Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×miniOrange’s SIEM Integration module enables seamless forwarding of identity, authentication, admin action, and access pattern event data (login, logout, MFA, session, policy violations, etc.) from the miniOrange identity platform into your SIEM of choice (e.g. Wazuh, Splunk, Sumo Logic, or custom tools).
This allows security teams to correlate SSO / IAM events with broader infrastructure logs for unified threat detection, monitoring, and compliance.
Correlate authentication, admin, and access pattern events with network or endpoint logs to detect anomalies like brute-force attempts, privilege escalations, or insider threats.
Trace an incident end-to-end — from user authentication to admin configuration changes — for faster root-cause analysis.
Maintain a unified, tamper-proof audit trail of identity, admin, and access events to support audit and regulatory compliance.
Enable rule-based alerts in your SIEM for repeated login failures, high-risk admin actions, or unusual access behavior.
Gain insights into user access trends, authentication health, admin operations, and platform activity across your environment.

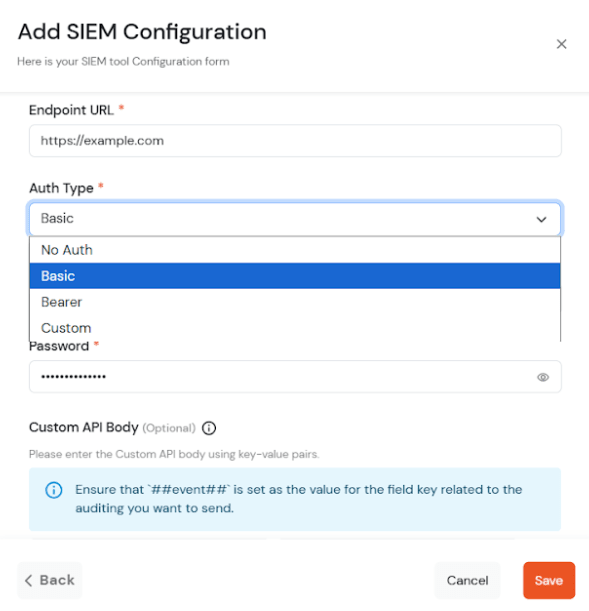
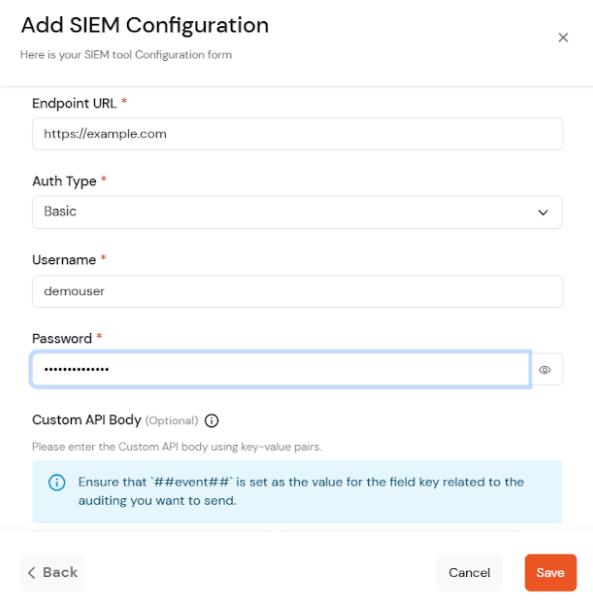
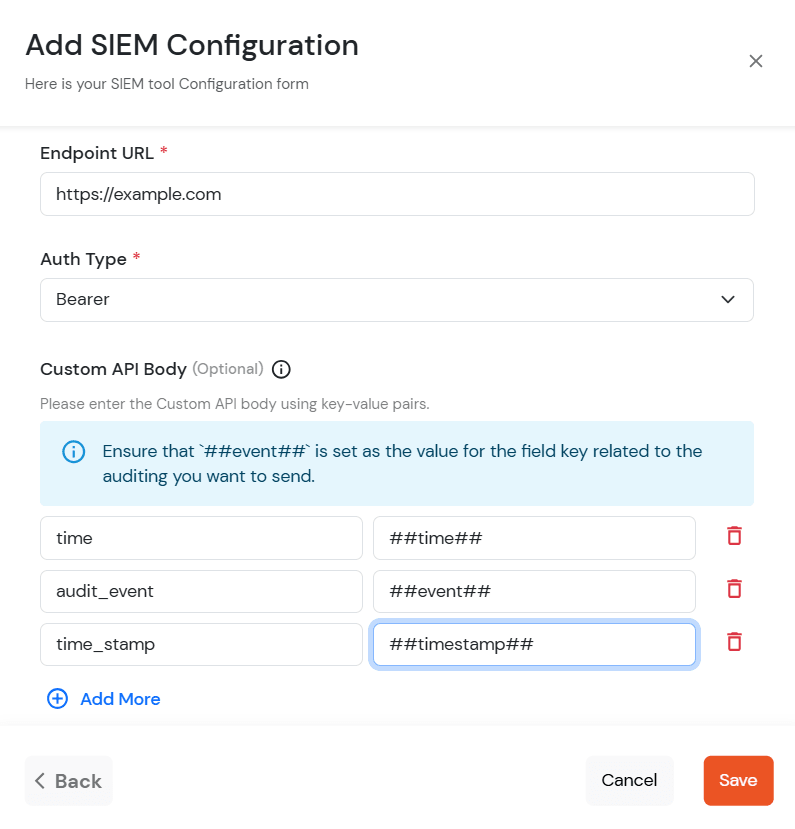
