Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×Google 2-step verification or Two-Factor Authentication (2FA/MFA) is a security measure which includes the process of secure Authentication and verifying identity in which a user or an organisational employee has to provide two factors to gain the access to Google (G Suite) Cloud Data. Gsuite 2-step verification or Gsuite 2fa starts with the user submitting his traditional username & password. Once the user successfully verifies the identity and gets authenticated with the 1st step verification, The second configured 2FA (OTP over SMS, Push Notifications, Google Authenticator etc) method prompts on for 2nd-step verification. After successfully signing in with both of the steps a user is granted access to the Google (G Suite) account. This additional verification layer acts as a security measure and prevents unauthorized people from accessing the Google account by verifying your identity even if cyber attackers get to know your credentials. You can also restrict your access based on location, time of access, and number of devices with the minOrange adaptive authentication solution for Gsuite and other apps.
miniOrange provides 15+ authentication methods as a security measure and solutions for various apps/websites including Google 2-step verification. It allows users and organizations to set up certain authentication & settings to verify identity which includes password restrictions, restricting sign-in methods, as well as other security settings. With miniOrange, you can configure TOTP based methods (Google Authenticator/Microsoft Authenticator, Authy Authenticator) as well as Push Notification, OTP over SMS/Email and many more as mfa methods for your Gsuite account. Apart from that, you can also add 2fa on multiple applications used by your organization.
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.

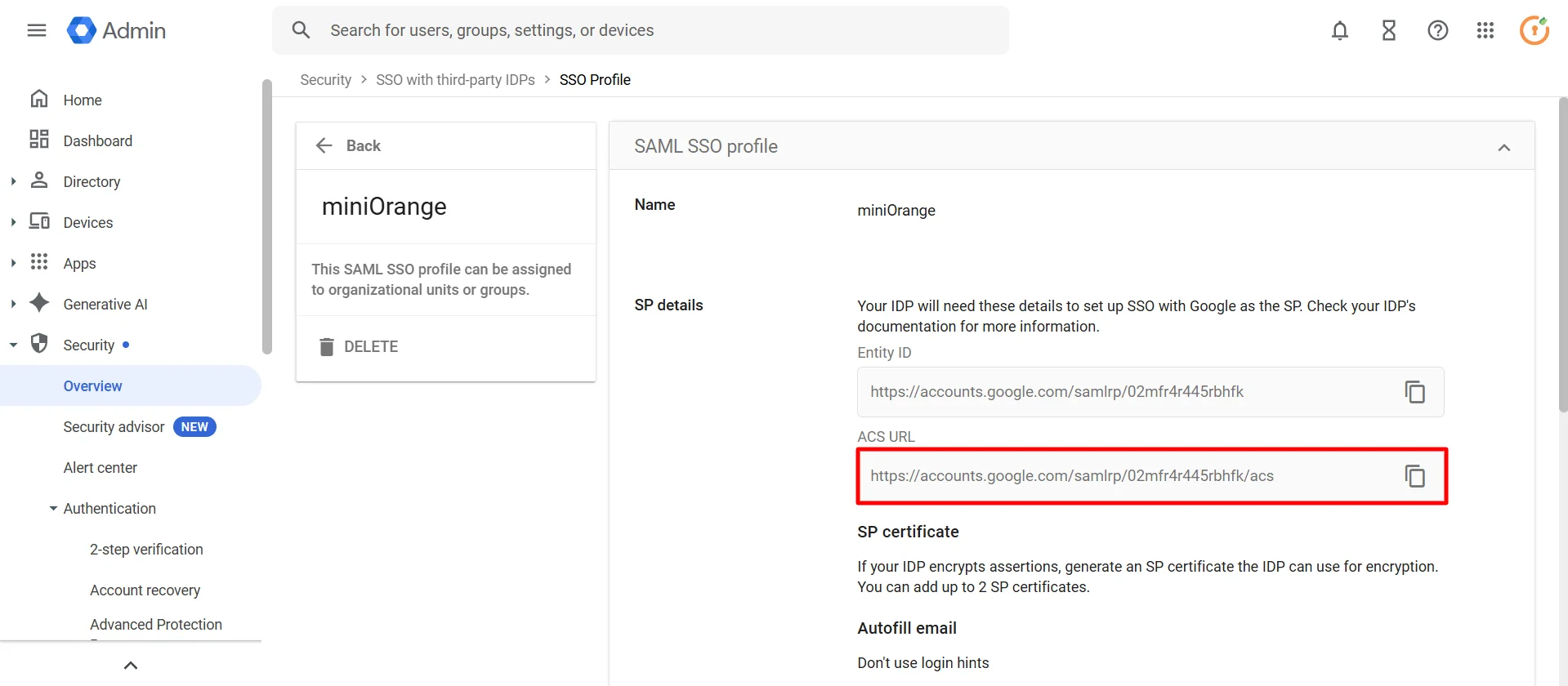
Google Appshttps://accounts.google.com/samlrp/<unique_app_id>https://accounts.google.com/samlrp/<unique_app_id>/acshttps://mail.google.com/a/out/tld/?logout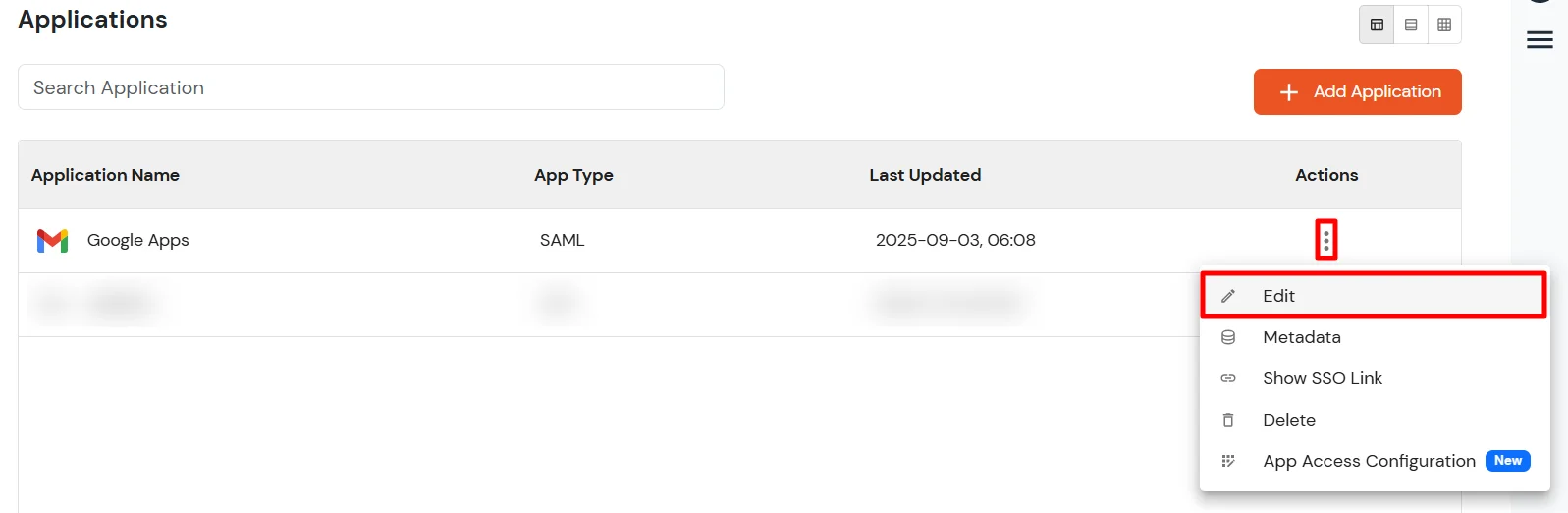
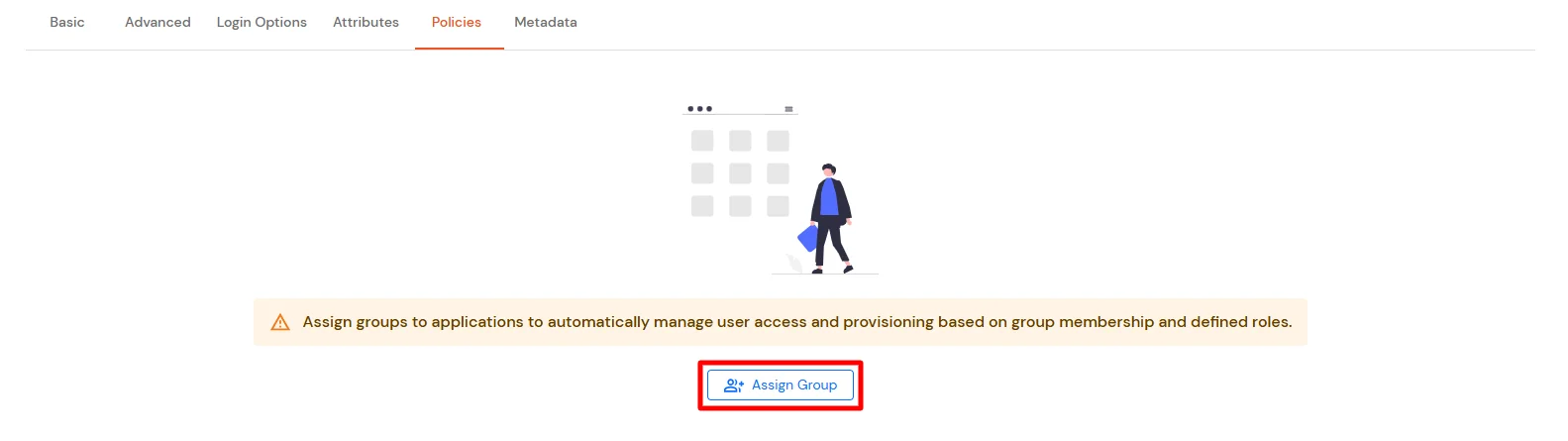
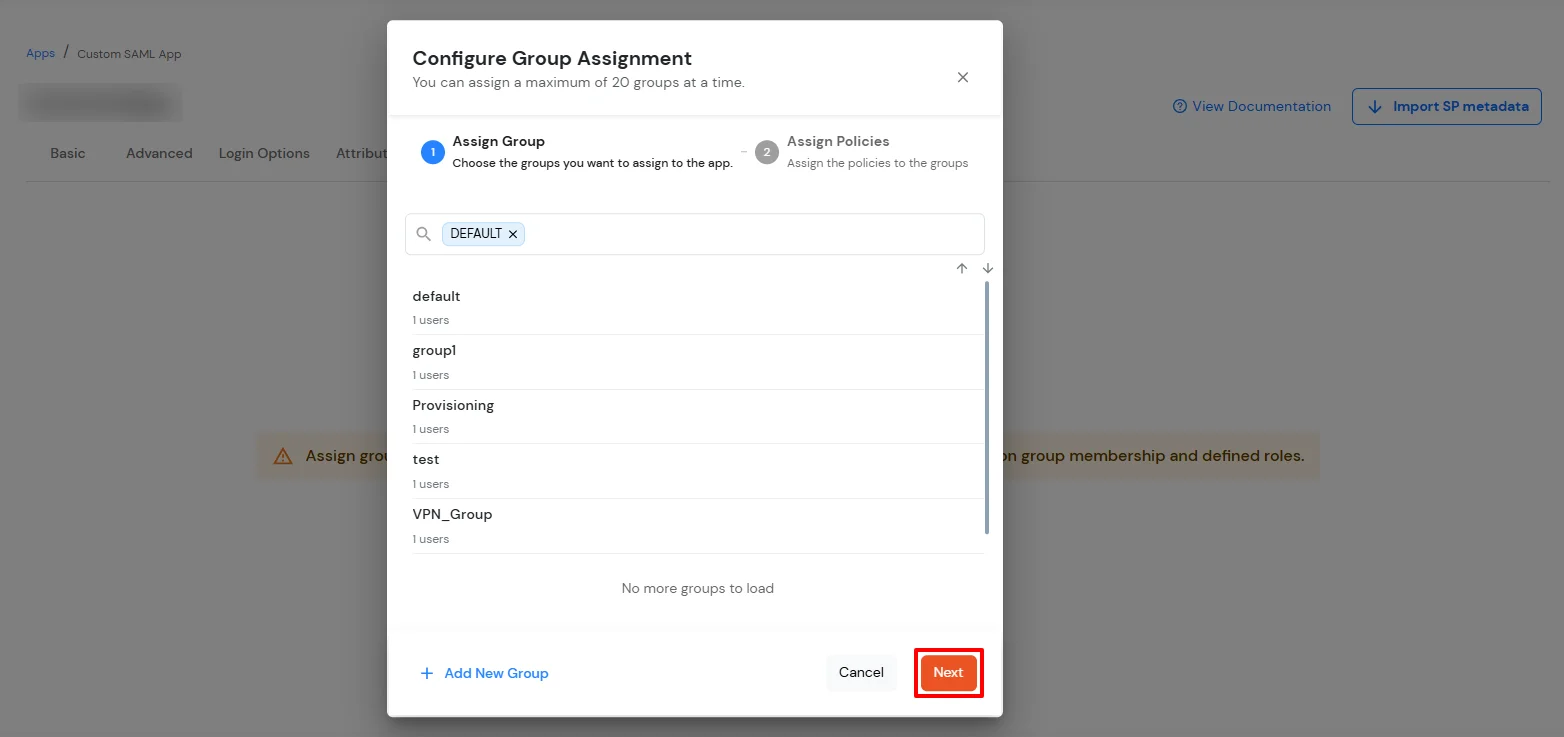
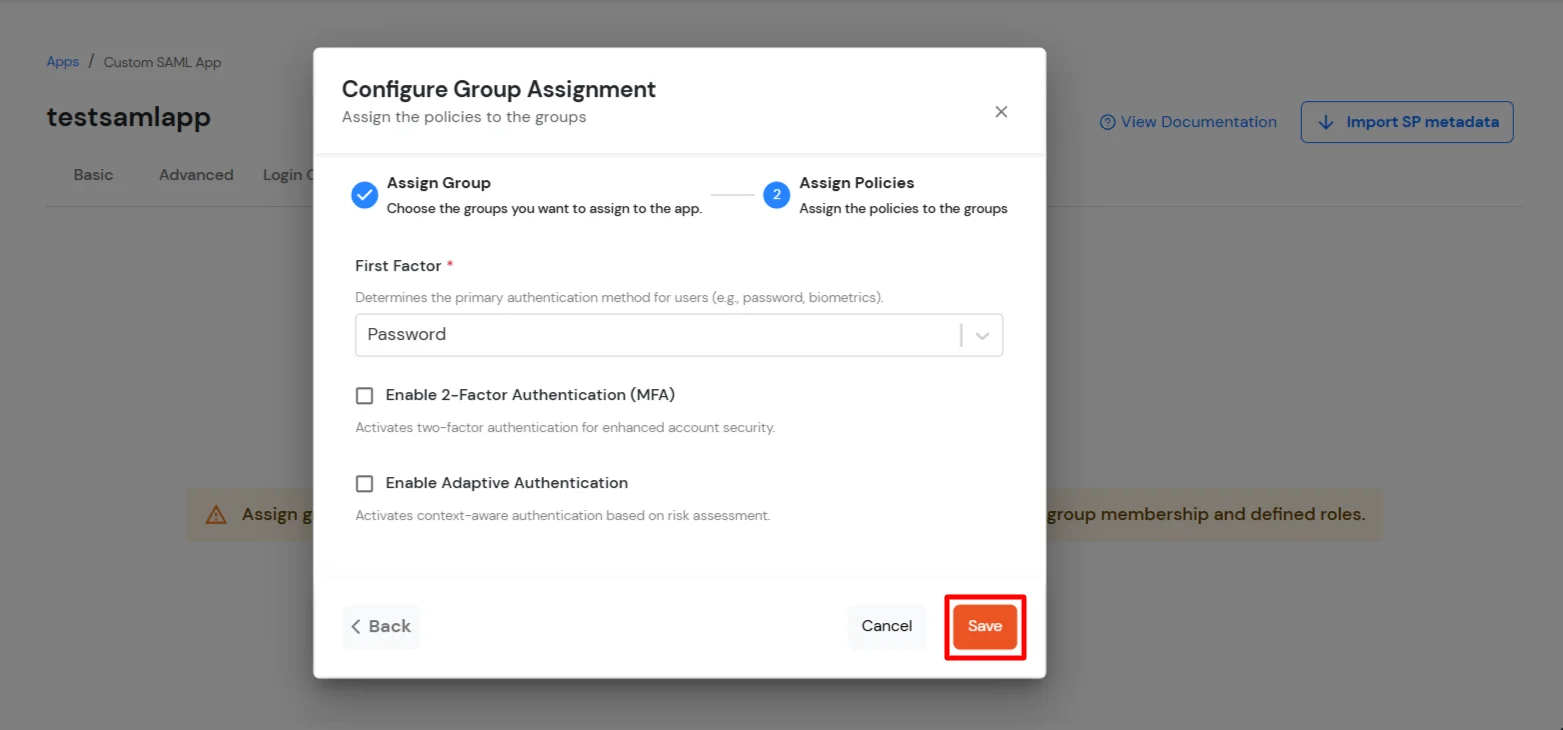
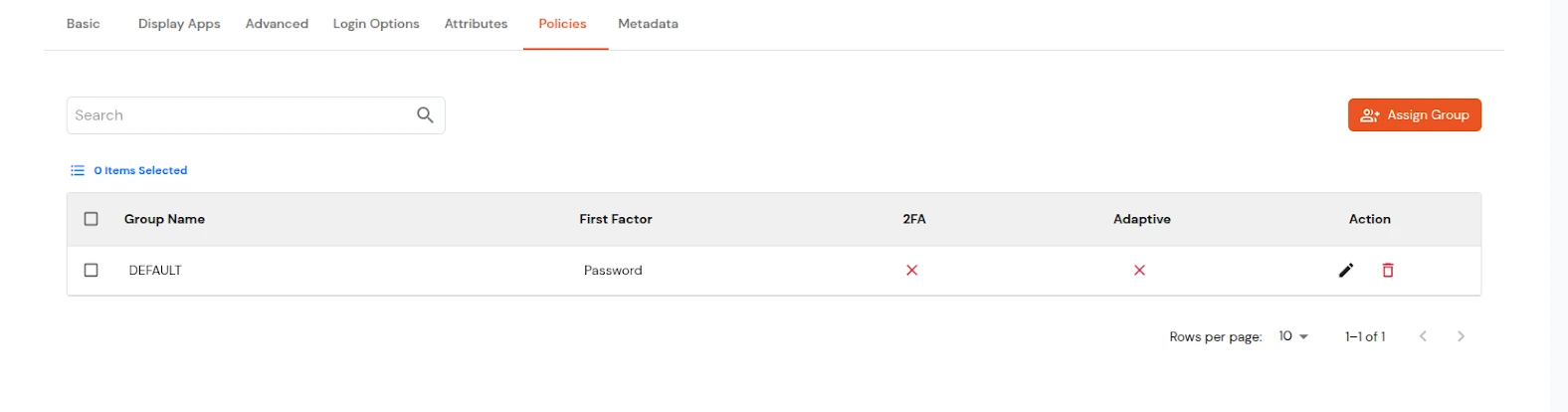
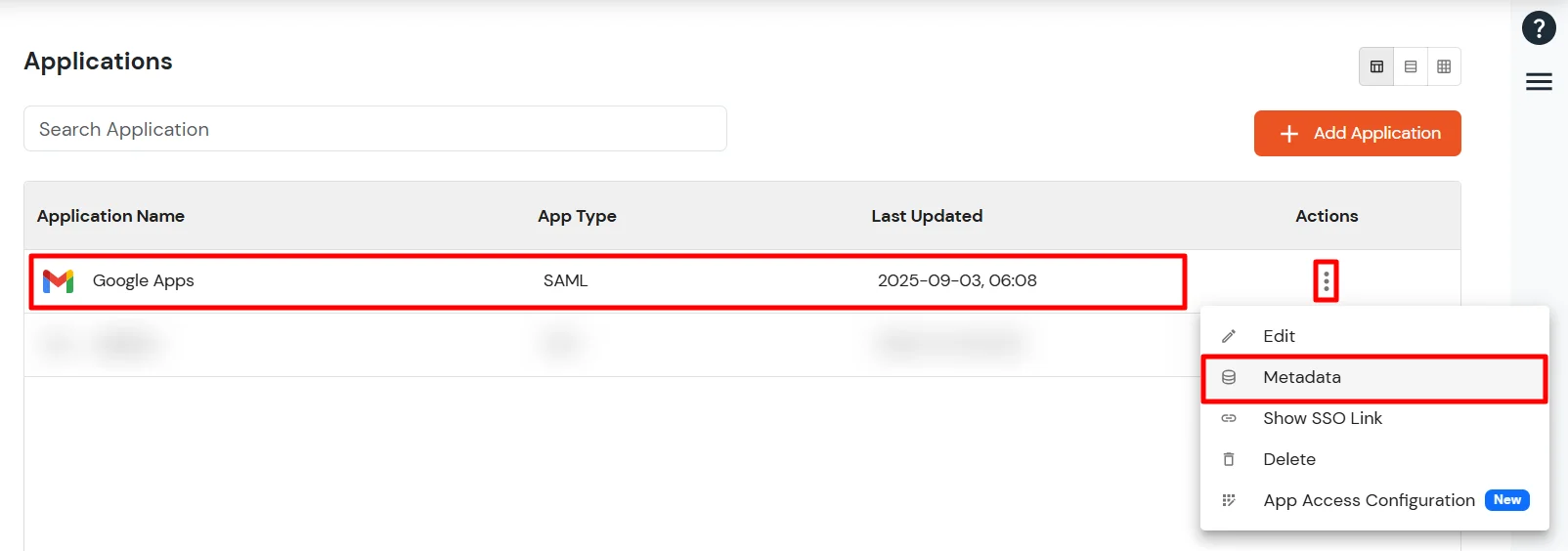
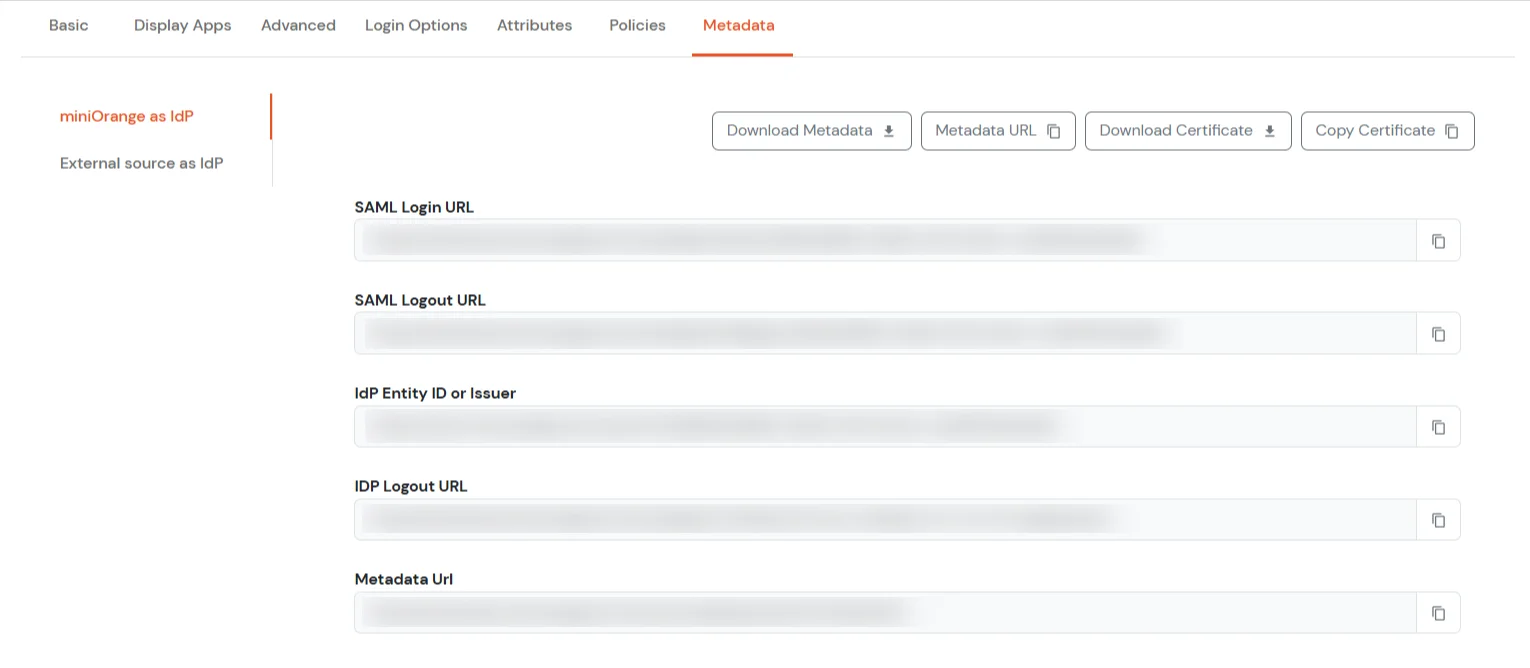
