Need Help? We are right here!
Search Results:
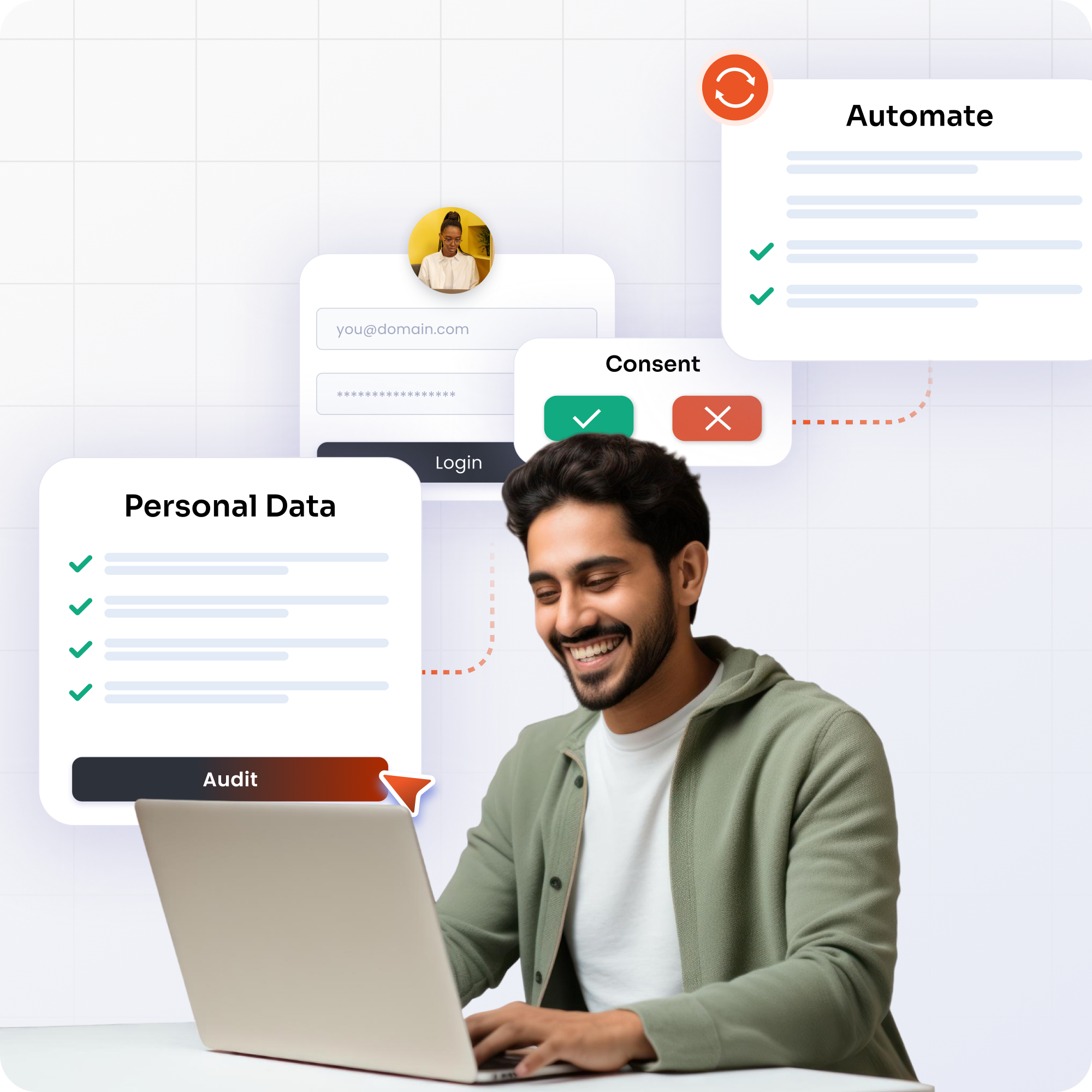
×Privacy has become a decisive factor in how organizations are evaluated by customers, partners, and stakeholders. miniOrange helps you proactively safeguard sensitive information through a unified platform built for modern digital ecosystems. Strengthen brand perception by demonstrating accountability, transparency, and responsible information practices at every touchpoint. Reduce risk, elevate trust, and support long-term growth while delivering secure, seamless user experiences.
