AWS SCIM Automatic Provisioning and Deprovisioning
AWS SCIM Automatic Provisioning allows to create account in a simplified and automated way to link AWS user's account to their existing or new third party apps. AWS SCIM Provisioning automates user provisioning with their identities across the applications where users need access to. Enable automatic provisioning in Amazon Web Services (AWS) Identity center for users using Active Directory credentials.
Automated User Provisioning saves time when setting up new users and teams, and also manages access privileges through user lifecycle managemnet. miniOrange can create, read, and update user accounts for new or existing users, remove accounts for deactivated users, and synchronize attributes across multiple user stores.
AWS SCIM User provisioning and deprovisioning actions are bi-directional, so you can create accounts inside an external application and import them into miniOrange, or alternatively create the accounts in miniOrange and then push them out to any linked external applications.
AWS SCIM automatic Deprovisioning means deleting a user and removing their access from multiple applications and network systems at once. Deprovisioning action is triggered when an employee leaves a company or changes roles within the organization. The deprovisioning features increase your organization's security profile by removing access to sensitive applications and content from people who leave your organization.
Automatic Provisioning & Deprovisioning Scenarios for Amazon Web Services (AWS) Identity center
miniOrange provides Provisioning solutions for all scenarios of user management (provisioning), which includes AD Integration, LDAP Integration and automated provisioning for all External Applications such as AWS SCIM, Google Workspace, Workday, Salesforce, Microsoft apps, etc.
Follow the step-by-step guide given below to setup Automated AWS SCIM Provisioning
1. Setup Provisioning for AWS SCIM
- Open the AWS SSO Console.
- Choose Settings in the left navigation pane.
- On the Settings page, under Identity source, next to Provisioning, choose Enable automatic provisioning. This immediately enables automatic provisioning in AWS SSO and displays the necessary endpoint and access token information.
- In the Inbound automatic provisioning dialog box, copy each of the values for the following options. You will need to paste these in later when you configure provisioning in your IdP.
a. SCIM endpoint
b. Access Token
- Choose Close.
2. Add SCIM Configuration for AWS application in miniOrange
- Login into miniOrange Admin Console.
- Click on Apps from the left-side navigation bar. Then click on Add Application.
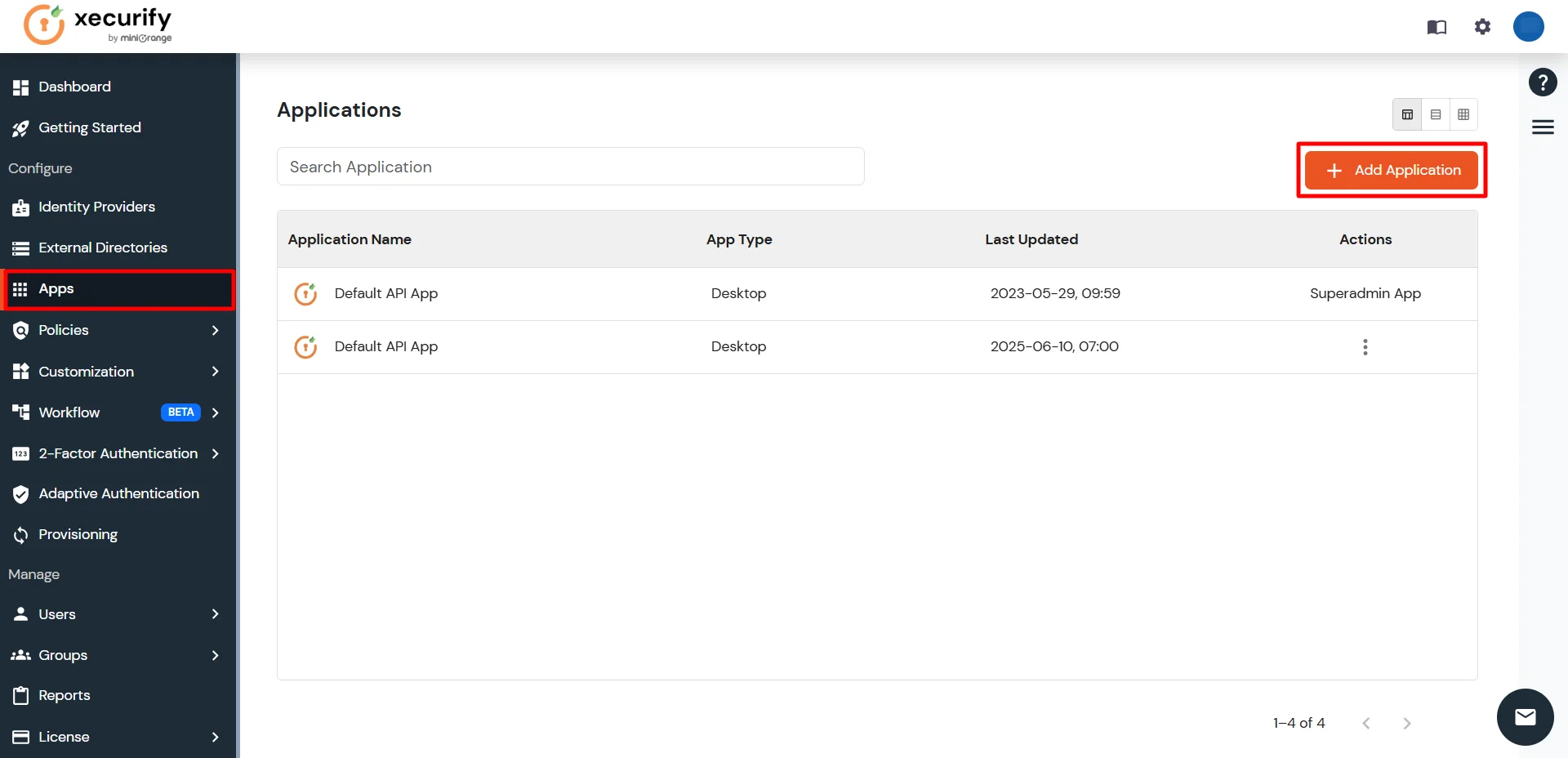
- In the Choose Application section, select Provisioning from All Apps dropdown.
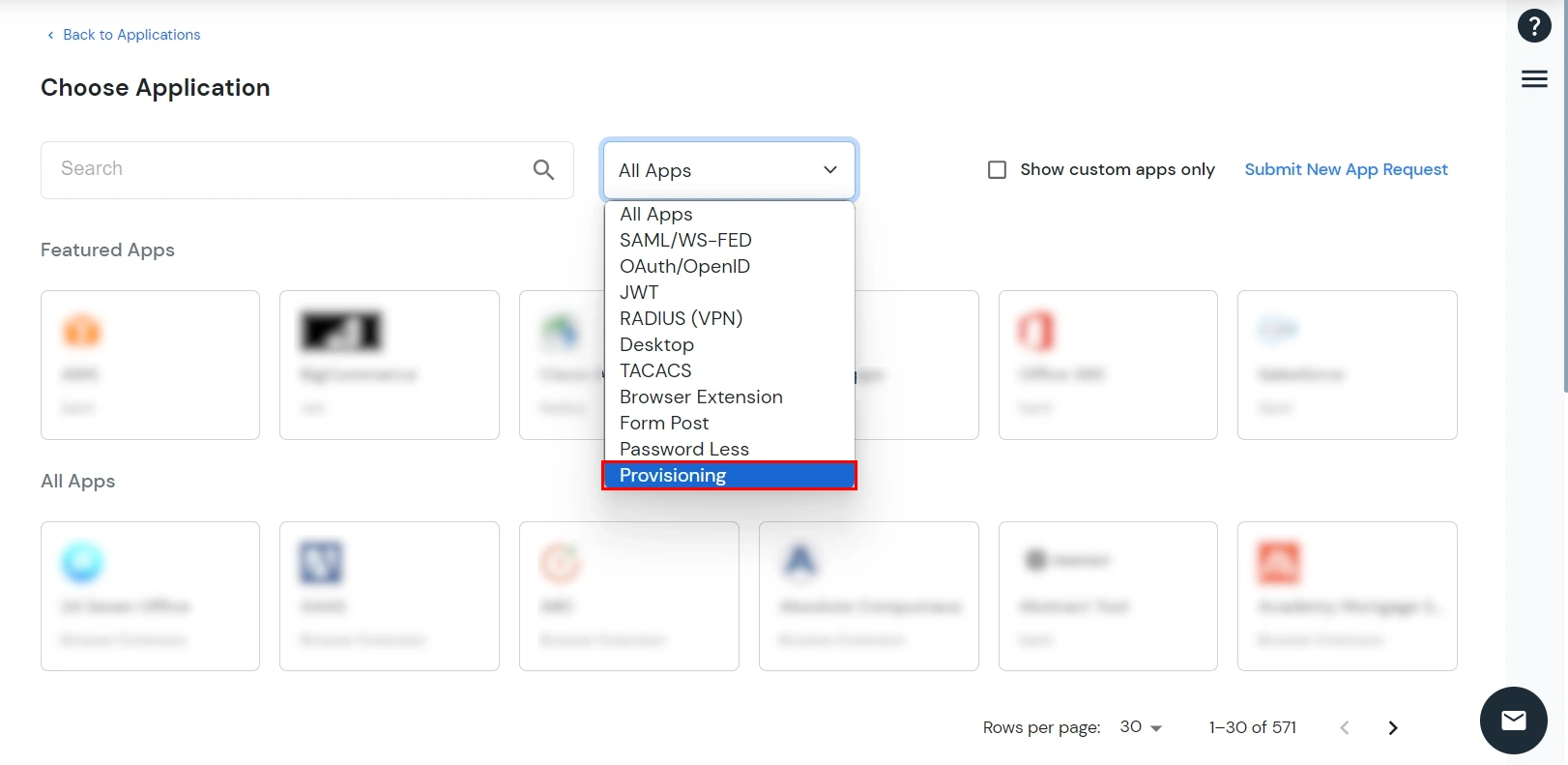
- Search for AWS in the search bar and select the AWS Sync application.
