Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×Configuring Adaptive Authentication (MFA) for users is crucial due to the elevated privileges they have. Specific users have access to certain levels of sensitive systems and data, making them targets for malicious actors.
Admins can dynamically adjust the authentication requirements based on risk factors like location, device, and behavior by implementing adaptive MFA. This ensures that even if an attacker gains access to admin credentials, they still face significant hurdles, reducing the likelihood of a successful breach.
Moreover, while balancing security and user experience is vital for regular users, the security of admin accounts should take precedence. Adaptive MFA allows for stricter authentication policies for administrators without impacting the daily workflow of typical users.
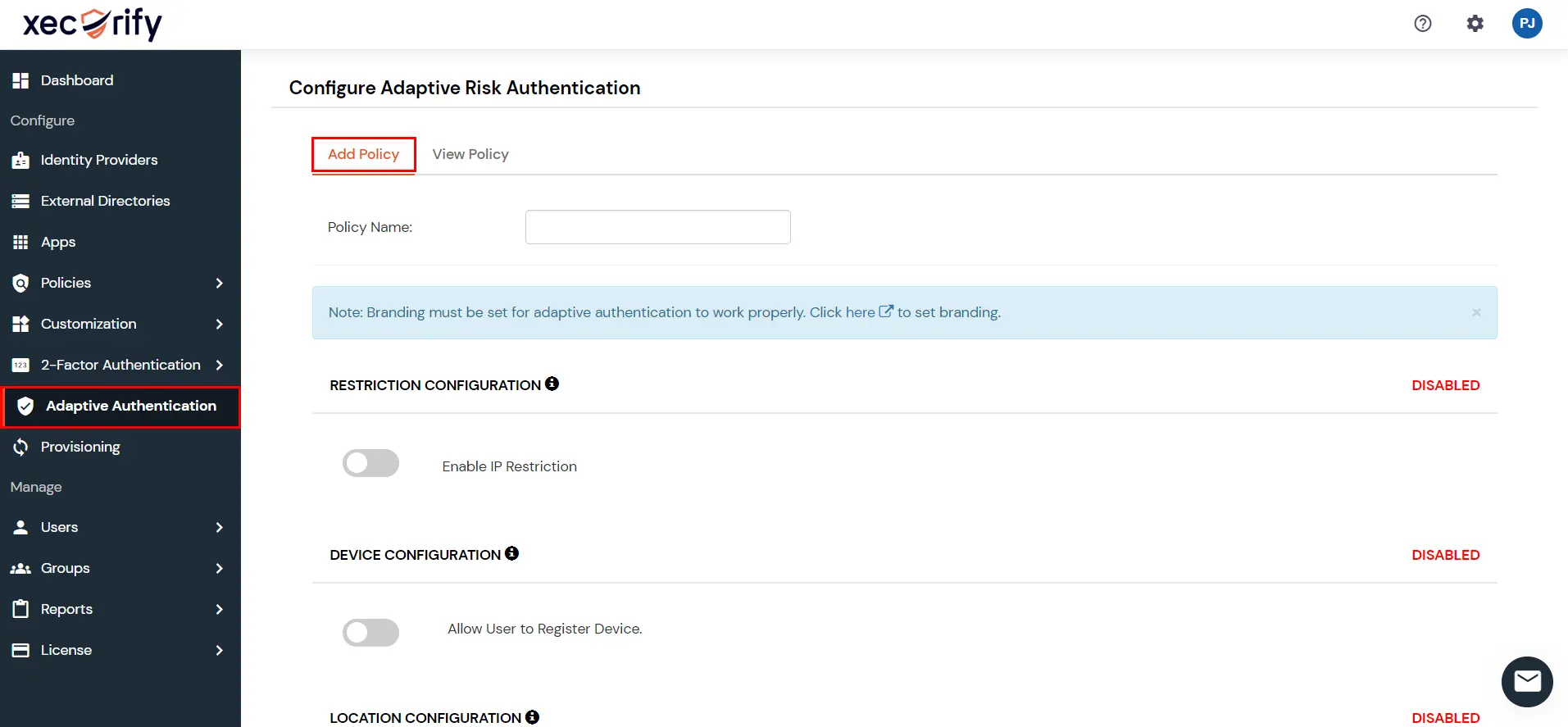
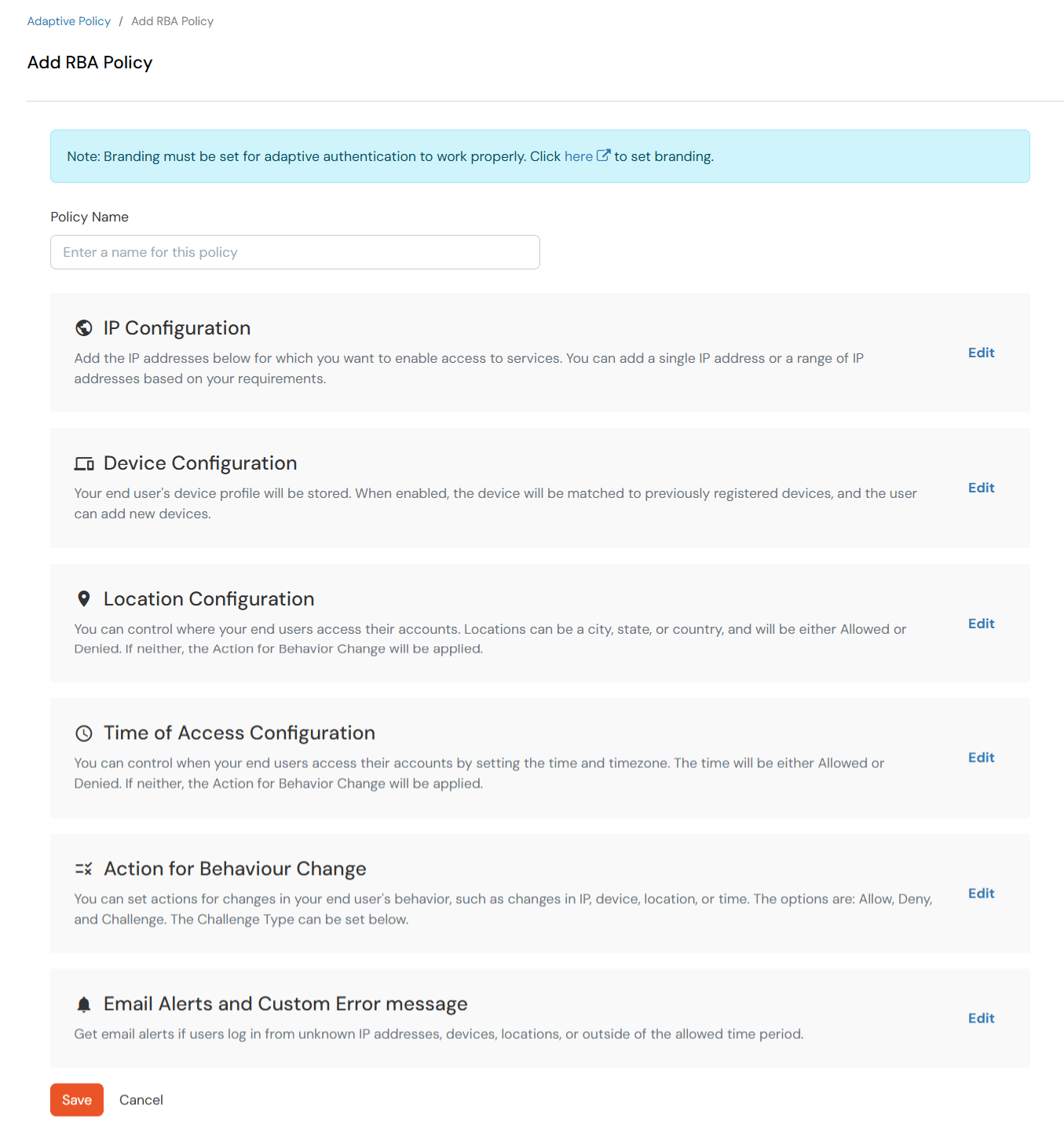
Login to the Self-Service Console and navigate to the Adaptive Authentication section from the side menu.
Click on the Add Policy button on the upper right.
