BigCommerce Two-Factor Authentication (2FA/MFA)
Enabling 2FA (2-step verification) for your BigCommerce Store provides an extra level of security that goes beyond relying solely on a username & password. By introducing a second authentication factor, such as a one-time password sent via phone or email, the risk of unauthorized access to your BigCommerce store is significantly reduced. Even if an attacker manages to obtain a user's password, they would still need the second factor to gain access.
By implementing BigCommerce 2FA, merchants & users can effectively safeguard their BigCommerce store, customer data & sensitive business information from unauthorized access attempts & potential security breaches.
With miniOrange BigCommerce 2FA solution, you can:
- Choose from 15+ 2FA methods including OTP over SMS/Email, Push notification and more.
- Enable Passwordless login for your BigCommerce Store.
- Prevent unauthorized person from accessing the resources even if cyber attackers get to know your credentials.
- Connect easily with any external identity source like Azure AD, ADFS, Cognito, etc.
Verified Technology Partner of BigCommerce
SSO + MFA Support for any BigCommerce Plan (Standard, Plus, Pro, Enterprise)
Get Free Installation Help
miniOrange offers free help through a consultation call with our System Engineers to Install or Setup BigCommerce 2FA solution in your environment with 30-day free trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you in no time.
Checkout Pricing
Connect with External Source of Users
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.

miniOrange
Authenticator App

Google
Authenticator App

Authy 2-Factor
Authentication App

Microsoft
Authenticator App
Follow the Step-by-Step Guide given below for BigCommerce two-factor authentication (2FA) :
1. Create BigCommerce API
- Log in to BigCommerce Admin Panel.
- Go to Settings >> API >> Store-level API Accounts.
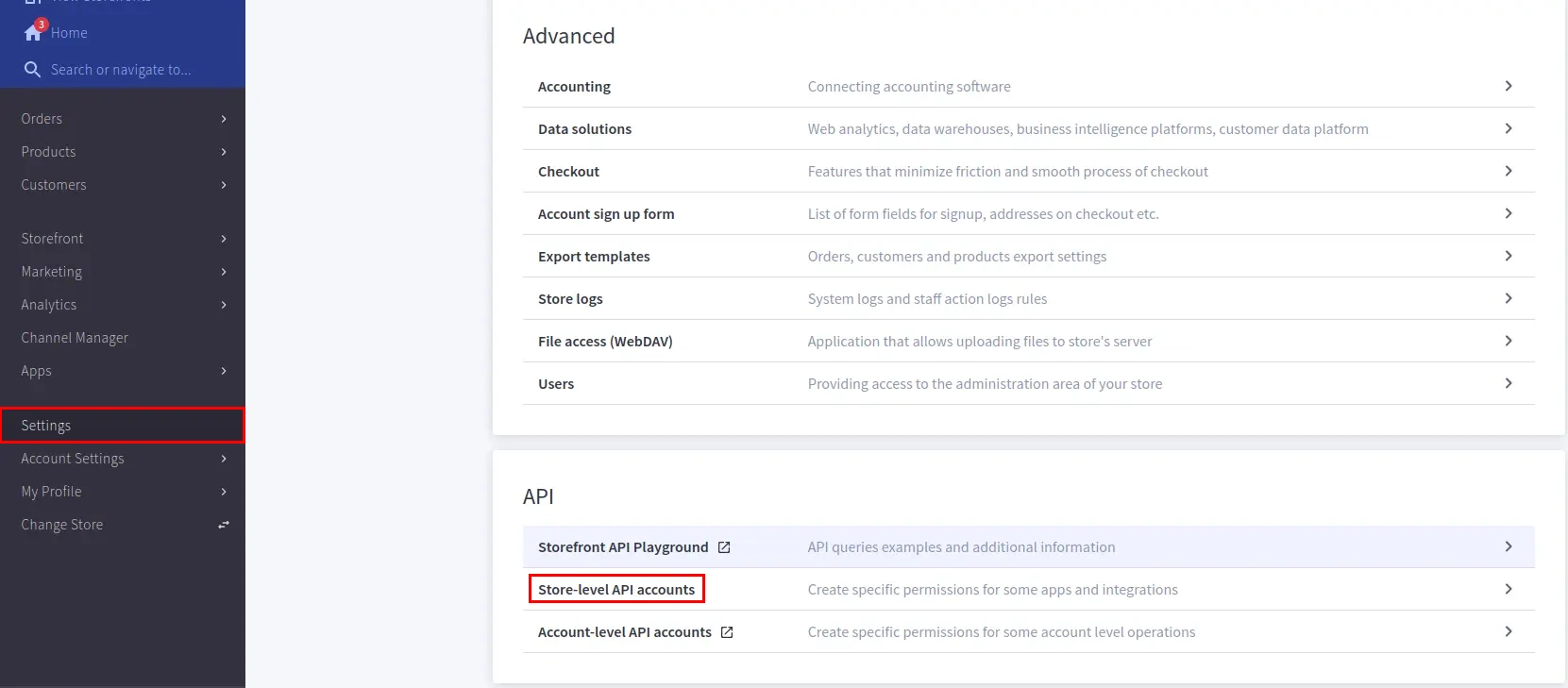
- Click Create API Account and choose the token type as V2/V3 API Token.
- Add a suitable name for your API account.
- In BigCommerce, the API Path is the base URL that your application or integration uses to connect to your store’s data through BigCommerce APIs. The Store Hash is a unique identifier automatically generated by BigCommerce for each store. It appears in the API Path.
- Copy the highlighted Store Hash from the API Path.
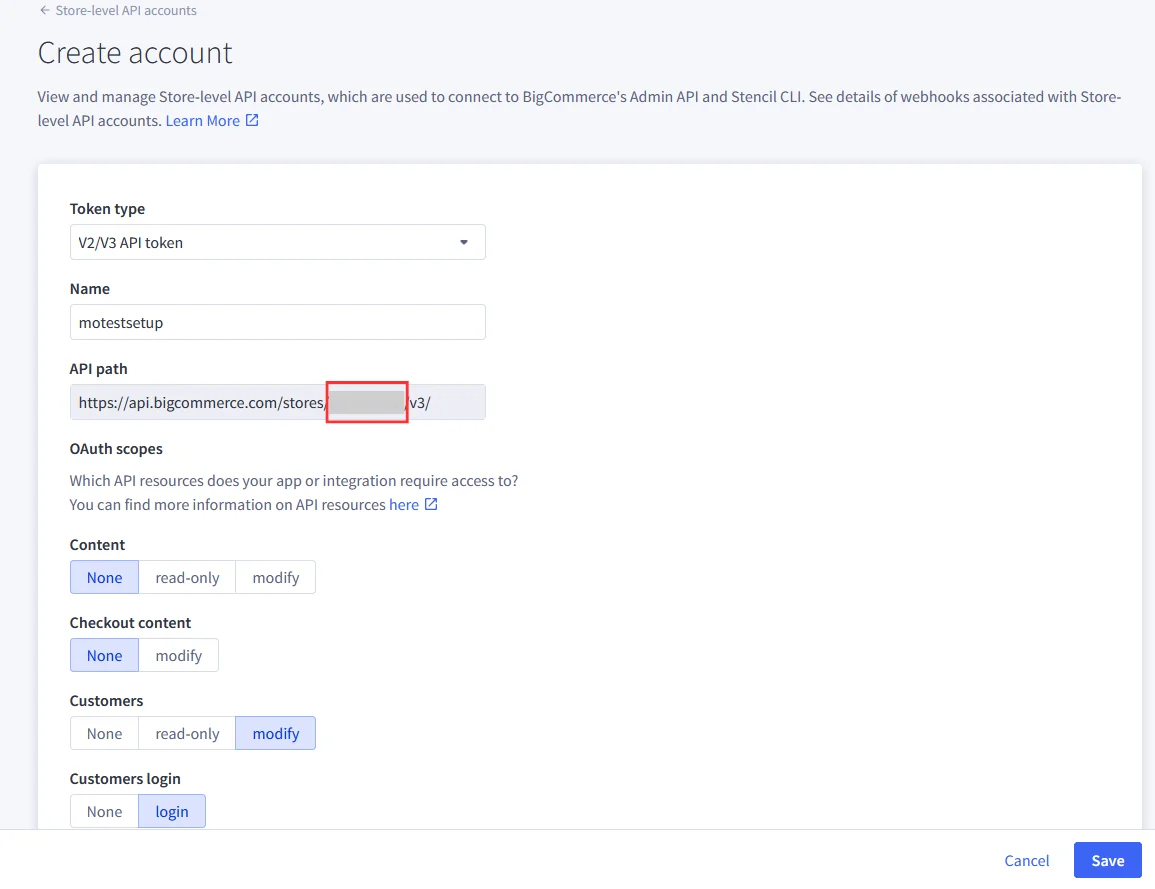
- This Store Hash will be required while configuring BigCommerce in miniOrange.
- Enable the Customers option as Modify and Customers Login option as login. Keep rest of the settings as it is.
- Click on Save.
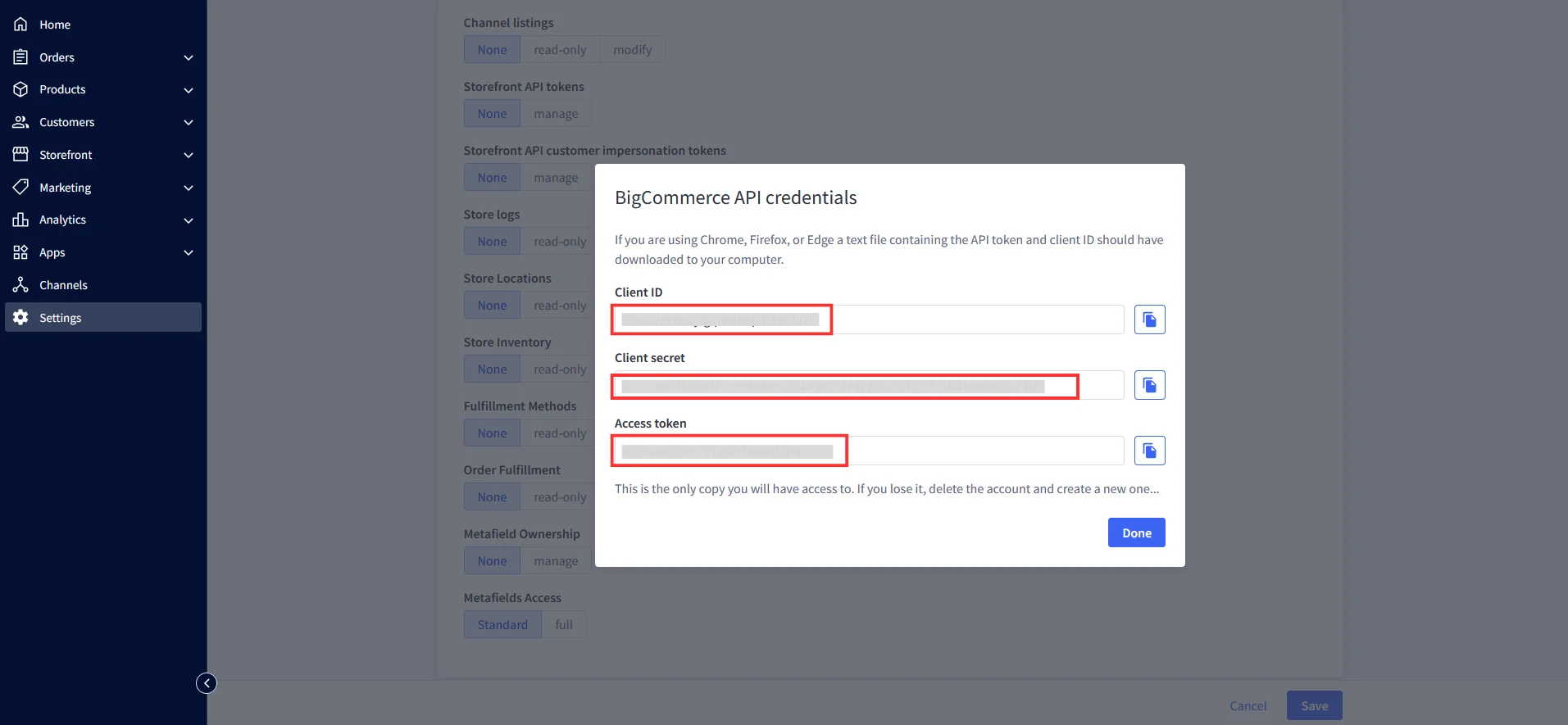
- Download the API credentials file. It contains the API token, Client ID and Client Secret.
2. Configure BigCommerce in miniOrange
- Login into miniOrange Admin Console.
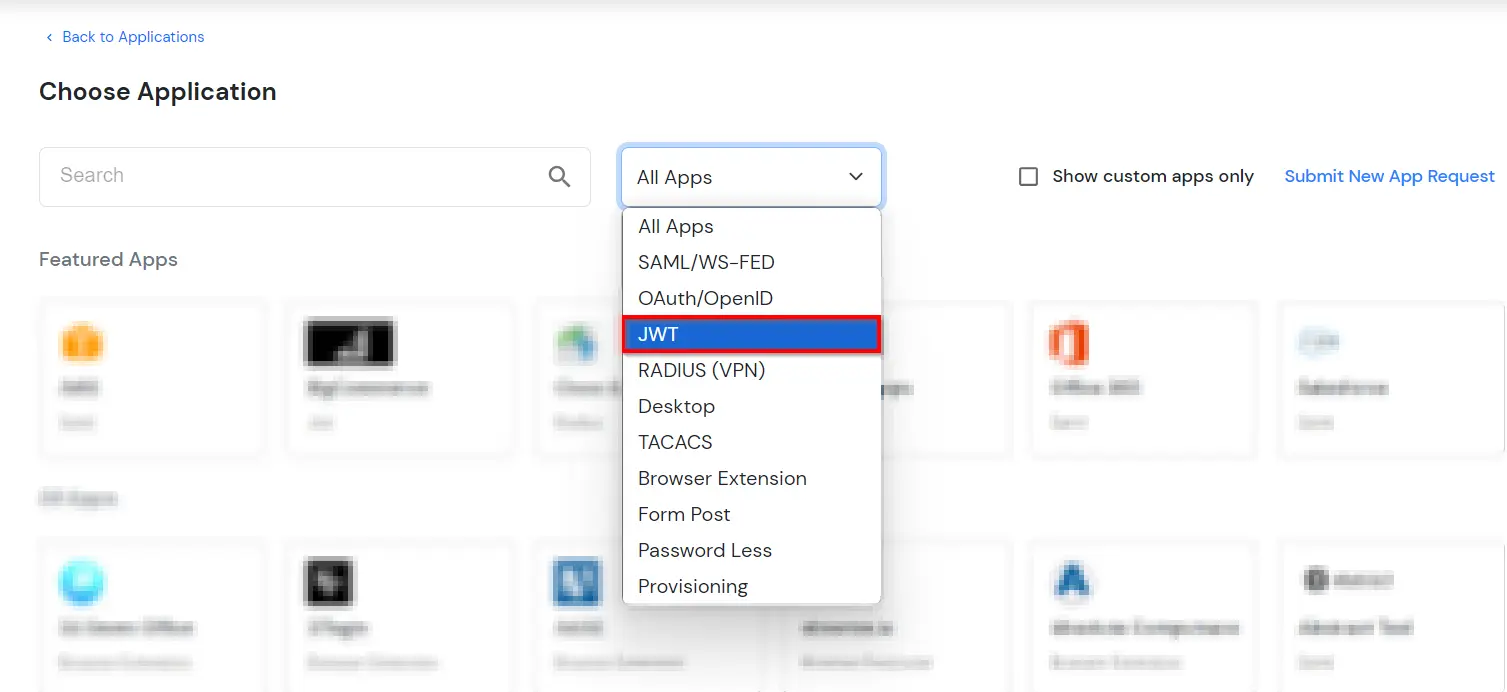
- Go to Apps click on Add Application button.

- In the Choose Application section, open the dropdown list of All Apps and select JWT.
- In the next step, search for BigCommerce application from the list and click on it.