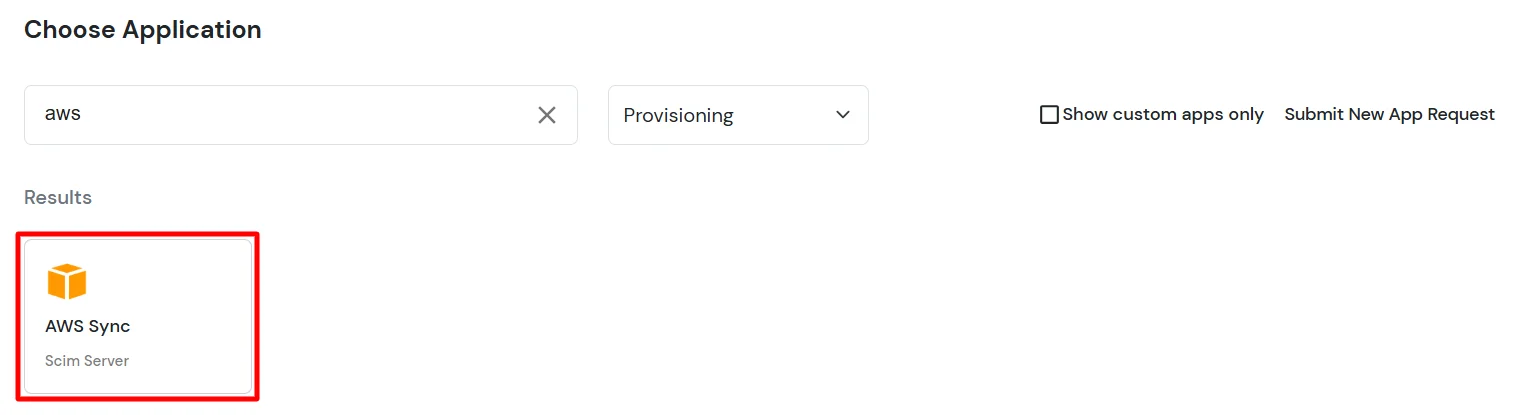
- Under Basic Settings, enter Display Application Name and click Save to add the app.
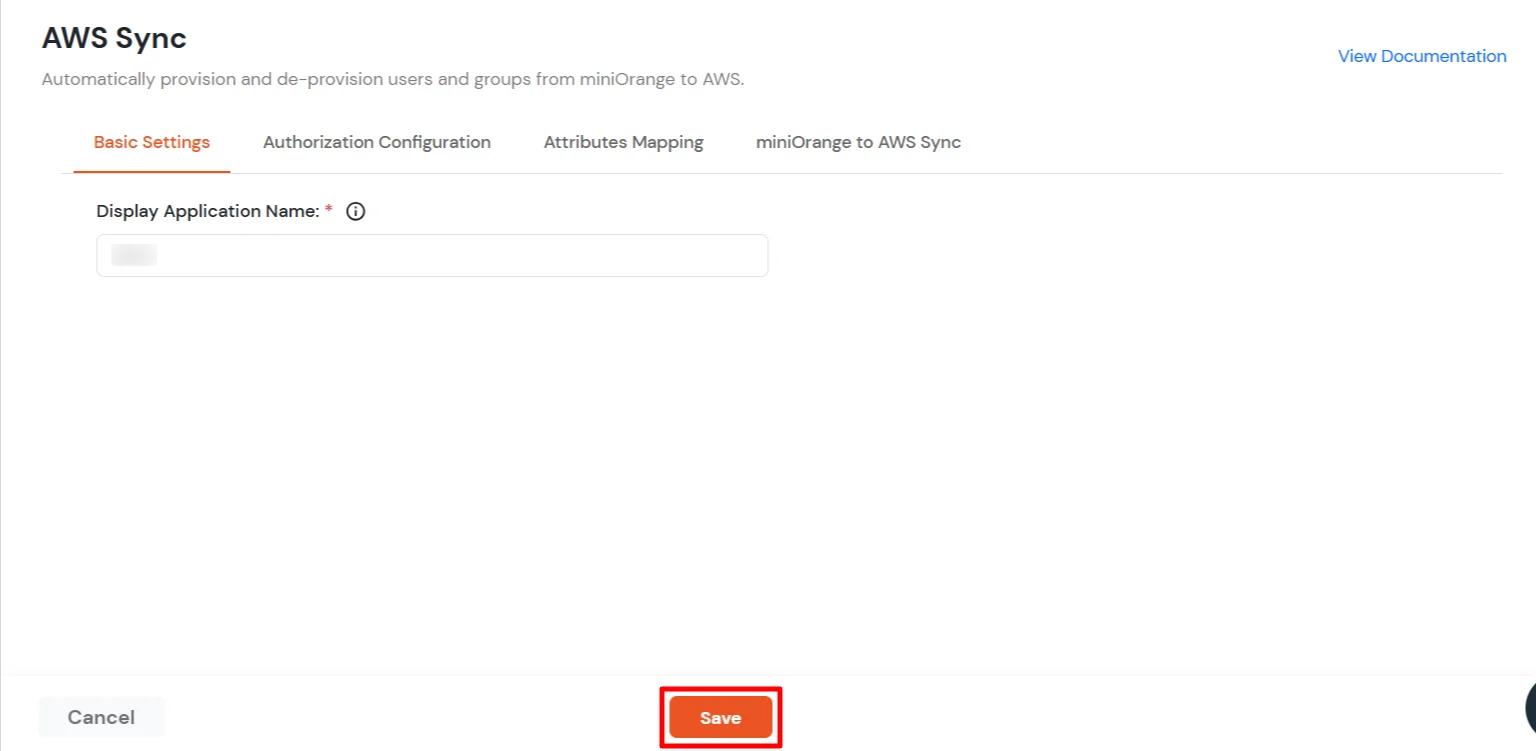
- In the Authorization Configuration enter the SCIM Base URL and Bearer Token that you got in Step 1.
- Click on Test Connection to verify details.
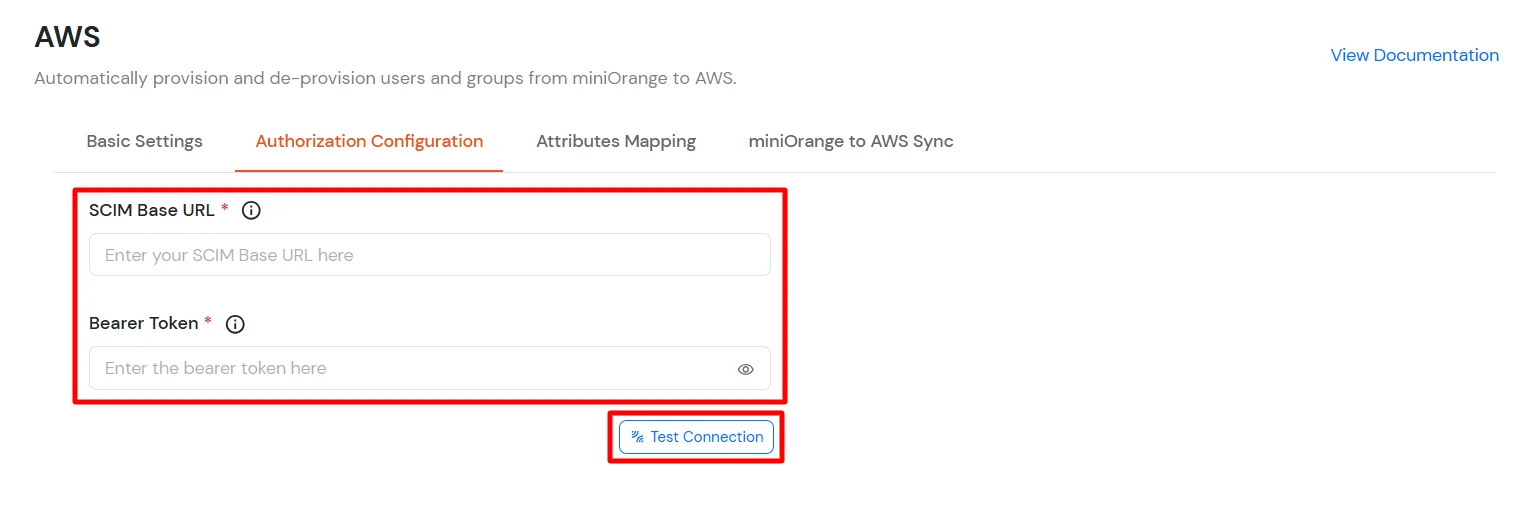
- Then, click Save & Next button.
3. Attribute Mapping
- Navigate to the Attributes Mapping tab in your AWS provisioning configuration.
- Under this tab, you'll find two sections: Users and Groups, where you can map miniOrange attributes to AWS attributes for synchronization.