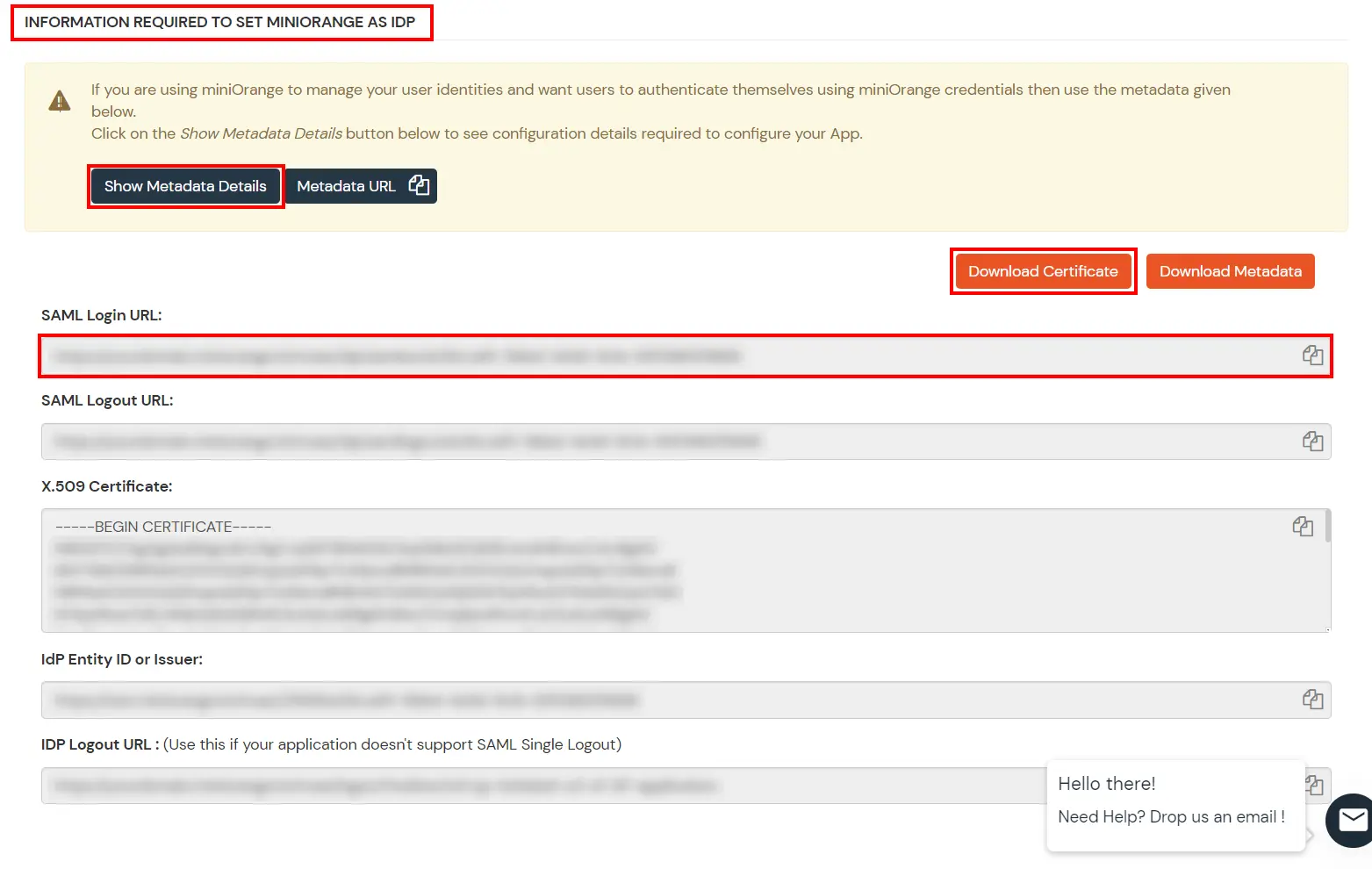
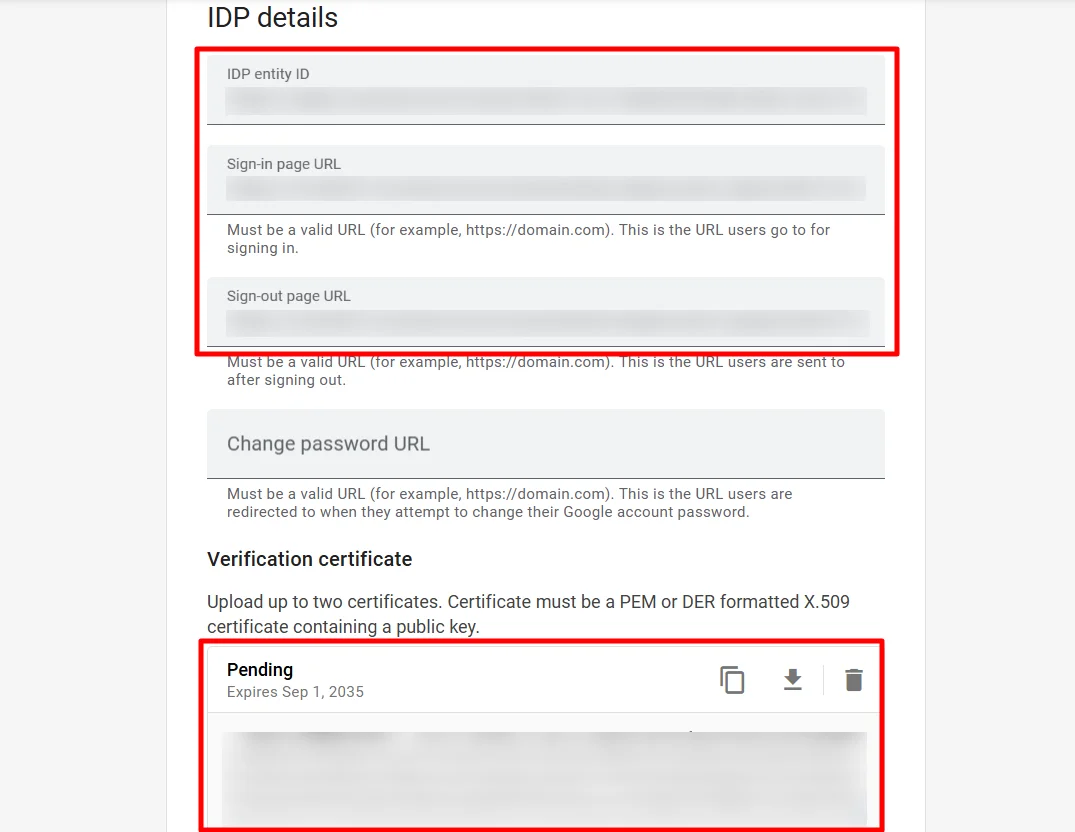
Get IdP Metadata Details to upload to Google Workspace:
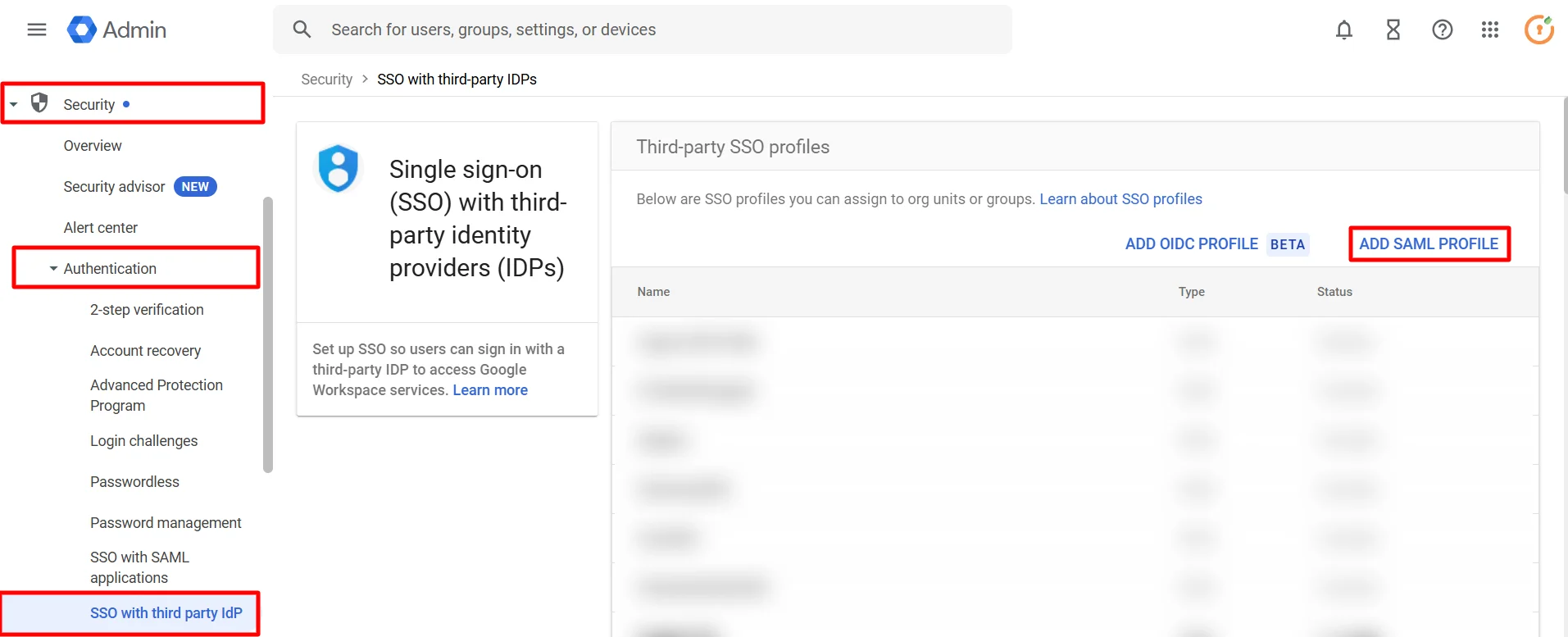
If you want some of your users to sign in to Google directly, you can move those users into an organizational unit (OU) or group. Then, manage SSO settings for the OU or group so that those users are authenticated by Google rather than using your third-party IdP. Follow the following steps:
Note: Get started is only available if you’ve already enabled your third-party SSO profile.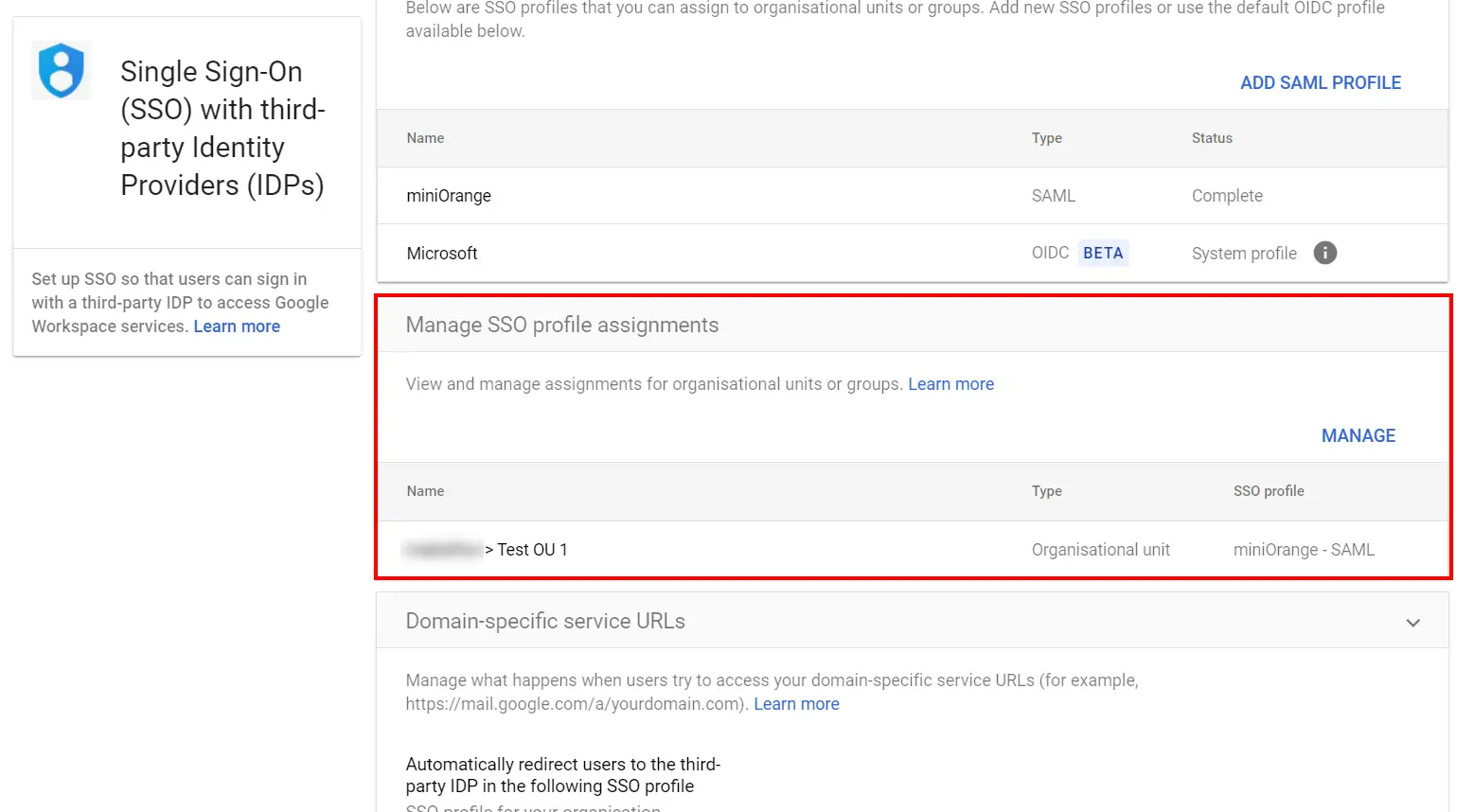
Note: If the SSO profile assignment for an OU or group differs from your domain-wide profile assignment, an
override warning appears when you select that OU or group. You can’t assign the SSO profile on a per-user