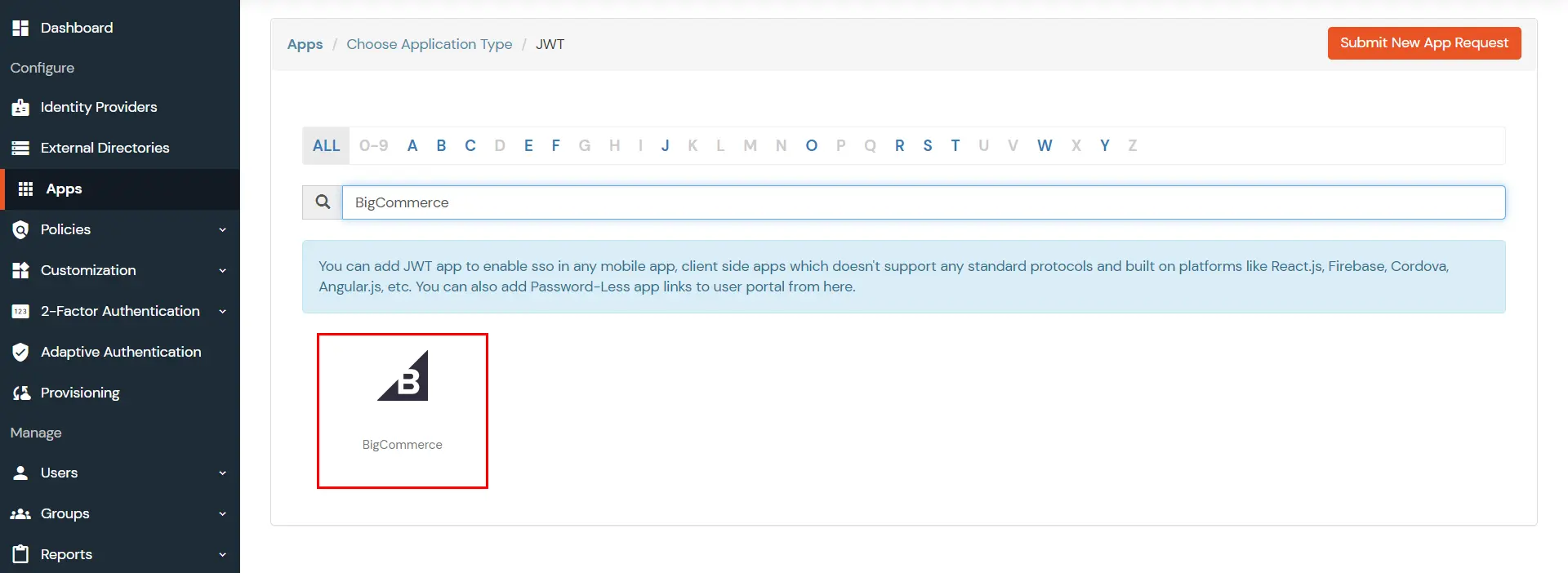
- Enter the following values in the respective fields.
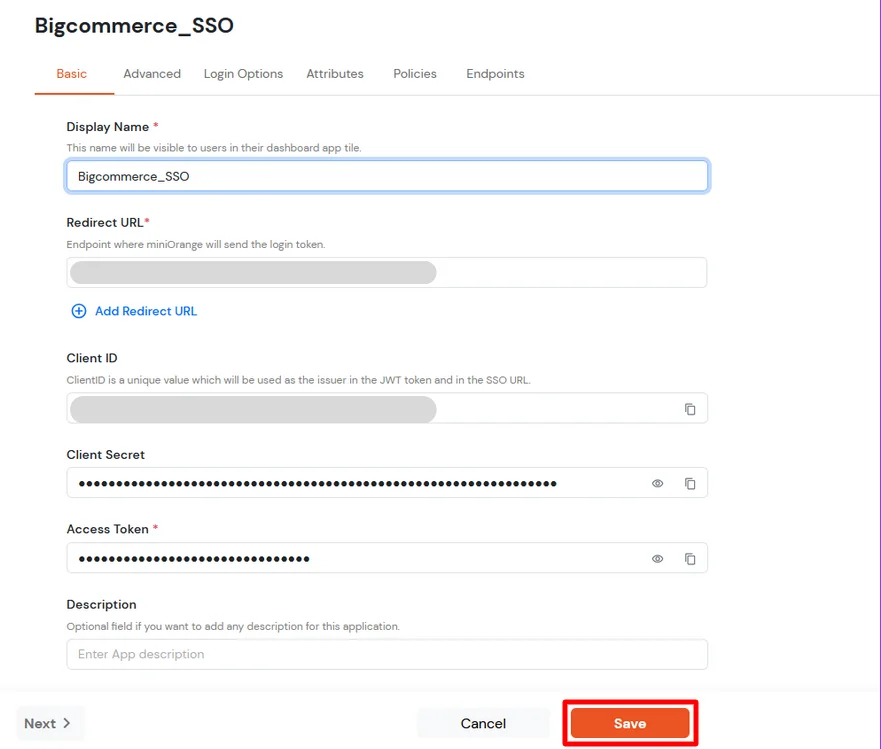
- Enter the Client Id, App Secret and Access token which we have downloaded from step 1 during API creation in BigCommerce Console.
| Display Name [Required] |
BigCommerce (According to your choice) |
| Redirect-URL [Required] |
Storefront URL/login/token/ |
| Client ID |
Copy from the downloaded file in Step 1 |
| Client Secret |
Copy from the downloaded file in Step 1 |
| Access Token |
Copy from the downloaded file in Step 1 |
| Description |
According to your choice |
- For Redirect URL-
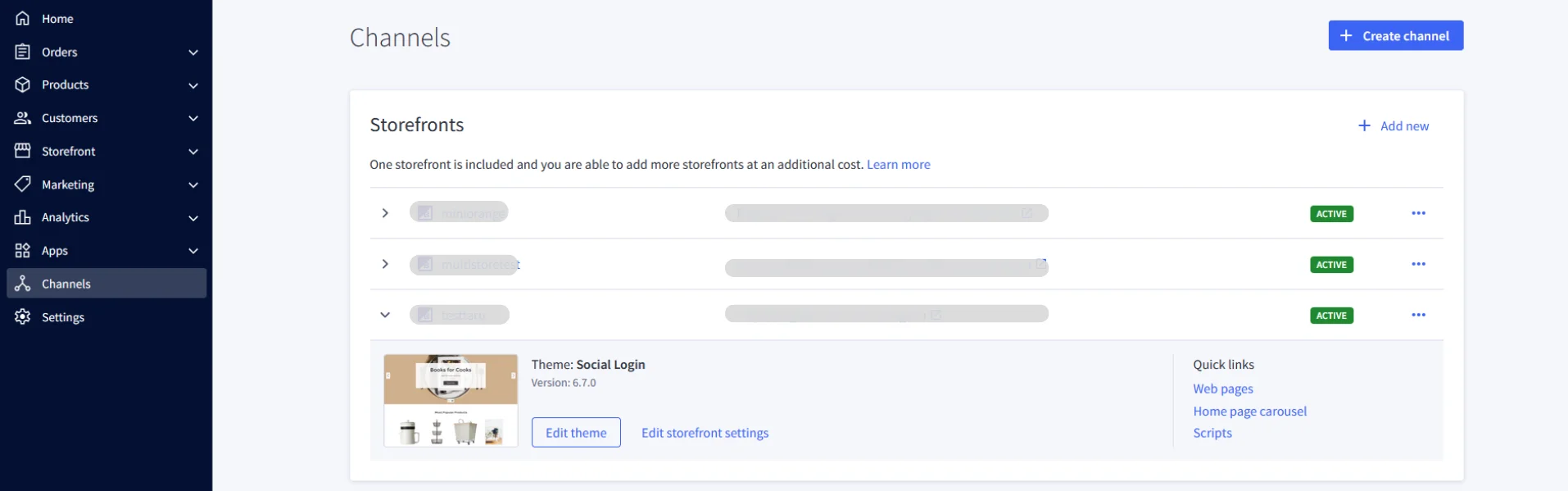
- Go to the Channels tab in the left-hand menu.
- Find your store listed under Storefronts. In front of the store name, you will see the full Storefront URL.
- Copy the entire Storefront URL.
- Paste the copied URL and append the login path, /login/token/, to the end.
- Now click on Save and go to Advanced tab.
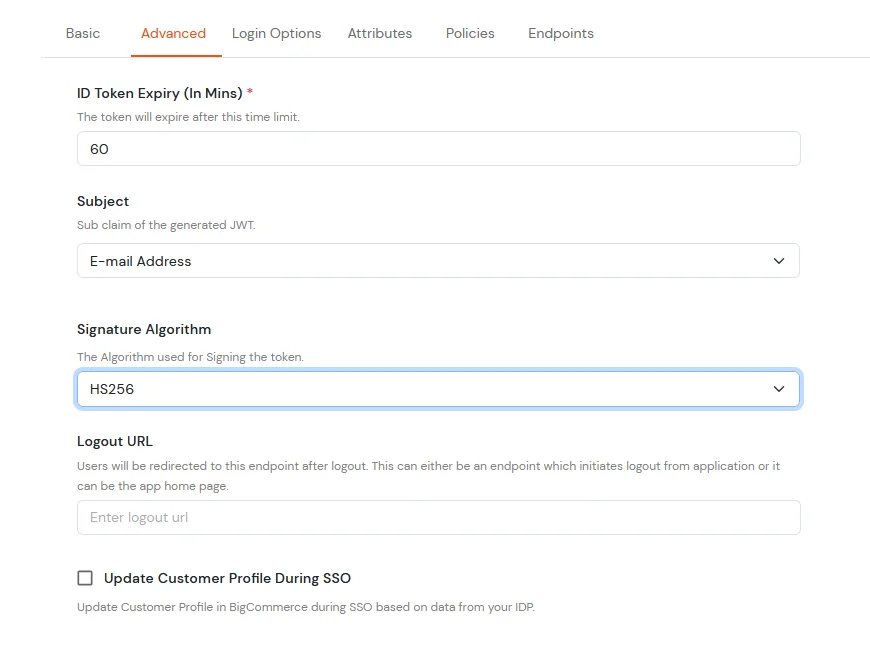
| Subject |
E-Mail Address. |
| Signature Algorithm |
HS256 |
| Logout URL |
Copy the storefront URL as mentioned above and append /login.php?action=logout
e.g., https://{{my-store}}.mybigcommerce.com/login.php?action=logout |
- Click Next to go to the Login Options tab.
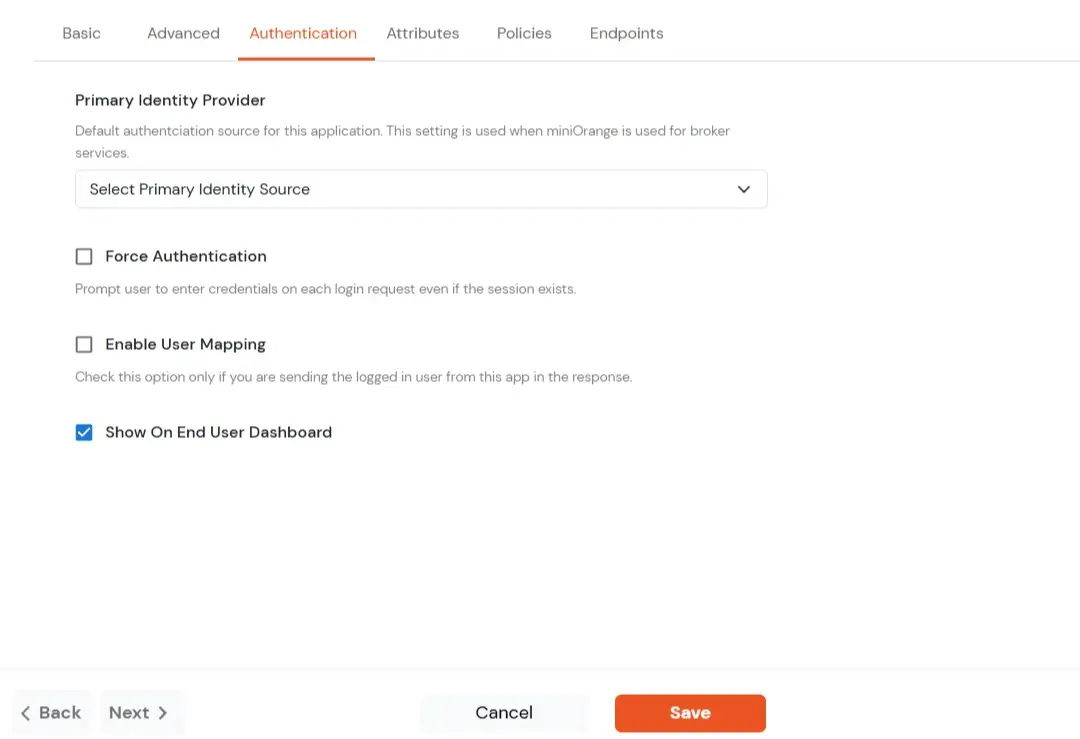
| Primary Identity Provider |
The identity source against which user will be authenticated |
| Force Authentication |
Enable if you want user to authenticate even if the user has a session |
| Enable User Mapping |
Enable if you are sending the logged-in user from this app in the response |
- Click on the Next.
Enable 2FA Policy for Users of BigCommerce app
- Navigate to Policies tab.
- Click on Assign Group button.
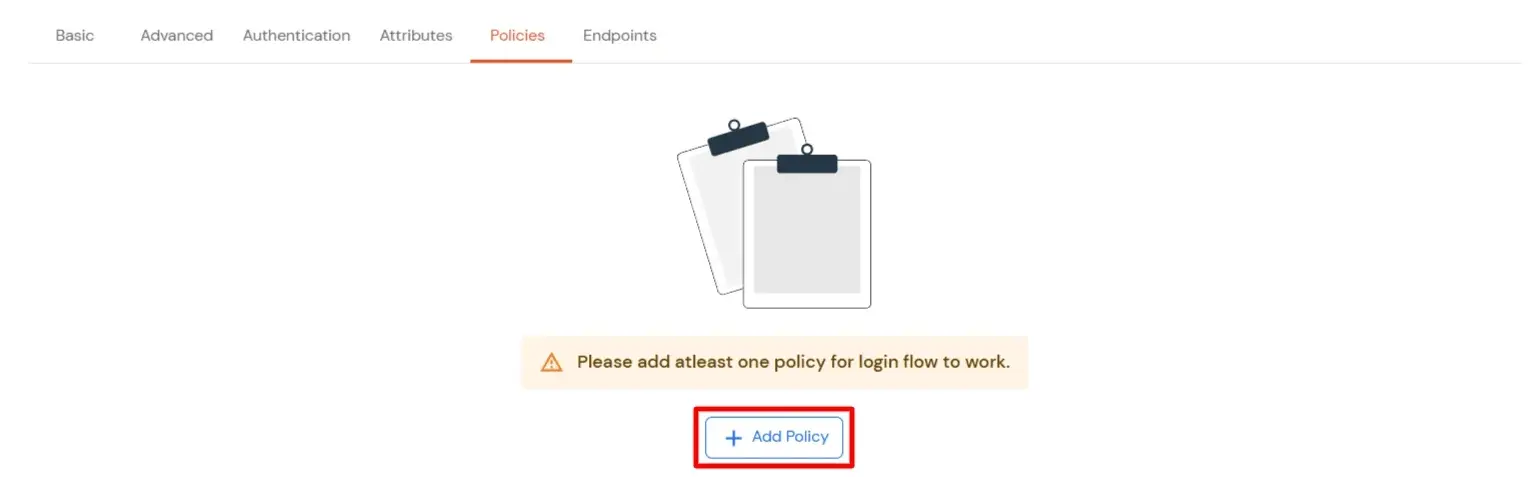
- On the Assign Group section.
- Choose the DEFAULT group.
- Click on the Next button.
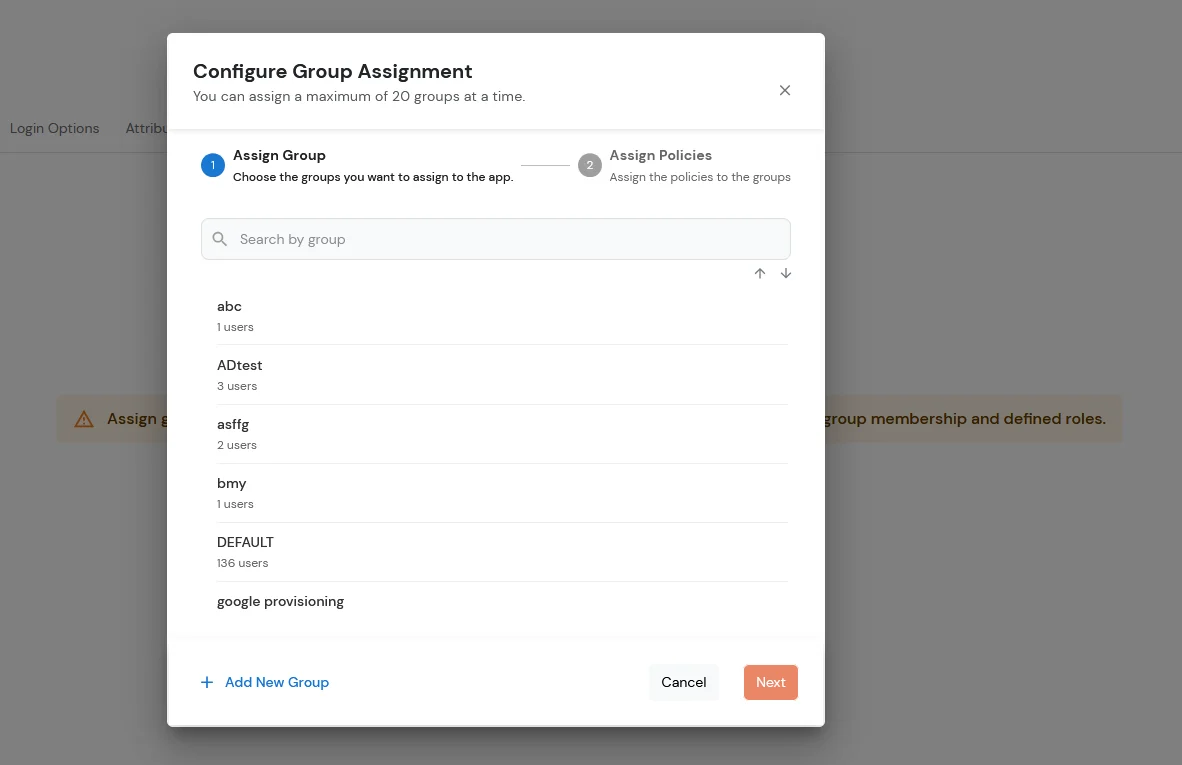
- Assign the policies to the group.