Enable transparent data collection with centralized consent management that captures user preferences, maintains detailed records, and adapts to evolving privacy expectations.
Streamline the fulfillment of data requests with intelligent workflows that automate access, correction, portability, and deletion processes, reducing manual effort while improving response efficiency.
Automatically identify and categorize sensitive data across systems to eliminate blind spots, prioritize risk areas, and support stronger information governance.
Protect critical information with layered security controls, including encryption, masking, and continuous monitoring to prevent unauthorized exposure.
Ensure the right individuals access the right data at the right time with granular, identity-driven controls that minimize risk and enforce least-privilege principles.
Maintain continuous visibility into data activity with comprehensive logs, real-time tracking, and reporting that strengthen accountability and support internal reviews.
Capture explicit, informed consent directly within sign-up and authentication flows. Consent is enforced before access is granted, versioned over time, and preserved as tamper-proof evidence to meet DPDP accountability requirements.
Key Capabilities
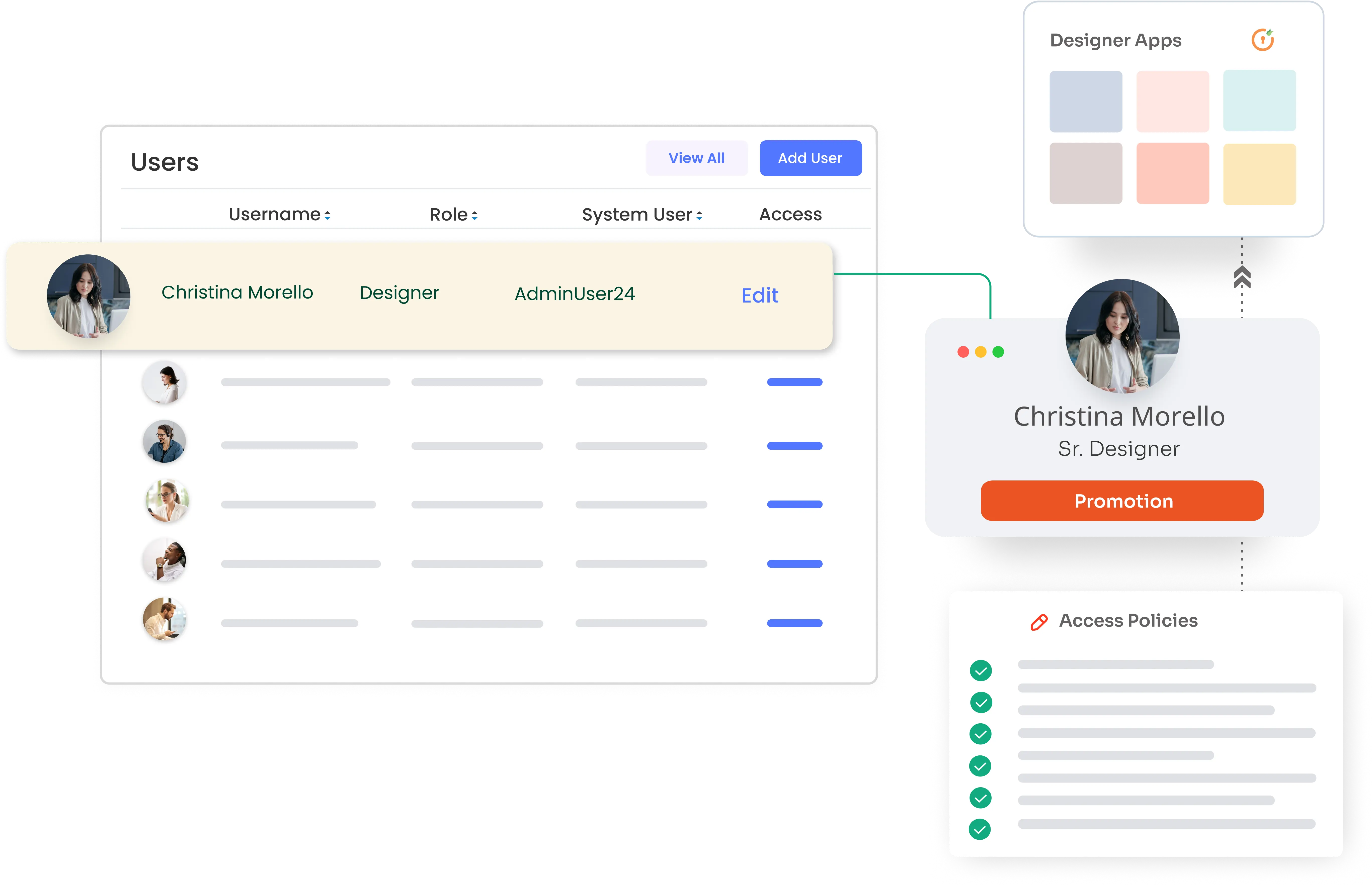
Ensure users remain informed and in control as access evolves. Whenever a new application is introduced or permissions are modified, users are prompted to review and re-approve consent before access is extended.
Key Capabilities
Prevent consent drift and stale permissions through periodic re-verification campaigns. Users reconfirm access during defined intervals, while administrators gain visibility into outstanding approvals, dormant accounts, and compliance gaps.
Key Capabilities