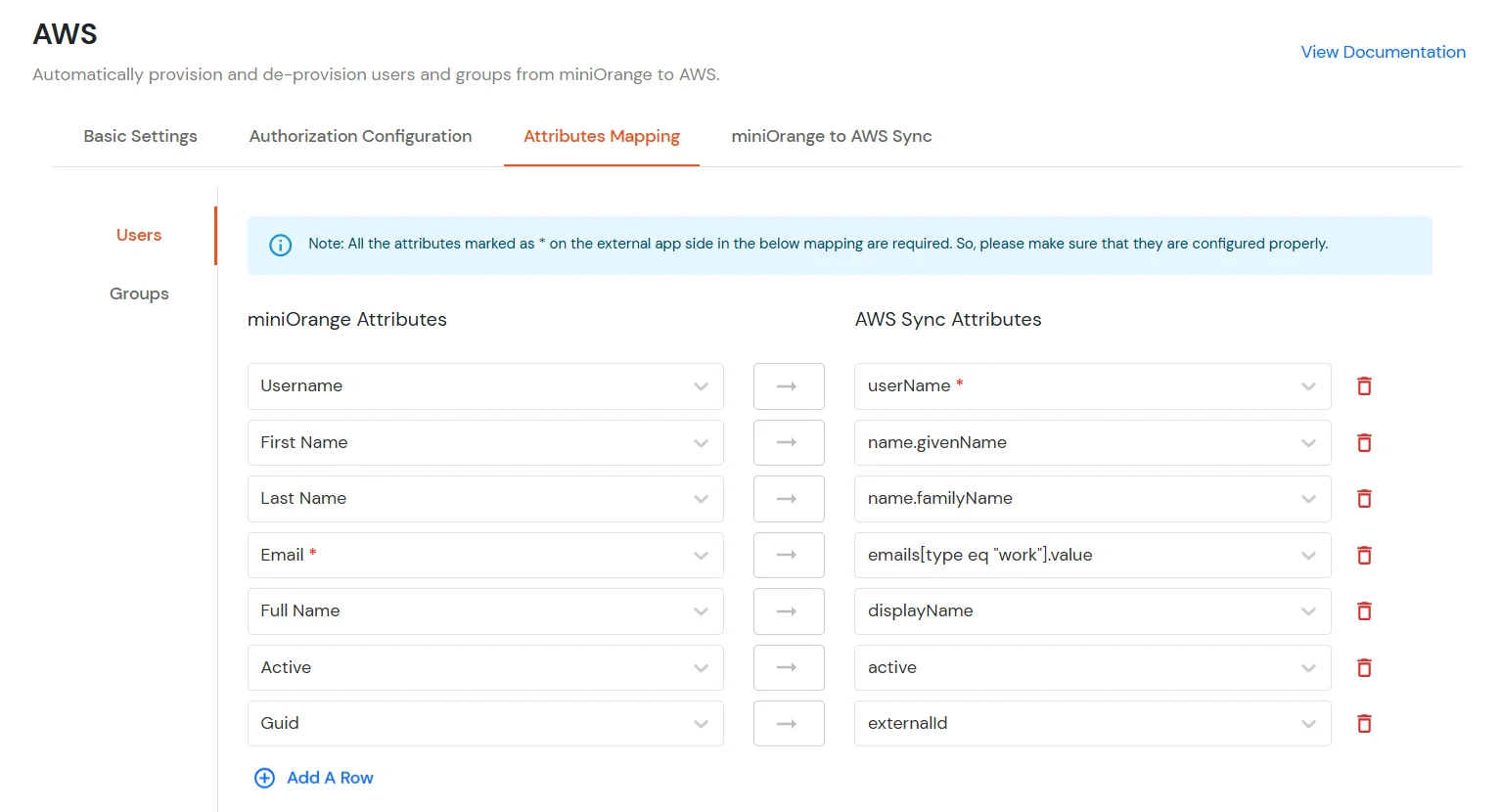
Users Mapping:
Note: The userName, name.givenName, name.familyName, emails[type eq \"work\"].value, displayName and active fields are required for AWS SCIM integration.
- In the Users section, map the attributes from miniOrange Attributes to the corresponding AWS Sync Attributes.

- Once all required mappings are configured, click the Save & Next button to proceed.
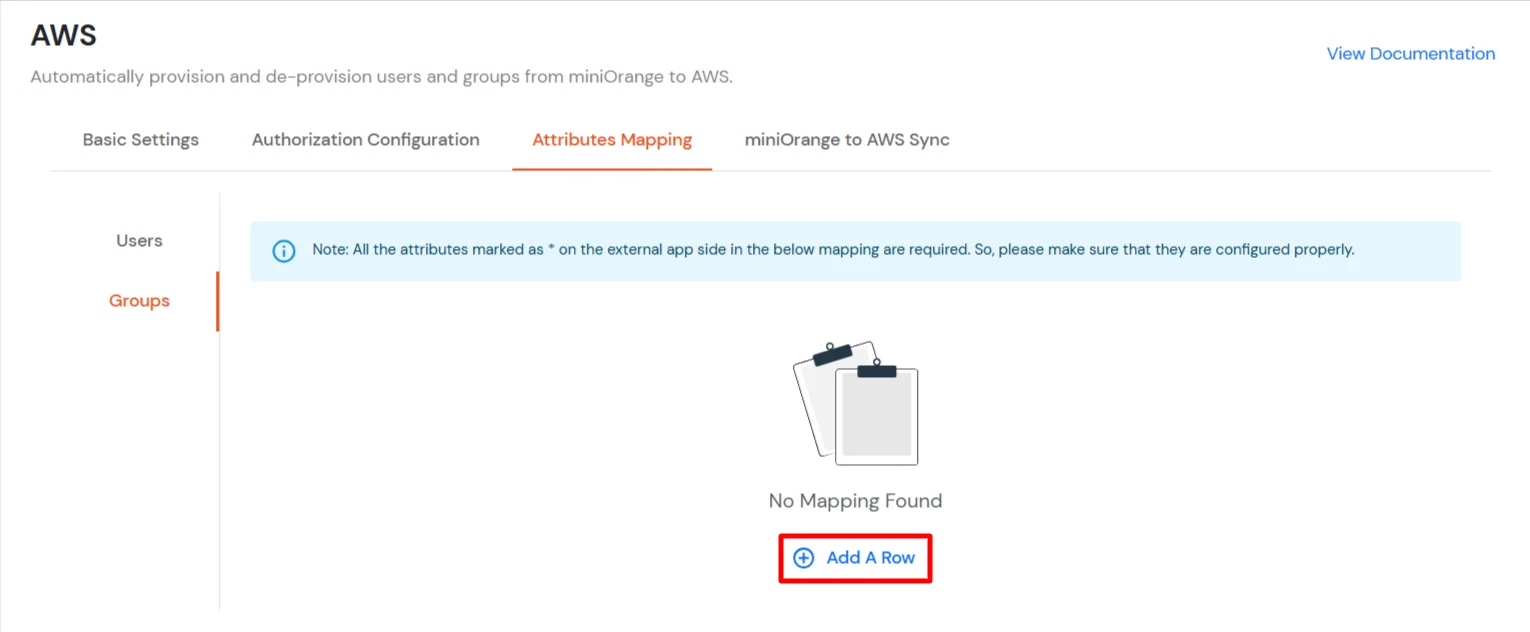
Groups Mapping:
Note: If you don't need group provisioning, skip this step.
- Click on the Groups tab.
- Click Add A Row to add a new mapping.
- From the miniOrange Attributes dropdown, choose an attribute (like Group Name).
- In the AWS Sync Attribute field, type the AWS attribute (like displayName).
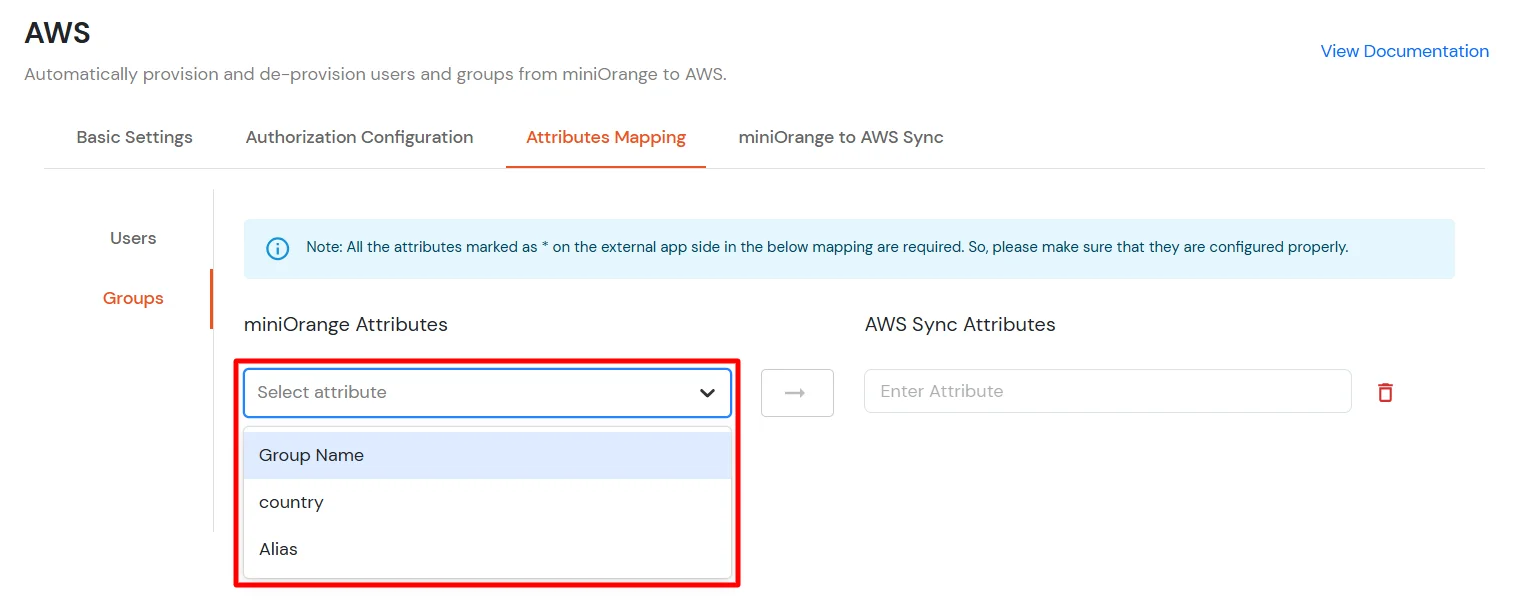
- Click Save & Next when done.