basis. The Users view let you check the setting for a specific user.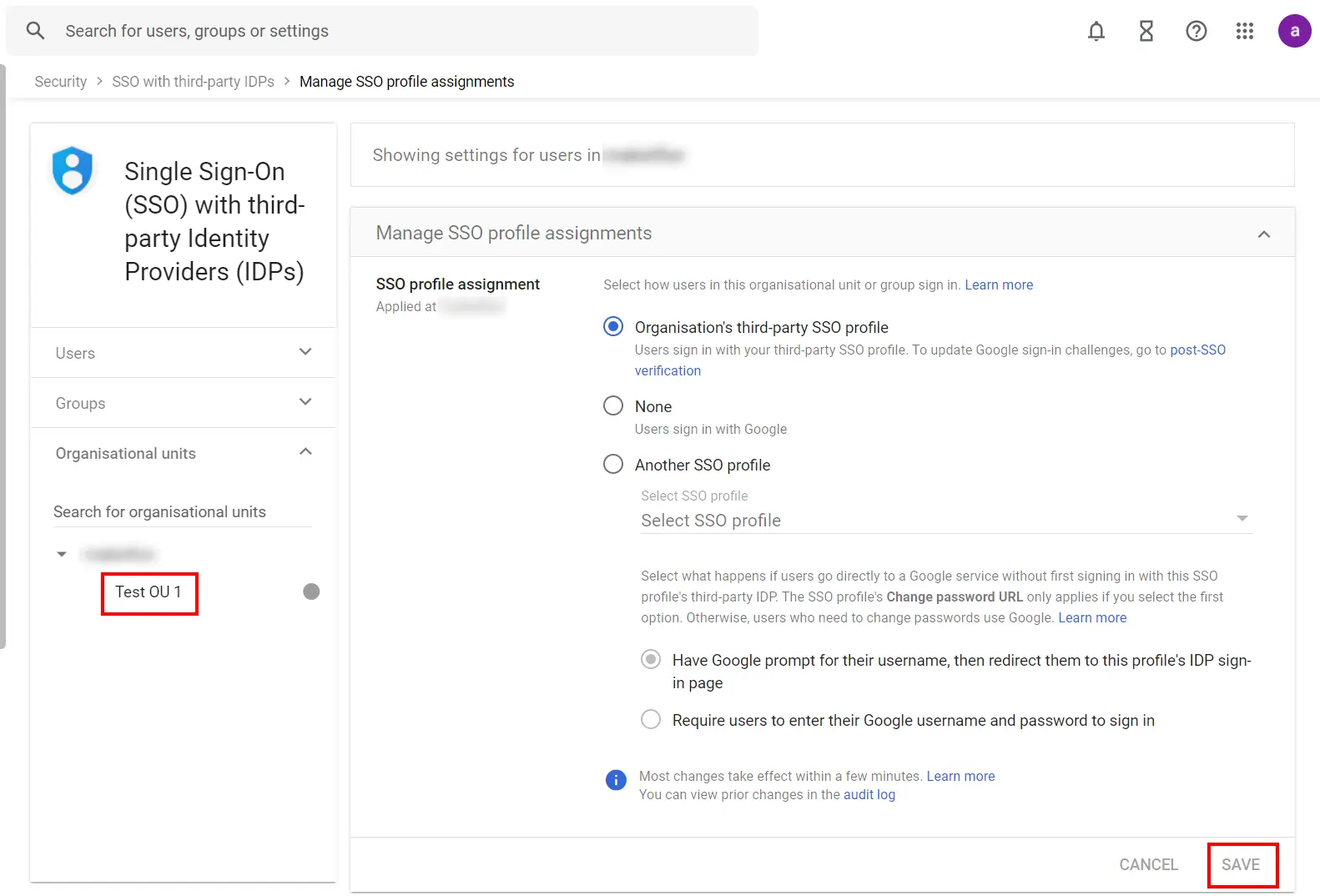
If you want to turn off the third-party authentication for all your users without changing the SSO profile assignment for OUs or groups, you can disable the third-party SSO profile:
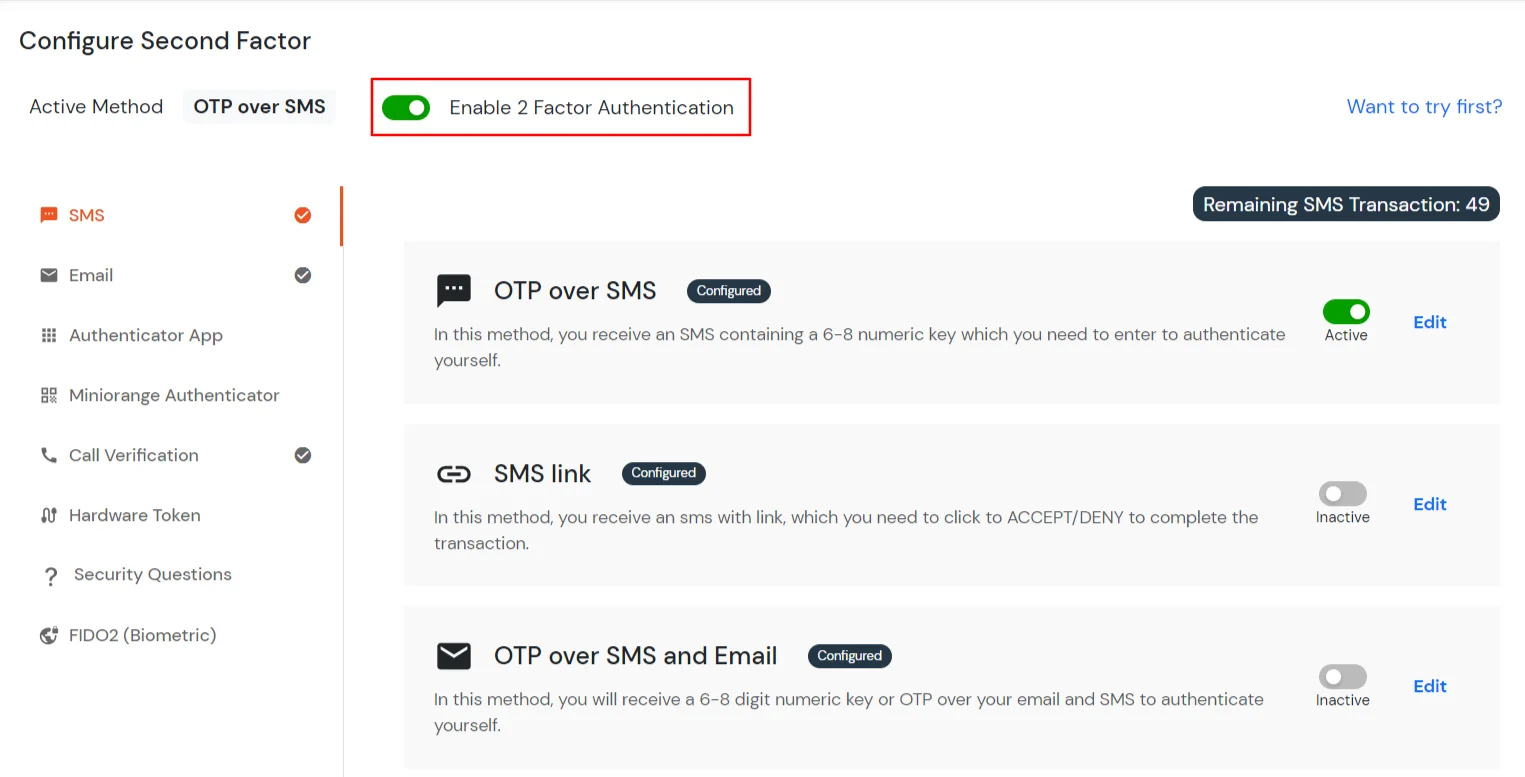
3.1: Enable 2FA for Users of Google Workspace (G Suite) app
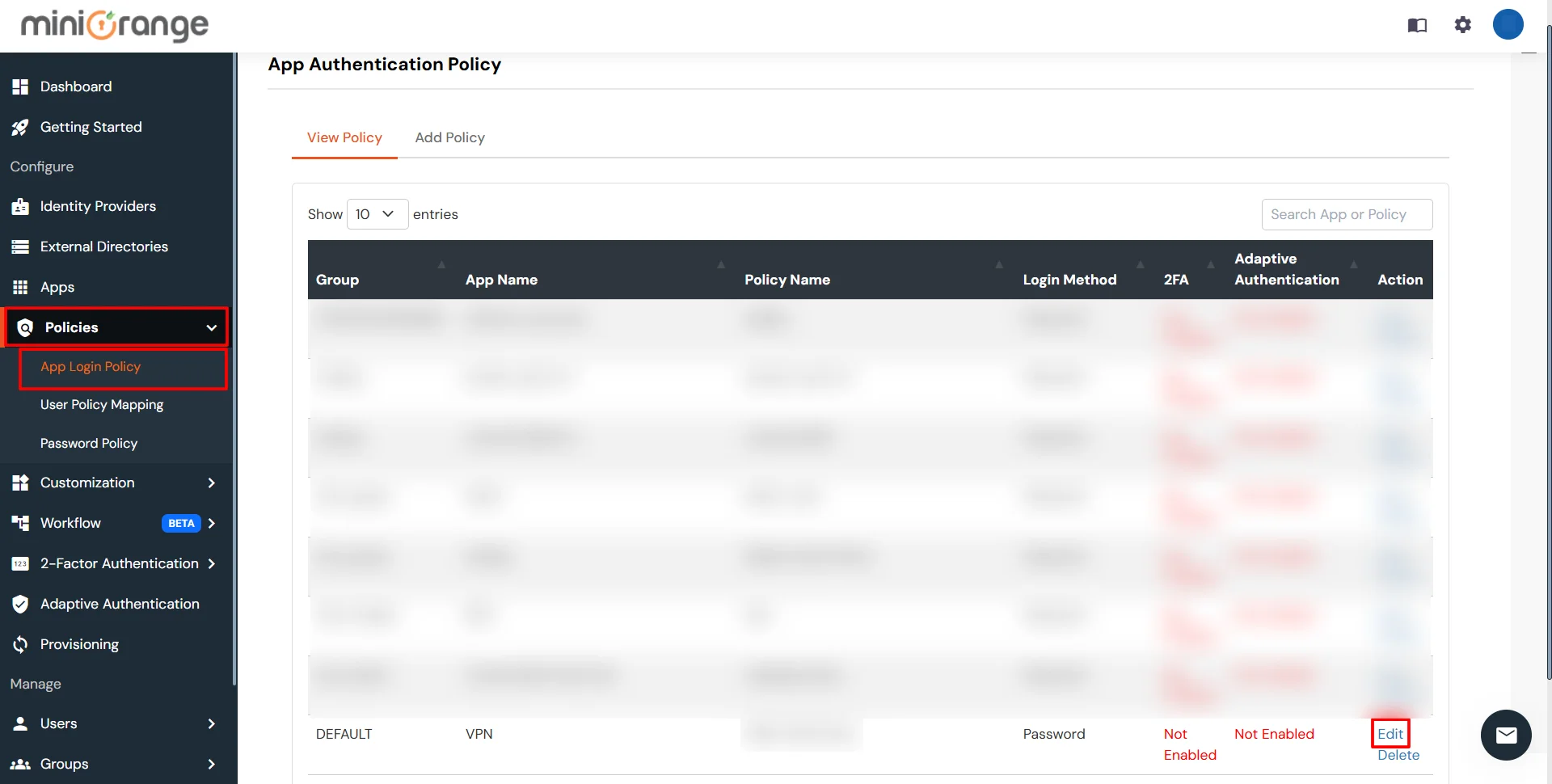
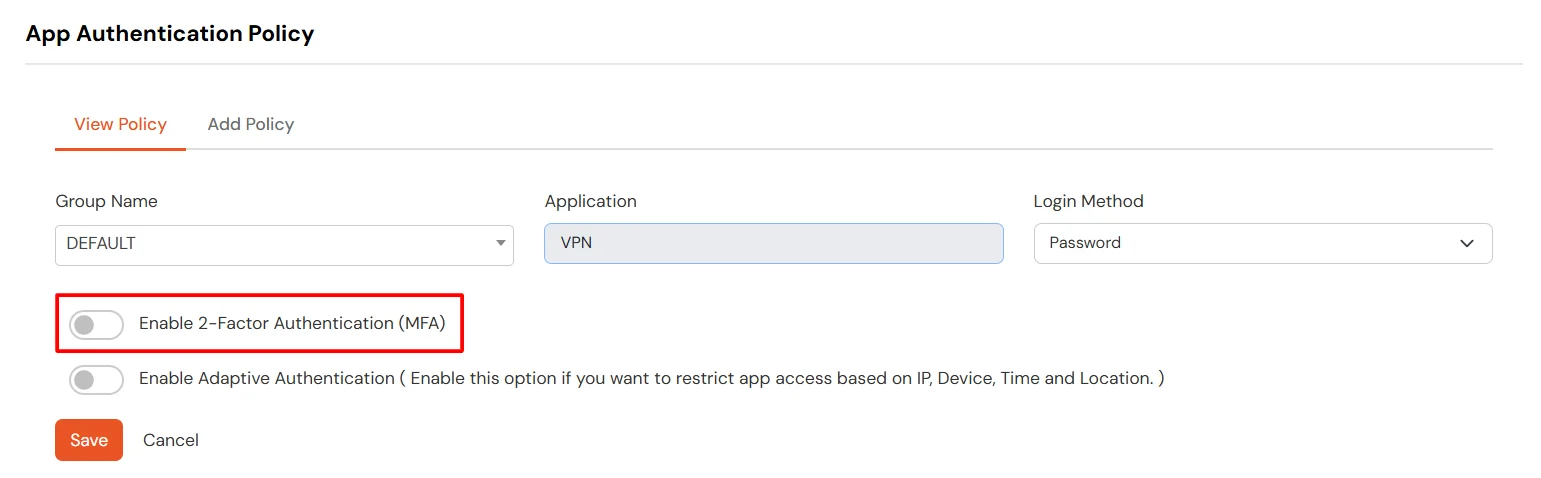
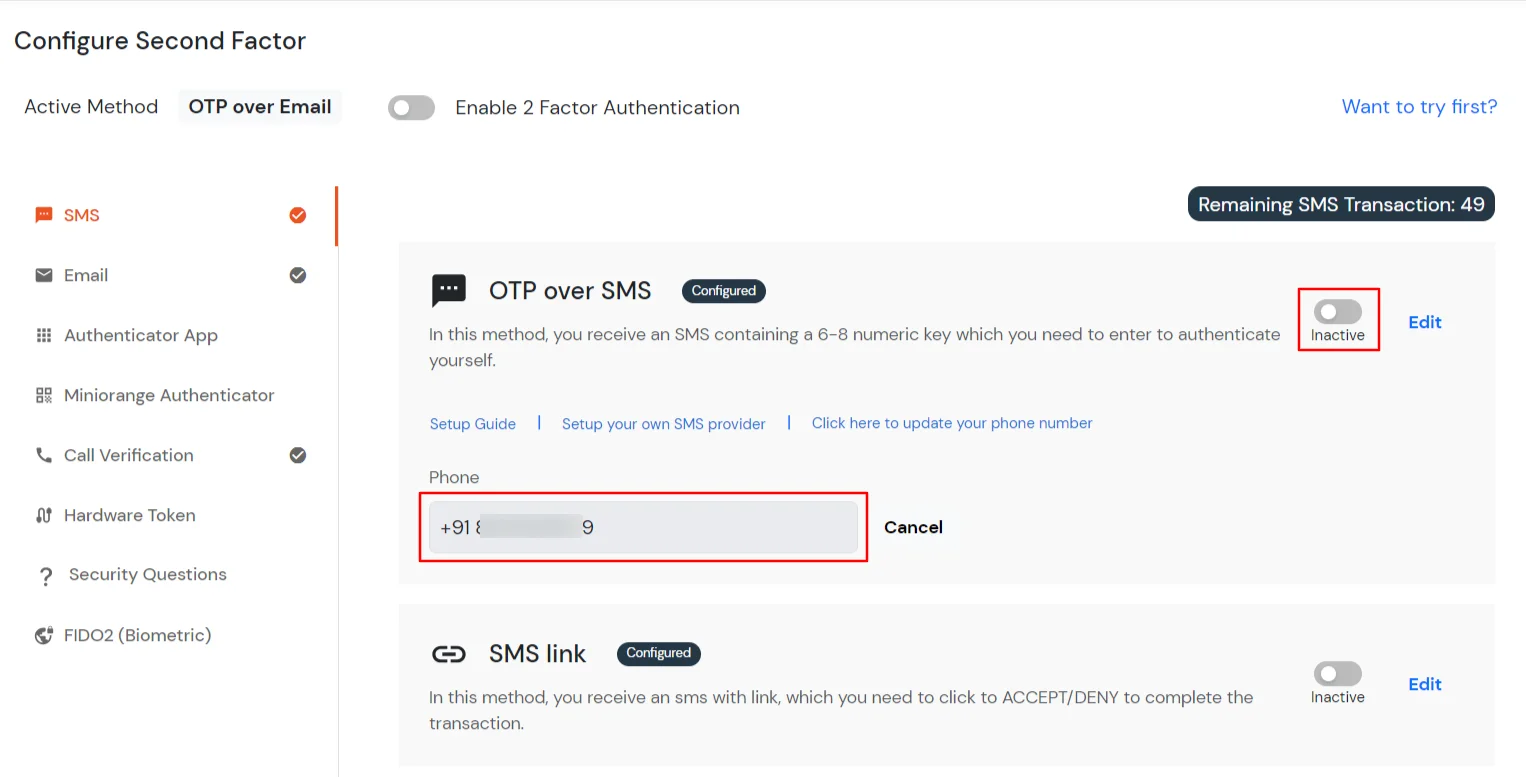
3.2: Configure 2FA for your Endusers
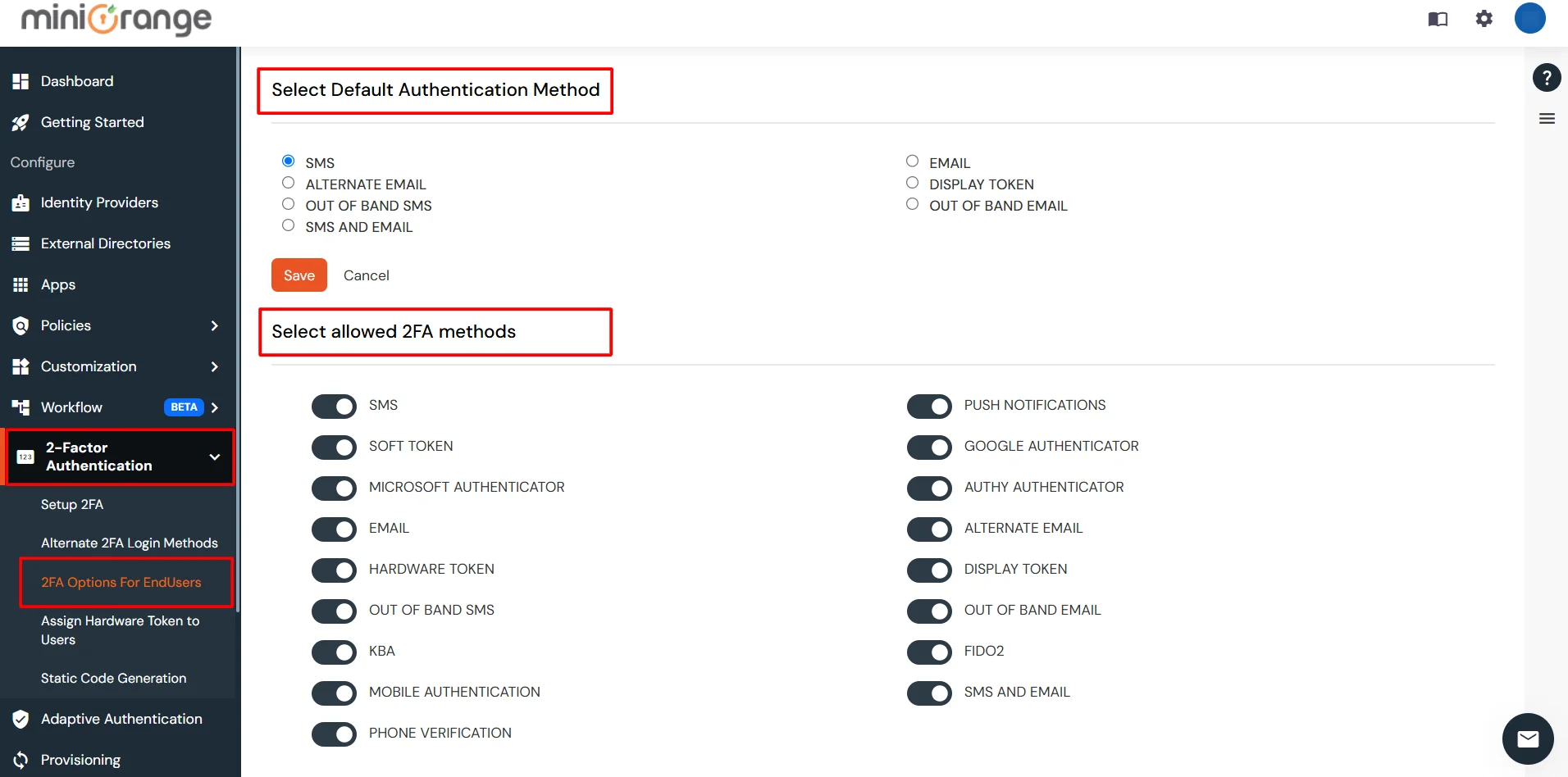
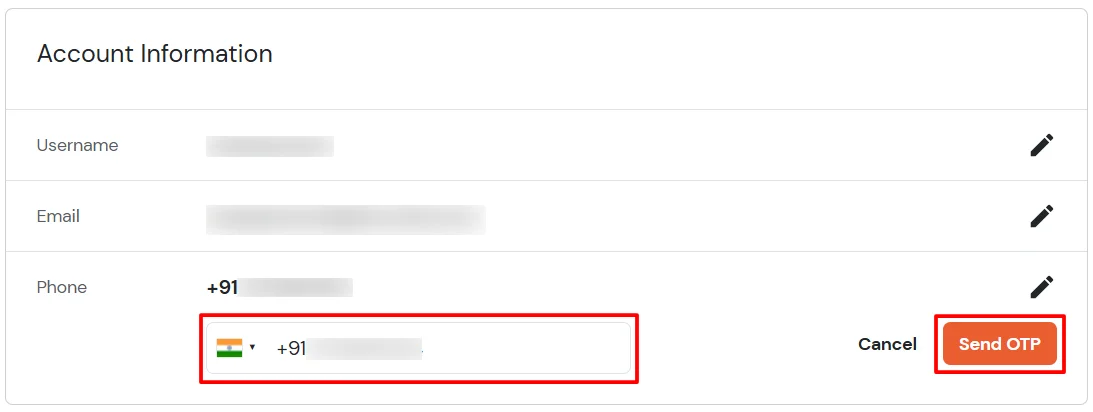
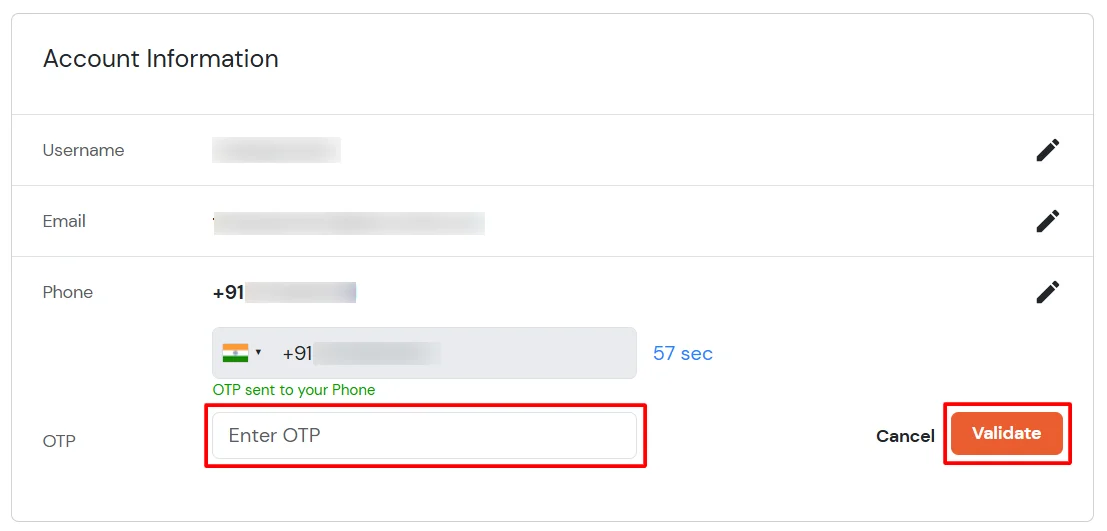
3.3: Enduser 2FA Setup
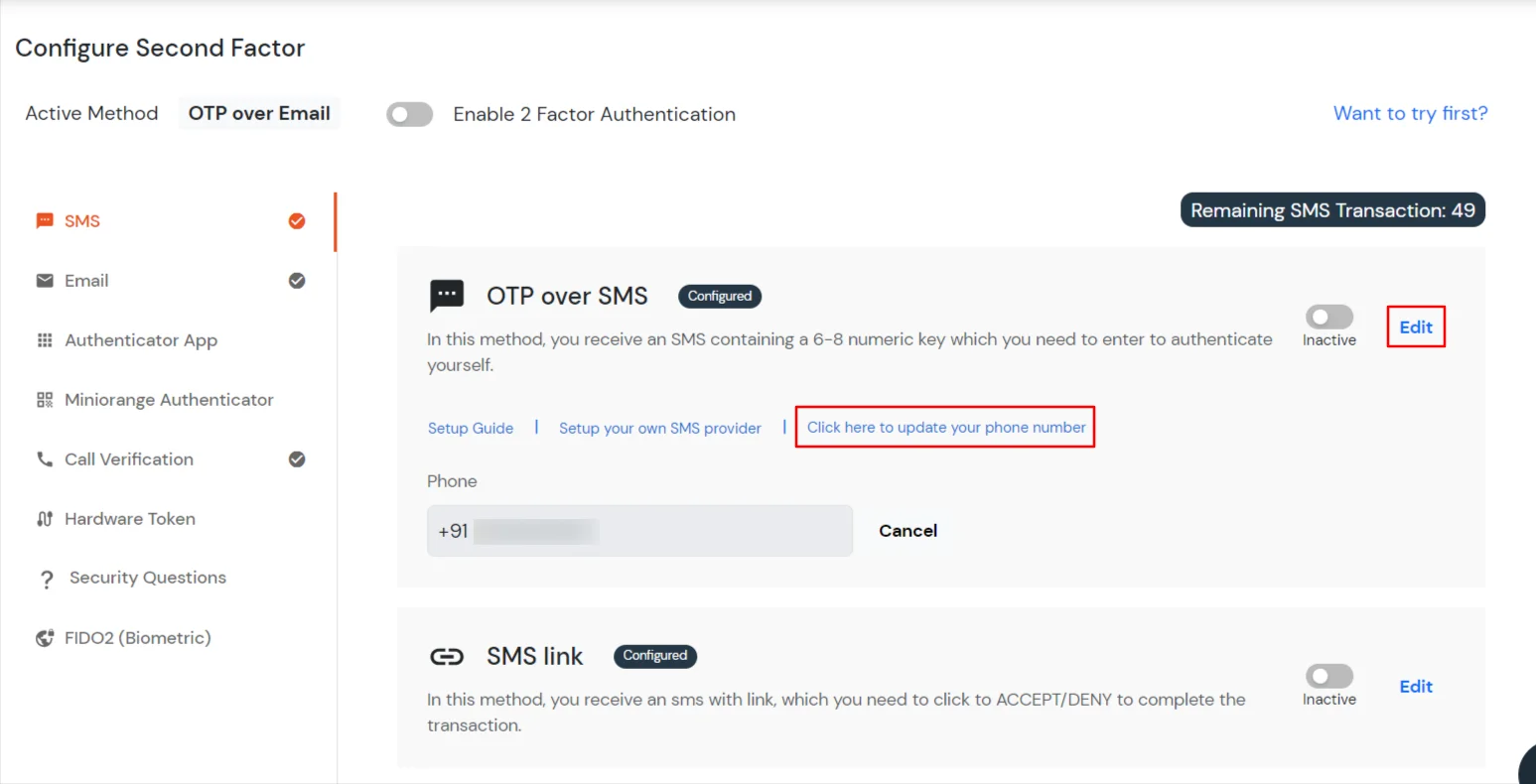