Translate consent decisions into real, enforceable access controls across applications, systems, and identities. Ensure users only retain access and associated data for as long as they are authorized.
Automatically grant access to applications only after valid consent is provided, and revoke access and associated data when consent is withdrawn, permissions change, or accounts are closed.
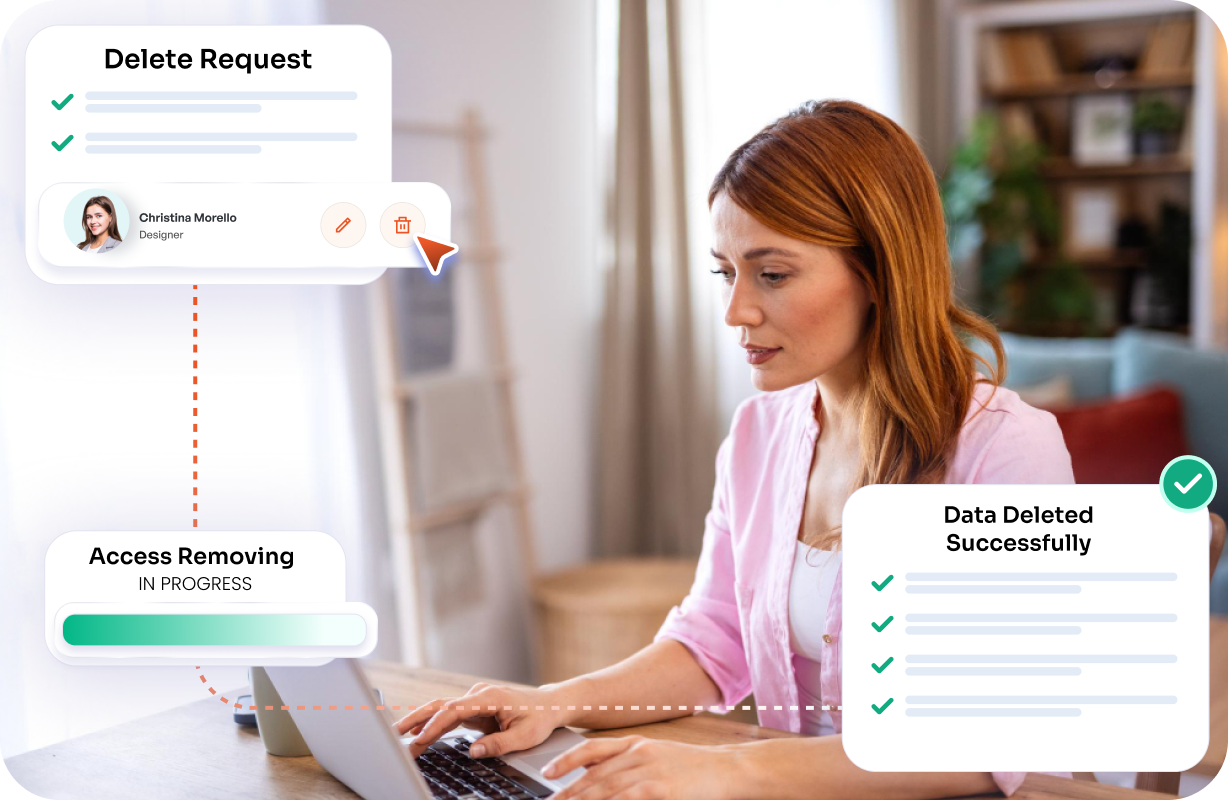
Ensure no residual access remains after user offboarding. When a user account is deleted or disabled, access is removed across all connected systems with verifiable completion.
Continuously identify and remediate access that is no longer required or approved, reducing over-exposure and DPDP risk.
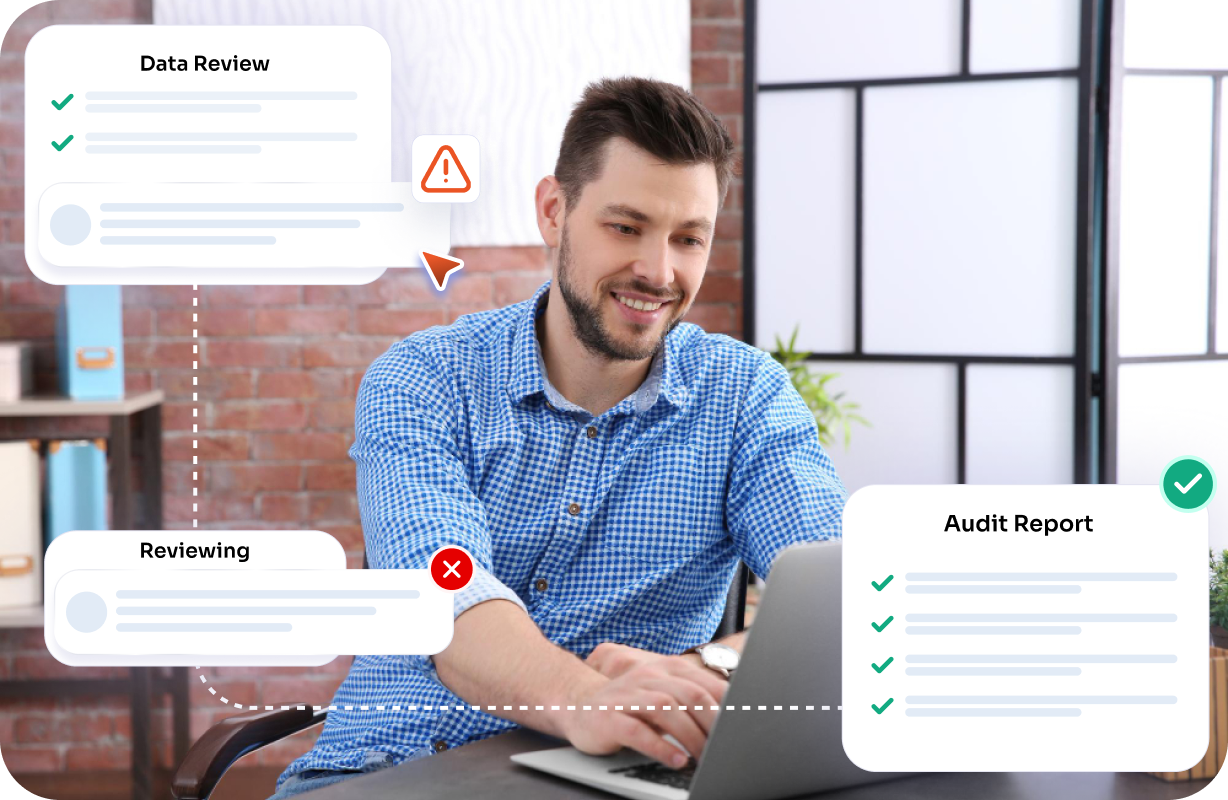
Continuously scan cloud and on-prem environments using agents and APIs to ensure broad coverage, uninterrupted monitoring, and complete visibility into where personal information resides.
