Need Help? We are right here!
Search Results:
×Kentico CMS is a web content management system (WCMS) for building websites, online stores, intranets, and Web 2.0 community sites. Kentico CMS uses ASP.NET and Microsoft SQL Server for development via its Portal Engine, using Visual Studio, or through Microsoft MVC.Kentico is the only fully integrated ASP.NET CMS, E-commerce, and Online Marketing platform that allows you to create truly optimized digital customer experiences across multiple channels. With Web Farms, Continuous Integration, GDPR and Data Protection, and MVC development fully supported across the platform, Kentico empowers your developers to deliver state-of-art websites and experiences faster.
https://<kentico-site-base-url>/?ssoaction=config
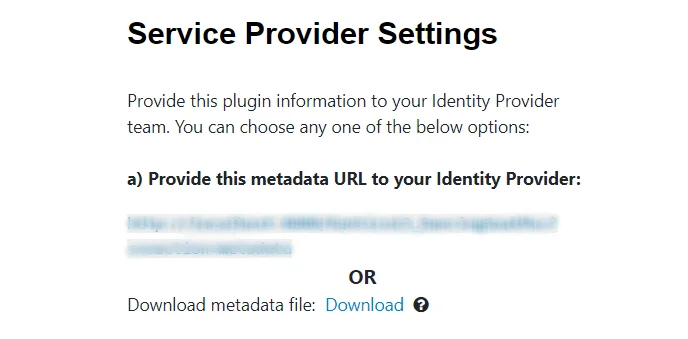
There are below two ways with which you can get the SAML SP metadata to configure on your identity provider end.
A] Using SAML metadata URL or metadata file:
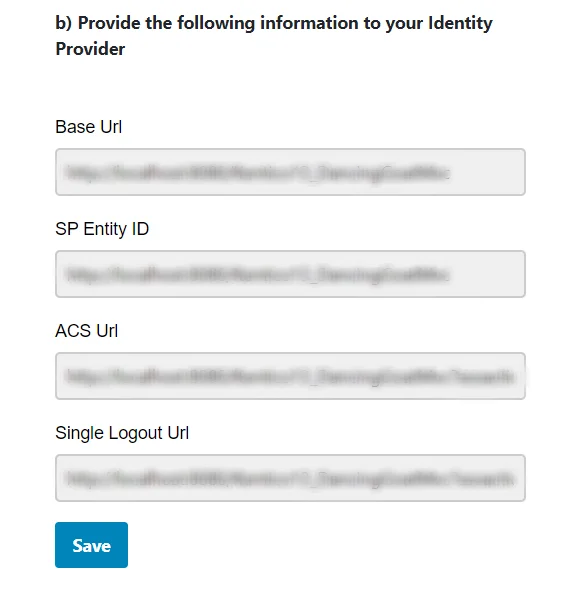
B] Uploading metadata manually:
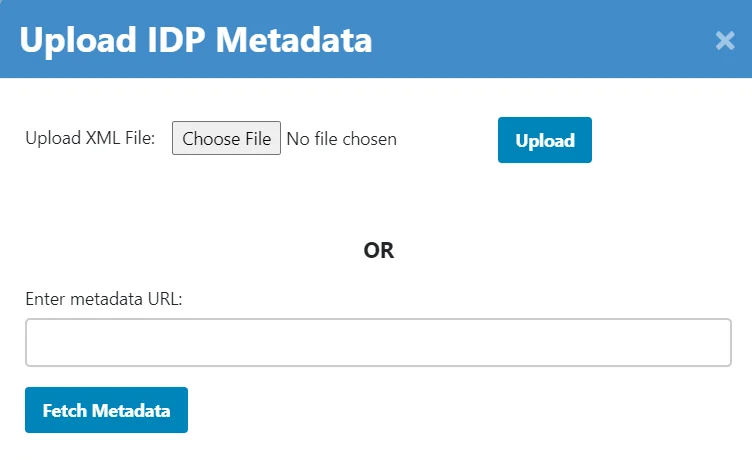
There are below two ways with which you can configure your SAML identity provider metadata in the module.