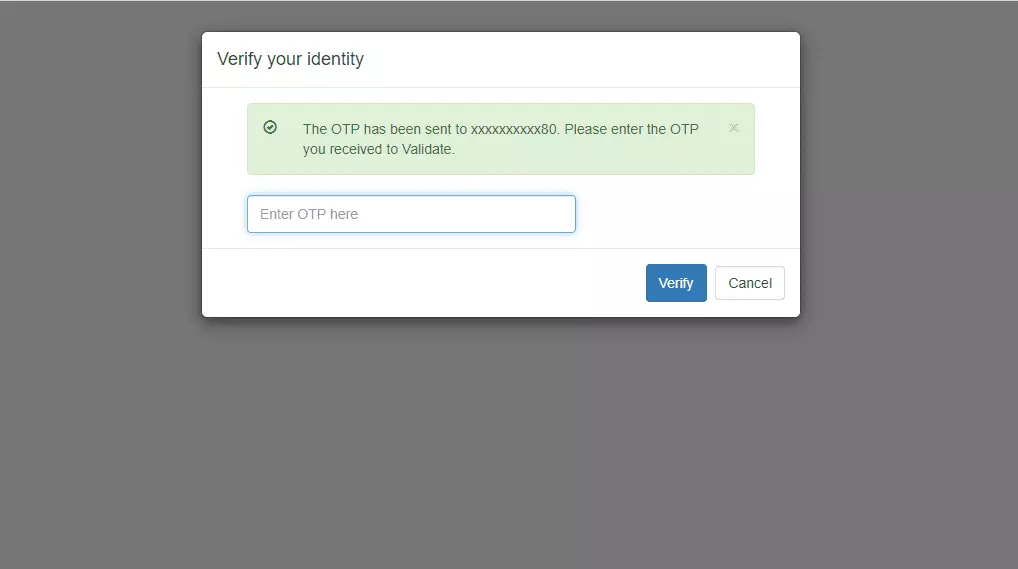
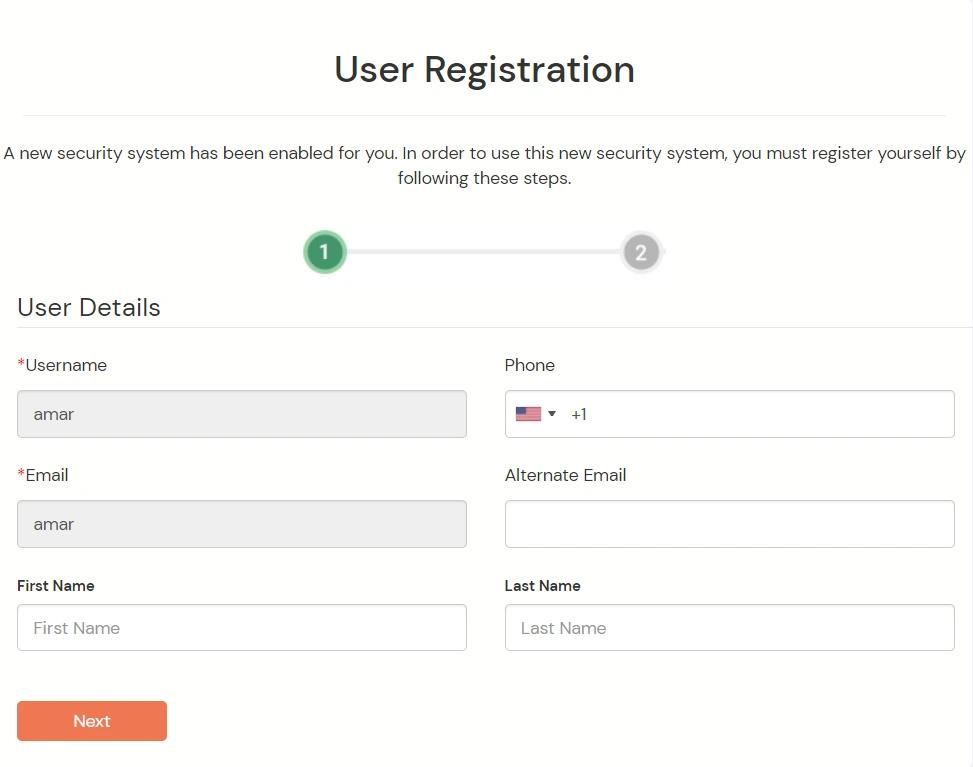
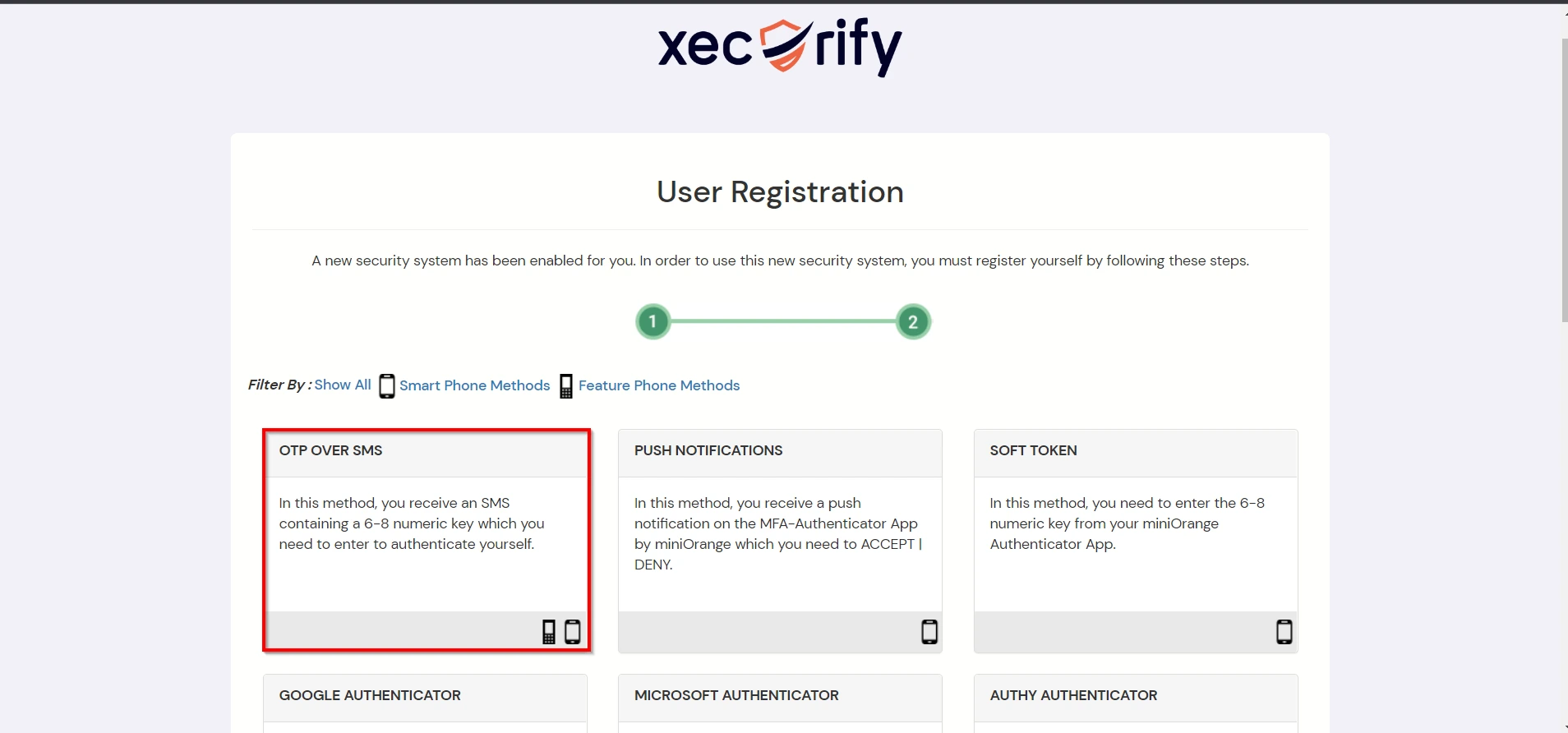
Contact us or email us at idpsupport@xecurify.com and we'll help you setting it up in no time.
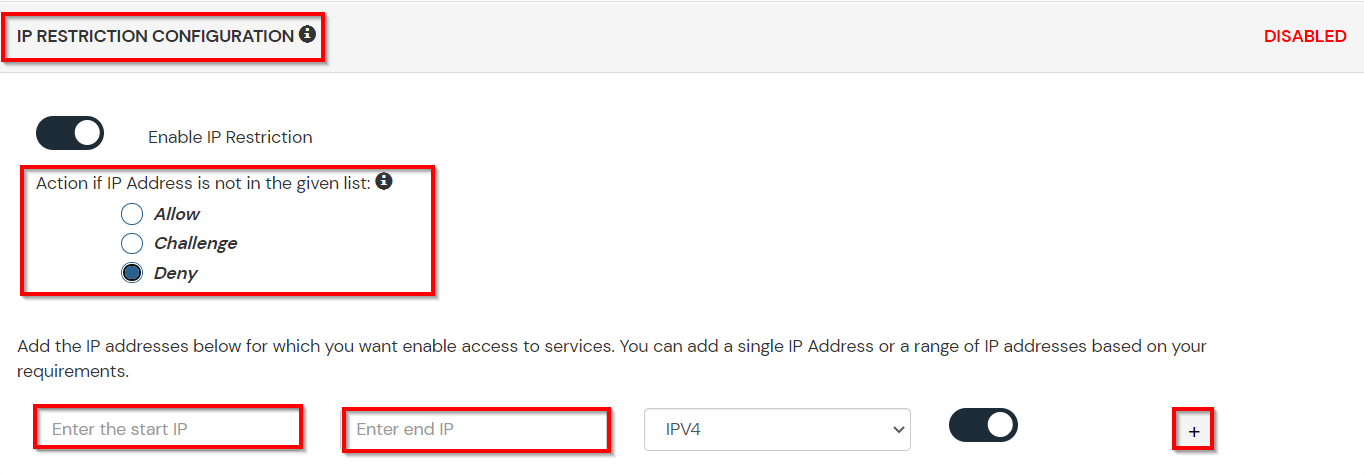
A. Restricting access to Google Workspace (G Suite) with IP Configuration
You can use adaptive authentication with Google Workspace (G Suite) Single Sign-On (SSO) to improve the security and functionality of Single Sign-On. You can allow a IP Address in certain range for SSO or you can deny it based your requirements and you can also challenge the user to verify his authenticity. Adaptive authentication manages the user authentication bases on different factors such as Device ID, Location, Time of Access, IP Address and many more.
