Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×Remote Authentication Dial-In User Service (RADIUS) is a software and client-server protocol used to centrally authenticate and authorize users attempting to access a network, acting as a central point to verify user credentials before granting network access. It performs functions like authentication, authorization, and accounting (AAA) for users trying to connect to a network, like through Wi-Fi or VPNs.
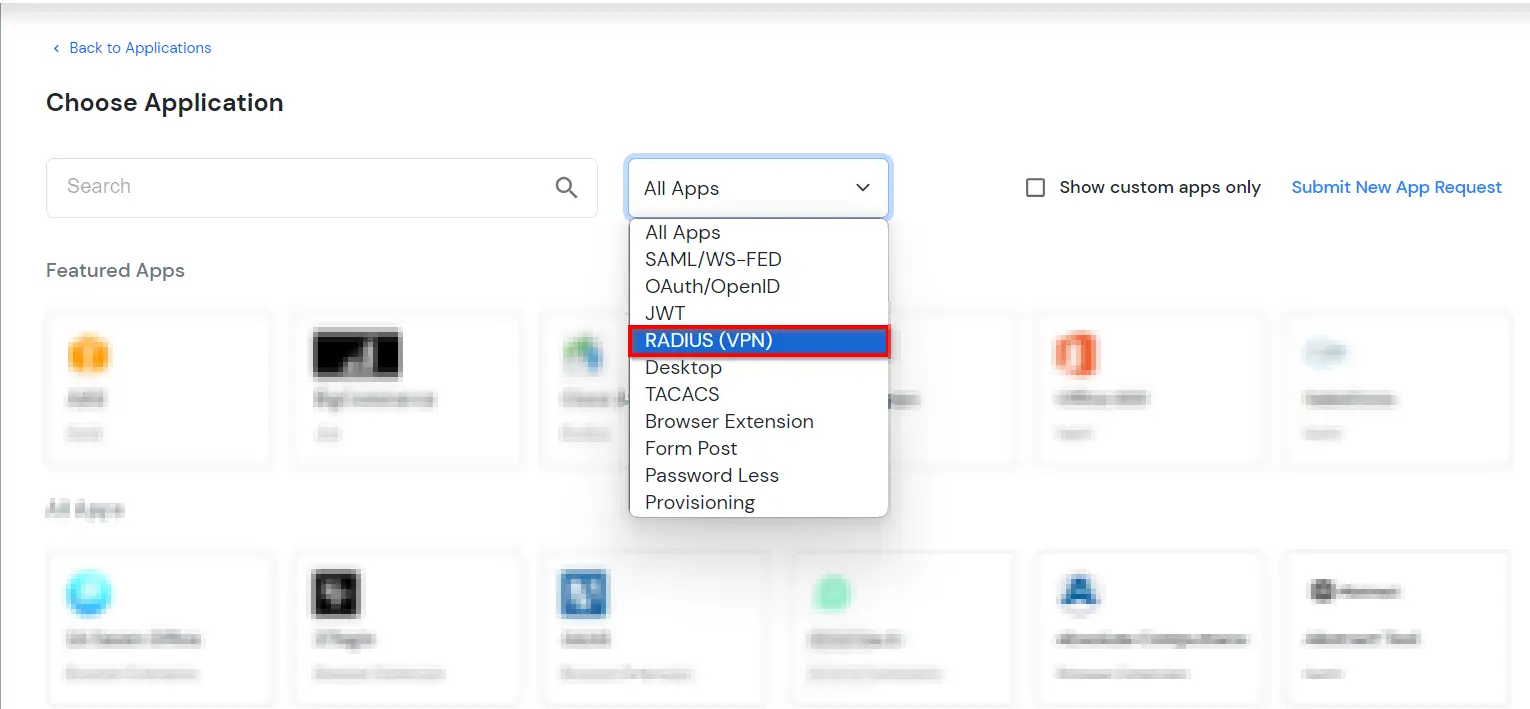
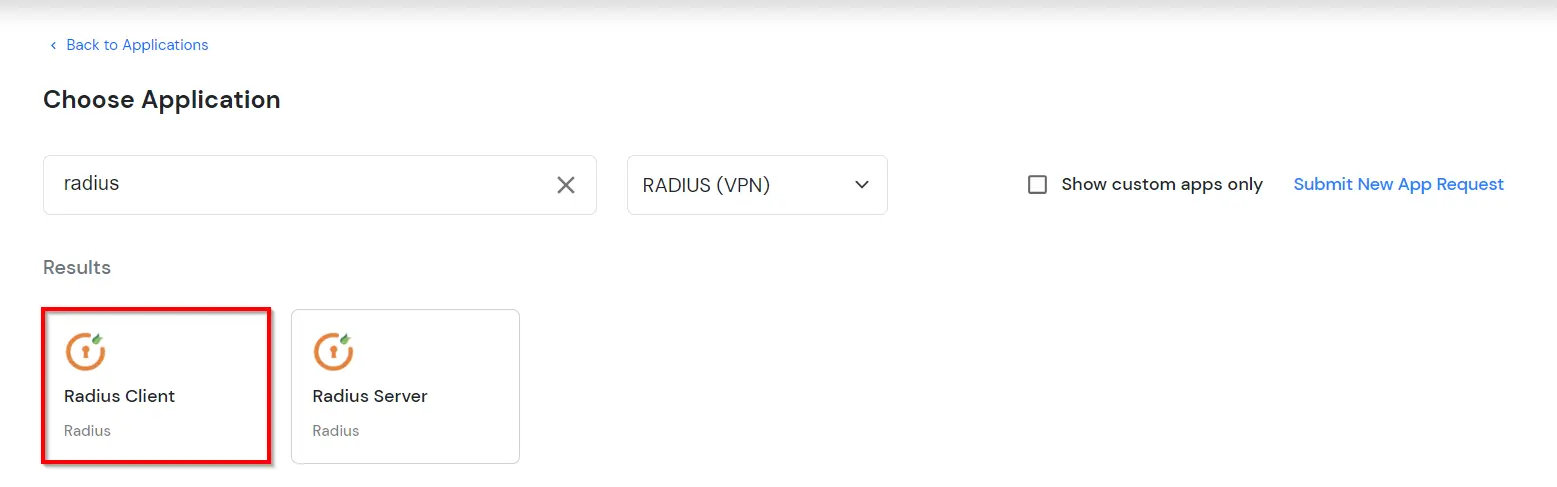
miniOrange enables several different protocols for your applications, such as SAML, WS-FED, OAuth, OIDC, JWT, RADIUS, and more. We