Need Help? We are right here!
Search Results:
×Google Workspace Security, for an organization, offers complete control and access over Google accounts and its applications. miniOrange offers various services such as SSO , 2FA , multi-factor authentication , adaptive authentication , and user lifecycle management into your Google Workspace account. You can now get seamless access to all your enterprise resources, be it in-cloud or on-premise. It is now possible to restrict the use of Google Workspace within your organization’s network. Overall, this enhances security by blocking users’ access outside this network.
Many global organizations exercise certain restrictions as a security measure to protect their data and other resources; such as turning off email servers manually so that employees are abstained from accessing their inbox after office hours. Enabling security for G Suite manually demands a high-versed technical person to handle the utilization case. If the person lacks technical knowledge and performs something wrong then your G Suite cloud security risk level might increase unexpectedly. So here we need an advanced cloud security system that will overcome these issues and provide a top-notch security solution to your G suite organizational data.
miniOrange takes full control and visibility of organizational data, which is stored on Google. It also allows IT administrators to analyze the employee’s behavior towards enterprise data. On detection of a possible breach, it instantly sends an alert email message to notify higher business authorities. miniOrange also renders the program to enforce access control standards at the macro level on the idea of the following:
A range of 15+ MFA methods to choose from adds an additional layer of security to get access to Google Workspace.
Restrict the number of devices the G Suite users can access the services on, Geo-location, IP restriction, time of login, etc.
Restrict access to your employee's personal Gmail accounts on their workstations using miniOrange’s consumer Gmail blocking service.
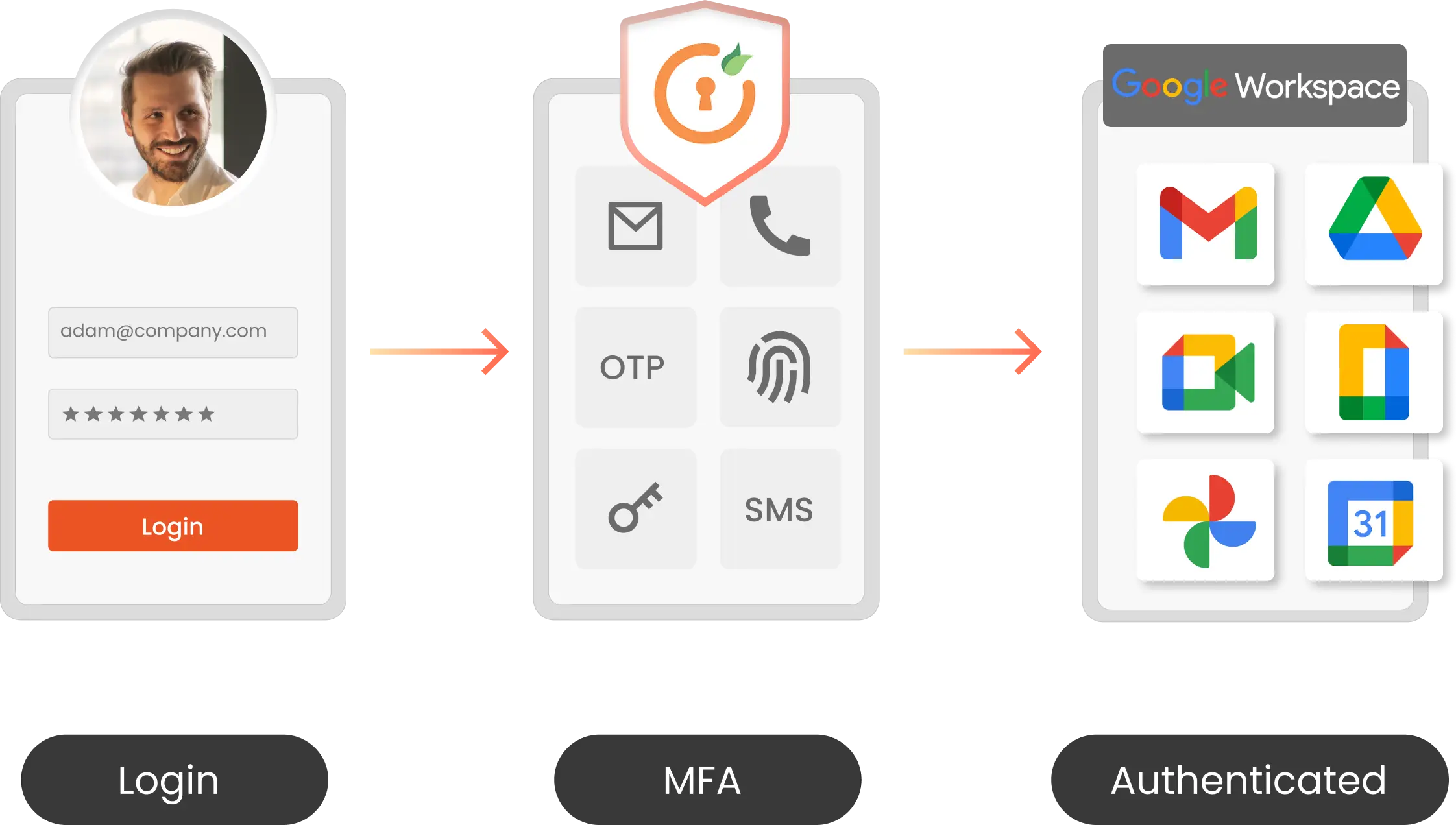
Google Workspace MFA security solution by miniOrange enables users to add an additional layer of security to their Google Workspace login authentication. Adding an additional verification layer acts as a security measure and prevents unauthorized people from accessing the Google account. You can also securely access Google Workspace with miniOrange Multi-Factor Authentication (MFA). MFA solution prevents unwanted users from accessing business information with 15+ authentication methods.