4. miniOrange to AWS Sync
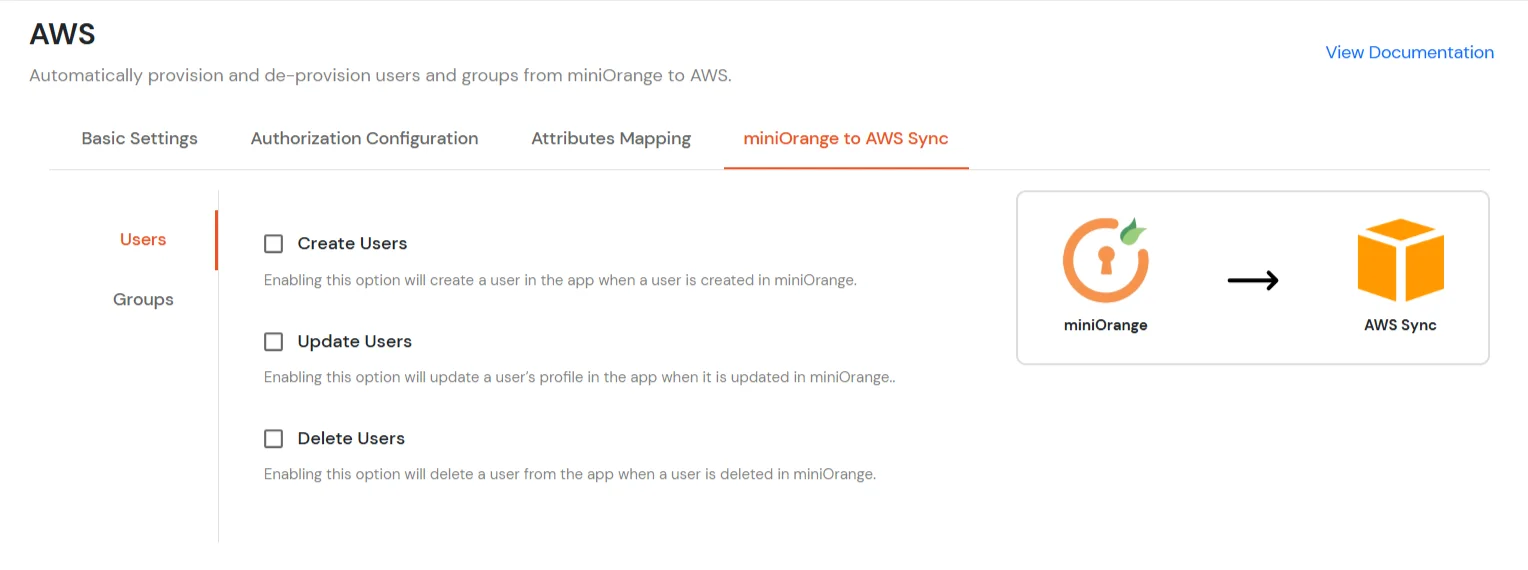
- In the miniOrange to AWS Sync tab, there are two sections: Users and Groups. Each section contains a list of attributes and their functions when enabled. You can enable or disable them as needed.
|
Attribute |
Description |
| Users |
Create Users |
Enabling this option will create the user in the selected application upon user creation in miniOrange. |
| Update Users |
Enabling this option will update the user profile in the selected application if updated in miniOrange. |
| Delete Users |
Enabling this option will delete the user from the selected application if the user is deleted from the miniOrange. |
|
Attribute |
Description |
| Groups |
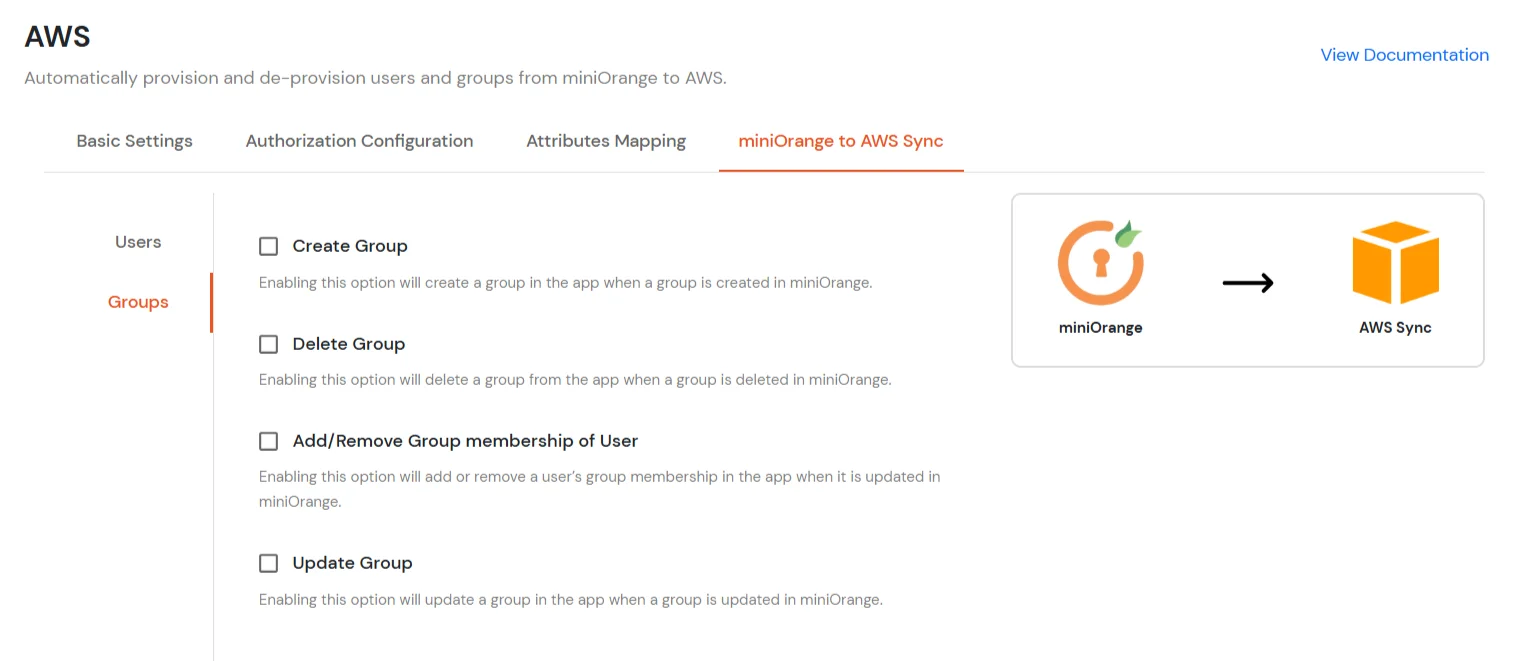
Create Group |
Enabling this option will create the Group in the selected application upon Group creation in miniOrange. |
| Delete Group |
Enabling this option will delete the Group from the selected application if the Group is deleted from the miniOrange. |
| Add/Remove Group membership of User |
Enabling this option will add/remove the Group membership of a user from the selected application if the respective user group membership is updated from the miniOrange. |
| Update Group |
Enabling this option will update the Group in the selected application upon Group updation in miniOrange. |
- Click Save to apply these changes.
5. Create Group
To create a group, follow these steps:
- Go to the Manage Groups section in the Groups tab, located on the left side and click on Create Group Button.
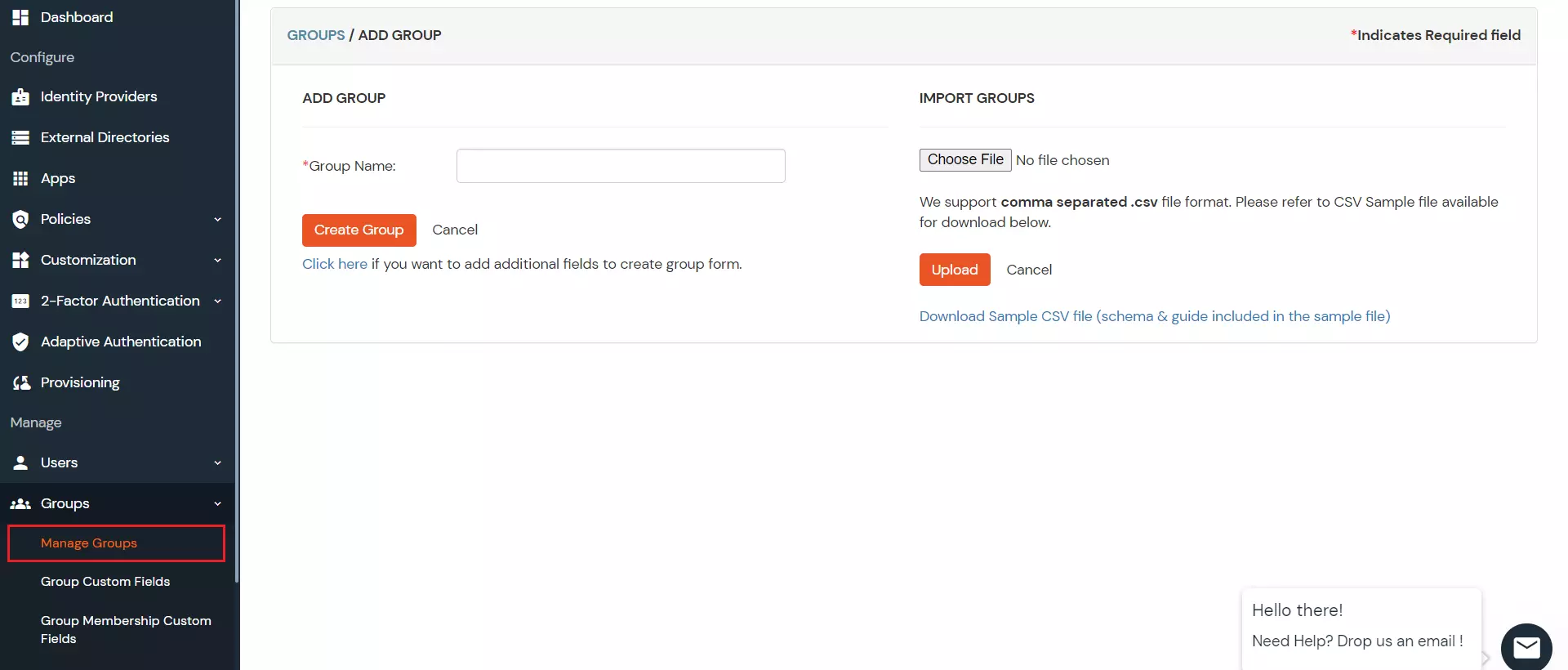
- Enter the Group Name and click the Create Group button.
