Need Help? We are right here!
Search Results:
×HTTP Header-based authentication provides user agent authentication to access backend applications and on-premise apps, where the information is sent through the HTTP headers. In the Header URL, the HTTP header section contains the authentication parameters that are configured to set the Header Based Authentication for on-premise apps.
This solution work for backend legacy apps and resources, where the admin needs to provide remote access to on-premise apps with ease, and without installing third-party software.
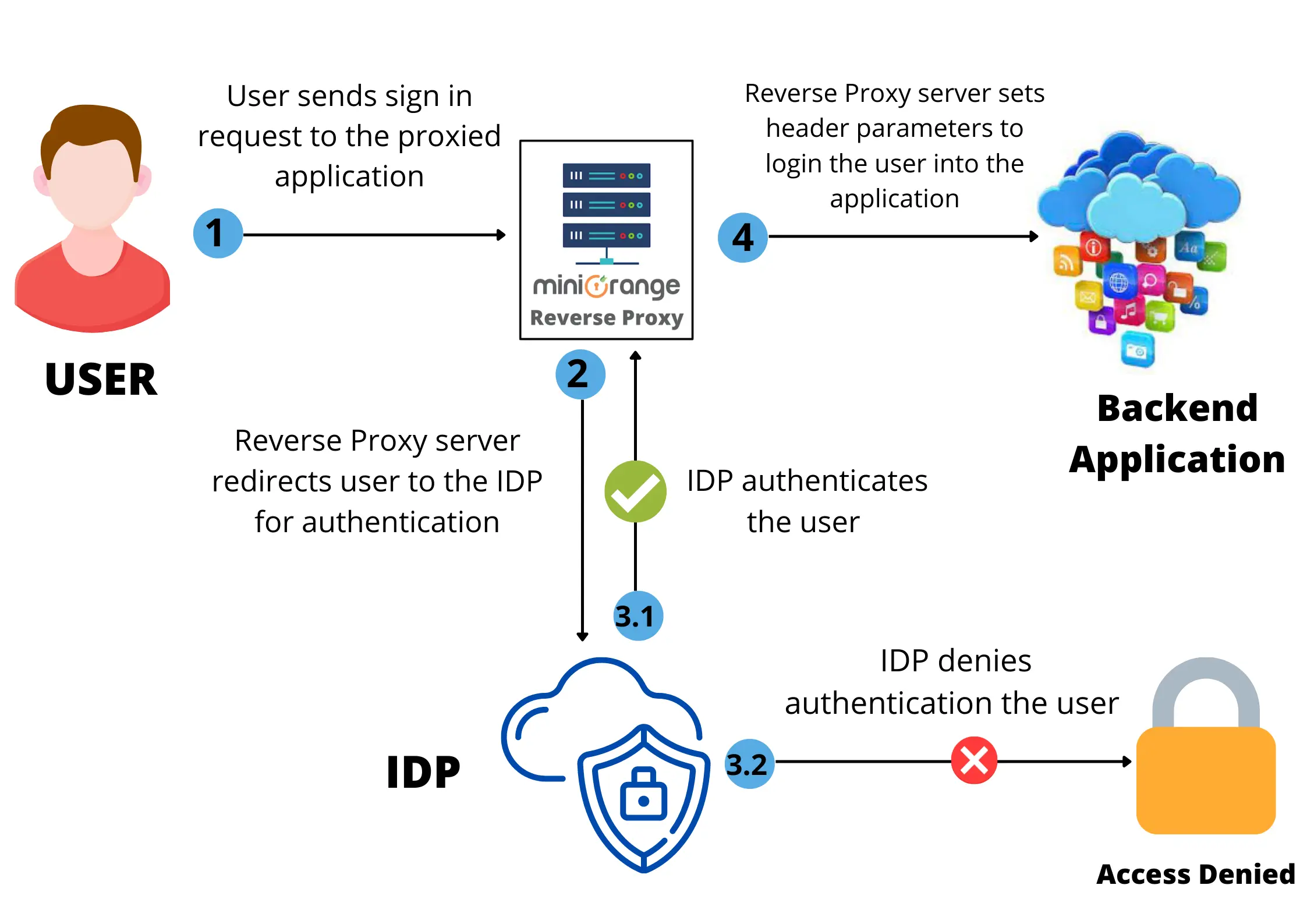
Most legacy applications (and on-premise solutions) do not support SSO for user agent access control. So we need a reverse proxy server in between them to set up SSO (or an IAM) to authenticate the users. By enabling Header Based Authentication for on-premise apps, users can log in to the proxied legacy application using just the contents of the header body of the URL. Admin can specify which parameters should be used to authenticate user agents and have it customized to their security needs.
When the URL header set by the reverse proxy server matches the required header for the proxied legacy application it authenticates user agents and logs in. In case the user’s header parameters do not match the required application parameters, then the application 401 unauthorized error page will be displayed.
HTTP header-based authentication for on-premise apps provides easy and secure single sign-on (SSO) for all authorized user agents.
No third-party apps or additional software is needed for your legacy apps to grant remote access and complete with ease of use along with header access control.
With header-based authentication for on-premise apps, you can set custom URL parameters in the header to be used to authenticate users. This offers customizability and reduces security risks.
Message integrity is maintained as we know the content will not be modified, as no unauthorized user agent will access the legacy apps.
Let’s see the steps of how Header Based Authentication for on premise apps works with a reverse proxy server
Suppose we have a user, Stephen. Stephen wants to access the backend application (example In-house SaaS applications ). He will see the proxied application and try to log in to it. A request will be initiated and sent to the reverse proxy server. The reverse proxy server will redirect him to the IAM set up by Stephen’s organization (example miniOrange or Azure AD).
A reverse proxy server is a special kind of proxy server. In contrast to a forward proxy server, which protects clients [...]
Role based access control (RBAC)means allowing access to users to a stack based on the set user roles and [...]
Ever felt concerned about the images that you added to your online folders, might be downloaded by users (who aren’t logged in) [...]
Google Workspace holds the entire collection of data that a company generates by storing [...]