How to Setup MFA for Fortinet Fortigate VPN?
Multi-factor authentication or MFA provides an extra authentication layer on the top of your Fortinet Fortigate SSL VPN to provide security to your Fortinet client VPN access. Various authentication methods are available with miniOrange Fortinet FortiGate MFA to secure user account access.
Fortinet VPN provides network security to your user’s systems and brings in safer remote access to your internal network. Two-factor authentication used with Fortinet VPN provides highly reliable security using miniOrange MFA product for safe remote access. RADIUS in Fortinet is used to communicate with miniOrange. Applying FortiClient MFA while setup Fortinet VPN is easy with this detailed guide.
Be Cyber Insurance compliant with miniOrange MFA solution. Read More
Get Free POC - Book a Slot
miniOrange offers free POC and help through a consultation call with our System Engineers to Setup Multi-Factor Authentication for Fortinet VPN in your environment with 30-day trial.
For this, you need to just send us an email at idpsupport@xecurify.com to get free POC and we'll help you setting up our solution in no time.
Get Free POC
miniOrange 2FA/MFA authentication for Fortinet Login
miniOrange accomplishes this by acting as a RADIUS server that accepts the username/password of the user entered as a RADIUS request and validates the user against the user store as Active Directory (AD). After the first level of authentication, miniOrange prompts the user with 2-factor authentication and either grants/revokes access based on the input by the user.
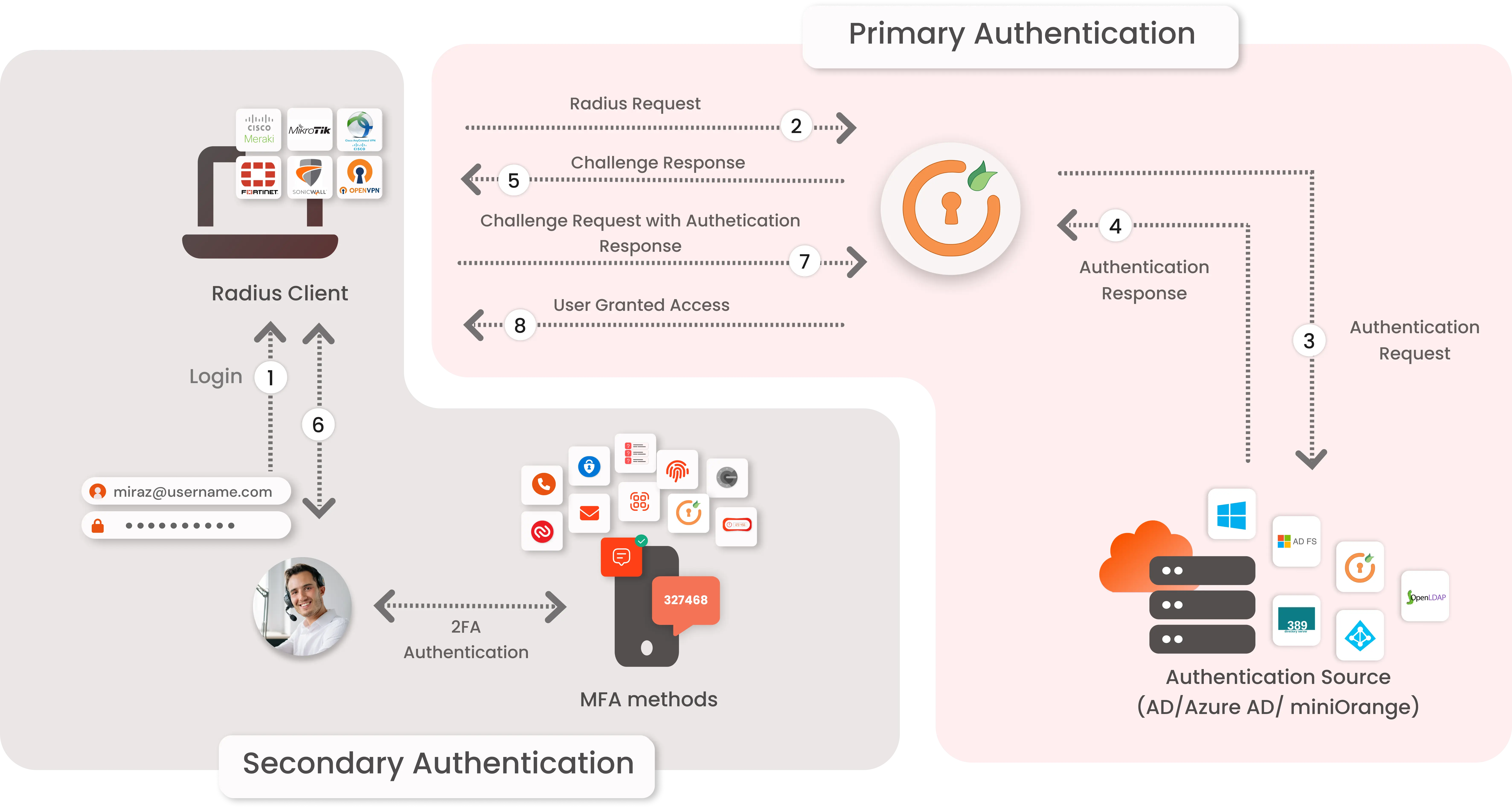
- Primary authentication initiates with the user submitting his Username and Password for Fortinet.
- User request acts as an authentication request to RADIUS Server(miniOrange).
- miniOrange RADIUS server passes user credentials to validate against the credentials stored in AD (Active Directory) / Database.
- Once the user's first level of authentication gets validated AD sends the confirmation to RADIUS Server.
- Now miniOrange RADIUS Server asks for a 2-factor authentication challenge to the user.
- Here user submits the response/code which he receives on his hardware/phone.
- User response is checked at miniOrange’s RADIUS Server side.
- On successful 2nd factor authentication the user is granted access to login.
Connect with any External Directories
miniOrange provides user authentication from various external directories such as miniOrange Directory, Microsoft AD, Microsoft Entra ID/LDAP, AWS Cognito and many more.
Can't find your Directory? Contact us on idpsupport@xecurify.com
Enable Multi Factor Authentication 2FA/MFA for Fortinet
1. Configure Fortinet in miniOrange
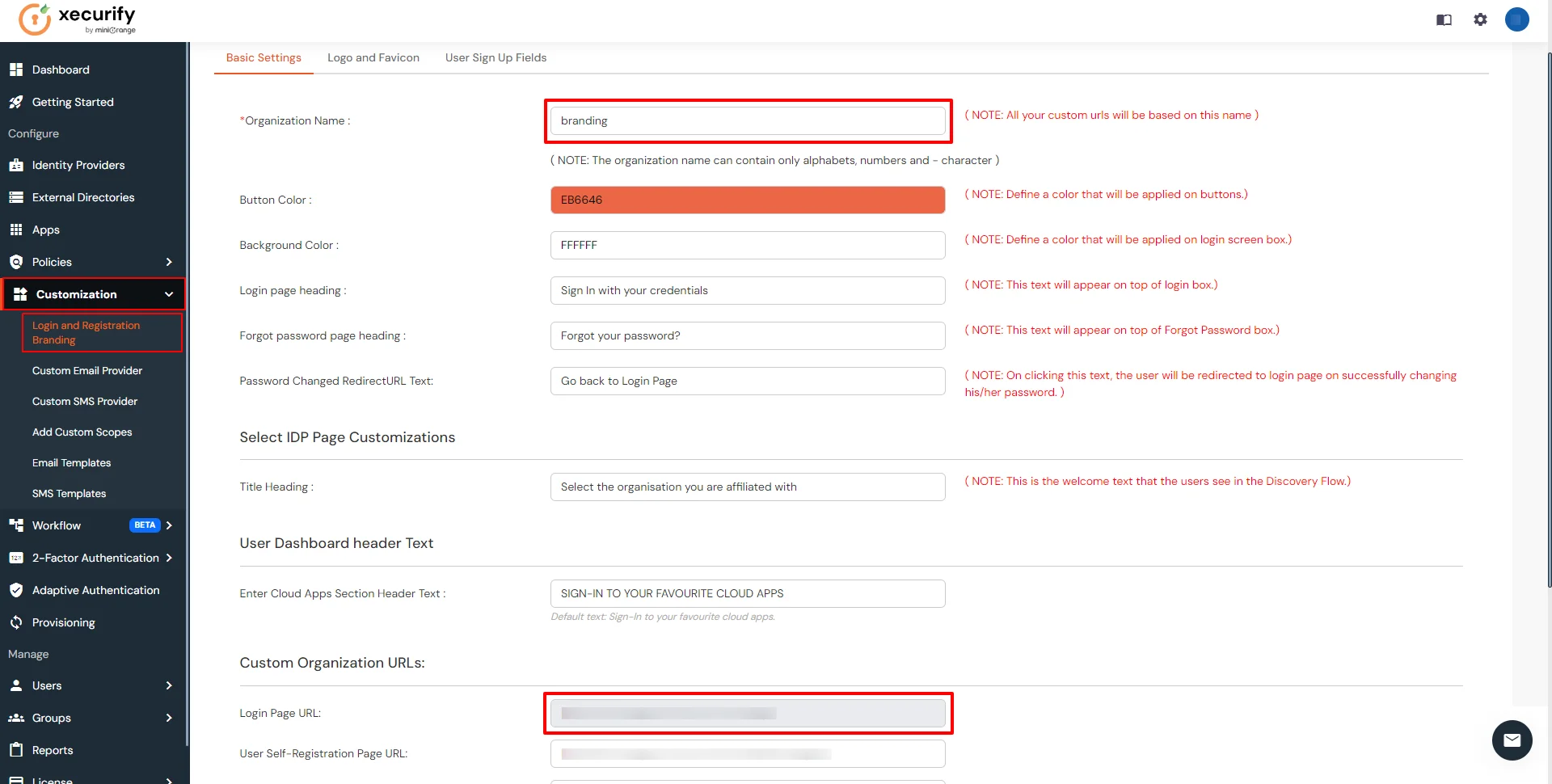
- Login into miniOrange Admin Console.
- Click on Customization >> Login and Registration Branding in the left menu of the dashboard.
- In Basic Settings, set the Organization Name as the custom_domain name.
- Click Save. Once that is set, the branded login URL would be of the format https://<custom_domain>.xecurify.com/moas/login
- Go to Apps, and click on Add Application button.

- In Choose Application, select RADIUS (VPN) from the application type dropdown.
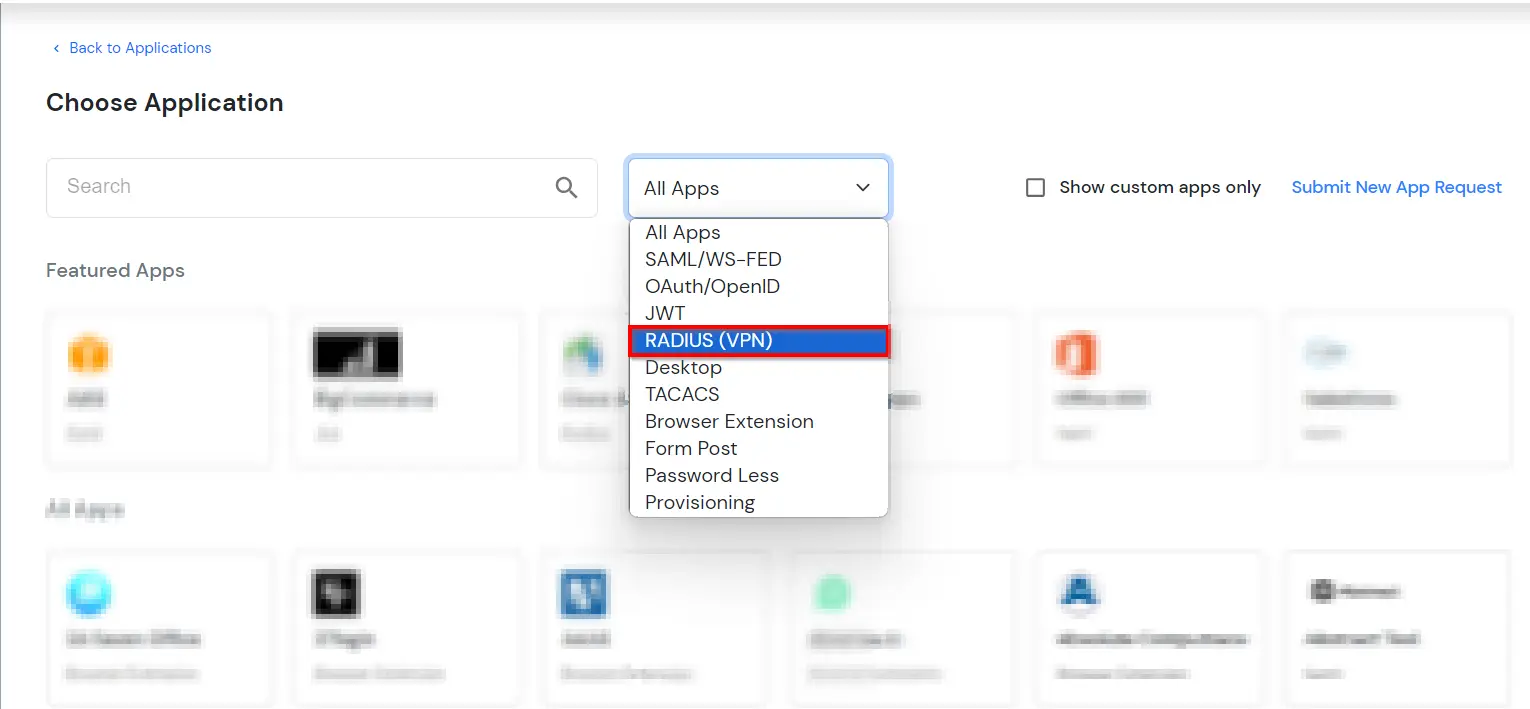
- Click on Fortinet application tab. If you don't find your application click on Radius Client application tab.
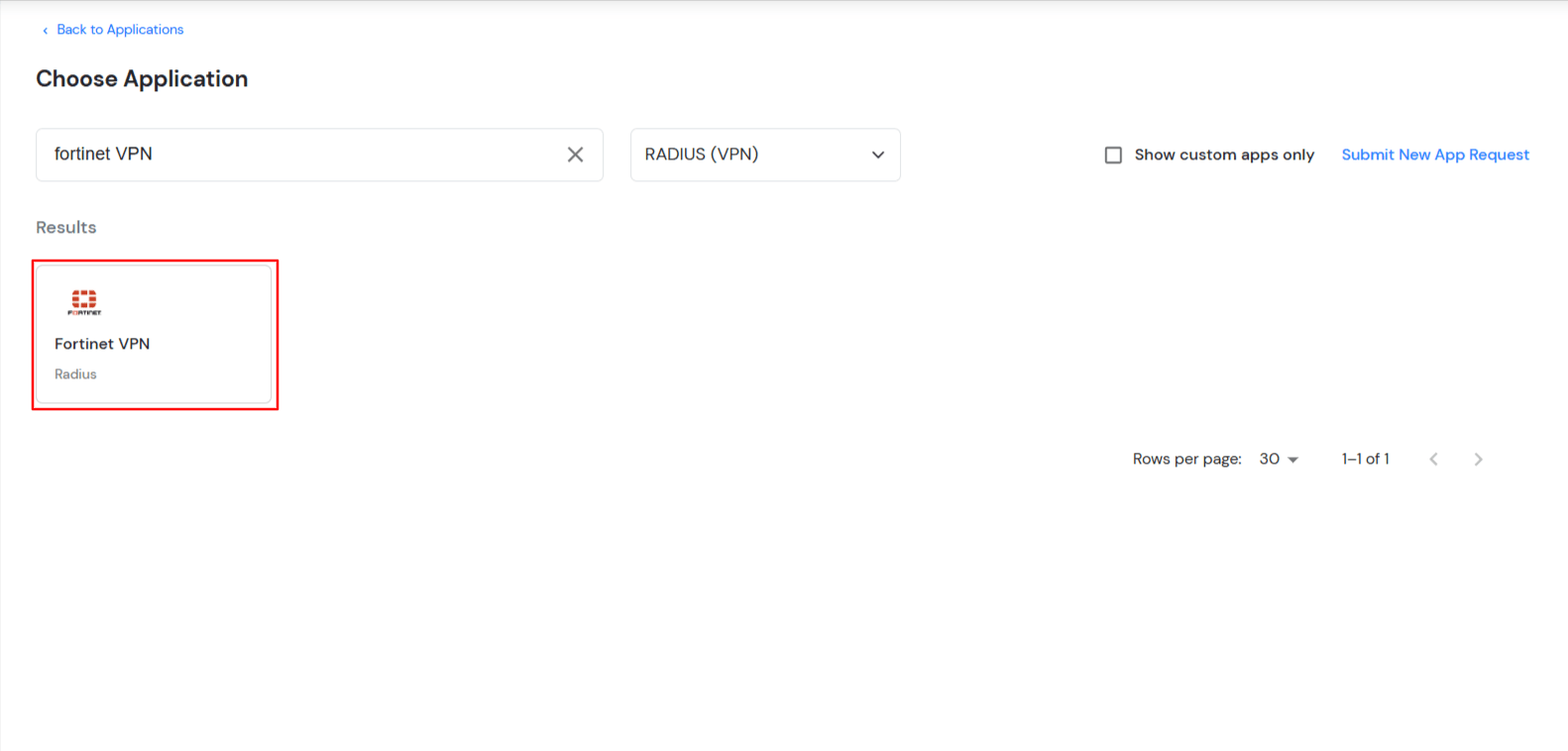
- Click on "View RADIUS IPs" to get the Radius server IPs.
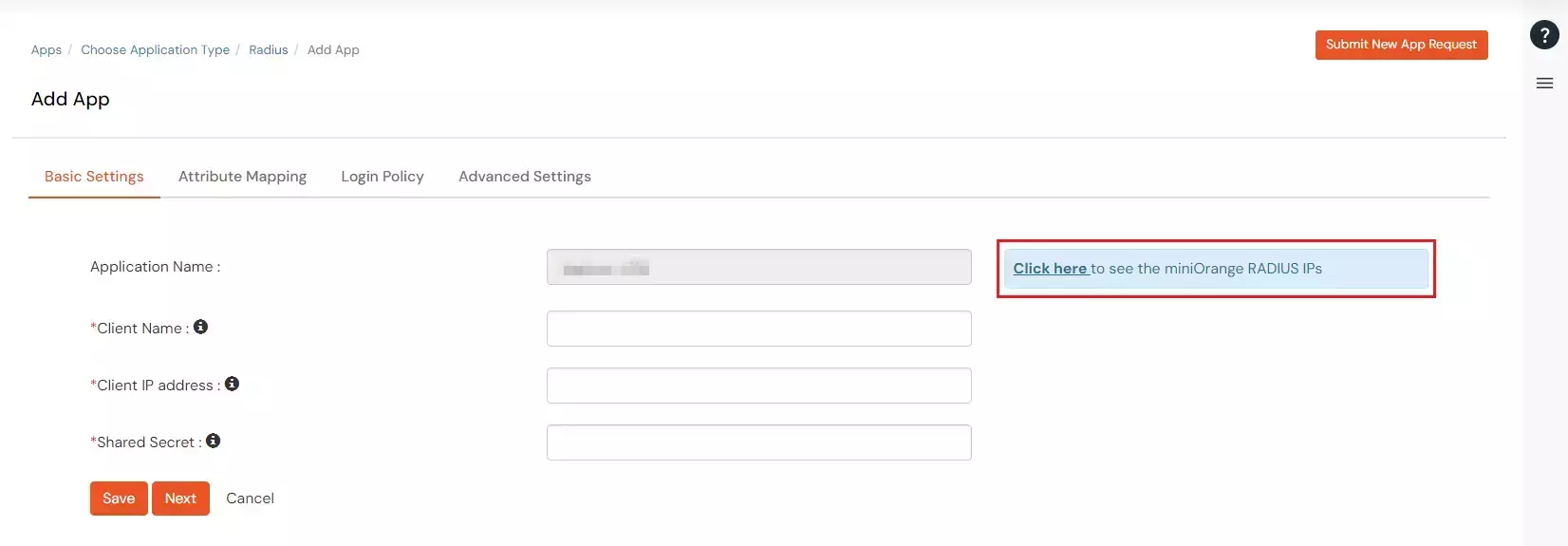
- Copy and save the Radius server IP which will be required to configure your Radius client.
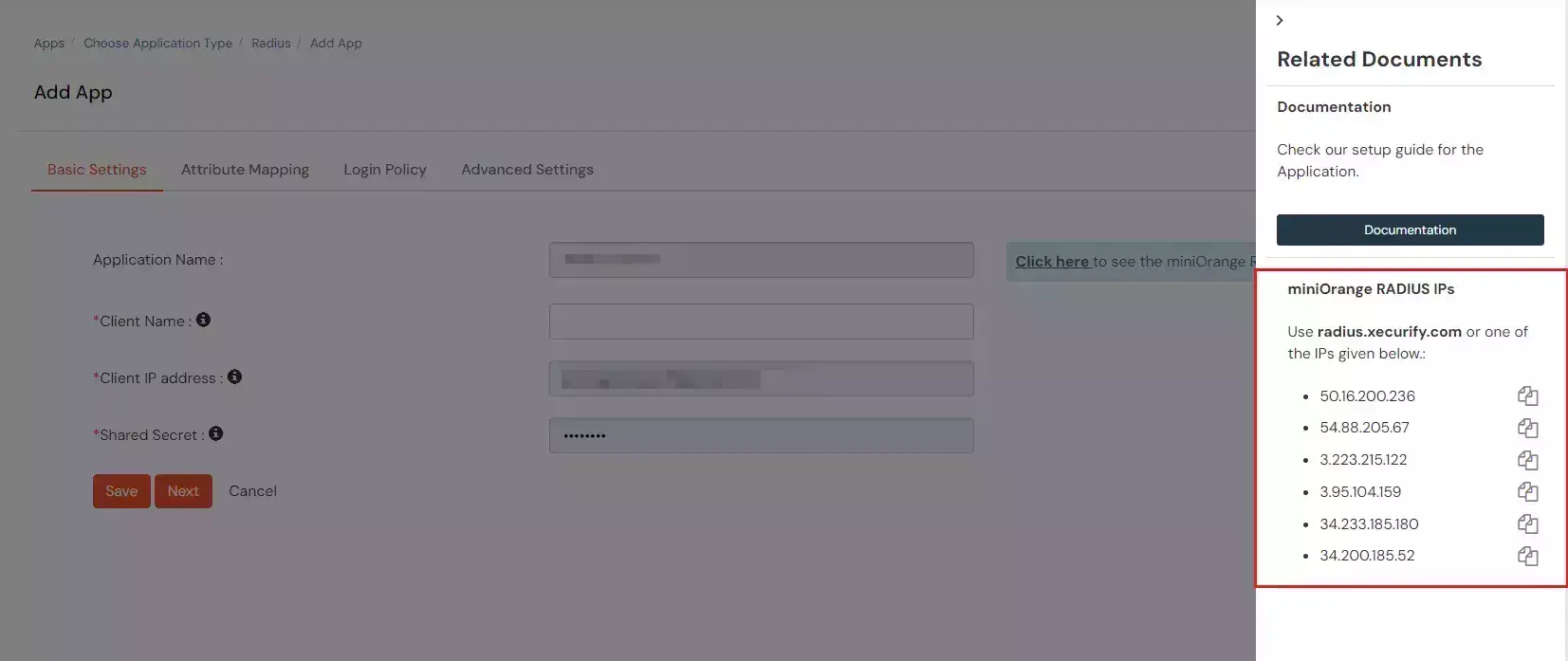
- Configure the below details to add Radius Client.
