How to add an OAuth App
miniOrange supports Single Sign-on into your apps, to securely login for admins and users. miniOrange supports several different protocols for your applications, such as
SAML, WS-FED, OAuth, OIDC, JWT, RADIUS, etc. Using Single Sign-on, users can use one set of credentials to login to multiple applications. This improves security, as it reduces avenues for phishing attacks, and also improves access to your application.
OAuth (Open Authorization) is an open standard for token-based authentication and authorization. OAuth allows an end-user's account information to be used by third-party services, such as Facebook, without exposing the user's password. It acts as an intermediary on behalf of the end-user, providing the service with an access token that authorizes specific account information to be shared.
miniOrange provides a solution to perform single sign-on(SSO) for applications supporting OAuth protocol, like Salesforce, WordPress, Joomla, Atlassian, Azure AD, Reddit, Spotify, Paypal, WHMCS, Slack, Discord, etc.
Configure Single Sign-On (SSO) Settings for OAuth Apps:
- Login into miniOrange Admin Console.
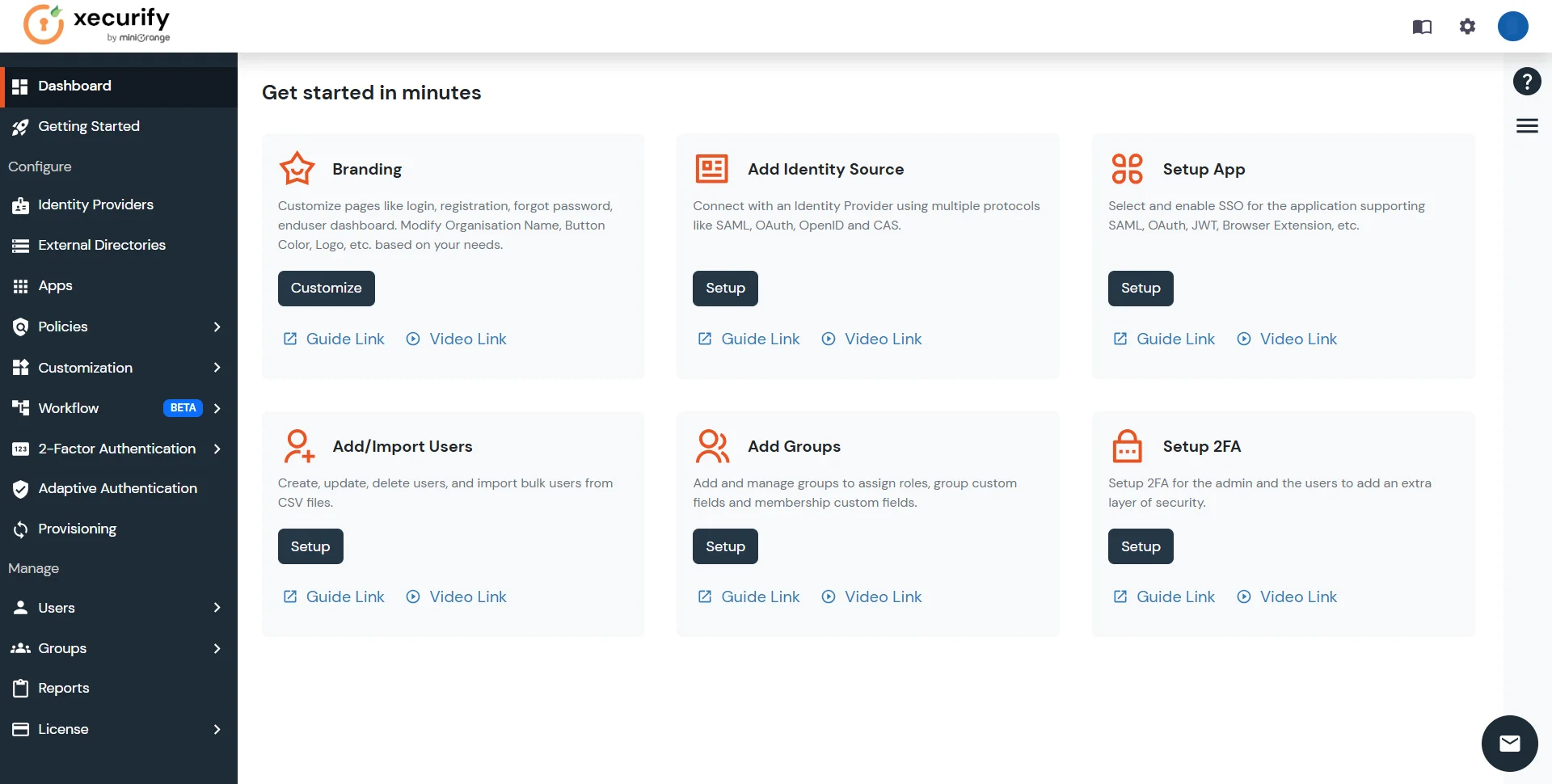
- Click on Apps. It shows a list of all configured applications and option to modify them. Click on Add Application.