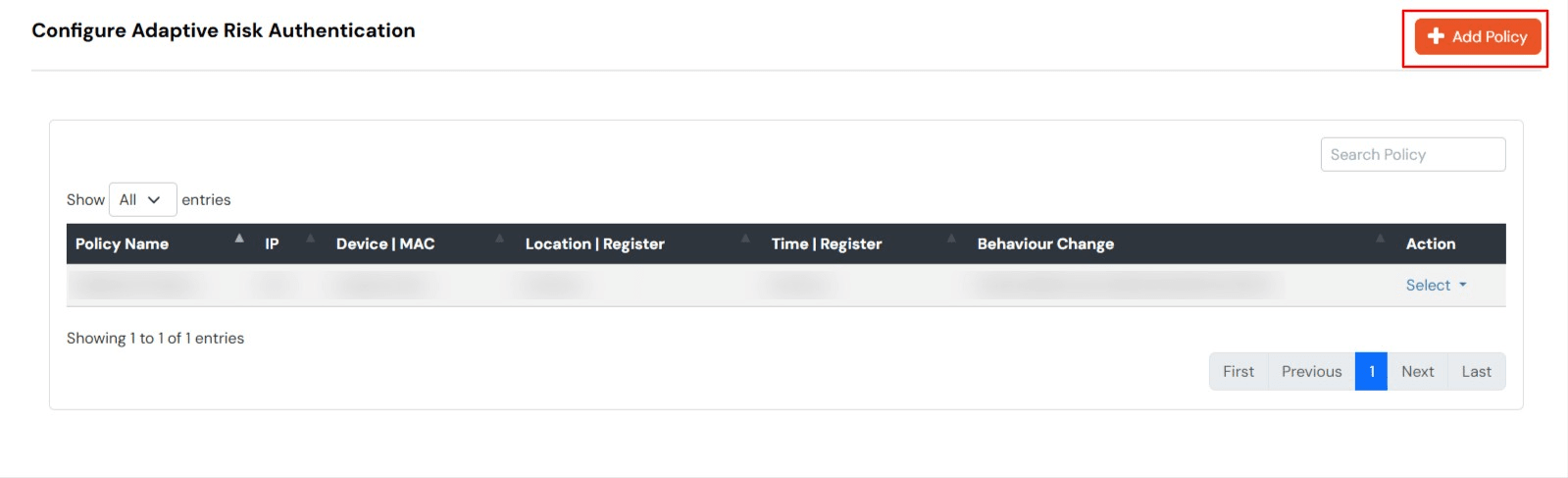
In IP restriction, admin configures a list of IP addresses to allow or deny access on and when a user tries to log into any of the applications configured with adaptive authentication, his IP address is checked against the configured IP list and based on that the action is decided as per the configuration (.i.e. Allow, Deny or Challenge).