provide MFA or adaptive authentication solutions for RADIUS apps like Fortinet VPN, SonicWall VPN, AWS Workspaces, and many more.
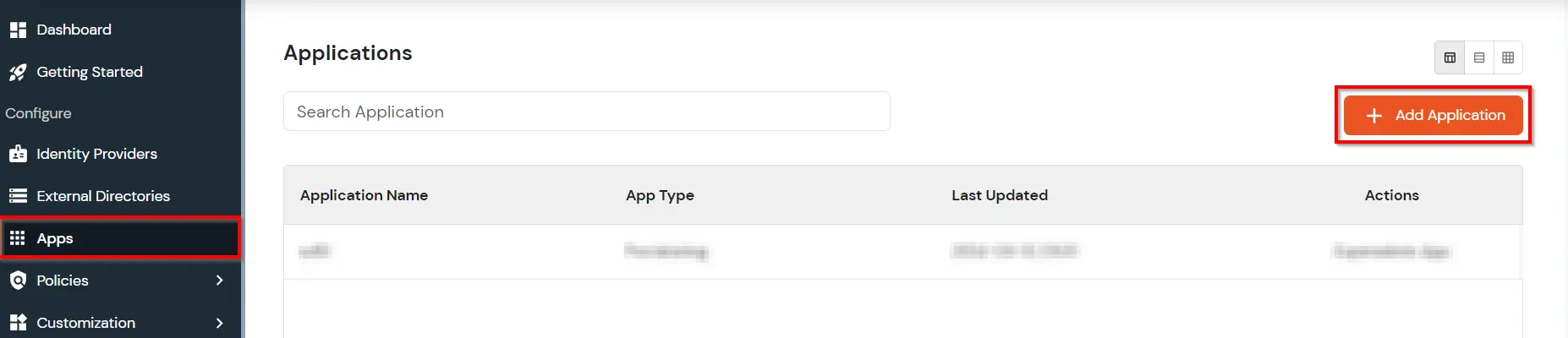
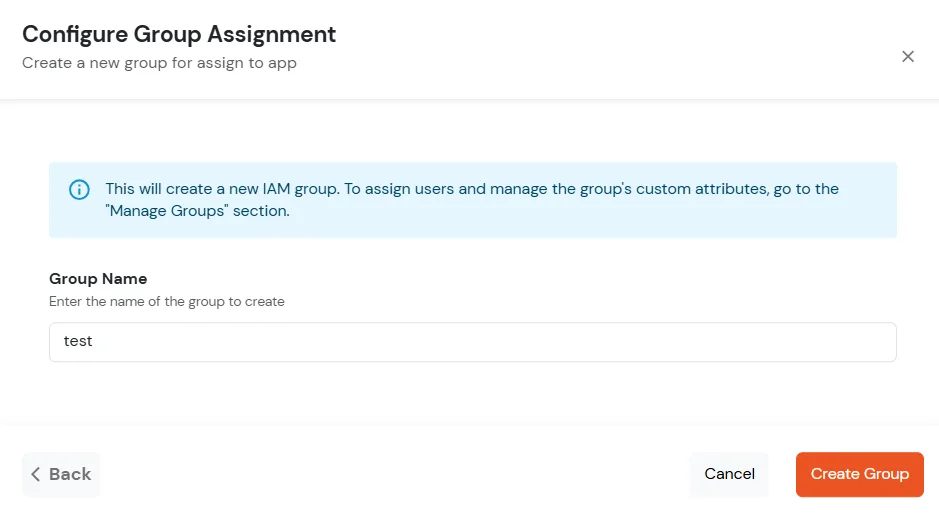
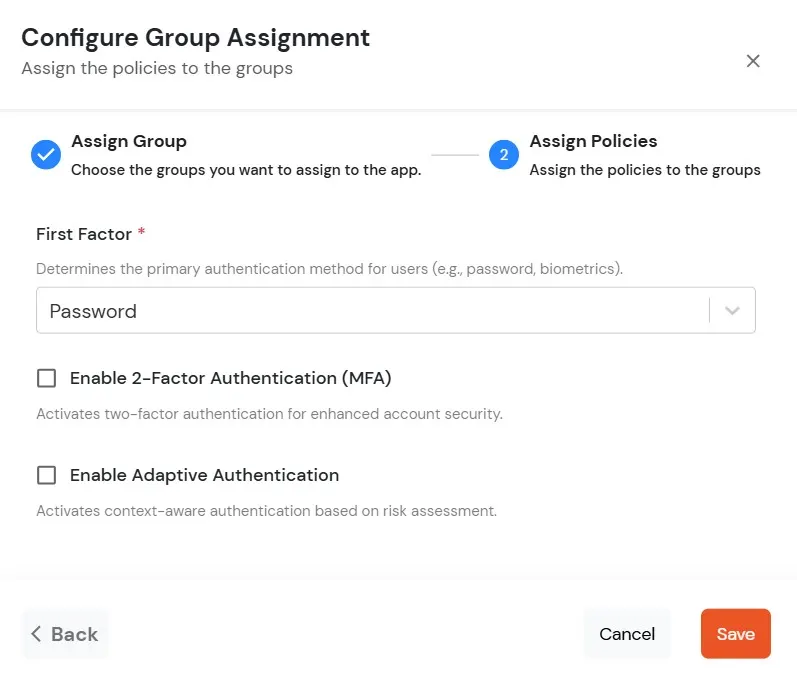
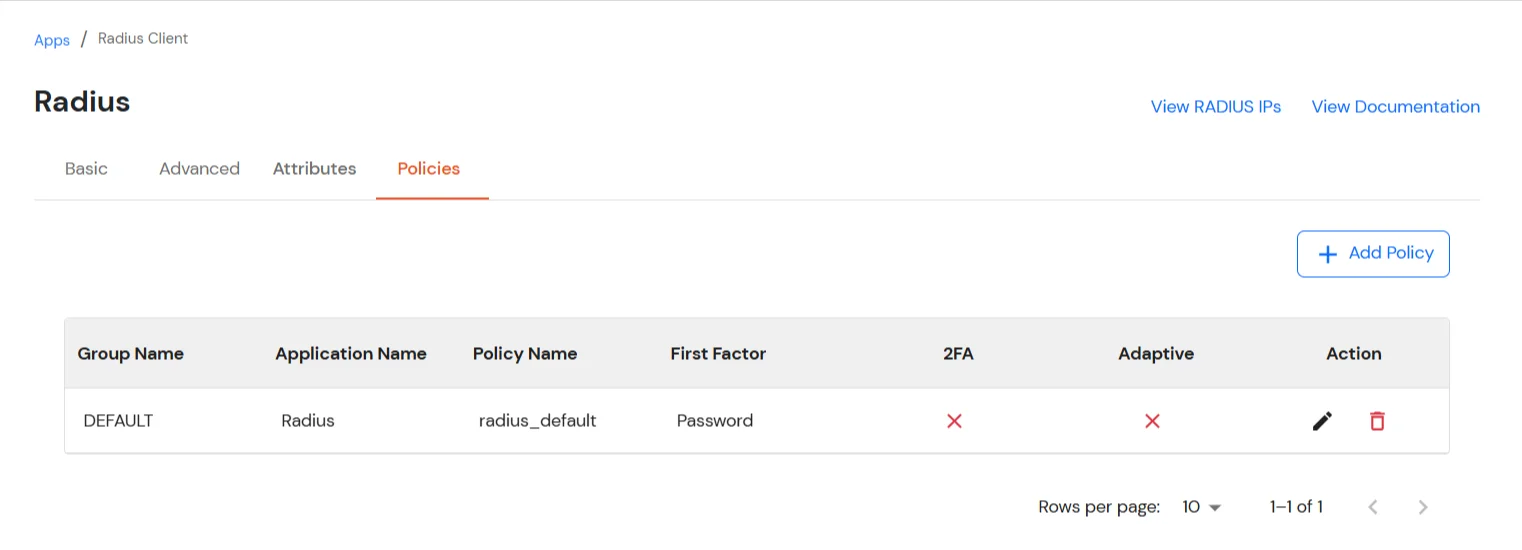
Let’s configure your application now.