- You will be redirected to the Groups List Screen when you can see the newly created group.
6. App Policy (Provision Group to AWS Sync App)
- Go to the App Login Policy section under Policies, and click Add Policy.
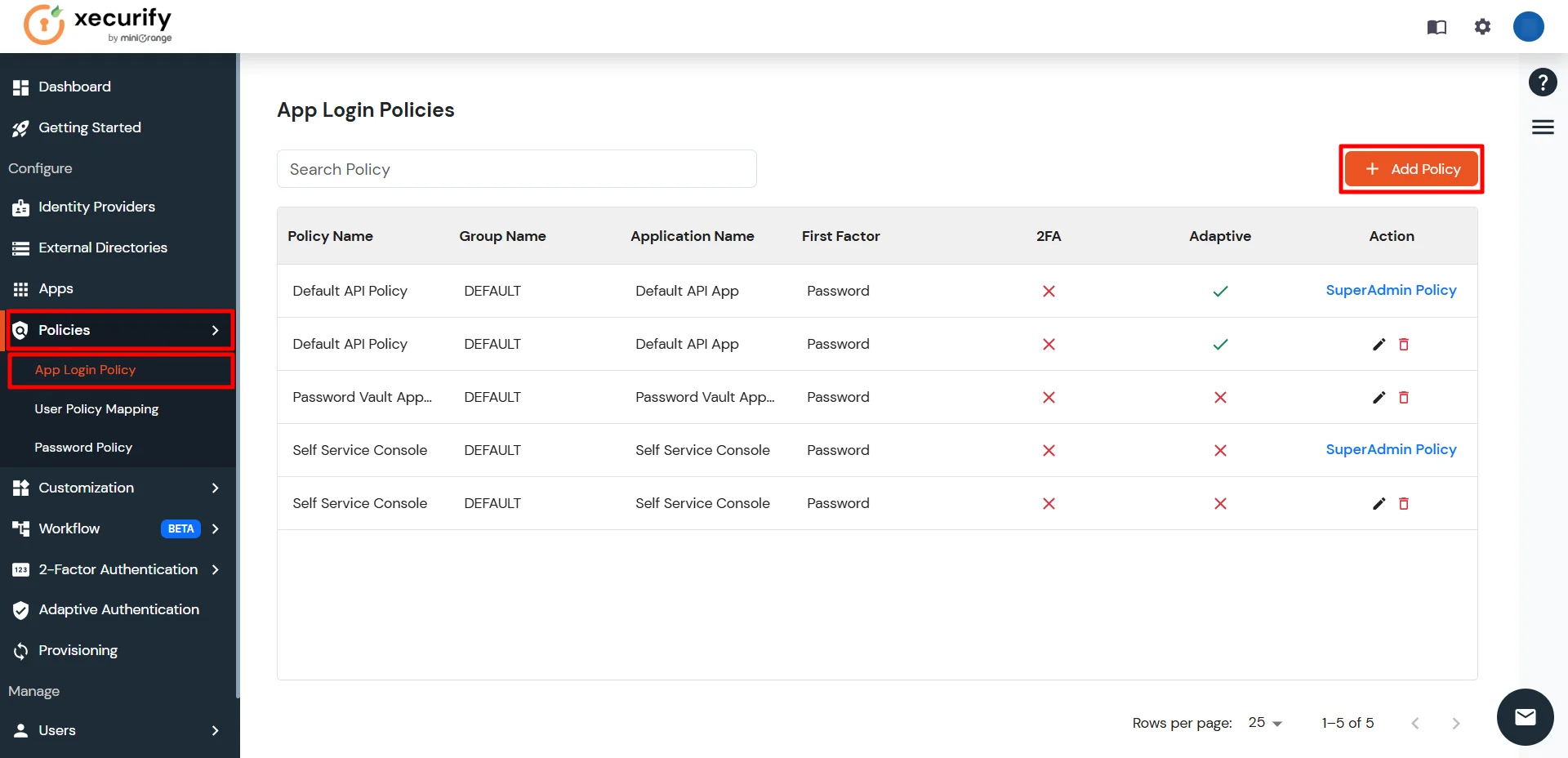
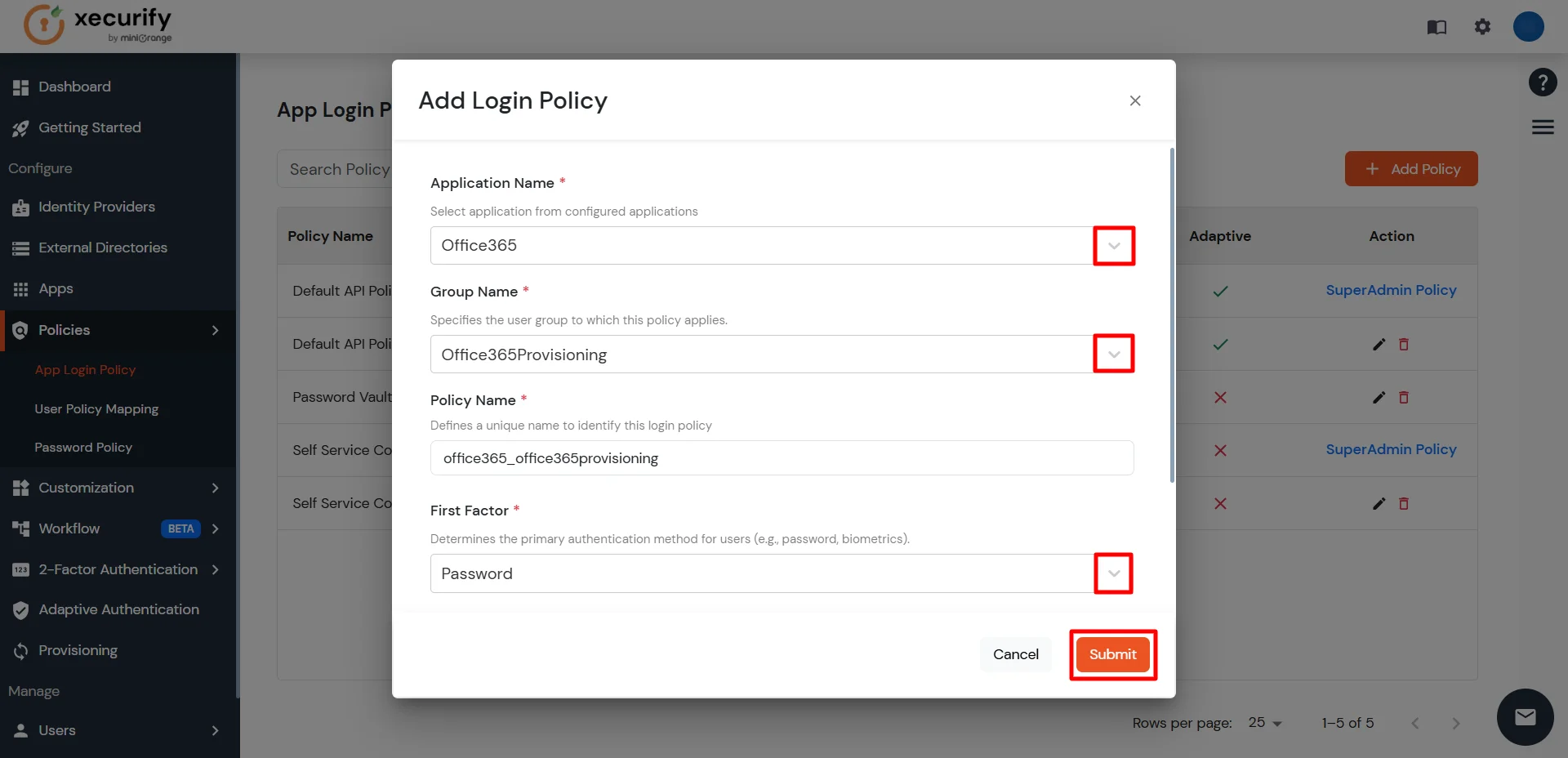
- Select the application you configured in the Apps tab (for example: AWS).
- Enter the Group Name you created (for example: AWSProvisioning).
- Enter a Policy Name of your choice (for example: AWSProvisioningPolicy).
- Click on Submit button to create a policy.
- You will receive a success notification upon policy creation, and the policy will be displayed in the App Login Policy section of the Policies tab.
- Provisioning configuration is complete now.
- Now, we can verify whether provisioning is working as expected.
- Go to the Manage Groups section under the Groups tab.
- Locate the group you created (e.g., AWSProvisioning), click Select, and then choose Assign Users.