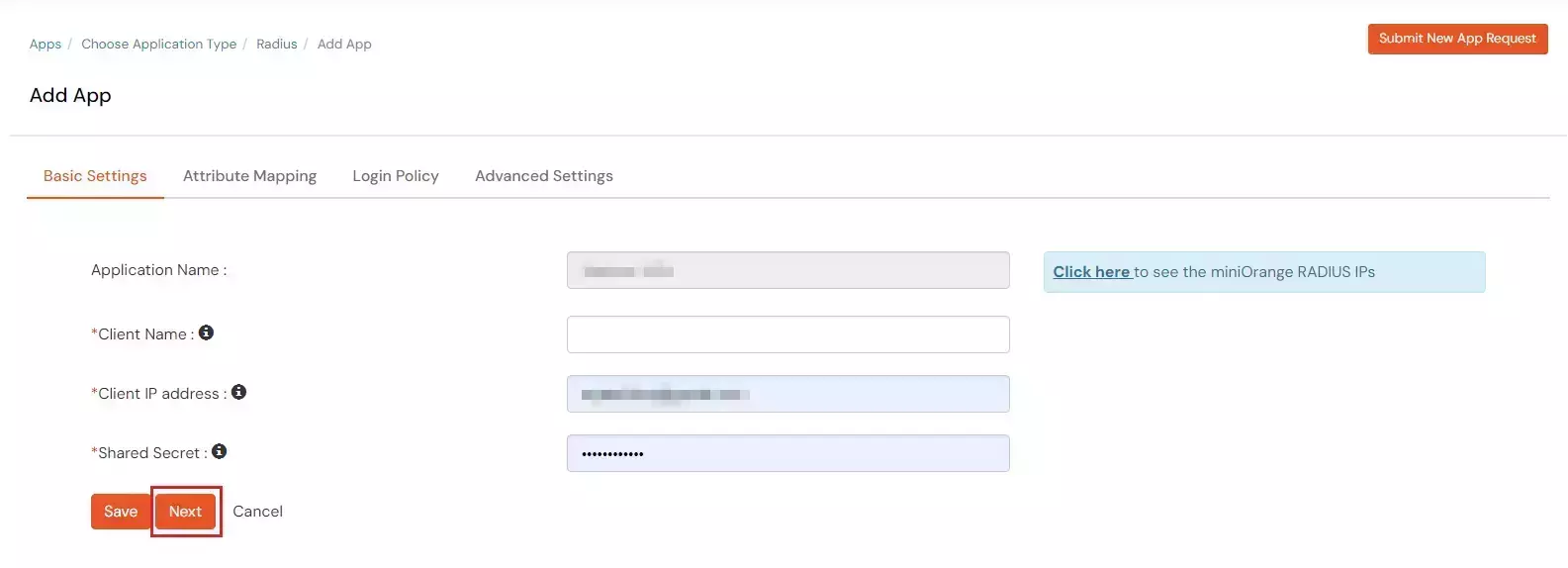
| Display Name: |
Any name for your reference. |
| Client IP: |
IP address of VPN server which will send Radius authentication request. |
| Shared Secret: |
Security key.
For Eg. "sharedsecret"
(Keep this with you, you will need to configure same on VPN Server). |
- Click Next.
- Under the Attribute Mappings tab, enable the toggle if you want to Send Custom Attributes in response.
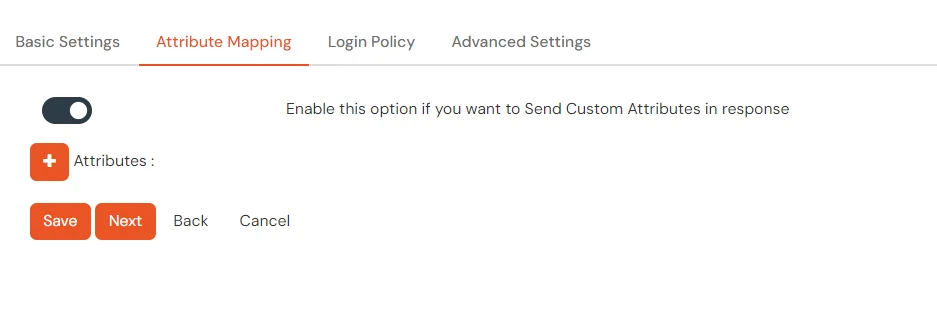
- To send groups in response, you can refer the below table for Vendor group attributes id.
| Vendor Name |
Vendor Attribute |
Value Type |
Attribute |
| Cisco ASA |
ASA-Group_policy |
User |
Groups |
| Fortinet |
Fortinet-Group-Name |
User |
Groups |
| Palo Alto |
PaloAlto-user-Group |
User |
Groups |
| SonicWall |
Sonicwall-user-group |
User |
Groups |
| Citrix |
Citrix-user-groups |
User |
Groups |
| Default(Can be used if your vendor is not in the list) |
Filter-Id |
User |
Groups |
- Value Type and Attribute can be changed based on the requirement.
- Click on Next to proceed.
- Navigate to Policies tab, and click on Add Policy button.
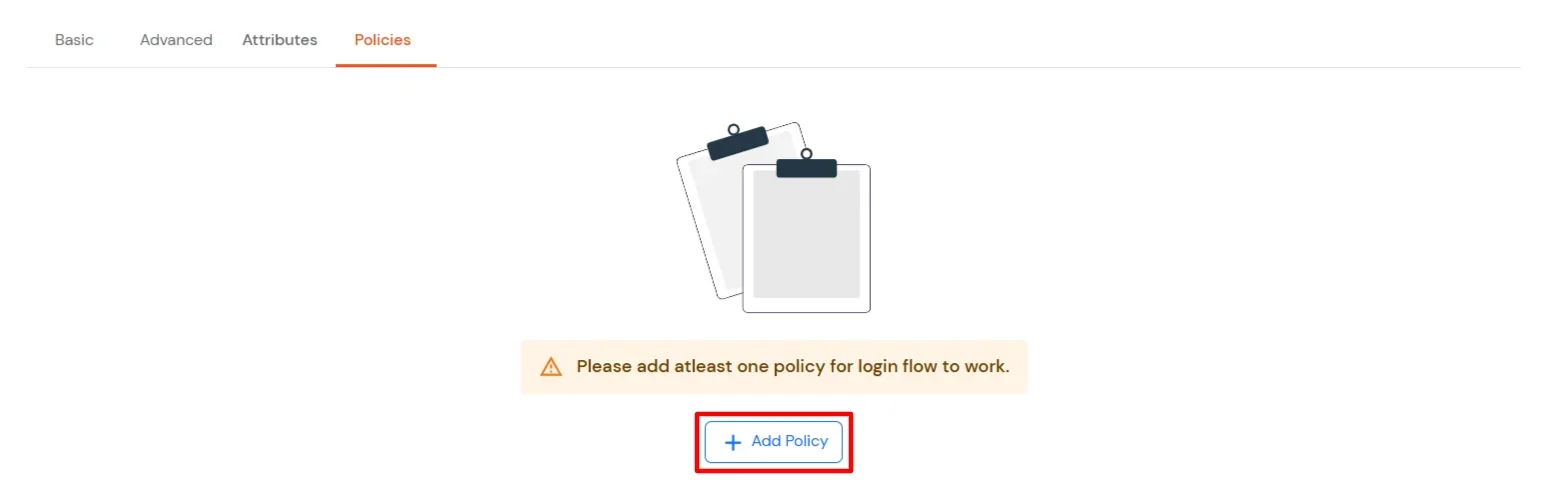
- Configure the following Policy details for the Radius Client.
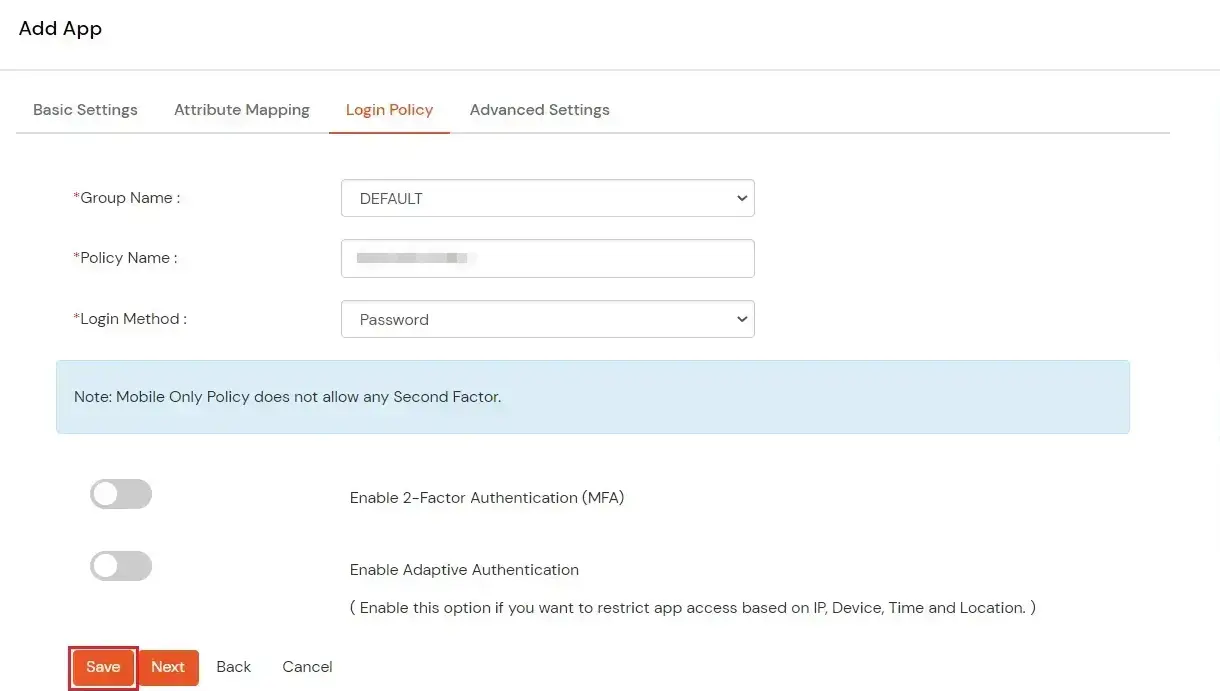
| Group Name: |
Group for which the policy will apply. |
| Policy Name: |
Any Identifier that specifies policy name. |
| First Factor |
Login Method for the users associated with this policy. |
| Enable 2-Factor Authentication |
Enables Second Factor during Login for users associated with this policy. |
| Enable Adaptive Authentication |
Enables Adaptive Authentication for Login of users associated with this policy. |
- After configuring the given above details, Click on Submit button.
Note: You can follow
this guide, if you want to configure Radius MFA using MSCHAPv2 protocol.
NOTE: For On-Premise version follow the below steps before testing the connectivity.
Only For On-Premise Version
Open Firewall Ports.
- In order to receive the RADIUS request, it is necessary to open UDP traffic on ports 1812 and 1813 for the machine where On-Premise IdP is deployed.
- If the hosting machine is a Windows Machine then you can follow this document.
- If the hosting machine is a Linux Machine then you can follow this document.
NOTE: If your machine is hosted on AWS, then enable the ports from the AWS panel.
2. Configure RADIUS in Fortinet
- Login to Fortinet FortiGate Admin console for the VPN application.
- Go to User & Device >> RADIUS Servers in left navigation bar and click on Create New.
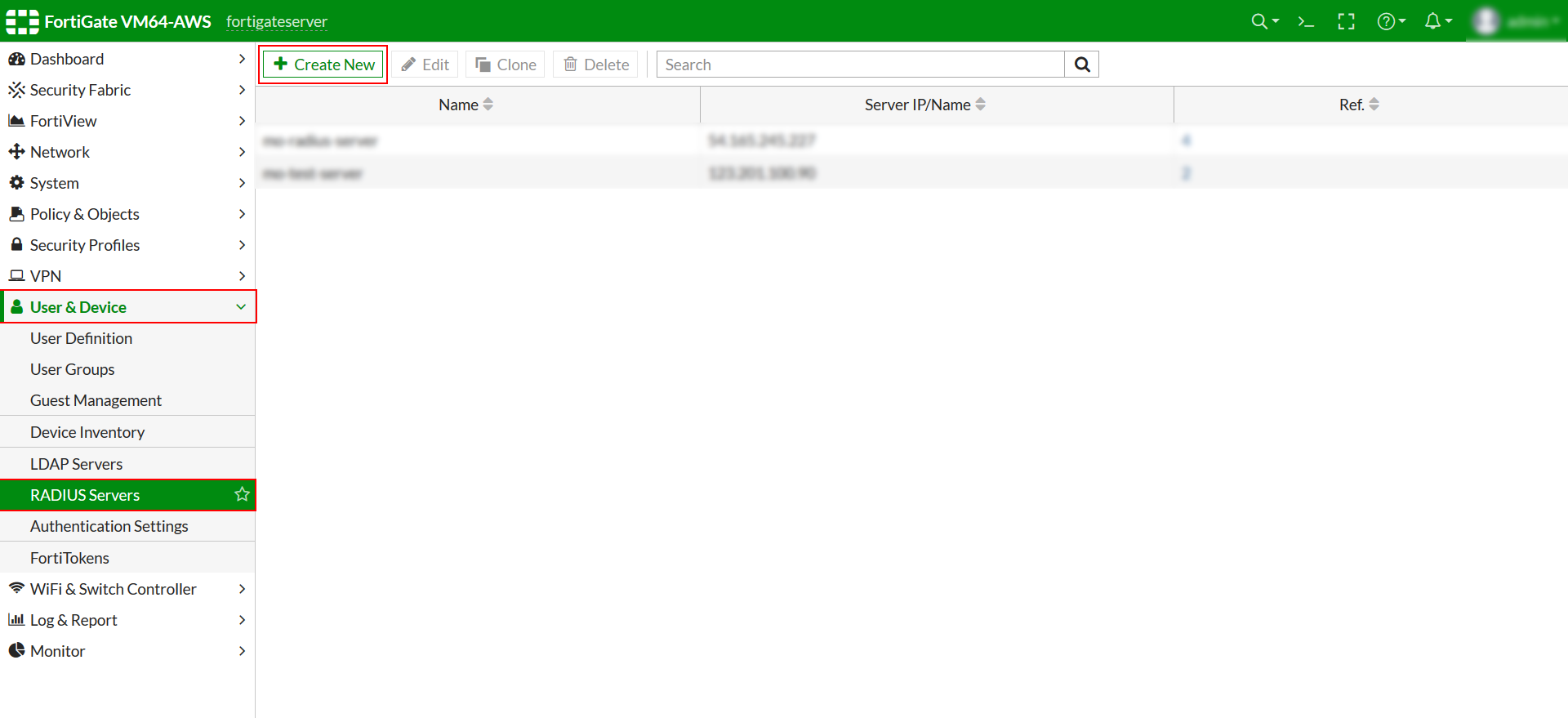
- Here you need to configure the RADIUS Server.
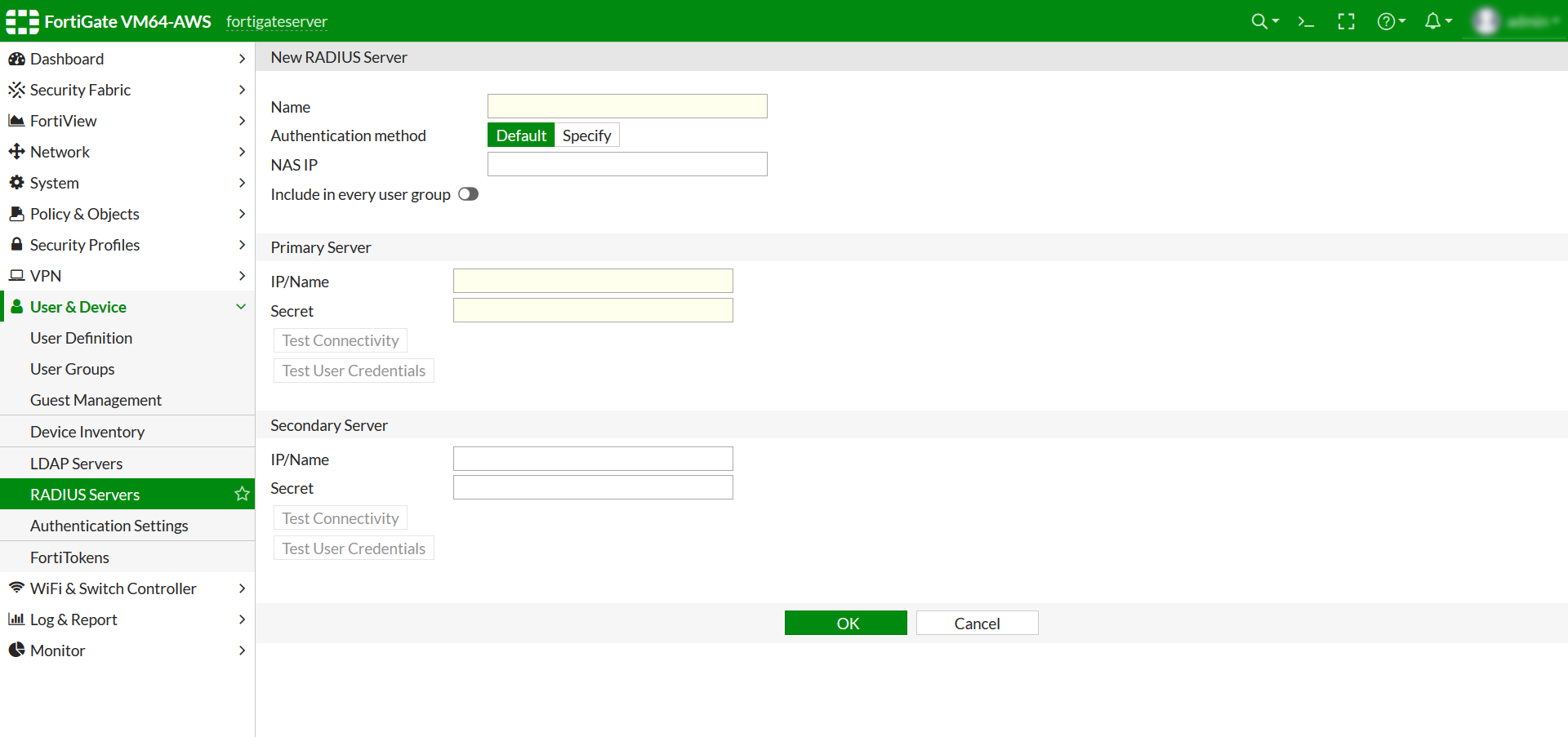
- Configure details below to add Radius Server.
| Name |
Appropriate nameEg: mo-radius-server |
| Authentication Method |
Click on Specify and then select PAP in the Dropdown. |
| Primary Server IP / Name |
For on-premise version: IP of server where IDP(miniOrange) is installed
For cloud version: Use the Radius Server IPs which you got from Step1.
|
| Primary Server Secret |
Secret Key for the Fortinet (RADIUS) App defined in step 1 |
| Secondary Server IP / Name |
Optional |
| Secondary Server Secret |
Optional |
- To Save these settings click OK.
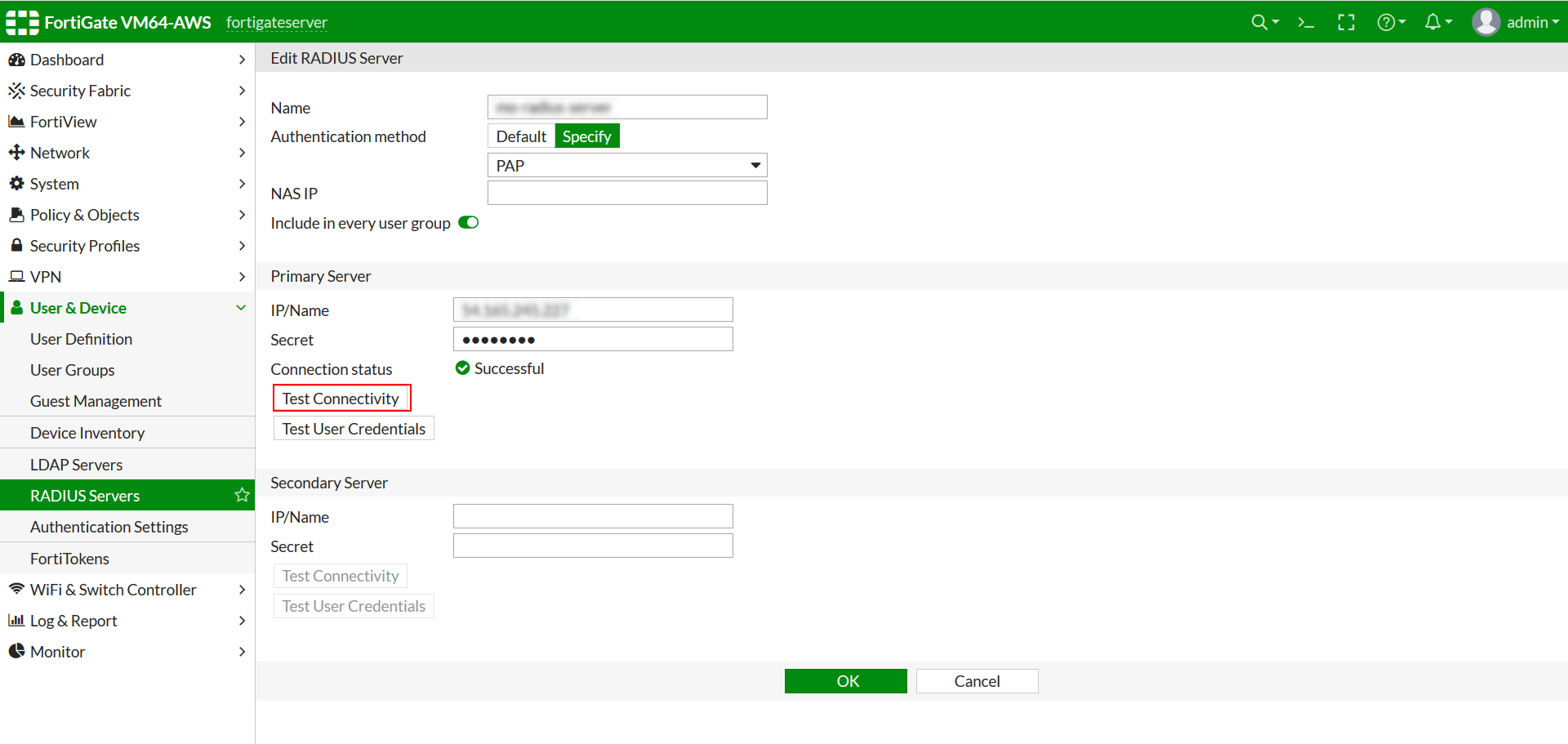
Test Fortinet Fortigate Connectivity
- You can now verify the connectivity by clicking on Test Connectivity.