- Select First Factor as Password option.
- Check the Enable Two-Factor Authentication (2FA) option.
- Click on Save.
Attribute Mapping
- Navigate to the Apps section.
- Locate and select your specific application.
- In the Action column for your application, click on the (⋮) to open the action menu.
- From the menu that appears, click on the Edit option.
- To map the attributes between the IDP and BigCommerce application, navigate to Attributes tab. Click on the +Add Attributes button.
- The first three attributes will be hard-coded values
| Attribute Name | Attribute Type | Attribute Value |
|---|
| store_hash | Custom Attribute Value | Refer to Step 1 above. |
| redirect_to | Custom Attribute Value | Endpoint where you wish to redirect the user to after sso.
[Homepage or account page e.g. /account.php] |
| operation | Custom Profile Attribute | customer_login |
| first_name | External Idp Attribute | first_name |
| last_name | External Idp Attribute | last_name |
| email | External Idp Attribute | email |
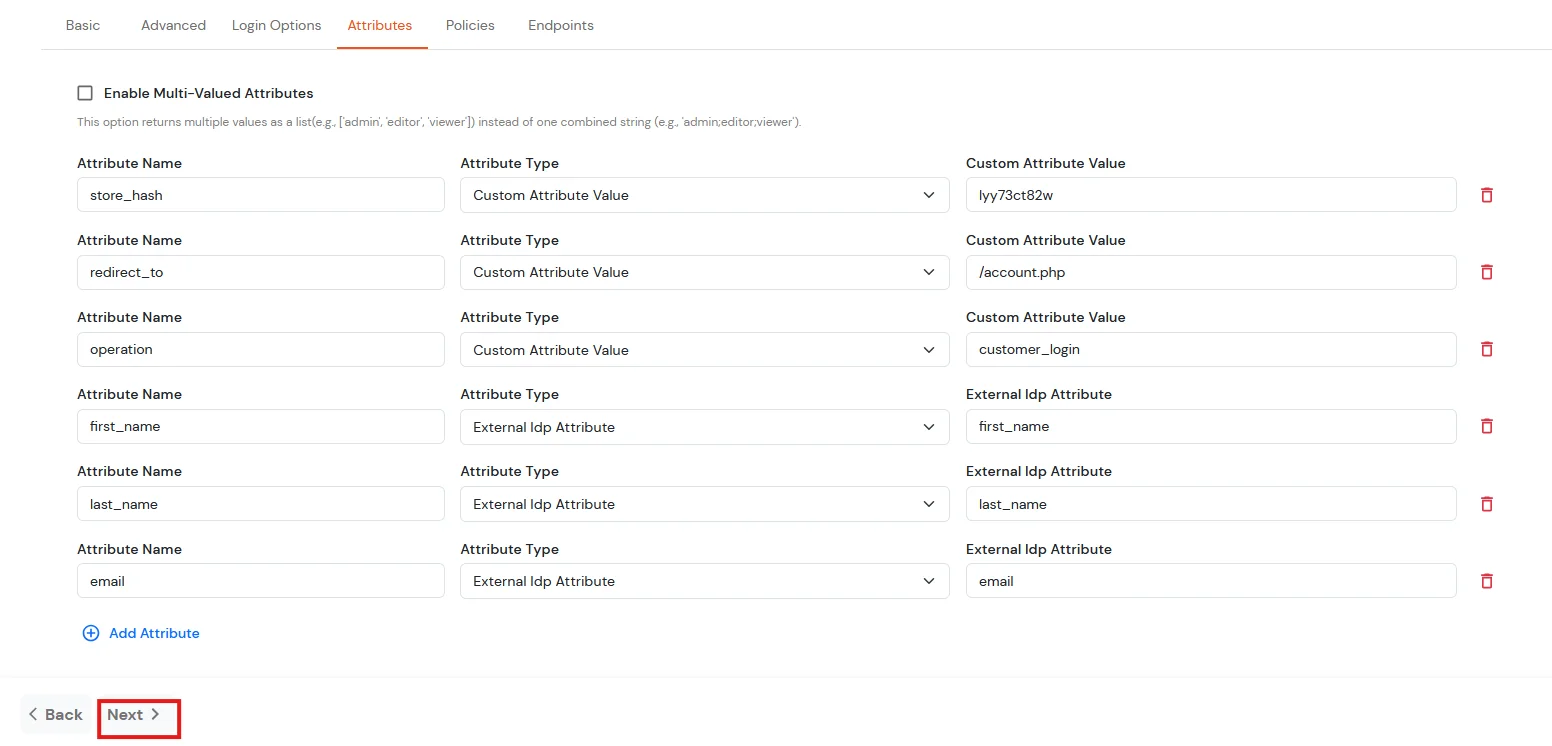
- Click on Next.
- Go to Endpoints tab.
- You will find the SSO URL to authenticate.
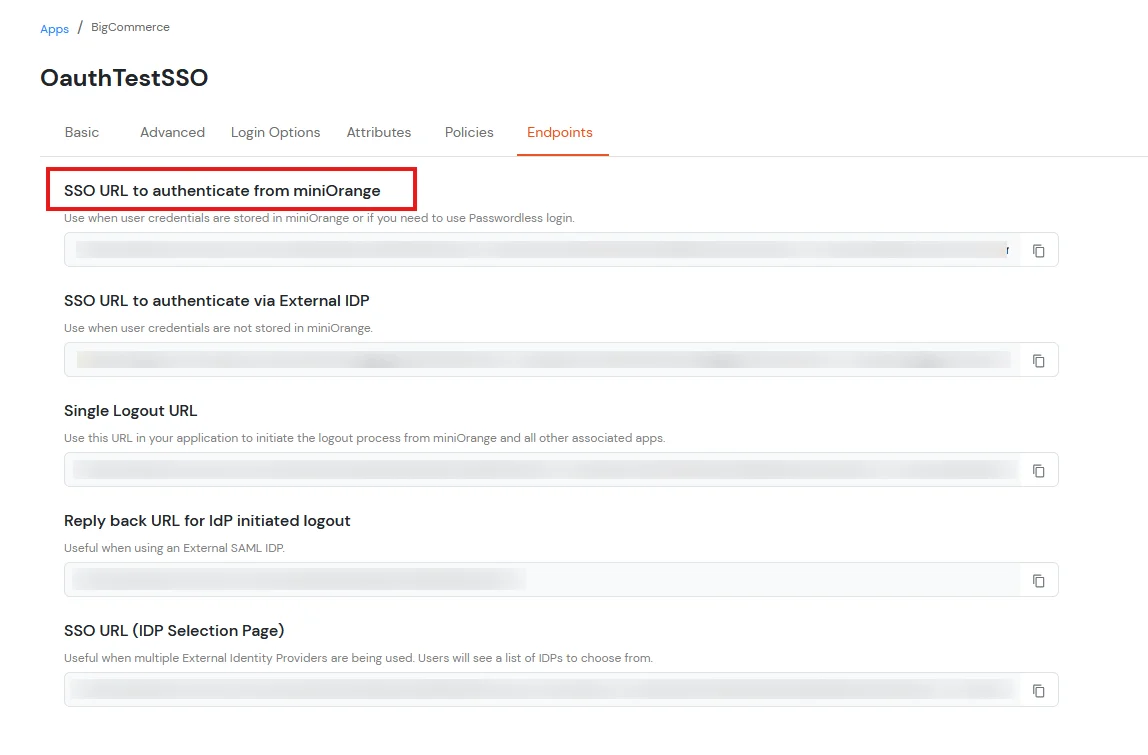
- Now, you can access BigCommerce Account Using IDP credentials through the Single-sign-on URL as shown in image above.
Now, you can access BigCommerce Account Using IDP credentials through SSO URL.
3. Syncing Address, Form, and Custom Attribute Fields to BigCommerce (Optional)
To synchronize address, custom attributes, and form fields from the Identity Provider (IDP) to BigCommerce, the following details must be configured:
Address Fields
To successfully sync customer address information, the following attributes are required:
- first_name
- last_name
- address1
- city
- country_code
In the below diagram, we are using miniOrange as the IDP.
- Before syncing these fields to BigCommerce, you must first create the corresponding attributes in the miniOrange user profile. These attributes will then be mapped and synced to BigCommerce.
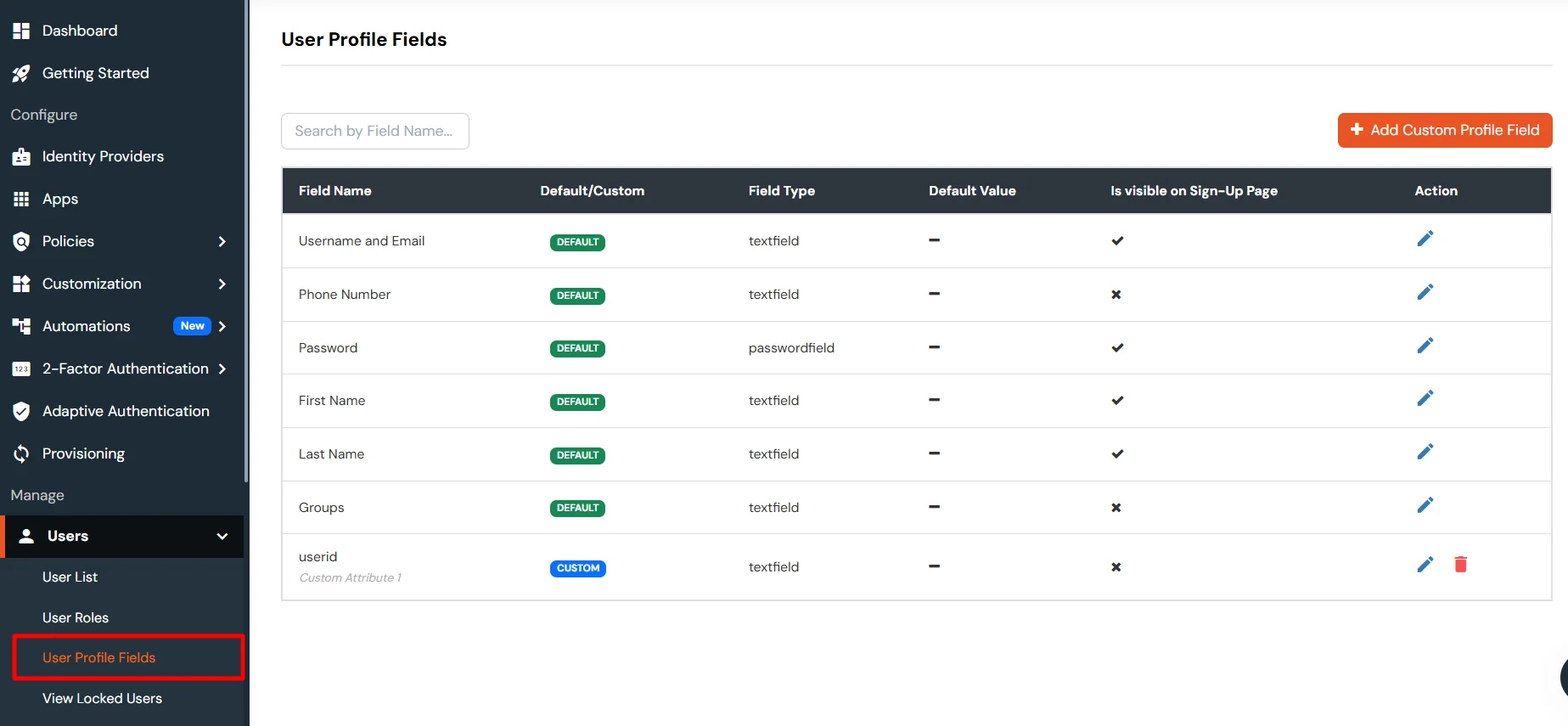
- Then we need to configure the attribute mapping in the application.
| Attribute Name | Attribute Type | Value |
|---|
| addresses.first_name | First Name | - |
| addresses.last_name | Last Name | - |
| addresses.address1 | Custom Profile Attribute | address1 |
| addresses.city | Custom Profile Attribute | city |
| addresses.state_or_province | Custom Profile Attribute | state/province |
| addresses.country_code | Custom Profile Attribute | country |
| addresses.postal_code | Custom Profile Attribute | postal_code |
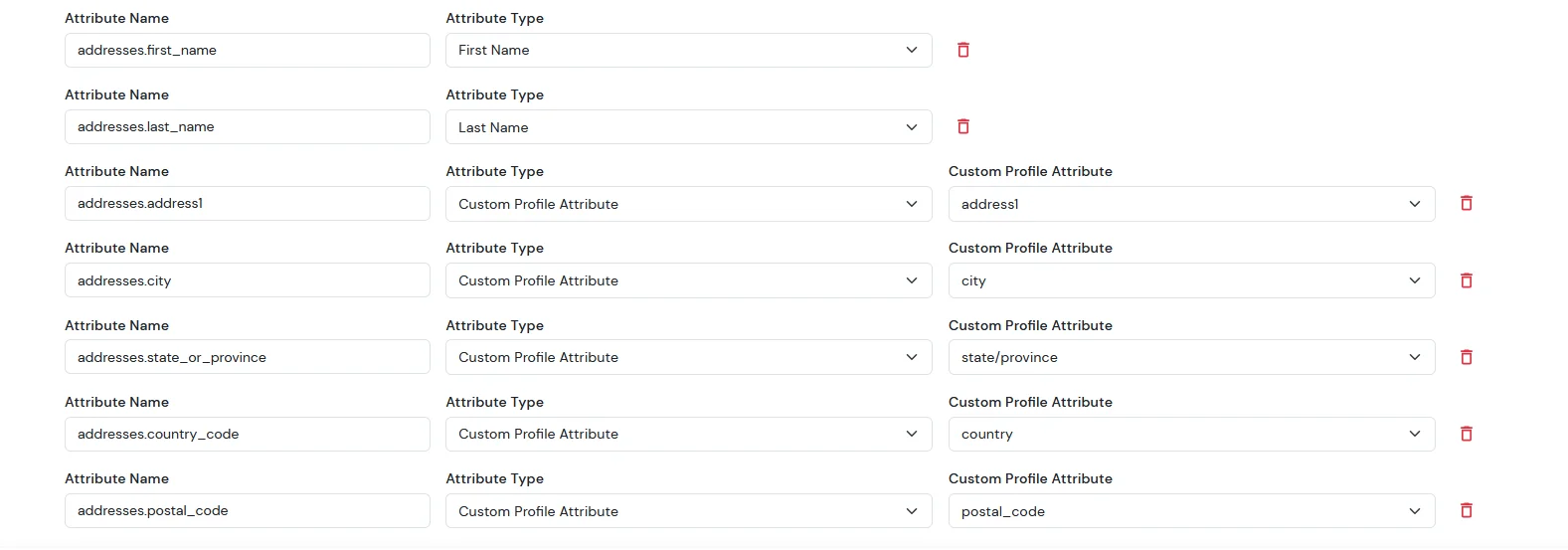
Note: When sending the country value, always use the country code (e.g., US, IN). If you pass the full country name such as “United States”, the value will not be updated — only country codes are supported for correct mapping.
While syncing address fields, ensure that the city, state, and country values you provide are valid options supported by BigCommerce and exist in their respective dropdown lists.