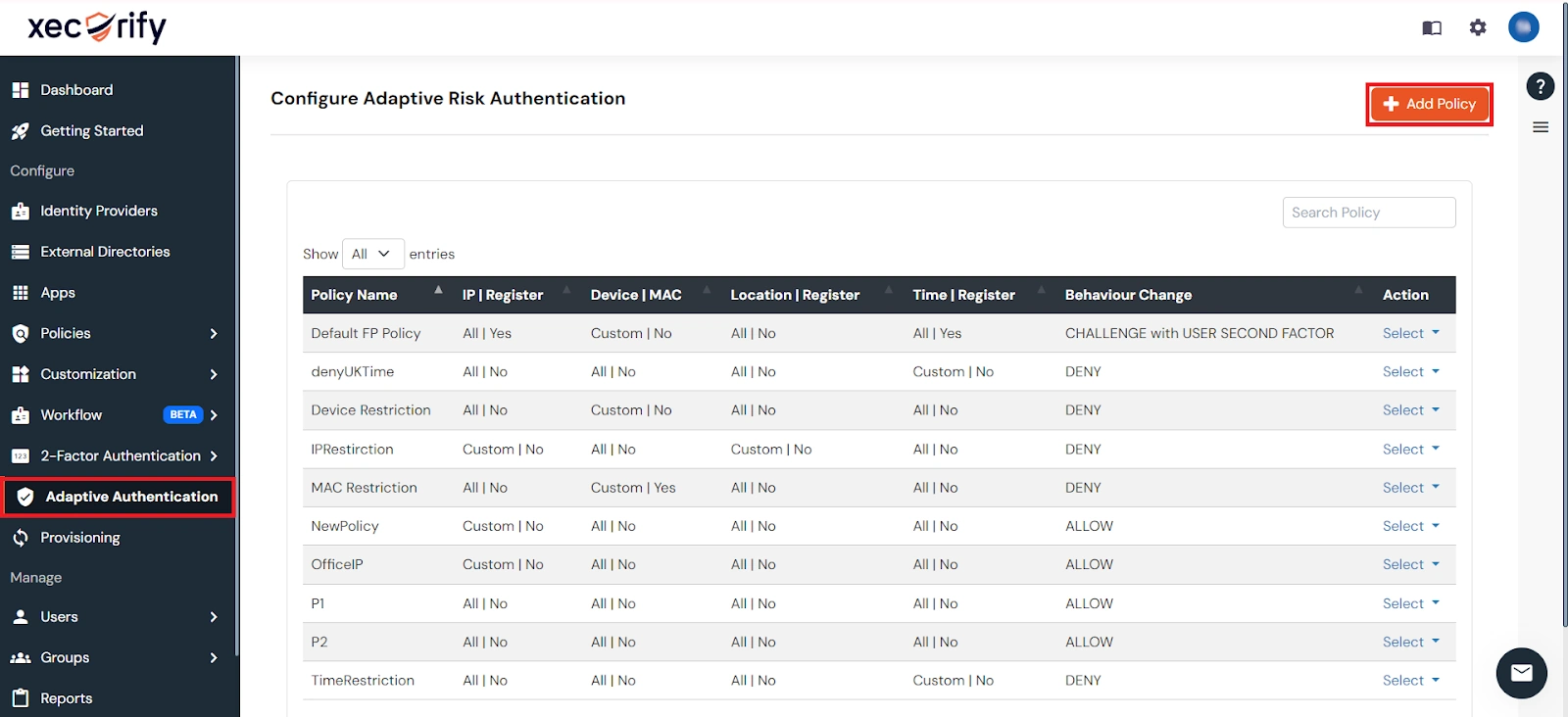
You can configure Adaptive Authentication with IP Blocking in following way :
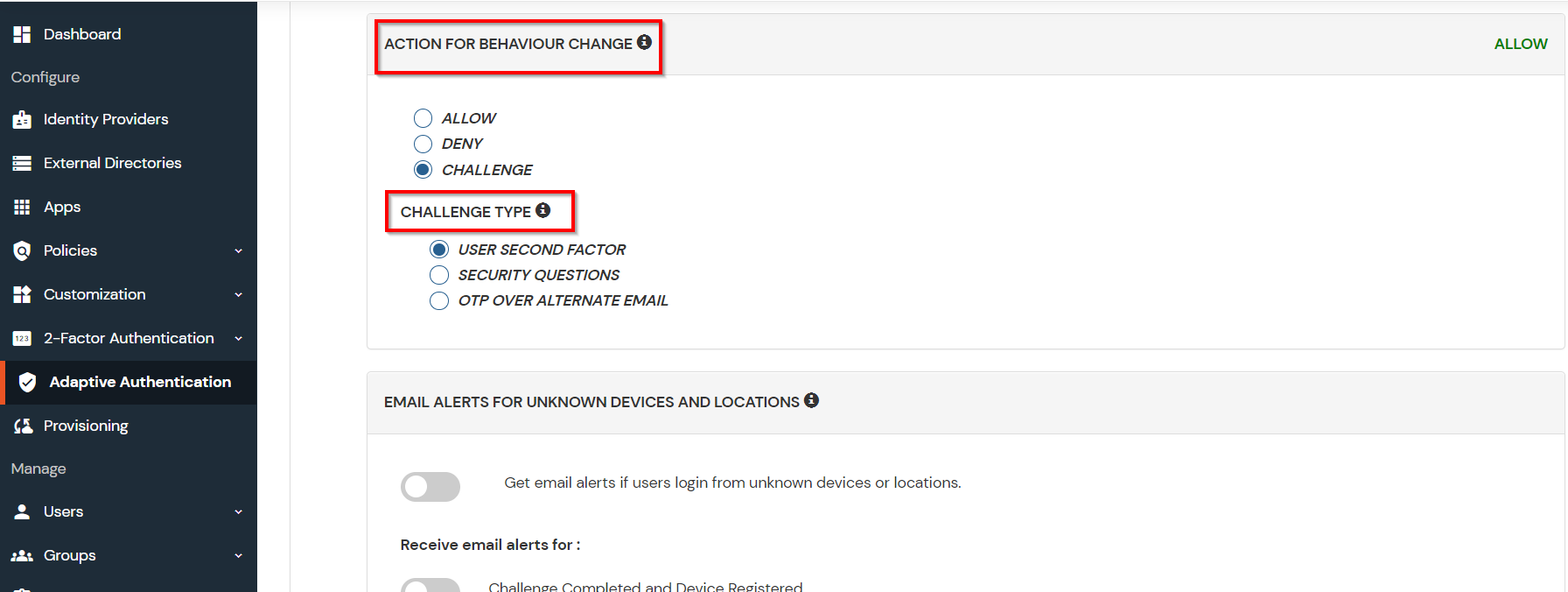
| Attribute | Description |
|---|---|
| Allow | Allow users to authenticate and use services if Adaptive authentication condition is true. |
| Deny | Deny user authentications and access to services if Adaptive authentication condition is true. |
| Challenge | Challenge users with one of the three methods mentioned below for verifying user authenticity. |
| Attribute | Description |
|---|---|
| User second Factor | The User needs to authenticate using the second factor he has opted or assigned for such as
|
| KBA (Knowledge-based authentication) | The System will ask the user for 2 of 3 questions he has configured in his Self-Service Console. Only after the right answer to both questions is the user allowed to proceed further. |
| OTP over Alternate Email | User will receive an OTP on the alternate email they have configured through the Self Service Console. Once the user provides the correct OTP, they are allowed to proceed further. |
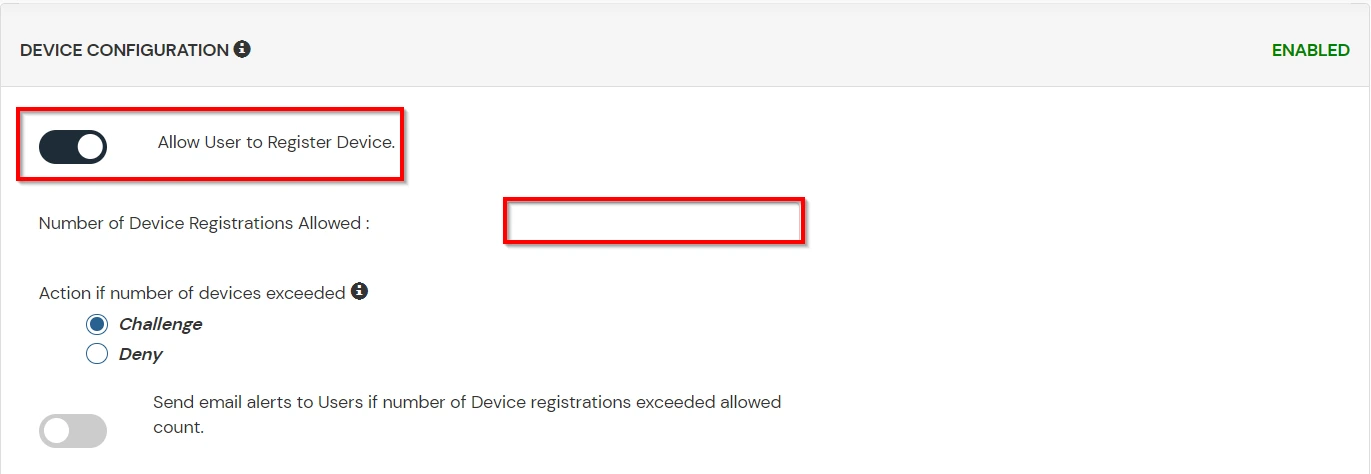
B. Adaptive Authentication with Limiting number of devices
Using Adaptive Authentication you can also restrict the number of devices the end user can access the Services on. You can allow end users to access services on a fixed no. of devices. The end users will be able to access services provided by us on this fixed no. of devices.