Create a User Group in Fortinet Fortigate
- NOTE: If you have a existing User Group then just add miniOrange Radius Server as the Remote Server. If not, then follow the below steps.
- Select User & Device >> User >> User Groups.
- To Create New group, Click on Create New.
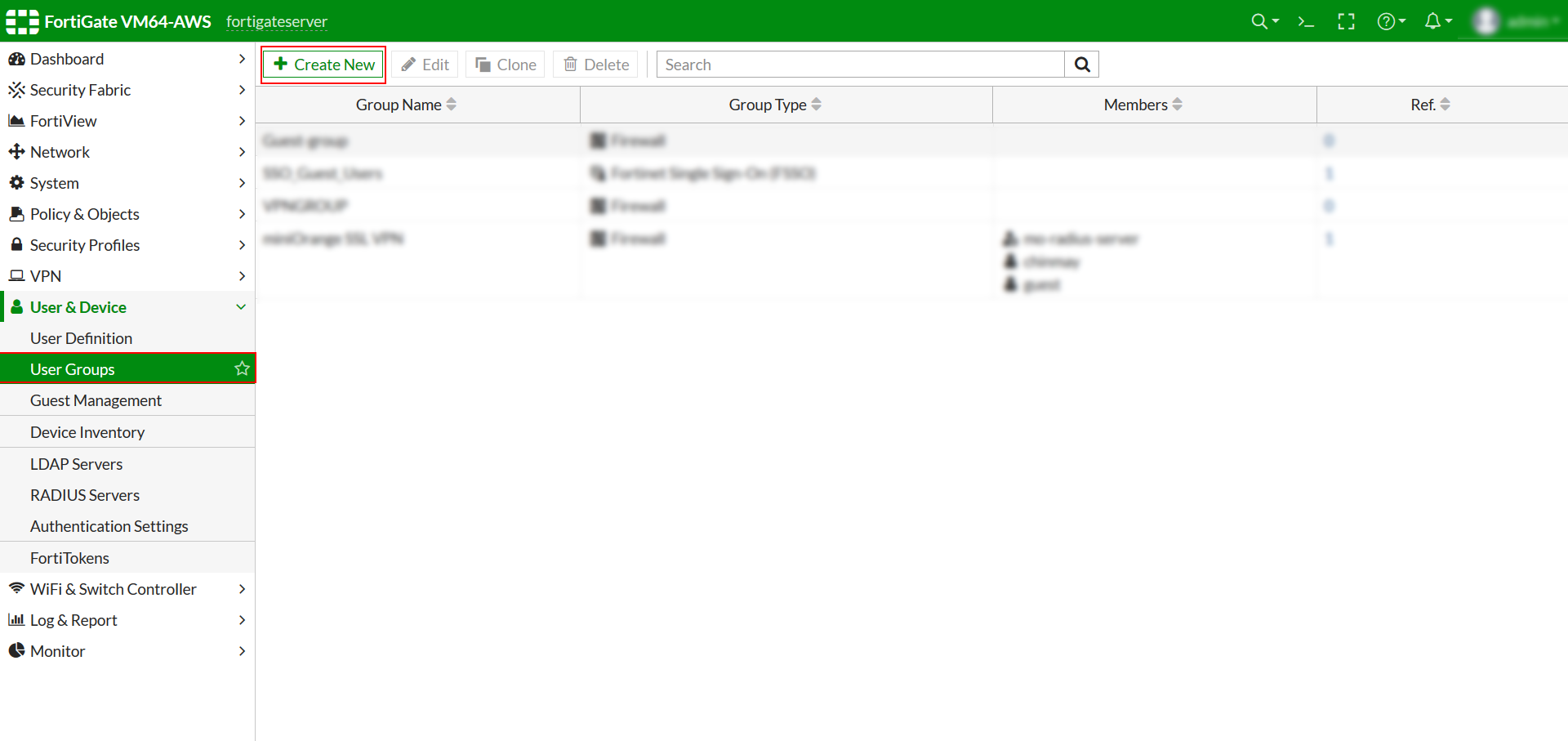
- Select Firewall in Type. Click on Add in the Remote Group Section and select miniOrange Radius Server as the Remote Server.
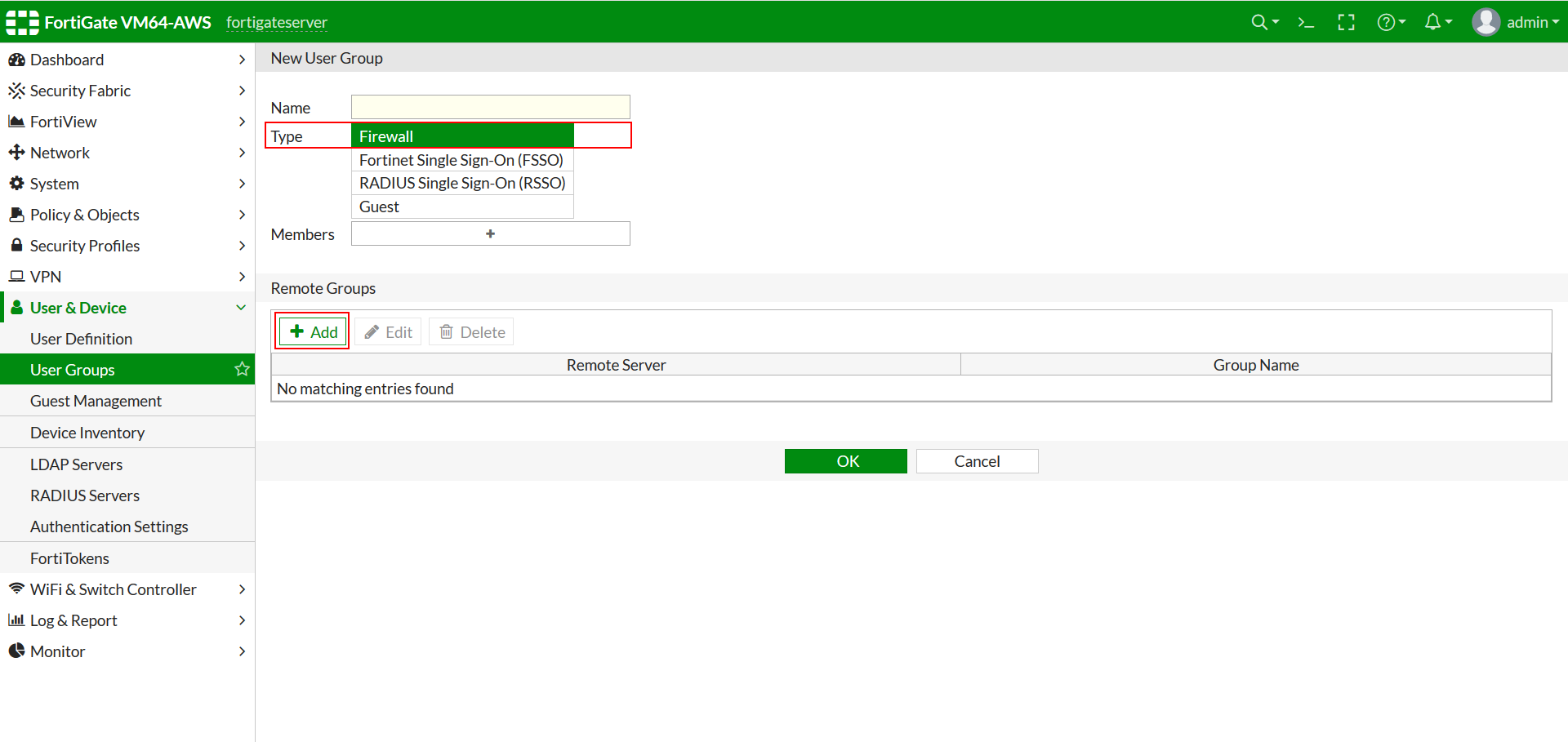
- Click on Ok.
Set Up VPN in Fortigate Admin Console.
- Create a IPSec Tunnel using IPSec Wizard if you have no Tunnel Configured. Click Here to learn more.
- Select VPN >> IPSec Tunnels and select the IPSec Tunnel you have configured.
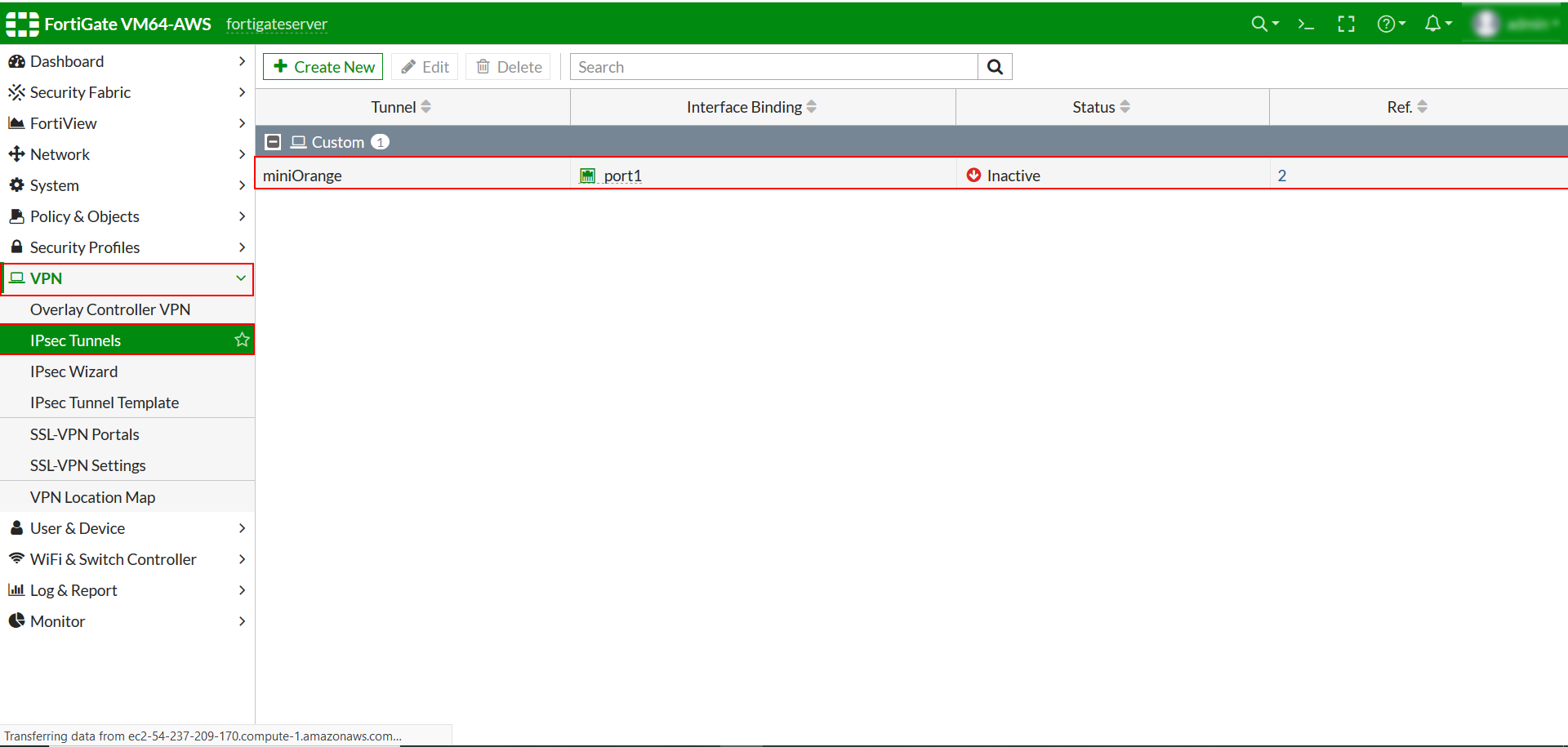
- Click on Convert To Custom Tunnel if the tunnel is not Custom Tunnel.
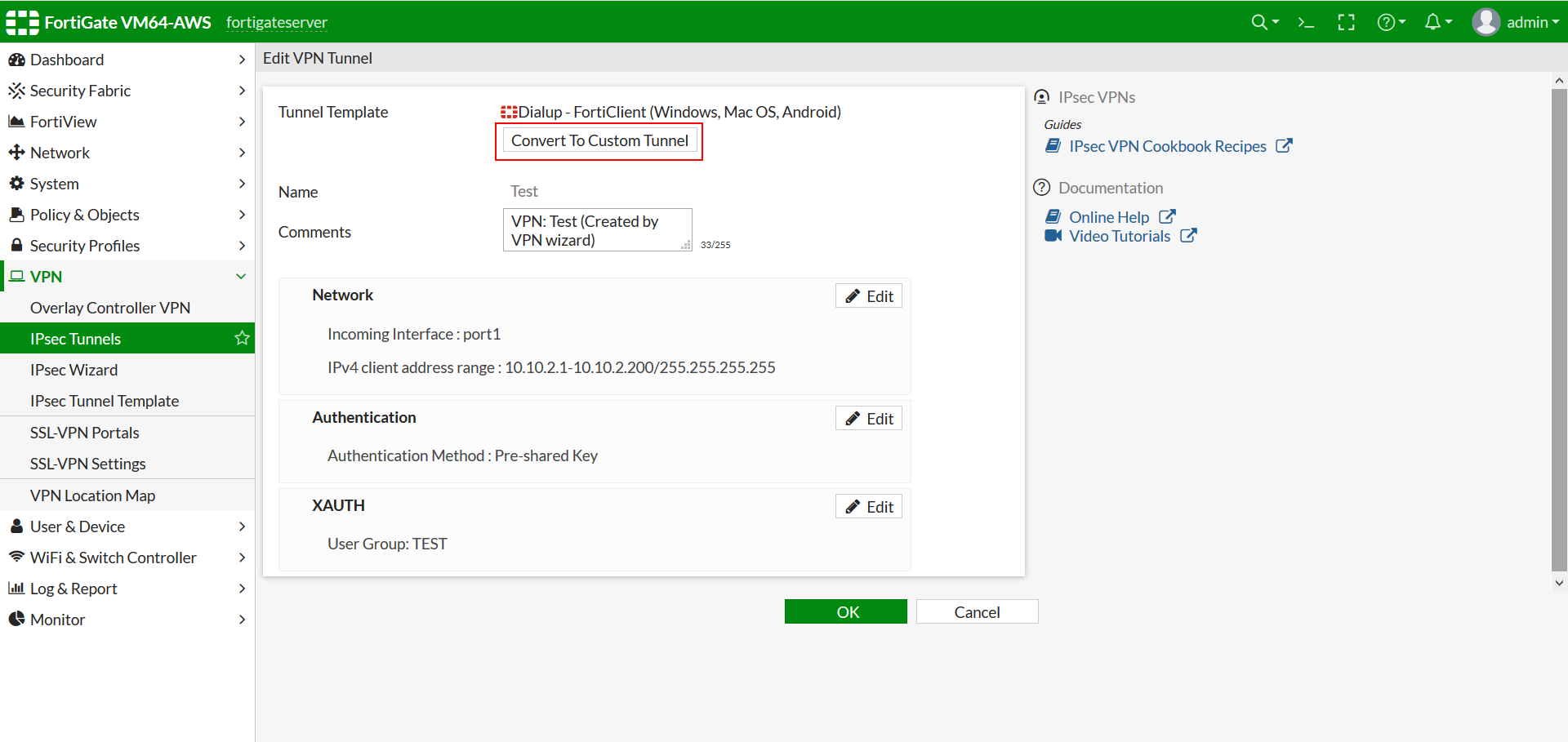
- Click on Edit button for XAuth section.
- Select PAP Server in the Type Dropdown.
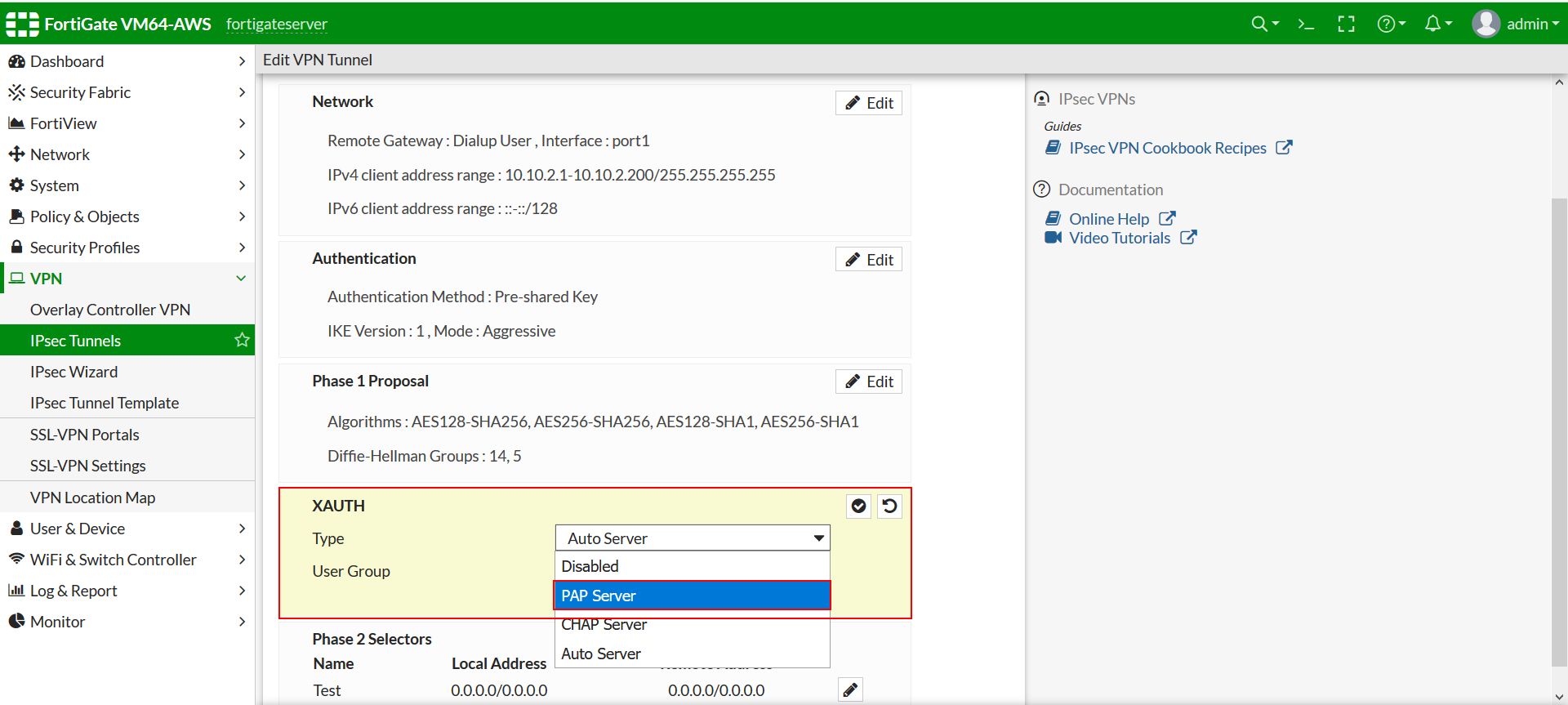
- Select the User Group configured in Step 4 in User Group Dropdown.
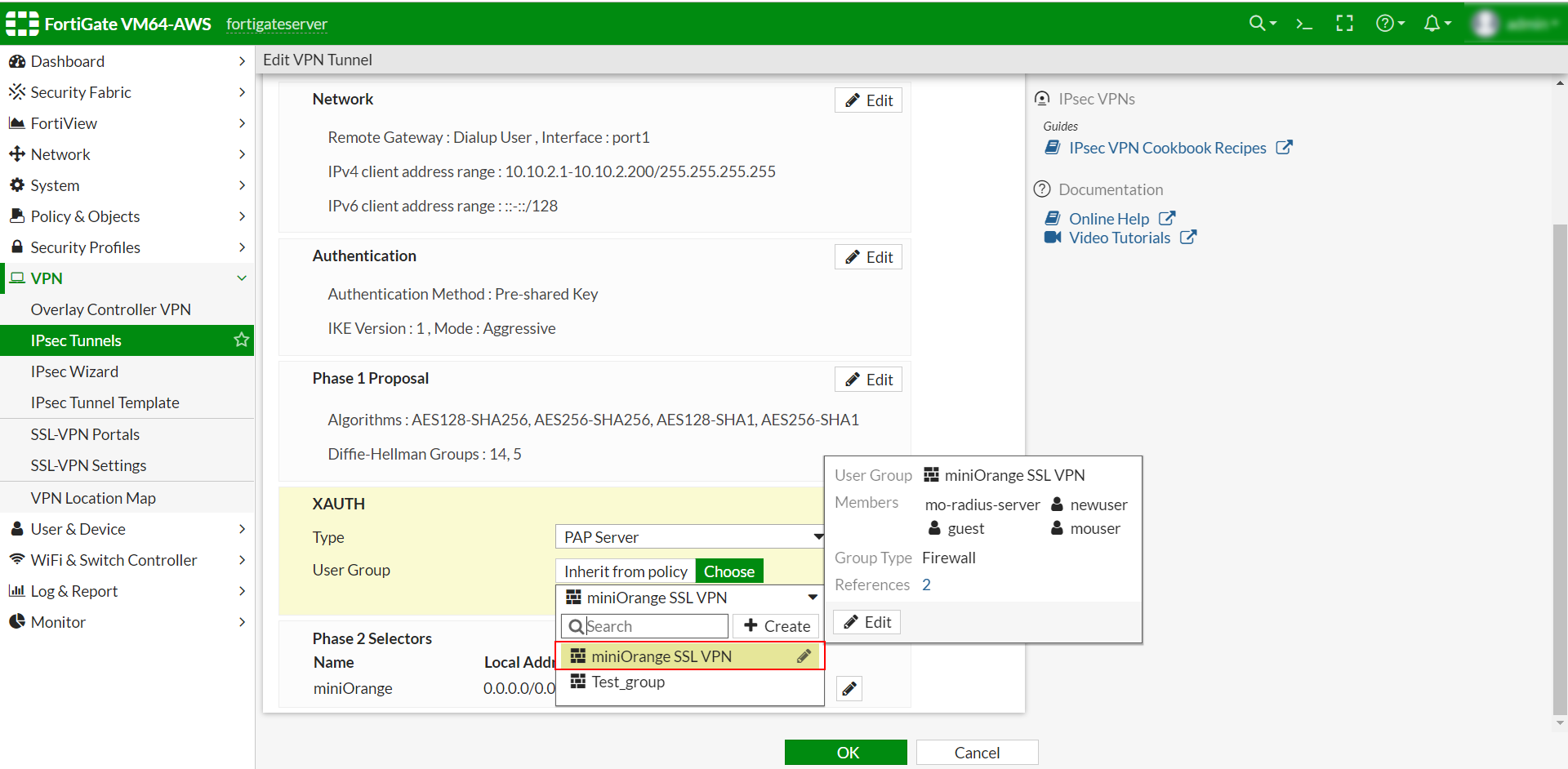
- Click on Ok.