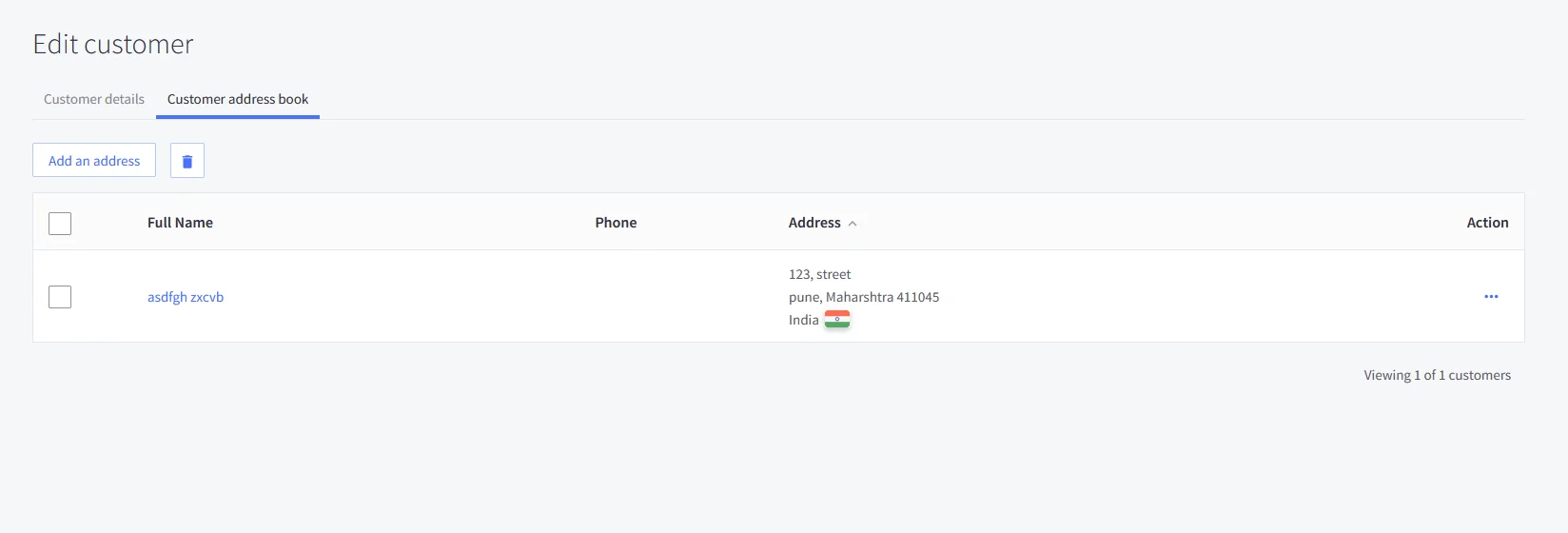
- Now, after completing SSO, go to your BigCommerce dashboard. From the sidebar, click on Customers.
- You will see the list of all customers. Search for the specific user and click on their name.
- Next, open the Customer Address Book section — this is where you will be able to view the customer’s address details.
For the Sign up form fields:
- In BigCommerce, the following form fields are available. We need to configure the corresponding attribute mappings in the application to ensure these fields are correctly synced to BigCommerce.
- Then we need to configure the attribute mapping in the application.
| Attribute Name | Attribute Type | Value |
|---|
| addresses.first_name | First Name | - |
| addresses.last_name | Last Name | - |
| addresses.address1 | Custom Profile Attribute | address1 |
| addresses.city | Custom Profile Attribute | city |
| addresses.state_or_province | Custom Profile Attribute | state/province |
| addresses.country_code | Custom Profile Attribute | country |
| addresses.postal_code | Custom Profile Attribute | postal_code |
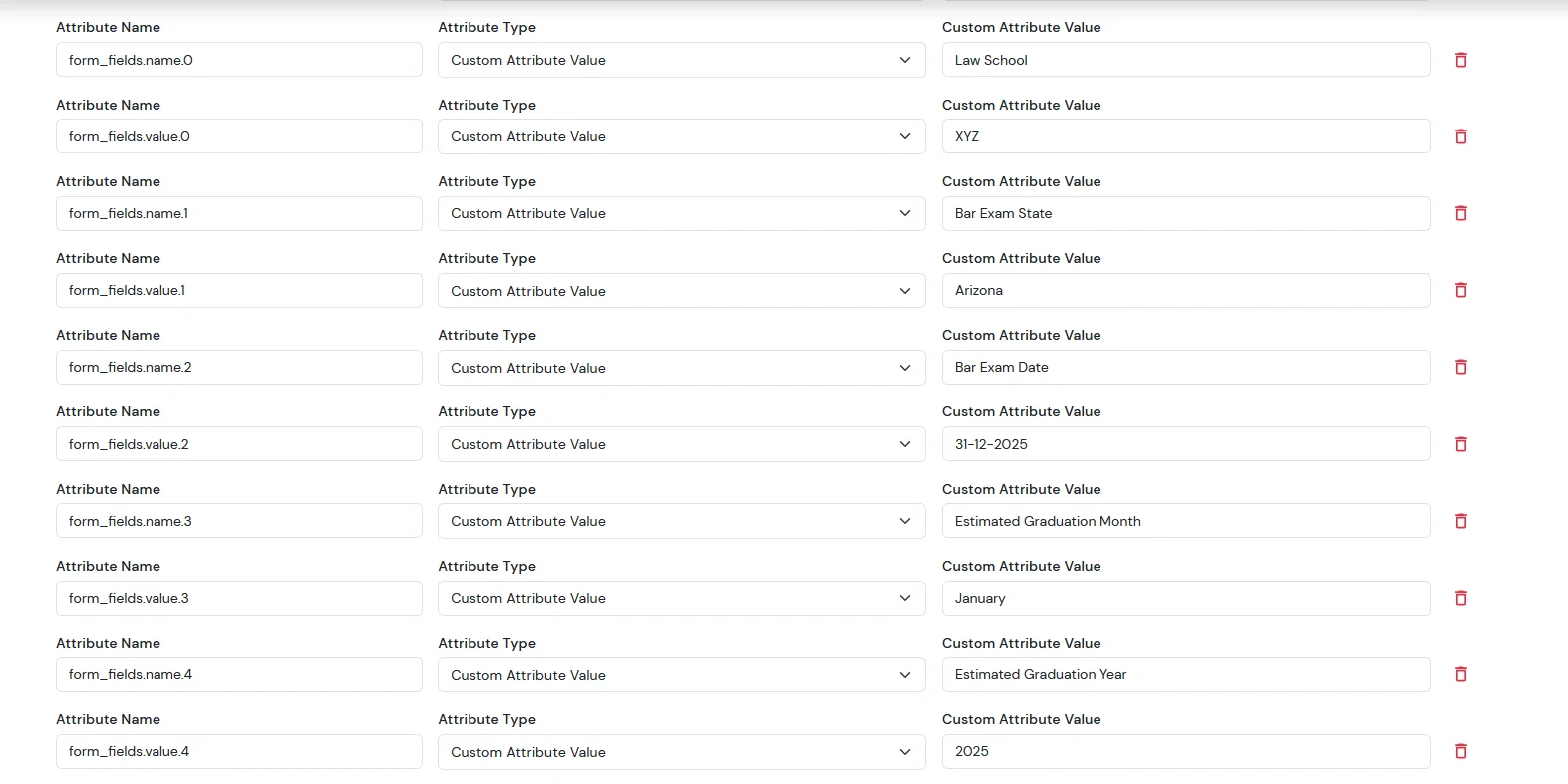
| form_fields.name.0 | Custom Attribute Value | Law School |
| form_fields.value.0 | Custom Attribute Value | XYZ |
| form_fields.name.1 | Custom Attribute Value | Bar Exam State |
| form_fields.value.1 | Custom Attribute Value | Arizona |
| form_fields.name.2 | Custom Attribute Value | Bar Exam Date |
| form_fields.value.2 | Custom Attribute Value | 31-12-2025 |
| form_fields.name.3 | Custom Attribute Value | Estimated Graduation Month |
| form_fields.value.3 | Custom Attribute Value | January |
| form_fields.name.4 | Custom Attribute Value | Estimated Graduation Year |
| form_fields.value.4 | Custom Attribute Value | 2025 |
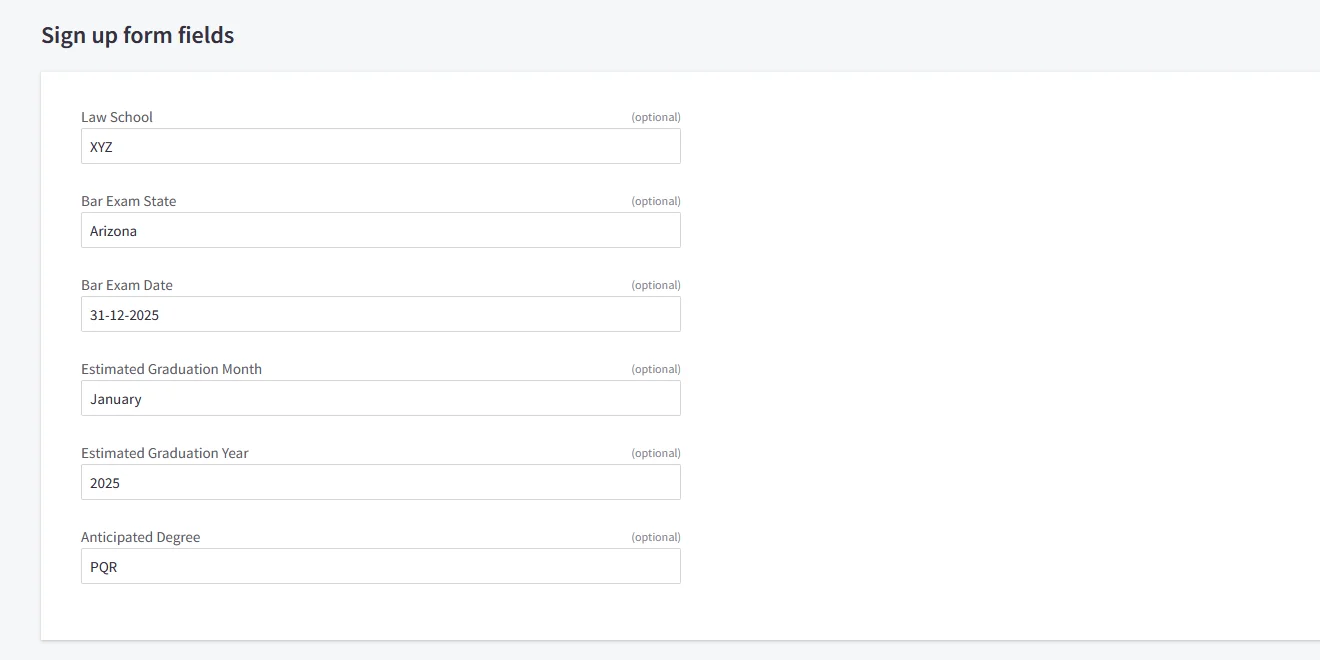
- After completing SSO, go to your BigCommerce dashboard.
- From the left sidebar, click on Customers.
- You will now see the list of all customers.
- Search for the specific user and click on their name.
- The customer profile will open — scroll down to the Customer Details section.
- Here, you will see the signup form fields, where you can view all the customer-submitted form-field details.
For the Attribute Fields
- In BigCommerce, the following attribute fields are available. We need to configure the corresponding attribute mappings in the application to ensure these fields are correctly synced to BigCommerce.
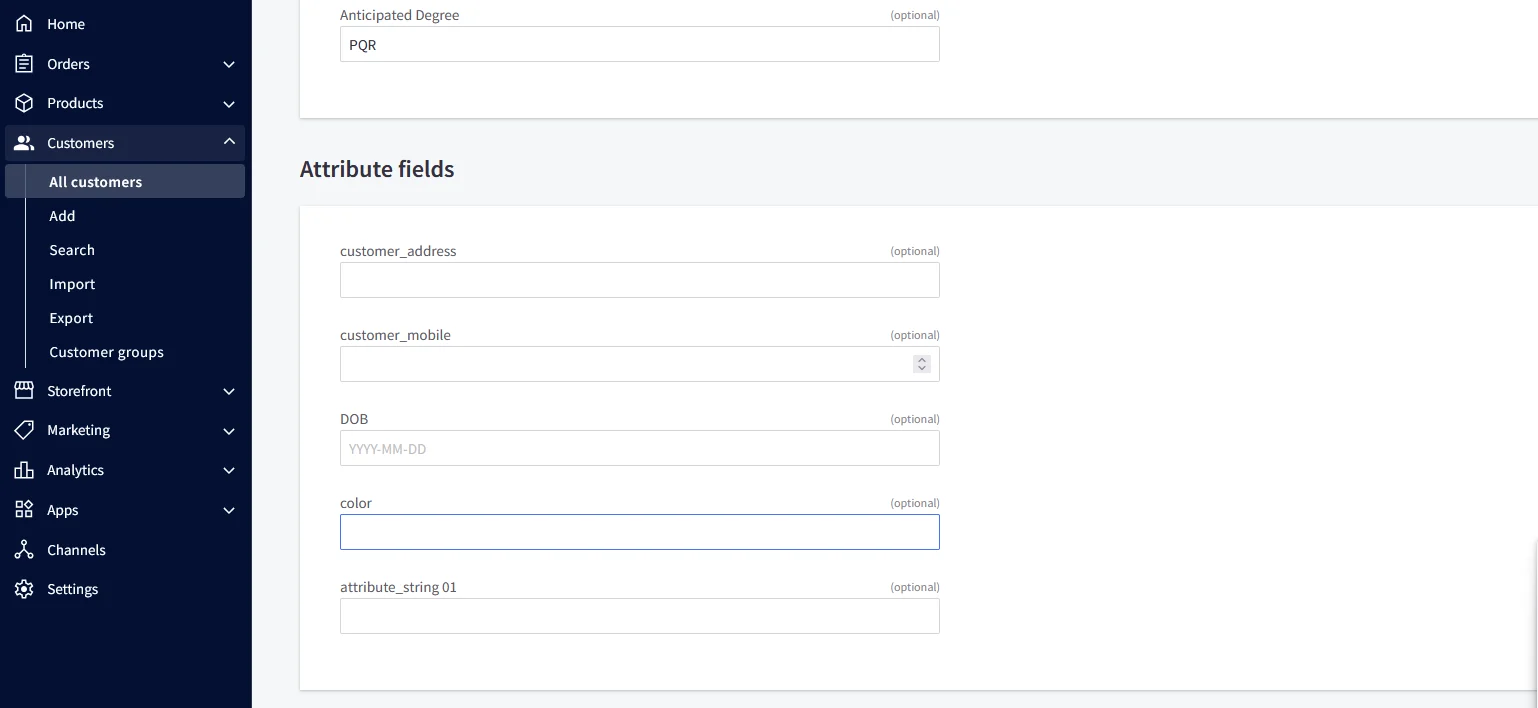
- Then we need to configure the attribute mapping in the application.
| Attribute Name | Attribute Type | Value |
|---|
| color | Custom Profile Attribute | blue |
| customer_address | Custom Profile Attribute | MG road |
| customer_mobile | Custom Profile Attribute | +911234567890 |
| DOB | Custom Profile Attribute | 2002-01-01 |
| attribute_string 01 | Custom Profile Attribute | testing |
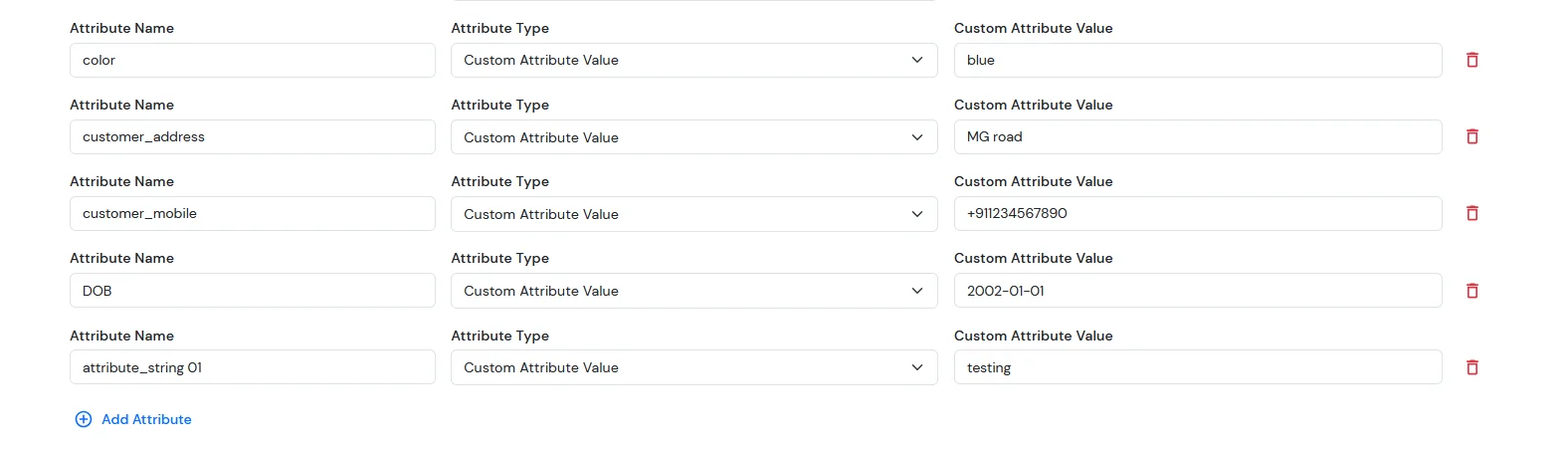
- After completing SSO, go to your BigCommerce dashboard.