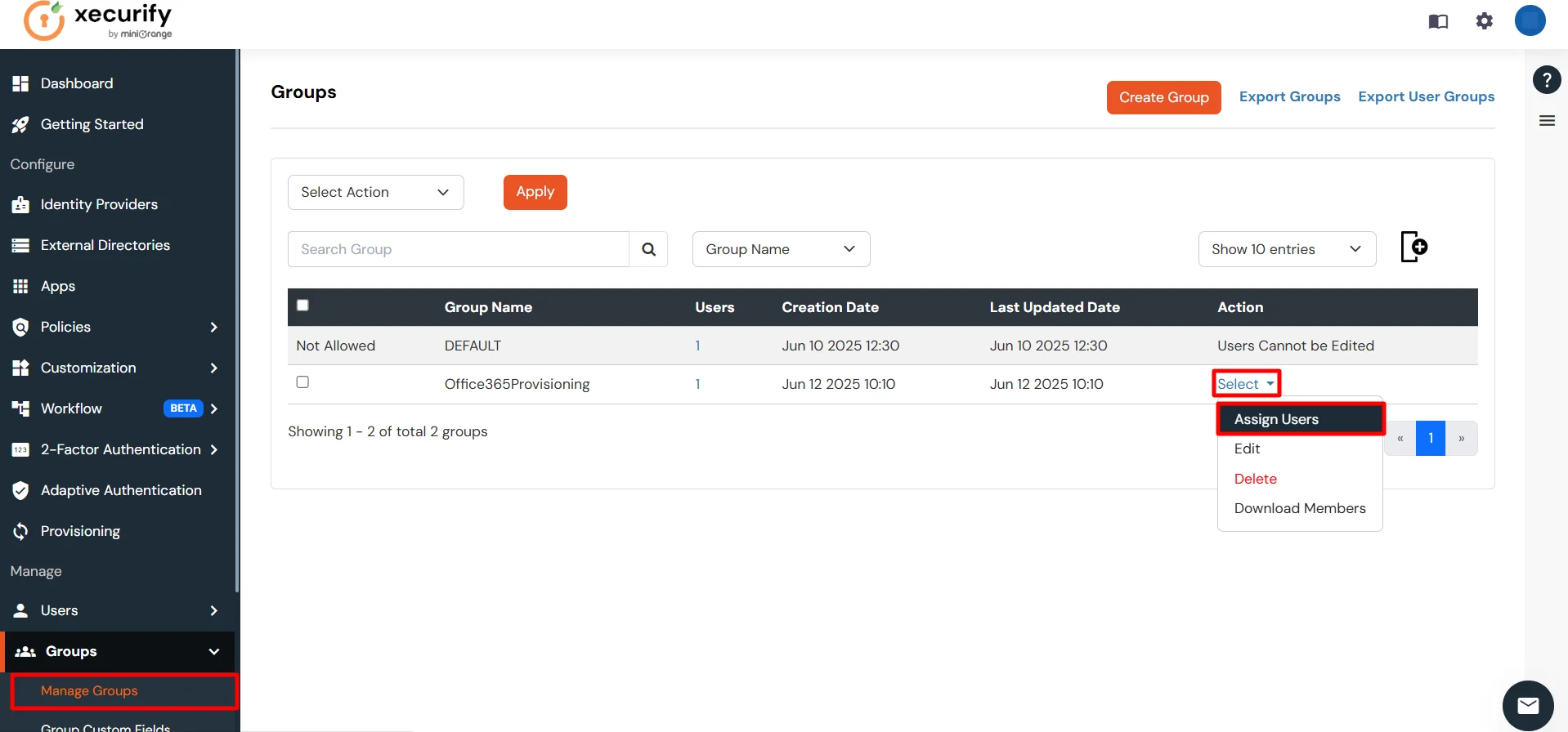
- Ensure that users are already present in miniOrange or import them into the user list. This allows you to assign the user you want to provision in AWS.
-
From the list below, select the user you want to provision, choose the Assign to Group option, and click Apply. This will automatically create the user in AWS services.
Note: Assign users to a group that contains the authorized domain names for the configured application.
To view the authorized domains, go to the Authorization Configuration section of the application you configured in the Apps tab.
Only users whose email addresses match one of the authorized domains will be provisioned.
- Select the users whose email addresses belong to an authorized domain, then click Assign to Group, and finally click the Apply button.
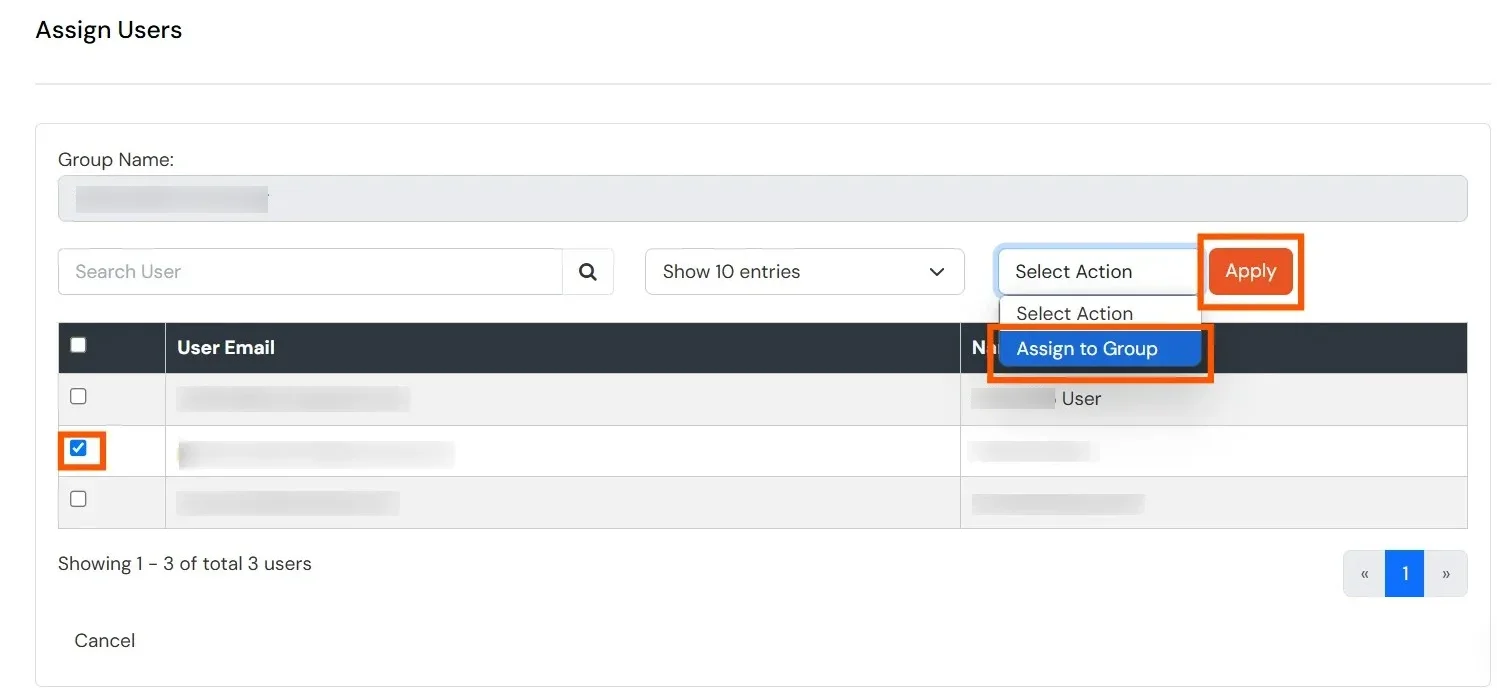
- Users are automatically created in AWS services.
- To update a user, go to the User List, select the user you want to update, click Select, and then choose Edit.