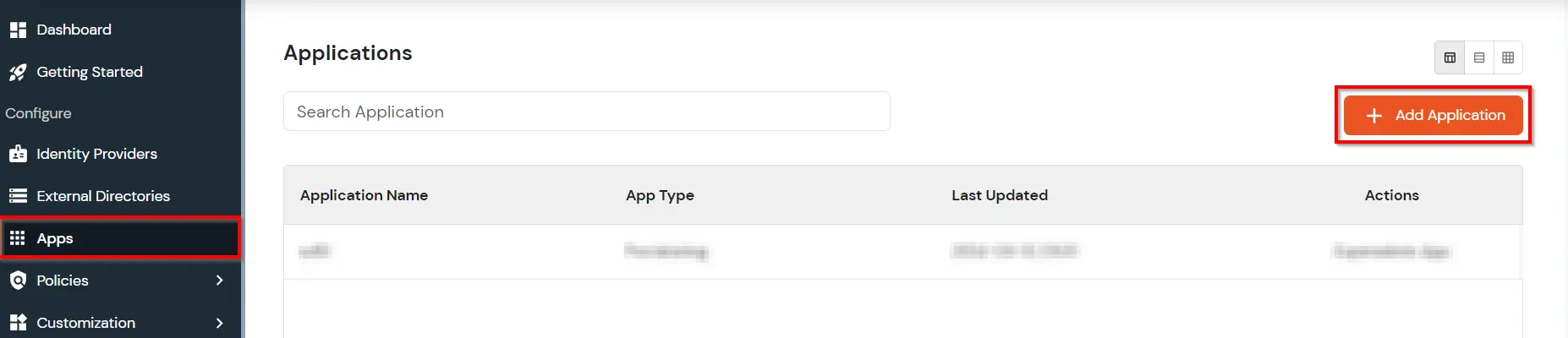
- Under Choose Application, select OAuth/OpenID from the All Apps dropdown.
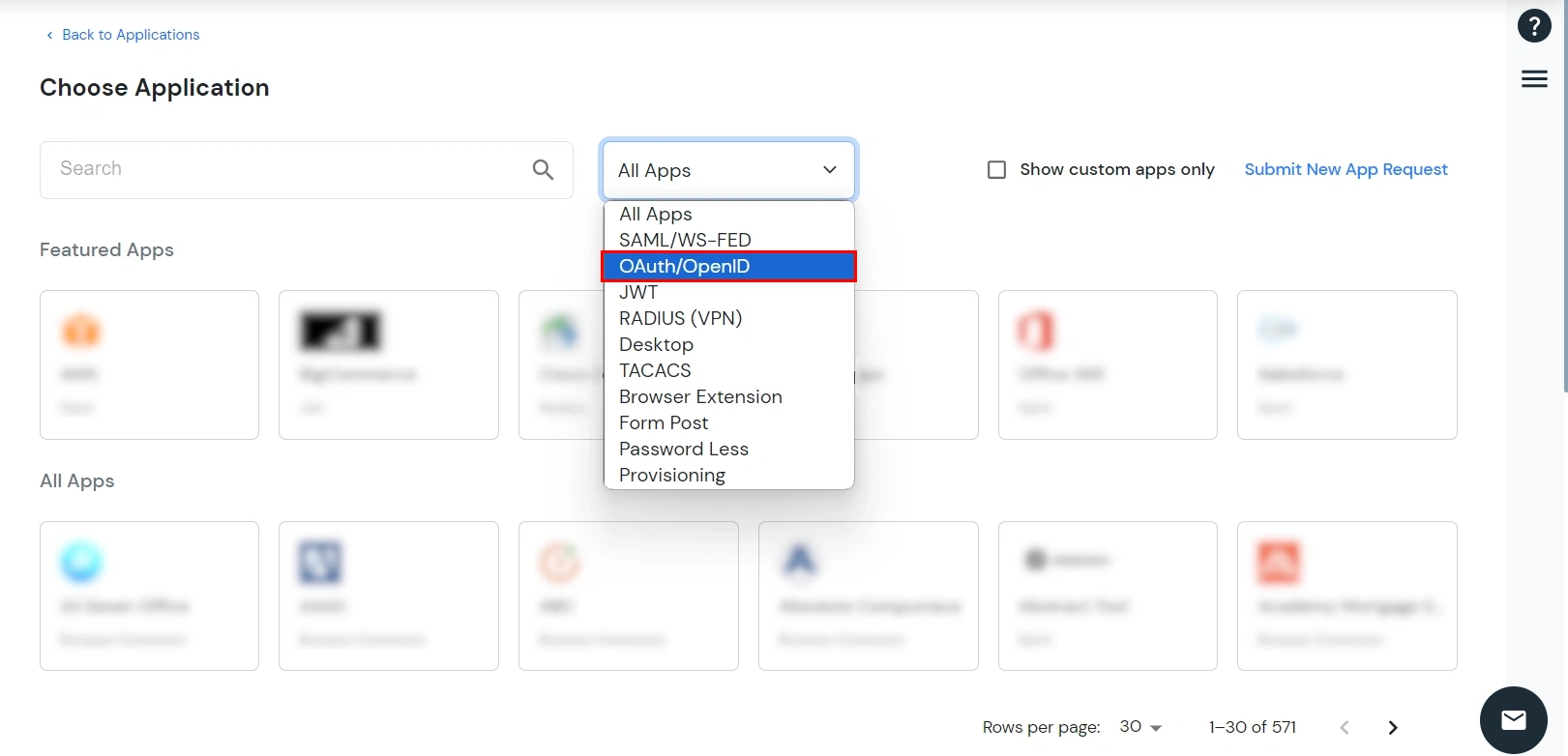
- Search for your application from the list, if your application is not found. Search for oauth and you can set up your app via OAuth2/OpenID Connect.