- Firstly setup a SSL-VPN . Click here for more information.
- Navigate to Policy & Objects >> IPV4 Policy.
NOTE: In some cases, there will only Firewall Policy option instead of IPV4 Policy
- Create/Edit the policy related to your SSL-VPN interface.
- Edit the Source, add the required address space and the Group that we configured in Step 4.
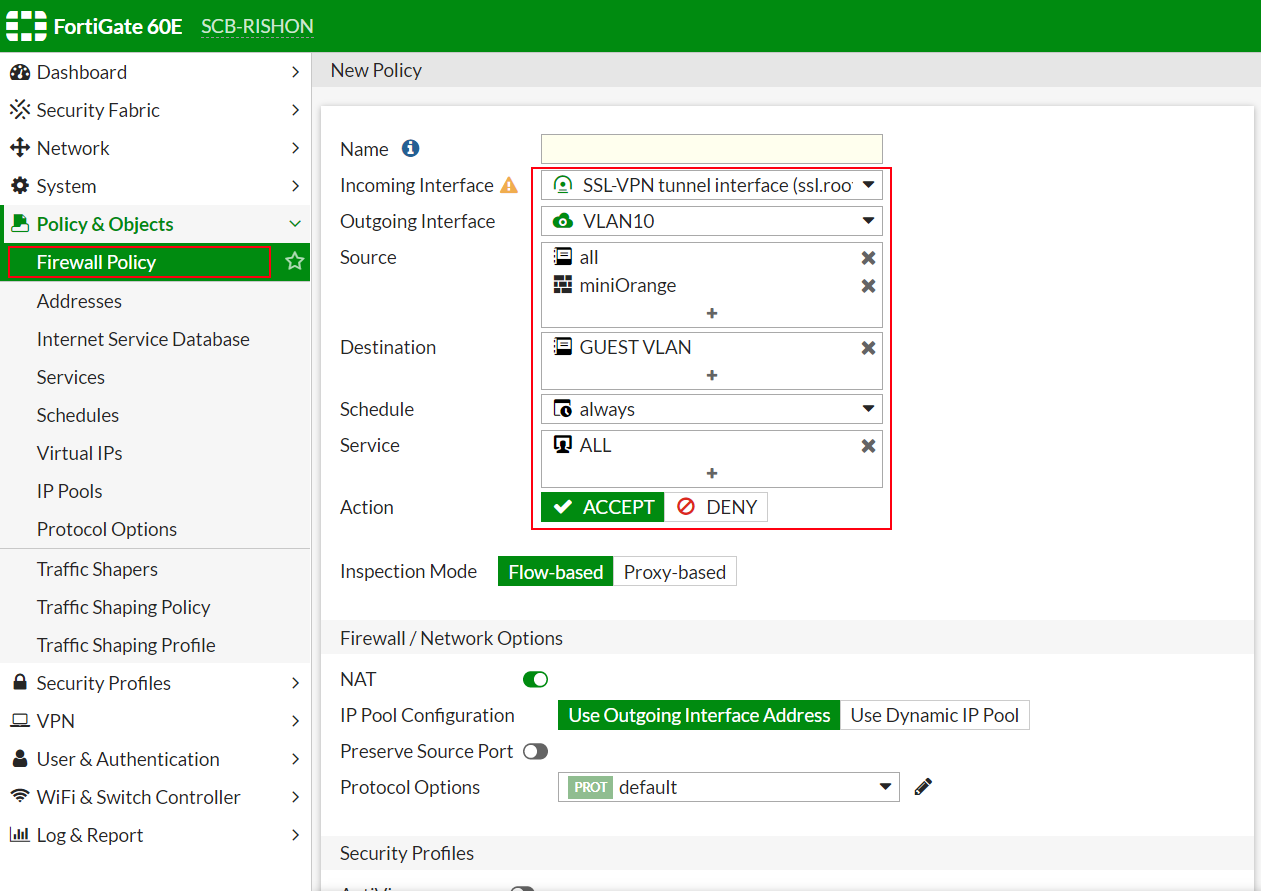
- Click OK to apply and save the settings.
- Next, we will define Authentication/Portal Mapping.
- Navigate to VPN >> SSL-VPN Settings, and then go to the Authentication/Portal Mapping section
- Create a new or edit an existing mapping to grant access to the Firewall User Group that we created in Step 4.
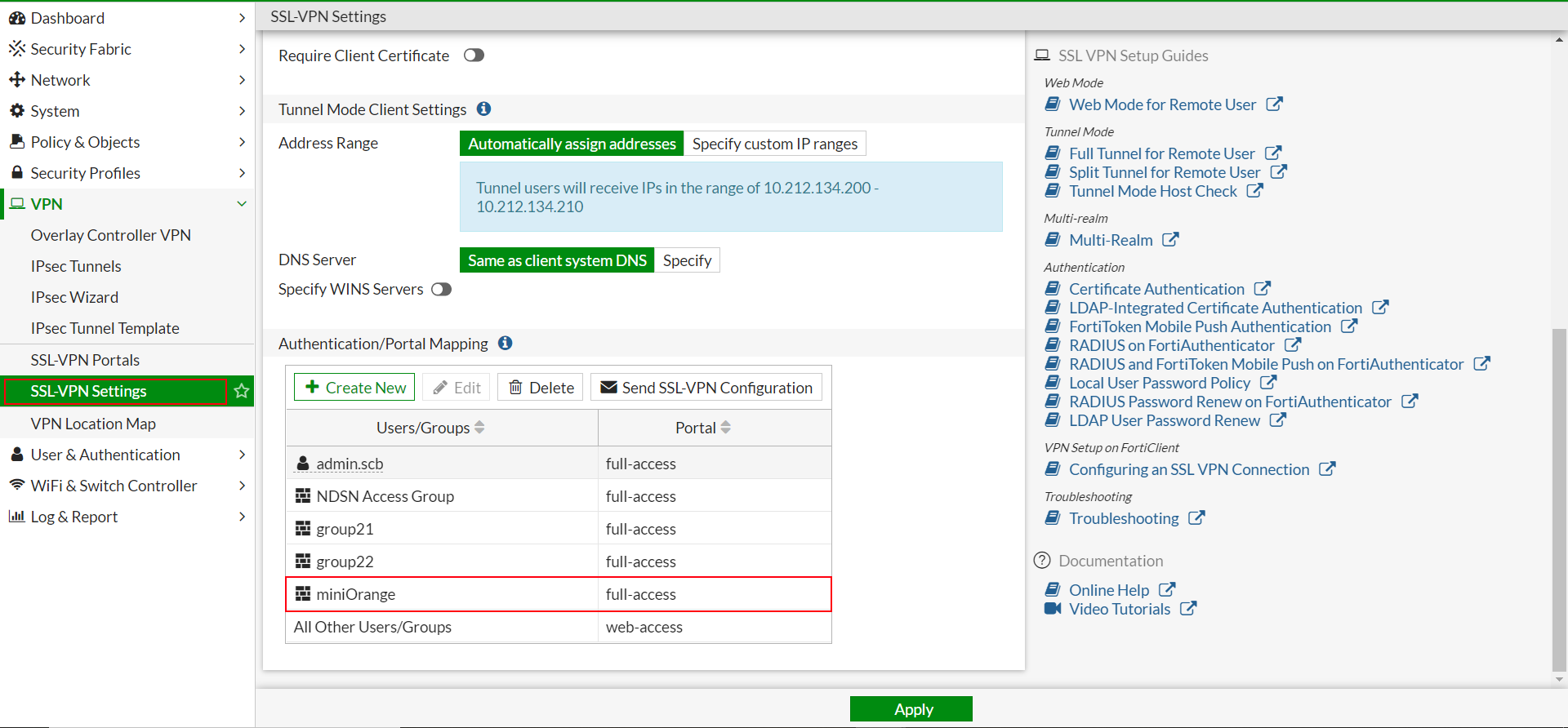
- Click Apply and save the settings.
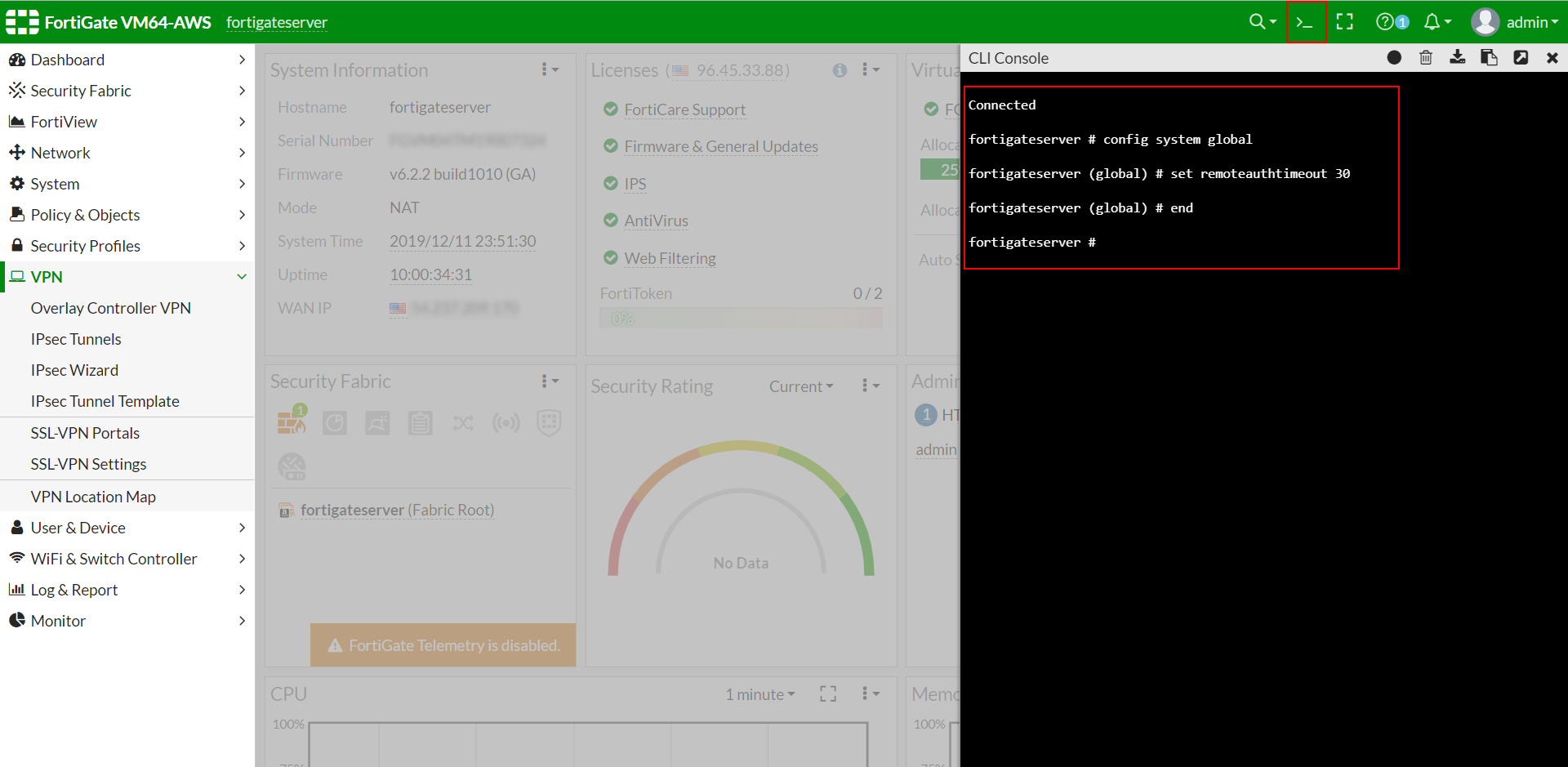
- Fortinet Fortigate default timeout is 5 Seconds, which is insufficient while setting up MFA. We have to reconfigure the timeout to 30 Seconds.
- So connect to the appliance CLI.
- And execute below commands in command line:
#config system global
#set remoteauthtimeout 30
#end
3. Configure Your User Directory
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, Microsoft Entra ID, OpenLDAP, Google, AWS Cognito etc), Identity Providers (like Okta, Shibboleth, Ping, OneLogin, KeyCloak), Databases (like MySQL, Maria DB, PostgreSQL) and many more. You can configure your existing directory/user store or add users in miniOrange.
Note: You can follow this guide, if you want to configure Radius MFA with your users stored in Microsoft Entra ID using OAuth Password Grant.
Setup AD/LDAP as User Directory
Setup miniOrange as User Directory
Configure your existing directories such as Microsoft Active Directory, Microsoft Entra ID, OpenLDAP, etc.
- Click on Identity Providers >> Add Identity Provider in the left menu of the dashboard.
- In Choose Identity Provider, select AD/LDAP Directories from the dropdown.
- Then search for AD/LDAP and click it.
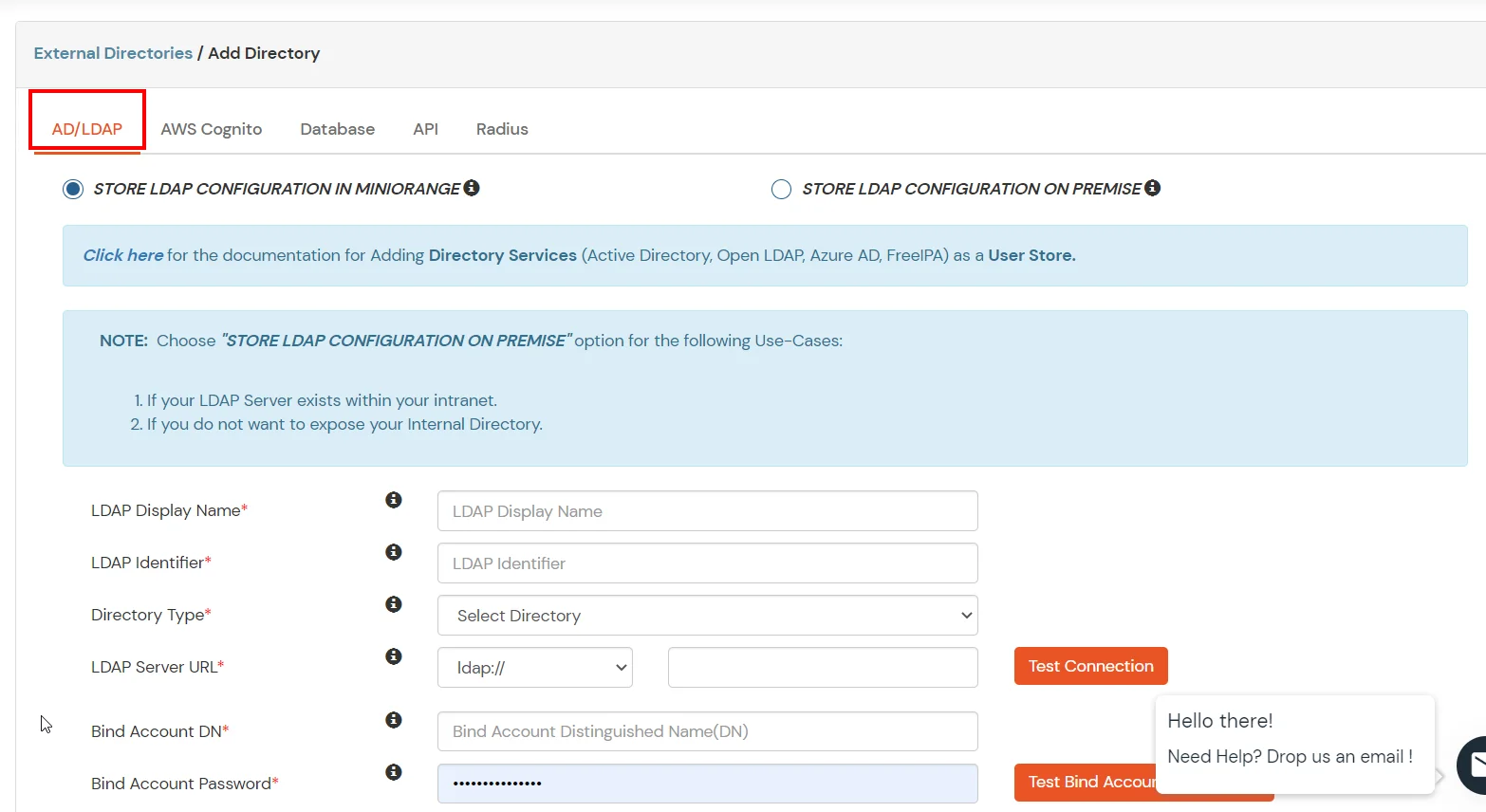
- STORE LDAP CONFIGURATION IN MINIORANGE: Choose this option if you want to keep your configuration in miniOrange. If the active directory is behind a firewall, you will need to open the firewall to allow incoming requests to your AD.
- STORE LDAP CONFIGURATION ON PREMISE: Choose this option if you want to keep your configuration in your premise and only allow access to AD inside premises. You will have to download and install miniOrange gateway on your premise.
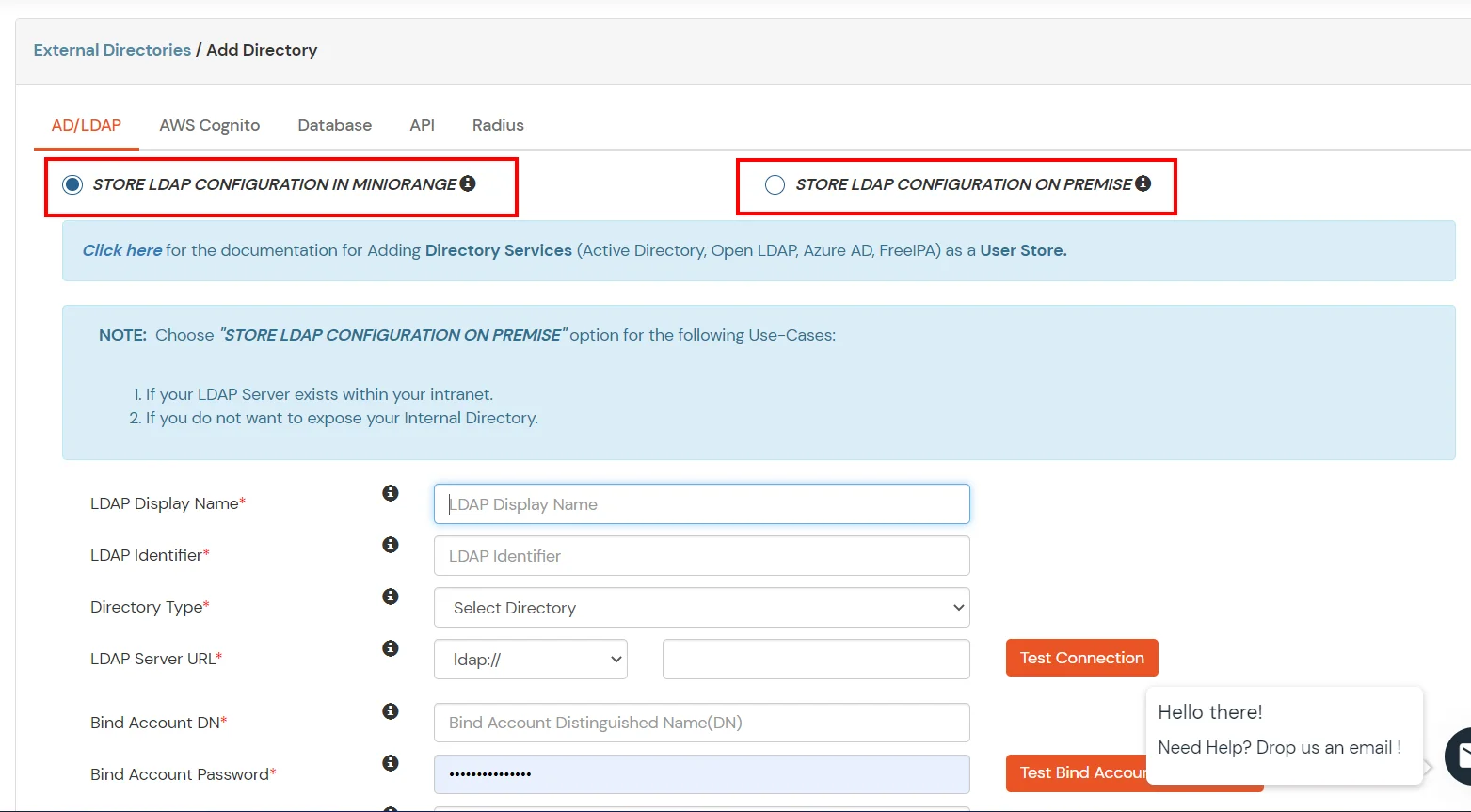
- Enter LDAP Display Name and Identifier name.