- From the left sidebar, click on Customers.
- You will now see the list of all customers.
- Search for the specific user and click on their name.
- The customer profile will open — scroll down to the Customer Details section.
- Here, you will see the attribute fields, where you can view all the customer-submitted form-field details.
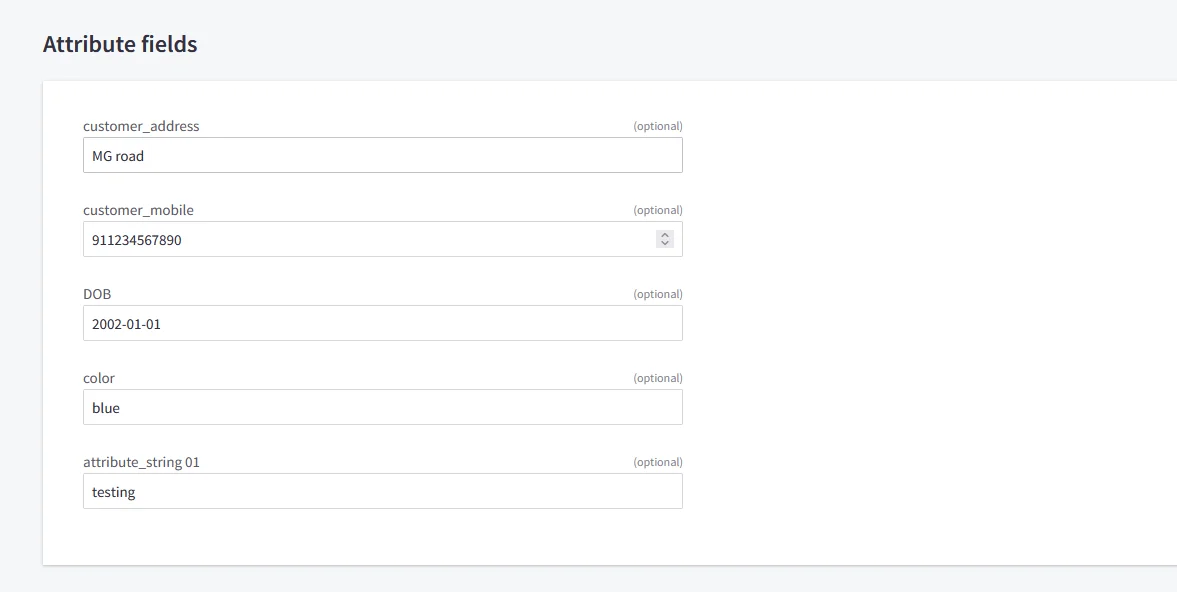
NOTE: Update customer profile during sso
- Go to the BigCommerce application you have configured in miniOrange.
- Open the Advanced tab.
- Scroll to the bottom of the page.
- Enable the checkbox Update Customer Profile During SSO.
For ExternaI Identity Provider
- Before syncing these fields to BigCommerce, you must first create the corresponding attributes in your external IDP. These attributes will then be mapped and synced to BigCommerce.
- Then we need to configure the attribute mapping in the application.
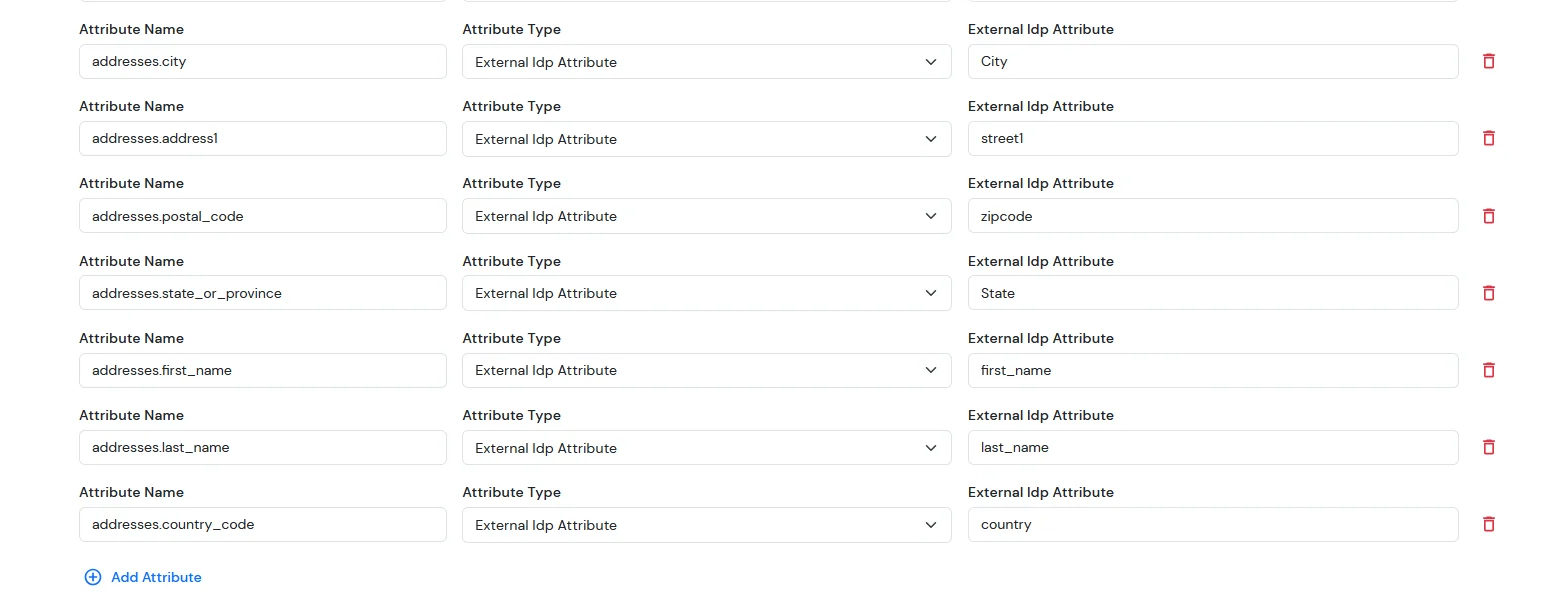
- For Address field:
| Attribute Name | Attribute Type | Value |
|---|
| addresses.first_name | External Idp Attribute | first_name |
| addresses.last_name | External Idp Attribute | last_name |
| addresses.address1 | External Idp Attribute | address1 |
| addresses.city | External Idp Attribute | city |
| addresses.state_or_province | External Idp Attribute | state/province |
| addresses.country_code | External Idp Attribute | country |
| addresses.postal_code | External Idp Attribute | postal_code |
Note: When sending the country value, always use the country code (e.g., US, IN). If you pass the full country name such as “United States”, the value will not be updated — only country codes are supported for correct mapping.
While syncing address fields, ensure that the city, state, and country values you provide are valid options supported by BigCommerce and exist in their respective dropdown lists.
- Now, after completing SSO, go to your BigCommerce dashboard. From the sidebar, click on Customers.
- You will see the list of all customers. Search for the specific user and click on their name.
- Next, open the Customer Address Book section — this is where you will be able to view the customer’s address details.

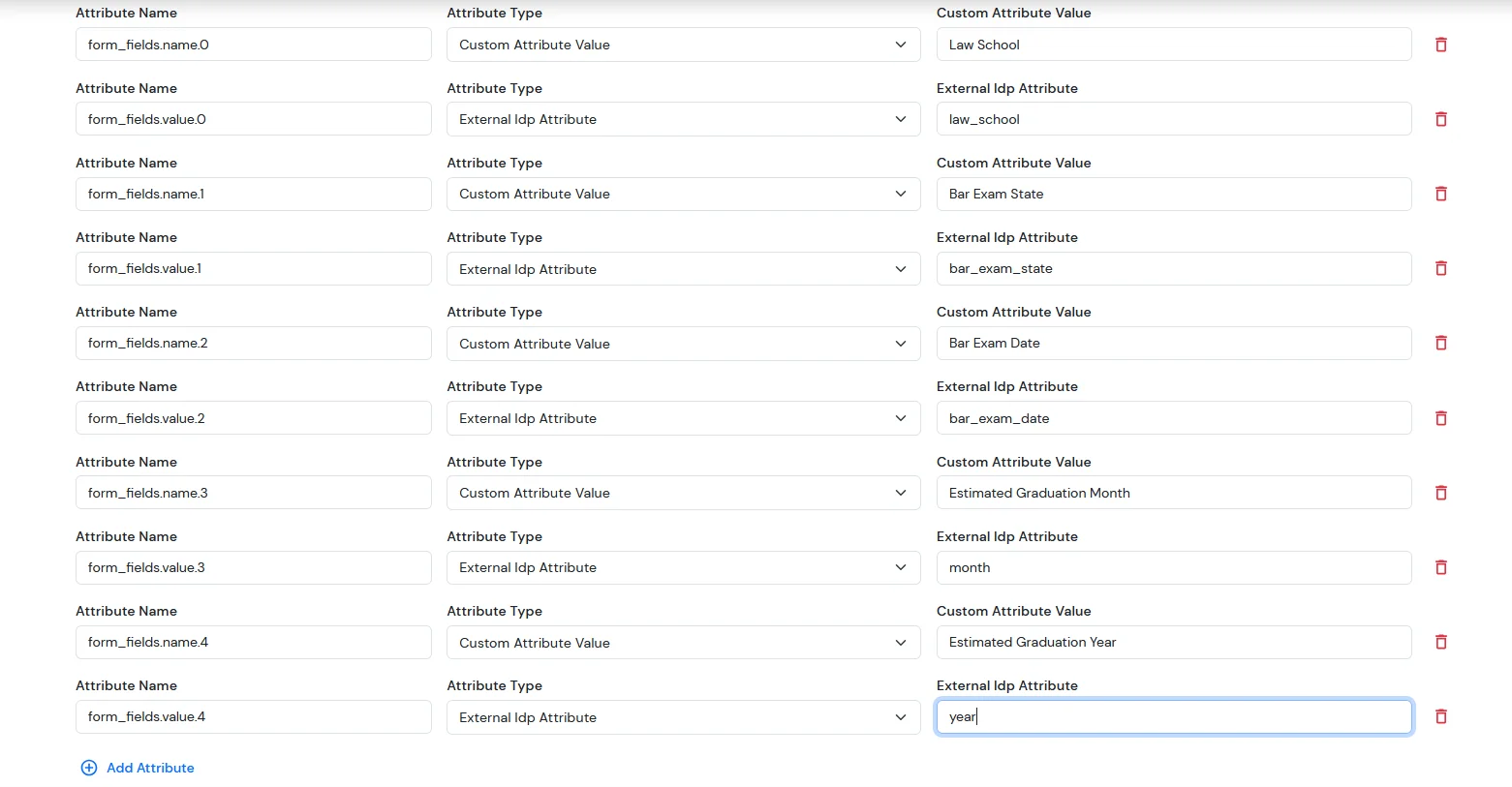
For the Sign up form fields:
- In BigCommerce, the following form fields are available. We need to configure the corresponding attribute mappings in the application to ensure these fields are correctly synced to BigCommerce.

| Attribute Name | Attribute Type | Value |
|---|
| form_fields.name.0 | Custom Attribute Value | Law School |
| form_fields.value.0 | External Idp Attribute | XYZ |
| form_fields.name.1 | Custom Attribute Value | Bar Exam State |
| form_fields.value.1 | External Idp Attribute | Arizona |
| form_fields.name.2 | Custom Attribute Value | Bar Exam Date |
| form_fields.value.2 | External Idp Attribute | 31-12-2025 |
| form_fields.name.3 | Custom Attribute Value | Estimated Graduation Month |
| form_fields.value.3 | External Idp Attribute | January |
| form_fields.name.4 | Custom Attribute Value | Estimated Graduation Year |
| form_fields.value.4 | External Idp Attribute | 2025 |
- After completing SSO, go to your BigCommerce dashboard.
- From the left sidebar, click on Customers.
- You will now see the list of all customers.
- Search for the specific user and click on their name.
- The customer profile will open — scroll down to the Customer Details section.
- Here, you will see the signup form fields, where you can view all the customer-submitted form-field details.

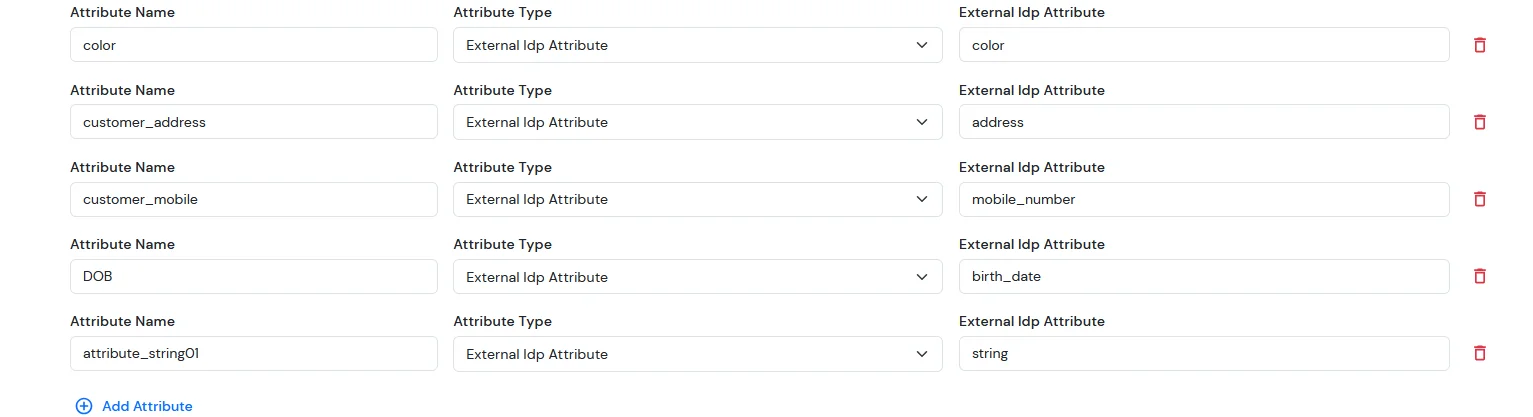
For Custom Attribute Fields
- In BigCommerce, the following attribute fields are available. We need to configure the corresponding attribute mappings in the application to ensure these fields are correctly synced to BigCommerce.

- Then we need to configure the attribute mapping in the application.
| Attribute Name | Attribute Type | Value |
|---|
| color | External Idp Attribute | blue |
| customer_address | External Idp Attribute | MG road |
| customer_mobile | External Idp Attribute | +911234567890 |
| DOB | External Idp Attribute | 2002-01-01 |
| attribute_string 01 | External Idp Attribute | testing |
- After completing SSO, go to your BigCommerce dashboard.
- From the left sidebar, click on Customers.
- You will now see the list of all customers.
- Search for the specific user and click on their name.
- The customer profile will open — scroll down to the Customer Details section.
- Here, you will see the attribute fields, where you can view all the customer-submitted form-field details.

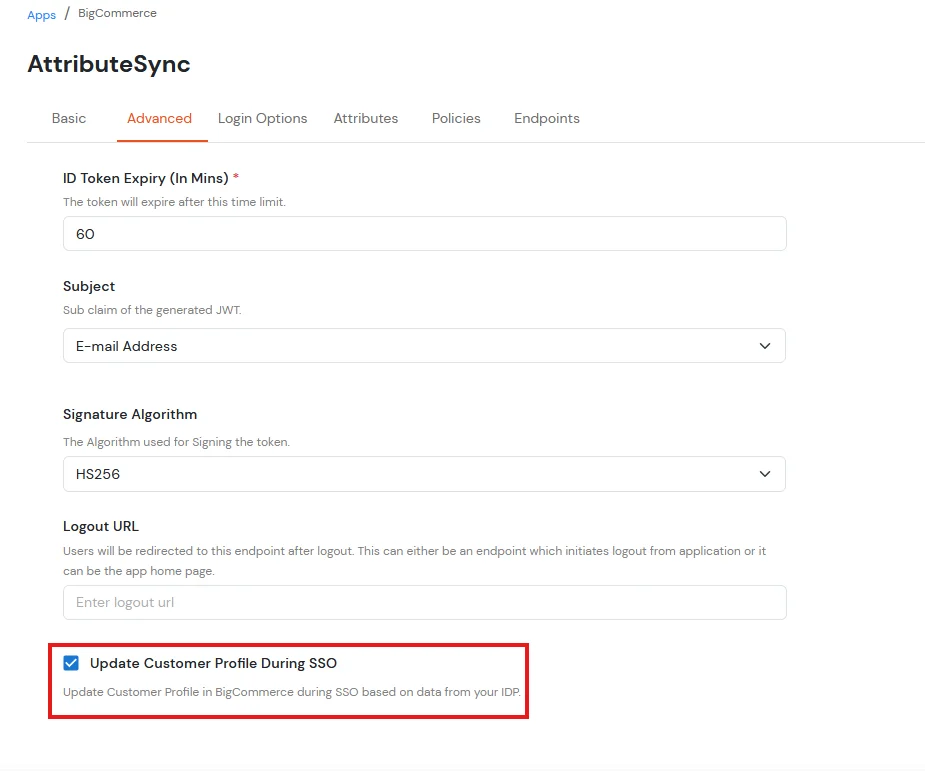
NOTE: Update customer profile during sso
- Go to the BigCommerce application you have configured in miniOrange.