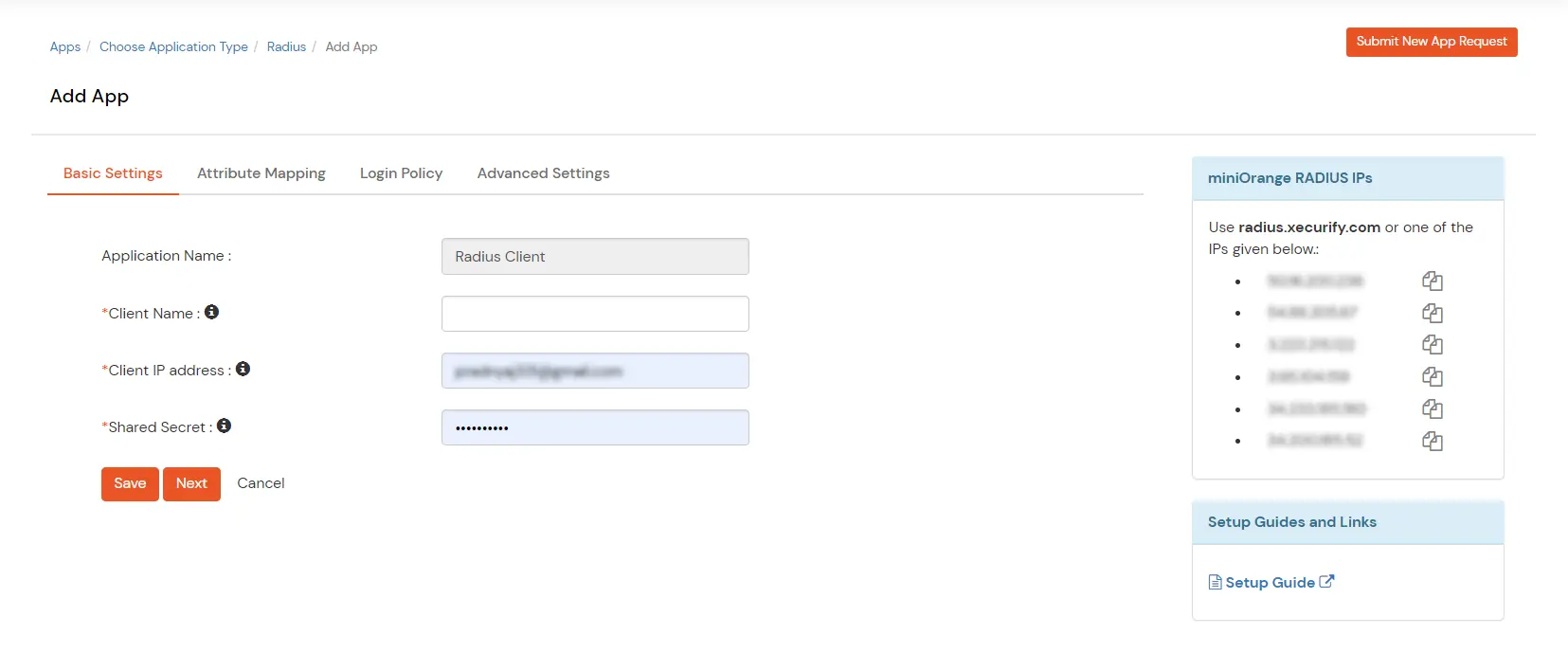
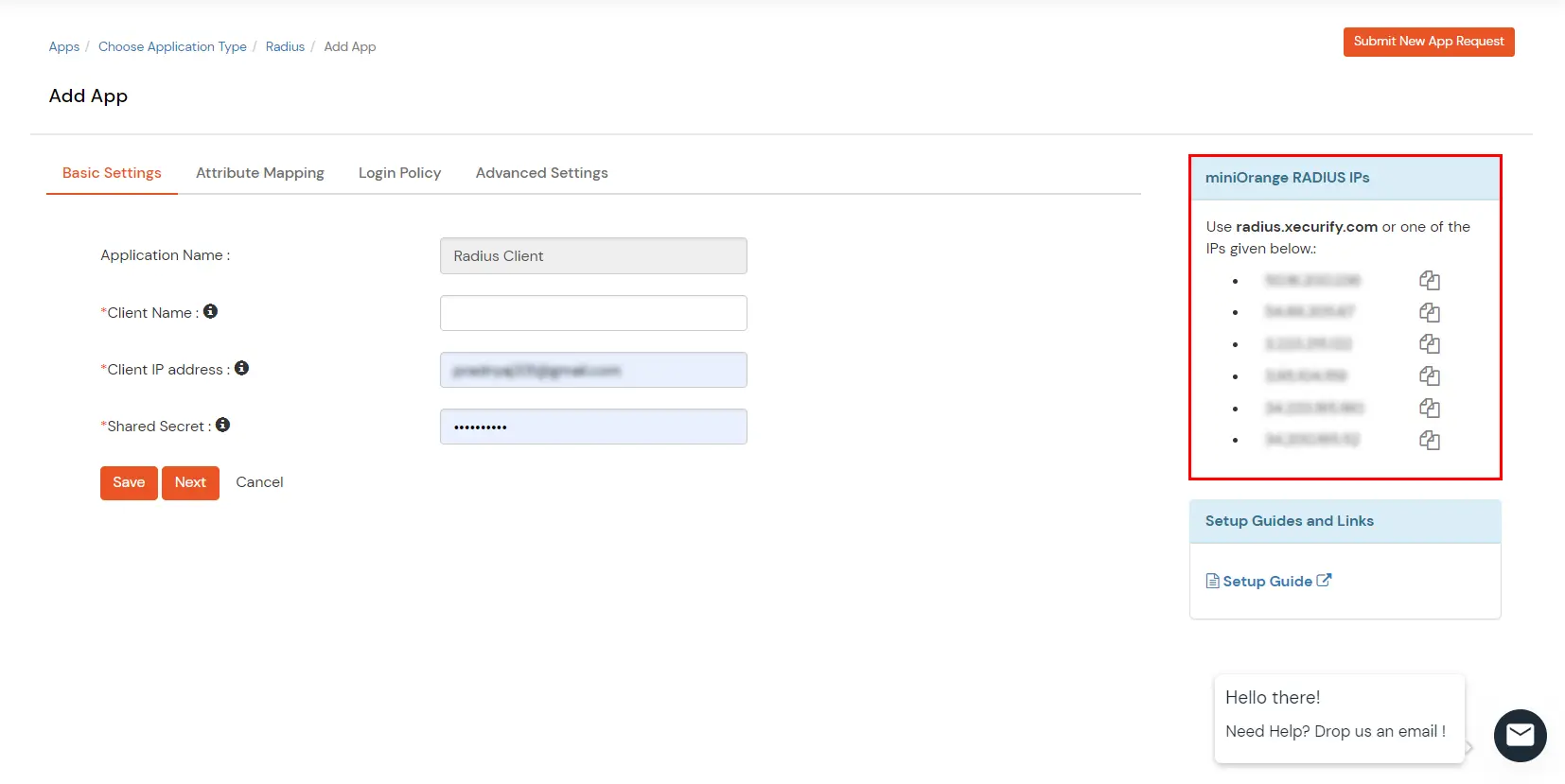
| Display Name | Any name for your reference. |
| Client IP | The IP address of the VPN server, which will send the Radius authentication request. |
| Shared Secret | Security key. For Eg. "shared-secret" (Keep this with you; you will need to configure the same on VPN Server) |
| Include Password & OTP in the same Request | Check this option for clients, which takes a password and the OTP in the same request. Otherwise, keep it unchecked. |

NOTE: Follow the below steps before testing the connectivity. Open Firewall Ports.