- Select Directory Type as Active Directory.
- Enter the LDAP Server URL or IP Address against the LDAP Server URL field.
- Click on the Test Connection button to verify if you have made a successful connection with your LDAP server.
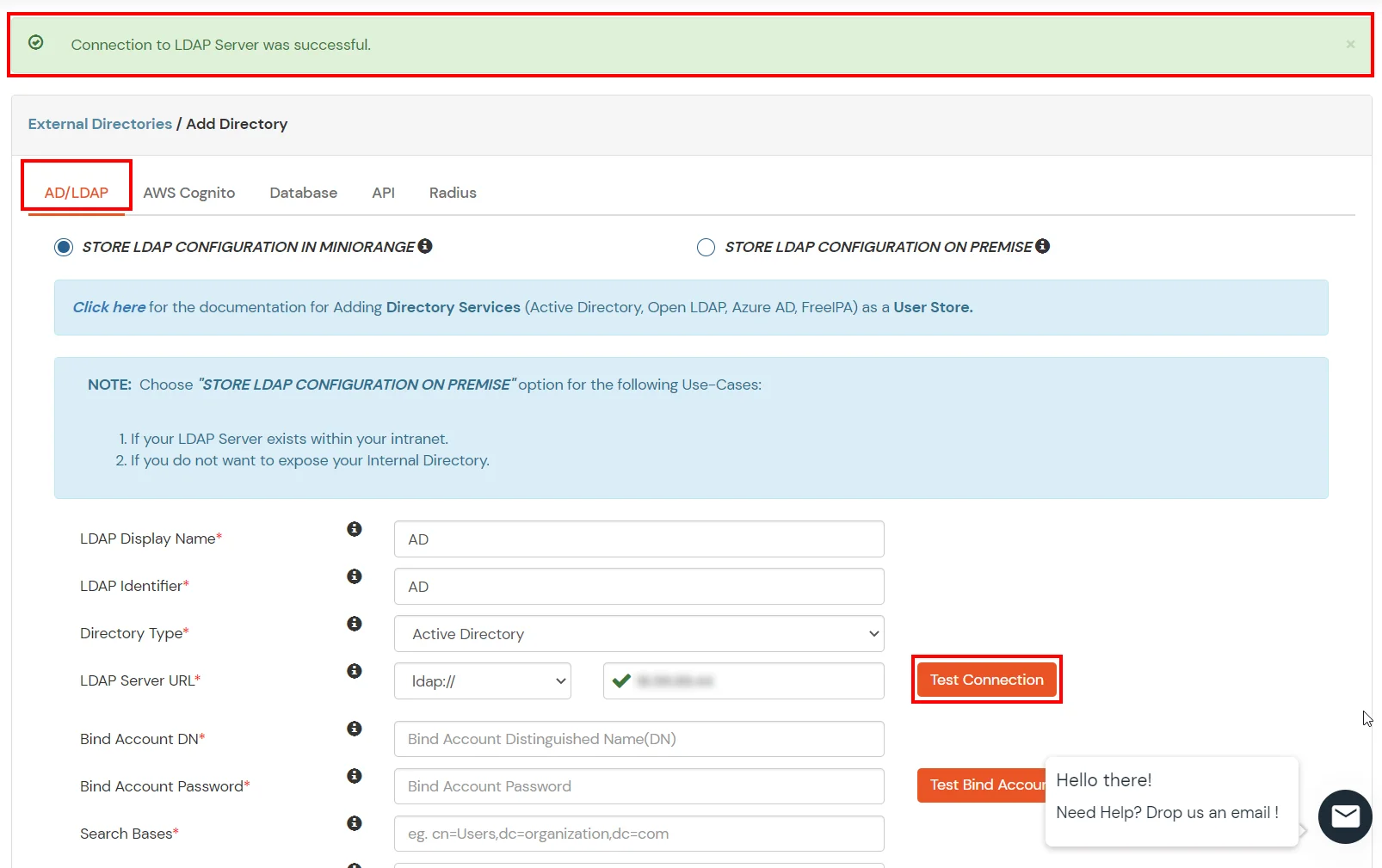
- In Active Directory, go to the properties of user containers/OU's and search for the Distinguished Name attribute. The bind account should have minimum required read privileges in Active Directory to allow directory lookups. If the use case involves provisioning (such as creating, updating, or deleting users or groups), the account must also be granted appropriate write permissions.
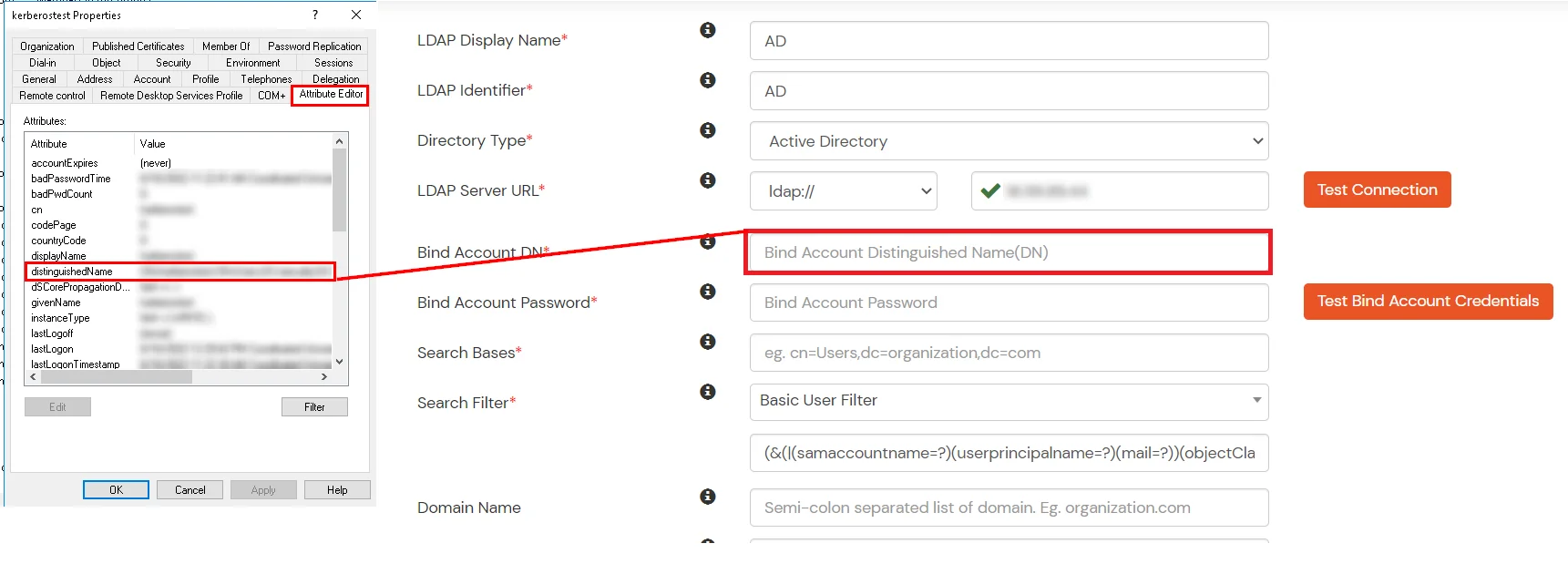
- Enter the valid Bind account Password.
- Click on the Test Bind Account Credentials button to verify your LDAP Bind credentials for LDAP connection.
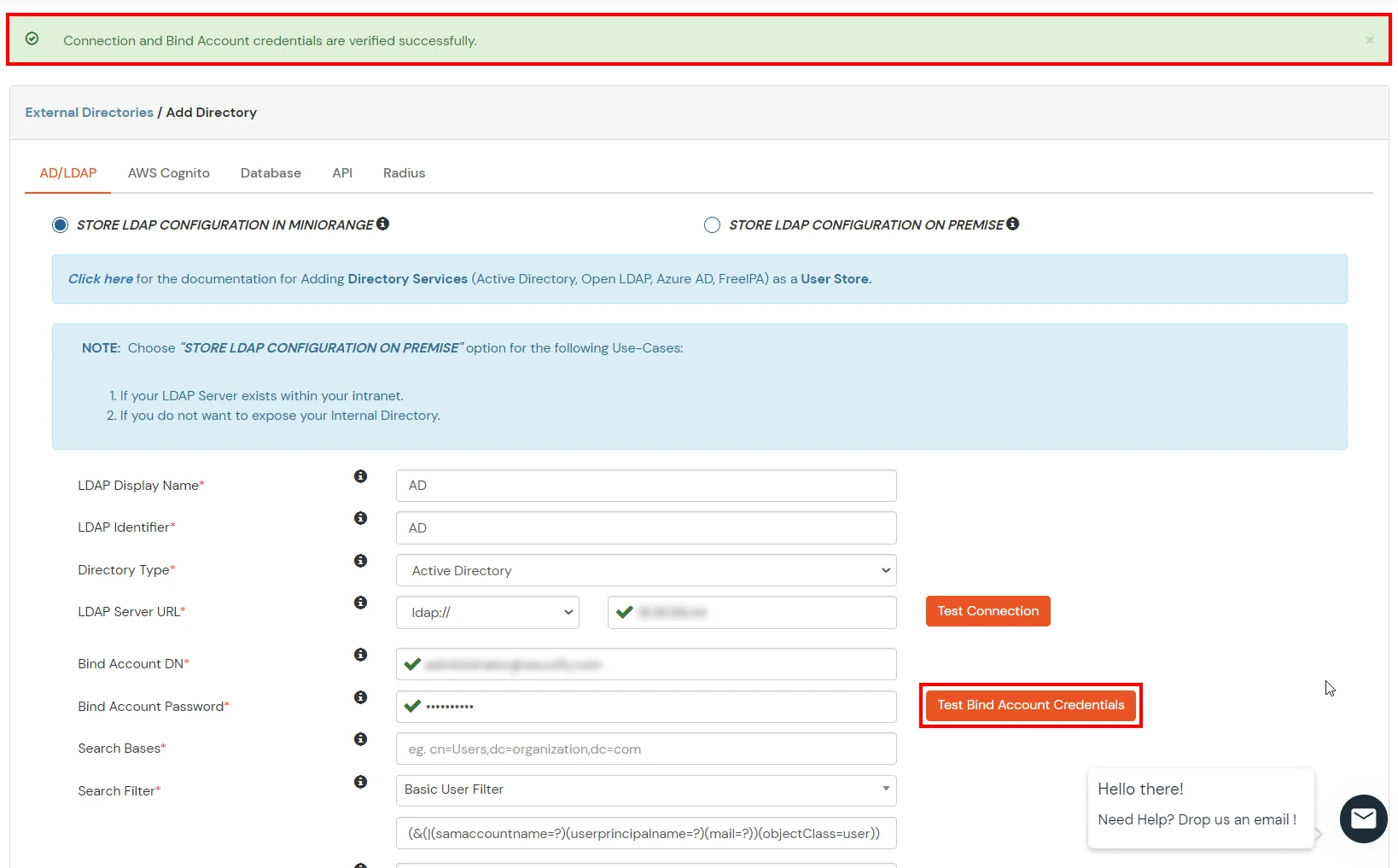
- Search Base is the location in the directory where the search for a user begins. You will get this from the same place you got your Distinguished name.
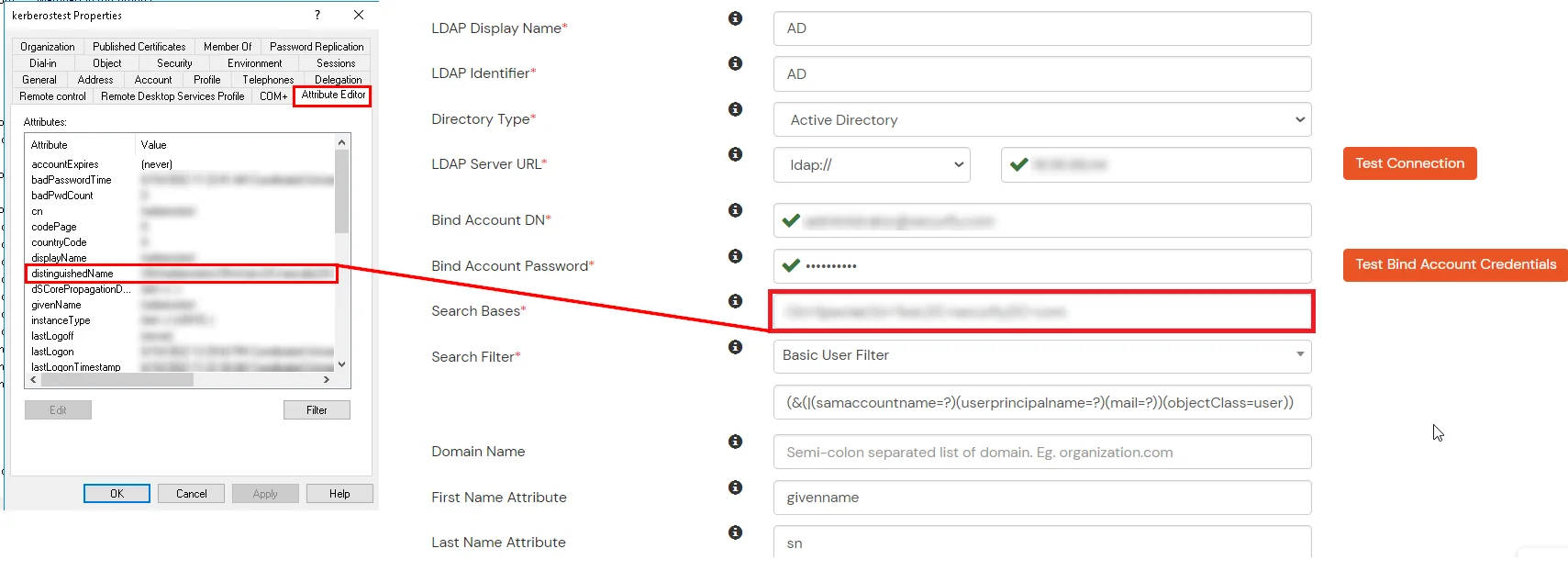
- Select a suitable Search filter from the drop-down menu. If you use User in Single Group Filter or User in Multiple Group Filter, replace the <group-dn> in the search filter with the distinguished name of the group in which your users are present. To use custom Search Filter select "Write your Custom Filter" option and customize it accordingly.
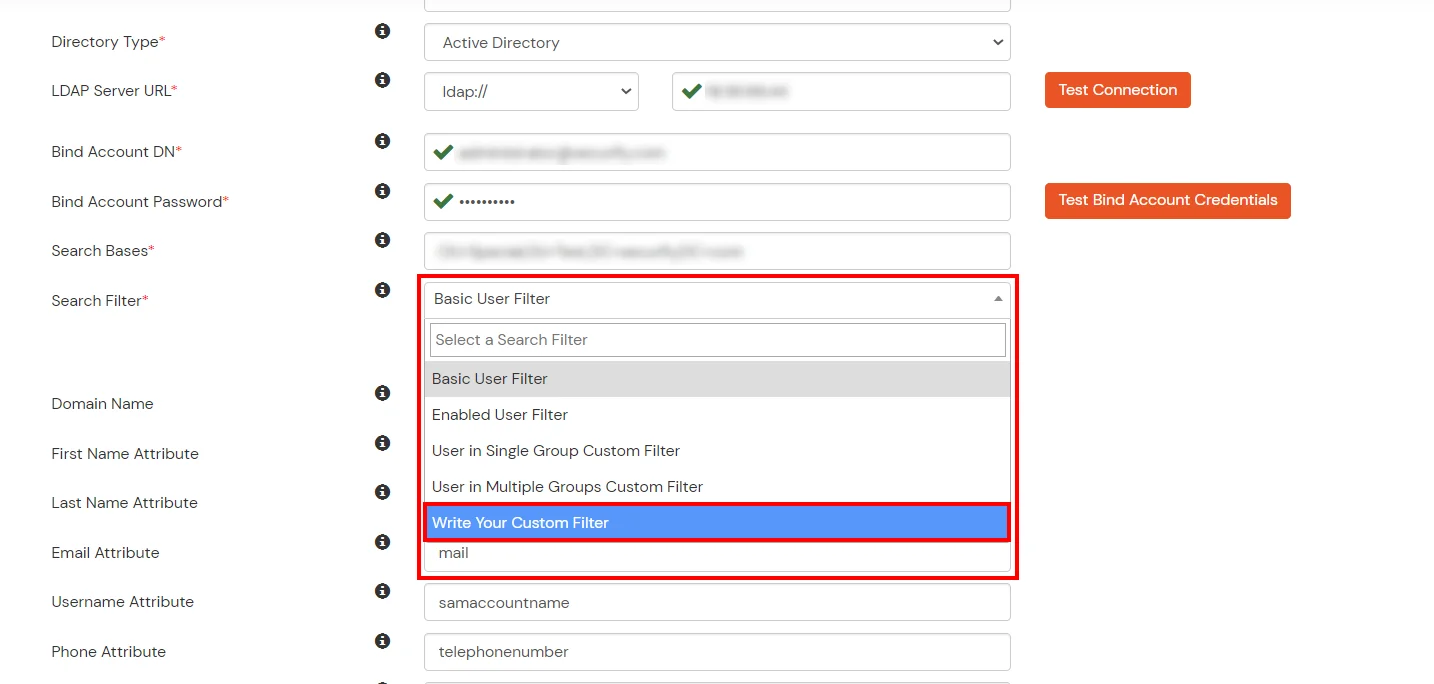
- Click on the Next button, or go to the Login Options tab.
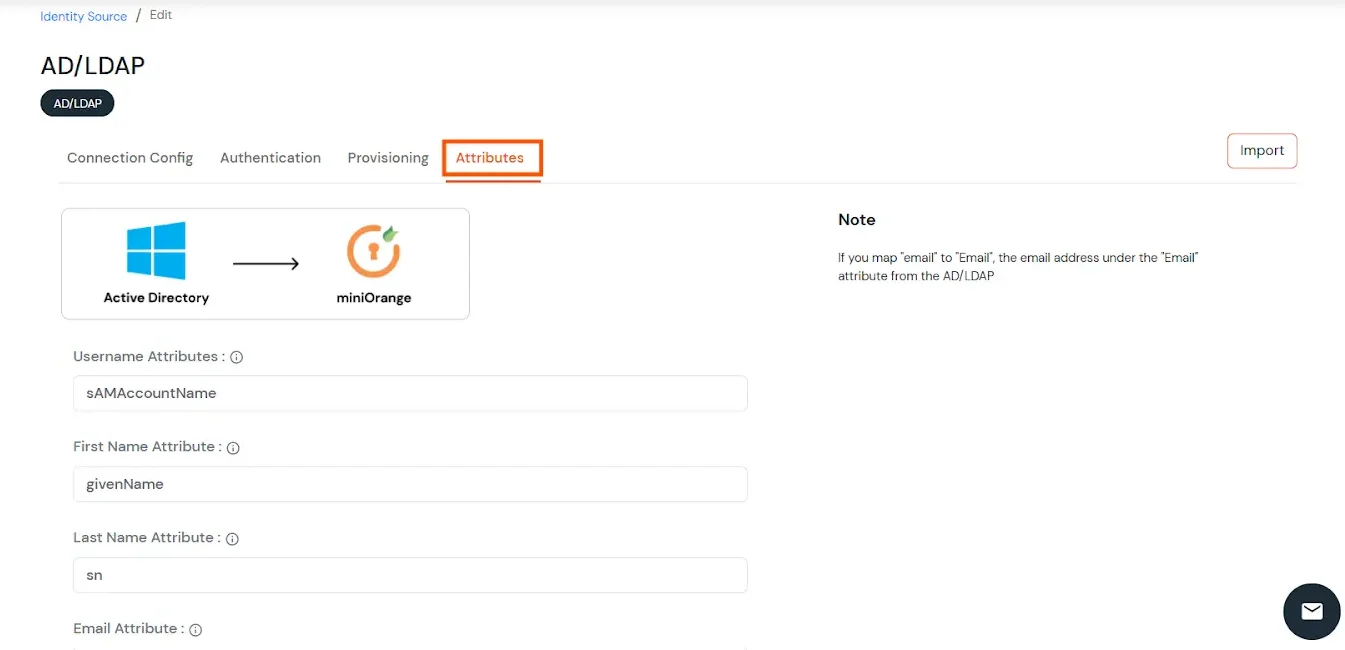
- You can also configure following options while setting up AD. Enable Activate LDAP in order to authenticate users from AD/LDAP. Click on the Next button to add user store.
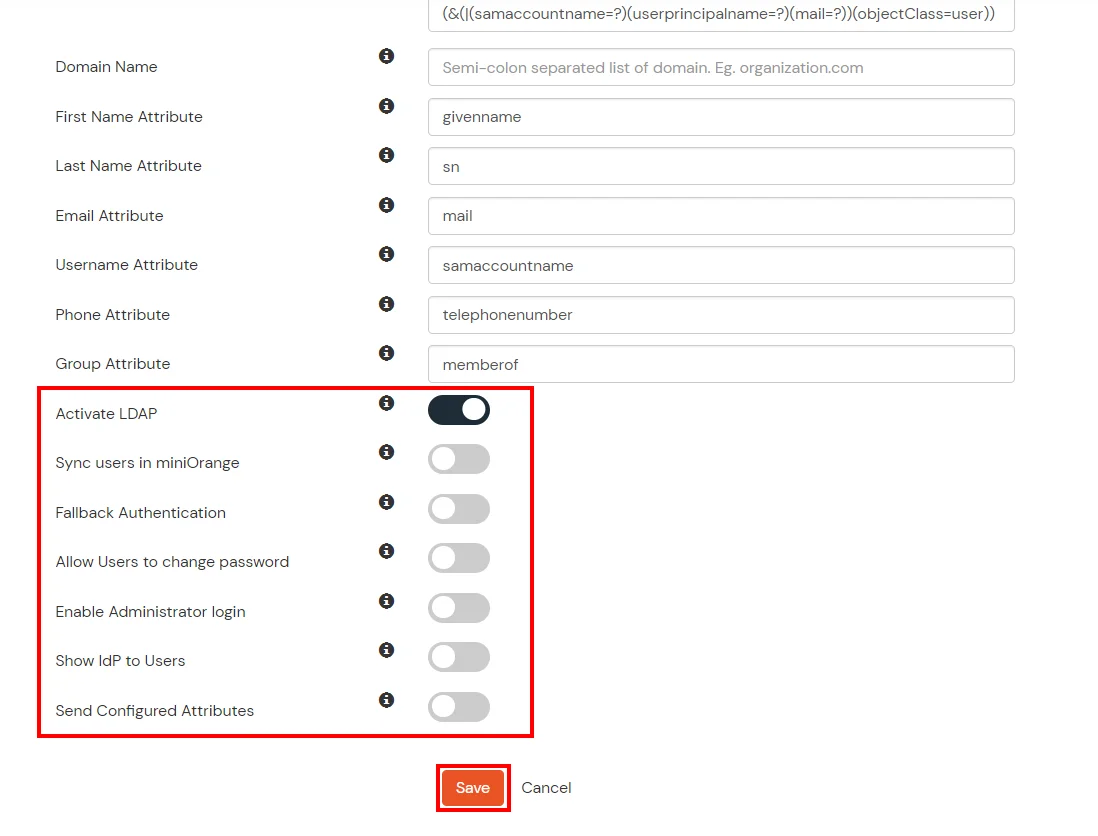
Here's the list of the attributes and what it does when we enable it. You can enable/disable accordingly.
| Attribute |
Description |
| Activate LDAP |
All user authentications will be done with LDAP credentials if you Activate it |
| Fallback Authentication |
If LDAP credentials fail then user will be authenticated through miniOrange |
| Enable administrator login |
On enabling this, your miniOrange Administrator login authenticates using your LDAP server |
| Show IdP to users |
If you enable this option, this IdP will be visible to users |
| Sync users in miniOrange |
Users will be created in miniOrange after authentication with LDAP |
- Click on the Next button, or go to the Attributes tab.