A] Upload metadata using the Upload IDP Metadata button:
B] Configure the identity provider metadata manually:
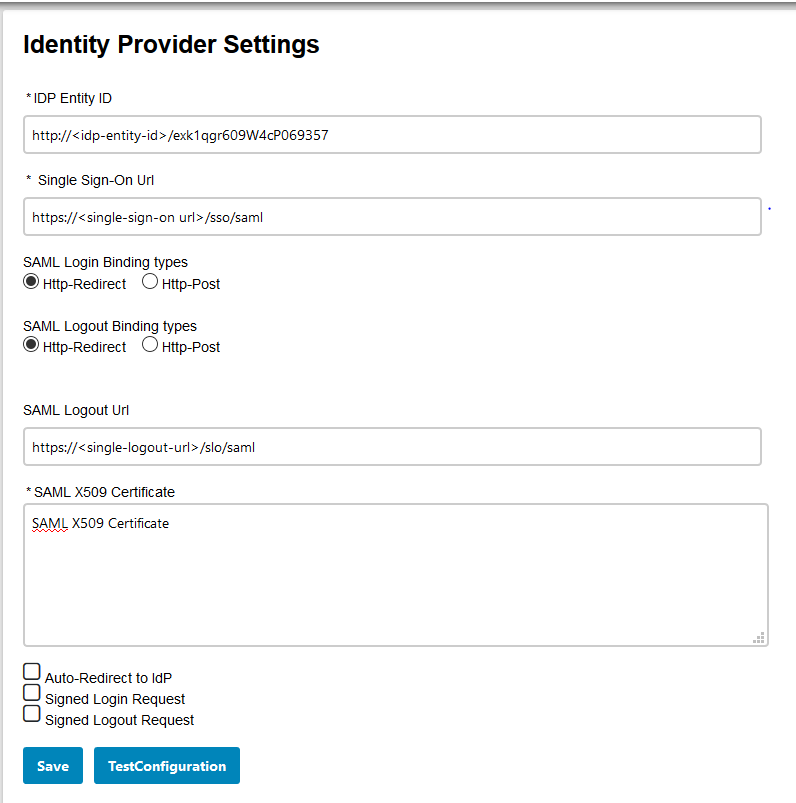
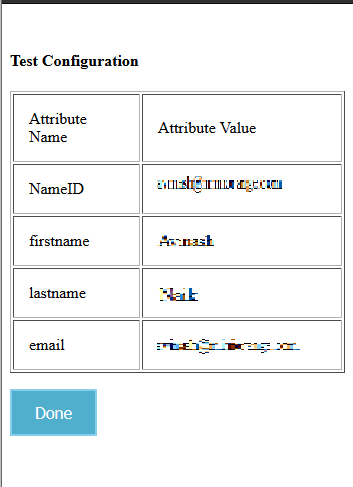
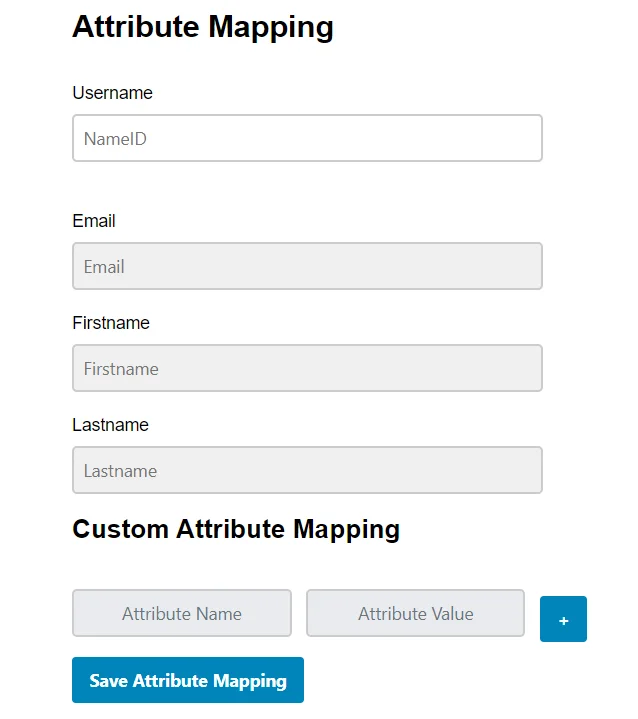
http://<kentico-base-url>/?ssoaction=login
<a href="http://<kentico-base-url>/?ssoaction=login”>Log in</a>"
http://base-url/?ssoaction=logout
<a href="http://base-url/?ssoaction=logout”>Log out</a>"
You can configure the kentico SAML 2.0 Single Sign-On (SSO) module with any Identity Provider such as ADFS, Azure AD, Bitium, Centrify, G Suite, JBoss Keycloak, Okta, OneLogin, Salesforce, AWS Cognito, OpenAM, Oracle, PingFederate, PingOne, RSA SecureID, Shibboleth-2, Shibboleth-3, SimpleSAML, WSO2 or even with your own custom identity provider.