How to Configure IP Address:
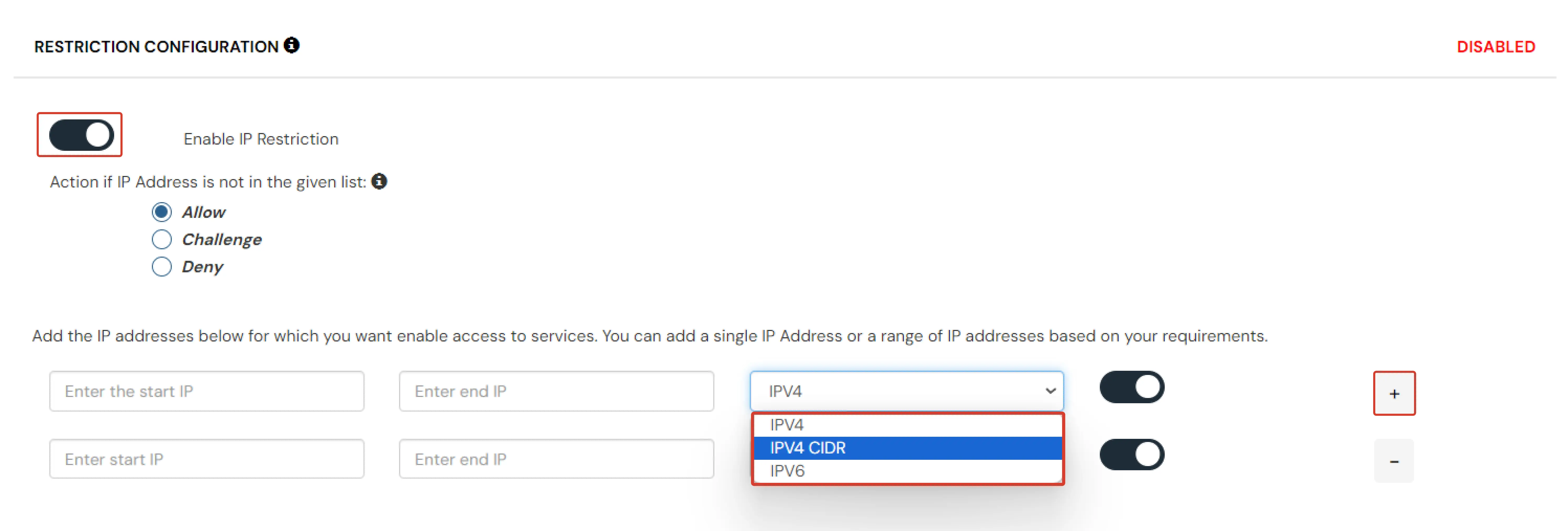
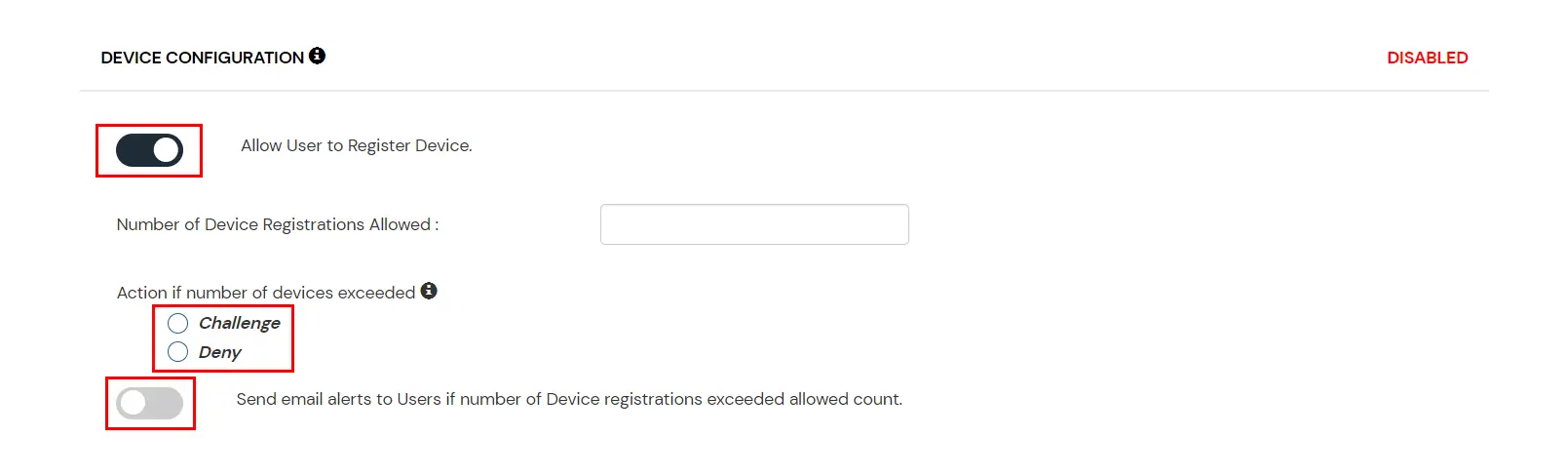
In device restriction, admin allows end-users to add a fixed number of devices as Trusted devices for their account. Once a device is registered for a user, then that user will be allowed to login without any restriction.