Leverage regex scans alongside AI-powered semantic detection to accurately identify sensitive information while maintaining audited findings, enhancing detection quality, and minimizing blind spots.
Visualize risk hotspots, exposure levels, ownership, applications, permissions, and stored personal information within a centralized interface that promotes transparency and enables both administrative oversight and user self-service actions.
Detect sensitive information across cloud platforms and user devices by monitoring downloads and sharing activity, enforcing block or allow policies, and enabling endpoint DLP protection through lightweight agents for real-time data detection. Automate policy enforcement with integrated alerts to prevent data leakage across endpoints, applications, and cloud environments.
Maintain comprehensive scan logs, findings trails, access records, and movement histories while exporting evidence-ready reports with complete timelines to streamline auditor reviews and demonstrate regulatory accountability.
Revoke authorization and trigger automated deprovisioning when consent is withdrawn or accounts are closed, ensuring downstream changes are enforced with fully auditable records.
Consent is presented during authentication and securely recorded as verifiable evidence, establishing a clear foundation for lawful data processing.
Individuals gain visibility into where their personal data resides across applications, files, endpoints, databases, and storage environments.
Data Principals can initiate deletion requests and track progress through completion, ensuring accountability and reinforcing trust.
Administrators confirm the scope of the request across connected systems while ensuring internal governance policies are followed.
Personal data is systematically removed from applications, drives, endpoints, databases, servers, and storage buckets to prevent residual exposure.
Actions are documented as audit evidence, and automated notifications confirm fulfillment to the Data Principal, closing the compliance loop.
Comprehensive timelines provide visibility into how data is accessed, shared, and processed, ensuring alignment with consent and policy requirements.
Auditors can confirm the presence of protective measures such as data loss prevention controls and encryption to support reasonable security obligations.
Detailed reports are available for export to support regulatory reviews. Every download is logged to preserve integrity and traceability.
Personal data must be collected and processed in a lawful manner with clear communication to individuals about how their data is used.
Data should only be gathered for specific, explicit purposes and not processed beyond those defined objectives.
Organizations should collect only the data that is necessary to fulfill the intended purpose, avoiding excessive or irrelevant information.

Reasonable steps must be taken to ensure personal data remains accurate, complete, and up to date.
Personal data should be retained only for as long as required to meet the stated purpose or legal obligations.
Appropriate technical and organizational measures must be implemented to protect personal data from breaches and unauthorized access.

Organizations are responsible for demonstrating compliance with the Act through governance, policies, and auditable data protection practices.

Phase 1: Governance & Visibility
Build a compliance foundation by auditing personal data, onboarding key sources, and running discovery scans to locate sensitive information. Unified dashboards deliver risk insights, while logging baselines strengthen accountability and prepare your organization for regulatory oversight.

Phase 2: Consent Management
Capture consent at sign-up and login, extend it to newly added applications, and trigger re-consent when permissions change. Consent Recertification campaigns keep records accurate, supporting lawful processing while improving transparency and reinforcing user trust.

Phase 3: Rights & Safeguards
Automate data rights and verified deletion with user notifications to ensure accountability. Protect sensitive information through cloud-based DLP, endpoint controls, and remote device wipe, while enabling breach reporting and audit-ready records to demonstrate ongoing compliance.