Role-Based MFA
15+ MFA Methods (Push Notification, Hardware Token support)
Passwordless Authentication
Offline MFA Support
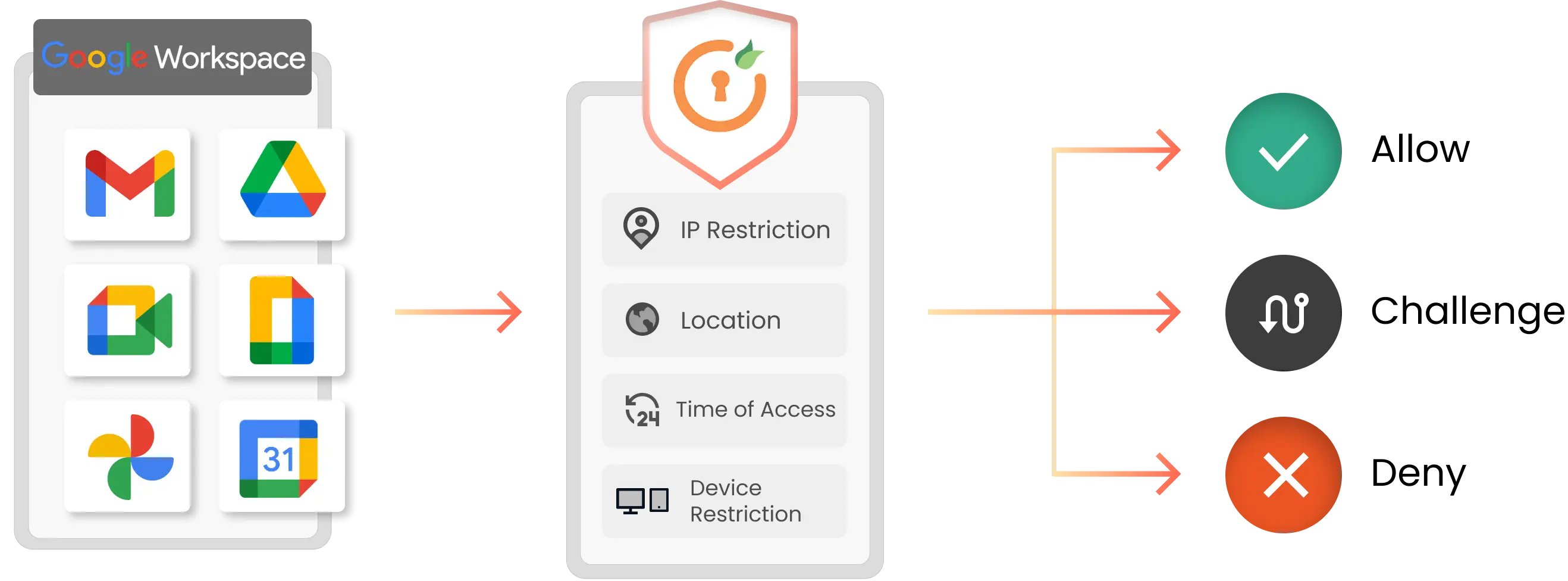
Risk-based MFA authenticates users based on - IP, Device, Location, and Time of login. It offers an additional layer of MFA security according to the user’s risk profile in real-time circumstances, along with access levels set by the security admin. As a part of the Risk-based MFA feature, it restricts access of users based on Geo-location, IP restriction , time of login, device used, etc. to detect and block frauds in real-time.
Restrict access based on - IP, Device, Location, and Time
Real time risk assessment
Group and Role based Assignment
Set granular access Security Policies

Denying access to personal Gmail account is required in order to ensure, there is no weak link in the organization and critical information is not shared outside the network. miniOrange offers Gmail blocking solution, where all the employees / users will use the email account given to them by their administrator only. A solution like this restricts access to a user’s personal Gmail account.
Limit users access to personal Gmail
Smooth policy setting process
Alert administrators about policy violations
Data Protection standard policy is appended by miniOrange during this consolidated Google Security software. These policies make sure that employees won't send confidential business information outside the business network. Whenever the G Suite solution detects the occurrence of such an incidence, it immediately blocks the user access and sends an alert mail to the business authority. Aside from this, many other subsequent security measures are provided by miniOrange.
Secure authentication for your G Suite environment with miniOrange’s 2FA and MFA methods. miniOrange provides 15+ Authentication methods such as OTP over SMS, hardware tokens, authenticator apps, etc. to enhance your security level.
Employee productivity and efficiency increase since they save time by not having to repeatedly log in to the G suite applications and getting an MFA prompt only when a robust authentication is needed.
MFA solution extends and adapts to all G suite applications. miniOrange's MFA plays a pivotal role in providing visibility for all risk areas, from on-premises networks to mobile devices and the cloud.
G suite security by miniOrange helps in runtime risk analysis which increases the effort and resources required to cope with a successful account breach.
miniOrange provides 24/7 support for all the Secure Identity Solutions. We ensure high-quality support to meet our customer’s satisfaction. We respond to all of our queries in less than 12 hours.
miniOrange provides the most affordable Secure Identity Solutions for all use cases and offers different packages based on customers’ requirements. You don’t have to pay for any users who are not using our system.