-
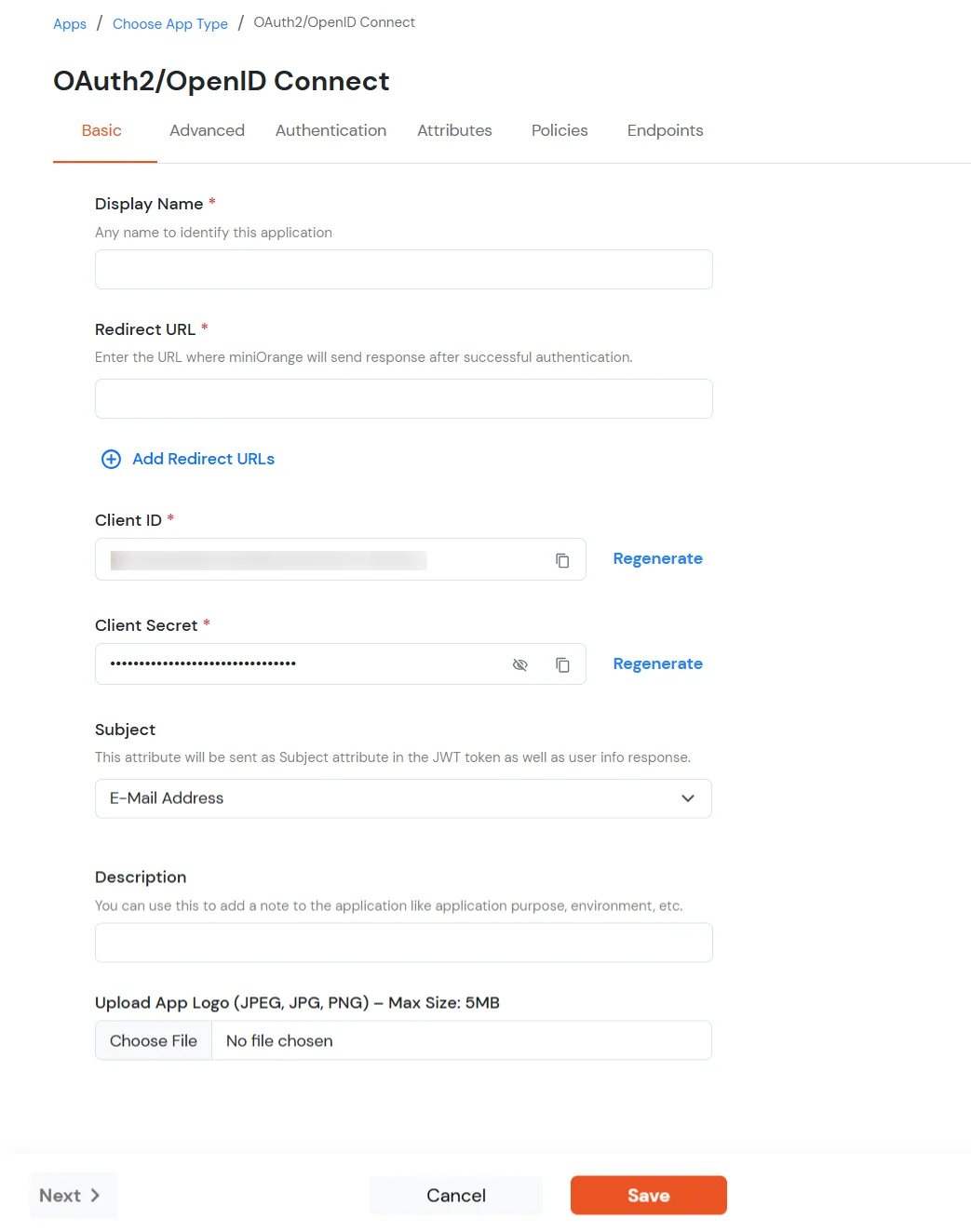
In the Basic tab, enter the following details:
| Display Name |
Enter the Display Name (i.e., the name for this application). |
| Redirect URL |
Enter the Redirect URL. Make sure it follows this format: https://<mycompany.domain-name.com>
|
| Client ID |
Auto-generated. Click the copy icon to use it in your application. |
| Client Secret |
Client Secret is hidden by default. Click the eye icon to reveal it and use the clipboard icon to copy it.
|
| Subject (Optional) |
Select an attribute from the dropdown list. |
| Description (Optional) |
Add a description if required.
|
| Upload App Logo (Optional) |