- Open the Advanced tab.
- Scroll to the bottom of the page.
- Enable the checkbox Update Customer Profile During SSO.

4. Configure 2FA for BigCommerce
4.1: Configure 2FA for your Endusers
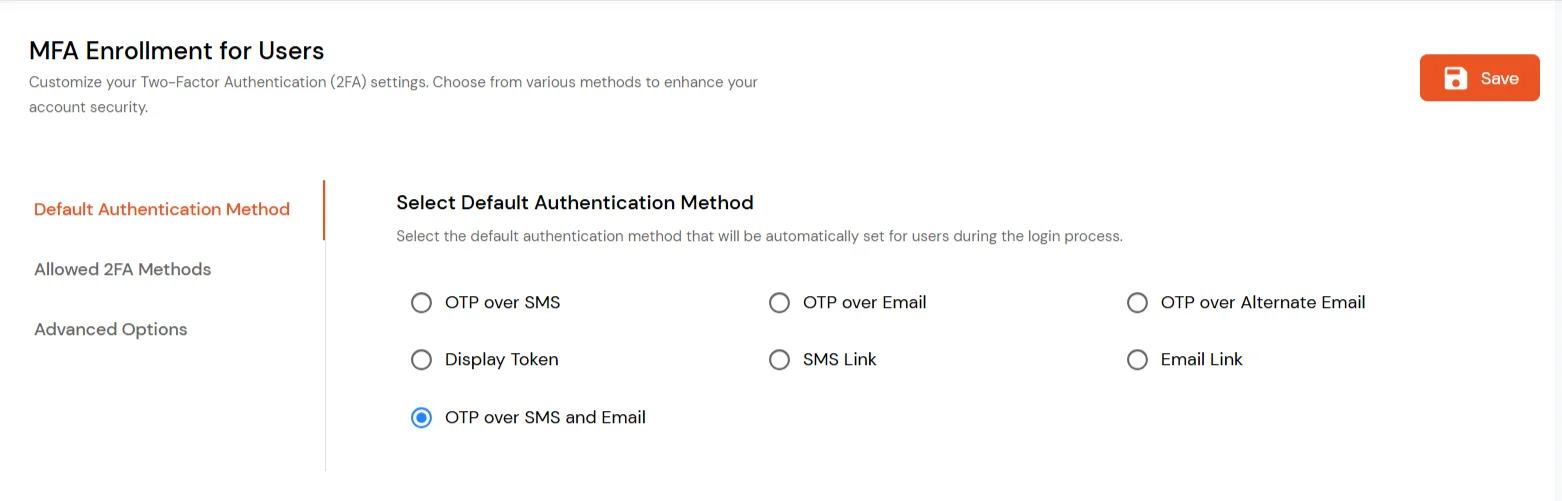
- To enable 2FA/MFA for endusers, go to 2-Factor Authentication >> 2FA Options For EndUsers.
- Select default Two-Factor authentication method for end users. Also, you can select particular 2FA methods, which you want to show on the end users dashboard.
- Once Done with the settings, click on Save to configure your 2FA settings.
4.2: Enduser 2FA Setup
- Login to End-User Dashboard using end user login URL.
- For Cloud Version: The login URL (branding url) which you have set.
- For On-Premise version: The login URL will be the same as Admin Login URL.
- Click on Setup 2FA tab . Then select any of the 2FA methods available.
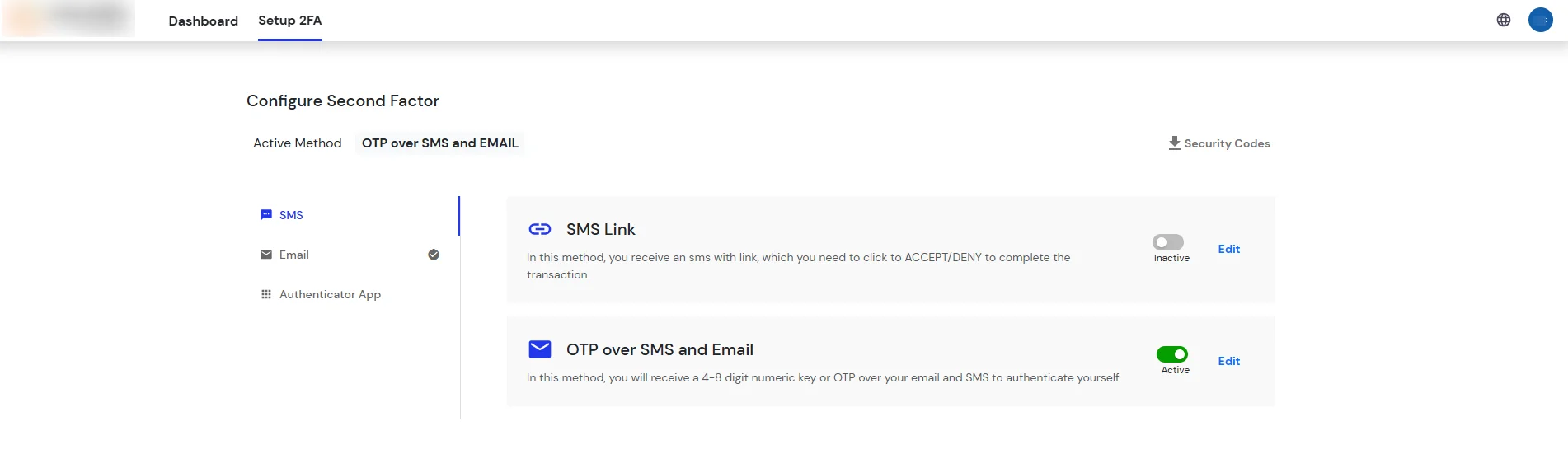
- For now, we have selected the SMS >> OTP OVER SMS and Email as our 2FA method. You can explore the guide to setup other 2FA methods here.
- Enable the OTP over SMS and Email, if you have your phone number or email added under your account information else click on Edit >> Click here to update.
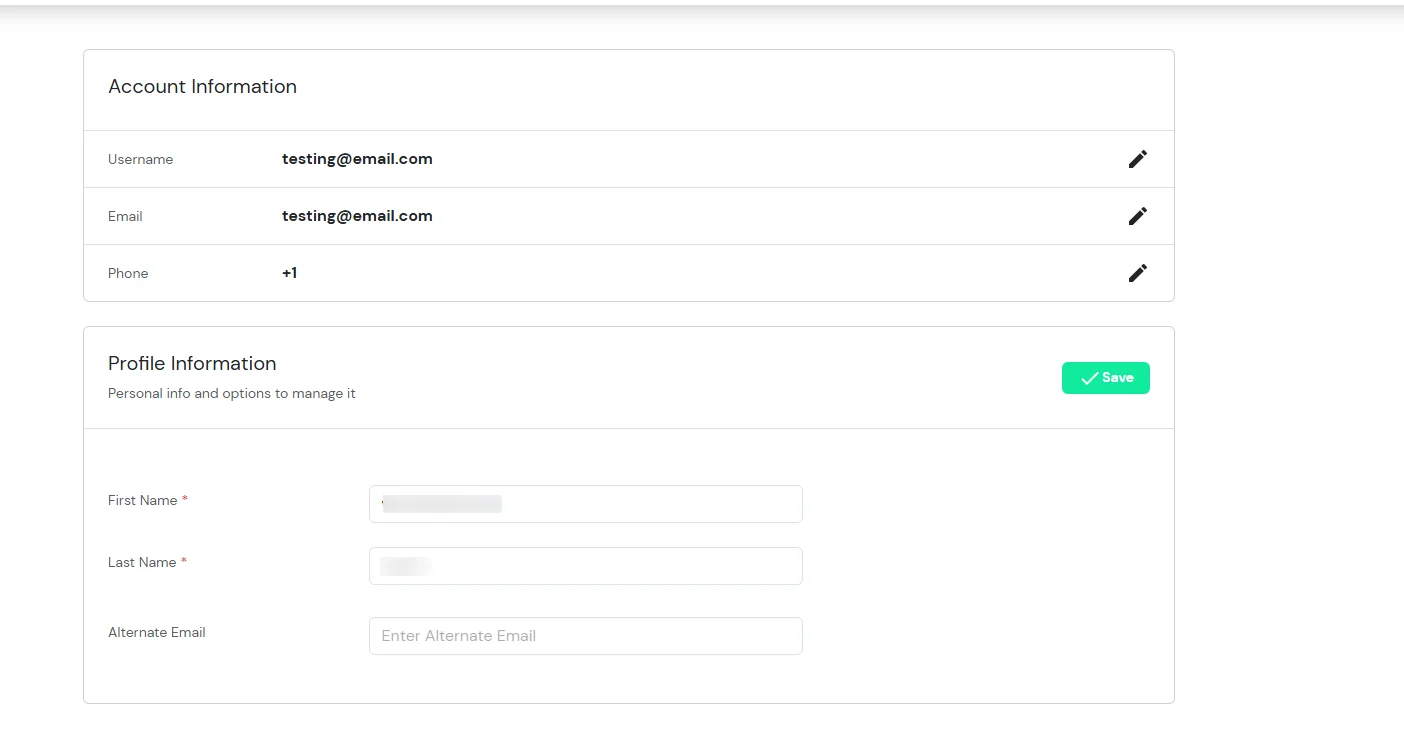
- In Account Information, click on edit icon.
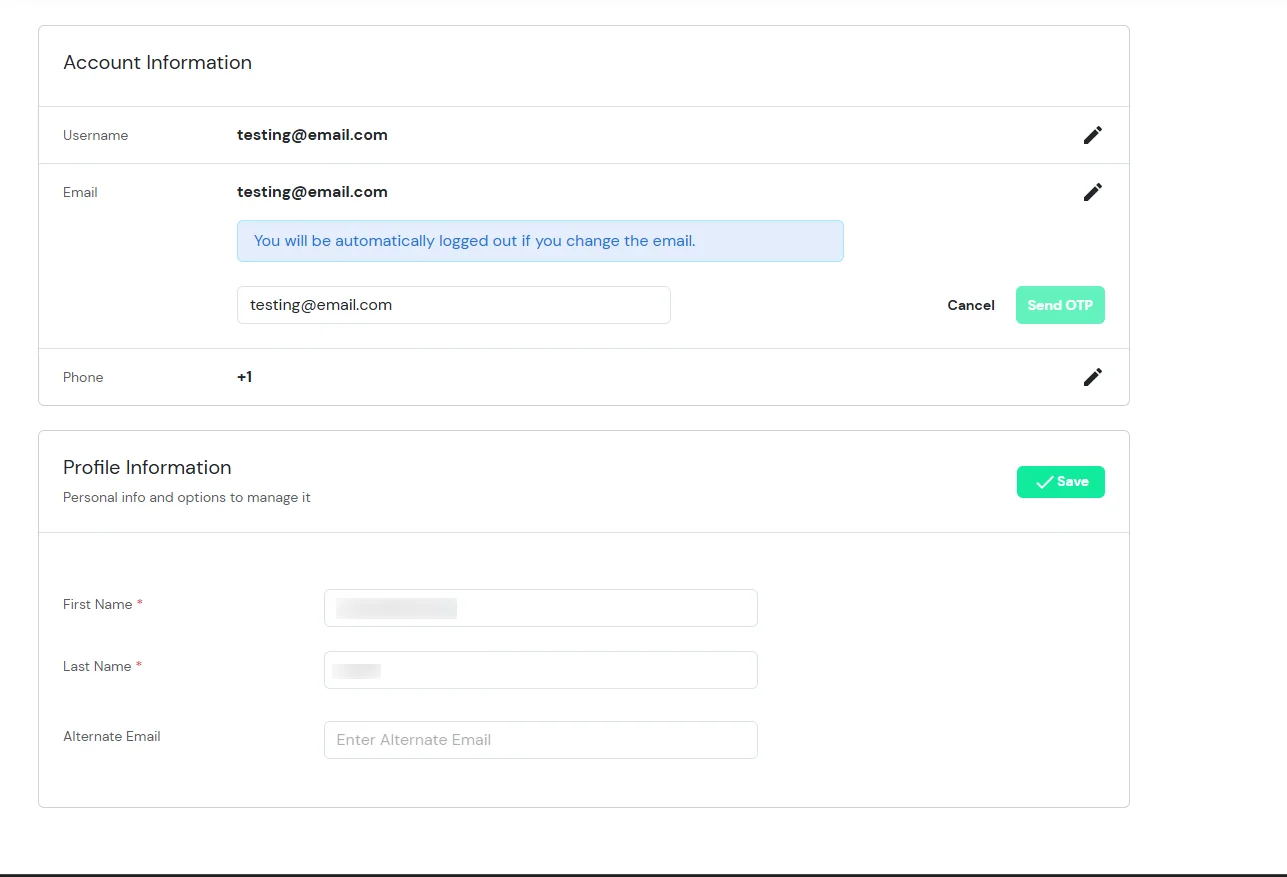
- Enter the OTP sent to your mail and click Validate.
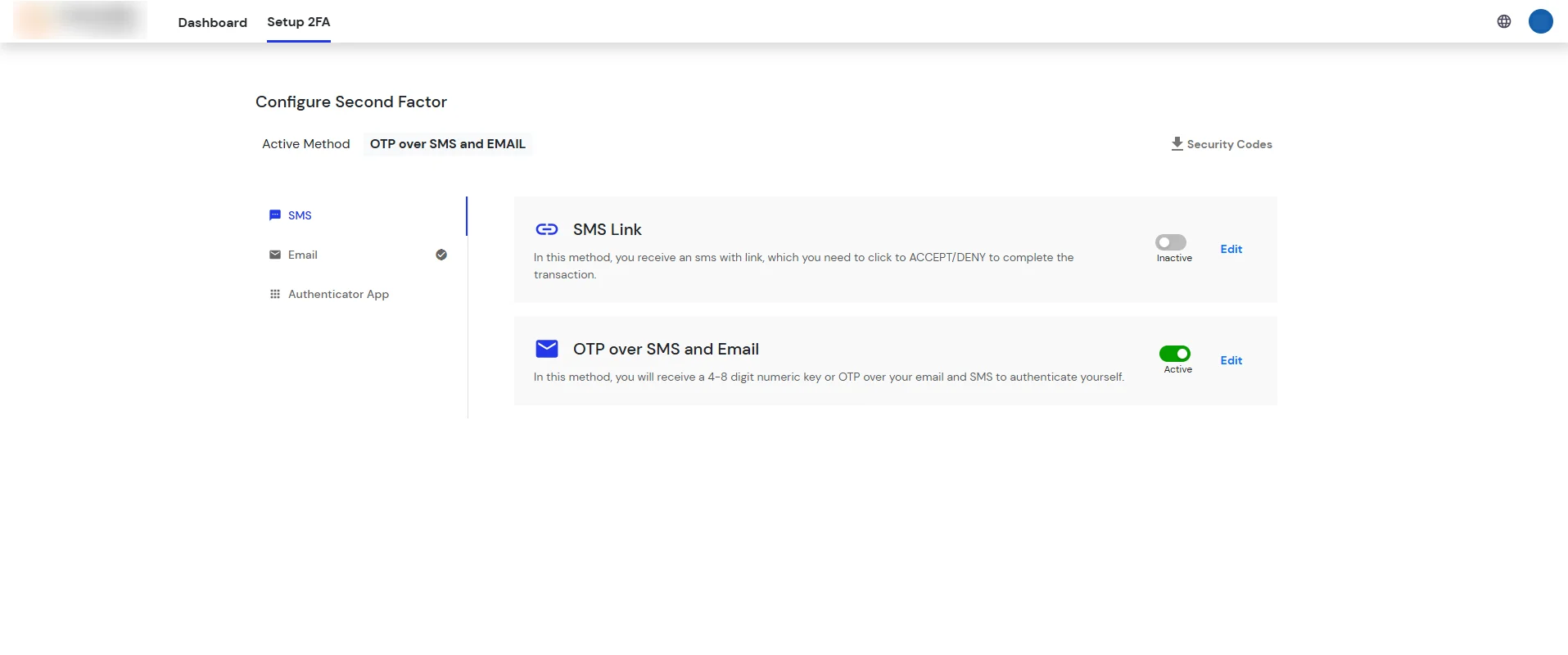
- After adding your phone number, turn on the toggle to activate OTP over SMS and Email.