Not able to find your IdP? Contact us at info@xecurify.com and we'll help you set up SSO with your IdP in no time.
| SAML SSO into Custom ASP.NET apps | Click here to know more |
| SAML SSO into DotNetNuke (DNN) site | Click here to know more |
| OAuth SSO into DotNetNuke (DNN) site | Click here to know more |
| SAML SSO into Sitefinity site | Click here to know more |
| SAML SSO into Umbraco site | Click here to know more |
miniOrange Identity Management Features
miniOrange Single Sign-On (SSO) Solution provides easy and seamless access to all enterprise resources with one set of credentials. miniOrange also provides secure authentication by establishing a trust relationship between the Service Provider and Identity Provider. miniOrange Single Sign-On supports SSO to any type of device or application whether they are in the cloud or on-premise. Learn More
Secure your application from password theft using multi-factor authentication methods with 15+ authentication types provided by miniOrange. Our multi-factor authentication methods prevent unauthorized users from accessing information and resources having passwords alone as an authentication factor. Enabling second-factor authentication for protects you against password thefts. Learn More
miniOrange provides IP blocking/IP restriction for login which adds security to Gmail, Web, and other applications. In this, we provide you option for IP blocking which includes both automatic (based on user behavior) and manual IP blocking which includes blacklisting and whitelisting of IP addresses to provide access restriction, the office only access, intranet access & network restriction. Learn More
miniOrange Adaptive Authentication aims to provide a better experience to reduce the authentication burden on users while enforcing strong authentication where it is needed the most. For example, when a user attempts to access an application via an unregistered device then they may be prompted to register it. If the user logs in from a geographical location other than their office, they may be asked to answer security questions. Learn More
miniOrange User Provisioning provides an easy way of creation, management, and maintenance of end-users especially for large enterprises to reduce the risk for unauthorized access of information. User provisioning includes the creation, updating and deletion of user accounts. User provisioning makes life easier for admins because they do not have to manually arrange access for each user. Learn More
The most practical way to strengthen authentication is to require a second factor after the username/password stage. Since a password is something that a user knows, ensuring that the user also has something or using biometrics thwarts attackers that steal or gain access to passwords.
Traditional two-factor authentication solutions use hardware tokens (or "fobs") that users carry on their keychains. These tokens generate one-time passwords for the second stage of the login process. However, hardware tokens can cost up to $40 each. It takes time and effort to distribute them, tracks who has which one, and replace them when they break. They're easy to lose, hard to use, and users consistently report high levels of frustration with token-based systems.
miniOrange authentication service has 15+ authentication methods.
You can choose from any of the above authentication methods to augment your password based authentication. miniOrange authentication service works with all phone types, from landlines to smart-phone platforms. In the simplest case, users just answer a phone call and press a button to authenticate. miniOrange authentication service works internationally and has customers authenticating from many countries around the world.
miniOrange helps you with adding login/authentication into your nopCommerce site using OAuth, OpenID, ADFS, SAML and WSFED protocols. Looking for site integration with legacy apps such as Active Directory, SiteMinder, Radius, Unix and so on, we can help you with that.
miniOrange provides 24/7 support for all the Secure Identity Solutions. We ensure high quality support to meet your satisfaction.
Try Nowminiorange provides most affordable Secure Identity Solutions for all type of use cases and offers different packages based on customer's requirement.
Request A QuoteWe offer Secure Identity Solutions for Single Sign-On, Two Factor Authentication, Adaptive MFA, Provisioning, and much more. Please contact us at -
+1 978 658 9387 (US) , +91 97178 45846 (India) | info@xecurify.com