Upload an app logo (Optional). The app will be shown in the end-user dashboard with the
logo that you configure here.
|
- Click on Save.
- You will be redirected to the Policies section.
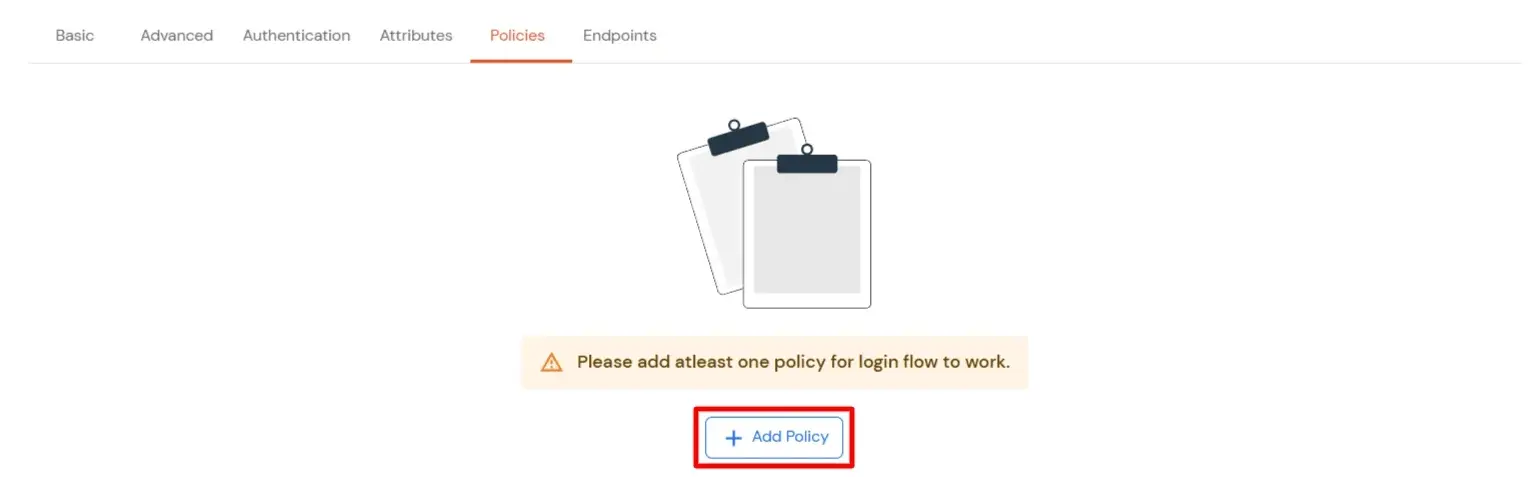
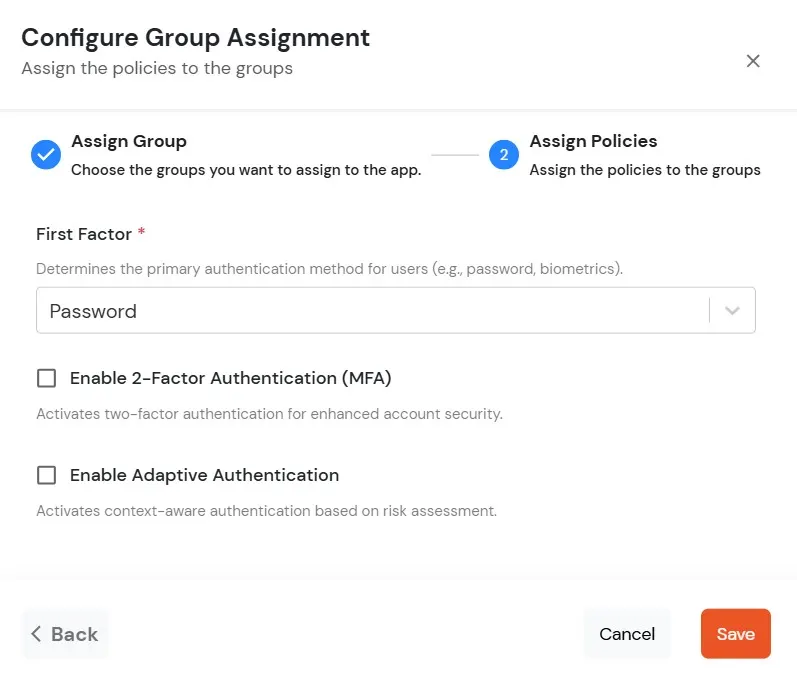
- Click on the Assign group button. A new Configure Group Assignment Modal tab will open.
- Assign Group: Select the groups you want to link with the application. You can select up to 20 groups at a time.
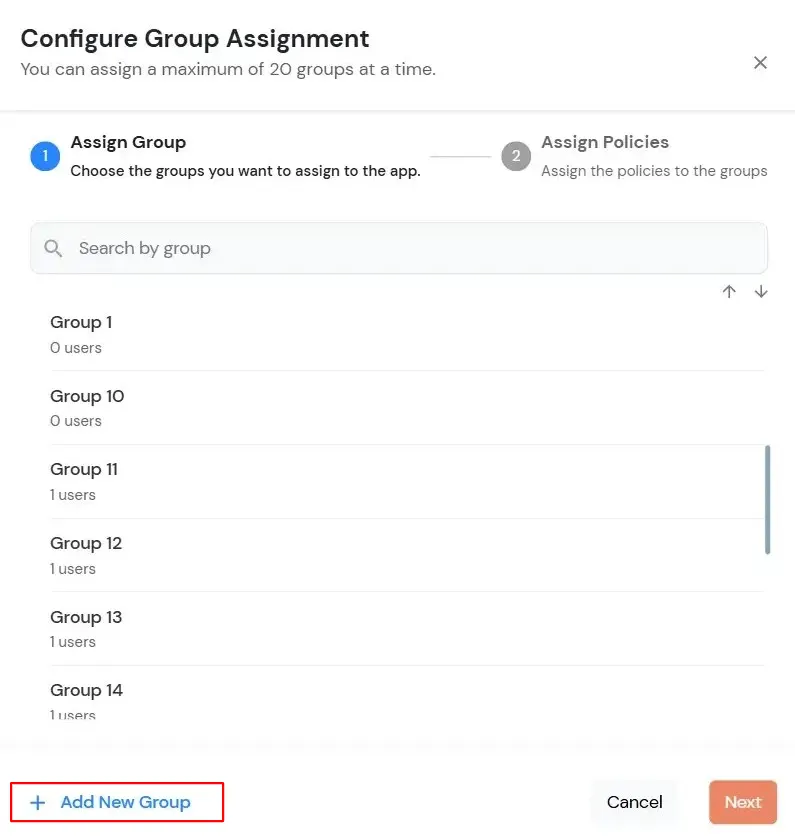
- If you need to create new group. Click on Add New Group button.
- Enter the Group name and click on Create Group.
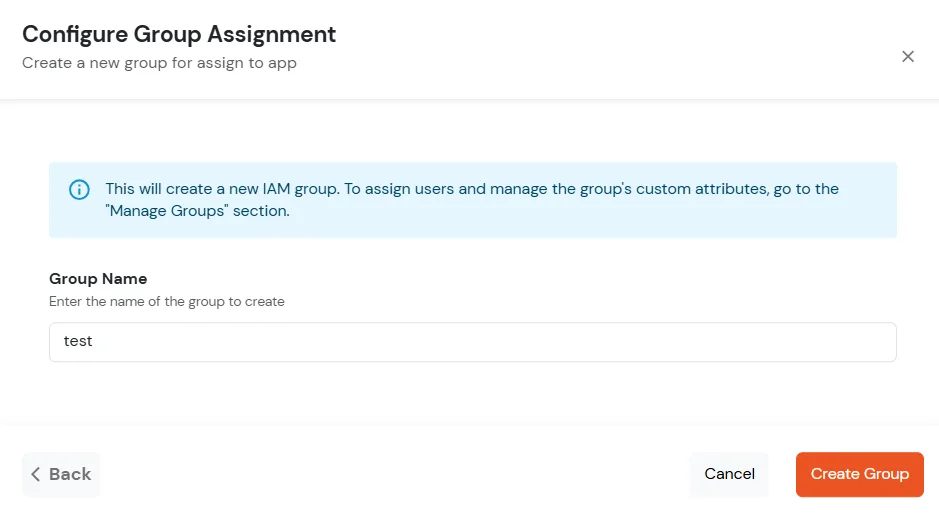
- Click on Next.