[If you configure custom api body, then ##event## is mandatory value field against any key]


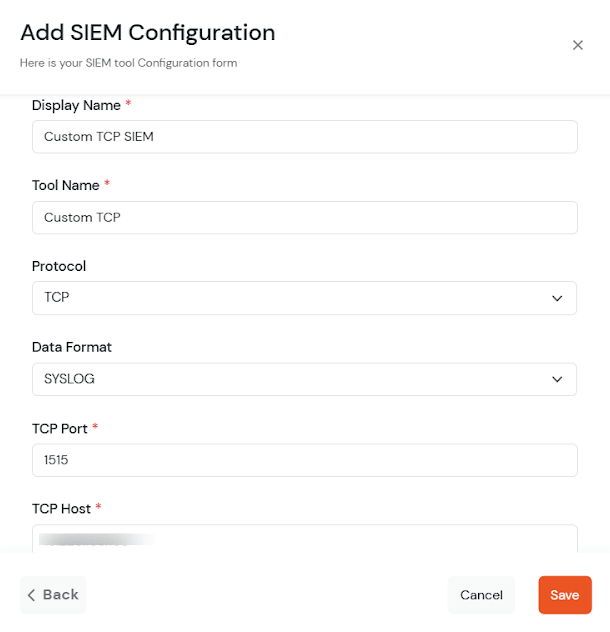
TCP Port and TCP Host are mandatory fields when the Protocol is TCP.
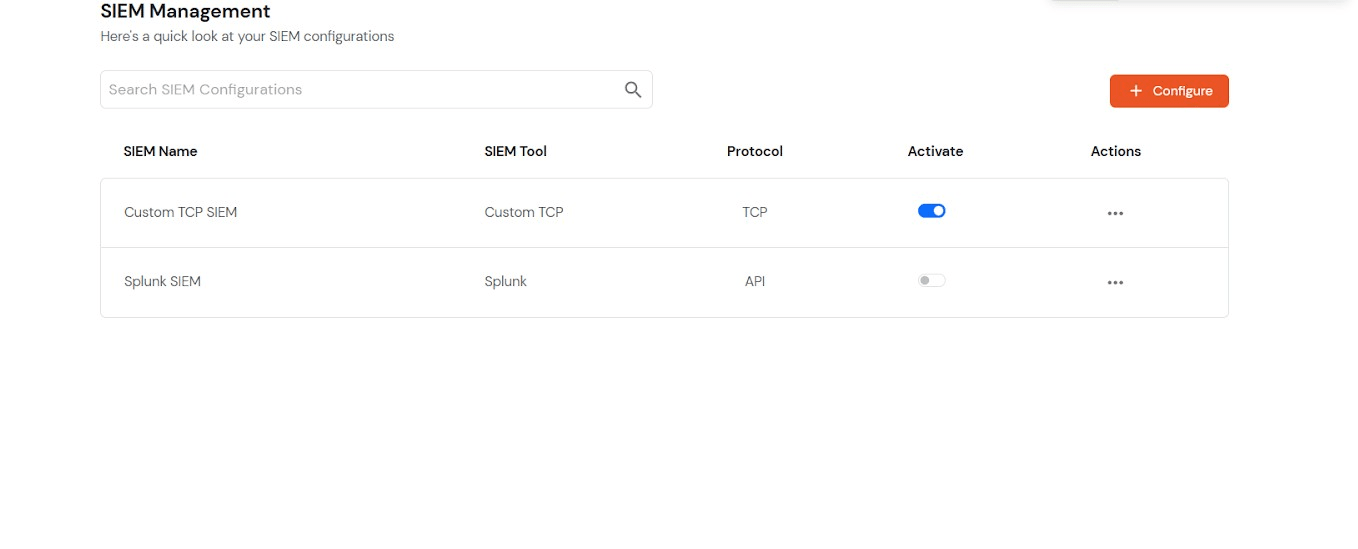
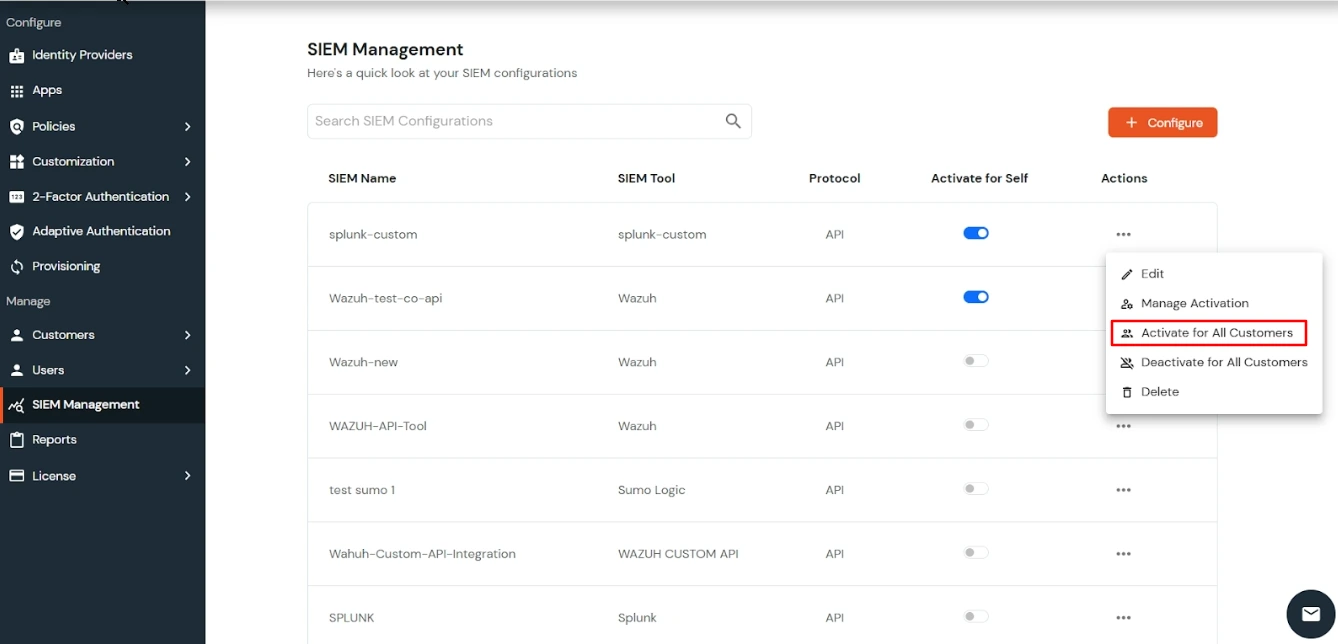
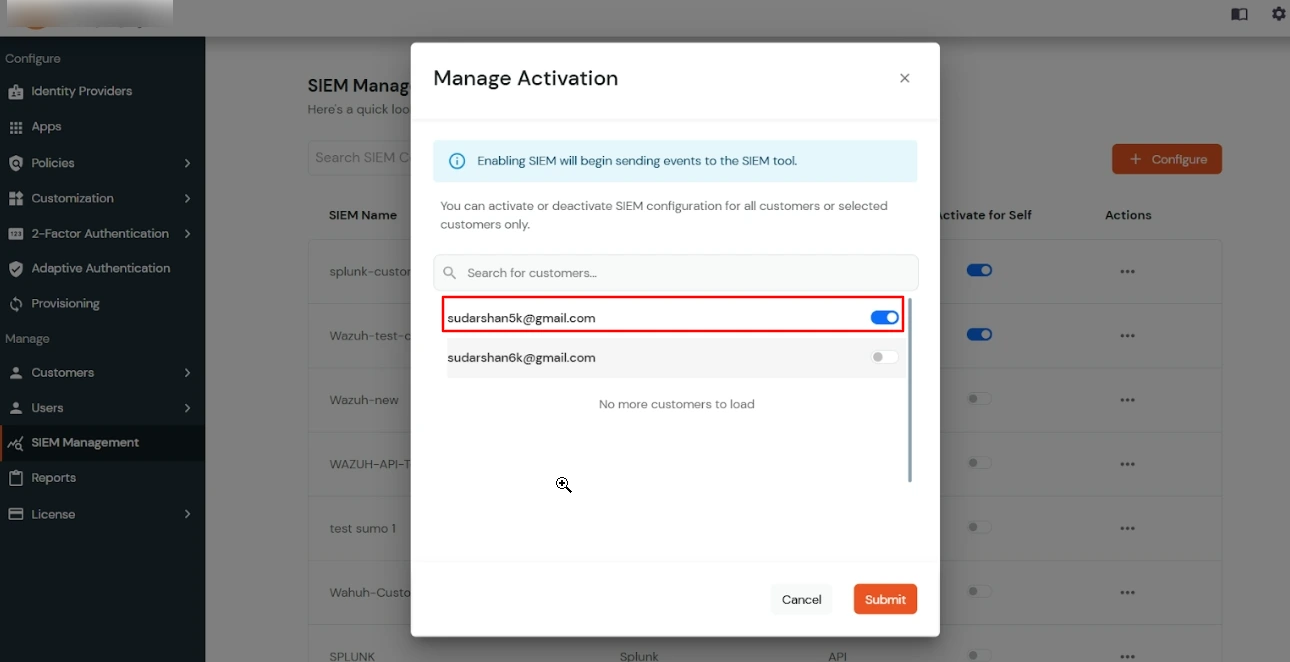
Superadmin can also activate the SIEM tool for customers using the Manage activation options. Admin can either activate the SIEM tool for all the customers using Activate For all customers option or can activate for individual customers using manage activation option available under the actions menu by clicking on 3 dots.
Please follow this guide to know more.