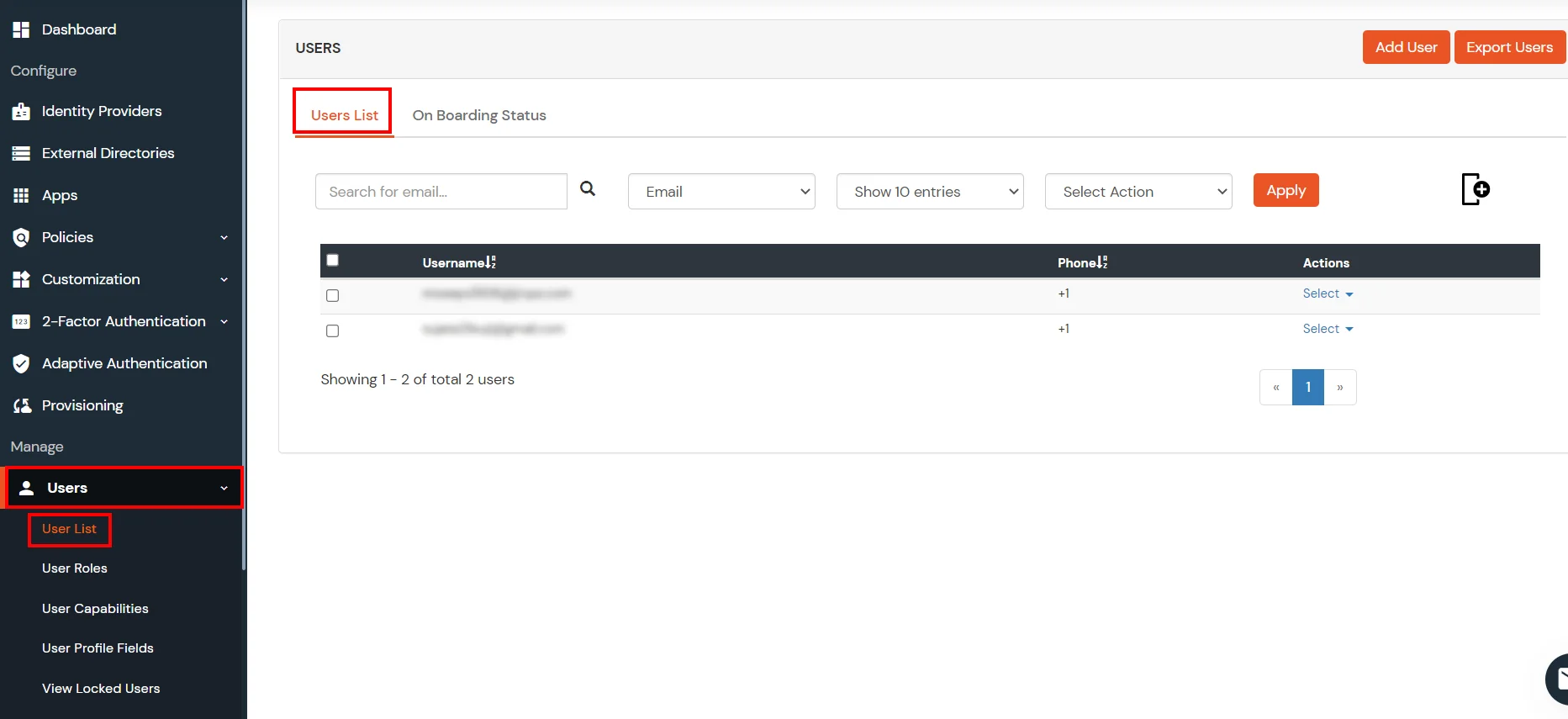
- All the imported users will be auto registered.
- These groups will be helpful in adding multiple 2FA policies on the applications.
miniOrange integrates with various external user sources such as directories, identity providers, and etc.
External References
- Learn how to set up Azure DevOps Multi-Factor Authentication (MFA)
- What is Microsoft Azure Active Directory?
- Solution for 5000+ Pre-Integrated Apps
- Azure DevOps SSO integration with on-premises environments
- Azure DevOps Two-Factor Authentication (2FA) solution