- Assign Policies: Add the required policies to the selected groups. Enter the following details:
- First Factor: Select the login method from the dropdown.
- If you select Password as the login method, you can enable 2-Factor Authentication (MFA) and Adaptive Authentication, if needed.
- If you select Password-less as login method, you can enable 2-Factor Authentication (MFA) if needed.
- Click on Save. Policies will be created for all the selected groups.
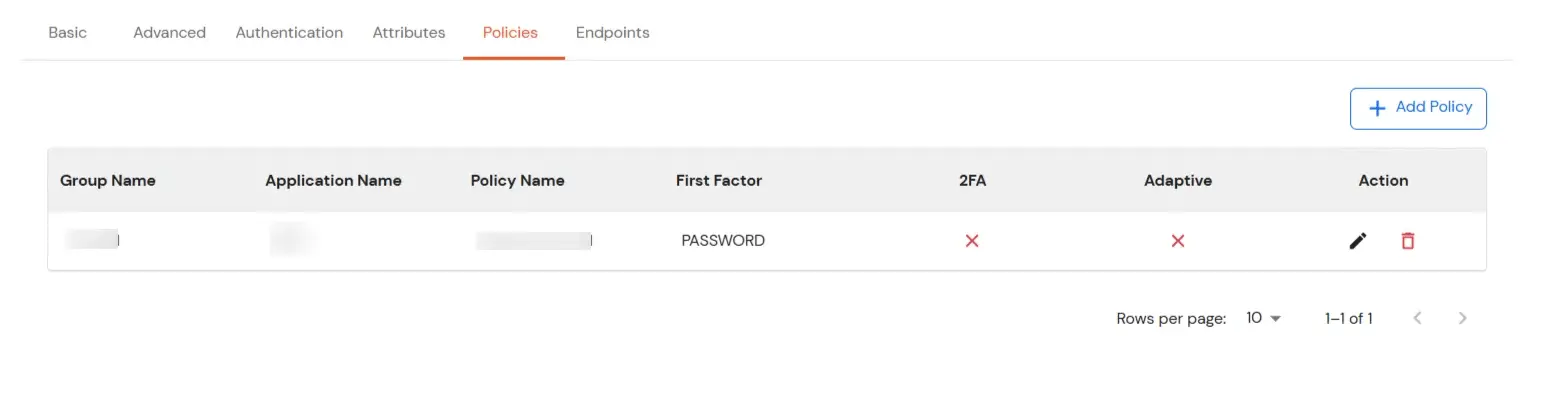
- You will see the policy listed once it’s successfully added.
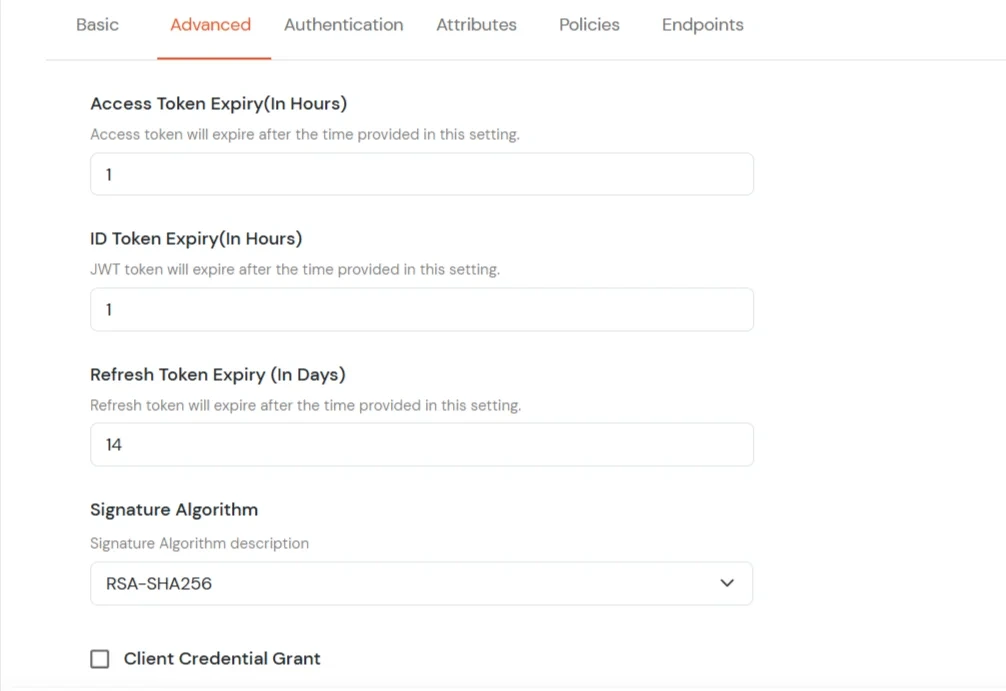
- You can go to the Advanced tab to change other settings, such as the expiry time for Access, JWT, and Refresh tokens.
- Access Token Expiry: For how long the provided access token should be valid from creation. [In Hours] A new access token has to be generated after the expiry.
- JWT Token Expiry: For how long the generated JWT token should be valid. [ In Hours ]
- Refresh Token Expiry:For how long the generated refresh token should be valid. [In Days] You will have to generate a new refresh token after the mentioned no. of days.