Attributes Mapping from AD
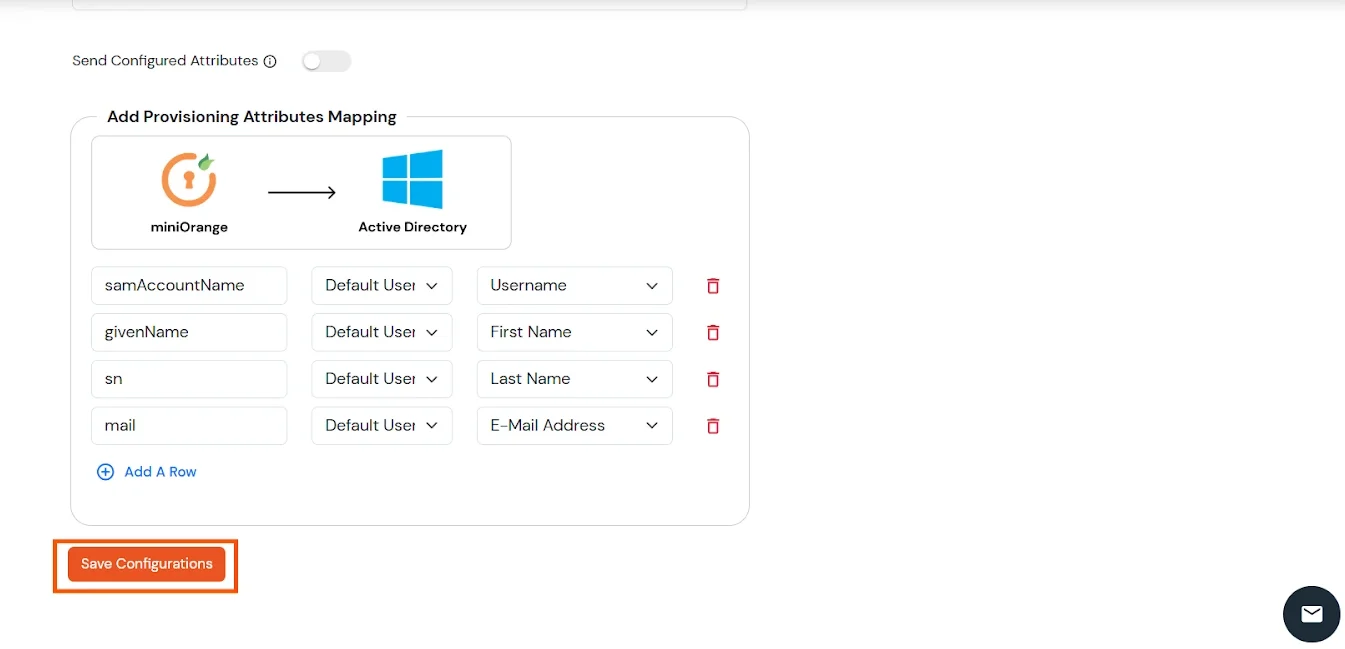
User Import and Provisioning from AD
- If you want to set up provisioning, click here for detailed information. We will skip this step for now.
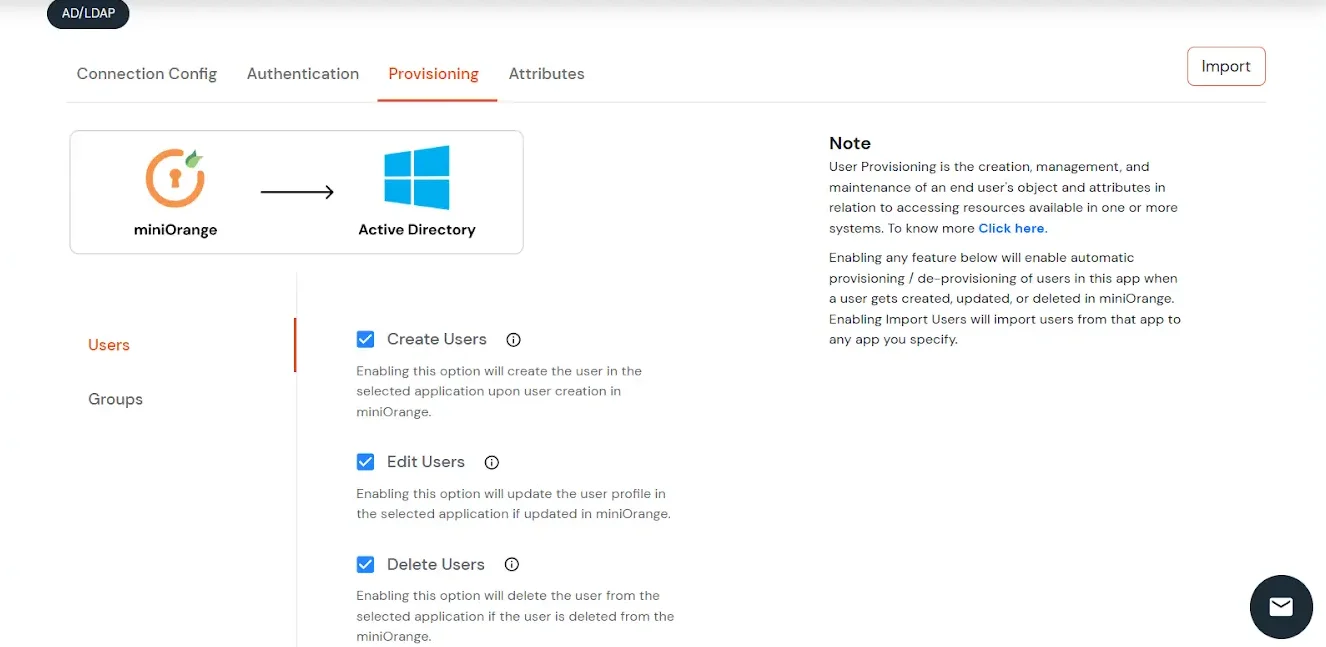
Test Connections
- You will see a list of directories under Identity Providers. From the dropdown, select AD/LDAP Directories, search for your configured directory, click the three dots next to it, and select Test Connection.
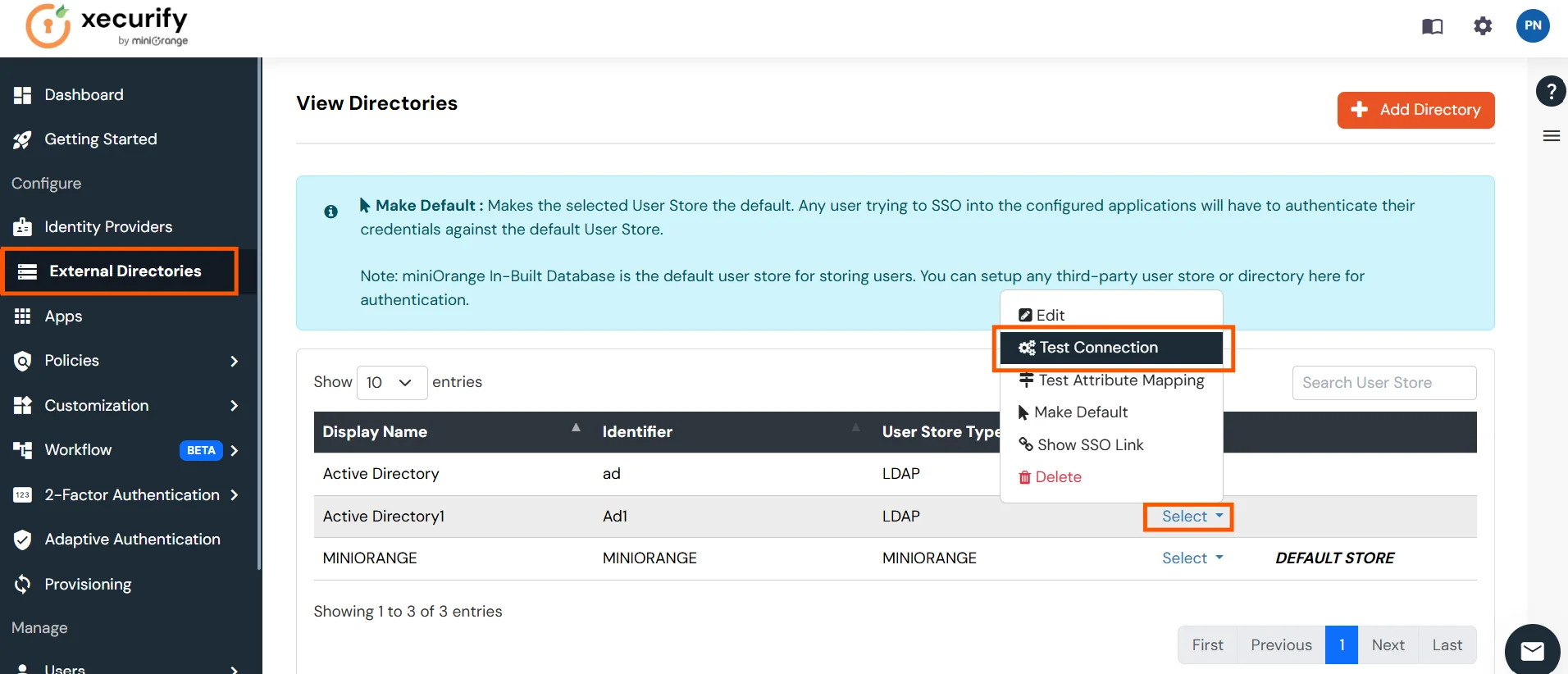
- A pop-up appears prompting you to enter a username and password to verify your LDAP configuration.
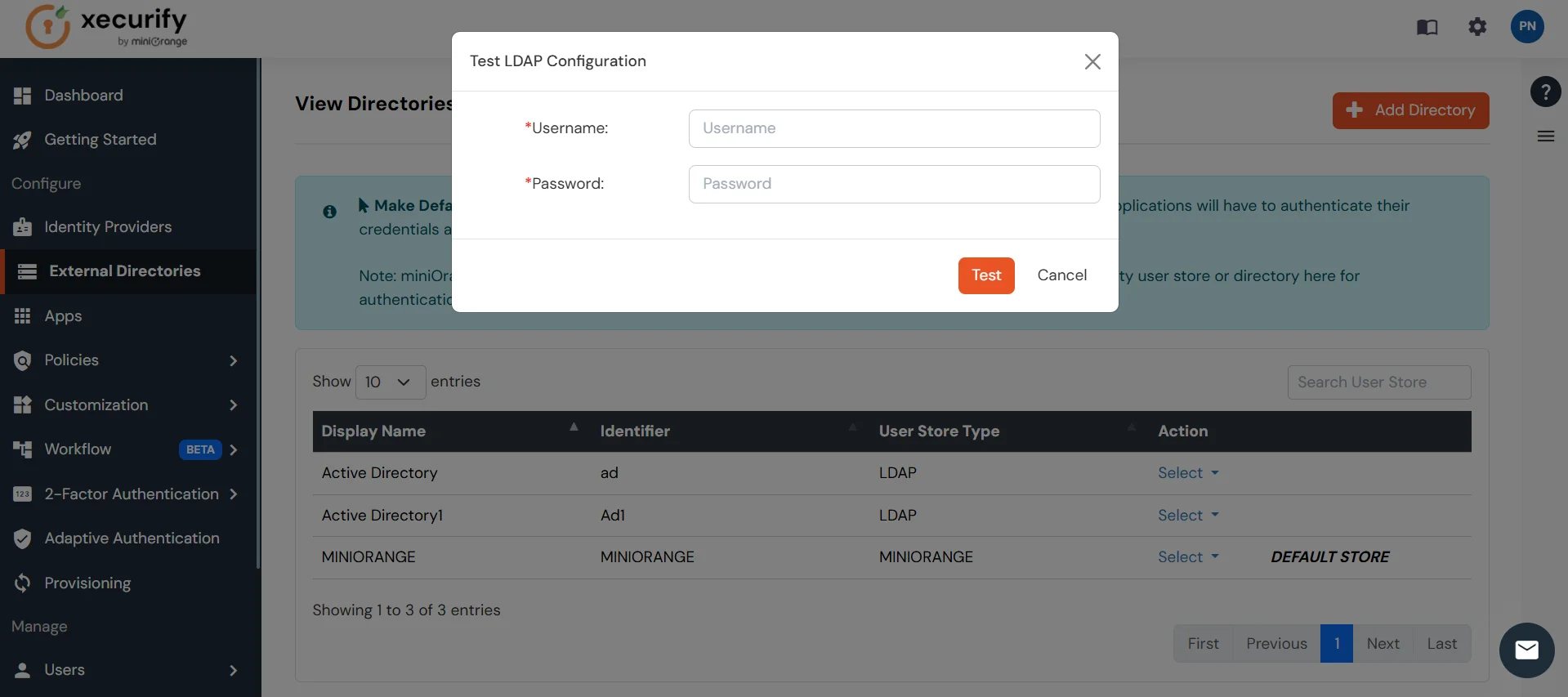
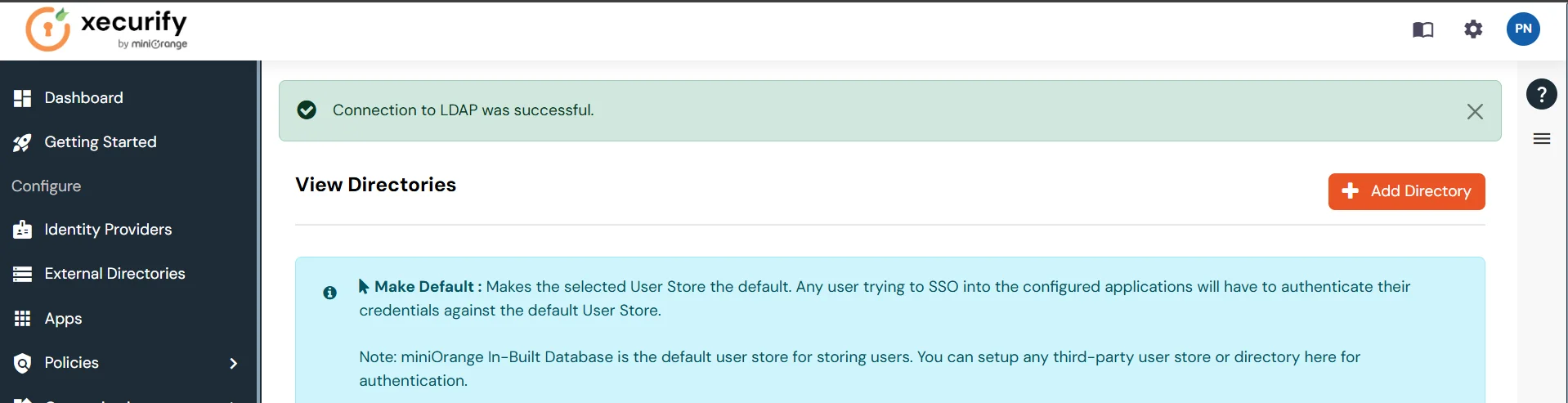
- On Successful connection with LDAP Server, a success message is shown.
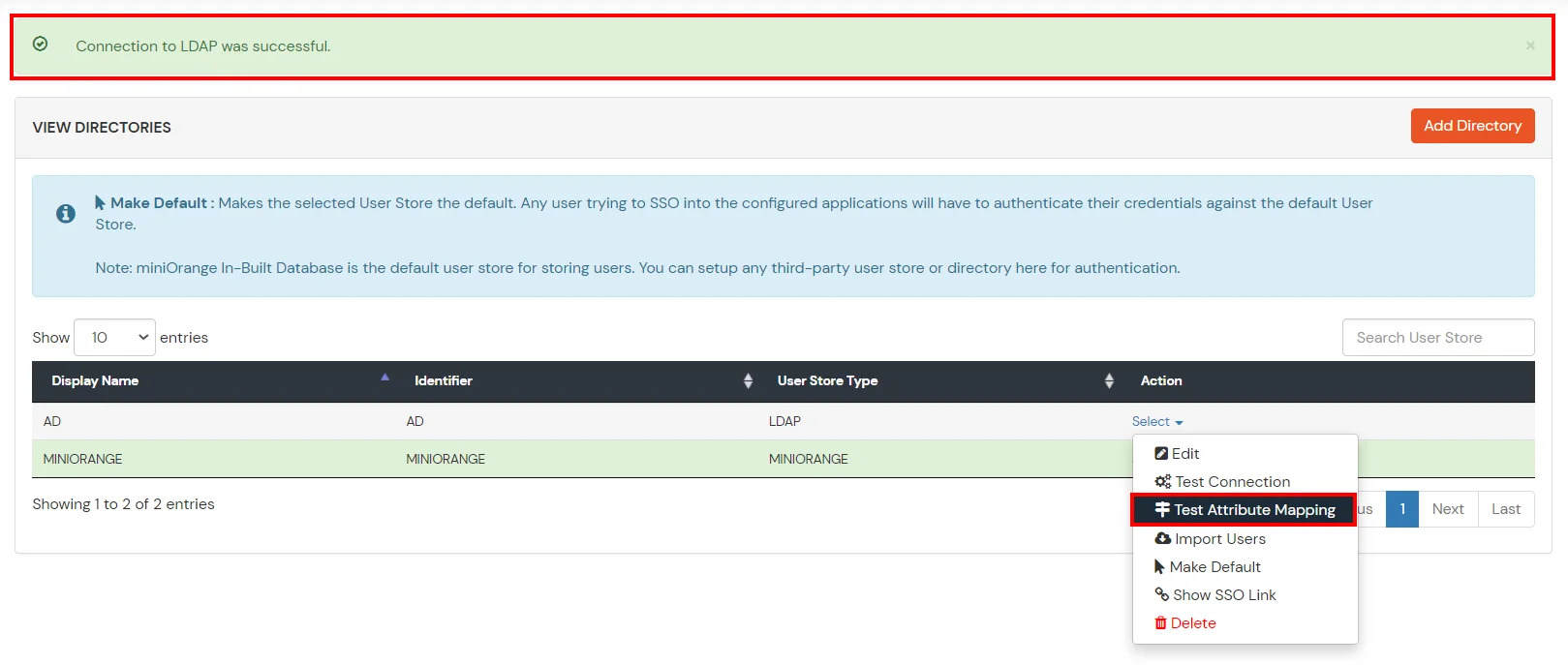
Test Attribute Mapping
- You will see a list of directories under Identity Providers. From the dropdown, select AD/LDAP Directories, search for your configured directory, click the three dots next to it, and select Test Attribute Mapping.
- A pop‑up appears to enter a username and click Test.
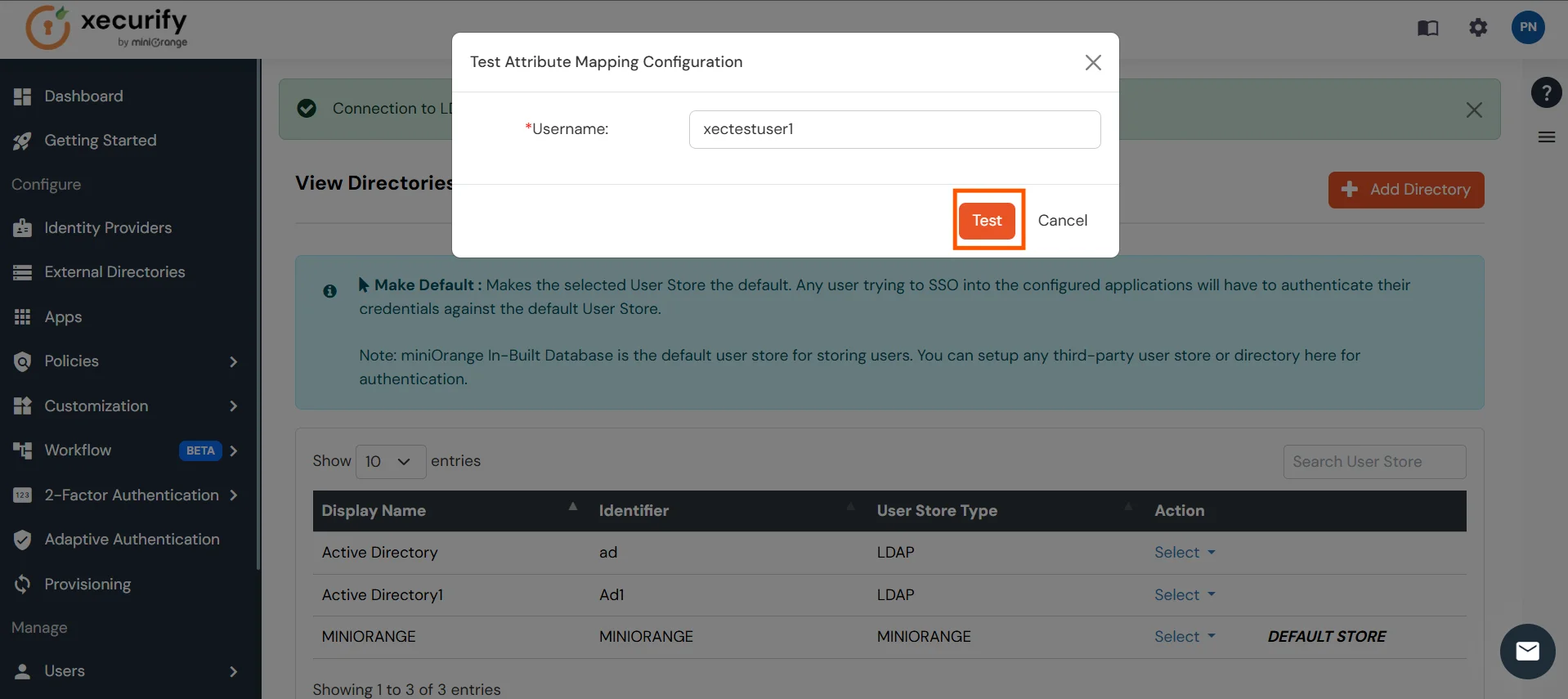
- The Test Attribute Mapping Result will be displayed.