You can configure Adaptive Authentication with Device Restriction in following way
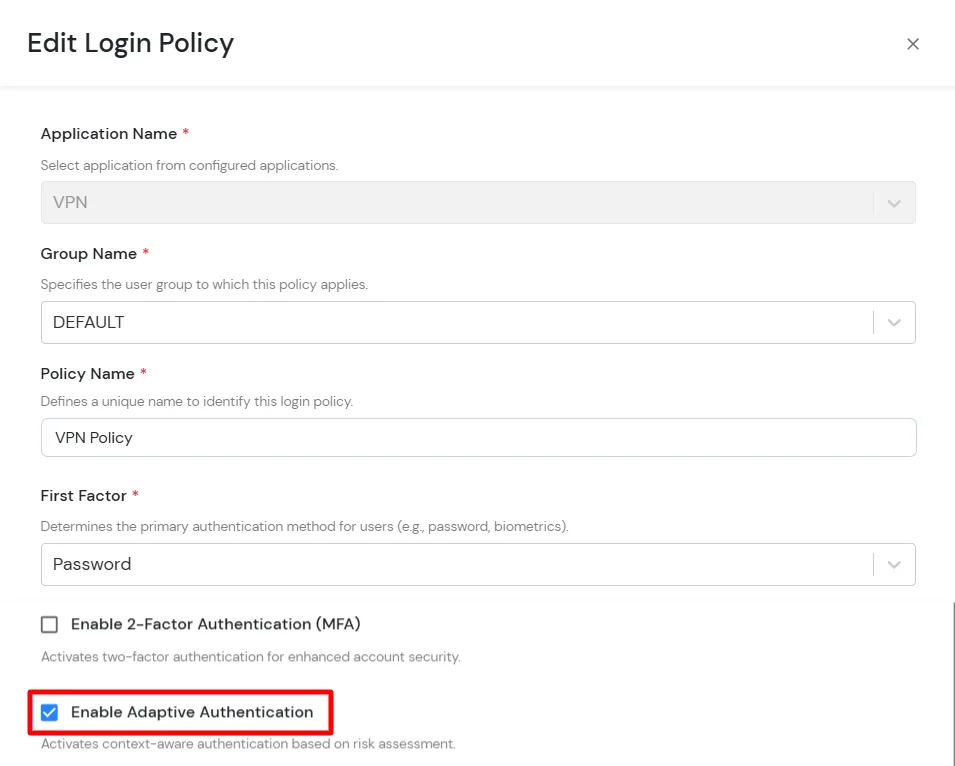
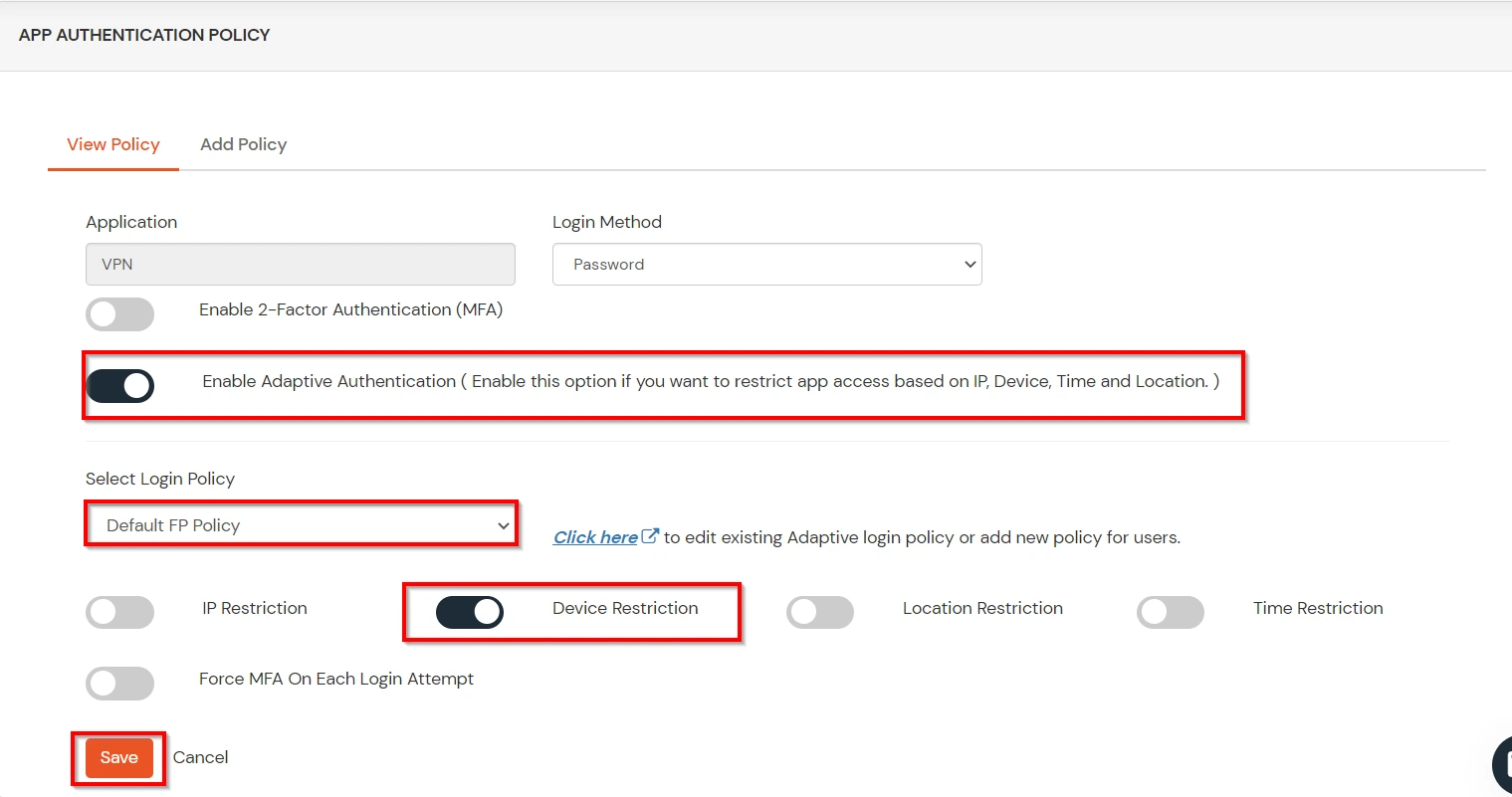
C. Add Adaptive Authentication policy to Google Workspace (G Suite)

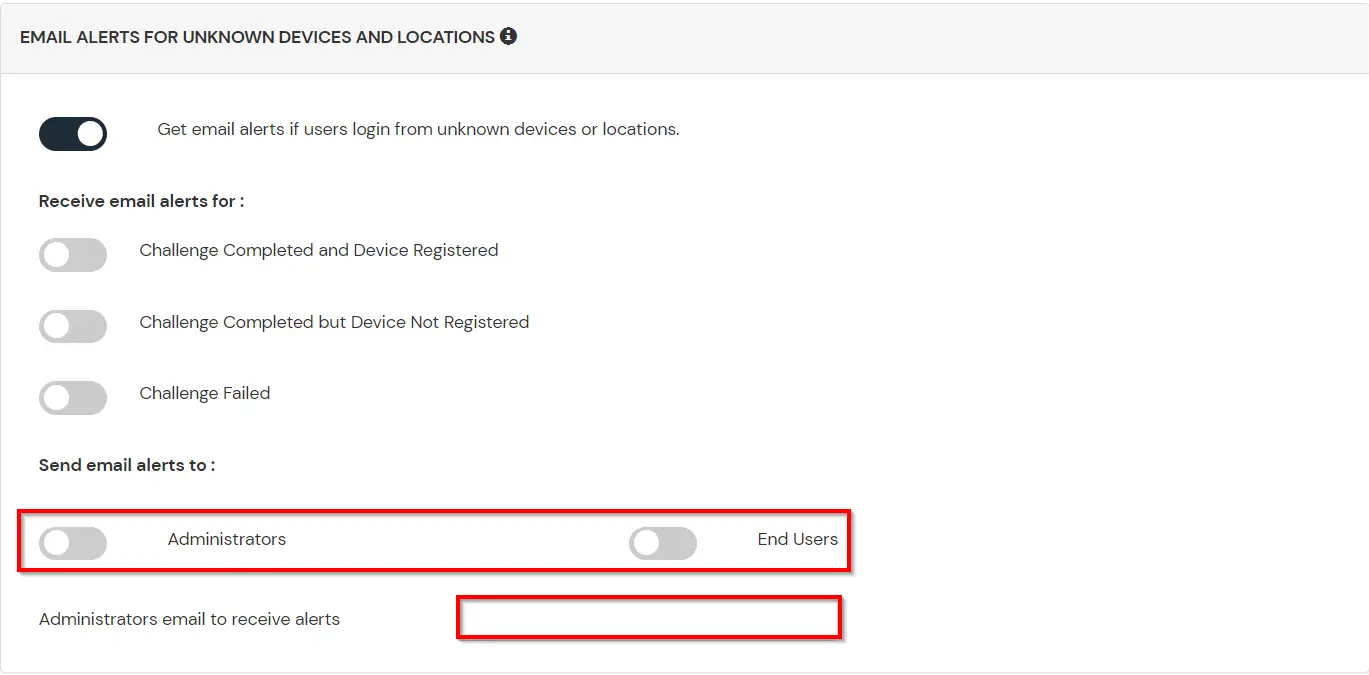
D. Notification and Alert Message.
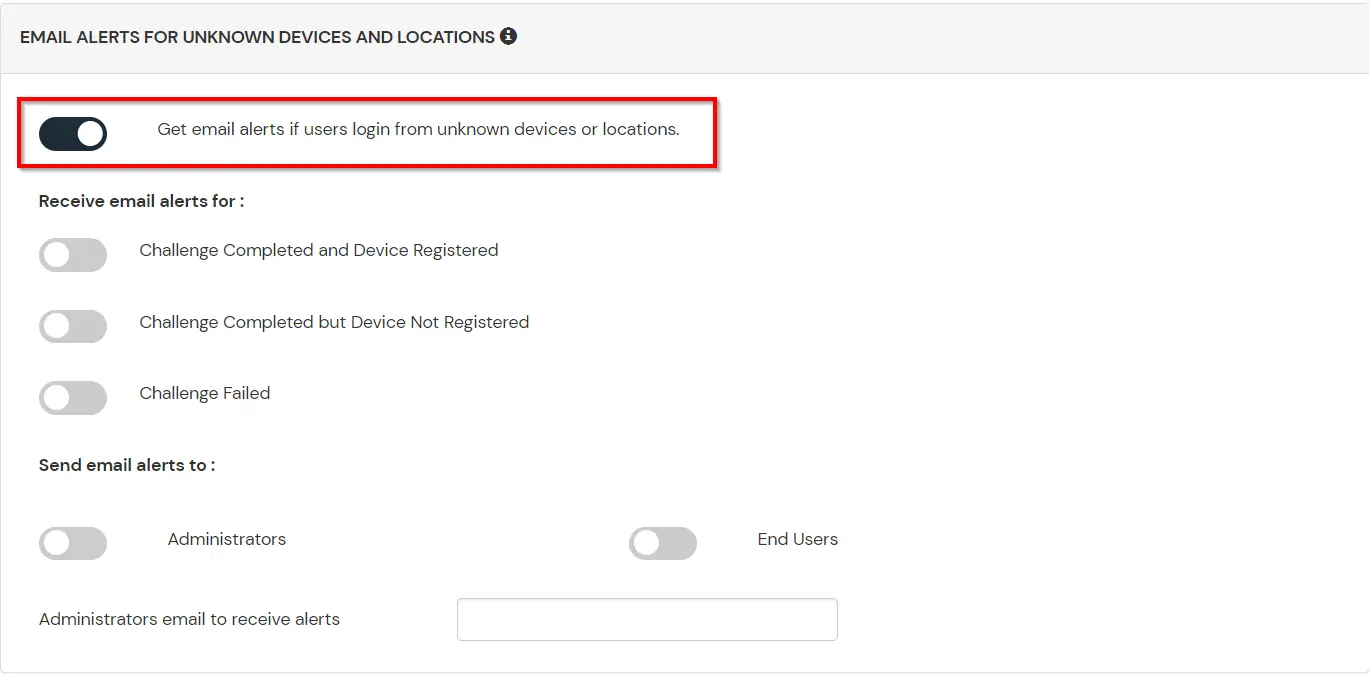
This section handles the notifications and alerts related to Adaptive Authentication. It provides the following options :
| Option | Description |
|---|---|
| Users login from unknown IP addresses, devices or locations | Enabling this option allows you to login from unknown IP addresses or devices and even locations. |
| Number of Device registrations exceeded allowed count | This option will allow you to register more devices than the devices you have numbered. |
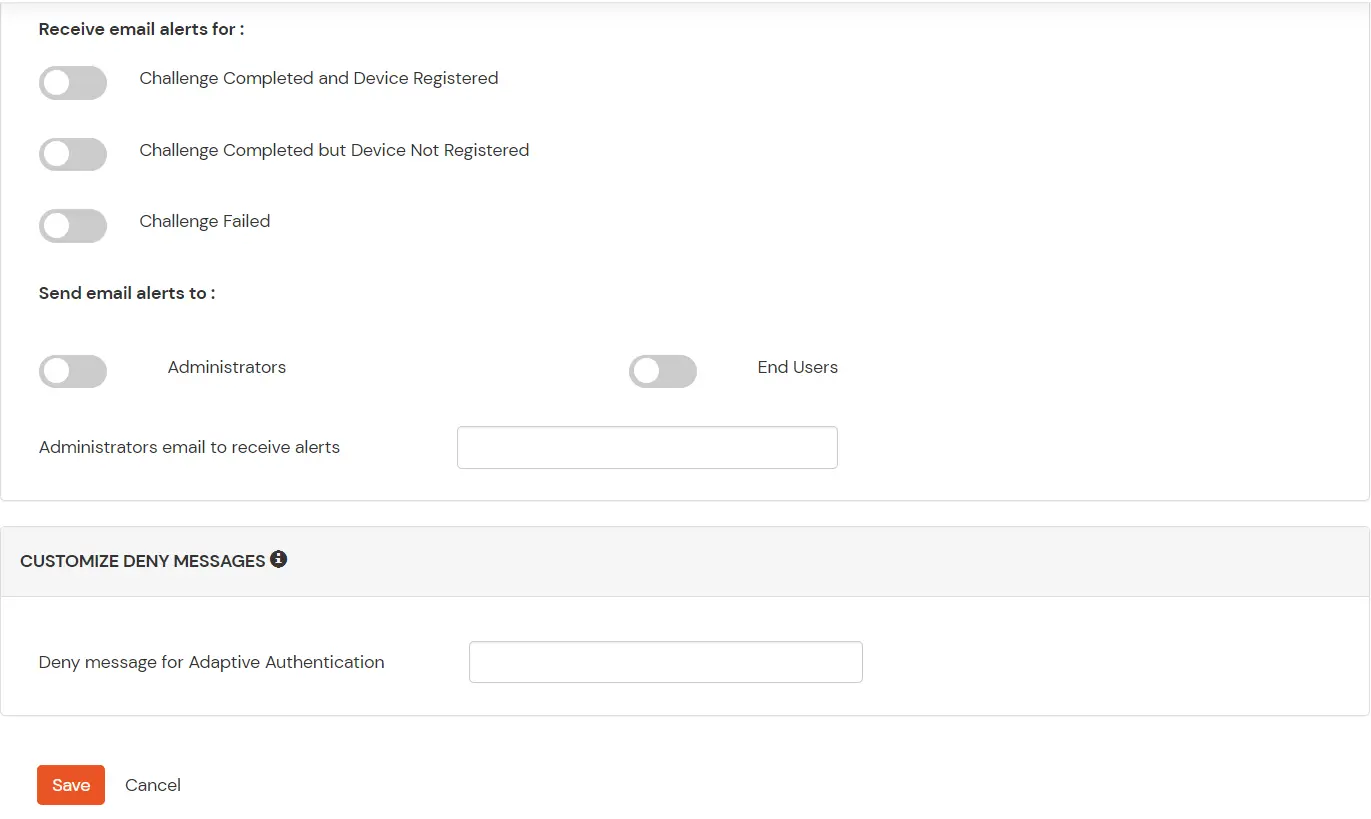
| Challenge Completed and Device Registered | Enabling this option allows you to send an email alert when an end-user completes a challenge and registers a device. |
| Challenge Completed but Device Not Registered | Enabling this option allows you to send an email alert when an end-user completes a challenge but do not registers the device. |
| Challenge Failed | Enabling this option allows you to send an email alert when an end-user fails to complete the challenge. |