-
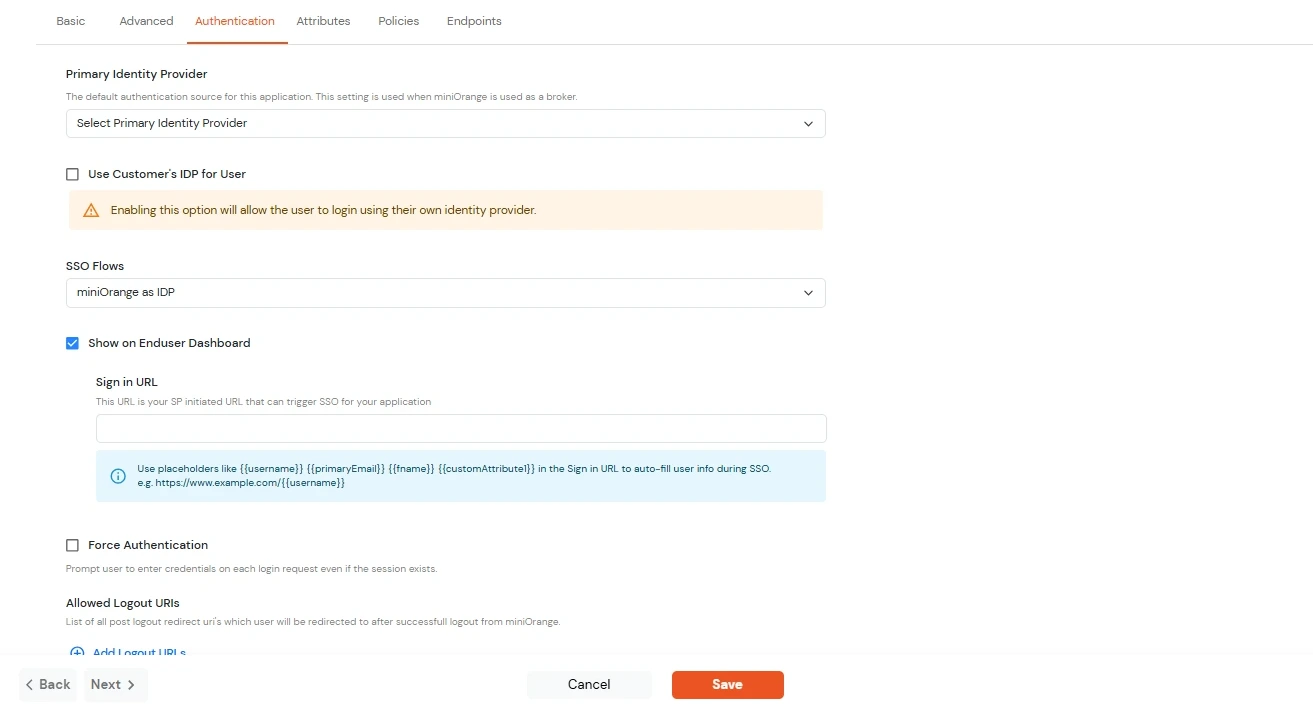
Switch to the Login options tab.
| Primary Identity Provider |
Select the default ID source from the dropdown for the application. If not selected, users will see the default
login screen and can choose their own IDP. [Choose miniOrange in this case.]
|
| SSO FLows |
Select the desired SSO flow from the dropdown, such as miniOrange as IDP, miniOrange as Broker, or miniOrange as Broker with Discovery Flow. |
| Show on Enduser Dashboard |
Enable this option if you want to show this app in the end-user dashboard. |
| Force Authentication |
If you enable this option, users will have to log in every time, even if their session already exists. |
| Allowed Logout URIs |
Click the Allowed Logout URIs link to add a list of post-logout redirect URIs. Users will be redirected to one of these URIs after a successful logout from miniOrange. |
| Single Logout Enabled |
Enable this option to send logout requests to other applications when logging out from this app. |
| Sign in URL |
You can include user attributes in the sign-in URL using placeholders like {{username}}, {{primaryEmail}}, {{customAttribute1}}, etc.
These placeholders will be dynamically replaced with the actual user values during the IdP-initiated SSO flow.
You can generate url using following attributes:
username, primaryEmail, alternateEmail, fname, lname, primaryPhone and customAttribute1.
The url could be like this login.com/{{username}}/?primaryEmail={{primaryEmail}}
- Query Parameter Format:
https://<sso-url>>?username={{username}}
https://<sso-url>>?username={{username}}&email={{primaryEmail}}
- Path Parameter Format:
https://<sso-url>>/{{customAttribute1}}/{{customAttribute2}}/?username={{username}}
|
- Switch to the Attributes tab.