How to configure Device-based Configuration:

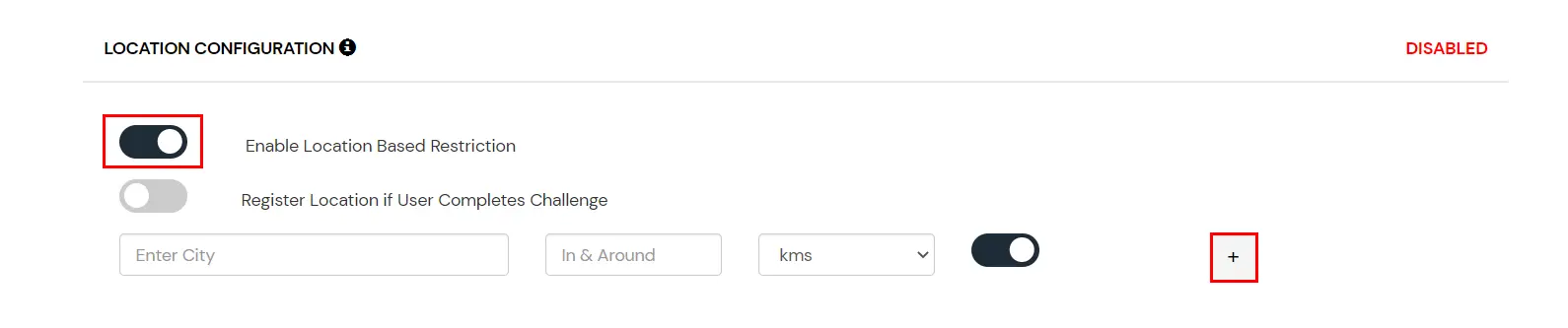
In location restrictions, admin configures a list of locations where they want to allow end-users to either login or deny based on the condition set by the admin. When a user tries to login with adaptive authentication enabled, their Location Attributes, such as (Latitude, Longitude, and Country Code) are verified against the Location list configured by the admin. Based on this user will be either allowed, challenged or denied.
How to configure Location-based Configuration:

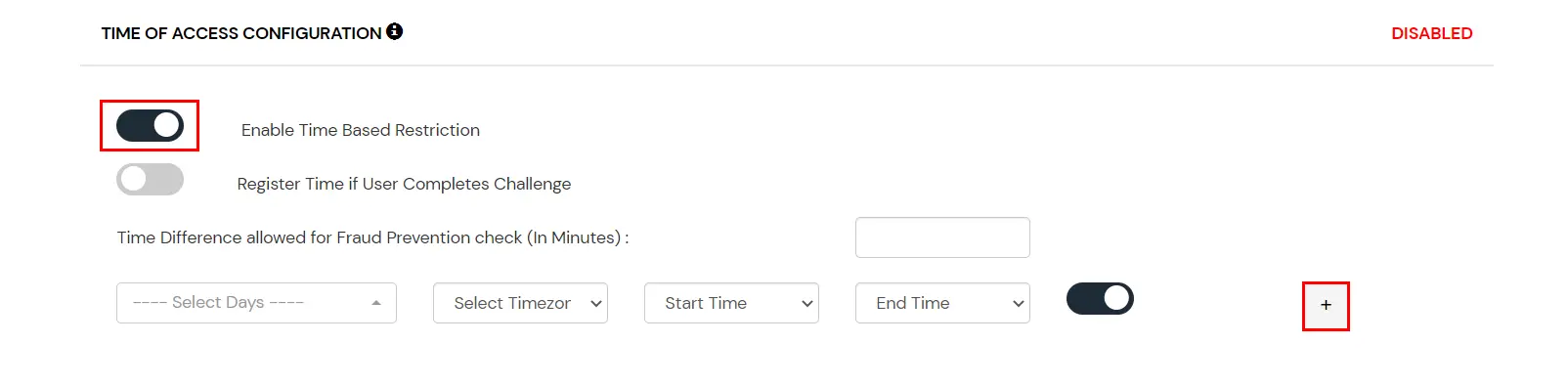
In time restriction, admin configures a time zone with Start and End Times for that timezone, and users are either allowed, denied, or challenged based on the condition in the policy. When an end-user tries to login with the adaptive authentication enabled, their time zone-related attributes such as Time-Zone and Current System Time, are verified against the list configured by the admin, and based on the configuration, the user is either allowed, denied, or challenged.