5. Test BigCommerce 2FA
5.1: If 2FA for for End-user is configured
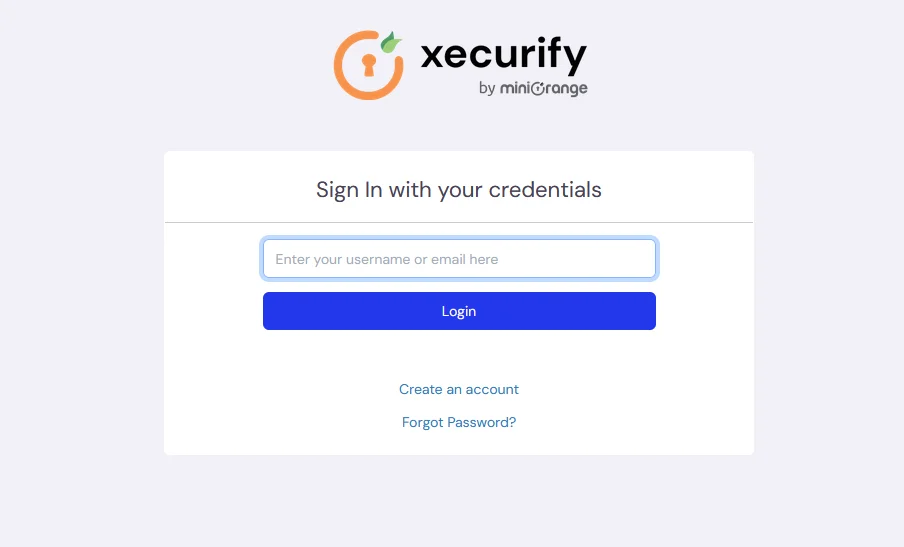
- Enter your login credentials of end user, and click on login. It will prompt you to verify yourself against the configured 2fa method.
For Example: If you have configured OTP over Email after entering credentials it will prompt for OTP.
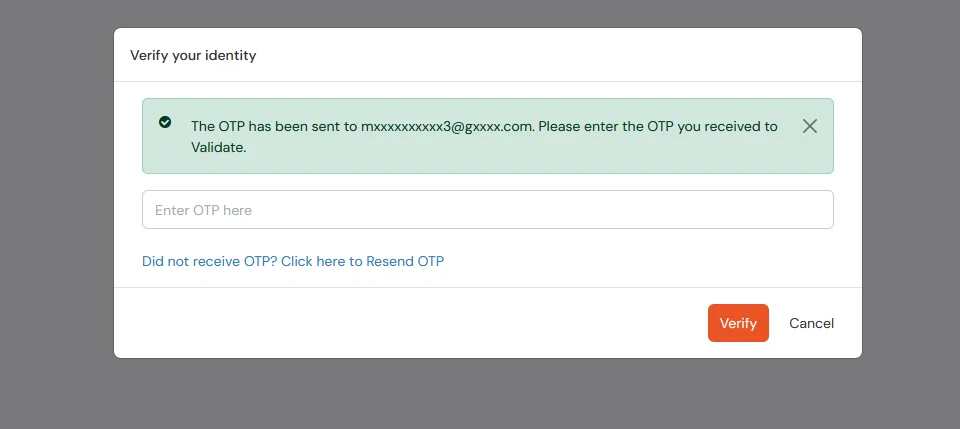
5.2: If 2FA for end-user is not enabled
- You will be prompted to register the end-user and set up the MFA method to get the user registered. It's a one time process.
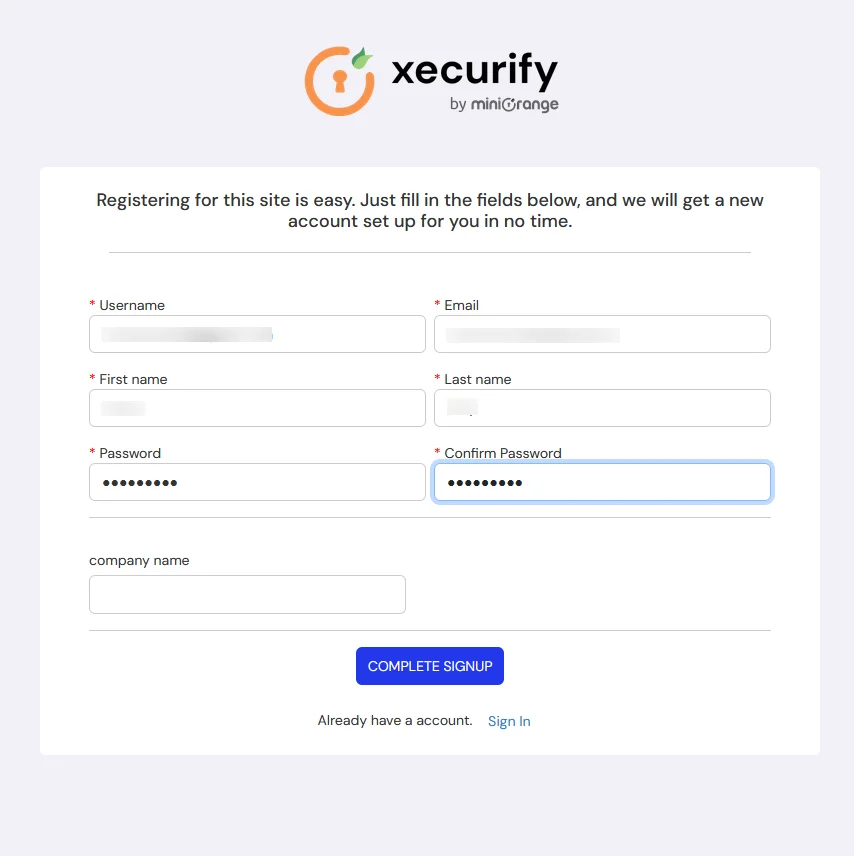
- Configure your basic details.
- Configure any authentication method of your choice.
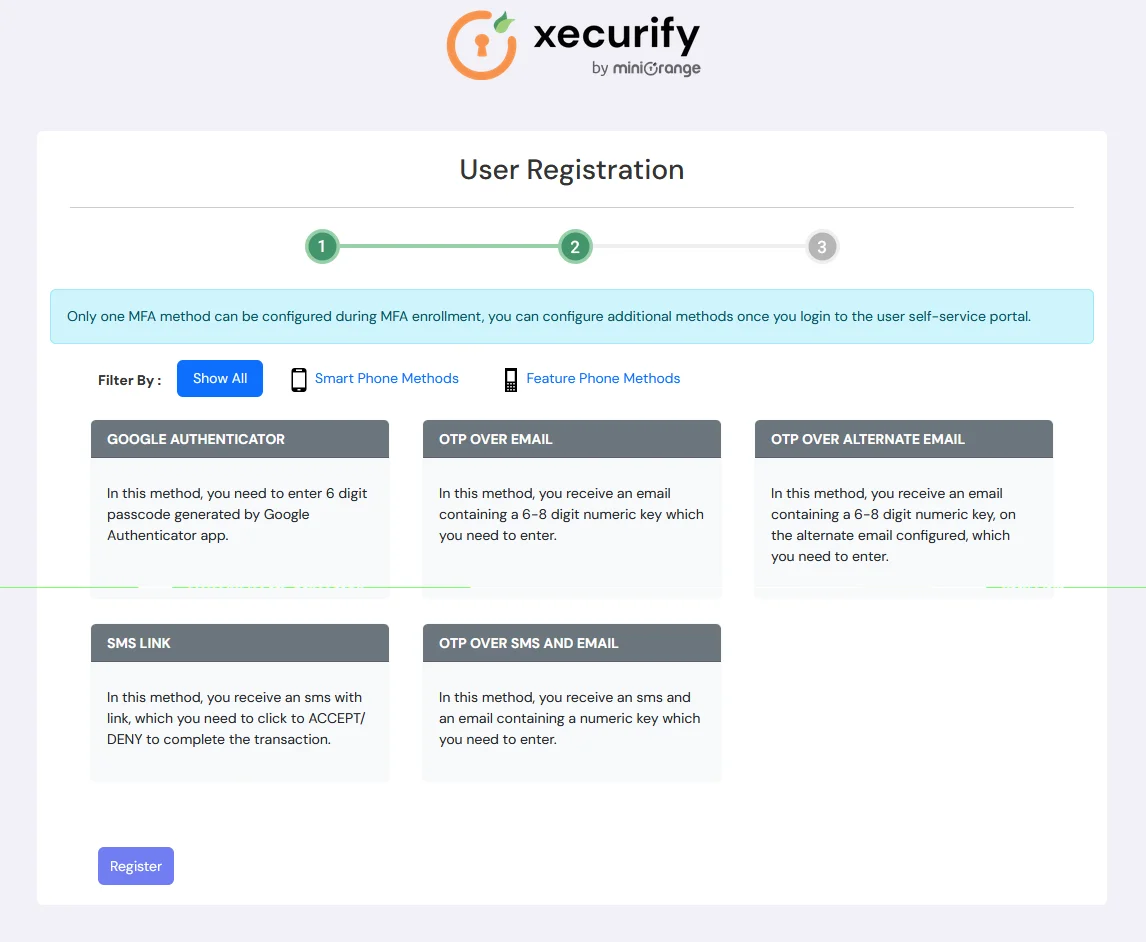
6. Adaptive Authentication with BigCommerce
6.1: Restricting access to BigCommerce with IP Blocking
- You can use adaptive authentication with BigCommerce Single Sign-On (SSO) to improve the security and functionality of Single Sign-On.
- You can allow an IP Address in a certain range for SSO or you can deny it based on your requirements and you can also challenge the user to verify his authenticity.
- Adaptive authentication manages the user authentication based on different factors such as Device ID, Location, Time of Access, IP Address and many more.
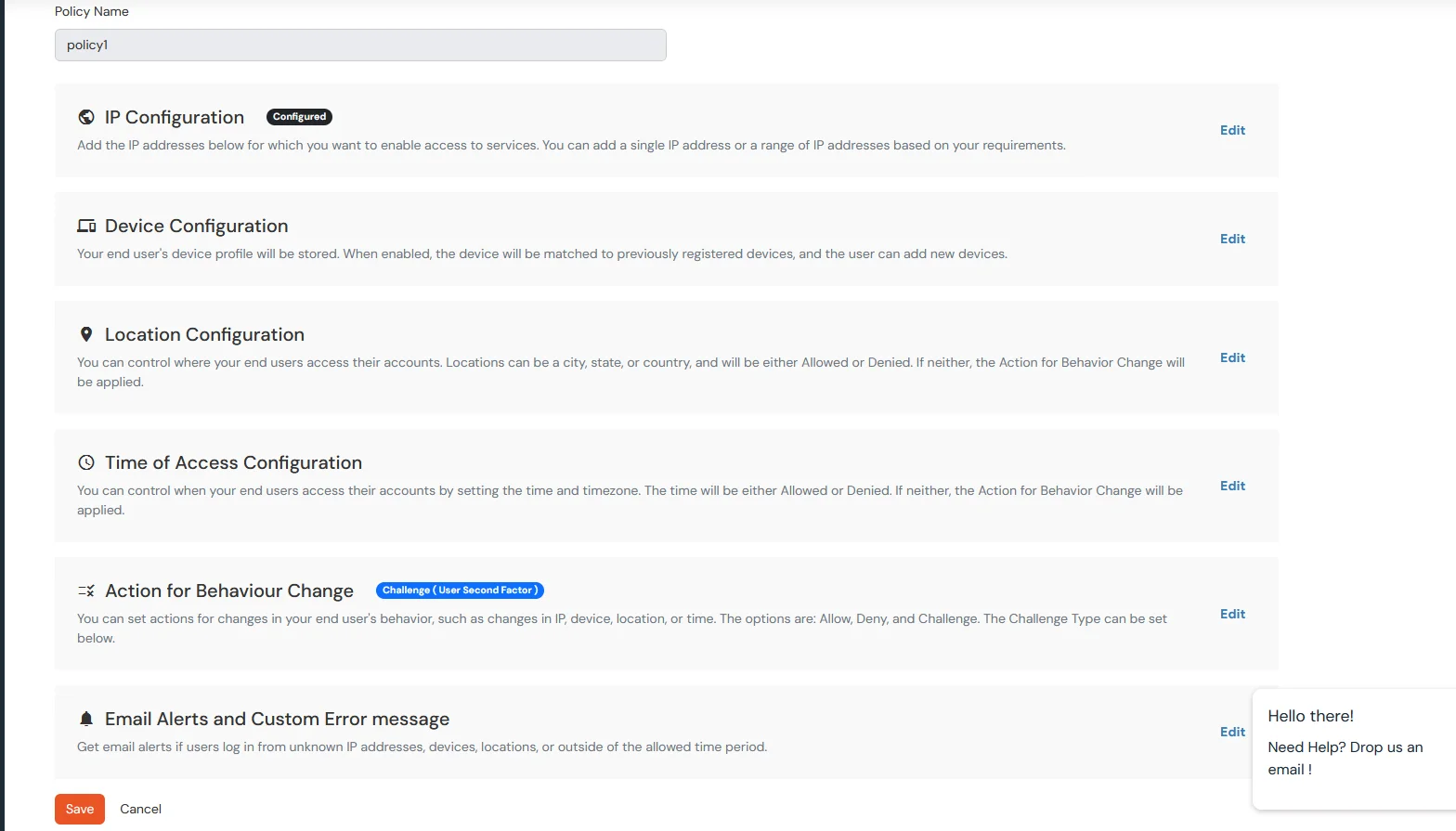
- You can configure Adaptive Authentication with IP Blocking in following way: Login to miniOrange >> Adaptive Authentication >> Add Policy.
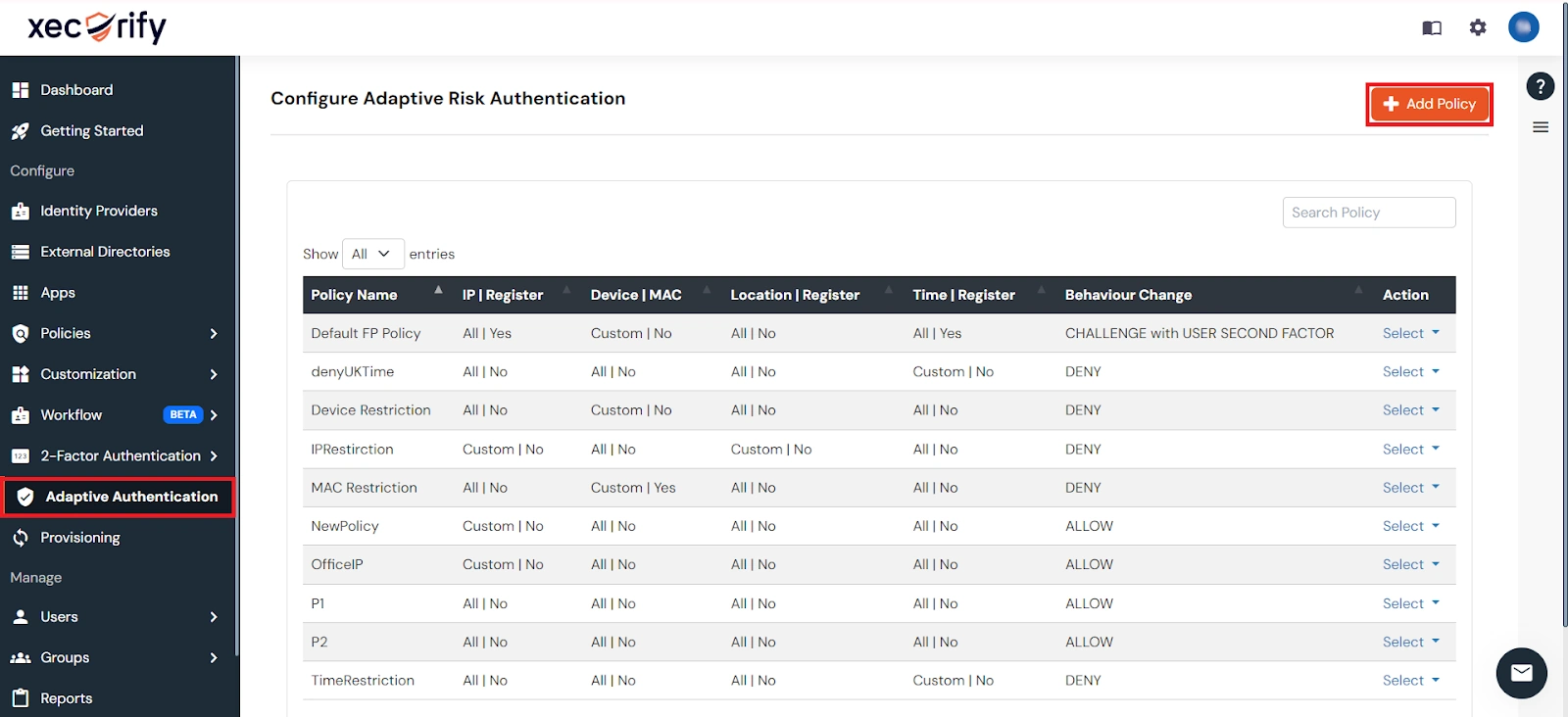
- Add a Policy Name for your Adaptive Authentication Policy.