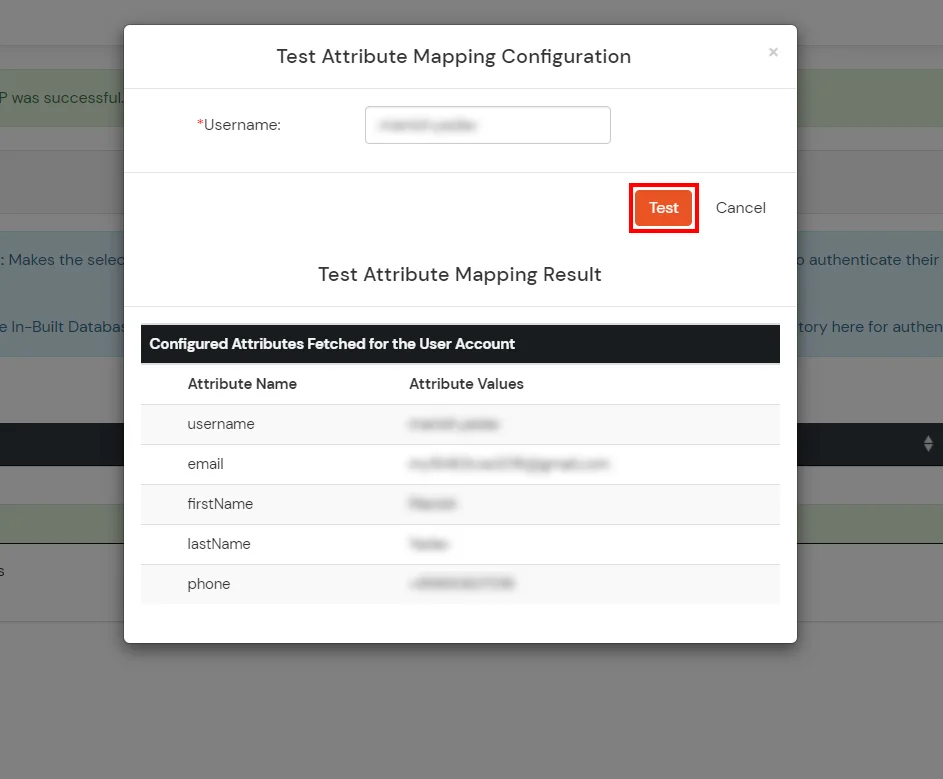
Set up AD as External Directory configuration is complete.
Note: Refer our guide to setup LDAP on windows server.
Creating User Groups (Recommended)
- Select Groups >> Manage Groups from left panel.
- Click on the Create Group button on the top.
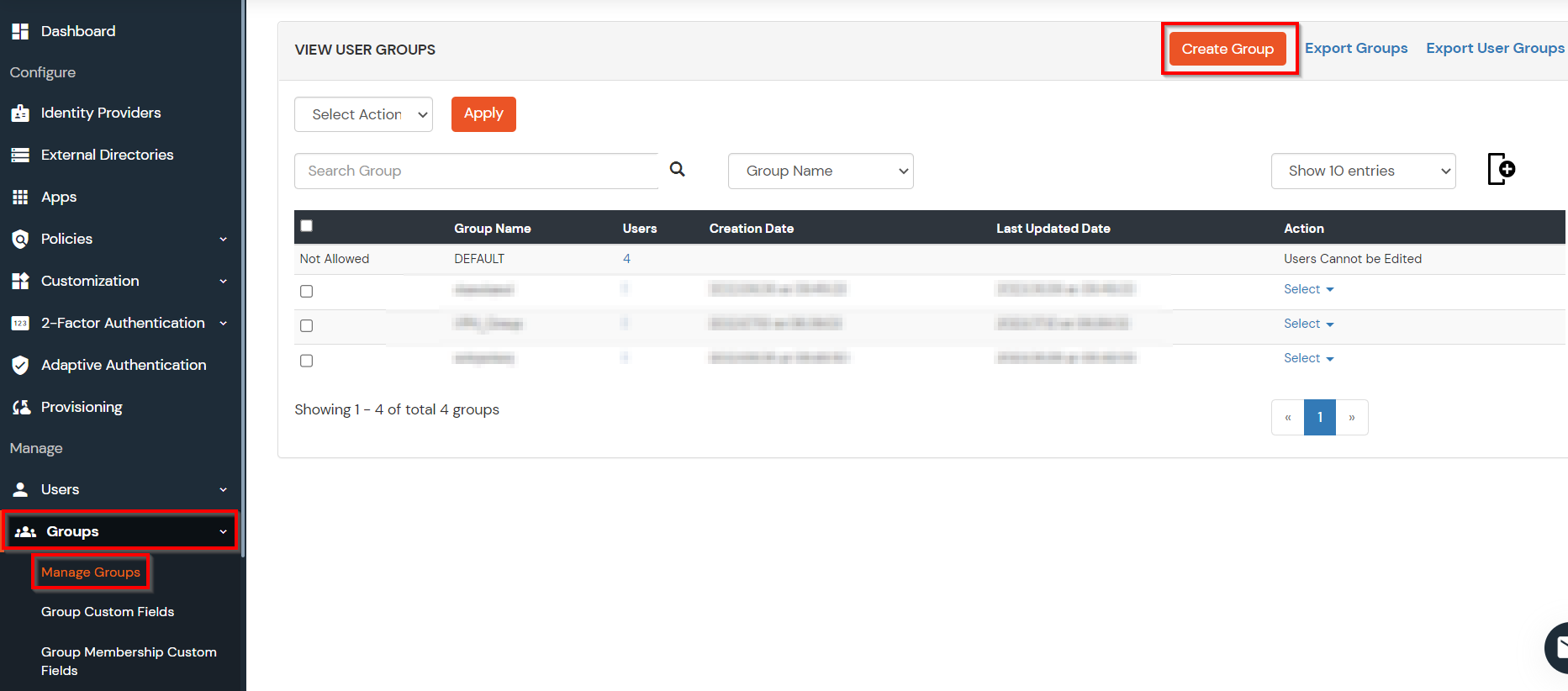
- Enter an appropriate Group Name and click on Create Group.
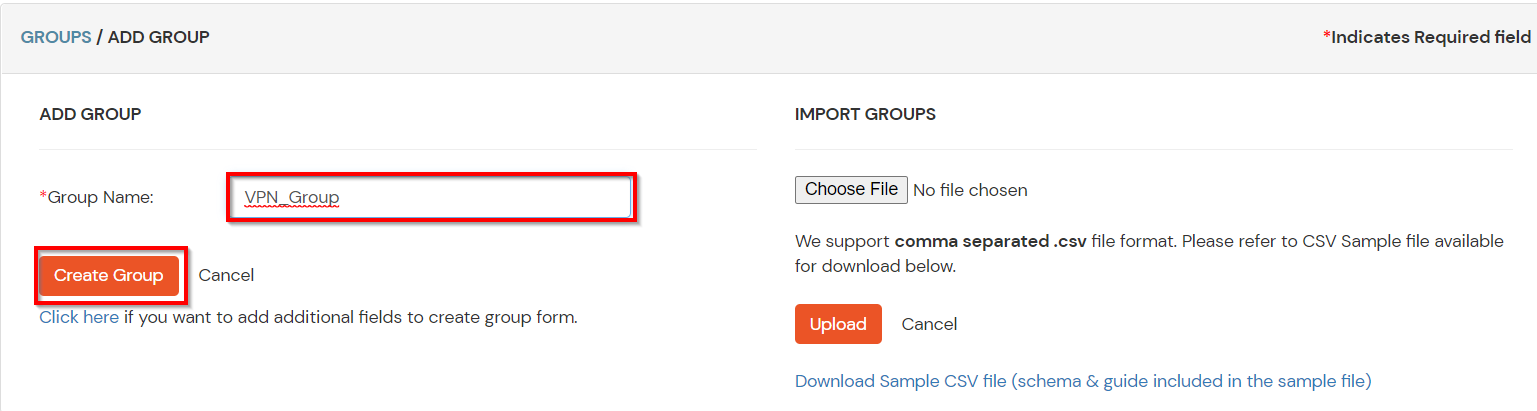
- In this guide we have created a Group by name VPN_Group.
- Assign various members to the group using the Assign User option associated with the group in the groups list.
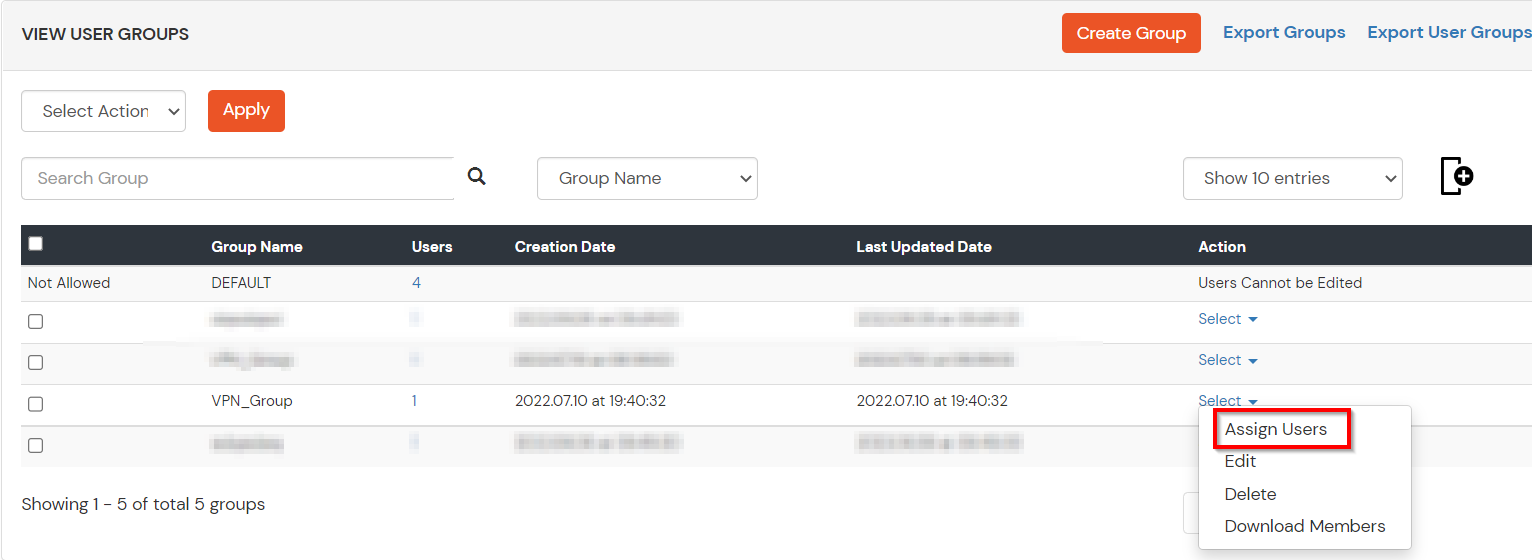
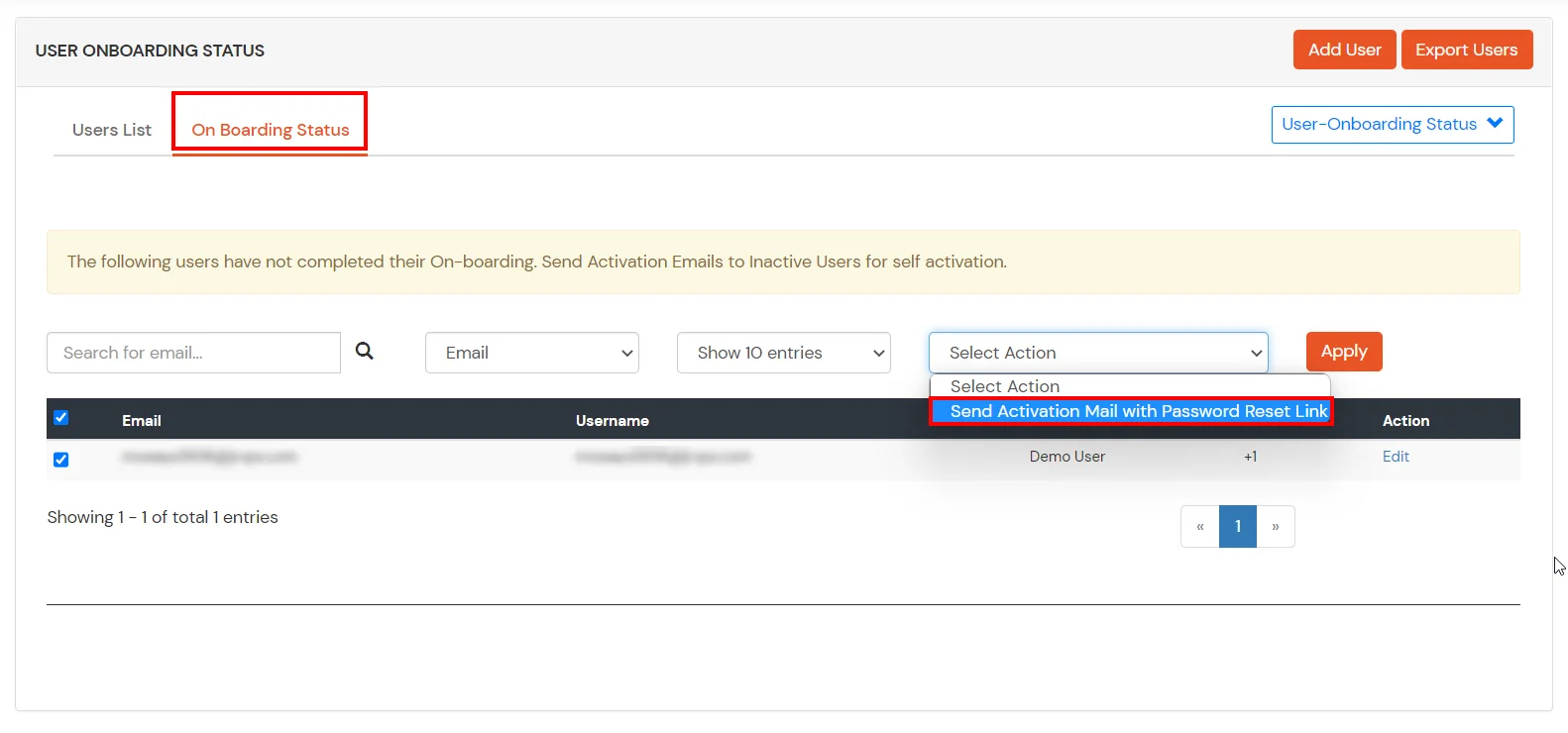
- Select the Users that are required to be assigned to this group. Then Select Assign to Group in Select Action Dropdown and click on Apply button.
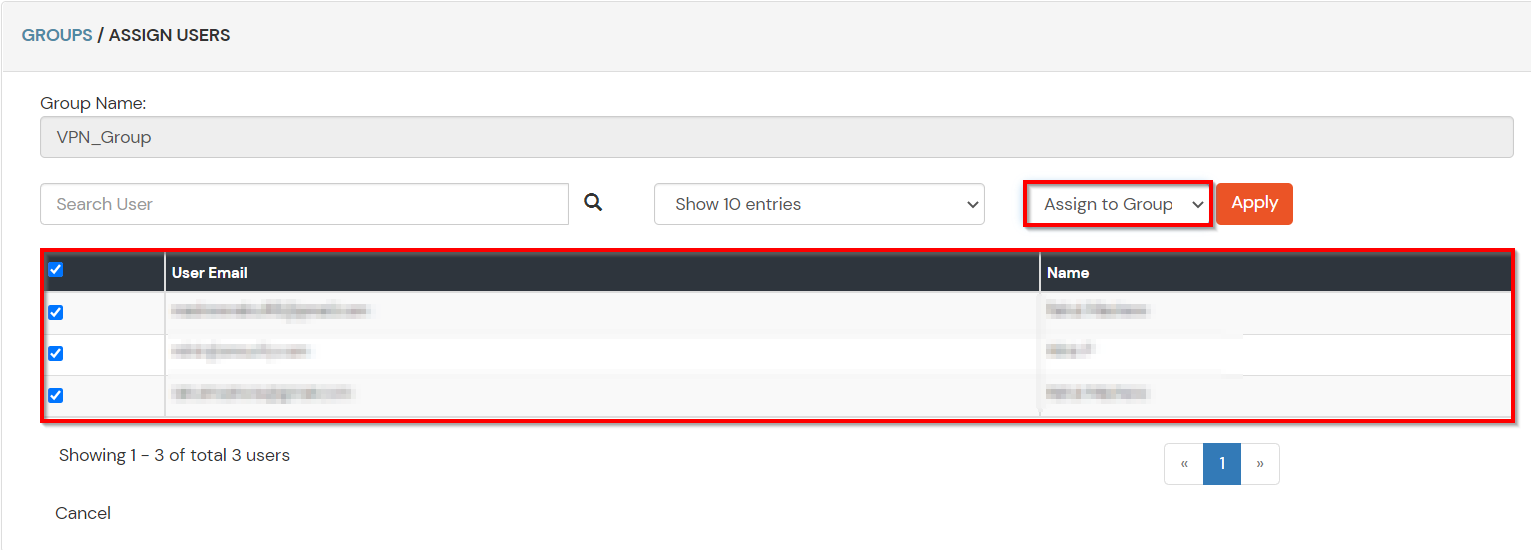
- These groups will be helpful in adding multiple 2FA policies on the applications.
4. Setup MFA for Fortinet
Note: You can follow this guide, if you want to customize and enroll MFA for end users.
- Here, we will configure a policy for the User Group that we created in this step and associate it with the Fortinet VPN Application.
- Click on Policies >> App Login Policy.
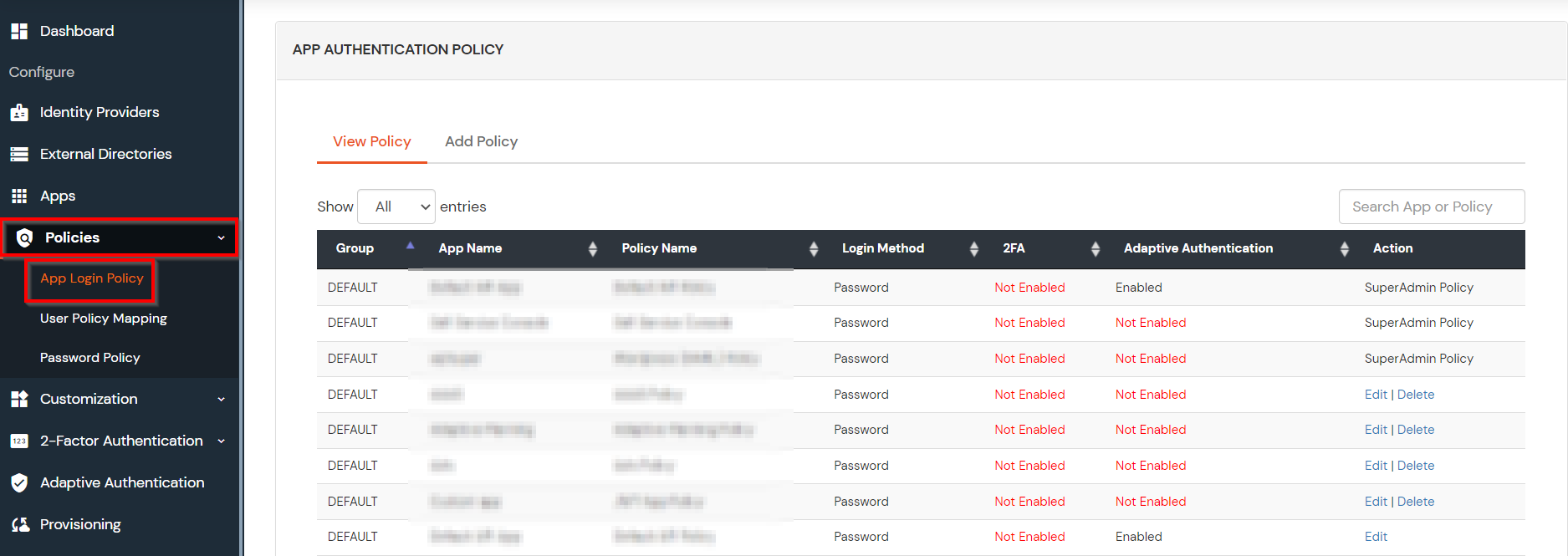
- Click on Add Policy button.
- In Application section, select the RADIUS App that we configured earlier in Step 1.
- Select the required User Group in Group Name and enter the Policy name.
- In this guide, we will configure a Password Only policy for "VPN_Group", so that only the VPN_Group members can access VPN Services without a Second Factor.
- Once done with the policy settings, click on Submit to Add Policy.