How to configure Time-based Configuration:

You can configure one of the three possible actions for your Adaptive Authentication Policy as explained below :

| Attribute | Description |
|---|---|
| Allow | Allow users to authenticate and use services if Adaptive authentication condition is true. |
| Deny | Deny user authentications and access to services if Adaptive authentication condition is true. |
| Challenge | Challenge users with one of the three methods mentioned below for verifying user authenticity. |
| Factors | Description |
|---|---|
| User second Factor | The User needs to authenticate using the second factor he has opted or assigned for such as
|
| KBA | The System will ask the user for 2 of 3 questions he has configured in his Self-Service Console. Only after the right answer to both questions is the user allowed to proceed further. |
| OTP over Alternate Email | User will receive an OTP on the alternate email they have configured through the Self Service Console. Once the user provides the correct OTP, they are allowed to proceed further. |
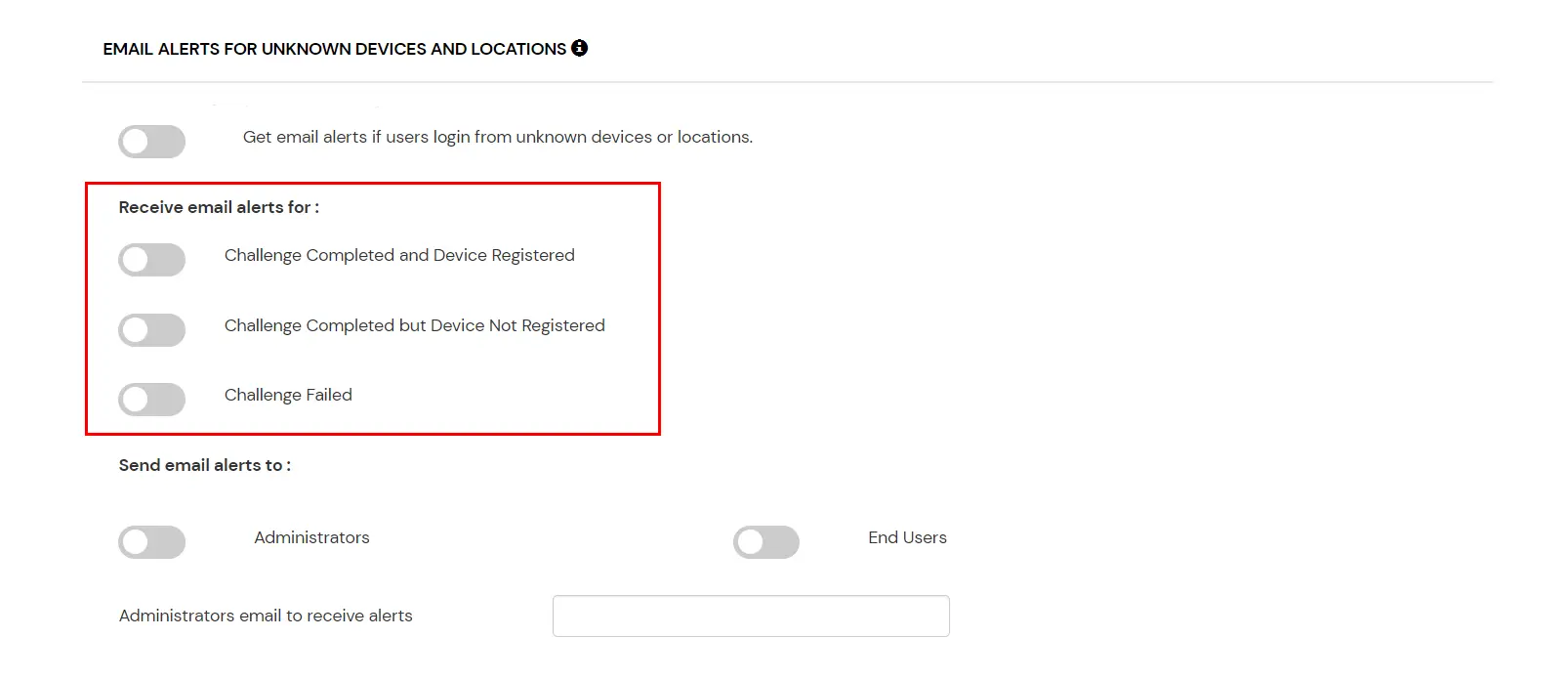
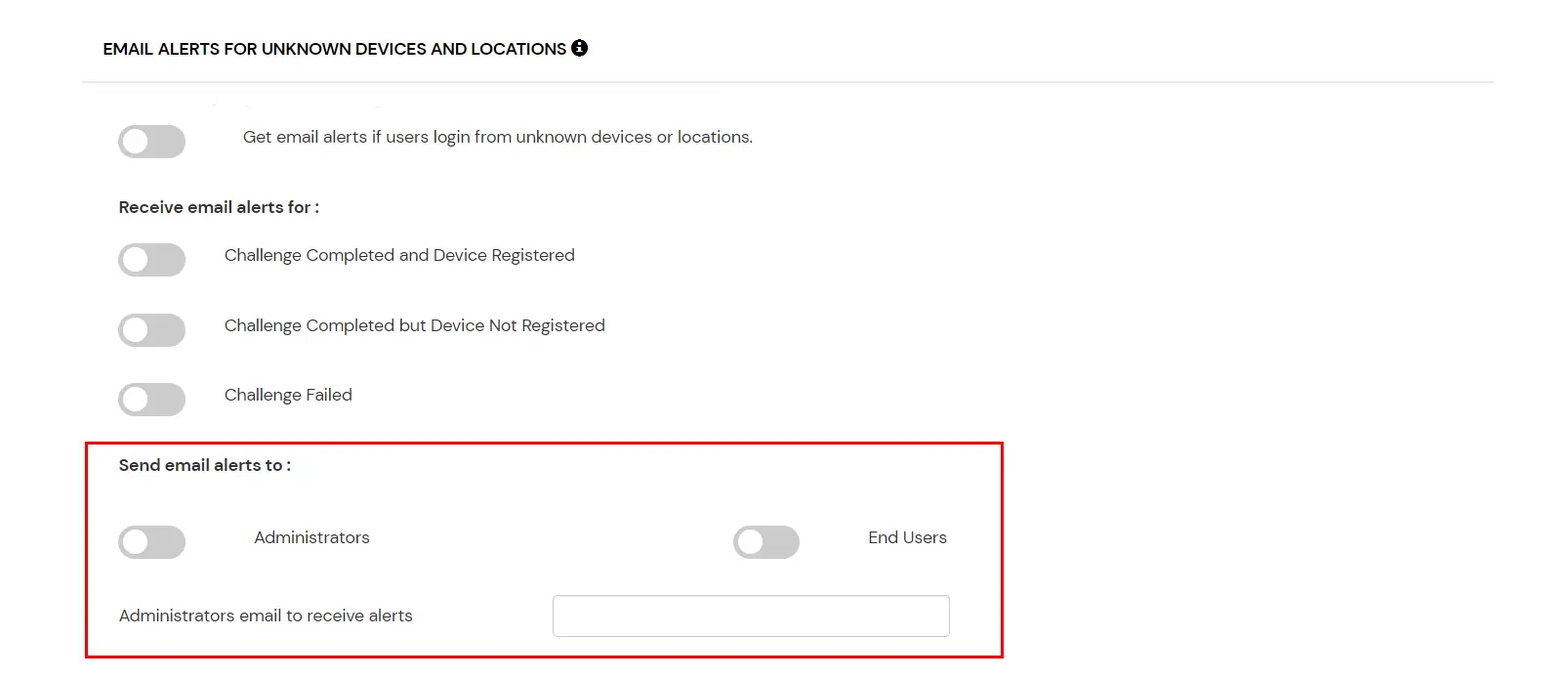
This section handles the notifications and alerts related to Adaptive Authentication.It provides the following options :
| Option | Description |
|---|---|
| Challenge Completed and Device Registered | Enabling this option allows you to send an email alert when an end-user completes a challenge and registers a device. |
| Challenge Completed but Device Not Registered | Enabling this option allows you to send an email alert when an end-user completes a challenge but do not register the device. |
| Challenge Failed | Enabling this option allows you to send an email alert when an end-user fails to complete the challenge. |
| Users login from unknown IP addresses, devices or locations | Enabling this option allows you to login from unknown ip addresses or devices and even locations. |
| Number of Device registrations exceeded allowed count | This option will allow you to register more devices than the devices you have numbered. |