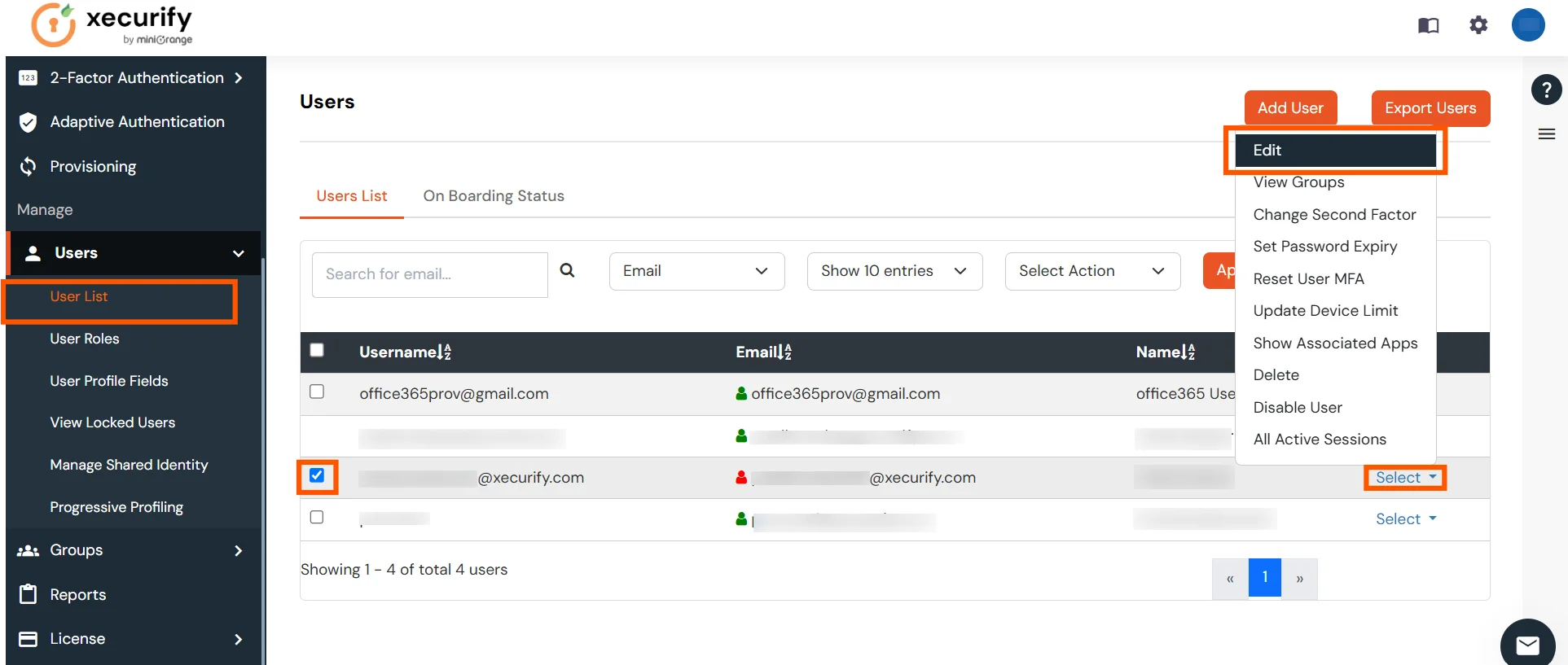
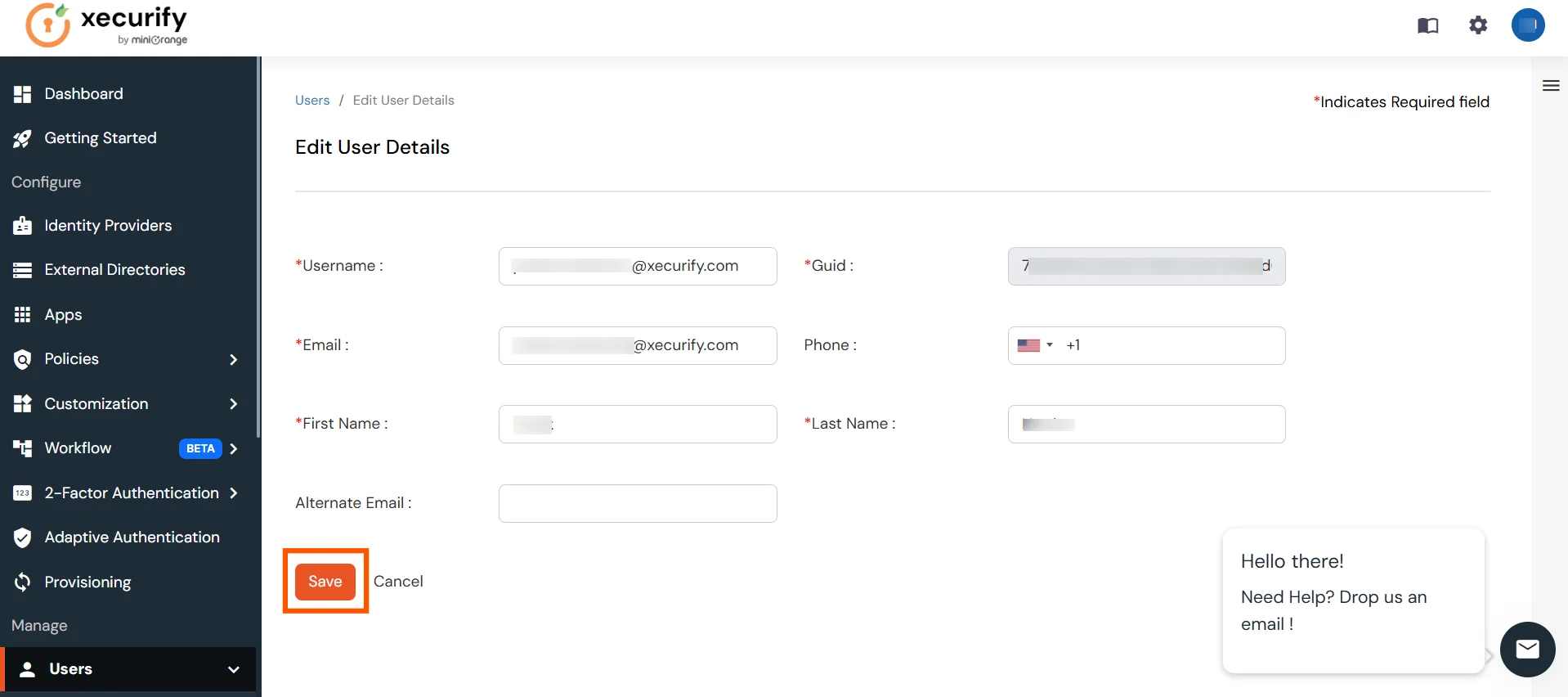
- After updating the user, click the Save button. This will automatically update the user in AWS services.
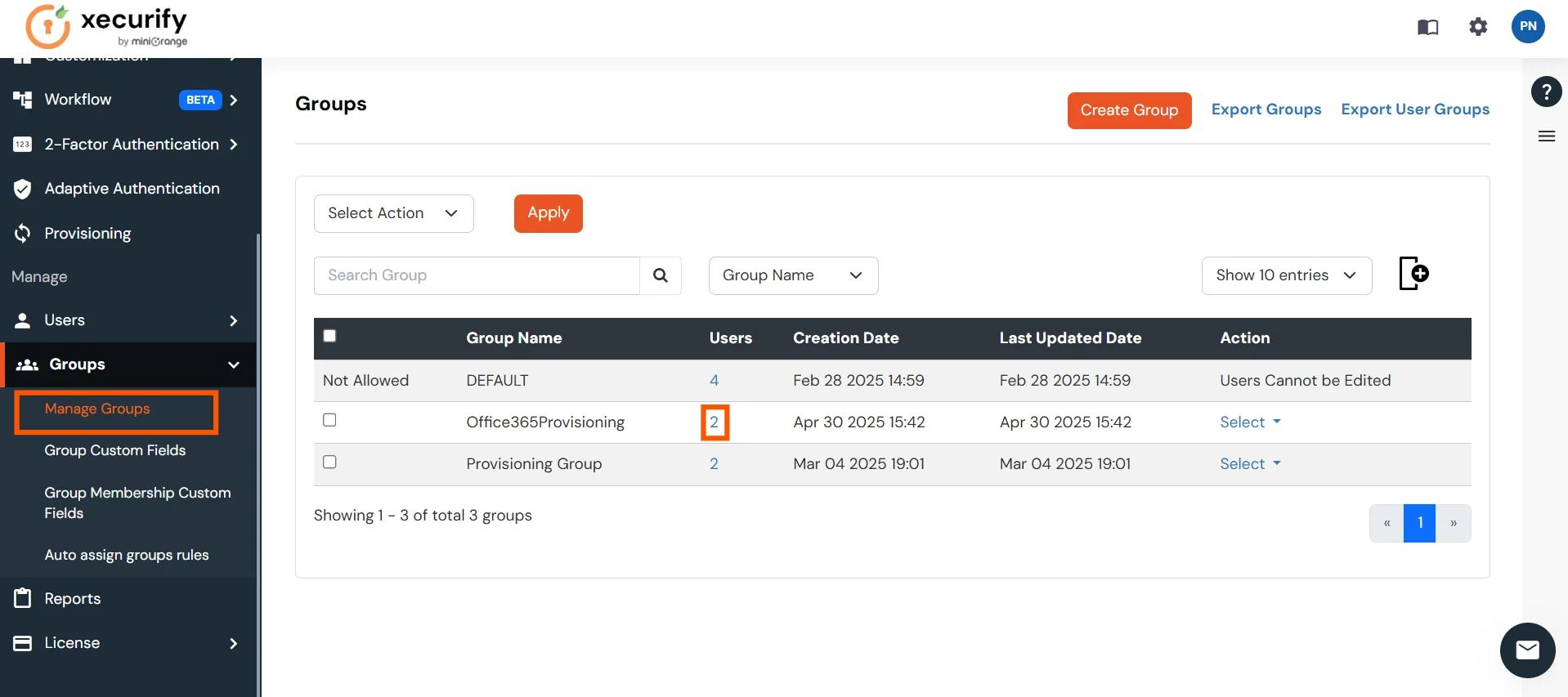
- To delete a user, go to the Manage Groups section of the Groups tab. Then, navigate to the group from which the user needs to be deleted. In the Users column, click on the displayed number of users.