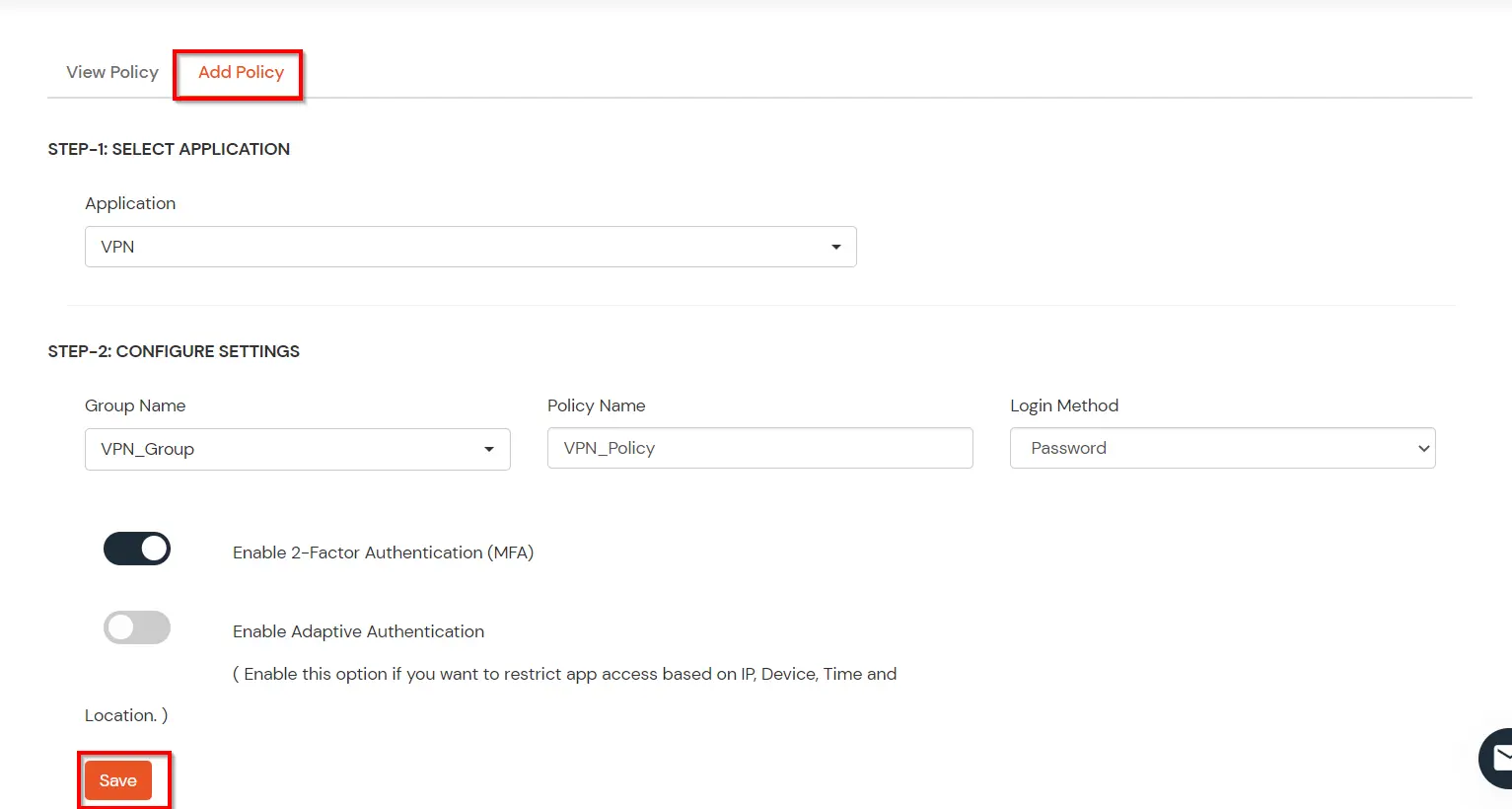
5. Test Fortinet MFA
- Download FortiClient from www.forticlient.com.
- Open the FortiClient Console and go to Remote Access > Configure VPN.
- Add a new connection:
- Set the connection name.
- Set Remote Gateway to <vpn_server_ip>.
- Select Customize Port and set it to 10443.
- Save your settings.
- Login to Forticlient and enter Username and Password.
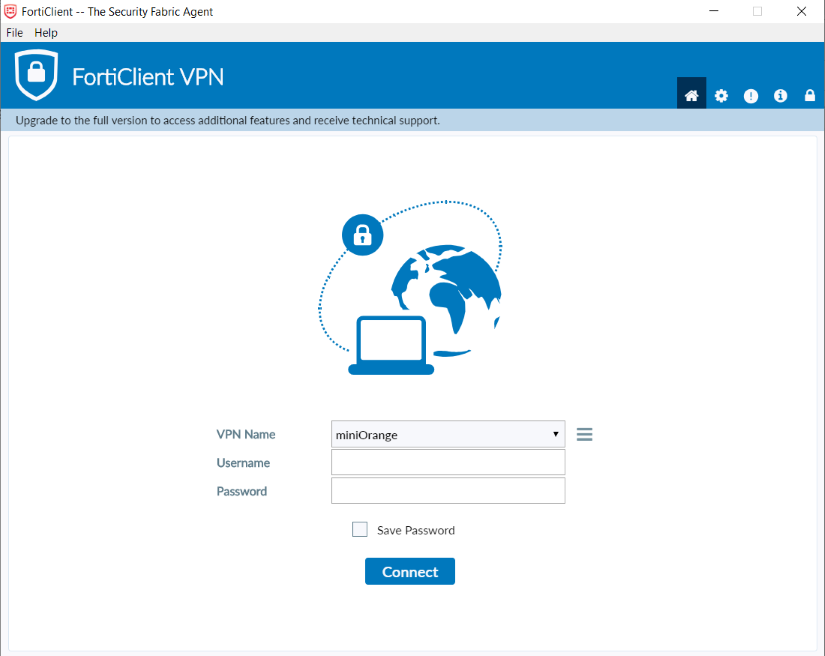
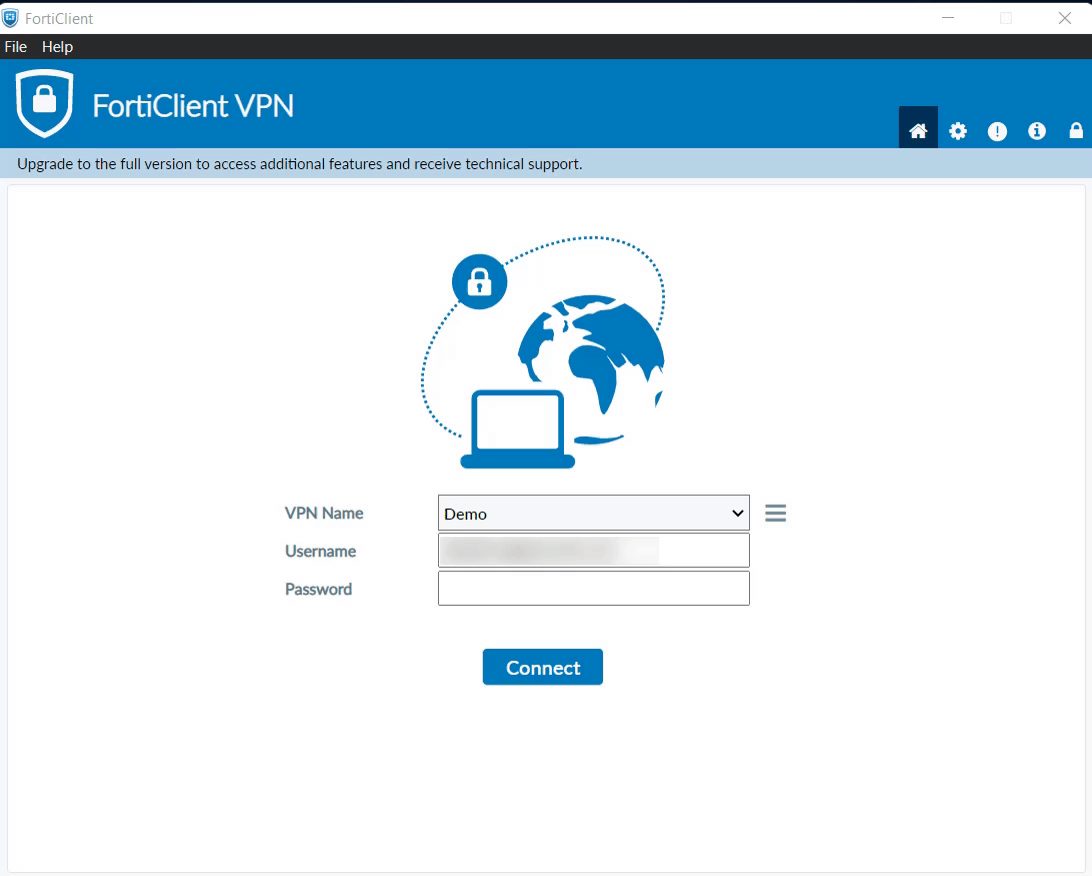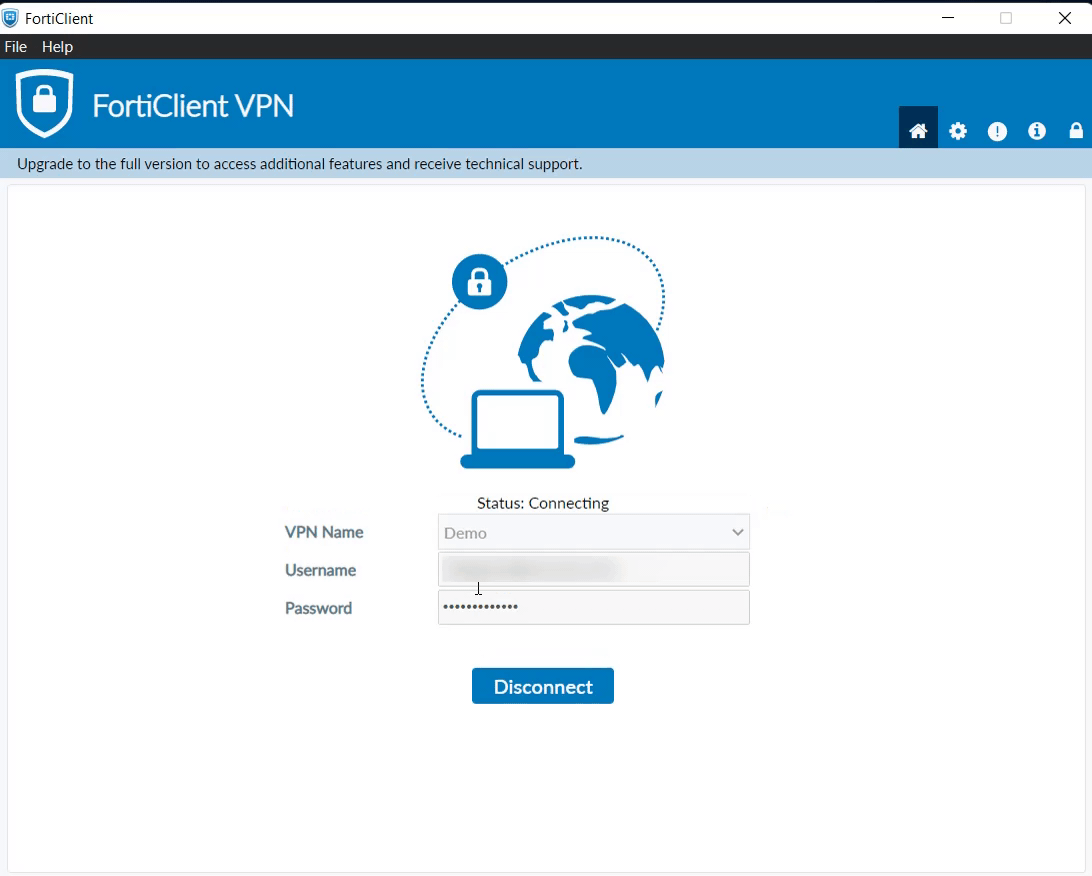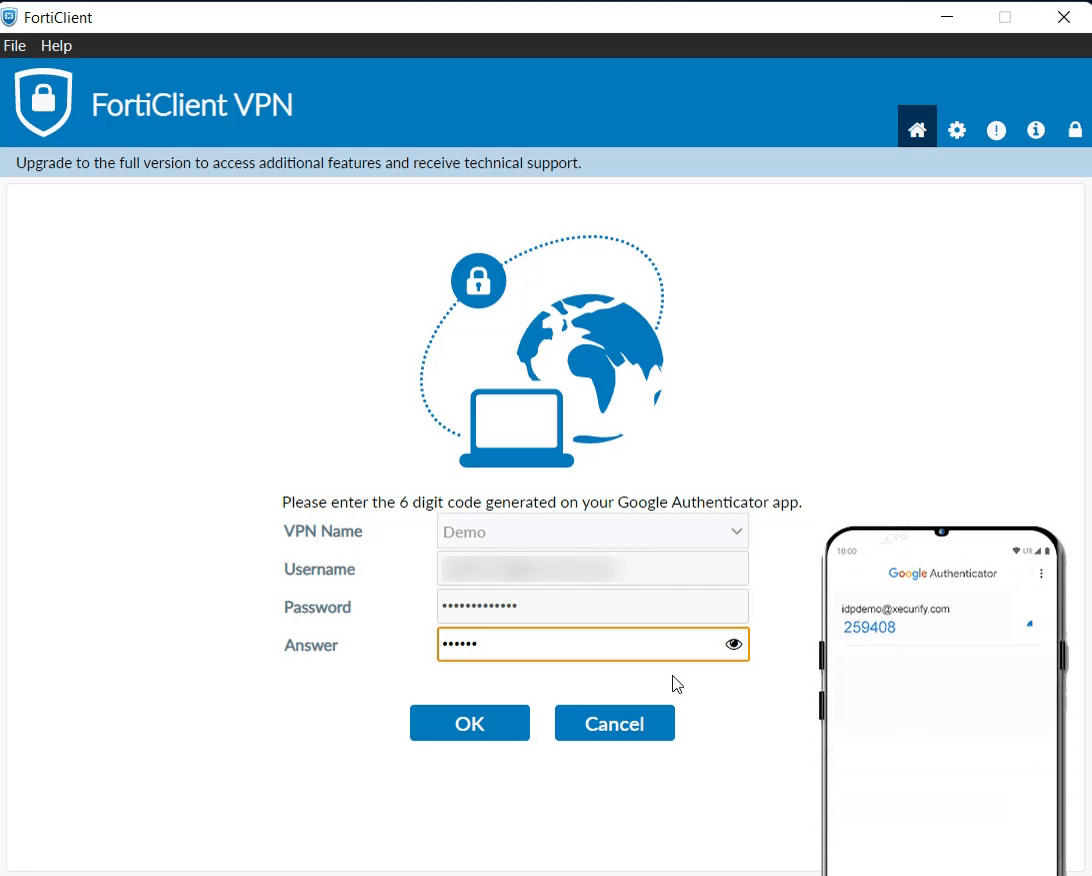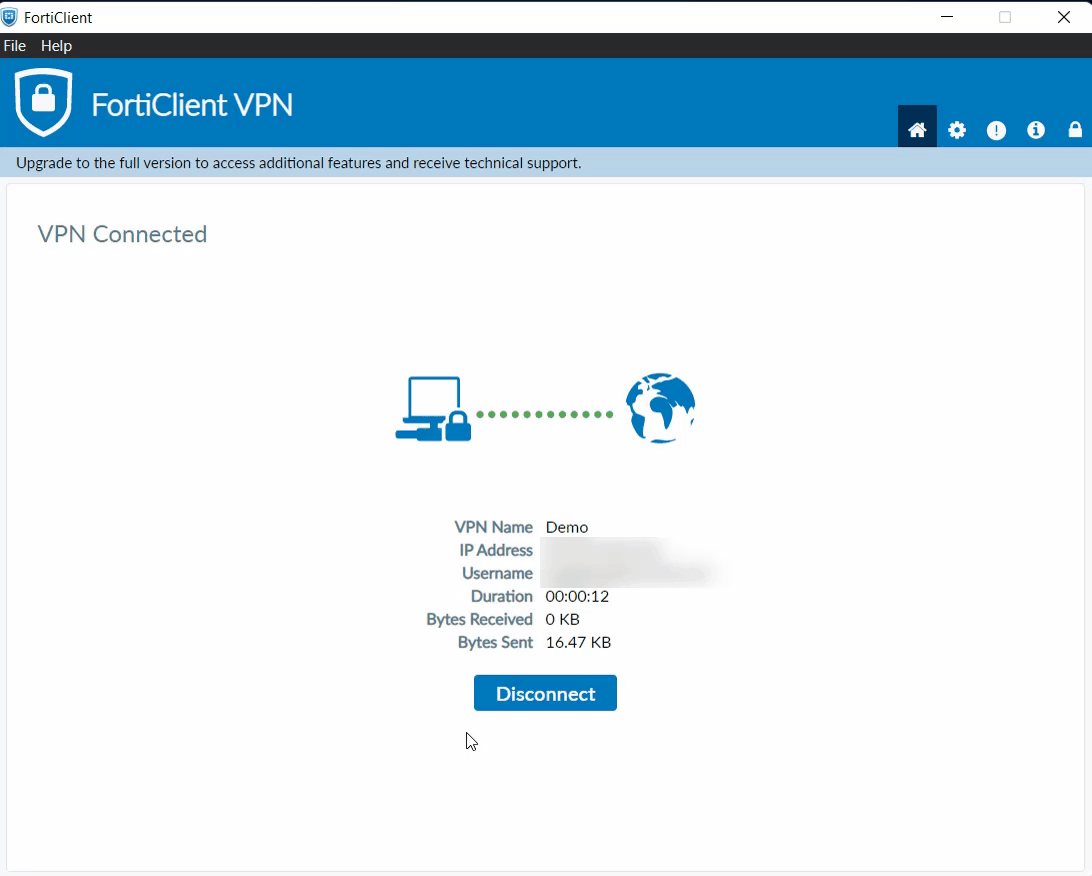
- It will prompt for a Second Factor Code if you have Enabled 2-Factor Authentication in miniOrange Policy.
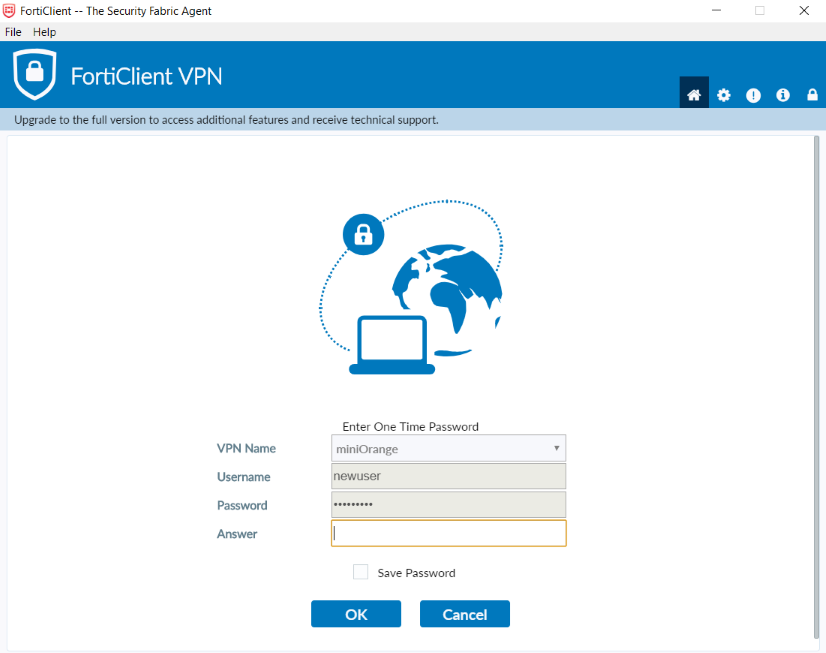
- Enter your 2-Factor Code and you should be connected to the VPN.
- NOTE: While configuring IPSec VPN connection in FortiClient make sure to use the Pre-Shared key of the IPSec Tunnel that was created LAST.
Fortinet has issues if multiple IPSec Tunnels are present at FortiGate Server.
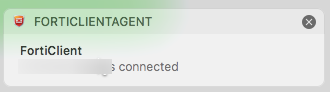
- On passing the valid credentials you can see the screen below:
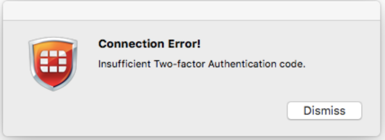
- If you enter an incorrect value you will be redirected to the below screen.
Troubleshooting
Error Message - Can't connect to Radius Server?
Cause: Either the firewall has multiple outgoing IPs or Fortinet UI is not working.
Solution: Check for the configuration and use static ip for firewall and try test authentication using CLI.
Enter the following command in CLI to test connection:
#diagnose test authserver radius <server_name> <chap | pap | mschap | mschap2> <username> <password>
Steps to setup admin 2FA:
- Login to Admin dashboard and click on CLI icon (>_).
#config user radius
edit "<server_name>"
set server "<vpn_server_ip>"
set secret SUPERSECRETPASSWORD
set auth-type <chap | pap | mschap | mschap2>
next
end
User group configuration with the Radius server user group:
#config user group
edit "radiusgroup"
set member "<server_name>"
config match
edit 1
set server-name "<server_name>"
set group-name "radiusgroup"
next
end
next
end
Local admin account configuration with the remote authentication and local backup password:
#config system admin
edit "radiusadmin"
set remote-auth enable
set accprofile "super_admin"
set vdom "root"
set remote-group "radiusgroup"
set password fortinetlocal
next
end
How can I check RADIUS User audit logs in miniOrange admin dashboard?
- Login to miniOrange Admin Dashboard.
- Click on Reports >> Radius User Authentication Report.
- Enter Enduser Identifier and Date range.
- Click on Search.
Fortinet firewall admin CLI log in asking for reset password when logging with 2FA enabled
Cause: This is because the server(from putty) does not read our 2FA challenge message.
Solution: Put received OTP in both New Password and Confirm Password.
Frequently Asked Questions (FAQs)
How to enable MFA on Fortinet VPN?
In the miniOrange Admin Console, add Fortinet VPN as a RADIUS client and connect it to your user directory. Choose the MFA techniques you want to use in miniOrange and turn them on. Set miniOrange up as the FortiGate RADIUS server. When individuals connect to the VPN, they will need to supply a second piece of information to prove who they are.
How to enable MFA authentication?
To turn on MFA for users or admins, log in to miniOrange and go to the 2-Factor Authentication settings. You can choose how you want to prove your identity, for as by SMS, email, or an authenticator app. When users log in, they will be requested to sign up. Everyone in the firm or just one person may obey the rules.
How to enable MFA in FortiGate?
Add FortiGate as an app in miniOrange using RADIUS. In FortiGate's authentication settings, provide the details for the miniOrange RADIUS server. Set the VPN login timeout to the time that is shown. Give users or groups MFA as needed to control who can access what.
Can I use Google Authenticator for FortiGate?
Yes, miniOrange works with both Google Authenticator and FortiGate. People can register their device with miniOrange and then use Google Authenticator's time-based OTPs to connect to their VPN.
What are different 2FA methods for Fortinet supported by miniOrange?
miniOrange supports push notifications, soft tokens, authenticator apps (like Google Authenticator, Microsoft Authenticator, and miniOrange Authenticator), one-time passwords given via SMS or email, hardware tokens (like YubiKey), and phone verification. Admins can choose which rules to use and how to use them based on what the business needs.
Further References