- Enable Multi-Valued Attributes Option:
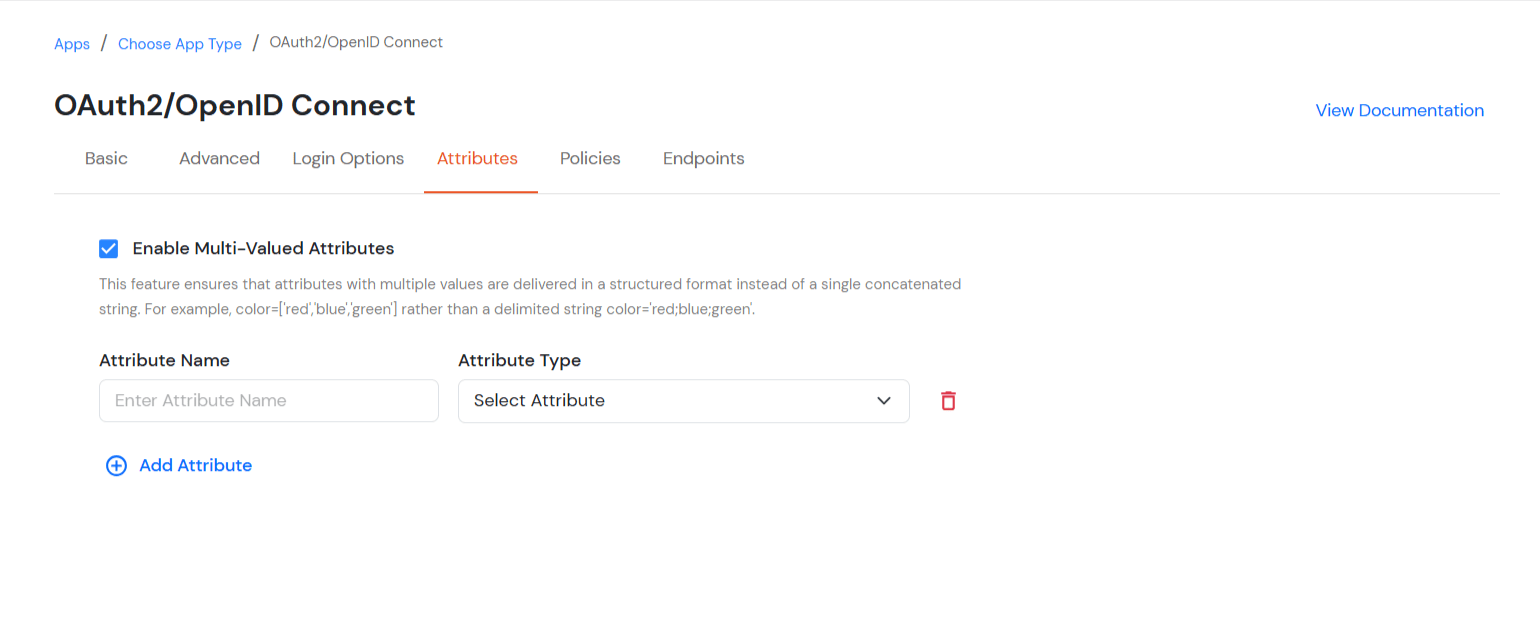
- When this option is enabled, both commas (,) and semicolons (;) are treated as delimiters. Any attribute containing these characters will be automatically split and converted into a multi-valued attribute based on their positioning.
- This feature ensures that attributes with multiple values are delivered in a structured format instead of as a single concatenated string.
- For example: when this option is enabled, Attributes will be will appear as a list like roles = ['admin', 'editor', 'viewer'] instead of a single string like roles = "admin;editor;viewer".
- When this option is disabled, attributes stored as a single concatenated string with commas (,) and semicolons (;) are treated in the way they are stored instead of a structured list.
- In this case, commas (,) and semicolons (;) are not treated as separators, so the values remain combined in one string.
- Getting Required App Details / Updating App Information::
- Go to the Apps section from the side menu. From the list of configured apps, locate the app you created. Click the three-dot icon next to the app and select the Edit option.
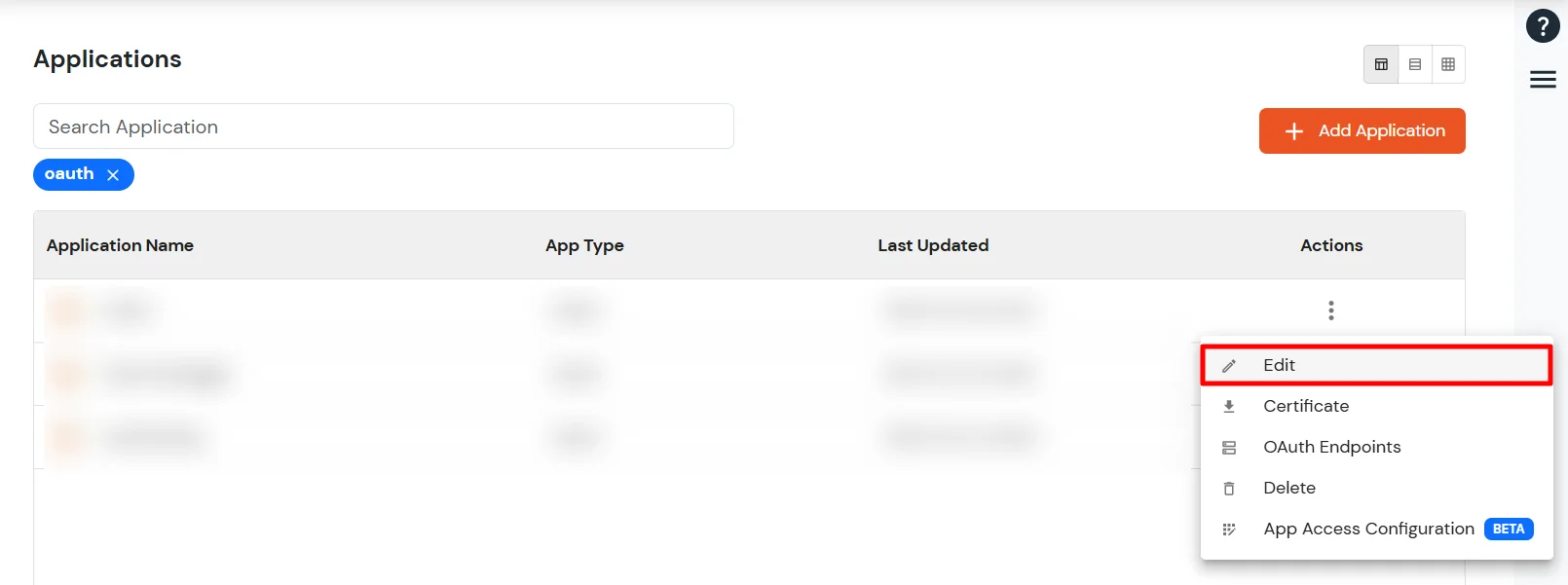
- You can edit any of the above-mentioned details in case you want to change them.