- Now Enable IP Restriction option from the IP RESTRICTION CONFIGURATION section to configure custom IP range.
- Specify the IP Address range for which you want above setting to reflect.
- You can add more than one IP Address ranges by clicking on following button +.
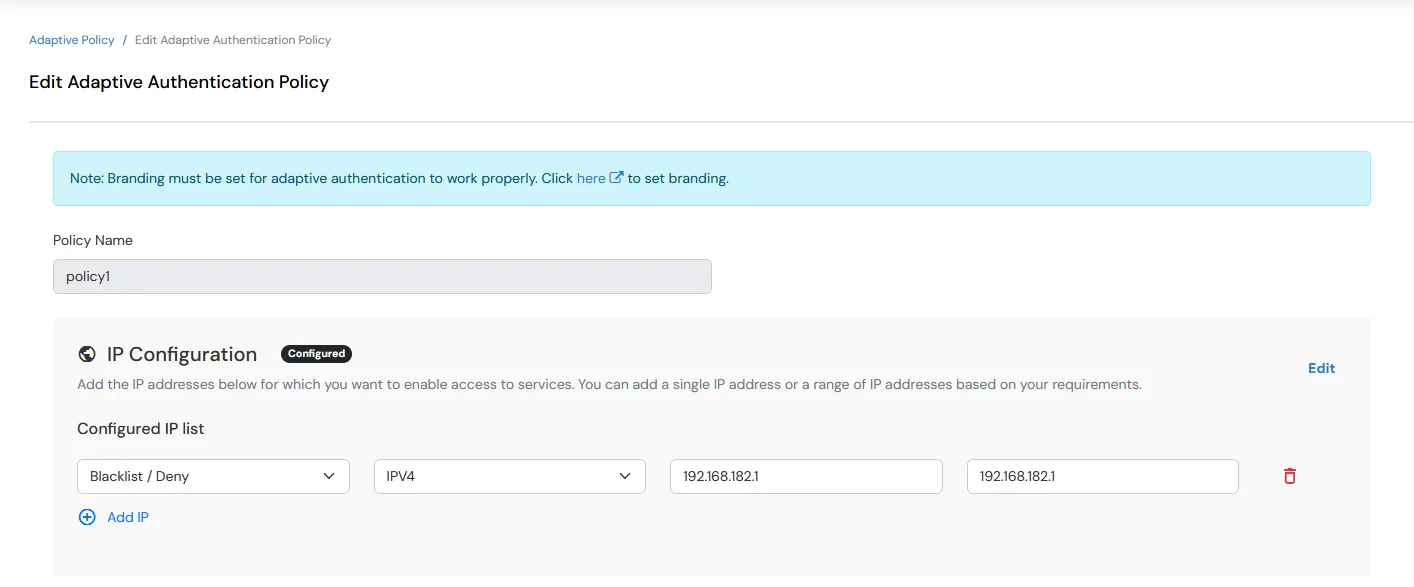
- Go to Action for behavior Change and then click on edit button and select the Challenge Type for user from the Action for behavior Change Section.
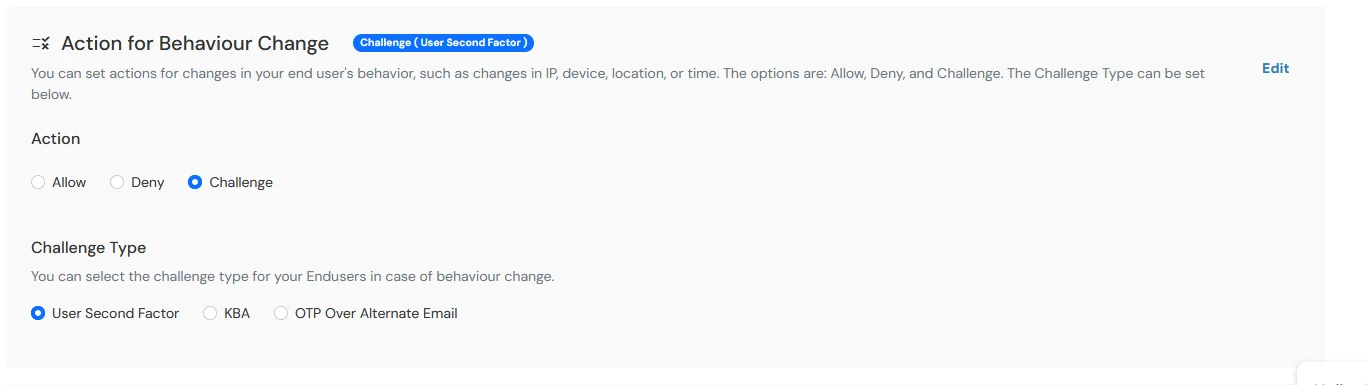
Action for behavior Change Options:
| Attribute |
Description |
| Allow |
Allow user to authenticate and use services if Adaptive authentication condition is true. |
| Deny |
Deny user authentications and access to services if Adaptive authentication condition is true. |
| Challenge |
Challenge users with one of the three methods mentioned below for verifying user authenticity. |
Challenge Type Options:
| Attribute |
Description |
| User second Factor |
The User needs to authenticate using the second factor he has opted or assigned for such as
|
| KBA (Knowledge-based authentication) |
The System will ask user for 2 of 3 questions he has configured in his Self Service Console. Only after right answer to both questions user is allowed to proceed further. |
| OTP over Alternate Email |
User will receive a OTP on the alternate email he has configured threw Self Service Console. Once user provides the correct OTP he is allowed to proceed further. |
- Scroll to the end and click on Save.
6.2: Adaptive Authentication with Limiting number of devices
- Using Adaptive Authentication you can also restrict the number of devices the end user can access the Services on.
- You can allow end users to access services on a fixed no. of devices. The end users will be able to access services provided by us on this fixed no. of devices.
- You can configure Adaptive Authentication with Device Restriction in following way
- Login to Self Service Console >> Adaptive Authentication.
- Add a Policy Name for your Adaptive Authentication Policy.
- Go to Action for behavior Change and then click on edit button and select the Challenge Type for user from the Action for behavior Change Section.
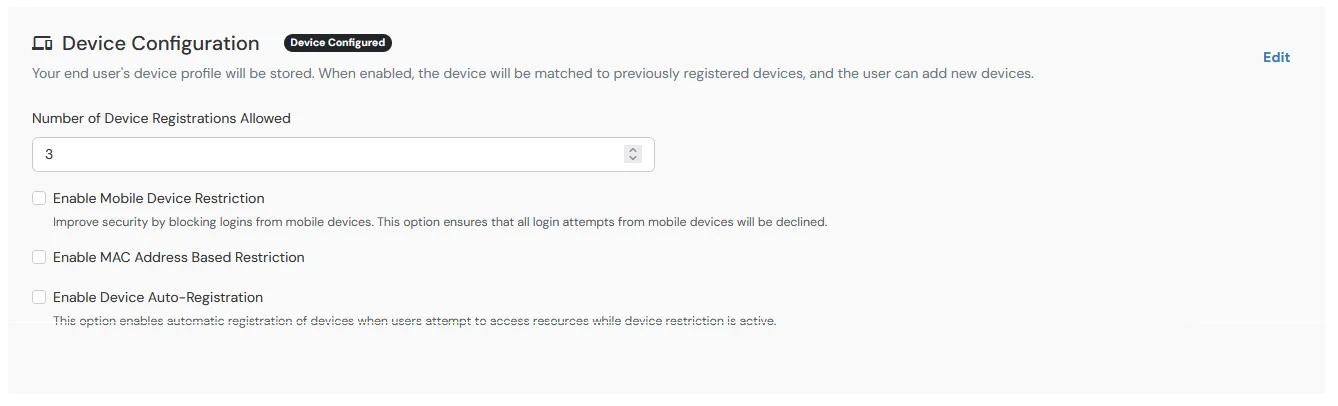
- Enter the Number of Devices which are allowed to register in field next to Number of Device Registrations Allowed.
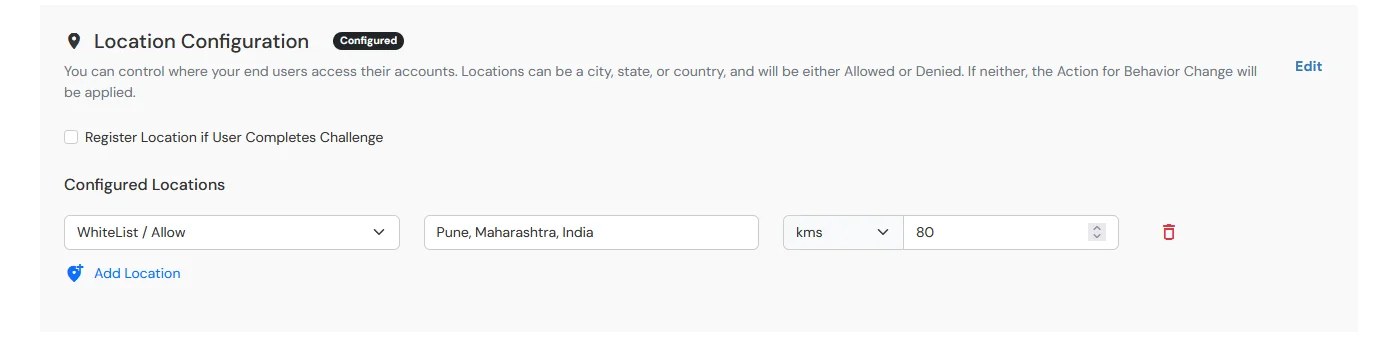
6.3: Location Restriction Configuration
- In this restriction method admin configures a list of locations where we want to allow end-users to either login or deny based on the condition set by the super admin.
- When a user tries to login with adaptive authentication enabled, his Location Attributes such as (Latitude, Longitude and Country Code) are verified against the Location list configured by the super admin and based on this user will be either allowed, challenged or denied.
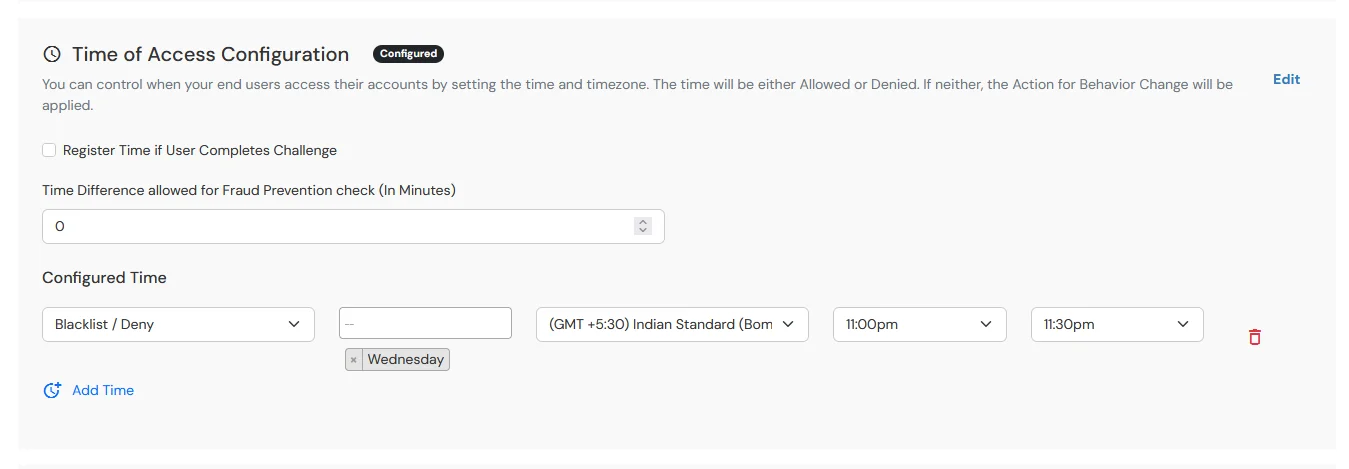
6.4: Time of Access Configuration
- In this restriction method super admin configures a time zone with Start and End Time’s for that time zone and users are either allowed, denied or challenged based on the condition in the policy.
- When an end-user tries to login with the adaptive authentication enabled, his time zone related attributes such as Time-Zone and Current System Time are verified against the list configured by the super admin and based on the configuration the user is either allowed, denied or challenged.
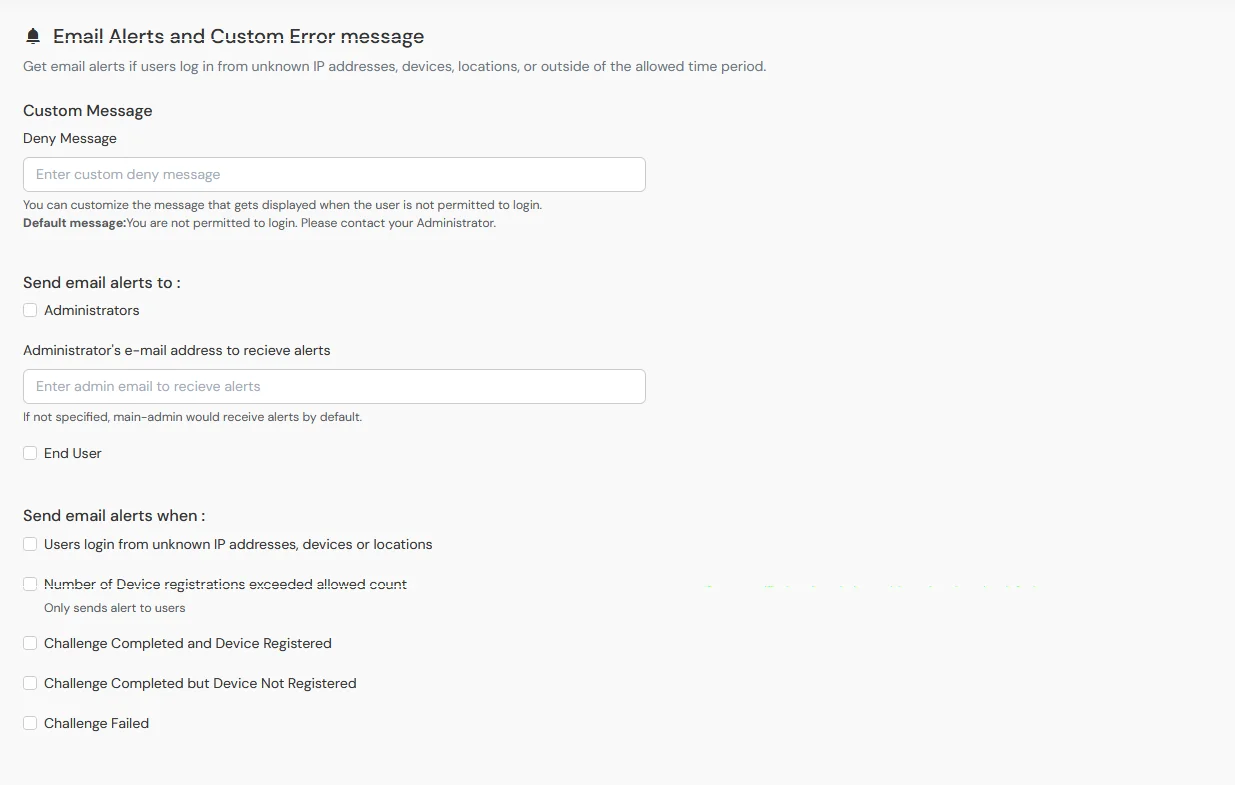
6.5: Email Alerts and Custom Error message
- This section handles the notifications and alerts related to Adaptive Authentication.
- In case you want to customize the deny message that end user receive in case his authentication denied due to adaptive policy, you can do this by entering the message inside Deny message text box.
- The Send Email Alerts section allows you to enable or disable email notifications for Administrators and End-Users.
| Option |
Description |
| Challenge Completed and Device Registered |
Enabling this option allows you to send an email alert when an end-user completes a challenge and registers a device. |
| Challenge Completed but Device Not Registered |
Enabling this option allows you to send an email alert when an end-user completes a challenge but do not registers the device. |
| Challenge Failed |
Enabling this option allows you to send an email alert when an end-user fails to complete the challenge. |
External References





















