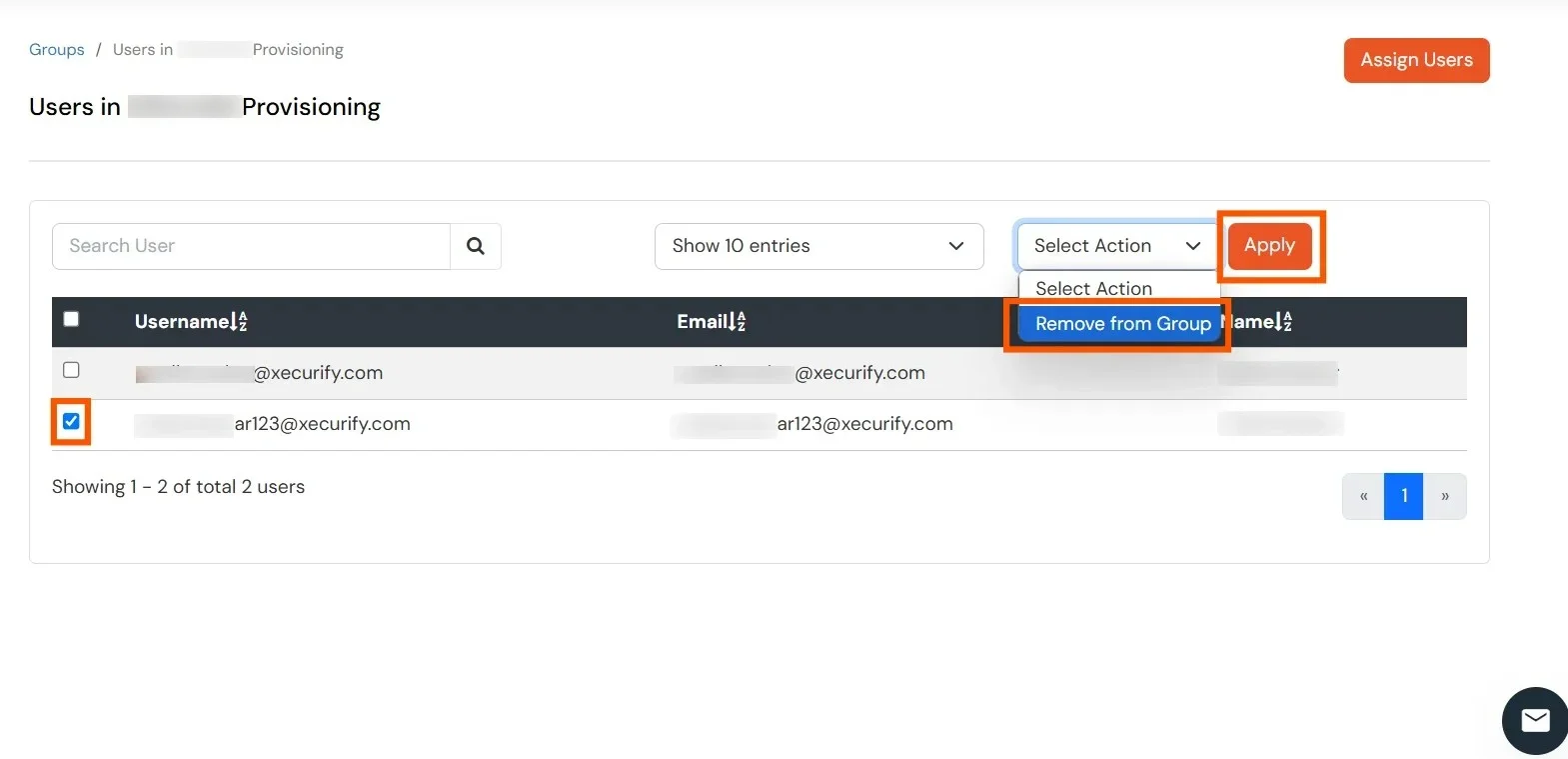
- Select the user you want to delete, choose Remove from Group as the action, and click the Apply button. This will automatically remove the user from AWS services as well.
View Provisioning Reports
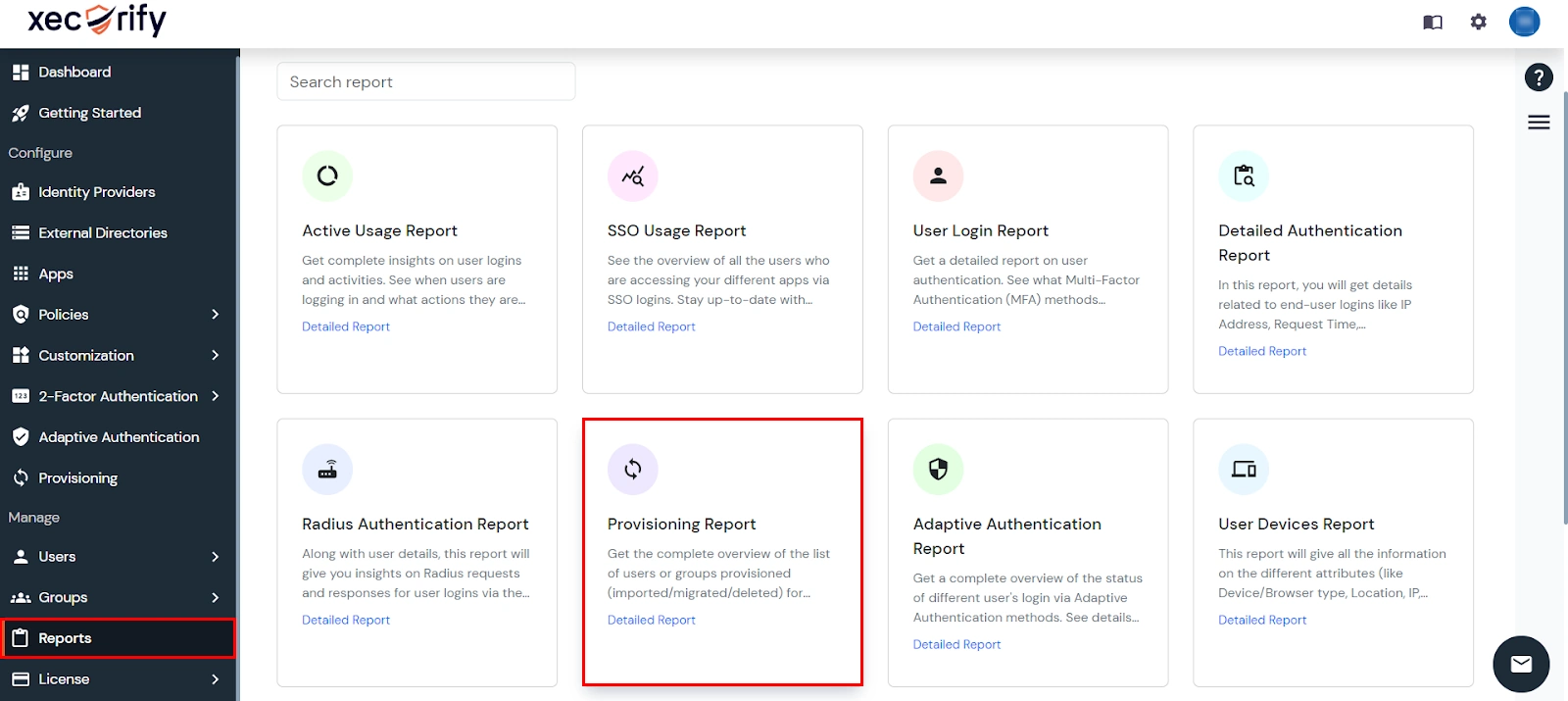
How to access Provisioning Reports?
- Navigate to Reports in the left-hand navigation pane, search for Provisioning, and select Provisioning Report.
- Filter the reports by specifying Enduser Identifier and Application Name criteria. Additionally, choose the desired timespan for the reports. Once done, click on the Search.
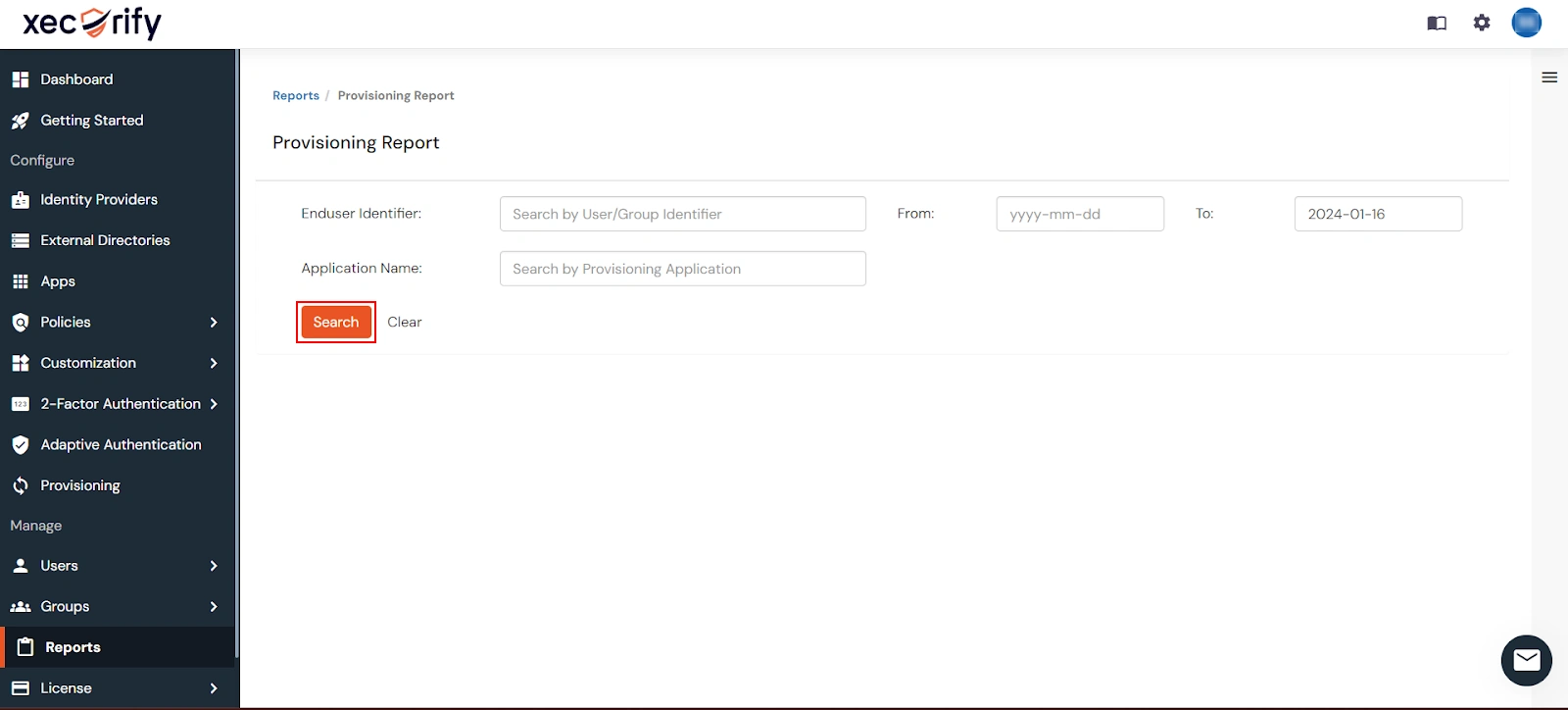
- Alternatively, you can directly click on Search to retrieve all provisioning reports based on time without applying any specific filters.
External References