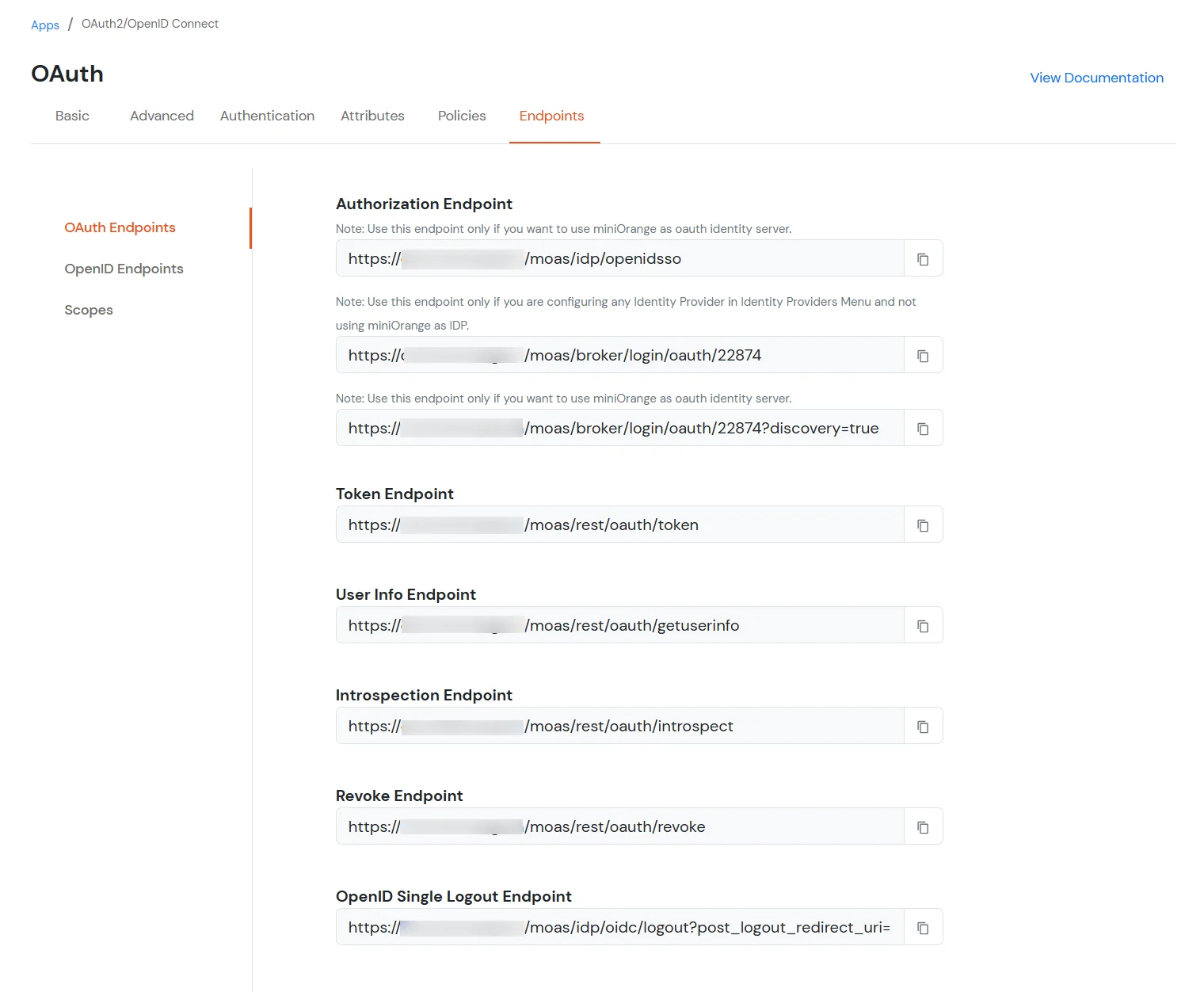
- OAuth Endpoints:
- Authorization Endpoint [ https://<your-company-name>.xecurify.com/moas/idp/openidsso ]:
- This endpoint is used to authenticate the end user with their miniOrange credentials. This authenticates the users and returns a response back to the redirect_url based on the parameters passed in the request. [Mainly the authorization code]
- This endpoint takes the following parameters :
- Client_id : client_id of the application as configured in the previous steps
- Redirect_uri : The callback URL where you want to return the response
- scope : scope of authorization or level of access, you can send a single or multiple scopes separated by ‘+’. e.g “email+openid”. We support the following scopes :
- Email : returns the email address of the user in the response
- Profile : returns user profile information in the response
- OpenID : returns the id_token containing user profile details.
- This returns the authorization code and the state parameters in the response.
- Token Endpoint [ https://<your-company-name>.xecurify.com/moas/rest/oauth/token ] :
- This endpoint returns the following :
- Id_token Contains user attributes and signatures which you have to validate with provided public certificate.
| iss |
https URI that indicates the issuer |
| sub |
identifier of the user at the issuer |
| aud |
client_id of the requesting client |
| nonce |
the nonce parameter value received from the client |
| exp |
expiration time of this token |
| iat |
time when this token was issued |
| auth_time |
time the authentication happened |
| at_hash |
the first half of a hash of the access token |
- Access_token : Valid for 1 hour and can be used to access user info or other endpoints until it is expired.
- This endpoint takes the following parameters in the request:
- Client_id : client_id of the application as configured in the previous steps.
- Client_secret : client_secret of the application as configured in the previous step.
- Redirect_url : The callback url where the response should be posted.
- Code : The authorization code received from the authorization endpoint.
- Grant_type : The OAuth grant you want to use for the request.
- User Info Endpoint [ https://<your-domain>.xecurify.com/moas/api/oauth/getuserinfo ] : [Required in case of OAuth Only]
- This API can be used to fetch user profile information with an access token that was assigned to the user. A GET request is sent to the user info endpoint.
- You need to send the access token in the authorization header to receive the user details.
- OpenID Single Logout Endpoint : [ https://<your-domain>.xecurify.com/moas/idp/oidc/logout?post_logout_redirect_uri ] :
- This endpoint removes the active user session from the miniOrange IDP and redirects the user to the URL mentioned in the post_logout_url parameter.
- Click here for a detailed setup guide if you want to authenticate your users via any external Identity Provider like Active Directory, Okta, OneLogin, etc. or any other custom IDPs.















